Dynamic Adaptation Attack Detection Model for a Distributed Multi-Access Edge Computing Smart City
Abstract
:1. Introduction
- A proposed model (IADM) produces model verification to detect and predict attacks using multi-class classification with high performance rates. Consider an intrusion detection model that is used to identify online threats. When a zero-day assault occurs on the system, the IDS repeatedly transmits the session records to a cybersecurity administrator to investigate the behaviors of users. The cybersecurity administrator marks the records as malicious or normal activities. This leads to introducing a false positive rate. Additionally, when the limits between the observation of normal and abnormal behaviors are not clear, normal activity changes quickly, which is difficult to learn offline.
- IADAM produces the detection model, which is used to prove this ability through the dynamic adaptation of the attack detection model based on reinforcement one-shot learning. The proposed model has the ability to autoconfigure and render any changed behaviors associated with the smart city environment as outdated. Autoconfiguration reduces false decisions in the system as it makes the system aware of zero-day attacks. Further, the model is adapted to the changed strategies based on a low number of instances. The reinforce learning method is used in the model to enable it to adapt to new and changed instances. One-shot learning is integrated into the model to create a comprehensive approach to a real-world system for categorizing major events from a limited number of training instances using computational power with constrained resources. Therefore, IADAM can use one-shot learning to achieve auto-adaptation rapidly using a lower number of instances.
2. Literature Review
3. Methodology
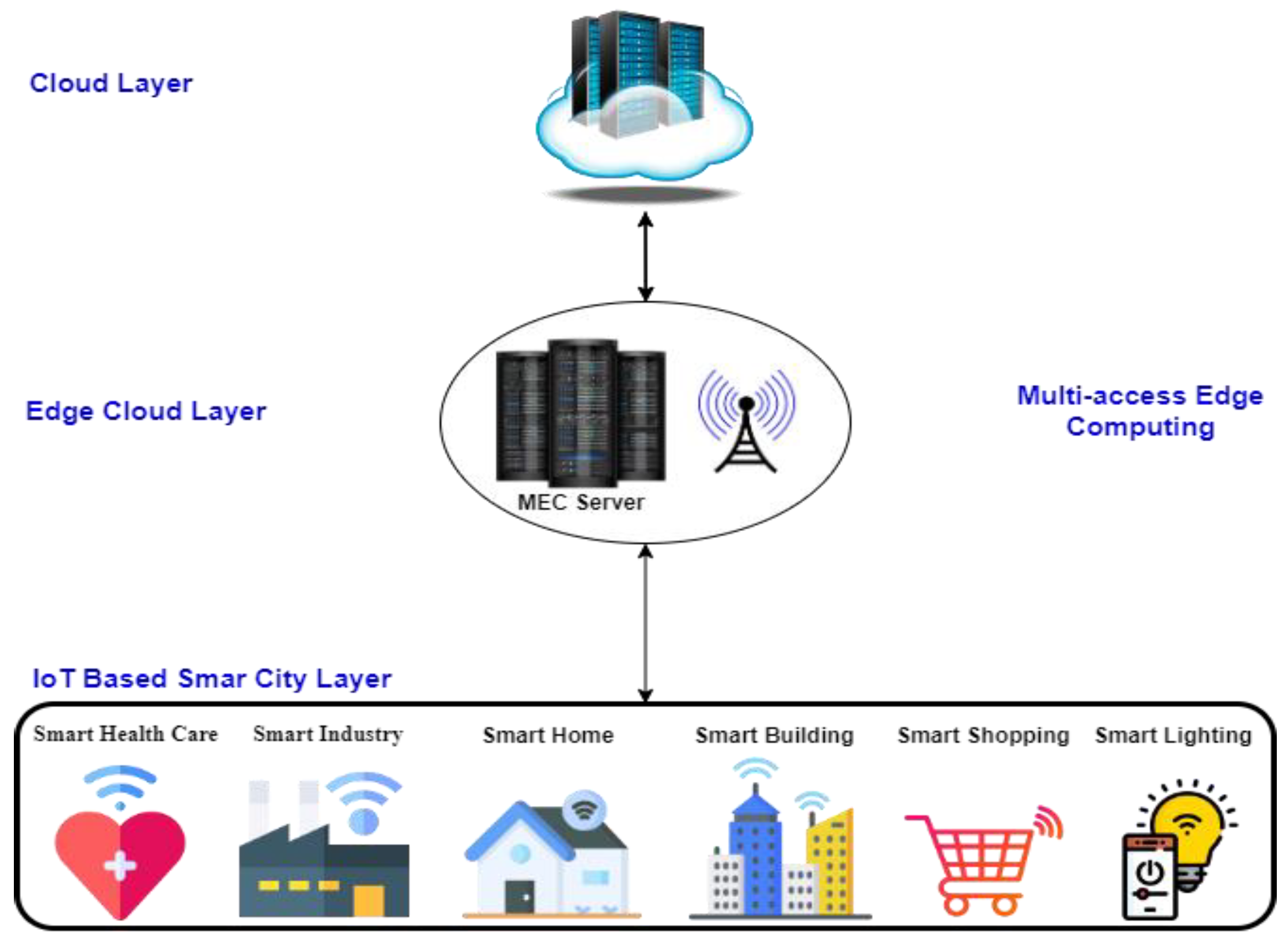
3.1. System Design
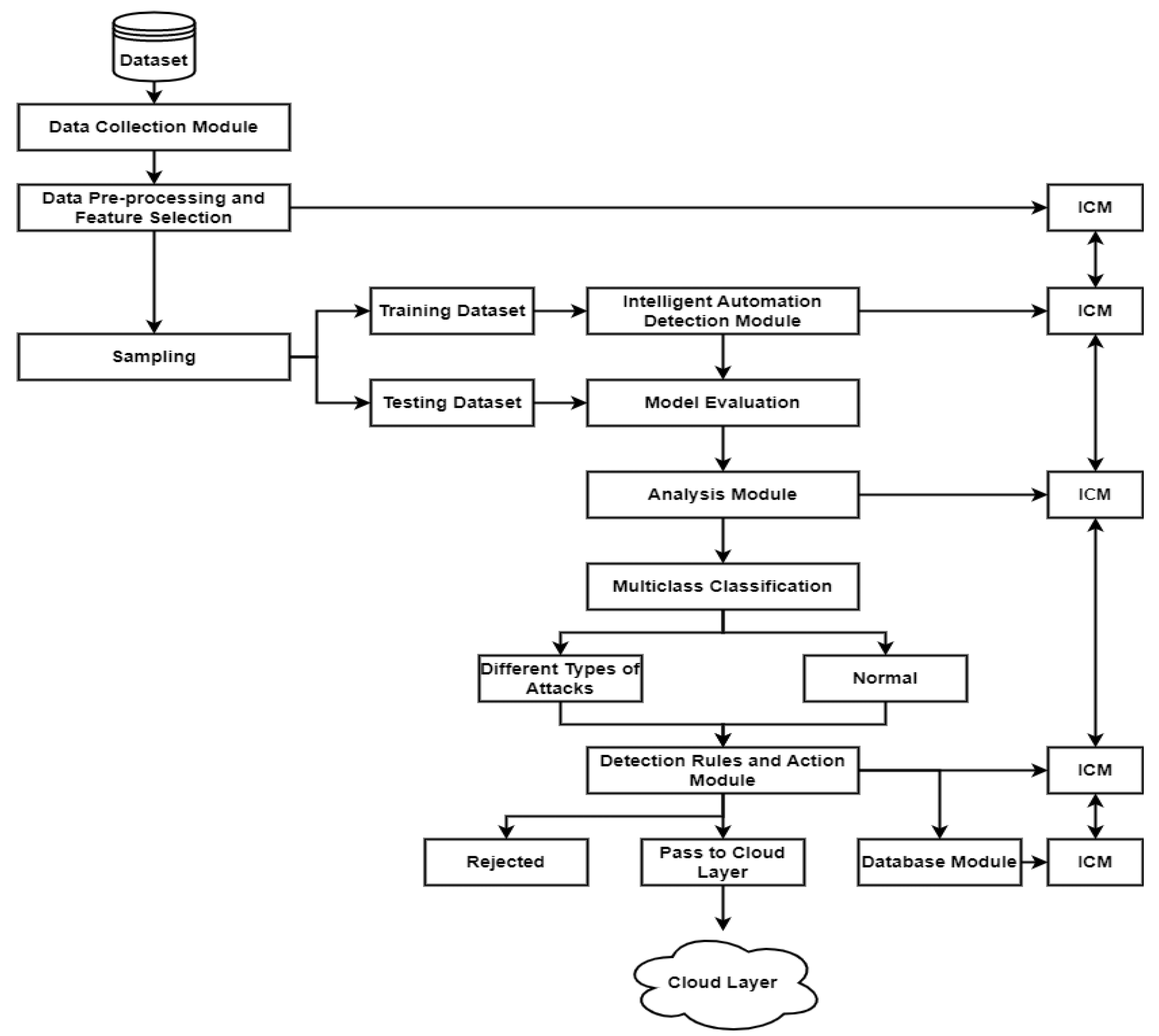
3.2. First Phase: An IADM Design Model Integrated within the IoT-Based Smart City
3.2.1. Dataset Collection and Pre-Processing Module
3.2.2. Intelligent Automation Detection Module
3.2.3. Analysis Module
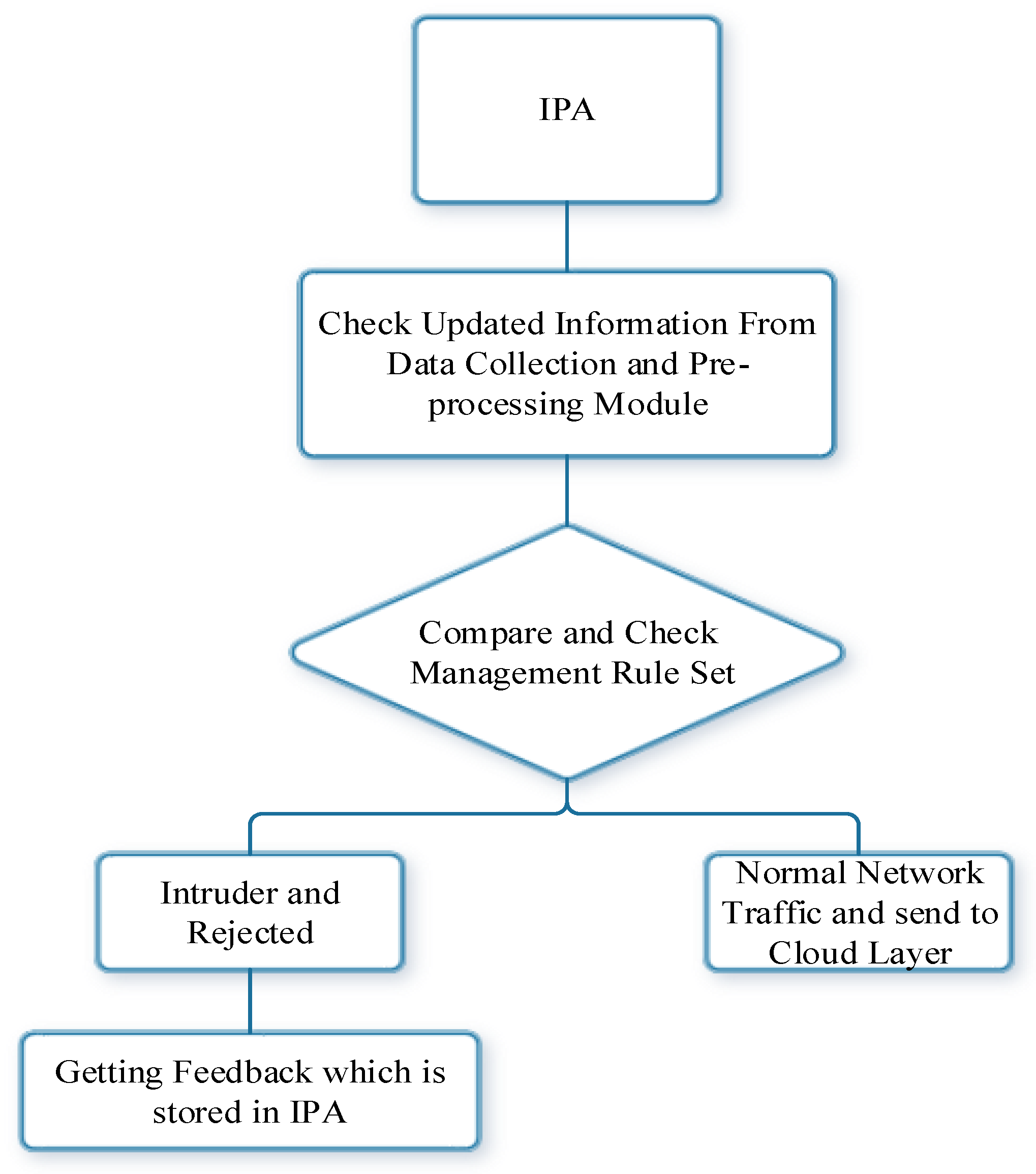
3.2.4. Detection Rules and Action Module
3.2.5. Database Module
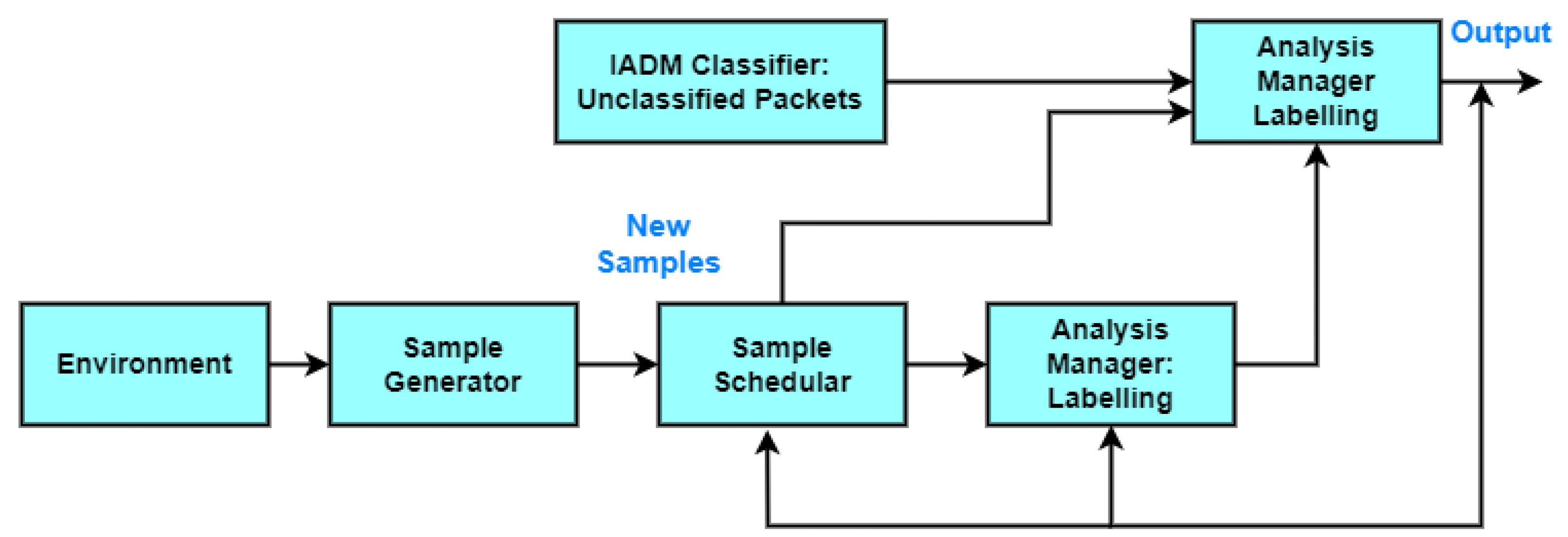
3.3. The Second Phase: Dynamic Adaptation of the Attack Detection Model Based on the Reinforcement of One-Shot Learning
4. Evaluation and Experimental Results
4.1. Datasets
4.2. Evaluation Criteria
4.3. Experimental Results of Dataset Pre-Processing
4.3.1. Experimental Results of the First Phase
4.3.2. Experimental Results of the Second Phase
5. Conclusions
Author Contributions
Funding
Institutional Review Board Statement
Informed Consent Statement
Data Availability Statement
Acknowledgments
Conflicts of Interest
References
- Rashid, M.M.; Kamruzzaman, J.; Hassan, M.M.; Imam, T.; Gordon, S. Cyberattacks detection in IoT-based smart city applications using machine learning techniques. Int. J. Environ. Res. Public Health 2020, 17, 9347. [Google Scholar] [CrossRef]
- Guevara, L.; Cheein, F.A. The role of 5g technologies: Challenges in smart cities and intelligent transportation systems. Sustainability 2020, 12, 6469. [Google Scholar] [CrossRef]
- McClellan, M.; Cervelló-Pastor, C.; Sallent, S. Deep learning at the mobile edge: Opportunities for 5g networks. Appl. Sci. 2020, 10, 4735. [Google Scholar] [CrossRef]
- Liang, C.; Shanmugam, B.; Azam, S.; Karim, A.; Islam, A.; Zamani, M.; Kavianpour, S.; Idris, N.B. Intrusion detection system for the internet of things based on blockchain and multi-agent systems. Electronics 2020, 9, 1120. [Google Scholar] [CrossRef]
- Coombs, C.; Hislop, D.; Taneva, S.K.; Barnard, S. The strategic impacts of intelligent automation for knowledge and service work: An interdisciplinary review. J. Strateg. Inf. Syst. 2020, 29, 101600. [Google Scholar] [CrossRef]
- Hasan, M.; Islam, M.M.; Zarif, M.I.I.; Hashem, M.M.A. Attack and anomaly detection in IoT sensors in IoT sites using machine learning approaches. Internet Things 2019, 7, 100059. [Google Scholar] [CrossRef]
- Alrashdi, I.; Alqazzaz, A.; Aloufi, E.; Alharthi, R.; Zohdy, M.; Ming, H. AD-IoT: Anomaly detection of IoT cyberattacks in smart city using machine learning. In Proceedings of the IEEE 9th Annual Computing and Communication Workshop and Conference (CCWC), Las Vegas, NV, USA; 2019; pp. 305–310. [Google Scholar]
- Hussain, F.; Abbas, S.G.; Fayyaz, U.U.; Shah, G.A.; Toqeer, A.; Ali, A. Towards a universal features set for IoT botnet attacks detection. In Proceedings of the 2020 IEEE 23rd International Multitopic Conference, Bahawalpur, Pakistan, 5–7 November 2020; pp. 1–7. [Google Scholar]
- Anthi, E.; Williams, L.; Slowinska, M.; Theodorakopoulos, G.; Burnap, P. A supervised intrusion detection system for smart home IoT devices. IEEE Internet Things J. 2019, 6, 9042–9053. [Google Scholar] [CrossRef]
- Al-Haija, Q.A.; Zein-Sabatto, S. An efficient deep-learning-based detection and classification system for cyber-attacks in IoT communication networks. Electronics 2020, 9, 2152. [Google Scholar] [CrossRef]
- Abeshu, A.; Chilamkurti, N. Deep Learning: The frontier for distributed attack detection in fog-to-things computing. IEEE Commun. Mag. 2018, 56, 169–175. [Google Scholar] [CrossRef]
- Koroniotis, N.; Moustafa, N.; Sitnikova, E.; Slay, J. Towards developing network forensic mechanism for botnet activities in the IoT based on machine learning techniques. Lect. Notes Inst. Comput. Sci. Soc.-Inform. Telecommun. Eng. 2018, 235, 30–44. [Google Scholar]
- Swarna Sugi, S.S.; Ratna, S.R. Investigation of machine learning techniques in intrusion detection system for IoT network. In Proceedings of the 3rd International Conference on Intelligent Sustainable Systems (ICISS), Thoothukudi, India, 3–5 December 2020. [Google Scholar]
- Nawir, M.; Amir, A.; Yaakob, N.; Lynn, O.B. Multi-classification of UNSW-NB15 Dataset for Network Anomaly Detection System. J. Theor. Appl. Inf. Technol. 2018, 96, 5094–5104. [Google Scholar]
- Moustafa, N.; Slay, J. UNSW-NB15: A comprehensive data set for network intrusion detection systems (UNSW-NB15 Network Data Set). In Proceedings of the Military Communications and Information Systems Conference (MilCIS), Canberra, ACT, Australia, 10–12 November 2015. [Google Scholar]
- UNSW_NB15 Kaggle. Available online: https://www.kaggle.com/datasets/mrwellsdavid/unsw-nb15 (accessed on 18 August 2022).
- Moustafa, N.; Slay, J. The evaluation of network anomaly detection systems: Statistical analysis of the UNSW-NB15 dataset and the comparison with the KDD99 dataset. Inf. Secur. J. Glob. Perspect. 2016, 25, 18–31. [Google Scholar] [CrossRef]
- Moustafa, N.; Slay, J.; Creech, G. Novel geometric area analysis technique for anomaly detection using trapezoidal area estimation on large-scale networks. IEEE Trans. Big Data 2017, 5, 481–494. [Google Scholar] [CrossRef]
- Schober, P.; Schwarte, L.A. Correlation coefficients: Appropriate use and interpretation. Anesth. Analg. 2018, 126, 1763–1768. [Google Scholar] [CrossRef] [PubMed]
- Syed, A.S.; Sierra-Sosa, D.; Kumar, A.; Elmaghraby, A. IoT in Smart Cities: A survey of technologies, practices and challenges. Smart Cities 2021, 4, 429–475. [Google Scholar] [CrossRef]
- Jawhar, I.; Mohamed, N.; Al-Jaroodi, J. Networking architectures and protocols for smart city systems. J. Internet Serv. Appl. 2018, 9, 26. [Google Scholar] [CrossRef] [Green Version]
- Abosata, N.; Al-Rubaye, S.; Inalhan, G.; Emmanouilidis, C. Internet of things for system integrity: A comprehensive survey on security, attacks and countermeasures for industrial applications. Sensors 2021, 21, 3654. [Google Scholar] [CrossRef]
- Kyriazopoulou, C. Smart city technologies and architectures: A literature review. In Proceedings of the International Conference on Smart Cities and Green ICT Systems (SMARTGREENS), Lisbon, Portugal, 20–22 May 2015; pp. 1–12. [Google Scholar]
- Ismagilova, E.; Hughes, L.; Dwivedi, Y.K.; Raman, K.R. Smart cities: Advances in research-An information systems perspective. Int. J. Inf. Manag. 2019, 47, 88–100. [Google Scholar] [CrossRef]
- Samih, H. Smart cities and internet of things. J. Inf. Technol. Case Appl. Res. 2019, 21, 312. [Google Scholar] [CrossRef] [Green Version]
- Jin, J.; Gubbi, J.; Marusic, S.; Palaniswami, M. An information framework for creating a smart city through internet of things. IEEE Internet Things J. 2014, 1, 112–121. [Google Scholar] [CrossRef]
- Shanthamallu, U.S.; Spanias, A.; Tepedelenlioglu, C.; Stanley, M. A brief survey of machine learning methods and their sensor and IoT applications. In Proceedings of the 8th International Conference on Information, Intelligence, Systems and Applications, IISA, Larnaca, Cyprus, 27–30 August 2017; pp. 1–8. [Google Scholar]
- Joshi, P.; Raghuvanshi, A.S. Hybrid approaches to address various challenges in wireless sensor network for IoT applications: Opportunities and open problems. Int. J. Comput. Netw. Appl. 2021, 8, 151–187. [Google Scholar] [CrossRef]
- Ullah, Z.; Al-Turjman, F.; Mostarda, L.; Gagliardi, R. Applications of artificial intelligence and machine learning in smart cities. Comput. Commun. 2020, 154, 313–323. [Google Scholar] [CrossRef]
- Zakaria, N.; Shamsi, J.A. Smart City Architecture: Vision and Challenges. Int. J. Adv. Comput. Sci. Appl. 2015, 6, 246–255. [Google Scholar] [CrossRef] [Green Version]
- Liang, C.; Shanmugam, B.; Azam, S.; Jonkman, M.; De Boer, F.; Narayansamy, G. Intrusion detection system for internet of things based on a machine learning approach. In Proceedings of the International Conference on Vision Towards Emerging Trends in Communication and Networking (ViTECoN), Vellore, India, 30–31 March 2019; pp. 1–6. [Google Scholar]
- Alsoufi, M.A.; Razak, S.; Siraj, M.M.; Nafea, I.; Ghaleb, F.A.; Saeed, F.; Nasser, M. Anomaly-based intrusion detection systems in iot using deep learning: A systematic literature review. Appl. Sci. 2021, 11, 8383. [Google Scholar] [CrossRef]
- Hajiheidari, S.; Wakil, K.; Badri, M.; Navimipour, N.J. Intrusion Detection Systems in The Internet of Things: A Comprehensive Investigation. Comput. Netw. 2019, 160, 165–191. [Google Scholar] [CrossRef]
- Wehbi, K.; Hong, L.; Al-Salah, T.; Bhutta, A.A. A survey on machine learning based detection on DDOS attacks for IoT systems. In Proceedings of the IEEE SOUTHEASTCON, Huntsville, AL, USA, 11–14 April 2019; pp. 1–6. [Google Scholar]
- Zheng, Y.; Pal, A.; Abuadbba, S.; Pokhrel, S.R.; Nepal, S.; Janicke, H. Towards IoT security automation and orchestration. In Proceedings of the TPS-ISA, Atlanta, GA, USA, 28–31 October 2020; pp. 55–63. [Google Scholar]
- Mishra, N.; Pandya, S. Internet of things applications, security challenges, attacks, intrusion detection, and future visions: A systematic review. IEEE Access 2021, 9, 59353–59377. [Google Scholar] [CrossRef]
- da Costa, K.A.P.; Papa, J.P.; Lisboa, C.O.; Munoz, R.; de Albuquerque, V.H.C. Internet of Things: A survey on machine learning-based intrusion detection approaches. Comput. Netw. 2019, 151, 147–157. [Google Scholar] [CrossRef]
- Laqtib, S.; El Yassini, K.; Hasnaoui, M.L. MANET: A survey on machine learning-based intrusion detection approaches. Int. J. Future Gener. Commun. Netw. 2019, 12, 55–70. [Google Scholar] [CrossRef]
- Zaman, S.; Tauqeer, H.; Ahmad, W.; Shah, S.M.A.; Ilyas, M. Implementation of intrusion detection system in the internet of things: A survey. In Proceedings of the IEEE 23rd International Multitopic Conference (INMIC), Bahawalpur, Pakistan, 5–7 November 2020; pp. 1–6. [Google Scholar]
- Manhas, J.; Kotwal, S. Implementation of intrusion detection system for internet of things using machine learning techniques. In Multimedia Security; Springer: Berlin/Heidelberg, Germany, 2021; pp. 217–237. [Google Scholar]
- Lv, L.; Wang, W.; Zhang, Z.; Liu, X. A novel intrusion detection system based on an optimal hybrid kernel extreme learning machine. Knowl.-Based Syst. 2020, 195, 105648. [Google Scholar] [CrossRef]
- Chakraborti, T.; Isahagian, V.; Khalaf, R.; Khazaeni, Y.; Muthusamy, V.; Rizk, Y.; Unuvar, M. From robotic process automation to intelligent process automation: Emerging trends. In Proceedings of the BPM 2020: Business Process Management: Blockchain and Robotic Process Automation Forum, Seville, Spain, 13–18 September 2020; Lecture Notes in Business Information Processing; Springer: Cham, Switzerland, 2020; Volume 393. [Google Scholar]
- Szelagowski, M.; Lupeikiene, A. Business process management systems: Evolution and development trends. Informatica 2020, 31, 579–595. [Google Scholar] [CrossRef]
- Berruti, F.; Nixo, G.; Taglioni, G.; Whiteman, R. Intelligent Process Automation: The Engine at the Core of the Next-Generation Operating Model; McKinsey & Company: Brussels, Belgium, 2017; pp. 1–9. [Google Scholar]
- Abdullahi, M.; Baashar, Y.; Alhussian, H.; Alwadain, A.; Aziz, N.; Capretz, L.F.; Abdulkadir, S.J. Detecting cybersecurity attacks in internet of things using artificial intelligence methods: A systematic literature review. Electronics 2022, 11, 198. [Google Scholar] [CrossRef]
- Chaabouni, N.; Mosbah, M.; Zemmari, A.; Sauvignac, C.; Faruki, P. Network intrusion detection for IoT security based on learning techniques. IEEE Commun. Surv. Tutor. 2019, 21, 2671–2701. [Google Scholar] [CrossRef]
- Ullah, I.; Mahmoud, Q.H. Design and development of a deep learning-based model for anomaly detection in IoT networks. IEEE Access 2021, 9, 103906–103926. [Google Scholar] [CrossRef]
- Raza, S.; Wang, S.; Ahmed, M.; Anwar, M.R. A survey on vehicular edge computing: Architecture, applications, technical issues, and future directions. Wirel. Commun. Mob. Comput. 2019, 2019, 3159762. [Google Scholar] [CrossRef]
- Gaur, A.; Scotney, B.; Parr, G.; McClean, S. Smart city architecture and its applications based on IoT. Procedia Comput. Sci. 2015, 52, 1089–1094. [Google Scholar] [CrossRef]
- Zhu, R.; Liu, L.; Song, H.; Ma, M. Multi-access edge computing enabled internet of things: Advances and novel applications. Neural Comput. Appl. 2020, 32, 1089–1094. [Google Scholar] [CrossRef]
- Taleb, T.; Dutta, S.; Ksentini, A.; Iqbal, M.; Flinck, H. Mobile Edge Computing Potential in Making Cities Smarter. IEEE Commun. Mag. 2017, 55, 38–43. [Google Scholar] [CrossRef] [Green Version]
- Shafiq, M.; Tian, Z.; Bashir, A.K.; Du, X.; Guizani, M. CorrAUC: A malicious bot-iot traffic detection method in iot network using machine-learning techniques. IEEE Internet Things J. 2021, 8, 3242–3254. [Google Scholar] [CrossRef]
- Ali, J.; Khan, R.; Ahmad, N.; Maqsood, I. Random forests and decision trees. Int. J. Comput. Sci. Issues (IJCSI) 2012, 9, 272–278. [Google Scholar]
- Cheng, D.; Zhang, S.; Deng, Z.; Zhu, Y.; Zong, M. k-NN Algorithm with Data-Driven K Value; Lecture Notes in Computer Science; Springer: Cham, Switzerland, 2014; Volume 8933, pp. 499–512. [Google Scholar]
- Kaur, G.; Chhabra, A. Improved J48 classification algorithm for the prediction of diabetes. Int. J. Comput. Appl. 2014, 98, 13–17. [Google Scholar] [CrossRef]
- Schapire, R.E. Explaining Adaboost. In Empirical Inference: Festschrift in Honor of Vladimir N. Vapnik; Springer: Berlin/Heidelberg, Germany, 2013. [Google Scholar]
- Hatwell, J.; Gaber, M.M.; Azad, R.M.A. Ada-WHIPS: Explaining AdaBoost classification with applications in the health sciences. BMC Med. Inform. Decis. Mak. 2020, 20, 250. [Google Scholar] [CrossRef] [PubMed]
- Kazllarof, V.; Kotsiantis, S. Active bagging ensemble selection. IFIP Adv. Inf. Commun. Technol. 2021, 628, 455–465. [Google Scholar]
- Sun, Q.; Pfahringer, B. Bagging ensemble selection. In Proceedings of the AI 2011: Australasian Joint Conference on Artificial Intelligence, Perth, Australia, 5–8 December 2011; Lecture Notes in Computer Science (Including Subseries Lecture Notes in Artificial Intelligence and Lecture Notes in Bioinformatics). Springer: Berlin/Heidelberg, Germany, 2011; Volume 7106. [Google Scholar]
- Ulvila, J.W.; Gaffney, J.E. Evaluation of intrusion detection systems. J. Res. Natl. Inst. Stand. Technol. 2003, 108, 453–473. [Google Scholar] [CrossRef]
- Sayed Ahmed, H.I.; Nasr, A.; Abdel-Mageid, S.M.; Aslan, H. Cross-Layer Distributed Attack Detection Model for the IoT. Int. J. Ambient. Comput. Intell. (IJACI) 2022, 13, 1–17. [Google Scholar] [CrossRef]
- Ahmed, H.I.; Nasr, A.A.; Abdel-Mageid, S.M.; Aslan, H.K. DADEM: Distributed attack detection model based on big data analytics for the enhancement of the security of internet of things (IoT). Int. J. Ambient. Comput. Intell. 2021, 12, 114–139. [Google Scholar] [CrossRef]
- Moustafa, N.; Creech, G.; Slay, J. Big data analytics for intrusion detection system: Statistical decision-making using finite dirichlet mixture models. In Data Analytics and Decision Support for Cybersecurity: Trends, Methodologies and Applications; Springer: Cham, Switzerland, 2017; pp. 127–156. [Google Scholar]
- AL-Hawawreh, M.; Moustafa, N.; Sitnikova, E. Identification of malicious activities in industrial internet of things based on deep learning models. J. Inf. Secur. Appl. 2018, 41, 1–11. [Google Scholar] [CrossRef]
- Koroniotis, N.; Moustafa, N.; Sitnikova, E. A new network forensic framework based on deep learning for internet of things networks: A particle deep framework. Future Gener. Comput. Syst. 2020, 110, 91–106. [Google Scholar] [CrossRef]
- Koch, G.; Zemel, R.; Salakhutdinov, R. Siamese neural networks for one-shot image recognition. In Proceedings of the 32nd International Conference on Machine Learning, Lille, France, 6–11 July 2015; Volume 31. [Google Scholar]
- Puzanov, A.; Zhang, S.; Cohen, K. Deep reinforcement one-shot learning for artificially intelligent classification in expert aided systems. Eng. Appl. Artif. Intell. 2020, 91, 103589. [Google Scholar] [CrossRef]
- Kong, X.; Bi, Y.; Glass, G.H. Anomaly detection in sequential data based on subsequence identification. J. Artif. Intell. Rev. 2020, 53, 625–652. [Google Scholar] [CrossRef]
- Kong, X.; Bi, Y.; Glass, G.H. Detecting seismic anomalies in outgoing long-wave radiation data. IEEE J. Sel. Top. Appl. Earth Obs. Remote Sens. 2015, 8, 649–660. [Google Scholar] [CrossRef]
- Bi, Y. The impact of diversity on the accuracy of evidential classifier ensembles. Int. J. Approx Reason. 2012, 53, 584–607. [Google Scholar] [CrossRef] [Green Version]
- Bi, Y.; Guan, J.; Bell, D.A. The combination of multiple classifiers using an evidential reasoning approach. Artif. Intell. 2008, 172, 1731–1751. [Google Scholar] [CrossRef] [Green Version]
- Abu Al-Haija, Q.; Al-Dala’ien, M. ELBA-IoT: An ensemble learning model for botnet attack detection in IoT networks. J. Sens. Actuator Netw. 2022, 11, 18. [Google Scholar] [CrossRef]
- Khalid, A.; Abu Al-Haija, Q.; Alsuhibany, S.A.; Jillepalli, A.A.; Ashrafuzzaman, M.; Sheldon, F.T. IoT intrusion detection using machine learning with a novel high performing feature selection method. Appl. Sci. 2022, 12, 5015. [Google Scholar]
- Abu Al-Haija, Q.; Al-Badawi, A. Attack-Aware IoT network traffic routing leveraging ensemble learning. Sensors 2022, 22, 241. [Google Scholar] [CrossRef]
- Abdulaziz, A.A.; Al-Haija, Q.A.; Tayeb, A.; Alqahtani, A. An intrusion detection and classification system for IoT traffic with improved data engineering. Appl. Sci. 2022, 12, 12336. [Google Scholar]
- Ahmad, M.; Riaz, Q.; Zeeshan, M.; Tahir, H.; Haider, S.A.; Khan, M.S. Intrusion detection in internet of things using supervised machine learning based on application and transport layer features using UNSW-NB15 data-set. EURASIP J. Wirel. Commun. Netw. 2021, 10, 1–23. [Google Scholar] [CrossRef]
- Sonule, A.R.; Kalla, M.; Jain, A.; Chouhan, D.S. Unsw-Nb15 dataset and machine learning based intrusion detection systems. Int. J. Eng. Adv. Technol. 2020, 9, 2638–2648. [Google Scholar] [CrossRef]




| Proposed Model | Methodology | Multiple Classification (MC)/Binary Classification (BC) | Auto-Adaptively Based on a Few Numbers of Instances | IoT Scalability Support | Performance Metrics |
|---|---|---|---|---|---|
| [1] M. M. Rashid et al., 2020 | Machine learning algorithms | MC | × | × | AC, precision, recall, and F1-score: approximately 95%, 94%, and 94%, respectively. |
| [4] C. Liang et al., 2020 | Multi-module system and blockchain using reinforcement algorithms | BC | × | × | AC, precision, recall, and F-scores of 83.9%, 85.53%, 84.14%, and 83.94%, respectively. |
| [7] I. Alrashdi et al., 2019. AD-IoT | Machine learning algorithm | BC | × | × | AC, false positive rate, and DR: 99.34%, 2%, and 82%, respectively. |
| [9] E. Anthi et al., 2019 | Machine learning algorithms | BC | × | × | Precision, F-measure, and recall: 96.2%, 90.0%, and 98.0%, respectively. |
| [10] Q. A. Al-Haija and S. Zein-Sabatto, 2020. IoT-IDCS-CNN | Deep learning | BC and MC | × | × | AC of the binary and multi-class classifications of 99.3% and 98.2%, respectively. |
| IADM | Machine learning techniques and deep one-shot learning | MC | Support auto-adaptivity by applying one-shot learning | Support the scalability manner of IoT | AC, error, precision, recall, F-measure: 98.8%. 2.4%, 97%, and 97%, respectively. |
| Attributes | Correlation | Attributes | Correlation |
|---|---|---|---|
| ct_dst_sport_ltm | 80.35% | is_sm_ips_ports | 59.04% |
| ct_src_dport_ltm | 71.01% | ct_ftp_cmd | 57.6% |
| ct_dst_src_ltm | 69.95% | Service | 56.3% |
| ct_srv_dst | 67.34% | response_body_len | 55.02% |
| ct_srv_src | 66.83% | Sbytes | 54.9% |
| ct_dst_ltm | 64.90% | Rate | 52.7% |
| Id | 63.7% | Sttl | 51.7% |
| is_ftp_login | 60.9% |
| The Performance Metrics | RFT | K-NN | J48 | AdaBoost | Bagging |
|---|---|---|---|---|---|
| AC | 97.99% | 97.99% | 85.5% | 97.99% | 91.4% |
| Error | 2.1% | 2.1% | 14.5% | 2.1% | 8.6% |
| Precision | 98% | 98% | 80.9% | 98% | 91.6% |
| Recall | 98% | 98% | 82.5% | 98% | 91.4% |
| F-measure | 97.5% | 97.5% | 79.5% | 97.5% | 91.1% |
| TP Rate | FP Rate | Precision | Recall | F-Measure | Class |
|---|---|---|---|---|---|
| 97.9% | 2.1% | 97.9% | 97.9% | 97.9% | Analysis |
| 97.5% | 2.5% | 97.5% | 97.5% | 97.5% | Backdoor |
| 97.9% | 2.1% | 97.9% | 97.9% | 97.9% | DoS |
| 97.9% | 2.1% | 97.9% | 97.9% | 97.9% | Exploits |
| 97.9% | 2.1% | 97.9% | 97.9% | 97.9% | Fuzzers |
| 97.9% | 2.1% | 97.9% | 97.9% | 97.9% | Reconnaissance |
| 97.9% | 2.1% | 97.9% | 97.9% | 97.9% | Shellcode |
| 97.9% | 2.1% | 97.9% | 97.9% | 97.9% | Worms |
| 97.9% | 2.1% | 97.9% | 97.9% | 97.9% | Normal |
| TP | FP | Precision | Recall | F-Measure | Class |
|---|---|---|---|---|---|
| 97.9% | 2.1% | 97.9% | 97.9% | 98.9% | Analysis |
| 97.9% | 2.1% | 97.9% | 97.9% | 98.9% | Backdoor |
| 97.9% | 2.1% | 97.9% | 97.9% | 98.9% | DoS |
| 97.9% | 2.1% | 97.9% | 97.9% | 98.9% | Exploits |
| 97.9% | 2.1% | 97.9% | 97.9% | 98.9% | Fuzzers |
| 97.9% | 2.1% | 97.9% | 97.9% | 98.9% | Reconnaissance |
| 97.9% | 2.1% | 97.9% | 97.9% | 98.9% | Shellcode |
| 97.9% | 2.1% | 97.9% | 97.9% | 98.9% | Worms |
| 97.9% | 2.1% | 97.9% | 97.9% | 98.9% | Normal |
| TP | FP | Precision | Recall | F-Measure | Class |
|---|---|---|---|---|---|
| 23.4% | 14.7% | 90.2% | 23.4% | 37.2% | Analysis |
| 48.8% | 11.7% | 72.1% | 48.8% | 58.2% | Backdoor |
| 79% | 1.4% | 76.2% | 70% | 14.3% | DoS |
| 97.4% | 0.1% | 67.4% | 97.4% | 79.7% | Exploits |
| 89.9% | 0.7% | 96.3% | 89.9% | 93.0% | Fuzzers |
| 77.5% | 0.3% | 95.2% | 77.5% | 85.4% | Reconnaissance |
| 80.2% | 0.2% | 82.6% | 80.2% | 81.4% | Shellcode |
| 58.1% | 9.1% | 58.1% | 69.4% | 70.8% | Worms |
| 99.7% | 0.2% | 99.6% | 99.7% | 99.6% | Normal |
| TP | FP | Precision | Recall | F-Measure | Class |
|---|---|---|---|---|---|
| 97.9% | 2.1% | 97.9% | 97.9% | 97.9% | Analysis |
| 97.9% | 2.1% | 97.9% | 97.9% | 97.9% | Backdoor |
| 97.9% | 2.1% | 97.9% | 97.9% | 97.9% | DoS |
| 97.9% | 2.1% | 97.9% | 97.9% | 97.9% | Exploits |
| 97.9% | 2.1% | 97.9% | 97.9% | 97.9% | Fuzzers |
| 97.9% | 2.1% | 97.9% | 97.9% | 97.9% | Reconnaissance |
| 97.9% | 2.1% | 97.9% | 97.9% | 97.9% | Shellcode |
| 97.9% | 2.1% | 97.9% | 97.9% | 97.9% | Worms |
| 97.9% | 2.1% | 97.9% | 98.9% | 97.9% | Normal |
| TP | FP | Precision | Recall | F-Measure | Class |
|---|---|---|---|---|---|
| 49.8% | 13.1% | 90.2% | 49.8% | 64.4% | Analysis |
| 67.9% | 7.82% | 84.0% | 67.9% | 75.1% | Backdoor |
| 58.4% | 11.7% | 58.4% | 66.5% | 64.4% | DoS |
| 95.7% | 0.8% | 81.8% | 95.7% | 88.2% | Exploits |
| 93.5% | 0.5% | 97.0% | 93.5% | 95.3% | Fuzzers |
| 86.0% | 0.3% | 96.1% | 86.0% | 90.7% | Reconnaissance |
| 88.6% | 0.1% | 90.3% | 88.6% | 89.4% | Shellcode |
| 60.5% | 9.7% | 92.9% | 60.5% | 73.2% | Worms |
| 99.8% | 0.1% | 99.9% | 99.8% | 99.8% | Normal |
| Machine Learning Algorithms | RFT | K-NN | J48 | AdaBoost | Bagging |
|---|---|---|---|---|---|
| Time | 1.6 msec. | 5.0 msec. | 6 msec. | 14 msec | 37 msec |
| Class | Algorithms | ||||
|---|---|---|---|---|---|
| RFT | K-NN | J48 | AdaBoost | Bagging | |
| Analysis | 98.9% | 98.9 | 36.4% | 98.9 | 83.2% |
| Backdoor | 98.9% | 98.9 | 47.8% | 98.9 | 85.4% |
| DoS | 98.9% | 98.9 | 37.5% | 98.9 | 81.6% |
| Exploits | 98.9% | 98.9 | 83.4% | 98.9 | 96.5% |
| Fuzzers | 98.9% | 98.9 | 94.8% | 98.9 | 99.3% |
| Recon-Naissance | 98.9% | 98.9 | 87.6% | 98.9 | 97.8% |
| Shellcode | 98.9% | 98.9 | 85.3% | 98.9 | 95.6% |
| Worms | 98.9% | 98.9 | 64.7% | 98.9 | 91.7% |
| Normal | 98.9% | 98.9 | 100% | 98.9 | 100% |
| Weighted Average | 98.9% | 98.9 | 86.0% | 98.9 | 96.6% |
Disclaimer/Publisher’s Note: The statements, opinions and data contained in all publications are solely those of the individual author(s) and contributor(s) and not of MDPI and/or the editor(s). MDPI and/or the editor(s) disclaim responsibility for any injury to people or property resulting from any ideas, methods, instructions or products referred to in the content. |
© 2023 by the authors. Licensee MDPI, Basel, Switzerland. This article is an open access article distributed under the terms and conditions of the Creative Commons Attribution (CC BY) license (https://creativecommons.org/licenses/by/4.0/).
Share and Cite
Alotaibi, N.S.; Ahmed, H.I.; Kamel, S.O.M. Dynamic Adaptation Attack Detection Model for a Distributed Multi-Access Edge Computing Smart City. Sensors 2023, 23, 7135. https://doi.org/10.3390/s23167135
Alotaibi NS, Ahmed HI, Kamel SOM. Dynamic Adaptation Attack Detection Model for a Distributed Multi-Access Edge Computing Smart City. Sensors. 2023; 23(16):7135. https://doi.org/10.3390/s23167135
Chicago/Turabian StyleAlotaibi, Nouf Saeed, Hassan Ibrahim Ahmed, and Samah Osama M. Kamel. 2023. "Dynamic Adaptation Attack Detection Model for a Distributed Multi-Access Edge Computing Smart City" Sensors 23, no. 16: 7135. https://doi.org/10.3390/s23167135
APA StyleAlotaibi, N. S., Ahmed, H. I., & Kamel, S. O. M. (2023). Dynamic Adaptation Attack Detection Model for a Distributed Multi-Access Edge Computing Smart City. Sensors, 23(16), 7135. https://doi.org/10.3390/s23167135






