A Method for Detecting LDoS Attacks in SDWSN Based on Compressed Hilbert–Huang Transform and Convolutional Neural Networks
Abstract
1. Introduction
- Redundant and similar IMFs in HHT were compressed to reduce the computation complexity and solve the modal mixing problem.
- Designed and implemented HCN, in which the compressed HHT was combined with CNN. HCN converted one-dimensional dataflow feature sequences into two-dimensional spectrogram features and then classified dataflows with CNN to improve the detection performance.
- Our simulated network environment was driven by real data traffic. The experimental results showed that the HCN was able to achieve an accuracy of 99.8%.
2. Related Work
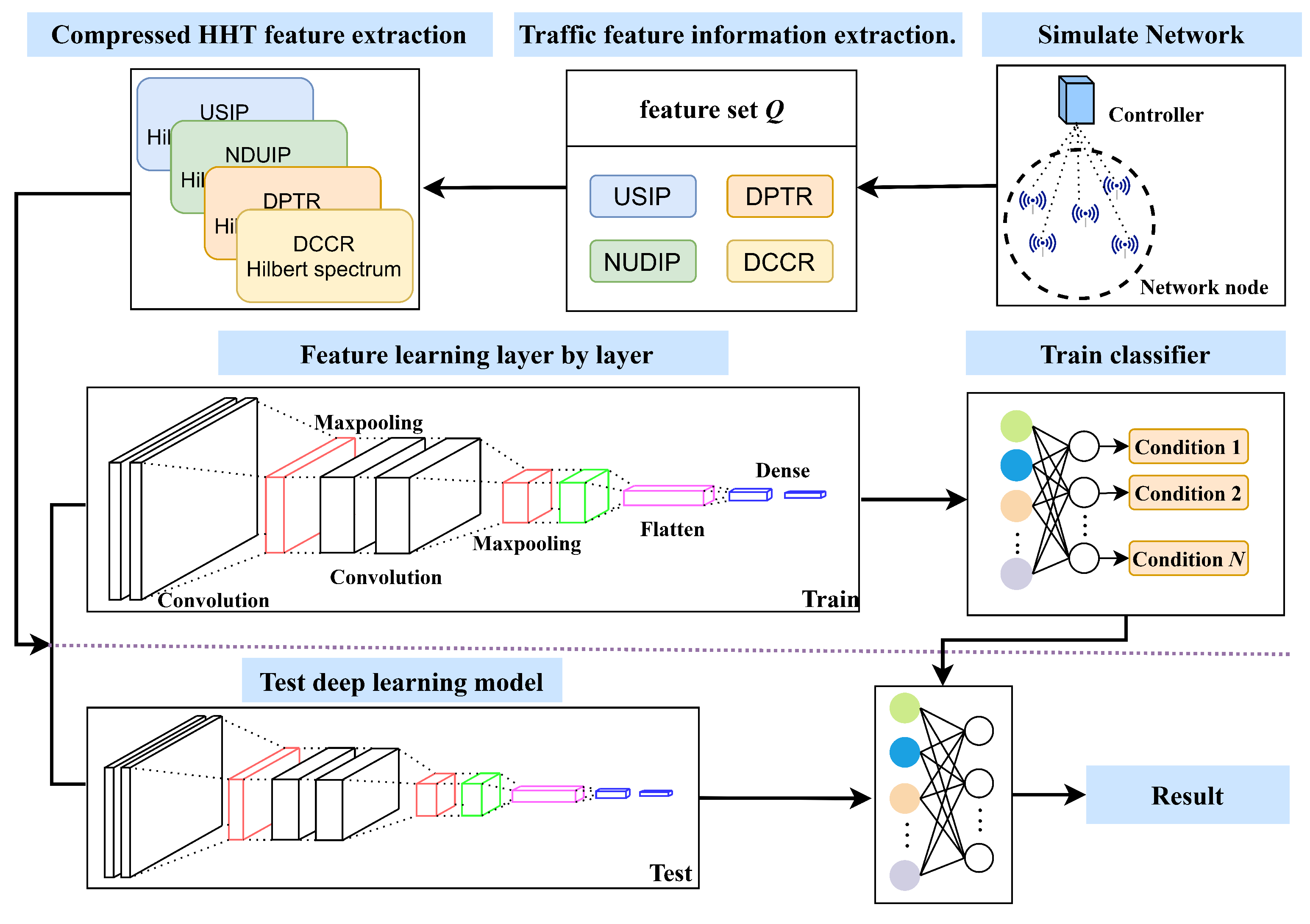
3. HCN Detection Method
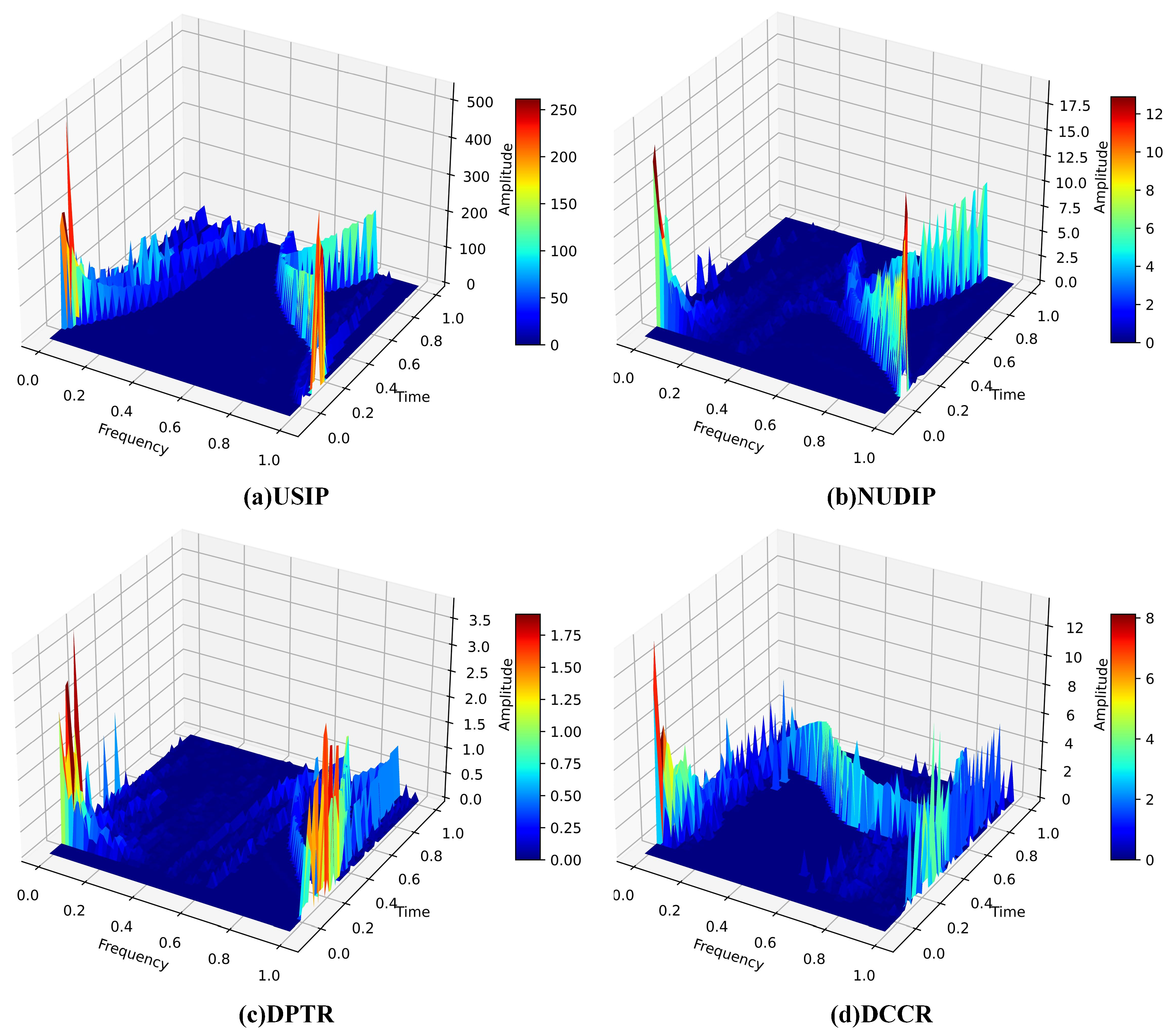
3.1. Traffic Feature Information Extraction
| Algorithm 1 Traffic feature information extraction. |
Require: Network traffic data Ensure: Feature set Q 1: for
do 2: for each time interval t do 3: if then 4: 5: else 6: 7: end if 8: if then 9: 10: else 11: 12: end if 13: 14: 15: 16: 17: end for 18: end for |
3.2. Compressed HHT
3.3. Frequency–Domain Feature Extraction
| Algorithm 2 Frequency–Domain Feature Extraction. |
Require: Ensure: 1: count ← 0 2: for in Q do 3: for each time interval t do 4: Statistics 5: if then 6: ; where stands for concatenation. 7: 8: else 9: 10: end if 11: ; where 12: end for 13: ; where 14: end for |
- In a local interval of the data, the number of extreme points of a function is equal to or differs from the number of zeros by, at most, one, and these extreme points and zeros appear alternately;
- The average value of a function over the entire data range is zero;
- The frequency of a function in a local interval varies monotonically with time.
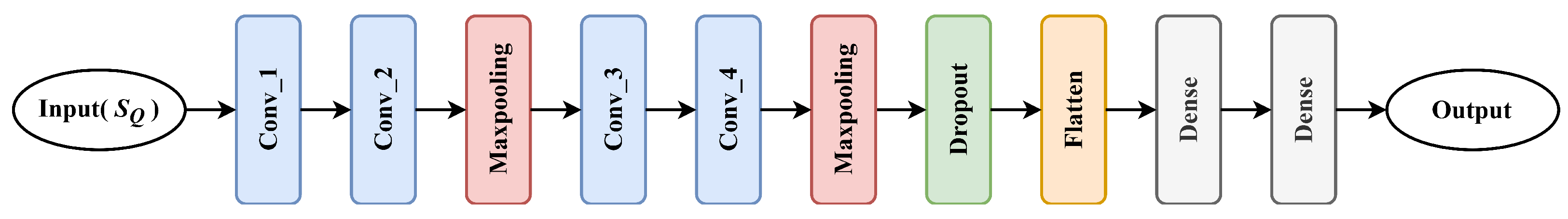
3.4. The HCN Model
| Algorithm 3 The HCN model for classification. |
Require: , two-dimensional spectrum. Ensure: , accuracy of HCN classification. 1: for do 2: for do 3: HCN ←, training HCN models. 4: Save training parameters. 5: end for 6: for do 7: HCN ←, input testing dataset to the trained HCN model. 8: ← HCN, calculating the accuracy of model judgments. 9: end for 10: Take the average of the accuracy rate of each epoch. 11: end for |
4. Experiment
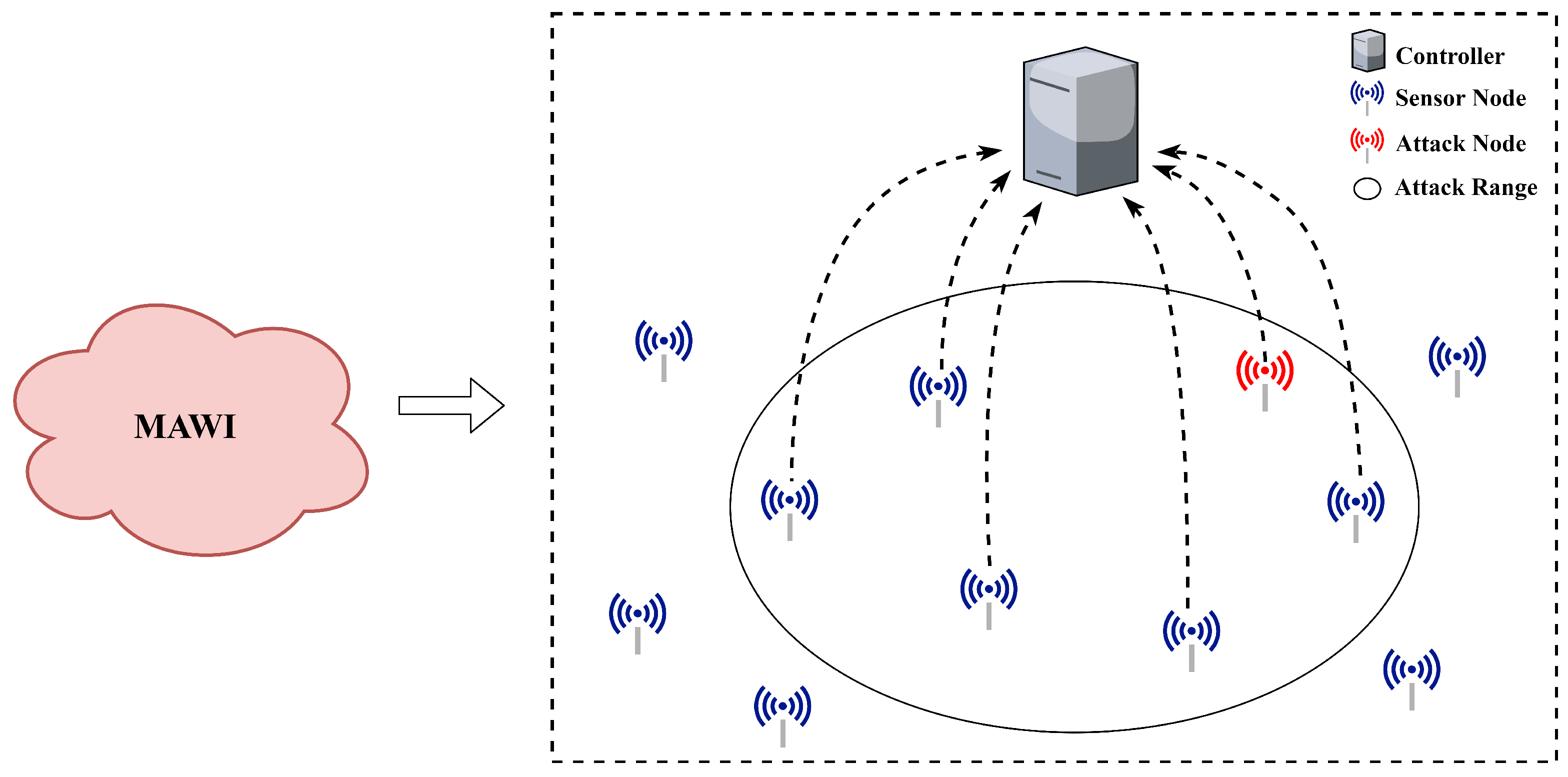
4.1. The Network Topology
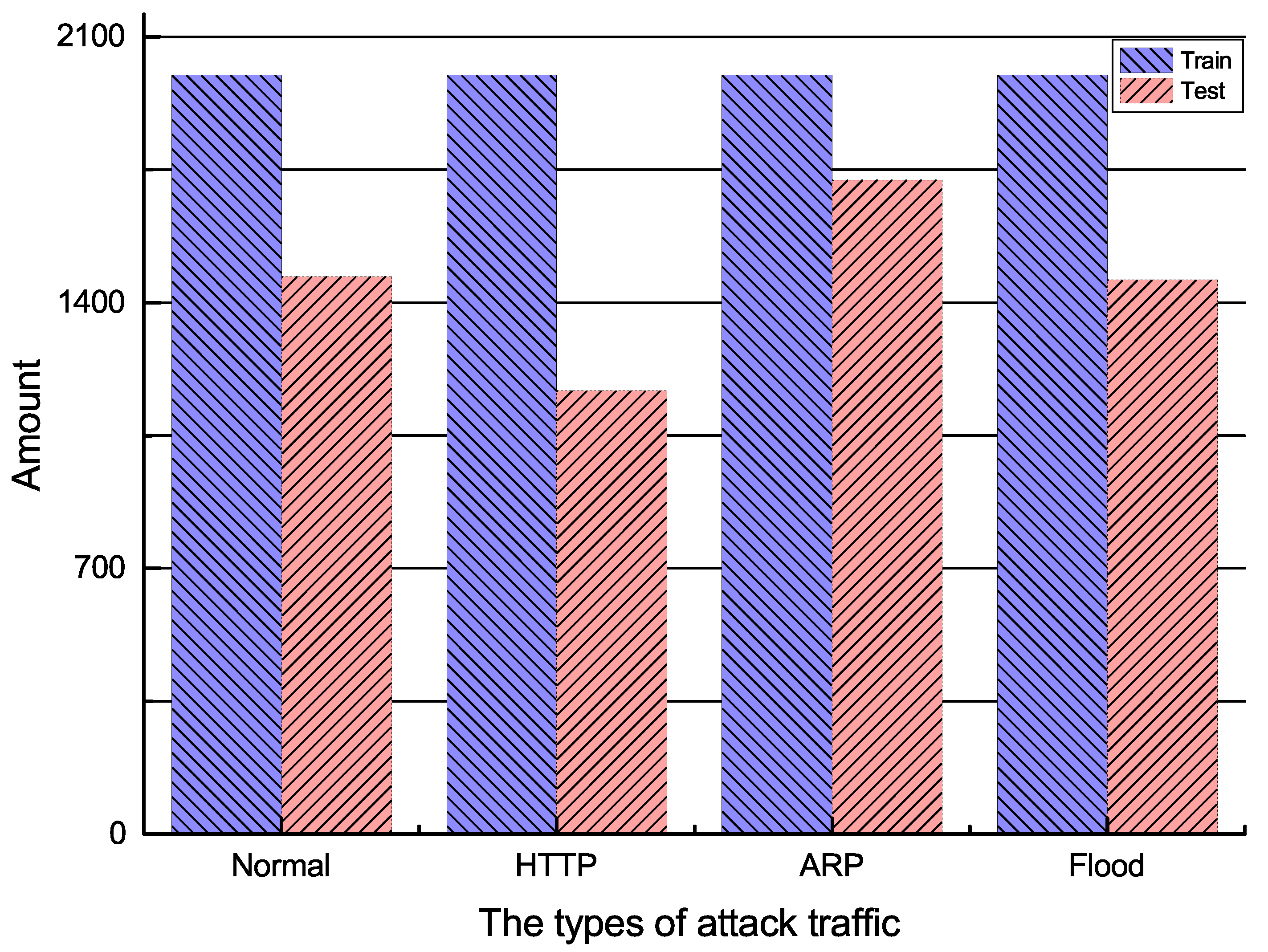
4.2. Dataset
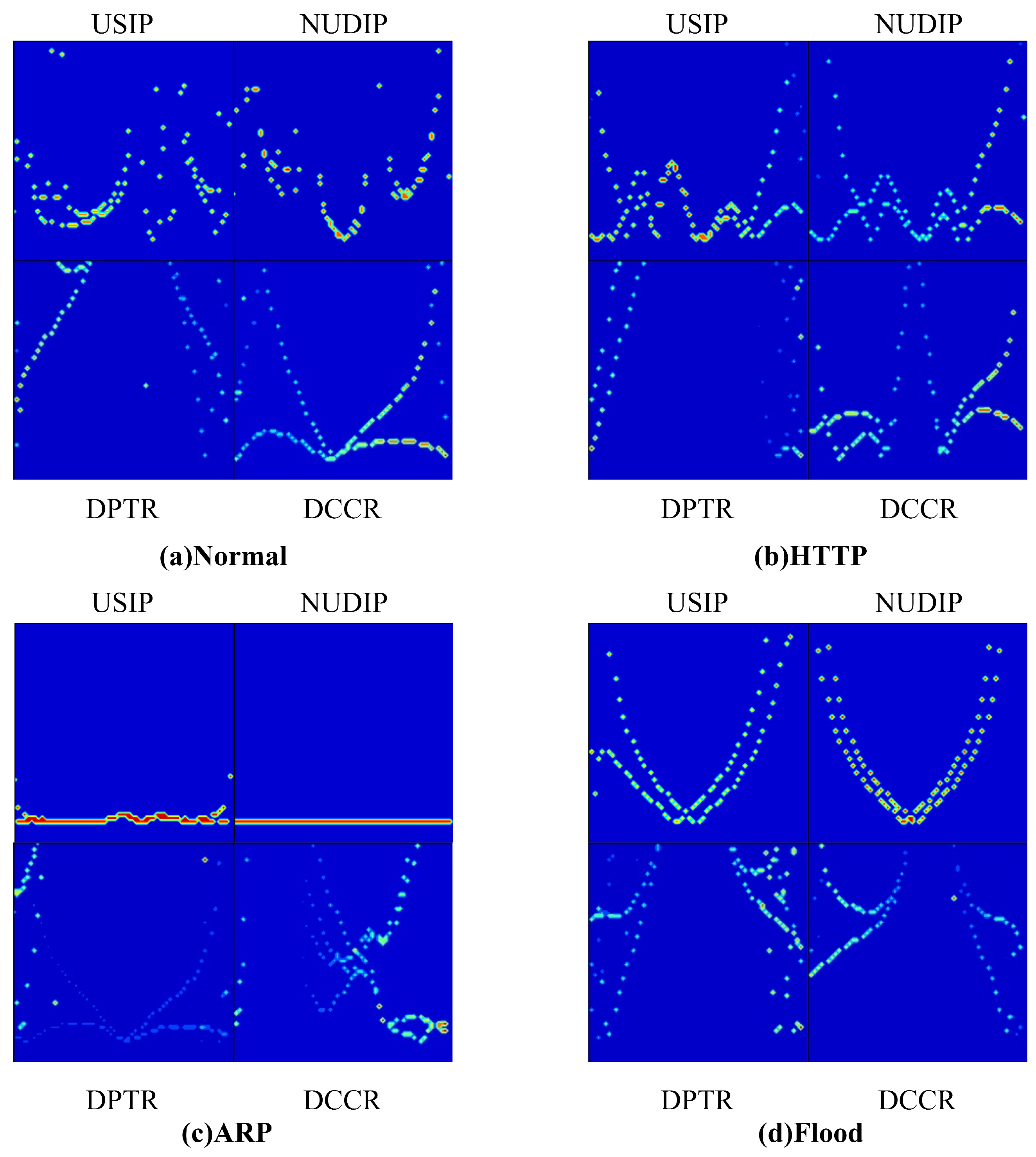
- HTTP slow DoS attack: exhausts the resources of the target server by continuously sending incomplete or intentionally slow connection requests in order to achieve the attack purpose;
- ARP attack: deceives other nodes in the network by changing the destination IP address of the traffic in the network to the victim’s IP address;
- Flood attack: overloads the network and lowers its availability by sending a large amount of data traffic or control messages to the network.
4.3. Experiment Results
5. Conclusions
Author Contributions
Funding
Institutional Review Board Statement
Informed Consent Statement
Data Availability Statement
Conflicts of Interest
Abbreviations
| LDoS | Low-Rate Denial of Service |
| SDWSN | Software-Defined Wireless Sensor Network |
| HHT | Hilbert–Huang Transform |
| IMF | Intrinsic Mode Function |
| EMD | Empirical Mode Decomposition |
| USIP | The total number of unique source IP addresses |
| NUDIP | The normalized number of total unique destination IP addresses |
| DPTR | The differential packet transform rate |
| DCCR | The differential network connection conversion rate |
References
- Modieginyane, K.M.; Letswamotse, B.B.; Malekian, R.; Abu-Mahfouz, A.M. Software defined wireless sensor networks application opportunities for efficient network management: A survey. Comput. Electr. Eng. 2018, 66, 274–287. [Google Scholar] [CrossRef]
- Gong, B.; Zheng, G.; Waqas, M.; Tu, S.; Chen, S. LCDMA: Lightweight Cross-domain Mutual Identity Authentication Scheme for Internet of Things. IEEE Internet Things J. 2023. [Google Scholar] [CrossRef]
- Gao, J.; Chai, S.; Zhang, B.; Xia, Y. Research about DoS Attack against ICPS. Sensors 2019, 19, 1542. [Google Scholar] [CrossRef]
- De Almeida, M.P.; De Sousa Júnior, R.T.; García Villalba, L.J.; Kim, T.H. New DoS Defense Method Based on Strong Designated Verifier Signatures. Sensors 2018, 18, 2813. [Google Scholar] [CrossRef]
- David, J.; Thomas, C. Efficient DDoS flood attack detection using dynamic thresholding on flow-based network traffic. Comput. Secur. 2019, 82, 284–295. [Google Scholar] [CrossRef]
- Tang, D.; Wang, X.; Li, X.; Vijayakumar, P.; Kumar, N. AKN-FGD: Adaptive Kohonen Network Based Fine-Grained Detection of LDoS Attacks. IEEE Trans. Dependable Secur. Comput. 2023, 20, 273–287. [Google Scholar] [CrossRef]
- Tang, D.; Gao, C.; Li, X.; Liang, W.; Xiao, S.; Yang, Q. A Detection and Mitigation Scheme of LDoS Attacks via SDN Based on the FSS-RSR Algorithm. IEEE Trans. Netw. Sci. Eng. 2023, 1–12. [Google Scholar] [CrossRef]
- Zhan, S.; Tang, D.; Man, J.; Dai, R.; Wang, X. Low-Rate DoS Attacks Detection Based on MAF-ADM. Sensors 2020, 20, 189. [Google Scholar] [CrossRef]
- Tang, D.; Wang, S.; Liu, B.; Jin, W.; Zhang, J. GASF-IPP: Detection and Mitigation of LDoS Attack in SDN. IEEE Trans. Serv. Comput. 2023, 1–12. [Google Scholar] [CrossRef]
- Makuvaza, A.; Jat, D.S.; Gamundani, A.M. Deep Neural Network (DNN) Solution for Real-time Detection of Distributed Denial of Service (DDoS) Attacks in Software Defined Networks (SDNs). SN Comput. Sci. 2021, 2, 107. [Google Scholar] [CrossRef]
- Waqas, M.; Tu, S.; Halim, Z.; Rehman, S.U.; Abbas, G.; Abbas, Z. The Role of Artificial Intelligence and Machine Learning in Wireless Networks Security: Principle, Practice and Challenges. Artif. Intell. Rev. 2022, 55, 5215–5261. [Google Scholar] [CrossRef]
- Wu, Z.; Zhang, L.; Yue, M. Low-Rate DoS Attacks Detection Based on Network Multifractal. IEEE Trans. Dependable Secur. Comput. 2016, 13, 559–567. [Google Scholar] [CrossRef]
- Agrawal, N.; Tapaswi, S. Low rate cloud DDoS attack defense method based on power spectral density analysis. Inf. Process. Lett. 2018, 138, 44–50. [Google Scholar] [CrossRef]
- Marnerides, A.K.; Pezaros, D.P.; Kim, H.C.; Hutchison, D. Internet traffic classification using energy time-frequency distributions. In Proceedings of the 2013 IEEE International Conference on Communications (ICC), Budapest, Hungary, 9–13 June 2013; pp. 2513–2518. [Google Scholar]
- Yazdani, A.; Salimi, M.; Roshan-Miavagi, A. Wavelet-Hilbert transform-based simulation of pulse-like ground motion. J. Seismol. 2022, 26, 949–965. [Google Scholar] [CrossRef]
- Chen, H.; Liu, M.; Zhongchuan, F. Using Improved Hilbert–Huang Transformation Method to Detect Routing-Layer Reduce of Quality Attack in Wireless Sensor Network. Wirel. Pers. Commun. 2018, 104, 595–615. [Google Scholar] [CrossRef]
- Tang, D.; Tang, L.; Shi, W.; Zhan, S.; Yang, Q. MF-CNN: A New Approach for LDoS Attack Detection Based on Multi-feature Fusion and CNN. Mob. Netw. Appl. 2020, 26, 1705–1722. [Google Scholar] [CrossRef]
- Tang, D.; Man, J.; Tang, L.; Feng, Y.; Yang, Q. WEDMS: An advanced mean shift clustering algorithm for LDoS attacks detection. Ad Hoc Netw. 2020, 102, 102145. [Google Scholar] [CrossRef]
- Yue, M.; Liu, L.; Wu, Z.; Wang, M. Identifying LDoS attack traffic based on wavelet energy spectrum and combined neural network. Int. J. Commun. Syst. 2018, 31, e3449. [Google Scholar] [CrossRef]
- Wu, H.; Chen, T.; Shao, Z.; Cheng, G.; Hu, X. Accurate and Fast Detection of DDoS Attacks in High-Speed Network with Asymmetric Routing. In Proceedings of the 2021 IEEE Global Communications Conference (GLOBECOM), Madrid, Spain, 7–11 December 2021; pp. 1–6. [Google Scholar]
- Kuzmanovic, A.; Knightly, E.W. Low-rate TCP-targeted denial of service attacks: The shrew vs. the mice and elephants. In Proceedings of the 2003 Conference on Applications, Technologies, Architectures, and Protocols for Computer Communications, Karlsruhe, Germany, 25–29 August 2003; pp. 75–86. [Google Scholar]
- Yan, Y.; Tang, D.; Zhan, S.; Dai, R.; Chen, J.; Zhu, N. Low-Rate DoS Attack Detection Based on Improved Logistic Regression. In Proceedings of the 2019 IEEE 21st International Conference on High Performance Computing and Communications; IEEE 17th International Conference on Smart City; IEEE 5th International Conference on Data Science and Systems (HPCC/SmartCity/DSS), Zhangjiajie, China, 10–12 August 2019; pp. 468–476. [Google Scholar]
- Liu, L.; Wang, H.; Wu, Z.; Yue, M. The detection method of low-rate DoS attack based on multi-feature fusion. Digit. Commun. Netw. 2020, 6, 504–513. [Google Scholar] [CrossRef]
- Zhang, D.; Tang, D.; Tang, L.; Dai, R.; Chen, J.; Zhu, N. PCA-SVM-Based Approach of Detecting Low-Rate DoS Attack. In Proceedings of the 2019 IEEE 21st International Conference on High Performance Computing and Communications; IEEE 17th International Conference on Smart City; IEEE 5th International Conference on Data Science and Systems (HPCC/SmartCity/DSS), Zhangjiajie, China, 10–12 August 2019; pp. 1163–1170. [Google Scholar]
- Liu, L.; Yin, Y.; Wu, Z.; Pan, Q.; Yue, M. LDoS attack detection method based on traffic classification prediction. IET Inf. Secur. 2022, 16, 86–96. [Google Scholar] [CrossRef]
- Fouladi, R.F.; Ermiş, O.; Anarim, E. A Novel Approach for distributed denial of service defense using continuous wavelet transform and convolutional neural network for software-defined network. Comput. Secur. 2022, 112, 102524. [Google Scholar] [CrossRef]
- Gasca, M.V.; Bueno-Lopez, M.; Molinas, M.; Fosso, O.B. Time-Frequency analysis for nonlinear and non-stationary signals using HHT: A mode mixing separation technique. IEEE Lat. Am. Trans. 2018, 16, 1091–1098. [Google Scholar] [CrossRef]
- Junsheng, C.; Dejie, Y.; Yu, Y. Research on the intrinsic mode function (IMF) criterion in EMD method. Mech. Syst. Signal Process. 2006, 20, 817–824. [Google Scholar] [CrossRef]
- Wu, Z.J.; Zhang, J.A.; Yue, M.; Zhang, C.F. Approach of detecting low-rate DoS attack based on combined features. J. Commun. 2017, 38, 19–30. [Google Scholar]
- Tang, D.; Tang, L.; Dai, R.; Chen, J.; Li, X.; Rodrigues, J.J. MF-Adaboost: LDoS attack detection based on multi-features and improved Adaboost. Future Gener. Comput. Syst. 2020, 106, 347–359. [Google Scholar] [CrossRef]


| Category | Proposal | Detection Method | Limitations |
|---|---|---|---|
| Detection methods based on features | Yan et al. (2019) | Enhanced logistic regression [22] | The feature extraction method was relatively weak. |
| Liu et al. (2020) | KNN [23] | This method was sensitive to noise data and could be easily affected by outliers. | |
| Zhang et al. (2019) | PCA-SVM [24] | This approach demonstrated limited efficacy in detecting complex attack behaviors. | |
| Tang et al. (2020) | Multi-feature fusion [17] | They required intricate computations and extensive model training. | |
| WEDMS [18] | |||
| Detection methods based on time–frequency domain | Agrawal et al. (2018) | FT [13] | FT could not effectively process non-periodic signals or signals with time constraints. |
| Yue et al. (2018) | WT [19] | WT could not achieve high time and frequency precision simultaneously, and WT required the selection of an appropriate wavelet basis function. | |
| Fouladi et al. (2022) | CWT [26] |
| Notation | Description |
|---|---|
| Q | Feature set |
| t | Sampling time interval |
| Feature Value | |
| D | Euclidean distance |
| M | Euclidean distance threshold |
| X | Feature |
| w | Sliding window size |
| The feature sequence after sliding window | |
| P | The total number of packets |
| C | Total network connections |
| Local maximum points | |
| Local minimum points | |
| The mean value between and | |
| IMF component | |
| Residual signal | |
| The Hilbert spectra of IMF components | |
| Amplitude | |
| Instantaneous frequency | |
| Spectrogram after compressed HHT of Q | |
| Training rounds | |
| Training data set | |
| Testing data set |
| Parameter | Value |
|---|---|
| Frequency | 100 HZ |
| Spectral resolution | 64 × 64 |
| Packets per second | 200 |
| Euclidean distance threshold M | 1 |
| Sliding window size w | 100 |
| Method | |||
|---|---|---|---|
| Multifractal | 9% | 10% | 91% |
| BP neural network | 3.32% | 3.89% | 96.68% |
| PSD | 4.9% | 3.7% | 95.1% |
| MF-Adaboost | 2.94% | 0.33% | 97.06% |
| HCN | 0.2% | 0.4% | 99.8% |
Disclaimer/Publisher’s Note: The statements, opinions and data contained in all publications are solely those of the individual author(s) and contributor(s) and not of MDPI and/or the editor(s). MDPI and/or the editor(s) disclaim responsibility for any injury to people or property resulting from any ideas, methods, instructions or products referred to in the content. |
© 2023 by the authors. Licensee MDPI, Basel, Switzerland. This article is an open access article distributed under the terms and conditions of the Creative Commons Attribution (CC BY) license (https://creativecommons.org/licenses/by/4.0/).
Share and Cite
Liu, Y.; Sun, D.; Zhang, R.; Li, W. A Method for Detecting LDoS Attacks in SDWSN Based on Compressed Hilbert–Huang Transform and Convolutional Neural Networks. Sensors 2023, 23, 4745. https://doi.org/10.3390/s23104745
Liu Y, Sun D, Zhang R, Li W. A Method for Detecting LDoS Attacks in SDWSN Based on Compressed Hilbert–Huang Transform and Convolutional Neural Networks. Sensors. 2023; 23(10):4745. https://doi.org/10.3390/s23104745
Chicago/Turabian StyleLiu, Yazhi, Ding Sun, Rundong Zhang, and Wei Li. 2023. "A Method for Detecting LDoS Attacks in SDWSN Based on Compressed Hilbert–Huang Transform and Convolutional Neural Networks" Sensors 23, no. 10: 4745. https://doi.org/10.3390/s23104745
APA StyleLiu, Y., Sun, D., Zhang, R., & Li, W. (2023). A Method for Detecting LDoS Attacks in SDWSN Based on Compressed Hilbert–Huang Transform and Convolutional Neural Networks. Sensors, 23(10), 4745. https://doi.org/10.3390/s23104745







