Direct Spread Spectrum Technology for Data Hiding in Audio †
Abstract
:1. Introduction
- Code division multiple access communication systems (IS-95, CDMA2000, WCDMA, DS-CDMA, TD-CDMA, TD-SCDMA, etc.);
- Global satellite navigation systems (American GPS, European Galileo, and Russian GLONASS);
- Family of wireless network protocols Wi-Fi (family of standards IEEE 802.11), and much more.
2. Related Works
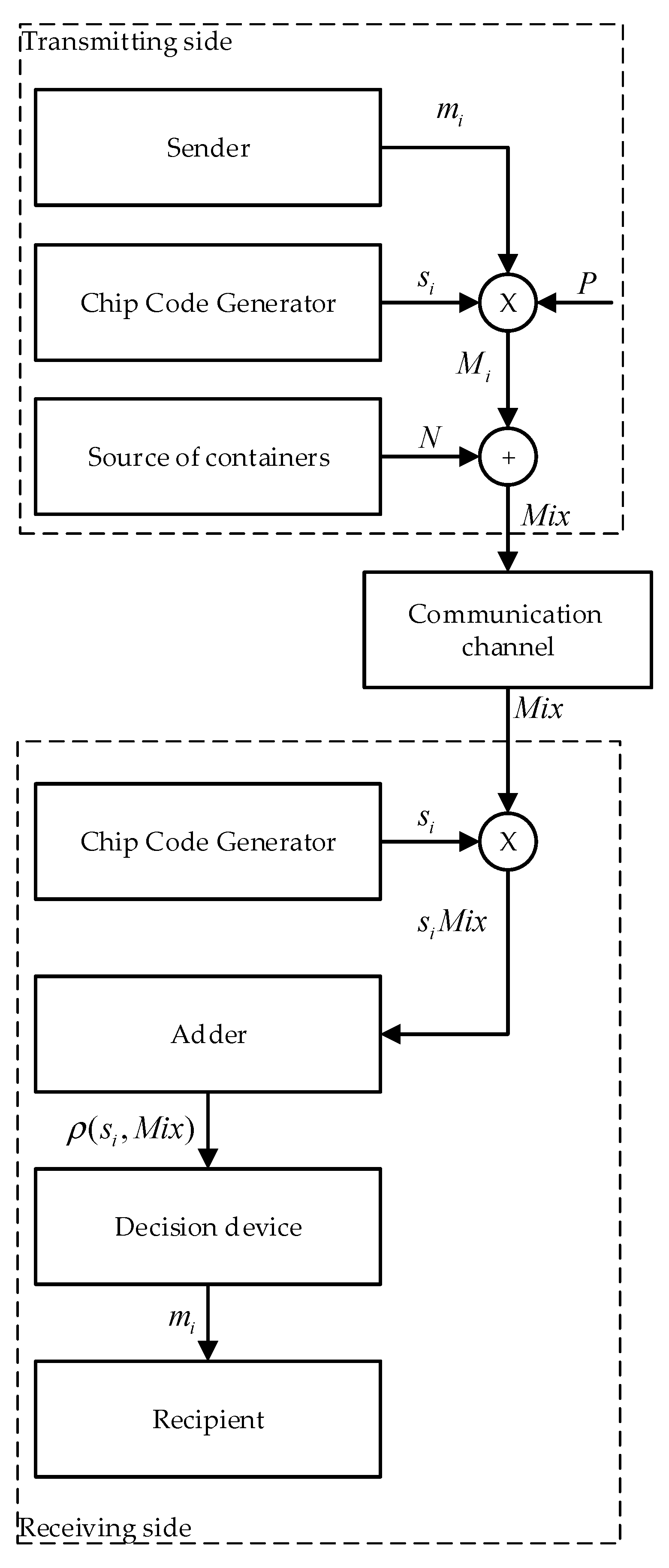
3. Materials and Methods
3.1. Direct Spread Spectrum Technology in Telecommunications
- —channel throughput, bit/s;
- —frequency band, Hz;
- —desired signal power;
- —additive white Gaussian noise power;
- —signal power to noise ratio (SNR).
- Resistance to unintended or intended jamming;
- Sharing a single channel among multiple users;
- Reduced signal/background-noise level hampers interception;
- Determination of relative timing between transmitter and receiver and much more.
3.2. Direct Spread Spectrum in Steganography
- Step 1
- The information message is presented in polar form ;
- Step 2
- multiplied bit by bit by the spreading sequence as in (3);
- Step 3
- Multimedia data (images, audio, video, etc.) are interpreted as noise in the communication channel. Using our notation, this is in (4).
- Step 4
- Further, these data are hidden in the cover data according to rule (4). However, we currently denote:
- —multimedia data (container, cover), inside which the message is hidden;
- —modified multimedia data (filled container) after hiding messages in them.
- Step 1
- Correlation is calculated.
- -
- The product is calculated ;
- -
- The sum is calculated ;
- Step 2
- If Equations (6) and (7) are true, then the value of the recovered bit is calculated by the Equation (8).
- Step 3
- The recovered message is presented in a custom view.
3.3. Initial Data for Hiding Messages
- the number of channels (streams) of audio data . We used stereo signals, i.e.,;
- sampling frequency . Our audio signals from ;
- the number of bits allocated to encode each discrete sample of the audio signal. We used covers from bit.
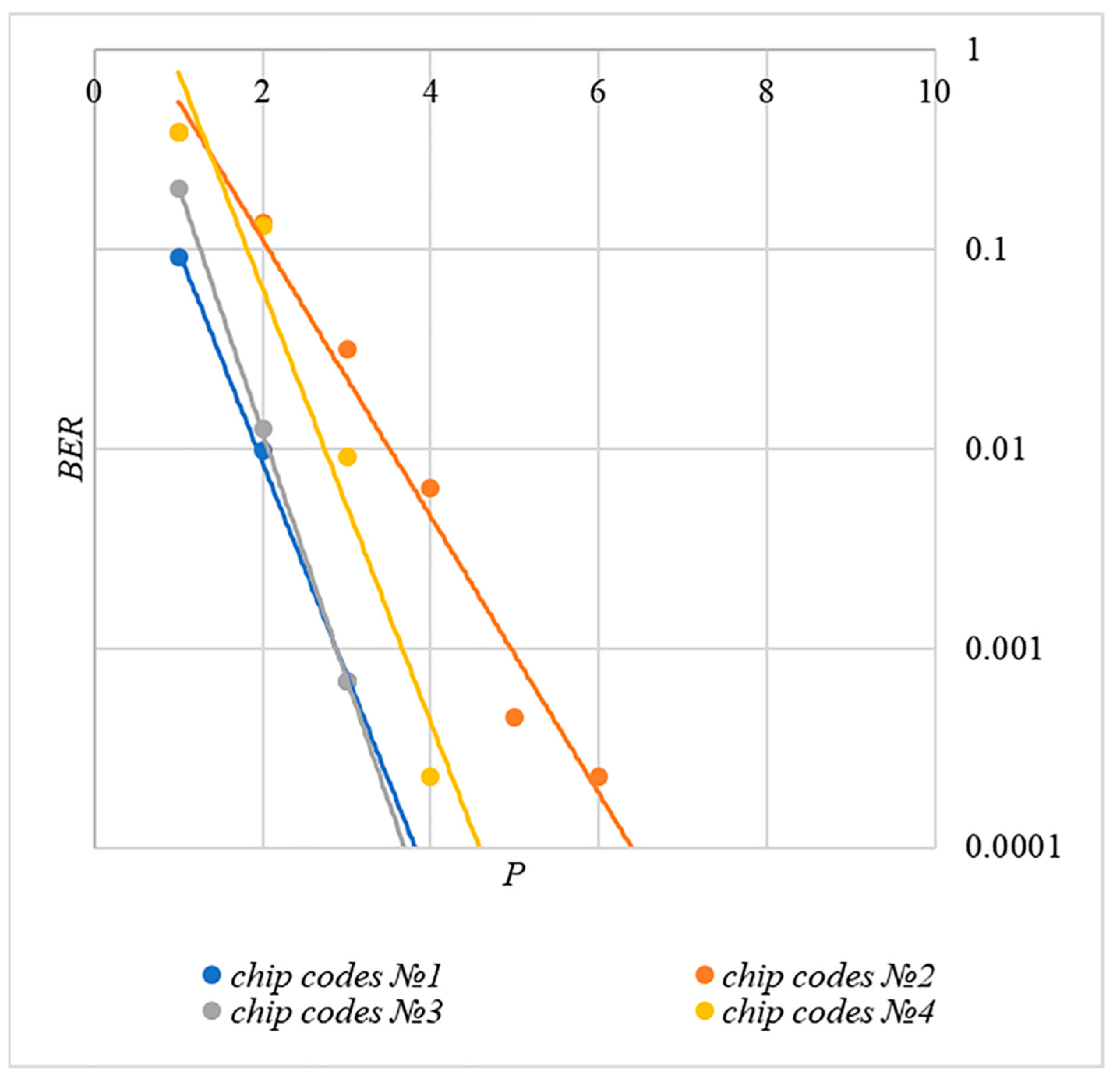
3.4. Used Chip Codes
- —implementation of a random variable uniformly distributed over the interval ;
- —inverse cumulative distribution function for a standard Gaussian random variable.
- 2.
- Chip codes from random numbers uniformly distributed over the interval [−1, 1]
- 3.
- Chip codes from normally distributed random numbers
- 4.
- Binary chip codes generated by a pseudo-random bit generator
- 5.
- Walsh–Hadamard spreading sequences
3.5. Indicators of Effectiveness of Hiding Messages
- Bit Error Rate, BER
- 2.
- Mean squared error, MSE
- 3.
- Peak signal-to-noise ratio, PSNR
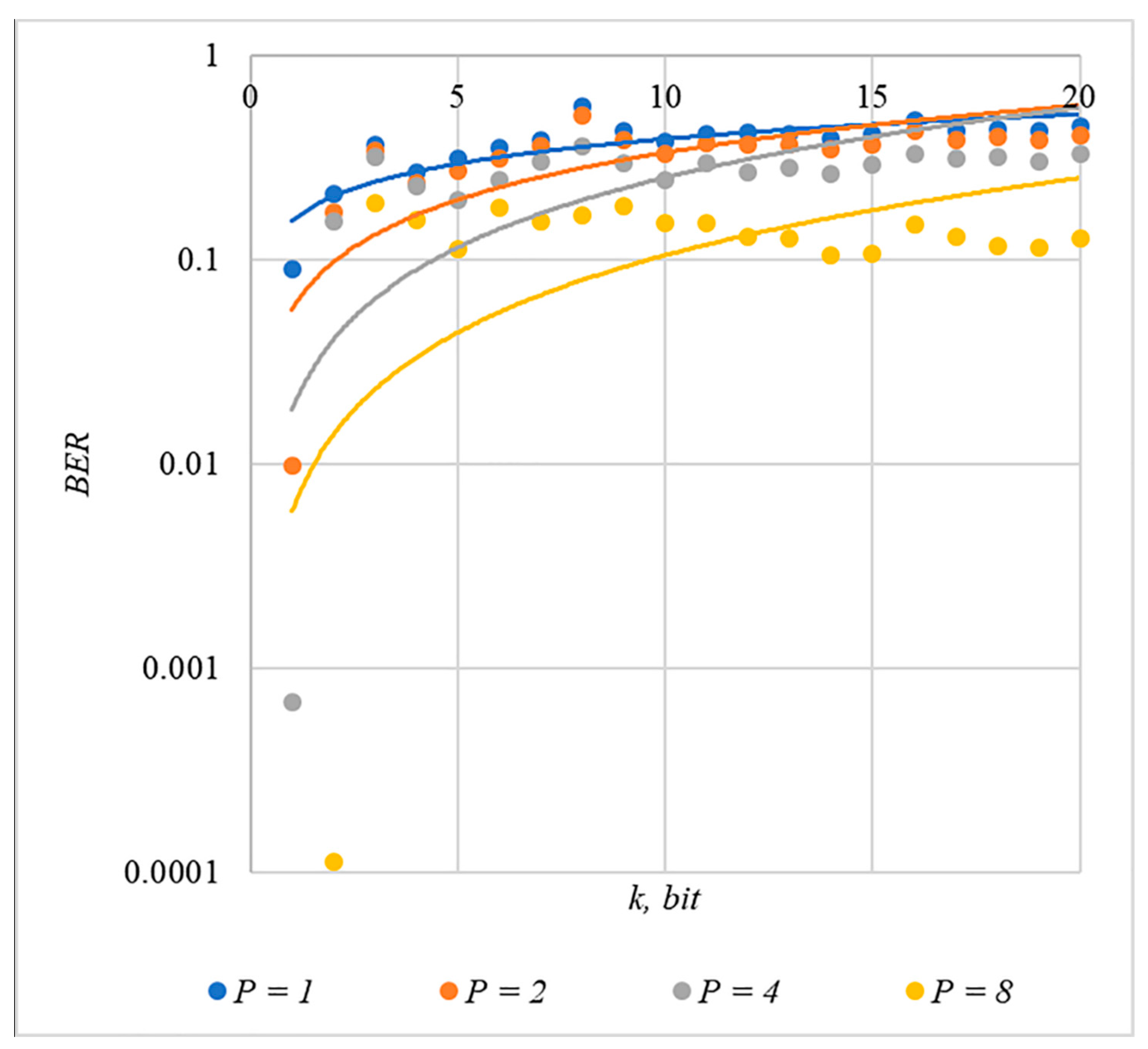
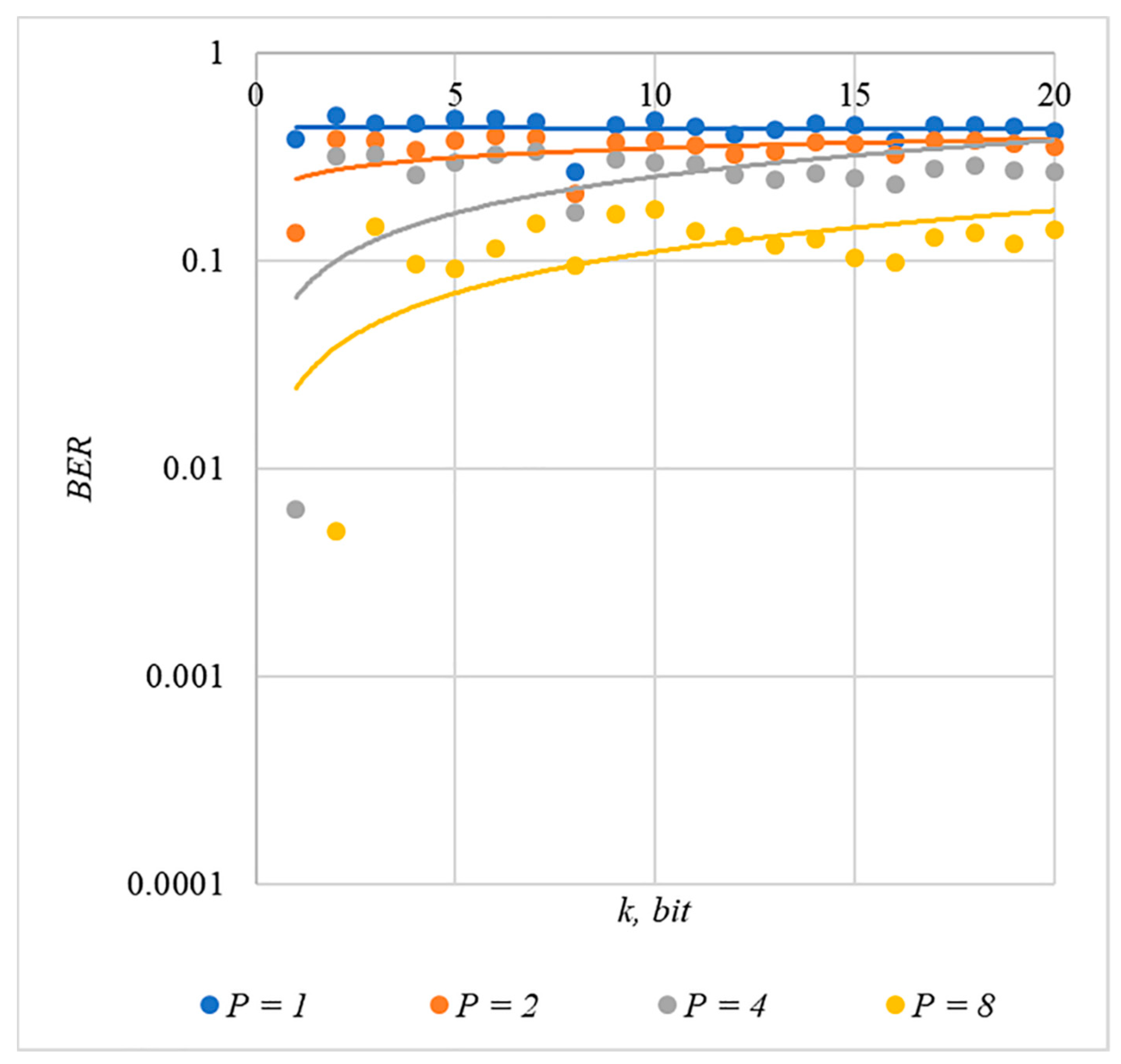
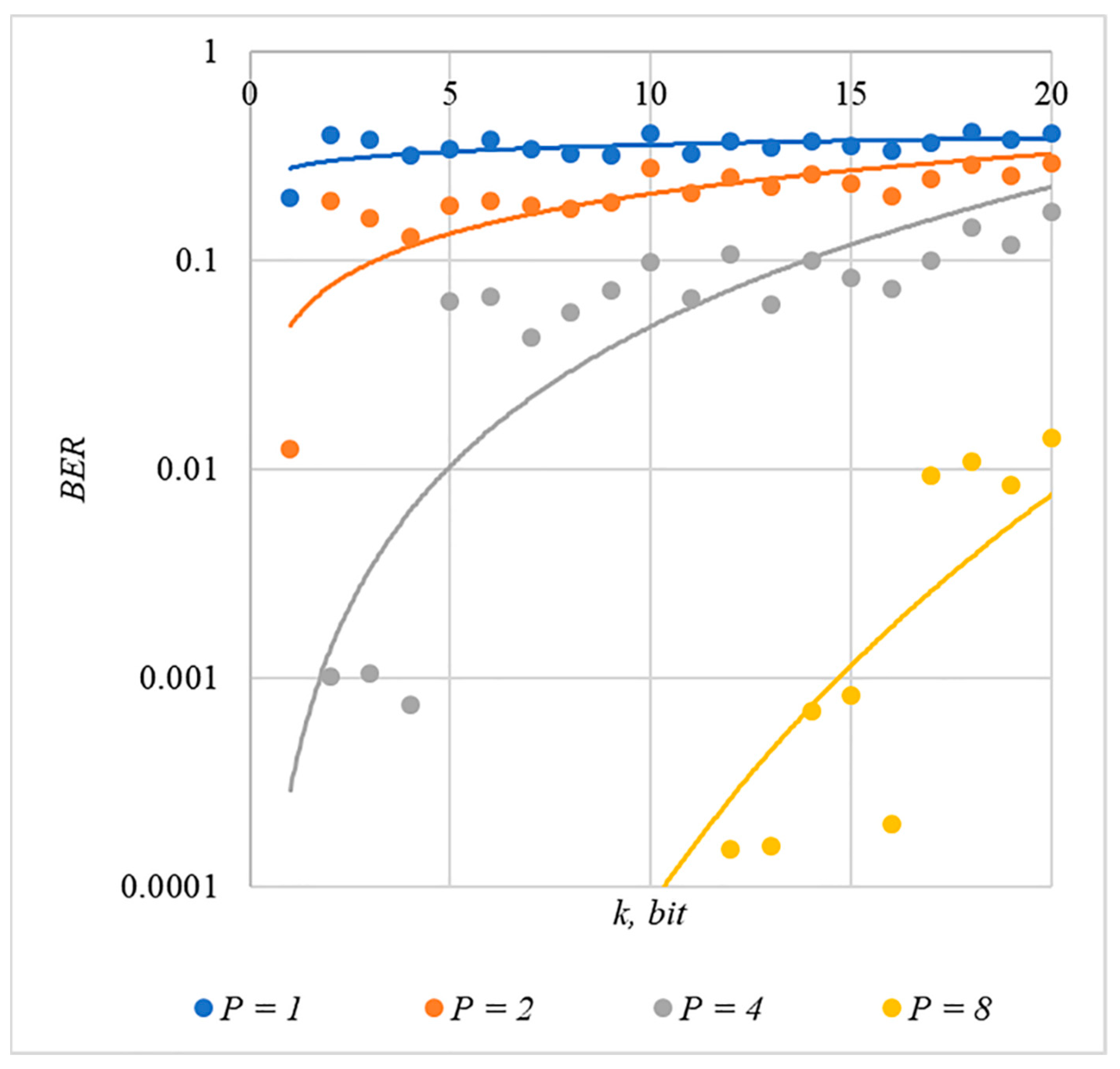
4. Results
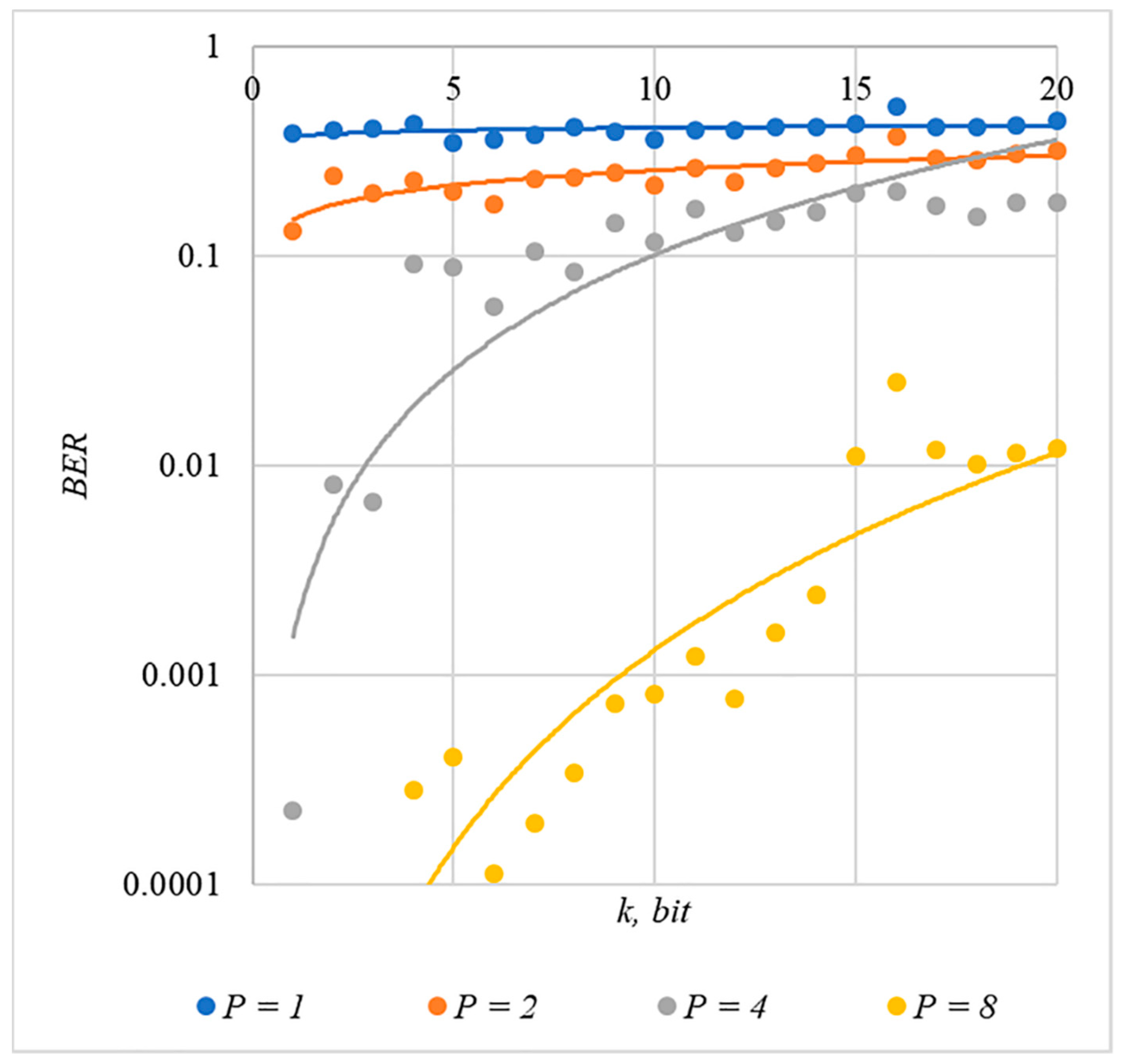
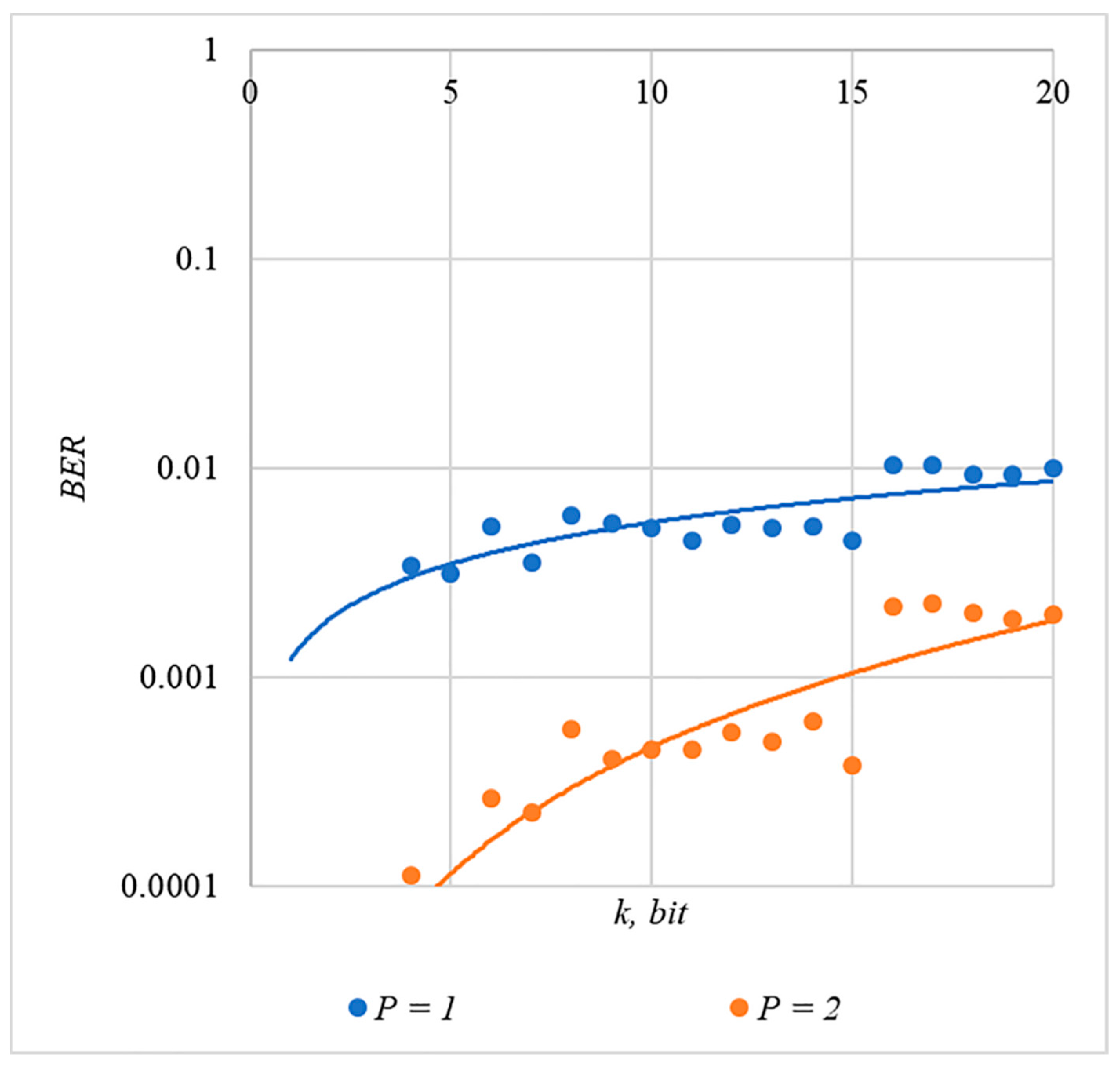
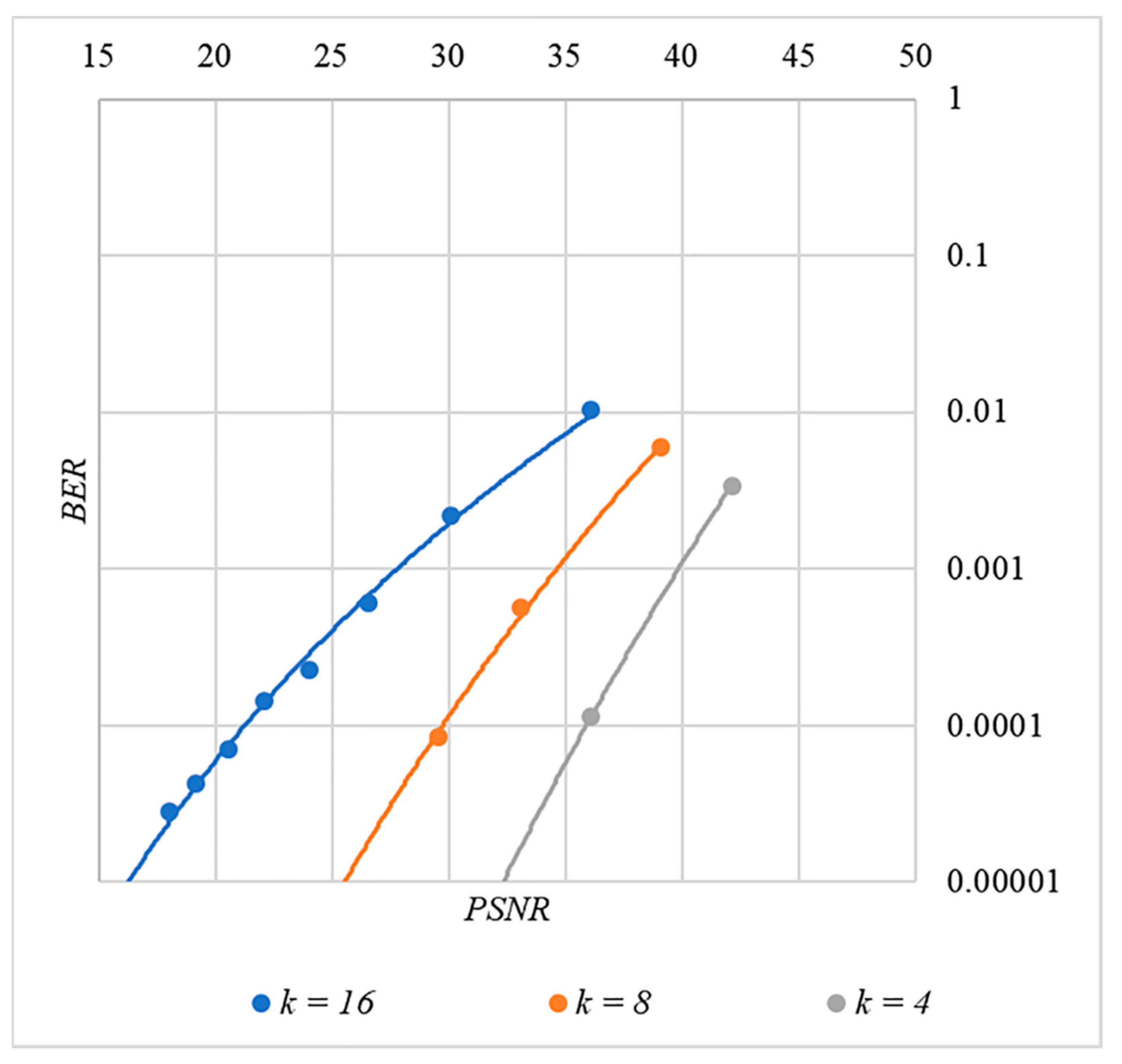
4.1. Experimental Evaluation of Hidden Message Distortion
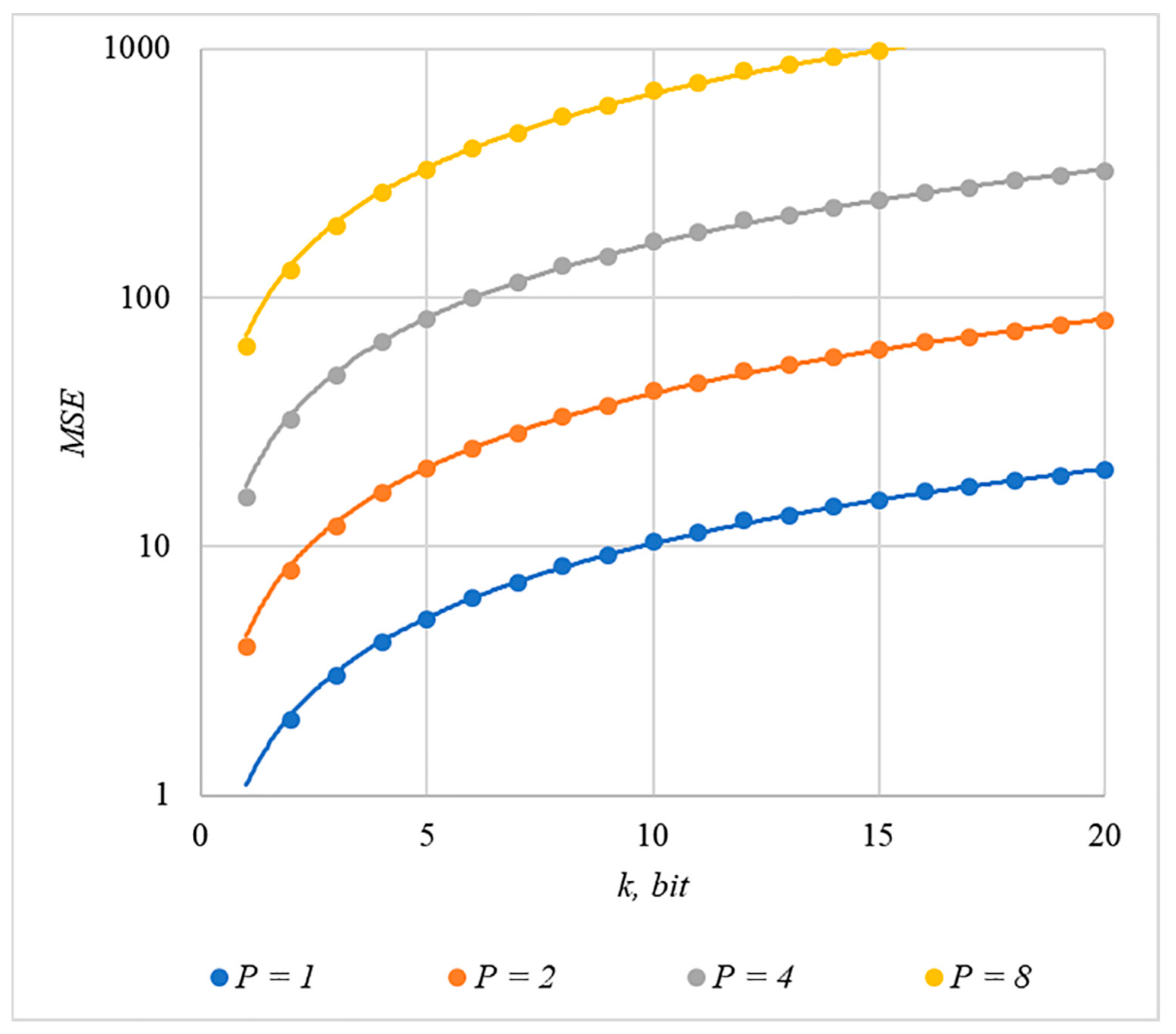
4.2. Experimental Evaluation of Container Distortion
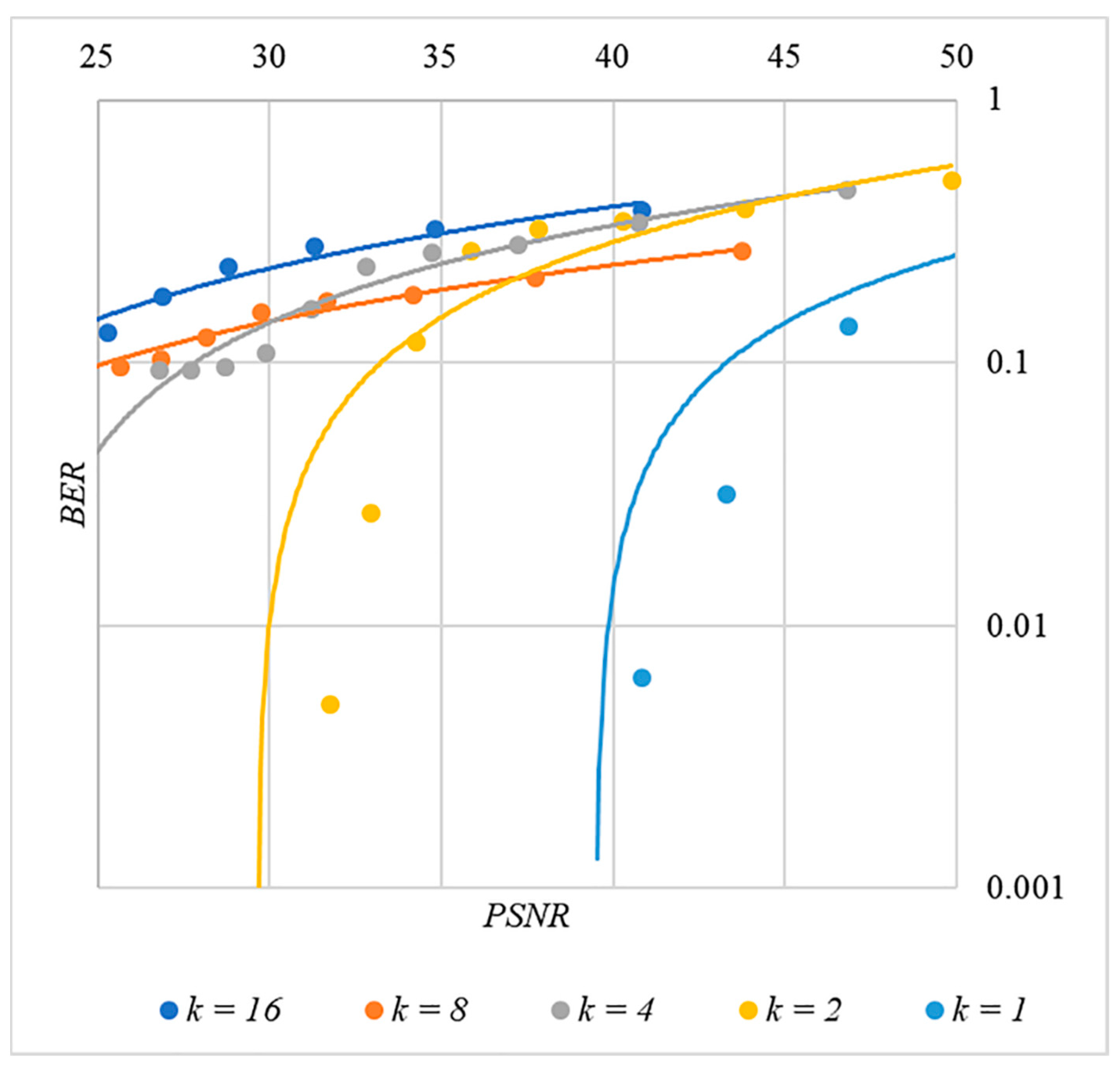
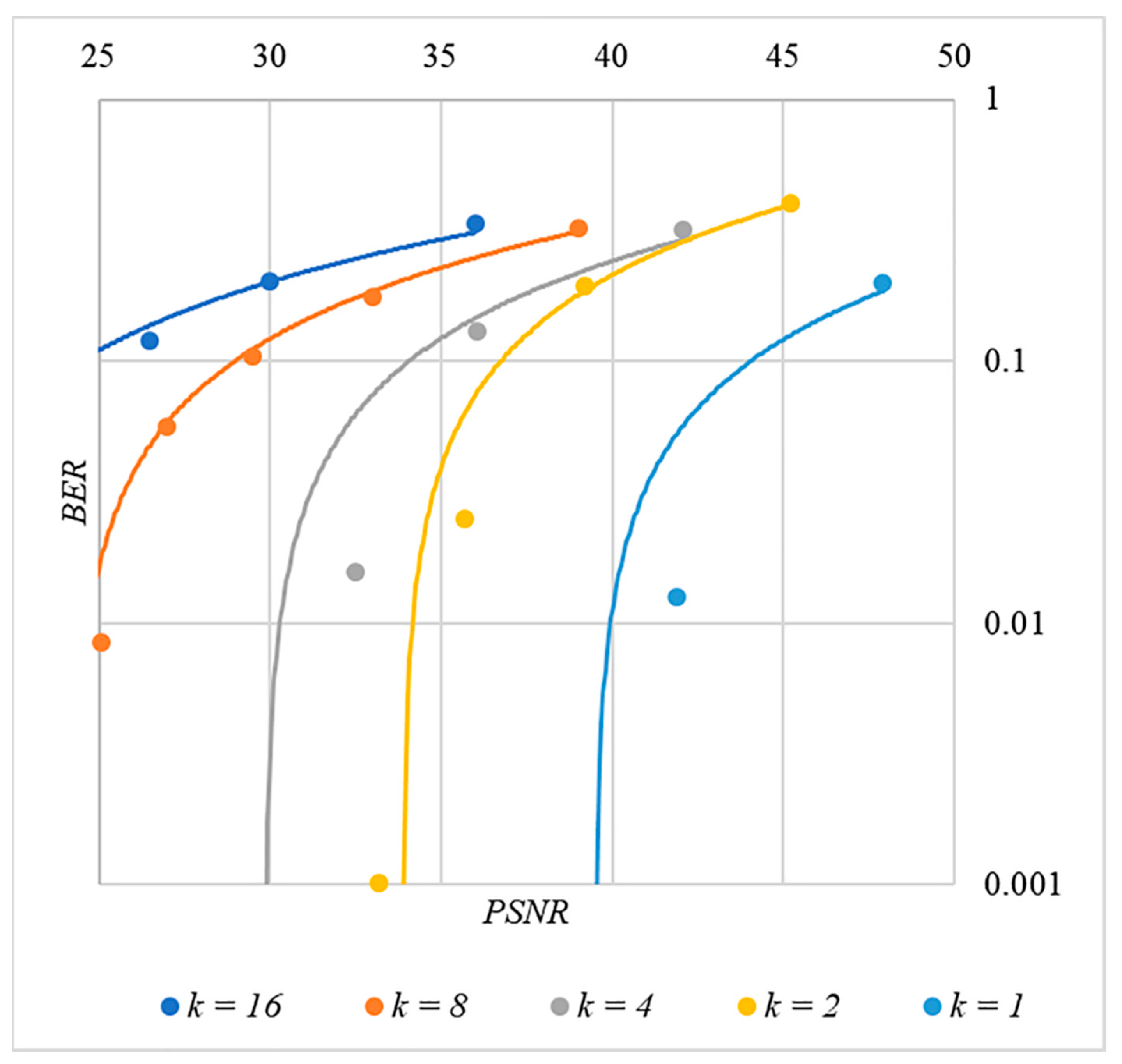
4.3. Correlation of Error Rate and Container Distortion, Finding a Compromise
5. Discussion
6. Conclusions
Author Contributions
Funding
Institutional Review Board Statement
Informed Consent Statement
Data Availability Statement
Conflicts of Interest
References
- Li, R.; Xu, S.; Rong, B.; Yang, H. Host Cancelation-Based Spread Spectrum Watermarking for Audio Anti-Piracy over Internet. Secur. Commun. Netw. 2016, 9, 4691–4702. [Google Scholar] [CrossRef]
- Manoj, I.V.S. Cryptography and Steganography. Int. J. Comput. Appl. 2010, 1, 63–68. [Google Scholar] [CrossRef]
- Moulin, P.; O’Sullivan, J.A. Information-Theoretic Analysis of Information Hiding. IEEE Trans. Inf. Theory 2003, 49, 563–593. [Google Scholar] [CrossRef]
- Aroua, S.; Champagnat, R.; Coustaty, M.; Falquet, G.; Ghadfi, S.; Ghamri-Doudane, Y.; Gomez-Kramer, P.; Howells, G.; McDonald-Maier, K.D.; Murphy, J.; et al. Security and PrIvacy foR the Internet of Things: An Overview of the Project. In Proceedings of the 2019 IEEE International Conference on Systems, Man and Cybernetics (SMC), Bari, Italy, 6–9 October 2019; pp. 3993–3998. [Google Scholar]
- Fazzat, A.; Khatoun, R.; Labiod, H.; Dubois, R. A Comparative Performance Study of Cryptographic Algorithms for Connected Vehicles. In Proceedings of the 2020 4th Cyber Security in Networking Conference (CSNet), Lausanne, Switzerland, 21–23 October 2020; pp. 1–8. [Google Scholar]
- Levi, I.; Rudin, Y.; Fish, A.; Keren, O. Embedded Randomness and Data Dependencies Design Paradigm: Advantages and Challenges. In Proceedings of the 2018 Design, Automation Test in Europe Conference Exhibition (DATE), Dresden, Germany, 19–23 March 2018; pp. 395–400. [Google Scholar]
- Menezes, A.J.; van Oorschot, P.C.; Vanstone, S.A.; van Oorschot, P.C.; Vanstone, S.A. Handbook of Applied Cryptography; CRC Press: Boca Raton, FA, USA, 2018; ISBN 978-0-429-46633-5. [Google Scholar]
- Yahya, A. Steganography Techniques. In Steganography Techniques for Digital Images; Yahya, A., Ed.; Springer International Publishing: Cham, Switzerland, 2019; pp. 9–42. ISBN 978-3-319-78597-4. [Google Scholar]
- Fridrich, J. Steganography in Digital Media: Principles, Algorithms, and Applications; Illustrated Edition; Cambridge University Press: Cambridge, MA, USA; New York, NY, USA, 2009; ISBN 978-0-521-19019-0. [Google Scholar]
- WAV File Extension-What Is It? How to Open a WAV File? Available online: https://filext.com/file-extension/WAV (accessed on 25 April 2021).
- Fleischman, E. WAVE and AVI Codec Registries. Available online: https://tools.ietf.org/html/rfc2361 (accessed on 25 April 2021).
- Song, T.; Zhou, K.; Li, T. CDMA System Design and Capacity Analysis Under Disguised Jamming. IEEE Trans. Inf. Forensics Secur. 2016, 11, 2487–2498. [Google Scholar] [CrossRef]
- Wang, X.; Liu, X.; Chen, H.-H.; Meng, W. Complementary Coded CDMA Systems With CP-Free OFDM. IEEE Trans. Veh. Technol. 2020, 69, 11515–11528. [Google Scholar] [CrossRef]
- Sedaghat, M.A.; Müller, R.R.; Marvasti, F. On Optimum Asymptotic Multiuser Efficiency of Randomly Spread CDMA. IEEE Trans. Inf. Theory 2015, 61, 6635–6642. [Google Scholar] [CrossRef] [Green Version]
- Khalife, J.; Kassas, Z.M. Navigation with Cellular CDMA Signals—Part II: Performance Analysis and Experimental Results. IEEE Trans. Signal Process. 2018, 66, 2204–2218. [Google Scholar] [CrossRef]
- Stüber, G.L. Spread Spectrum Techniques. In Principles of Mobile Communication; Stüber, G.L., Ed.; Springer International Publishing: Cham, Switzerland, 2017; pp. 449–499. ISBN 978-3-319-55615-4. [Google Scholar]
- Torrieri, D. Chapter 2 Direct-Sequence Systems. In Principles of Spread-Spectrum Communication Systems; Torrieri, D., Ed.; Springer International Publishing: Cham, Switzerland, 2015; pp. 79–145. ISBN 978-3-319-14096-4. [Google Scholar]
- Ipatov, V.P. Spread Spectrum and CDMA: Principles and Applications; John Wiley & Sons, Ltd.: Chichester, UK, 2005; ISBN 978-0-470-09180-7. [Google Scholar]
- Torrieri, D. Principles of Spread-Spectrum Communication Systems; Springer International Publishing: Cham, Switzerland, 2018. [Google Scholar]
- Smith, J.R.; Comiskey, B.O. Modulation and Information Hiding in Images. In International Workshop on Information Hiding; Anderson, R., Ed.; Springer: Berlin/Heidelberg, Germany, 1996; pp. 207–226. [Google Scholar]
- Marvel, L.M.; Boncelet, C.G.; Retter, C.T. Methodology of Spread-Spectrum Image Steganography; Army Research Lab Aberdeen Proving: Ground, MD, USA, 1998. [Google Scholar]
- Wang, Y.-G.; Zhu, G.; Kwong, S.; Shi, Y.-Q. A Study on the Security Levels of Spread-Spectrum Embedding Schemes in the WOA Framework. IEEE Trans. Cybern. 2018, 48, 2307–2320. [Google Scholar] [CrossRef] [PubMed]
- Kuznetsov, A.; Smirnov, O.; Arischenko, A.; Chepurko, I.; Onikiychuk, A.; Kuznetsova, T. Pseudorandom Sequences for Spread Spectrum Image Steganography. In Proceedings of the International Workshop on Cyber Hygiene (CybHyg-2019) Co-Located with 1st International Conference on Cyber Hygiene and Conflict Management in Global Information Networks (CyberConf 2019), Kyiv, Ukraine, 30 November 2019; CEUR-WS.org: Tilburg, The Netherlands, 2020; Volume 2654, pp. 122–131. [Google Scholar]
- Kuznetsov, A.; Smirnov, A.; Gorbacheva, L.; Babenko, V. Hiding Data in Cover Images Using a Pseudo-Random Sequences. In Proceedings of the Proceedings of The Third International Workshop on Computer Modeling and Intelligent Systems (CMIS-2020), Zaporizhzhia, Ukraine, 27 April–1 May 2020; Subbotin, S., Ed.; CEUR-WS.org: Tilburg, The Netherlands, 2020; Volume 2608, pp. 646–660. [Google Scholar]
- Avci, D.; Tuncer, T.; Avci, E. A New Information Hiding Method for Audio Signals. In Proceedings of the 2018 6th International Symposium on Digital Forensic and Security (ISDFS), Antalya, Turkey, 22–25 March 2018; pp. 1–4. [Google Scholar]
- Rajput, S.P.; Adhiya, K.P.; Patnaik, G.K. An Efficient Audio Steganography Technique to Hide Text in Audio. In Proceedings of the 2017 International Conference on Computing, Communication, Control and Automation (ICCUBEA), Pune, India, 17–18 August 2017; pp. 1–6. [Google Scholar]
- Nassrullah, H.A.; Flayyih, W.N.; Nasrullah, M.A. Enhancement of LSB Audio Steganography Based on Carrier and Message Characteristics. J. Inf. Hiding Multimed. Signal Process. 2020, 11, 126–137. [Google Scholar]
- Ramya, G.; Janarthanan, P.P.; Mohanapriya, D. Steganography Based Data Hiding for Security Applications. In Proceedings of the 2018 International Conference on Intelligent Computing and Communication for Smart World (I2C2SW), Erode, India, 14–15 December 2018; pp. 131–135. [Google Scholar]
- Lee, M.C.; Lau, C.Y. Three Orders Mixture Algorithm of Audio Steganography Combining Cryptography. J. Inf. Hiding Multimed. Signal Process. 2018, 9, 959–969. [Google Scholar]
- Akbay, K.; Konyar, M.Z.; İlkın, S.; Sondaş, A. Data Hiding Using Shuffle Algorithm and LSB Method. In Proceedings of the 2018 26th Signal Processing and Communications Applications Conference (SIU), Izmir, Turkey, 2–5 May 2018; pp. 1–4. [Google Scholar]
- Gopalan, K. Audio Steganography for Information Hiding and Covert Communication–a Tutorial. In Proceedings of the 2018 IEEE International Conference on Electro/Information Technology (EIT), Rochester, MI, USA, 3–5 May 2018; pp. 0242–0243. [Google Scholar]
- Unoki, M.; Imabeppu, K.; Hamada, D.; Haniu, A.; Miyauchi, R. Embedding Limitations with Digital-Audio Watermarking Method Based on Cochlear Delay Characteristics. J. Inf. Hiding Multimed. Signal Process. 2011, 2, 1–23. [Google Scholar]
- Altinbaş, A.E.; Yalman, Y. Bit Reduction Based Audio Steganography Algorithm. In Proceedings of the 2021 6th International Conference on Computer Science and Engineering (UBMK), Ankara, Turkey, 15–17 September 2021; pp. 703–706. [Google Scholar]
- Tabara, B.; Wojtuń, J.; Piotrowski, Z. Data Hiding Method in Speech Using Echo Embedding and Voicing Correction. In Proceedings of the 2017 Signal Processing Symposium (SPSympo), Debe, Poland, 12–14 September 2017; pp. 1–6. [Google Scholar]
- Wang, S.; Yuan, W.; Unoki, M. Multi-Subspace Echo Hiding Based on Time-Frequency Similarities of Audio Signals. IEEE/ACM Trans. Audio Speech Lang. Process. 2020, 28, 2349–2363. [Google Scholar] [CrossRef]
- Latypov, R.K.; Stolov, E.L. Ternary Echo Hiding in Audio Files. In Proceedings of the 2020 28th Telecommunications Forum (℡FOR), Belgrade, Serbia, 24–25 November 2020; pp. 1–4. [Google Scholar]
- Cho, K.; Bae, S.H.; Choi, I.K.; Kim, N.S.; Unoki, M. Robust Audio Data Hiding Method Based on Phase of Modulated Complex Lapped Transform. In Proceedings of the 2013 Ninth International Conference on Intelligent Information Hiding and Multimedia Signal Processing, Beijing, China, 16–18 October 2013; pp. 263–266. [Google Scholar]
- Manunggal, T.T.; Arifianto, D. Data Protection Using Interaural Quantified-Phase Steganography on Stereo Audio Signals. In Proceedings of the 2016 IEEE Region 10 Conference (TENCON), Singapore, 22–25 November 2016; pp. 3817–3821. [Google Scholar]
- Ginanjar, R.R.; Bhardwaj, S.; Kim, D.-S.; Lee, J.-M. Rounding Modulation for Transparent Data-Hiding Scheme in High-Quality Audio File. In Proceedings of the 2019 IEEE International Conference on Consumer Electronics (ICCE), Las Vegas, NV, USA, 11–13 January 2019; pp. 1–2. [Google Scholar]
- Marvel, L.M.; Boncelet, C.G.; Retter, C.T. Spread Spectrum Image Steganography. IEEE Trans. Image Process. 1999, 8, 1075–1083. [Google Scholar] [CrossRef] [PubMed] [Green Version]
- Marvel, L.M. Image Steganography for Hidden Communication; Army Research Lab Aberdeen Proving: Ground, MD, USA, 2000. [Google Scholar]
- Youail, R.S.; Samawi, V.W.; Kadhim, A.-K.A.-R. Combining a Spread Spectrum Technique with Error-Correction Code to Design an Immune Stegosystem. In Proceedings of the Security and Identification 2008 2nd International Conference on Anti-counterfeiting, Guiyang, China, 20–23 August 2008; pp. 245–248. [Google Scholar]
- Agrawal, N.; Gupta, A. DCT Domain Message Embedding in Spread-Spectrum Steganography System. In Proceedings of the 2009 Data Compression Conference, Washington, DC, USA, 16–18 March 2009; p. 433. [Google Scholar]
- Lu, L.; Sun, X.; Cai, L. A Robust Image Watermarking Based on DCT by Arnold Transform and Spread Spectrum. In Proceedings of the 2010 3rd International Conference on Advanced Computer Theory and Engineering (ICACTE), Chengdu, China, 20–22 August 2010; Volume 1, pp. V1-198–V1-201. [Google Scholar]
- Satish, K.; Jayakar, T.; Tobin, C.; Madhavi, K.; Murali, K. Chaos Based Spread Spectrum Image Steganography. IEEE Trans. Consum. Electron. 2004, 50, 587–590. [Google Scholar] [CrossRef]
- Kumar, A.; Albagul, A.; Ghose, M.; Negrat, K. Improved Chaos Based Spread Spectrum Image Steganography. In Proceedings of the 10th IASTED International Conference, Beijing China, 8–10 October 2008; pp. 18–20. [Google Scholar]
- Weihua, X.; Yongbing, W.; Shuiyuan, Y.H. 264 Video Watermark Algorithm Using DCT Spread Spectrum. In Proceedings of the 2015 3rd International Conference on Applied Computing and Information Technology/2nd International Conference on Computational Science and Intelligence, Okayama, Japan, 12–16 July 2015; pp. 447–450. [Google Scholar]
- Zarmehi, N.; Akhaee, M.A. Video Steganalysis of Multiplicative Spread Spectrum Steganography. In Proceedings of the 2014 22nd European Signal Processing Conference (EUSIPCO), Lisbon, Portugal, 1–5 September 2014; pp. 2440–2444. [Google Scholar]
- Nugraha, R.M. Implementation of Direct Sequence Spread Spectrum Steganography on Audio Data. In Proceedings of the 2011 International Conference on Electrical Engineering and Informatics, Bandung, Indonesia, 17–19 July 2011; pp. 1–6. [Google Scholar]
- Li, X.; Yu, H.H. Transparent and Robust Audio Data Hiding in Subband Domain. In Proceedings of the International Conference on Information Technology: Coding and Computing (Cat. No.PR00540), Las Vegas, NV, USA, 27–29 March 2000; pp. 74–79. [Google Scholar]
- Hernandez-Garay, S.; Vazquez-Medina, R.; Nino de Rivera, L.; Ponomaryov, V. Steganographic Communication Channel Using Audio Signals. In Proceedings of the 2008 12th International Conference on Mathematical Methods in Electromagnetic Theory, Odessa, Ukraine, 29 June–2 July 2008; pp. 427–429. [Google Scholar]
- Sklar, B. Digital Communications: Fundamentals and Applications, 2nd ed.; Prentice Hall: Upper Saddle River, NJ, USA, 2017; ISBN 978-0-13-472405-8. [Google Scholar]
- Brundick, F.S.; Marvel, L.M. Implementation of Spread Spectrum Image Steganography; Defense Technical Information Center: Fort Belvoir, VA, USA, 2001.
- Boncelet, J.C.G.; Marvel, L.M.; Retter, C.T. Spread Spectrum Image Steganography/Unified Patents. Patents US6557103B1, 29 April 2003. [Google Scholar]
- Kuznetsov, A.; Smirnov, O.; Kovalchuk, D.; Kuznetsova, T. New Technique for Data Hiding in Cover Images Using Adaptively Generated Pseudorandom Sequences. In Proceedings of the International Workshop on Cyber Hygiene (CybHyg-2019) co-located with 1st International Conference on Cyber Hygiene and Conflict Management in Global Information Networks (CyberConf 2019), Kyiv, Ukraine, 30 November 2019; CEUR-WS.org: Tilburg, The Netherlands, 2020; Volume 2654, pp. 1–14. [Google Scholar]
- Kuznetsov, A.; Smirnov, O.; Onikiychuk, A.; Makushenko, T.; Anisimova, O.; Arischenko, A. Adaptive Pseudo-Random Sequence Generation for Spread Spectrum Image Steganography. In Proceedings of the 2020 IEEE 11th International Conference on Dependable Systems, Services and Technologies (DESSERT), Kyiv, Ukraine, 14–18 May 2020; pp. 161–165. [Google Scholar]
- Gaudeamus Igitur. Available online: http://graecolatini.bsu.by/texts/gaudeamus/gaudeamus-data/gaudeamus03.mp3 (accessed on 7 May 2021).
- Kuznetsov, A.; Kiian, A.; Kuznetsova, K.; Smirnov, A. Data Hiding Scheme Based on Spread Sequence Addressing. In Proceedings of the 1st International Workshop on Computational & Information Technologies for Risk-Informed Systems (CITRisk 2020) co-located with XX International scientific and technical conference on Information Technologies in Education and Management (ITEM 2020), Kherson, Ukraine, 15–16 October 2020; pp. 44–58. [Google Scholar]






Publisher’s Note: MDPI stays neutral with regard to jurisdictional claims in published maps and institutional affiliations. |
© 2022 by the authors. Licensee MDPI, Basel, Switzerland. This article is an open access article distributed under the terms and conditions of the Creative Commons Attribution (CC BY) license (https://creativecommons.org/licenses/by/4.0/).
Share and Cite
Kuznetsov, A.; Onikiychuk, A.; Peshkova, O.; Gancarczyk, T.; Warwas, K.; Ziubina, R. Direct Spread Spectrum Technology for Data Hiding in Audio. Sensors 2022, 22, 3115. https://doi.org/10.3390/s22093115
Kuznetsov A, Onikiychuk A, Peshkova O, Gancarczyk T, Warwas K, Ziubina R. Direct Spread Spectrum Technology for Data Hiding in Audio. Sensors. 2022; 22(9):3115. https://doi.org/10.3390/s22093115
Chicago/Turabian StyleKuznetsov, Alexandr, Alexander Onikiychuk, Olga Peshkova, Tomasz Gancarczyk, Kornel Warwas, and Ruslana Ziubina. 2022. "Direct Spread Spectrum Technology for Data Hiding in Audio" Sensors 22, no. 9: 3115. https://doi.org/10.3390/s22093115
APA StyleKuznetsov, A., Onikiychuk, A., Peshkova, O., Gancarczyk, T., Warwas, K., & Ziubina, R. (2022). Direct Spread Spectrum Technology for Data Hiding in Audio. Sensors, 22(9), 3115. https://doi.org/10.3390/s22093115






