Smart and Adaptive Architecture for a Dedicated Internet of Things Network Comprised of Diverse Entities: A Proposal and Evaluation
Abstract
:1. Introduction
- Describe the role of different communication service providers, applications, domain providers, and other service providers in such a setup.
- Architect a system that can meet the requirements of the above scenario.
- Evaluate the proposed competing architectures’ functional suitability, performance, and modifiability.
- C1.
- Described a representative industrial use case: Identification, exploration, evolution, and presentation of an industrial use case that is representative of a dedicated IoT network with major requirements as a part of enhanced mobile broadband spectrum and making it available for the research community. This is an important contribution since, as described above, the gaming domain will have significant future growth, and it presents unique challenges for a dedicated IoT network. Following a systematic approach (Section 3), we have further elaborated the use case in several fundamental ways, which include: the addition of a multi-stakeholder perspective, the ability to have different communications service providers and contracts, scalability to accommodate additional sensors, efficient monitoring and autonomic network management, and billing-as-a-service.
- C2.
- Proposed candidate architectures: Two candidate architectures for addressing the challenges and meeting the requirements of the identified use case.
- C3.
- Evaluated the proposed architectures: Scenario development and detailed scenario-based architecture analysis of the proposed candidate architectures and systems with leading domain and IoT experts. Moreover, expert-judgement based effort analysis of the candidate architectures.
2. Related Work
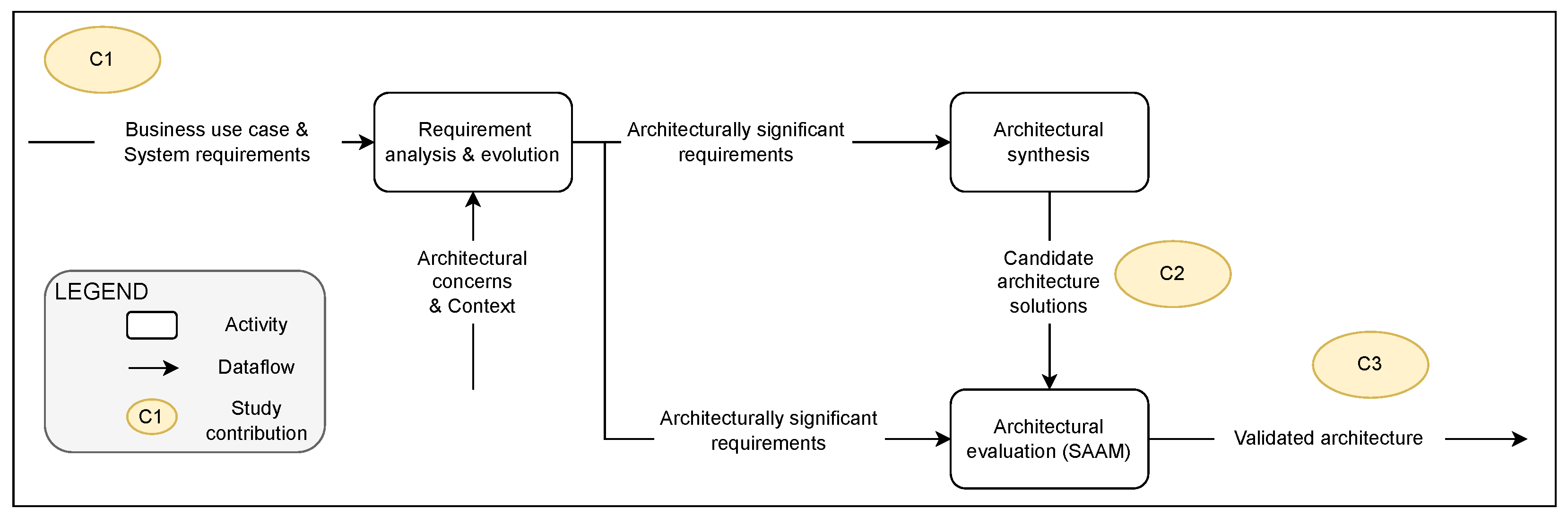
3. Methodology
3.1. C1—Describing the Representative Use Case
3.2. C2—Developing the Candidate Architectures
3.3. C3—Architecture Evaluation
- The candidate architectures were explained to the experts.
- Scenarios were developed based on the chosen use case as in Section 3.1 above.
- Each scenario was evaluated for both the candidate architectures keeping into perspective the functional suitability, performance, and modifiability quality parameters.
- Scenario interactions were discussed.
- The transcripts of the workshop were shared with the experts for validation.
- Evaluation goals:Software and system architecture analysis was performed in this study, taking the major quality characteristics of functional suitability, maintainability and performance into consideration. Therefore, the following parameters based on the ISO 9126 and 25010:2011 standards [39] were used for evaluation. The product quality characteristics considered are: (1) maintainability, (2) functional suitability, and (3) performance. There definitely can be many other important quality characteristics such as security and reliability expected from a mature system. However, as the focus of this research paper is to provide candidate architecture for taking care of the disparate requirements of the different stakeholders coming together in a dedicated IoT network, we shall perform the evaluations on the decided quality characteristics.
- Different requirements are well understood by the different stakeholders involved in the usability process.
- Different team members’ technical competence is adequate for the job with minimum variance between the members.
- Different team members’ domain competence is adequate for the job with minimum variance between the members.
- Three-point estimating (considering the best-case, most likely, and the worst-case estimates and combining in a beta-PERT distribution [41]).
- Reserve estimating (with the contingency reserves for the risk of the known unknowns of the project).
- Analogous estimating (utilizing the analogous measures for a similar set of activities).
- Bottom-up estimating (using a work breakdown structure for the initial cost and change-scenario-based cost).
- Optimistic time (o) is the time based on the ideal availability of resources, and their ideal productivity. It is the minimum possible time required to accomplish an activity or task, assuming all circumstances are better than normal.
- Pessimistic time (p) is the maximum possible time required for accomplishing a task taking the worst-case scenario into perspective.
- Most likely time (m) is based on the best-case scenario assuming all circumstances behave as normal. It is the best estimate or most likely amount of time required to accomplish a task.
- Expected time (te) is the estimated time for accomplishing an activity or task, taking into consideration that normally all circumstances do not fall in line as expected.
- Telecom and Internet of Things domain experts:Expert 1 (A Senior Specialist R&D at a leading Telecommunications vendor with 29 years of experience in Telecom and “Internet of Things” domains)Expert 2 (A Subject Matter Expert at a leading Telecommunications vendor with 31 years of experience in Telecom and “Internet of Things” domains)Expert 3 (A Chief Domain Architect at a leading Telecommunications vendor with 14 years of experience in software architecture and the Telecom domain)
- Software Architect:Expert 4 (A Chief Software Architect, Next Generation BSS at a leading telecommunication vendor with 19 years of experience in software architecture in the Telecom domain after doctorate degree)
- Program Managers:Expert 5 (A Portfolio Program Manager at a leading telecommunication vendor with 13 years of experience in the Telecom domain and project/program management)Expert 6 (A Portfolio Program Manager at a leading telecommunication vendor with 16 years of experience in the Telecom domain and project/program management)
4. Threats to Validity
5. Results
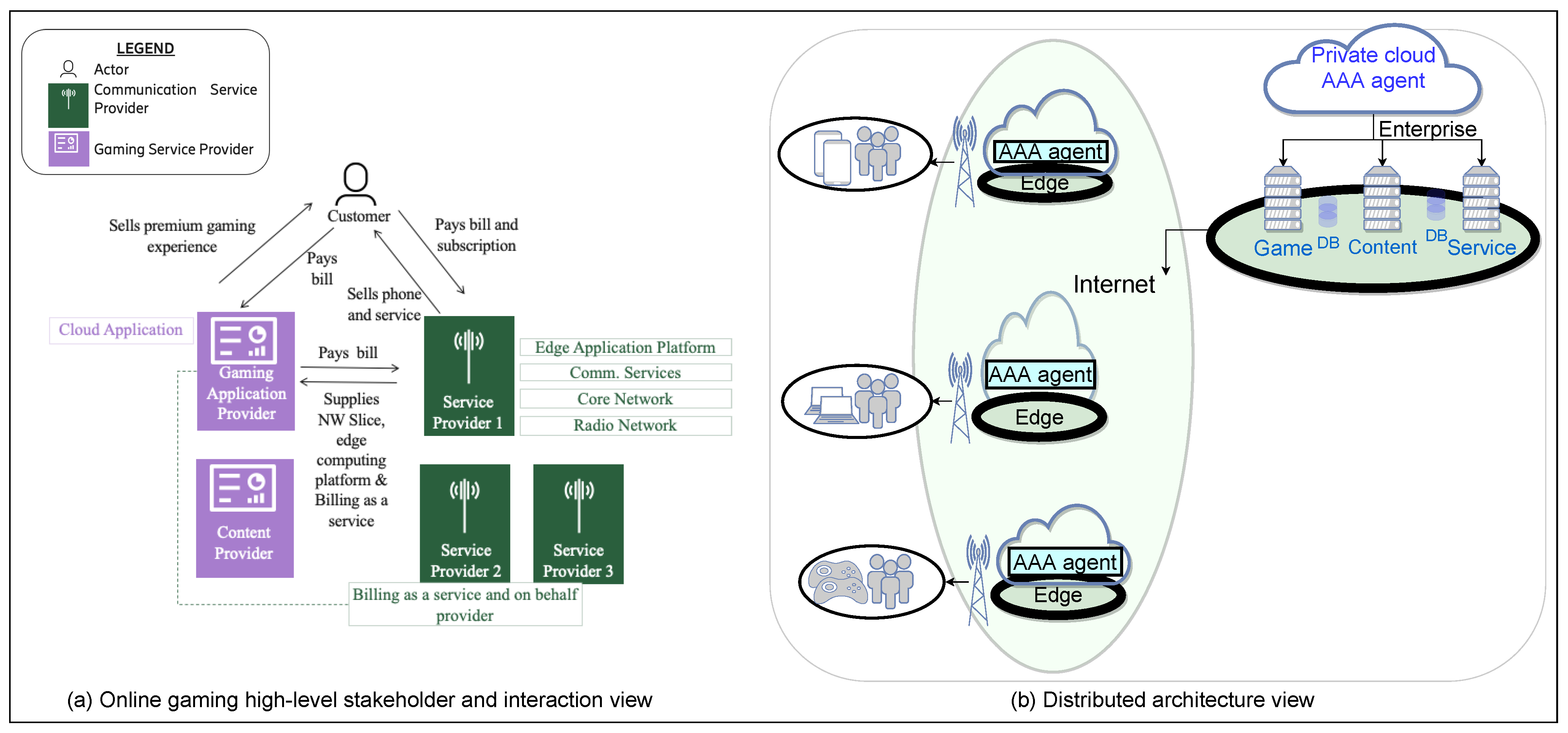
5.1. C1—Use Case
- The multi-stakeholder view that goes beyond the current perspective of one communication service provider and one gaming company providing all the requirements of the dedicated IoT network for the gaming use case.
- A gaming user cannot be bound to only one communication service provider or only one communication medium for playing the games.
- There can be multiple communication service providers in a region or country and the gaming user should be able to play the game (with high speed) irrespective of the communication service provider as a gaming user has a contract with the gaming company and not them for the game.
- The gaming company should have a separate contract with the different communication providers for a network slice with high bandwidth for its games.
- Besides, a gaming company may require several other stakeholders to bring their contents, sensors, and devices into the gaming ecosystem.
- There could be various other services, such as a billing-as-a-service which could be provided by one of the providers in the system.
- Autonomic network management would be a significant requirement for the quick assimilation of all the different stakeholders to inter-work together as well as automatic network changes based on the different contexts of the gaming user and other stakeholders in the system.
- Efficient monitoring of a large number of different stakeholders should also be a requirement in the evolving nature of the stakeholders and the frequent context changes taking place in the system.
- Assimilation of the different stakeholders in the evolving system.
- Run-time-properties based adaptations, such as customer usage and his/her heart rate.
- The dedicated IoT network should provide a seamless gaming experience across different partners (communication service providers), channels (cellular network, Wi-Fi, Wired LAN), and access methodologies (such as 5G-NR, 4G LTE-EPC, Wi-Fi bands) in the enterprise IoT network ecosystem.
- Secure connectivity across the IoT network (same security policy across different partners, access channels, and methodologies).
- Convergent and holistic view of the ecosystem to the different stakeholders in the dedicated IoT network.
- Game is free of charge to the customer. Gaming Inc charges the customer for features (high speed gaming over dedicated network slice), devices, sensors, and characters (avatars).
- Gaming customer activity-/inactivity-based behavior for security and session management.
- Customer usage pattern-based dynamic and enhanced authentication, authorization, and accounting (on Gaming Inc., edge or device) for catering to the different requirements in the dedicated IoT network as described earlier using the Zachman framework.
- Content provider provides premium media content including famous proprietary profiles, avatars and their related video for the game.
- Content provider charges Gaming Inc for the premium content as accessed by its subscribers.
- Seamless integration of new stakeholders and enterprise in the dedicated IoT network.
- Gaming Inc to retain customer sensitive data on its own server and not on the edge cloud provided by the service provider.
- Sensitive information to be passed as range or state as required for the edge computing rather than the sensitive value itself.
- Gaming Inc to have network slice with multiple communication/internet service providers, and agreements for gaming experience and charging and billing as well.
- Convergent billing and billing as a service for the different stakeholders in the system.
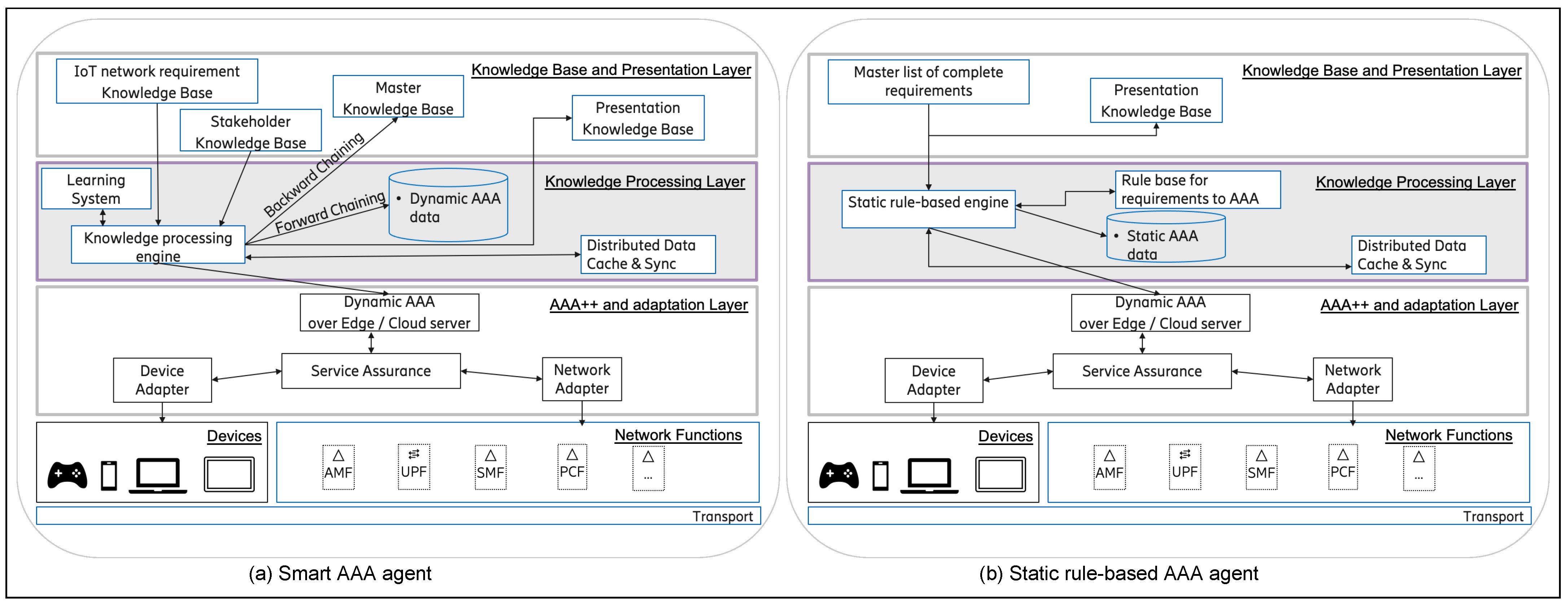
5.2. C2—Architectures
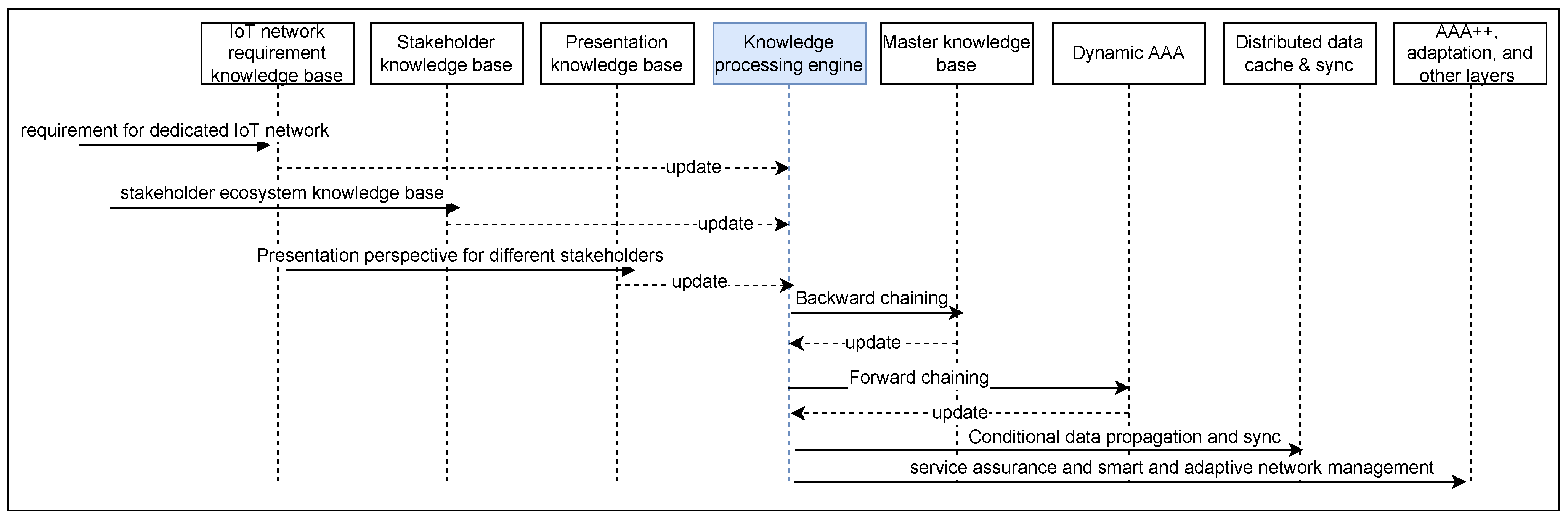
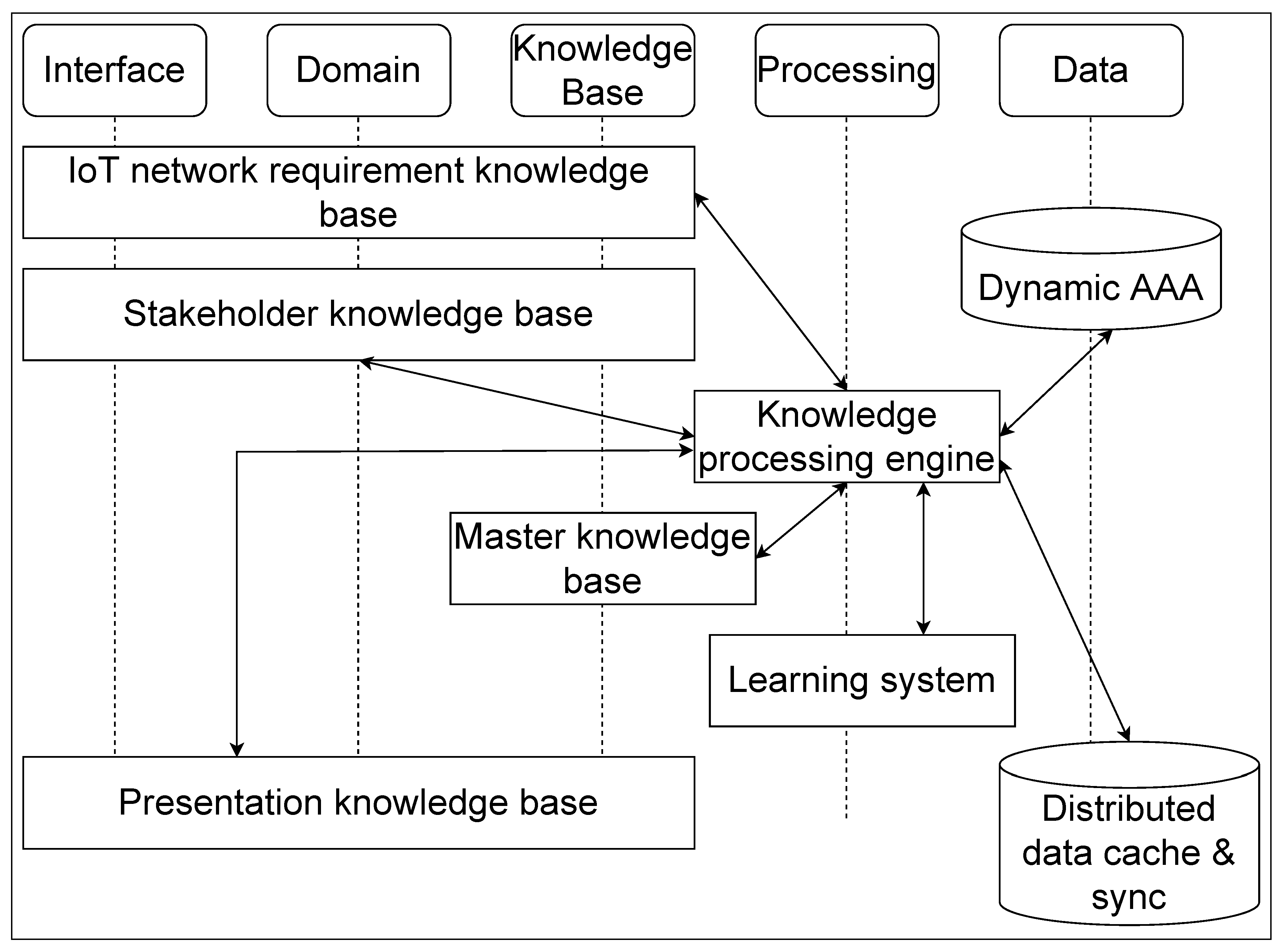
5.2.1. Smart AAA Agent Architecture
5.2.2. Static AAA Agent Architecture
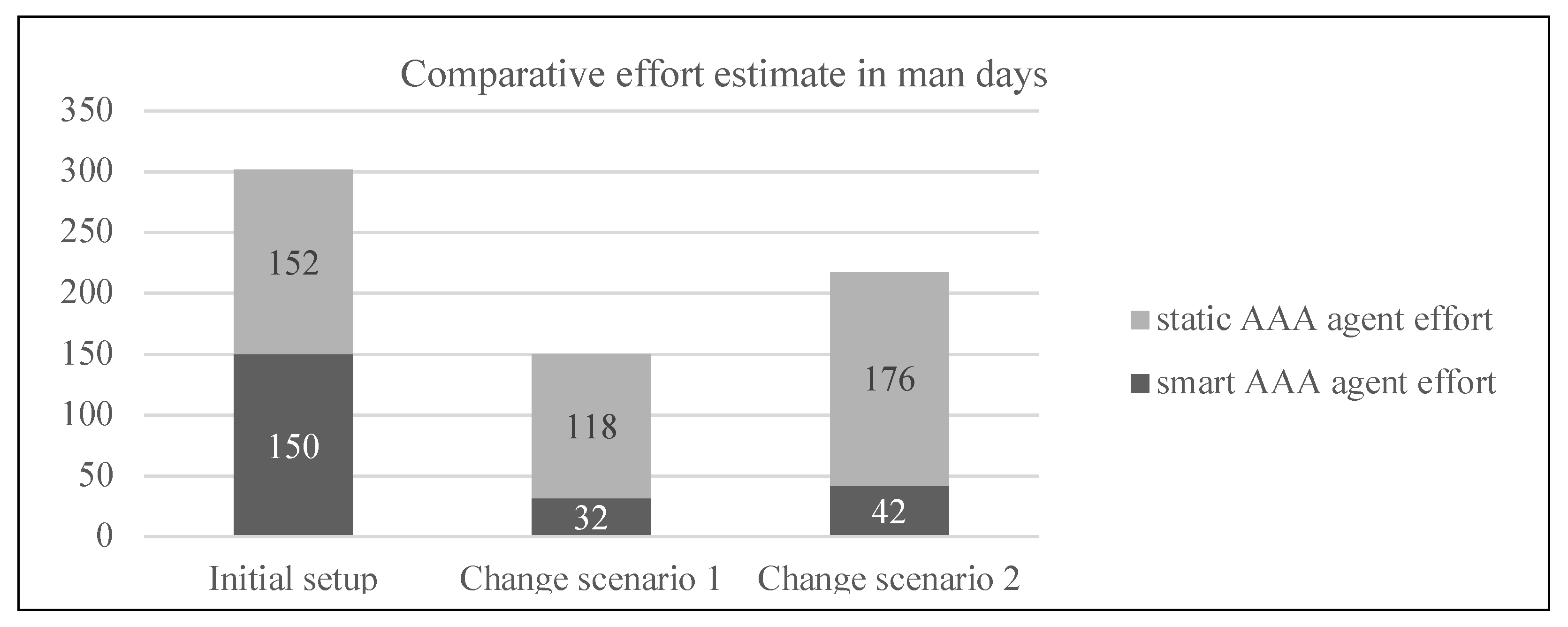
5.3. C3—Evaluation Results
- WBS for the Smart AAA agent (initial effort): Definition of various policies and relevant requirements for the system and its stakeholders, a task that involves Business Analysts (BA), Product Managers (PM), System Managers (SM), and System Engineers (SE). It entails: (i) BAs capturing business opportunity through workshops, and reconciling the requirements for the complete IoT network, (ii) PMs in consultations with BAs creating requirements based on the business opportunity, (iii) SMs and SEs defining and creating the knowledge-fact bases and knowledge rule base for the system with its forward and backward chaining mechanism, and its translation to technical requirements for the system, and (iv) SEs configuring the system for the corresponding knowledge bases and using test automation to secure future changes.
- WBS for the Static rule-based AAA agent (initial effort): Understanding the various policies and other relevant requirements for the system and its stakeholders. This involves similar activities as in the case of the smart AAA agent, however, for PMs, requirements design may change as the system now requires more elaborated parameters which need to be specified in the requirements. This activity can be confined to the current set of requirements and not all the policies need to be modelled into the system. It entails: (i) The same tasks for BAs as in the case of the smart AAA agent, (ii) PMs in consultation with BAs create requirements based on the business opportunity, (iii) PMs and SMs deliberate in detail the various AAA requirements from the system in the context of the above step analysis. They need to understand the policies and requirements from each stakeholder and how they fit into the larger ecosystem and create one large set of AAA requirements for the system based on the immediate needs from each of the system stakeholders, (iv) SEs configure the AAA in the system based on the analysis and inputs from the PMs and SMs as mentioned in the step above, integrate with a learning system for the classification and clustering of usage patterns, and ensure project integrations with the product base for maintainability and upgrades.
- A new sensitive piece of information such as heart rate value is now required to be acquired from the gaming user for a new feature.
- A new service provider is introduced into the dedicated IoT network ecosystem.
- BAs and PMs to understand the policies and requirements just for a new stakeholder or a policy and enlist them. It entails for Scenario 1: BA and PM introduce heart rate value in the system, and for Scenario 2: BA and PM reconcile the change with the IoT ecosystem.
- System manager and engineer to create/update the knowledge base for the delta/change requirement. For Scenario 1: SMs incorporate the heart rate fetching feature, and SEs implement the necessary configuration and automation, and for Scenario 2: SMs introduce a new service provider and SEs implement the necessary changes in the ecosystem and automation.
- Addition of the new/updated knowledge base in the system. For Scenario 1: system enrichment of knowledge base, and for Scenario 2: system enrichment of knowledge base.
- BAs and PMs to understand the policies and requirements for the new stakeholder or a policy and look at the context of the whole system and remodel the whole system. It entails for Scenario 1: BAs and PMs elaborate heart rate value and identify sensitive categorization, and for Scenario 2: BA and PM reconcile requirements with the ecosystem for which it is introduced.
- SMs and SEs remodel the AAA for the whole system. For Scenario 1: SMs reconcile with GDPR compliance and translation of sensitive data to configuration requirements and SEs introduce necessary configuration and automation, and for Scenario 2: SMs and PMs complete the new service provider requirement’s technical translation and SEs implement the necessary configuration and automation.
- Reconfigure the AAA for the whole system. For Scenario 1: Change as new system configuration, and for Scenario 2: Reconfiguration with the whole system
- Integration and reconfiguration for the learning systems for both the scenarios
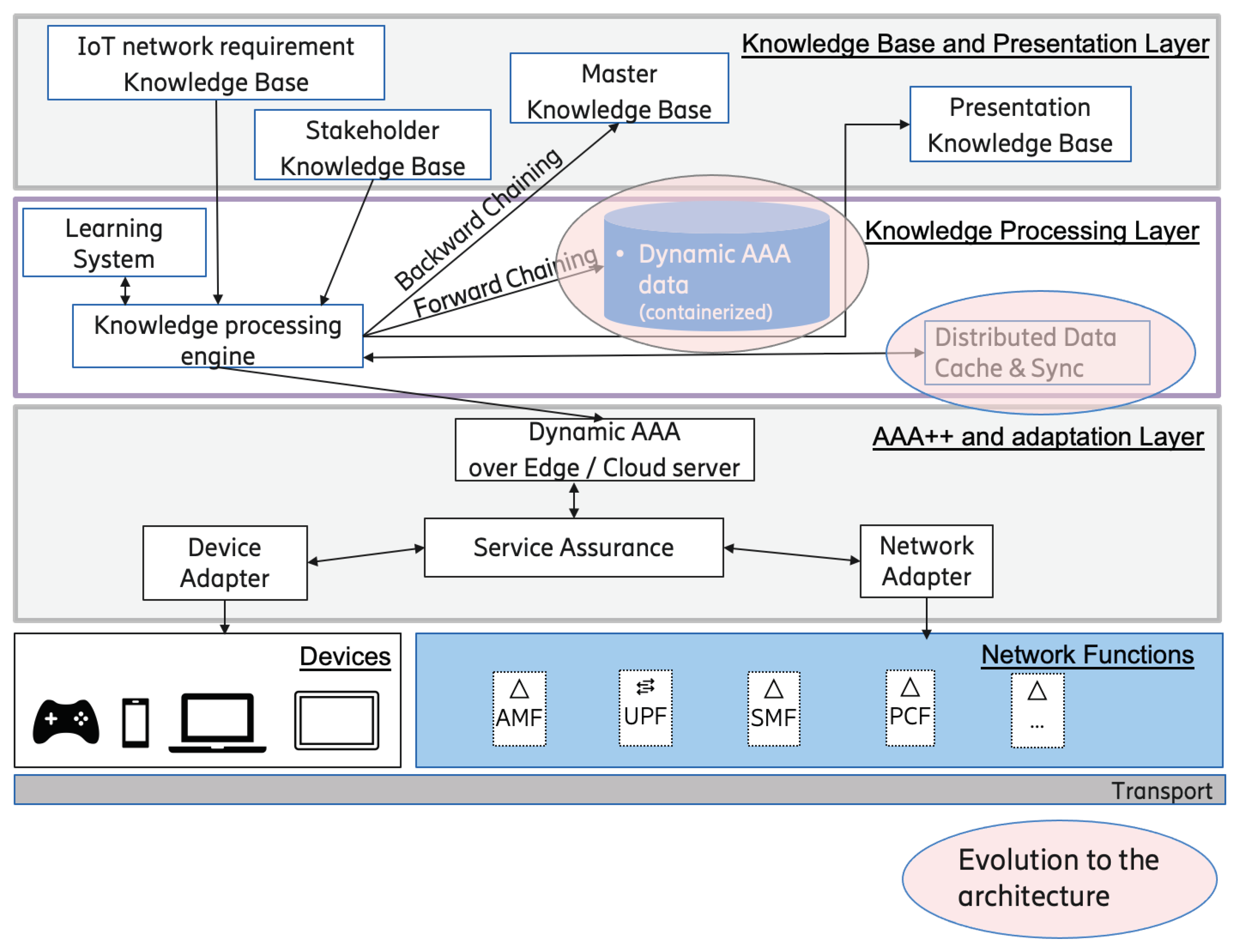
6. Discussion and Updated Architecture
7. Conclusions
Author Contributions
Funding
Conflicts of Interest
Abbreviations
| IoT | Internet of Things |
| AAA | Authentication, authorization, and accounting |
| MEC | Multi-access Edge Computing |
| UX | User experience |
| ML | Machine learning |
| SLA | Service Level Agreement |
| SAAM | Scenario-based Architecture Analysis Method |
| PERT | Program Evaluation and Review Technique |
| BSS | Business Support System |
| PMBOK | Project Management Book of Knowledge |
| WBS | Work Breakdown Structure |
| S-NSSAI | Single Network Slice Selection Assistance Information |
| 5G-NR | 5G New Radio |
| LTE | Long-Term Evolution |
| EPC | Evolved Packet Core |
| CSP | Communication Service Provider |
| REST | Representational State Transfer |
| SP | Service Provider |
| PyKE | Python Knowledge Engine |
| 3GPP | 3rd Generation Partnership Project |
| BA | Business Analyst |
| PM | Product Manager |
| SM | System Manager |
| SE | System Engineer |
| GDPR | EU General Data Protection Regulation |
References
- Chettri, L.; Bera, R. A Comprehensive Survey on Internet of Things (IoT) toward 5G Wireless Systems. IEEE Internet Things J. 2020, 7, 16–32. [Google Scholar] [CrossRef]
- Cero, E.; Baraković Husić, J.; Baraković, S. IoT’s Tiny Steps towards 5G: Telco’s Perspective. Symmetry 2017, 9, 213. [Google Scholar] [CrossRef]
- Sharma, S.; Chang, V.; Tim, U.S.; Wong, J.; Gadia, S. Cloud and IoT-based emerging services systems. Clust. Comput. 2019, 22, 71–91. [Google Scholar] [CrossRef] [Green Version]
- Wong, S.; Sastry, N.; Holland, O.; Friderikos, V.; Dohler, M.; Aghvami, H. Virtualized authentication, authorization and accounting (V-AAA) in 5G networks. In Proceedings of the 2017 IEEE Conference on Standards for Communications and Networking (CSCN), Helsinki, Finland, 18–20 September 2017; pp. 175–180. [Google Scholar] [CrossRef]
- Nitti, M.; Pilloni, V.; Colistra, G.; Atzori, L. The Virtual Object as a Major Element of the Internet of Things: A Survey. IEEE Commun. Surv. Tutor. 2016, 18, 1228–1240. [Google Scholar] [CrossRef] [Green Version]
- Vlacheas, P.; Giaffreda, R.; Stavroulaki, V.; Kelaidonis, D.; Foteinos, V.; Poulios, G.; Demestichas, P.; Somov, A.; Biswas, A.; Moessner, K. Enabling smart cities through a cognitive management framework for the internet of things. IEEE Commun. Mag. 2013, 51, 102–111. [Google Scholar] [CrossRef]
- Atzori, L.; Iera, A.; Morabito, G. The Internet of Things: A survey. Comput. Netw. 2010, 54, 2787–2805. [Google Scholar] [CrossRef]
- Singh, S.P.; Sidorova, J.; Bin Ali, N.; Lundberg, L. From Traditional to Next Generation AAA: A reference Architecture for a Dedicated IoT Network. In Proceedings of the IV International Scientific Conference “Convergent Cognitive Information Technologies”, Moscow, Russia, 17 November 2019; Available online: http://it-edu.oit.cmc.msu.ru/index.php/convergent/convergent2019/paper/view/1122 (accessed on 20 January 2021).
- Arnold, P.; Von Hugo, D. Future integrated communication network architectures enabling heterogeneous service provision. Adv. Radio Sci. 2018, 16, 59–66. [Google Scholar] [CrossRef]
- Henry, S.; Alsohaily, A.; Sousa, E. 5G is Real: Evaluating the Compliance of the 3GPP 5G New Radio System with the ITU IMT-2020 Requirements. IEEE Access 2020, 8, 42828–42840. [Google Scholar] [CrossRef]
- Alkhabbas, F.; Spalazzese, R.; Davidsson, P. An Agent-Based Approach to Realize Emergent Configurations in the Internet of Things. Electronics 2020, 9, 1347. [Google Scholar] [CrossRef]
- Bellavista, P.; Giannelli, C.; Lanzone, S.; Riberto, G.; Stefanelli, C.; Tortonesi, M. A Middleware Solution for Wireless IoT Applications in Sparse Smart Cities. Sensors 2017, 17, 2525. [Google Scholar] [CrossRef] [Green Version]
- Su, B.; Wang, S. An agent-based distributed real-time optimal control strategy for building HVAC systems for applications in the context of future IoT-based smart sensor networks. Appl. Energy 2020, 274, 115322. [Google Scholar] [CrossRef]
- Han, B.; Wong, S.; Mannweiler, C.; Crippa, M.R.; Schotten, H.D. Context-Awareness Enhances 5G Multi-Access Edge Computing Reliability. IEEE Access 2019, 7, 21290–21299. [Google Scholar] [CrossRef]
- Rothe, L.; Loske, M.; Gertler, D.G. Proposing Context-Aware Authentication for the Industrial Internet of Things. In Proceedings of the 2018 IEEE Global Conference on Internet of Things (GCIoT), Alexandria, Egypt, 5–7 December 2018; pp. 1–5. [Google Scholar] [CrossRef]
- Zarca, A.M.; Garcia-Carrillo, D.; Bernabe, J.B.; Ortiz, J.; Marin-Perez, R.; Skarmeta, A. Managing AAA in NFV/SDN-enabled IoT scenarios. In Proceedings of the 2018 Global Internet of Things Summit, GIoTS, Bilbao, Spain, 4–7 June 2018; Institute of Electrical and Electronics Engineers Inc.: Piscataway, NJ, USA, 2018. [Google Scholar] [CrossRef]
- Zarca, A.M.; Garcia-Carrillo, D.; Bernabe, J.B.; Ortiz, J.; Marin-Perez, R.; Skarmeta, A. Enabling virtual AAA management in SDN-based IoT networks. Sensors 2019, 19, 295. [Google Scholar] [CrossRef] [Green Version]
- Shahzad, M.; Singh, M.P. Continuous authentication and authorization for the internet of things. IEEE Internet Comput. 2017, 21, 86–90. [Google Scholar] [CrossRef]
- Mobile Cloud Gaming—Mobility Report—Ericsson. Available online: https://www.ericsson.com/en/mobility-report/articles/mobile-cloud-gaming (accessed on 20 January 2021).
- Arzo, S.T.; Bassoli, R.; Granelli, F.; Fitzek, F.H. Multi-Agent Based Autonomic Network Management Architecture. IEEE Trans. Netw. Serv. Manag. 2021, 18, 3595–3618. [Google Scholar] [CrossRef]
- Kallel, A.; Rekik, M.; Khemakhem, M. IoT-fog-cloud based architecture for smart systems: Prototypes of autism and COVID-19 monitoring systems. Softw. Pract. Exp. 2021, 51, 91–116. [Google Scholar] [CrossRef]
- Raposo, D.; Rodrigues, A.; Sinche, S.; Silva, J.S.; Boavida, F. Industrial IoT monitoring: Technologies and architecture proposal. Sensors 2018, 18, 3568. [Google Scholar] [CrossRef] [Green Version]
- Santamaria, A.F.; Raimondo, P.; Tropea, M.; De Rango, F.; Aiello, C. An IoT surveillance system based on a decentralised architecture. Sensors 2019, 19, 1469. [Google Scholar] [CrossRef] [Green Version]
- Weyrich, M.; Ebert, C. Reference architectures for the internet of things. IEEE Softw. 2016, 33, 112–116. [Google Scholar] [CrossRef]
- Larrucea, X.; Combelles, A.; Favaro, J.; Taneja, K. Software Engineering for the Internet of Things. IEEE Softw. 2017, 34, 24–28. [Google Scholar] [CrossRef]
- Fahmideh, M.; Abbasi, A.A.; Behnaz, A.; Grundy, J.; Susilo, W. Software Engineering for Internet of Things. IEEE Trans. Softw. Eng. 2021. [Google Scholar] [CrossRef]
- Trnka, M.; Cerny, T.; Stickney, N. Survey of Authentication and Authorization for the Internet of Things. Secur. Commun. Netw. 2018, 2018, 4351603. [Google Scholar] [CrossRef] [Green Version]
- Hofmeister, C.; Kruchten, P.; Nord, R.L.; Obbink, H.; Ran, A.; America, P. A general model of software architecture design derived from five industrial approaches. J. Syst. Softw. 2007, 80, 106–126. [Google Scholar] [CrossRef]
- TR276 Introducing 5G Monetization R18.5; TM Forum: London, UK, 2018.
- Runeson, P.; Höst, M. Guidelines for conducting and reporting case study research in software engineering. Empir. Softw. Eng. 2009, 14, 131–164. [Google Scholar] [CrossRef] [Green Version]
- Wegmann, A.; Kotsalainen, A.; Matthey, L.; Regev, G.; Giannattasio, A. Augmenting the Zachman Enterprise Architecture Framework with a Systemic Conceptualization. In Proceedings of the 2008 12th International IEEE Enterprise Distributed Object Computing Conference, Munich, Germany, 15–19 September 2008; pp. 3–13. [Google Scholar] [CrossRef] [Green Version]
- Iyamu, T. Implementation of the enterprise architecture through the Zachman Framework. J. Syst. Inf. Technol. 2018, 20, 2–18. [Google Scholar] [CrossRef]
- Kazman, R.; Abowd, G.; Bass, L.; Clements, P. Scenario-Based Analysis of Software Architecture; Software Engineering Institute: Pittsburgh, PA, USA, 1996. [Google Scholar] [CrossRef] [Green Version]
- Ionita, M.T.; Hammer, D.K.; Obbink, H. Scenario-based software architecture evaluation methods: An overview. In Proceedings of the Workshop on Methods and Techniques for Software Architecture Review and Assessment at the International Conference on Software Engineering, Orlando, FL, USA, 19–25 May 2002; pp. 1–12. [Google Scholar]
- Kazman, R.; Bass, L.; Abowd, G.; Webb, M. SAAM: A method for analyzing the properties of software architectures. In Proceedings of the International Conference on Software Engineering, Sorrento, Italy, 16–21 May 1994; pp. 81–90. [Google Scholar] [CrossRef]
- Daramola, O.; Thebus, D. Architecture-Centric Evaluation of Blockchain-Based Smart Contract E-Voting for National Elections. Informatics 2020, 7, 16. [Google Scholar] [CrossRef]
- Roy, B.; Mondal, A.K.; Roy, C.K.; Schneider, K.A.; Wazed, K. Towards a Reference Architecture for Cloud-Based Plant Genotyping and Phenotyping Analysis Frameworks. In Proceedings of the 2017 IEEE International Conference on Software Architecture, ICSA 2017, Gothenburg, Sweden, 3–7 April 2017; Institute of Electrical and Electronics Engineers Inc.: Piscataway, NJ, USA, 2017; pp. 41–50. [Google Scholar] [CrossRef]
- Leotta, M.; Ricca, F.; Reggio, G.; Astesiano, E. Comparing the maintainability of two alternative architectures of a postal system: SOA vs. non-SOA. In Proceedings of the European Conference on Software Maintenance and Reengineering, CSMR, Oldenburg, Germany, 1–4 March 2011; pp. 317–320. [Google Scholar] [CrossRef]
- ISO/IEC 25010:2011(en); Systems and Software Engineering—Systems and Software Quality Requirements and Evaluation (SQuaRE)—System and Software Quality Models. ISO: London, UK; IEC: Geneva, Switzerland, 2011.
- Project Management Institute. A Guide to the Project Management Body of Knowledge (PMBOK Guide)/Project Management Institute; Project Management Institute: Newtown Square, PA, USA, 2017. [Google Scholar]
- Engwall, M. PERT, Polaris, and the realities of project execution. Int. J. Manag. Proj. Bus. 2012, 5, 595–616. [Google Scholar] [CrossRef]
- Ali, N.B.; Petersen, K.; Schneider, K. FLOW-assisted value stream mapping in the early phases of large-scale software development. J. Syst. Softw. 2016, 111, 213–227. [Google Scholar] [CrossRef] [Green Version]
- Shah, S.D.A.; Gregory, M.A.; Li, S.; Fontes, R.D.R. SDN enhanced multi-access edge computing (MEC) for E2E mobility and QoS management. IEEE Access 2020, 8, 77459–77469. [Google Scholar] [CrossRef]
- Porambage, P.; Okwuibe, J.; Liyanage, M.; Ylianttila, M.; Taleb, T. Survey on Multi-Access Edge Computing for Internet of Things Realization. IEEE Commun. Surv. Tutor. 2018, 20, 2961–2991. [Google Scholar] [CrossRef] [Green Version]
- Pham, Q.V.; Fang, F.; Ha, V.N.; Piran, M.J.; Le, M.; Le, L.B.; Hwang, W.J.; Ding, Z. A Survey of Multi-Access Edge Computing in 5G and beyond: Fundamentals, Technology Integration, and State-of-the-Art. IEEE Access 2019, 8, 116974–117017. [Google Scholar] [CrossRef]
- Day, P.; Iannucci, S.; Banicescu, I. Autonomic Feature Selection using Computational Intelligence. Future Gener. Comput. Syst. 2020, 111, 68–81. [Google Scholar] [CrossRef]
- Zhang, X.; Moynihan, G.P.; Ernest, A.N.S.; Gutenson, J.L. Evaluation of the benefits of using a backward chaining decision support expert system for local flood forecasting and warning. Expert Syst. 2018, 35, e12261. [Google Scholar] [CrossRef]
- Mec. GS MEC 003—V2.2.1—Multi-Access Edge Computing (MEC); Framework and Reference Architecture; Technical Report; ETSI: Sophia Antipolis, France, 2020. [Google Scholar]
- Specification # 28.804. Available online: https://portal.3gpp.org/desktopmodules/Specifications/SpecificationDetails.aspx?specificationId=3549 (accessed on 20 January 2021).
| What | How | Where | Who | When | Why | |
|---|---|---|---|---|---|---|
| Authentication | Gaming device, mobile device with gaming app, gaming customer, IoT network stakeholder | Device id, pin, password, fingerprint, face recognition, iris | Network and other zones, geographical location, auth engine | Device, customer, IoT administrator, service providers | Time, day, state of device | Security, risk mitigation, change of location and jurisdiction, & other motivations |
| Authorization | Device administration, premium gaming, sensitive information | Local, workflow, message queue | Location based authorization and associated workflow | Device, gaming customer, IoT admin, stakeholder | Conditional, time, day, state of device | SLA (service level agreement), service, monetization, maintenance, criticality and mitigation |
| Accounting | ML (machine learning) data, device data, network data | Local log, event record, workflow, message queue | On device, edge, stakeholder cloud, server | Device, user, stakeholder network, application | Continuous, conditional or need based | IoT network requirement, optimization, UX (user experience) |
| Quality Attributes | ID | Zachman’s Interogatives | |||||||
|---|---|---|---|---|---|---|---|---|---|
| Performance | Functional suitability | Modifiability | What | Who | Where | How | When | Why | |
| ✔ | ✔ | S1 | Premium Gaming Customer’s new sensitive information such as heart rate acquisitionof an existing customer of a partner communication service provider (CSP)is to be done in the Gaming Inc cloud/serverusing the secure REST interface and following security policywhen a new request is received at Gaming Inc server for bio feedback-based gamingbecause it is very important, sensitive and urgent information. | ||||||
| ✔ | ✔ | ✔ | S2 | Access of premium Gaming Customer sensitive information such as heart rateof an existing customer of a partner CSPis to be conducted from the Gaming Inc cloud/serverusing the secure REST interface and on encrypted state/range information as required by the game, rather than the original heart rate valuewhen a new request is received at Gaming Inc server for bio feedback-based gamingbecause it is very important, sensitive and urgent information. | |||||
| ✔ | ✔ | S3 | Existing premium Gaming Customer Network slice information provisioningof an existing customer of Gaming Incis to be conducted in a new partner communication service providerusing the dedicated NSSAI interfacewhen a new partner Communication Service provider onboards the partnershipbecause it is very important, and operational information for high-speed gaming service delivery and monetization. | ||||||
| ✔ | ✔ | S4 | Gaming app to require lower level of configured security for accessof gaming app consumer and their devicein home locationusing the secure REST interfacewhen the consumer is trying to access game and has pre-registered it as home location in the systembecause it is important for security and ease of access in the system. | ||||||
| ✔ | ✔ | S5 | Gaming app to require lowest level of configured security for accessof gaming app consumer and their devicein home location and the usual pattern of time for the customerusing the secure REST interfacewhen the consumer is trying to access game and has pre-registered it as home location in the system and the system has learned the usage pattern and classified it safebecause it is important for security and ease of access in the system. | ||||||
| ✔ | ✔ | S6 | A new SP being introduced in the dedicated IoT networkby the IoT network administratorin admin office locationusing the secure REST interfaceshould be performed on demand and seamlesslyto allow the intelligent enterprise integration and enhancement. | ||||||
| ✔ | ✔ | S7 | The event records to be sent to billing as a service provider for the consumption of media content from the new content provider just introduced in the dedicated IoT networkby the IoT network administrationin smart AAA agent and IoT network administrationusing the secure REST interfaceshould be conducted on onboarding of a new content provider and seamlesslyto allow the intelligent enterprise integration and enhancement. | ||||||
| ✔ | ✔ | S8 | Event records to be split, merged or duplicatedfor a stakeholder having a different configuration of time zone, calendar and cyclesin smart AAA agent and IoT network administrationusing the secure REST interfaceshould be conducted on onboarding or any corresponding change for a stakeholder and seamlesslyto allow the intelligent enterprise integration and enhancement. | ||||||
| Candidate Architecture | Tasks Based on Work Break Down Structure | Three-Point Estimation | Work Package Effort (PERT) | Risk Coverage | Total Estimated Effort in Man Days (with 68% Probability) | ||
|---|---|---|---|---|---|---|---|
| o | m | p | te | ||||
| Initial/Upfront effort estimate. | |||||||
| Smart AAA agent | Business analyst and project management | 27 | 49 | 65 | 48 | 18 | 150 (±standard deviation of 4.5) |
| System management and engineering tasks | 20 | 30 | 40 | 30 | 15 | ||
| Configuration and automation | 19 | 26 | 35 | 26 | 13 | ||
| Static AAA agent | Business analyst and project management | 16 | 29 | 38 | 28 | 18 | 152 (±standard deviation of 3.6) |
| System management and engineering tasks | 43 | 59 | 81 | 60 | 22 | ||
| Maintainability | 5 | 7 | 10 | 7 | 5 | ||
| Change scenario 1: New sensitive information such as a heart rate value is now required to be acquired from the gaming user for a new feature. | |||||||
| Smart AAA agent | Business analyst and project management | 5 | 8 | 10 | 8 | 3 | 32 (±standard deviation of 1.5) |
| System management and engineering tasks | 5 | 9 | 14 | 9 | 4 | ||
| Knowledge base configuration | 3 | 5 | 8 | 5 | 2 | ||
| Static AAA agent | Business analyst and project management | 16 | 20 | 24 | 20 | 10 | 118 (±standard deviation of 2.8) |
| System management and engineering tasks | 23 | 30 | 37 | 30 | 13 | ||
| Configuration | 10 | 15 | 18 | 15 | 8 | ||
| Integration and reinforcement | 10 | 15 | 18 | 15 | 8 | ||
| Change scenario 2: A new service provider is introduced into the dedicated IoT network ecosystem. | |||||||
| Smart AAA agent | Business analyst and project management | 7 | 10 | 12 | 10 | 4 | 42 (±standard deviation of 1.4) |
| System management and engineering tasks | 11 | 15 | 18 | 15 | 6 | ||
| Knowledge base configuration | 3 | 5 | 8 | 5 | 2 | ||
| Static AAA agent | Business analyst and project management | 20 | 24 | 30 | 24 | 11 | 176 (±standard deviation of 3.7) |
| System management and engineering tasks | 40 | 51 | 60 | 51 | 23 | ||
| Configuration | 20 | 25 | 30 | 25 | 11 | ||
| Integration and reinforcement | 15 | 20 | 25 | 20 | 11 | ||
| Scenario | Existing Network Architecture | Static Rule-Based AAA Agent | Smart AAA Agent for Dedicated IoT Network |
|---|---|---|---|
| S1 | Not compliant, requires explicit configuration and adaptation in the system | Partially compliant, with some level of classification of data into sensitivity categories and explicit configuration for the same | Compliant, with the intelligent system performing the machine reasonings based on the configured knowledge base |
| S2 | Not compliant, requires integration with an intelligent system that can classify the data into the required format | Partially compliant, requires integration with an intelligent system that can classify the data into the required format | Compliant, with the intelligent system performing the machine reasonings based on the configured knowledge base |
| S3 & S6 | Not compliant. It requires huge effort for integration with other networks and creating a centralized “Home Subscriber server” kind of system for the whole dedicated IoT network | Partially compliant, requires explicit configuration of rules for the new stakeholder/communication service provider | Compliant, with addition of the knowledge base for the new service provider and the intelligent system assimilates it into the existing knowledge base for the system |
| S4 & S5 | Not compliant, requires integration to an intelligent learning system | Partially compliant, and requires explicit rules to be configured and integration to a learning system | Compliant, with the intelligent learning system and knowledge rule base as an integral part of the system |
| S7 | Not compliant | Partially complaint, requires an explicit configuration of rules for the new content provider introduced in the system | Compliant, with the configured knowledge base in the system taking care of the requirement |
| S8 | Not compliant, requires integration with a mediation system or some other custom solution for the same | Compliant, however requires explicit configuration of accounting rules for the new stakeholder or the requirements | Compliant, with the configured knowledge base in the system taking care of the requirement |
Publisher’s Note: MDPI stays neutral with regard to jurisdictional claims in published maps and institutional affiliations. |
© 2022 by the authors. Licensee MDPI, Basel, Switzerland. This article is an open access article distributed under the terms and conditions of the Creative Commons Attribution (CC BY) license (https://creativecommons.org/licenses/by/4.0/).
Share and Cite
Singh, S.P.; Ali, N.B.; Lundberg, L. Smart and Adaptive Architecture for a Dedicated Internet of Things Network Comprised of Diverse Entities: A Proposal and Evaluation. Sensors 2022, 22, 3017. https://doi.org/10.3390/s22083017
Singh SP, Ali NB, Lundberg L. Smart and Adaptive Architecture for a Dedicated Internet of Things Network Comprised of Diverse Entities: A Proposal and Evaluation. Sensors. 2022; 22(8):3017. https://doi.org/10.3390/s22083017
Chicago/Turabian StyleSingh, Shailesh Pratap, Nauman Bin Ali, and Lars Lundberg. 2022. "Smart and Adaptive Architecture for a Dedicated Internet of Things Network Comprised of Diverse Entities: A Proposal and Evaluation" Sensors 22, no. 8: 3017. https://doi.org/10.3390/s22083017
APA StyleSingh, S. P., Ali, N. B., & Lundberg, L. (2022). Smart and Adaptive Architecture for a Dedicated Internet of Things Network Comprised of Diverse Entities: A Proposal and Evaluation. Sensors, 22(8), 3017. https://doi.org/10.3390/s22083017






