Towards Double Defense Network Security Based on Multi-Identifier Network Architecture
Abstract
:1. Introduction
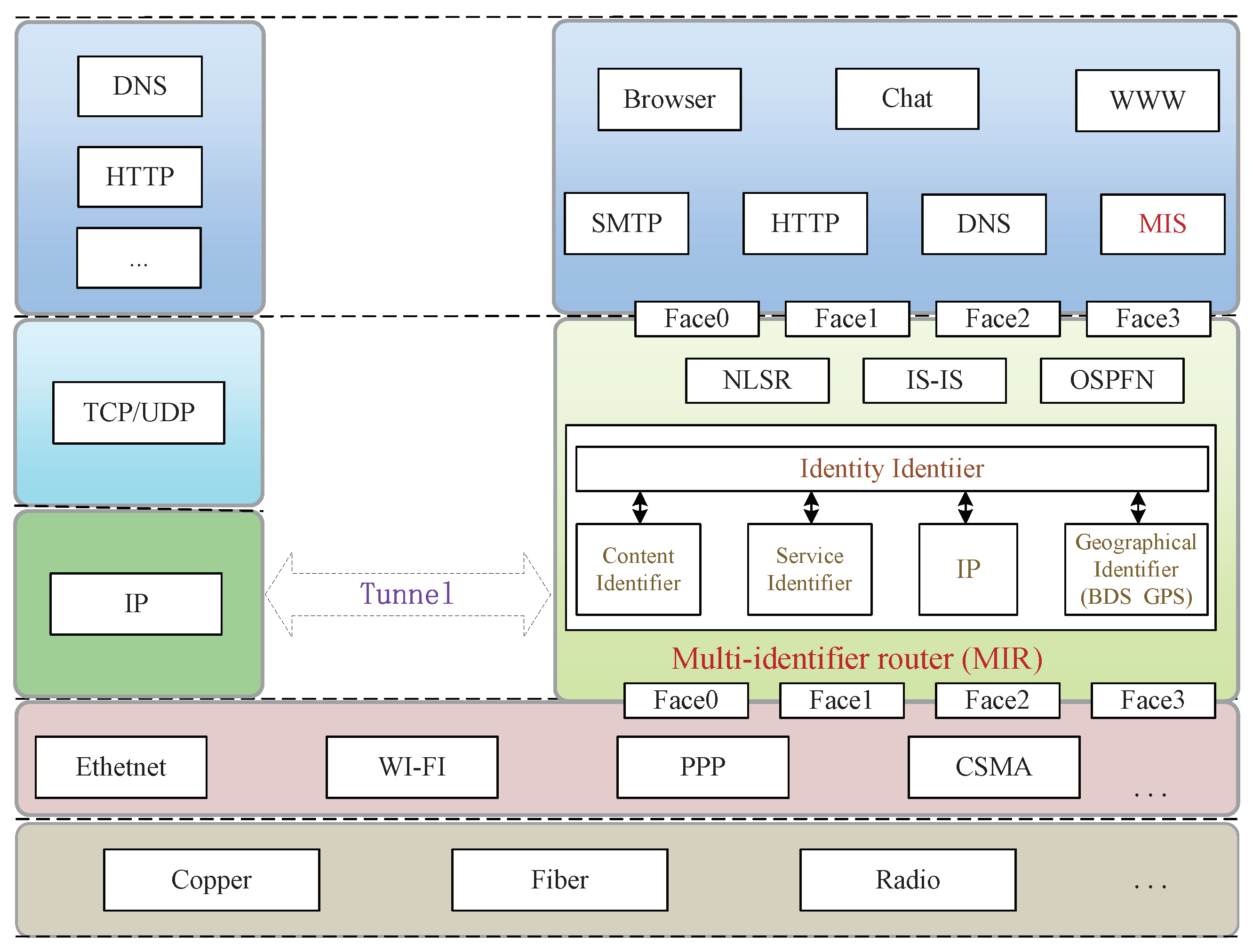
- This paper discusses the problem of the network’s bottleneck resulting from the traditional IP-network carrying capacity and the poor network security. In this regard, we inspire our proposed system from the idea of zero-trust network [10]. In doing so, based on MIN architecture [9,11], we built a security strategy with an identity identifier as the core of network transmission. This strategy is built based on identity identifiers rather than network locations. Only after user authentication, authorization, and account verification can the user and the application communicate.
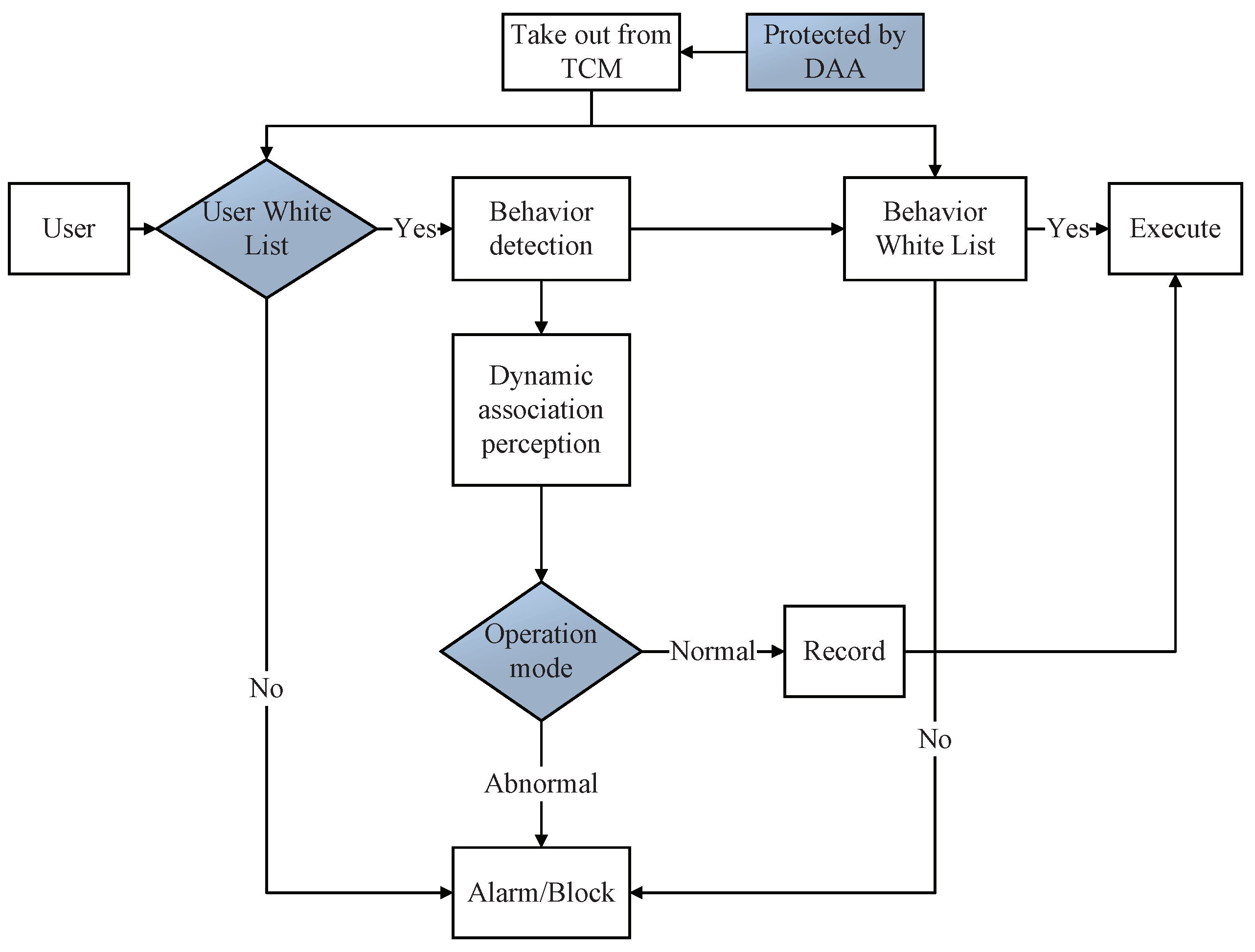
- Signature of network transmission packets protects data from theft. A variety of the data related to the identifiers is stored in the consortium blockchain of the MIN to ensure the identifier data’s non-repudiation, tampering-resistance, and traceability. The independently developed voting consensus algorithm Proof of Vote (PoV) [12] improves the throughput of the system. At the same time, the encryption key and data are stored in the trusted computing modules (TCM) to ensure that they are not read or disclosed [13], and protected by remote authentication [14]. Real-time monitoring of the trusted whitelist of accessing applications can promptly detect and respond to attacks.
- The network traffic and application access logs are collected and analyzed for further situation awareness. DDESS classifies and extracts appropriate attack information, including attack behavior and mode, and makes use of the convolutional neural networks (CNN) to evaluate the network security attack index of attack information. In addition, DDESS predicts the network security of the existing network system and provides the corresponding solutions. DDESS simulates network behaviors in the sandbox. It then analyzes these simulation results, cultivates a security immune vaccine, enriches the network attack behavior database, and prevents unknown network attack behaviors.
2. Related Work
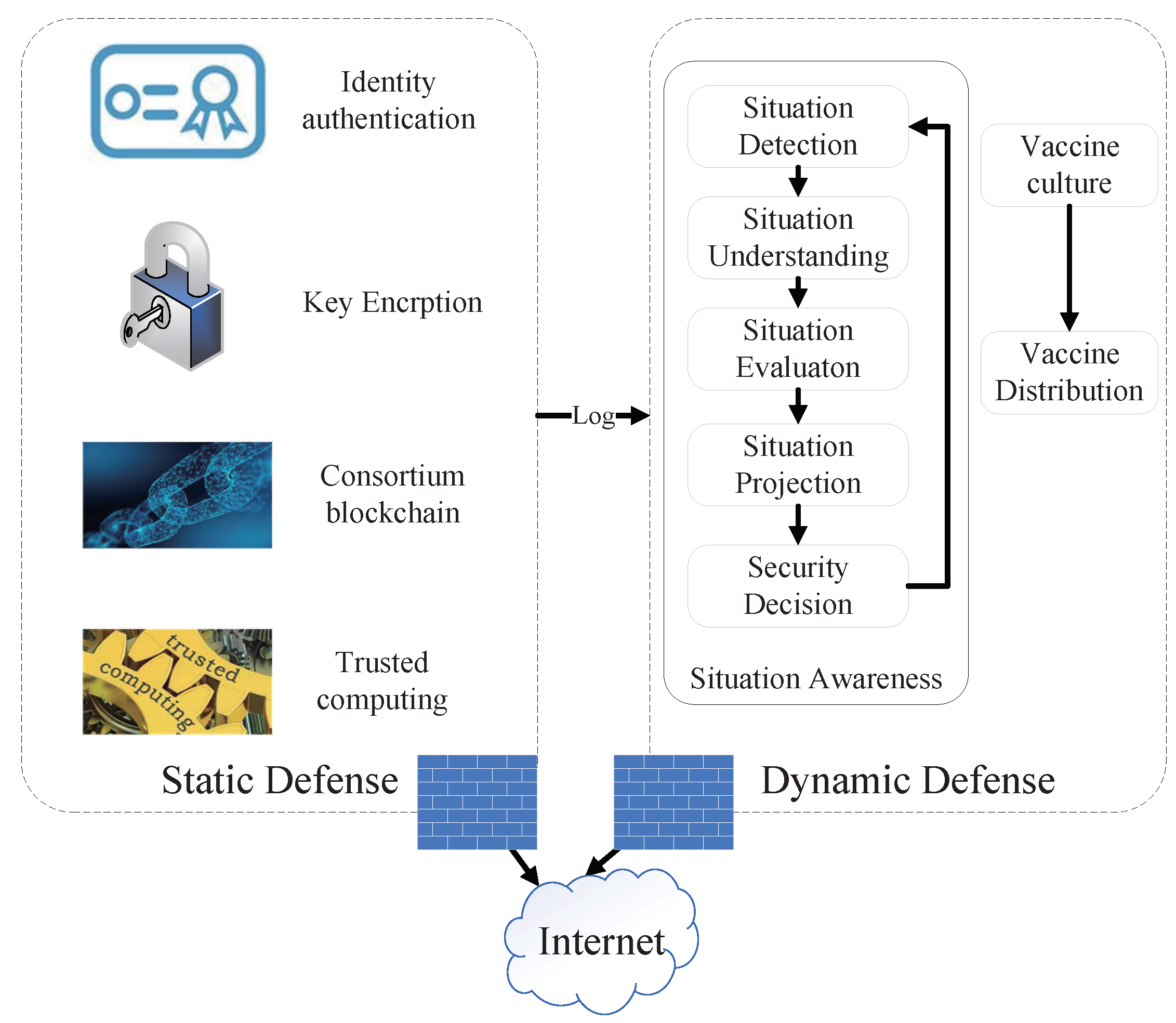
3. Static Defense
3.1. Multi-Identifier Network System with Identity as the Core
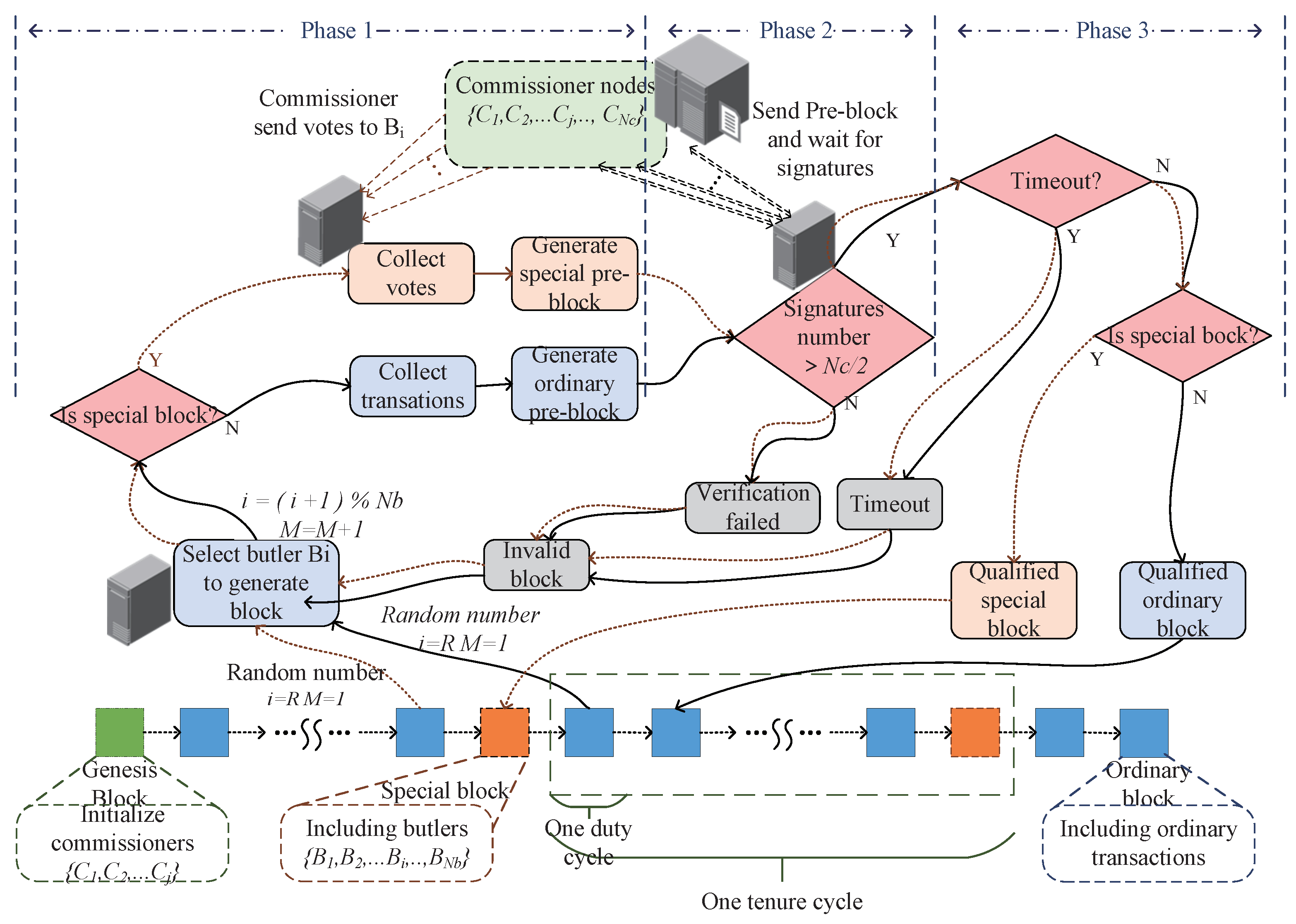
3.2. Encryption and Blockchain Protection
3.3. Trusted Computing Whitelist
4. Dynamic Defense
4.1. Situation Awareness
| Algorithm 1 Training of security situational project model |
| Input: |
| The total number of layers L, the number of neurons in each hidden layer and output layer, |
| activation function f, loss function, iteration step , |
| maximum iteration times and stop iteration threshold |
| Output: |
| linear relation coefficient matrix and bias vector b of each hidden layer and output layer. |
| 1: Input the risk vector dataset . |
| 2: for m=1 to L do |
| 3: Extract the layer features with a convolution kernel |
| 4: Reduce network scale with max pooling: |
| 5: end for |
| 6: update the weight with backpropagation: |
| 7: for to 2 do |
| 8: Compute based on and and |
| 9: Compute the gradient and |
| 10: Update and in lth layer: |
| 11: if or then |
| 12: break; |
| 13: end if |
| 14: end for |
4.2. Network Security Vaccine Training and Herd Immunity
5. Experiments
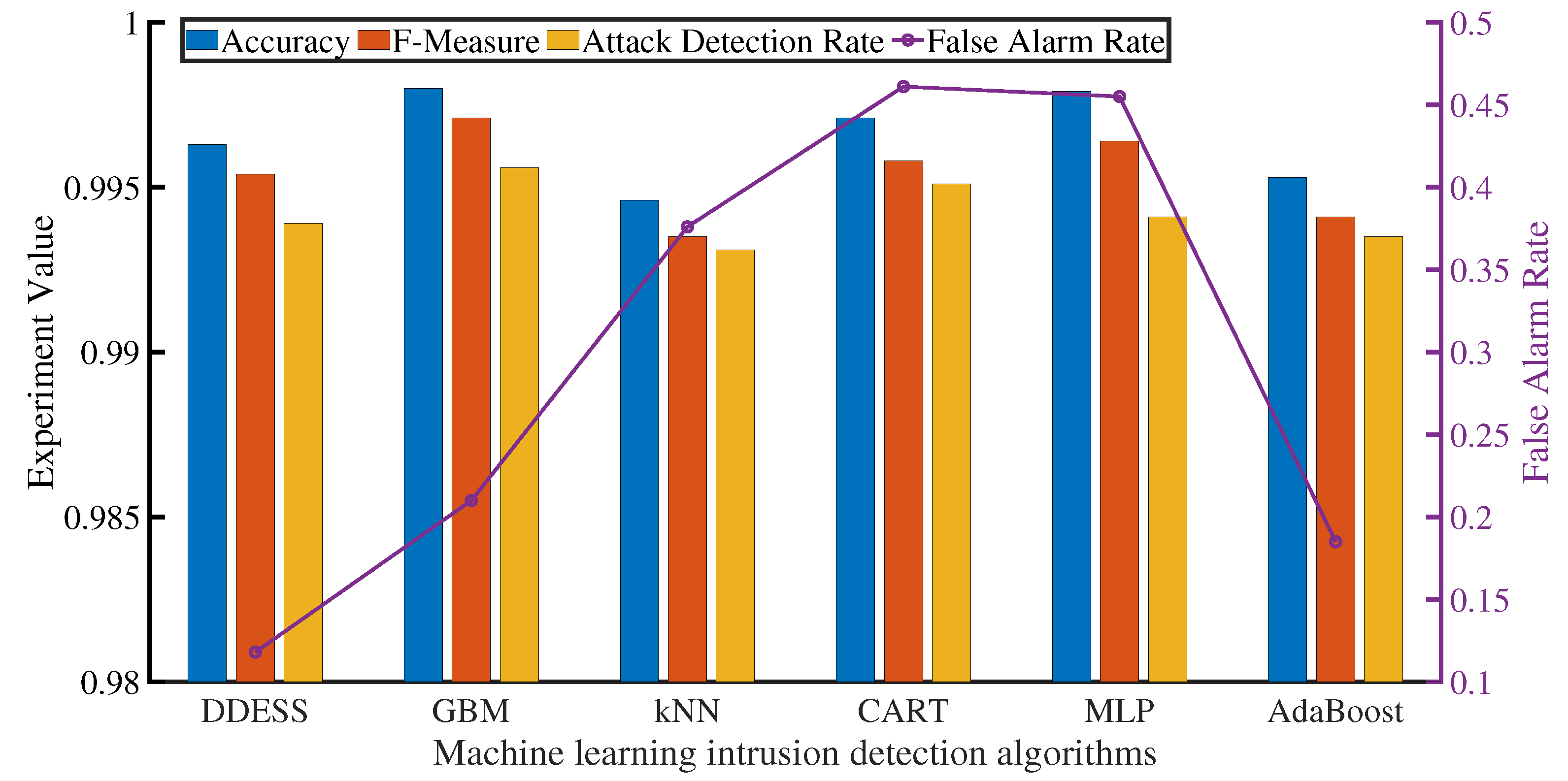
5.1. Overall Performance Evaluation
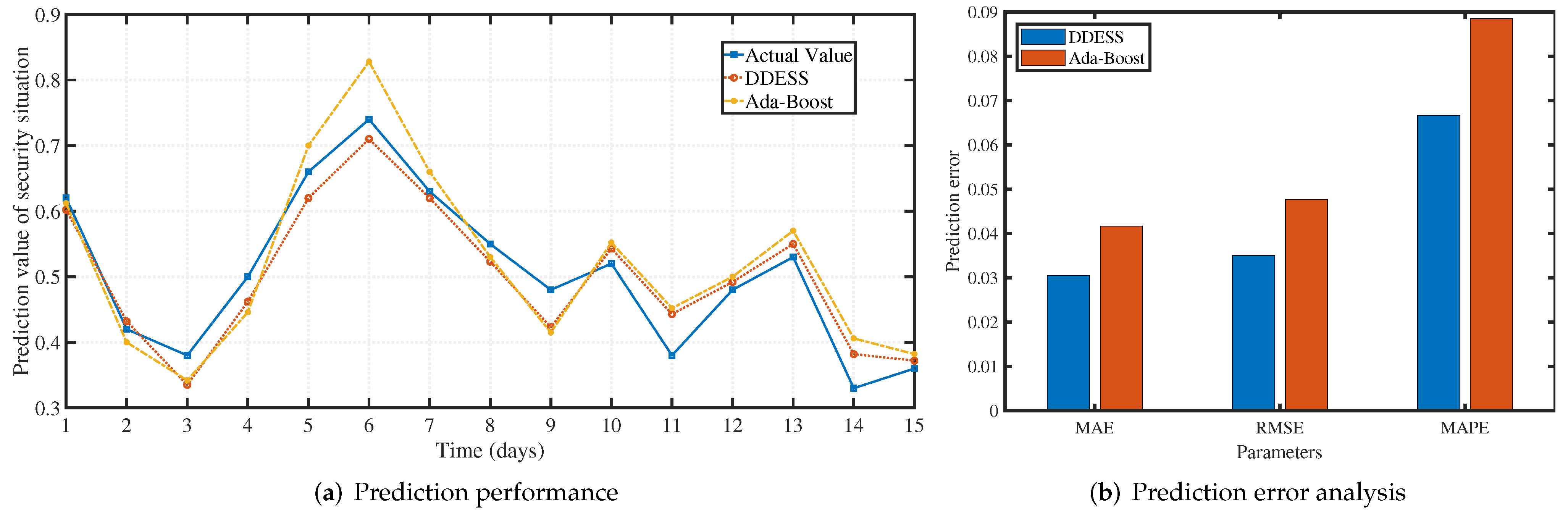
5.2. Performance of Dynamic Defense
5.3. Competition and Trial
6. Conclusions and Future Work
Author Contributions
Funding
Institutional Review Board Statement
Informed Consent Statement
Data Availability Statement
Conflicts of Interest
Abbreviations
| DDESS | Double Defense strategy with Endogenous Safety and Security |
| NDN | Named Data Networking |
| MIN | Multi-Identifier Network |
| MIS | Multi-Identifier System |
| MIR | Multi-Identifier Router |
| PoV | Proof of Vote |
| DAA | Direct Anonymous Attestation |
| TCM | Trusted Computing Module |
| ACC | Accuracy |
| ADR | Attack Detection Rate |
| FAR | False Alarm Rate |
References
- Blumenthal, M.S.; Clark, D.D. Rethinking the design of the internet: The end-to-end arguments vs. the brave new world. ACM Trans. Internet Technol. 2001, 1, 70–109. [Google Scholar] [CrossRef]
- Kouicem, D.E.; Bouabdallah, A.; Lakhlef, H. Internet of things security: A top-down survey. Comput. Netw. 2018, 141, 199–221. [Google Scholar] [CrossRef] [Green Version]
- Contreras-Castillo, J.; Zeadally, S.; Guerrero-Ibañez, J.A. Internet of vehicles: Architecture, protocols, and security. IEEE Internet Things J. 2017, 5, 3701–3709. [Google Scholar] [CrossRef]
- Park, S.M.; Kim, Y.G. A Metaverse: Taxonomy, components, applications, and open challenges. IEEE Access 2022, 10, 4209–4251. [Google Scholar] [CrossRef]
- Wu, J. Cyberspace Endogenous Safety and Security: Mimic Defense and Generalized Robust Control; Science Press: Beijing, China, 2020. [Google Scholar]
- Forrest, S.; Hofmeyr, S.A.; Somayaji, A. Computer immunology. Commun. ACM 1997, 40, 88–96. [Google Scholar] [CrossRef]
- Dasgupta, D. Advances in artificial immune systems. IEEE Comput. Intell. Mag. 2006, 1, 40–49. [Google Scholar] [CrossRef]
- Yu, Q.; Ren, J.; Zhang, J.; Liu, S.; Fu, Y.; Li, Y.; Ma, L.; Jing, J.; Zhang, W. An Immunology-Inspired Network Security Architecture. IEEE Wirel. Commun. 2020, 27, 168–173. [Google Scholar] [CrossRef]
- Li, H.; Yang, X. Architecture of Sovereignty Network. In Co-Governed Sovereignty Network: Legal Basis and Its Prototype & Applications with MIN Architecture; Springer: Singapore, 2021; pp. 61–94. [Google Scholar] [CrossRef]
- Rose, S.W.; Borchert, O.; Mitchell, S.; Connelly, S. Zero Trust Architecture, Special Publication (NIST SP). 2020. Available online: https://www.nist.gov/publications/zero-trust-architecture (accessed on 29 November 2021).
- Wang, Y.; Li, H.; Huang, T.; Zhang, X.; Bai, Y. Scalable Identifier System for Industrial Internet Based on Multi-Identifier Network Architecture. IEEE Internet Things J. 2021, 1. [Google Scholar] [CrossRef]
- Li, K.; Li, H.; Hou, H.; Li, K.; Chen, Y. Proof of vote: A high-performance consensus protocol based on vote mechanism & consortium blockchain. In Proceedings of the IEEE HPCC, Bangkok, Thailand, 18–20 December 2017. [Google Scholar]
- Shen, C. To Create a Positive Cyberspace by Safeguarding Network Security with Active Immune Trusted Computing 3.0. J. Inf. Secur. Res. 2018, 4, 282–302. [Google Scholar]
- Brickell, E.; Camenisch, J.; Chen, L. Direct anonymous attestation. In Proceedings of the 11th ACM conference on Computer and communications security, Washington, DC, USA, 25–28 October 2004; pp. 132–145. [Google Scholar]
- Kaur, T.; Malhotra, V.; Singh, D. Comparison of network security tools-firewall, intrusion detection system and Honeypot. Int. J. Enhanc. Res. Sci. Technol. Eng. 2014, 3, 200–204. [Google Scholar]
- Song, X. Firewall technology in computer network security in 5G environment. J. Phys. Conf. Ser. 2020, 1544, 012090. [Google Scholar] [CrossRef]
- Aman, M.N.; Basheer, M.H.; Sikdar, B. Data provenance for IoT with light weight authentication and privacy preservation. IEEE Internet Things J. 2019, 6, 10441–10457. [Google Scholar] [CrossRef]
- Sandhu, R.S.; Samarati, P. Access control: Principle and practice. IEEE Commun. Mag. 1994, 32, 40–48. [Google Scholar] [CrossRef]
- Tidjon, L.N.; Frappier, M.; Mammar, A. Intrusion detection systems: A cross-domain overview. IEEE Commun. Surv. Tutor. 2019, 21, 3639–3681. [Google Scholar] [CrossRef]
- Williams, L.; McGraw, G.; Migues, S. Engineering security vulnerability prevention, detection, and response. IEEE Softw. 2018, 35, 76–80. [Google Scholar] [CrossRef]
- Kausar, F.; Aljumah, S.; Alzaydi, S.; Alroba, R. Traffic analysis attack for identifying users’ online activities. IT Prof. 2019, 21, 50–57. [Google Scholar] [CrossRef]
- Roger, M.; Goubault-Larrecq, J. Log auditing through model-checking. In Proceedings of the Proceedings of the 14th IEEE workshop on Computer Security Foundations, Cape Breton, NS, Canada, 11–13 June 2001; pp. 220–234. [Google Scholar]
- Sun, Y.; Tian, Z.; Li, M.; Su, S.; Du, X.; Guizani, M. Honeypot Identification in Softwarized Industrial Cyber–Physical Systems. IEEE Trans. Ind. Inform. 2020, 17, 5542–5551. [Google Scholar] [CrossRef]
- Fan, W.; Du, Z.; Fernández, D.; Villagrá, V.A. Enabling an anatomic view to investigate honeypot systems: A survey. IEEE Syst. J. 2017, 12, 3906–3919. [Google Scholar] [CrossRef]
- Shrivastava, R.K.; Bashir, B.; Hota, C. Attack detection and forensics using honeypot in IoT environment. In Proceedings of the International Conference on Distributed Computing and Internet Technology, Bhubaneswar, India, 10–13 January 2019; pp. 402–409. [Google Scholar]
- Zhuang, R.; DeLoach, S.A.; Ou, X. Towards a theory of moving target defense. In Proceedings of the ACM Workshop on Moving Target Defense, Scottsdale, AZ, USA, 7 November 2014; pp. 31–40. [Google Scholar]
- Wu, J. Cyberspace Mimic Defense; Springer: Cham, Switzerland, 2020. [Google Scholar]
- Wang, C.; Lu, Z. Cyber deception: Overview and the road ahead. IEEE Secur. Priv. 2018, 16, 80–85. [Google Scholar] [CrossRef]
- Makarfi, A.U.; Rabie, K.M.; Kaiwartya, O.; Adhikari, K.; Nauryzbayev, G.; Li, X.; Kharel, R. Toward Physical-Layer Security for Internet of Vehicles: Interference-Aware Modeling. IEEE Internet Things J. 2020, 8, 443–457. [Google Scholar] [CrossRef]
- Kumar, S.; Singh, K.; Kumar, S.; Kaiwartya, O.; Cao, Y.; Zhou, H. Delimitated anti jammer scheme for Internet of vehicle: Machine learning based security approach. IEEE Access 2019, 7, 113311–113323. [Google Scholar] [CrossRef]
- Wu, J. Thoughts on the development of novel network technology. Sci. China Inf. Sci. 2018, 61, 101301. [Google Scholar] [CrossRef] [Green Version]
- Zhang, L.; Afanasyev, A.; Burke, J.; Jacobson, V.; Claffy, K.; Crowley, P.; Papadopoulos, C.; Wang, L.; Zhang, B. Named data networking. ACM SIGCOMM Comp. Commun. Rev. 2014, 44, 66–73. [Google Scholar] [CrossRef]
- Li, H.; Yang, X. Key Technologies of Sovereignty Network. In Co-Governed Sovereignty Network; Springer: Cham, Switzerland, 2021; pp. 95–182. [Google Scholar]
- López, J.; Maña, A.; Muñoz, A. A secure and auto-configurable environment for mobile agents in ubiquitous computing scenarios. In Proceedings of the International Conference on Ubiquitous Intelligence and Computing, Wuhan, China, 3–6 September 2006; pp. 977–987. [Google Scholar]
- Gürgens, S.; Rudolph, C.; Scheuermann, D.; Atts, M.; Plaga, R. Security evaluation of scenarios based on the TCG’s TPM specification. In Proceedings of the European Symposium on Research in Computer Security, Oslo, Norway, 11–13 September 2007; pp. 438–453. [Google Scholar]
- Camenisch, J.; Lysyanskaya, A. A signature scheme with efficient protocols. In Proceedings of the International Conference on Security in Communication Networks, Amalfi, Italy, 11–13 September 2002; pp. 268–289. [Google Scholar]
- Endsley, M.R. Design and evaluation for situation awareness enhancement. In Proceedings of the Human Factors Society Annual Meeting, Anaheim, CA, USA, 24 October 1988; Volume 32, pp. 97–101. [Google Scholar]
- Bass, T. Intrusion detection systems and multisensor data fusion. Commun. ACM 2000, 43, 99–105. [Google Scholar] [CrossRef]
- LeCun, Y.; Bengio, Y.; Hinton, G. Deep learning. Nature 2015, 521, 436–444. [Google Scholar] [CrossRef]
- Ioffe, S.; Szegedy, C. Batch normalization: Accelerating deep network training by reducing internal covariate shift. In Proceedings of the International Conference on Machine Learning, Lille, France, 6–11 July 2015; pp. 448–456. [Google Scholar]
- Lin, M.; Chen, Q.; Yan, S. Network in network. arXiv 2013, arXiv:1312.4400. [Google Scholar]
- Tavallaee, M.; Bagheri, E.; Lu, W.; Ghorbani, A.A. A detailed analysis of the KDD CUP 99 data set. In Proceedings of the 2009 IEEE Symposium on Computational Intelligence for Security and Defense Applications, Ottawa, ON, Canada, 8–10 July 2009; pp. 1–6. [Google Scholar]
- Tama, B.A.; Rhee, K.H. An in-depth experimental study of anomaly detection using gradient boosted machine. Neural Comput. Appl. 2019, 31, 955–965. [Google Scholar] [CrossRef]
- Li, W.; Yi, P.; Wu, Y.; Pan, L.; Li, J. A new intrusion detection system based on KNN classification algorithm in wireless sensor network. J. Electr. Comput. Eng. 2014, 2014, 240217. [Google Scholar] [CrossRef]
- Soylu, T.; Erdem, O.; Carus, A.; Güner, E.S. Simple CART based real-time traffic classification engine on FPGAs. In Proceedings of the 2017 International Conference on ReConFigurable Computing and FPGAs (ReConFig) (ReConFig), Cancun, Mexico, 4–6 December 2017; pp. 1–8. [Google Scholar]
- Ahmad, I.; Abdullah, A.; Alghamdi, A.; Alnfajan, K.; Hussain, M. Intrusion detection using feature subset selection based on MLP. Sci. Res. Essays 2011, 6, 6804–6810. [Google Scholar]
- Hu, W.; Hu, W. Network-based intrusion detection using Adaboost algorithm. In Proceedings of the The 2005 IEEE/WIC/ACM International Conference on Web Intelligence (WI’05), Compiegne, France, 19–22 September 2005; pp. 712–717. [Google Scholar]
- Fawcett, T. An introduction to ROC analysis. Pattern Recognit. Lett. 2006, 27, 861–874. [Google Scholar] [CrossRef]
- Zhao, Y.; Cheng, G.; Duan, Y.; Gu, Z.; Zhou, Y.; Tang, L. Secure IoT edge: Threat situation awareness based on network traffic. Comput. Netw. 2021, 201, 108525. [Google Scholar] [CrossRef]
- Laboratories, P.M. Mimic Defense International Elite Challenge. 2021. Available online: http://www.pmlabs.com.cn/plus/view.php?aid=1464 (accessed on 29 November 2021).
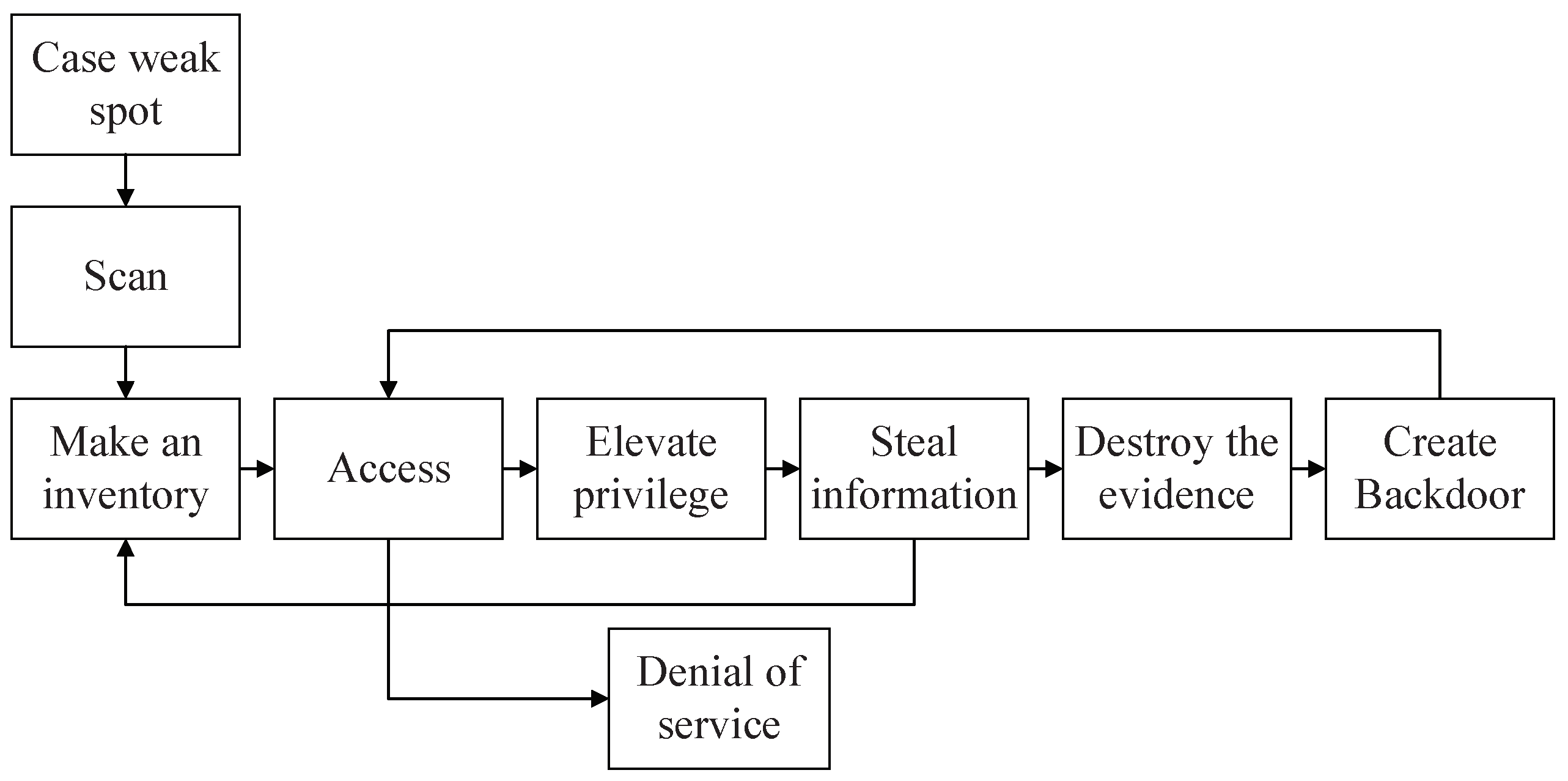

| Attack Phase | Description | IP-IP | IP-MIN | |
|---|---|---|---|---|
| Target detection | Host discovery | ✓ | ✗ | |
| ping scan | ✓ | ✗ | ||
| OS recognition | System fingerprints obtained | Host non-survival | ||
| Port scan | All ports probed | The host is alive, but no port detected | ||
| Attack injection | Trojan | TCP trojan | ✓ | ✗ |
| UDP trojan | ✓ | ✗ | ||
| ICMP trojan | ✓ | ✗ | ||
| One-sentence shell | ✓ | ✗ | ||
| Action | ARP Attack | Information sniffing | Target cannot be sniffed | |
| Network disconnection attack | Target not affected |
Publisher’s Note: MDPI stays neutral with regard to jurisdictional claims in published maps and institutional affiliations. |
© 2022 by the authors. Licensee MDPI, Basel, Switzerland. This article is an open access article distributed under the terms and conditions of the Creative Commons Attribution (CC BY) license (https://creativecommons.org/licenses/by/4.0/).
Share and Cite
Wang, Y.; Smahi, A.; Zhang, H.; Li, H. Towards Double Defense Network Security Based on Multi-Identifier Network Architecture. Sensors 2022, 22, 747. https://doi.org/10.3390/s22030747
Wang Y, Smahi A, Zhang H, Li H. Towards Double Defense Network Security Based on Multi-Identifier Network Architecture. Sensors. 2022; 22(3):747. https://doi.org/10.3390/s22030747
Chicago/Turabian StyleWang, Yunmin, Abla Smahi, Huayu Zhang, and Hui Li. 2022. "Towards Double Defense Network Security Based on Multi-Identifier Network Architecture" Sensors 22, no. 3: 747. https://doi.org/10.3390/s22030747
APA StyleWang, Y., Smahi, A., Zhang, H., & Li, H. (2022). Towards Double Defense Network Security Based on Multi-Identifier Network Architecture. Sensors, 22(3), 747. https://doi.org/10.3390/s22030747






