BBNSF: Blockchain-Based Novel Secure Framework Using RP2-RSA and ASR-ANN Technique for IoT Enabled Healthcare Systems
Abstract
1. Introduction
2. Background and Related Work
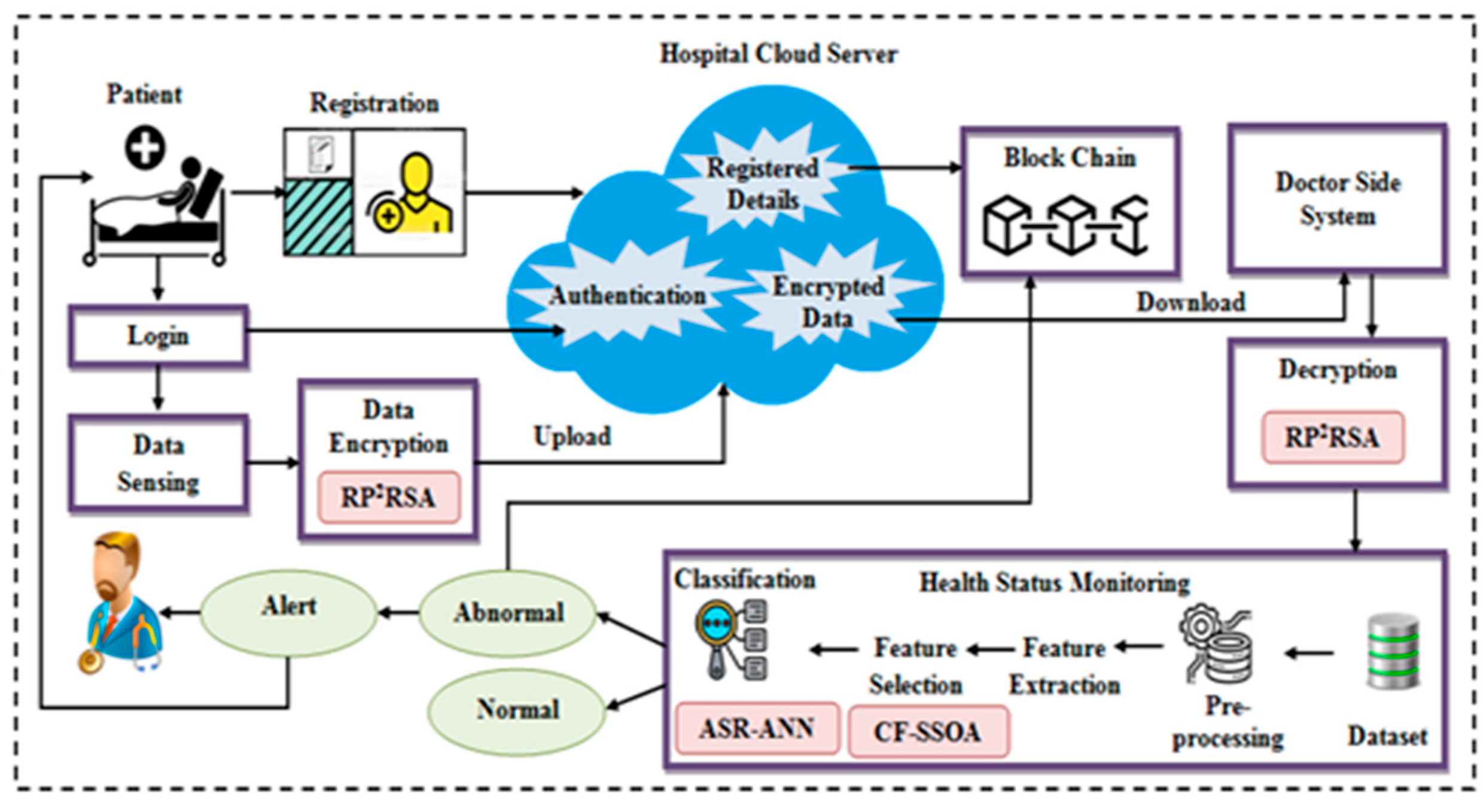
3. Proposed Methodology
3.1. Registration Phase
- ❖
- Let β be the patient unique ID and the timestamp of the patient at the registration time is represented as T. is the string of bytes for which checksum is to be calculated. The patient ID and timestamp are combined together to convert them into hash codes. It is shown below.
- ❖
- Next, the hash code is generated for the combined values using the Adler-32 hashing technique which is mathematically expressed below. Here, 65521 represents the largest prime number smaller than 216.where n denotes the length of α, Here, H is the sum of individual values of G.
- ❖
- The hash code can be formed as follows,
3.2. Blockchain
3.3. Login
3.4. User Authentication
3.5. Data Encryption Using RP2-RSA
3.5.1. Key Generation
- ❖
- At first, ‘2′ large prime numbers are randomly chosen and gauge
- ❖
- Next, the Euler totient function is gauged as,
- ❖
- Choose a random integer centered on the subsequent condition, and and calculate,wherein signifies the multiplication inverse element of that fulfills the Equation (7),Consequently, implies the public key and signifies the private key.
- ❖
- Next, these public keys are joined with the private keys and reversed to make the secret key for ameliorated security. The secret key is generated utilizing the subsequent equation,Additionally, this secret key is employed in the encryption as well as decryption of the information.
3.5.2. Encryption
3.5.3. Decryption
3.6. Health Status Prediction
3.6.1. Pre-Processing
3.6.2. Feature Extraction
3.6.3. Feature Selection Using CF-SSOA
| Algorithm 1: Pseudocode for the proposed CF-SSOA |
| Input: Extracted features Output: Selected feature Begin Generate initial swarm population Initialize the food source For Compute the fitness of each Choose the leader and followers While Update Calculate the correlation factor If Renew the position of leader Else Keep posted the follower’s position End if Improve the salps based on upper and lower bounds End while End for Return End |
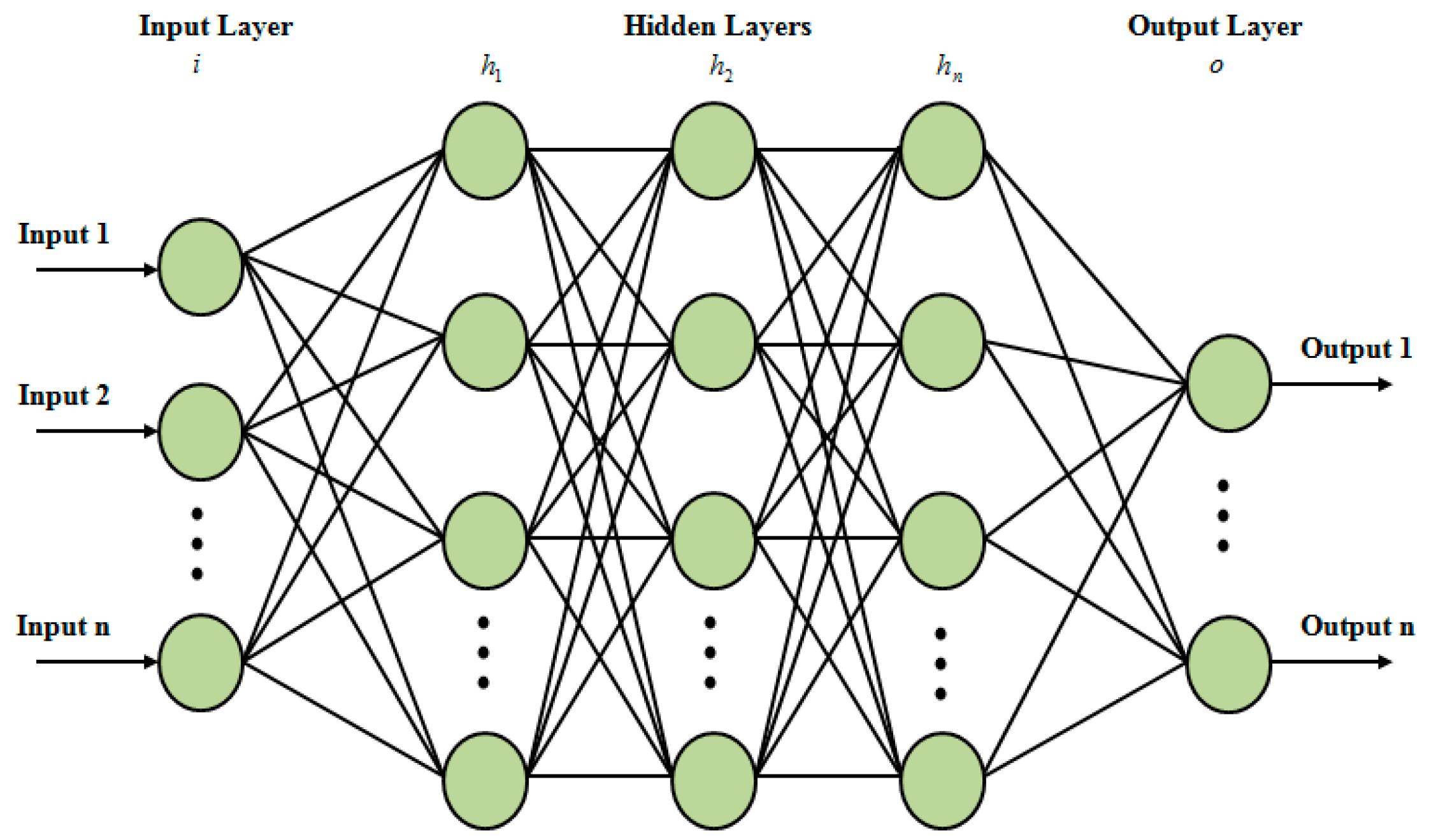
3.6.4. Classification via ANN
4. Result and Discussion
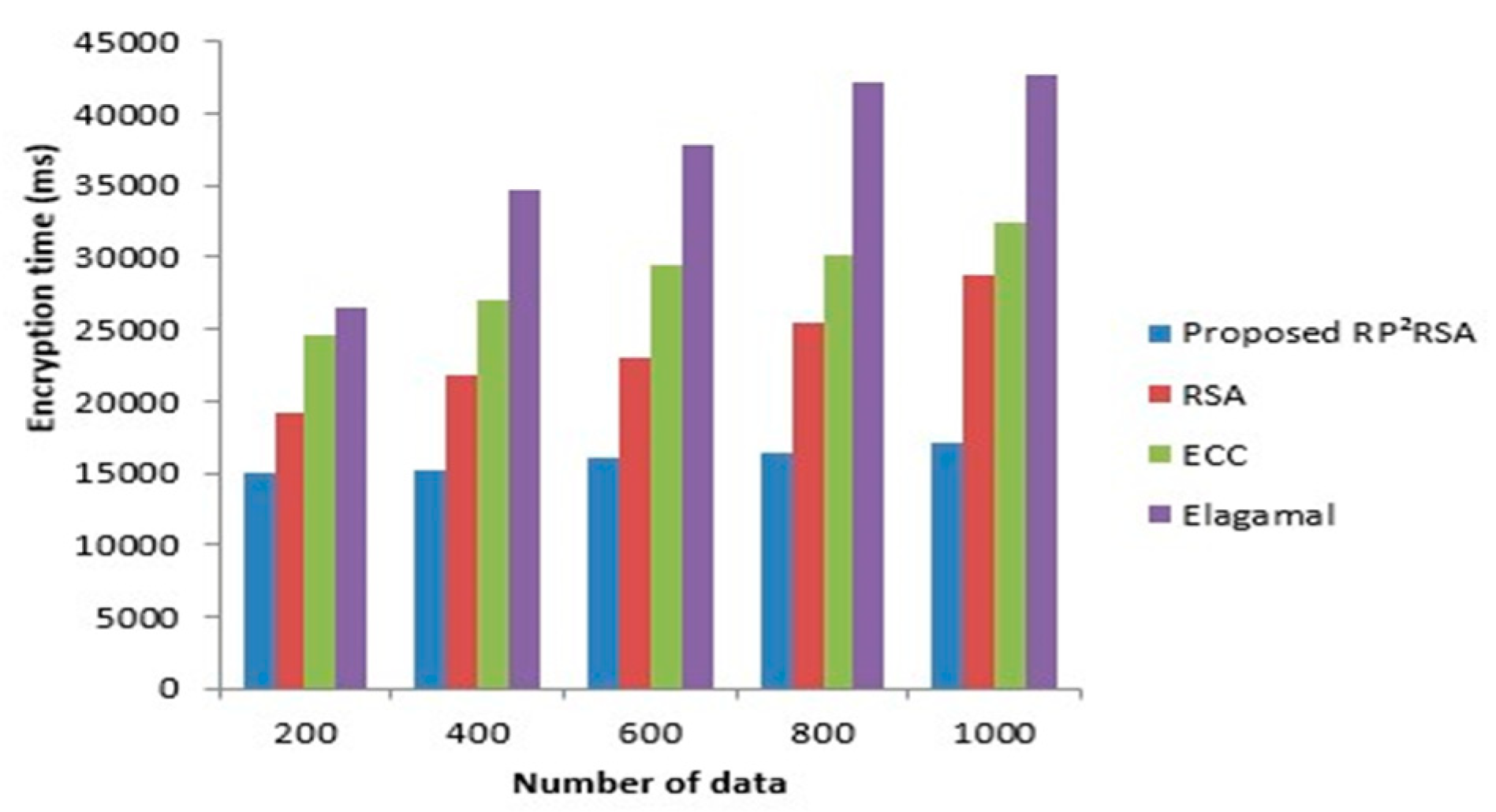
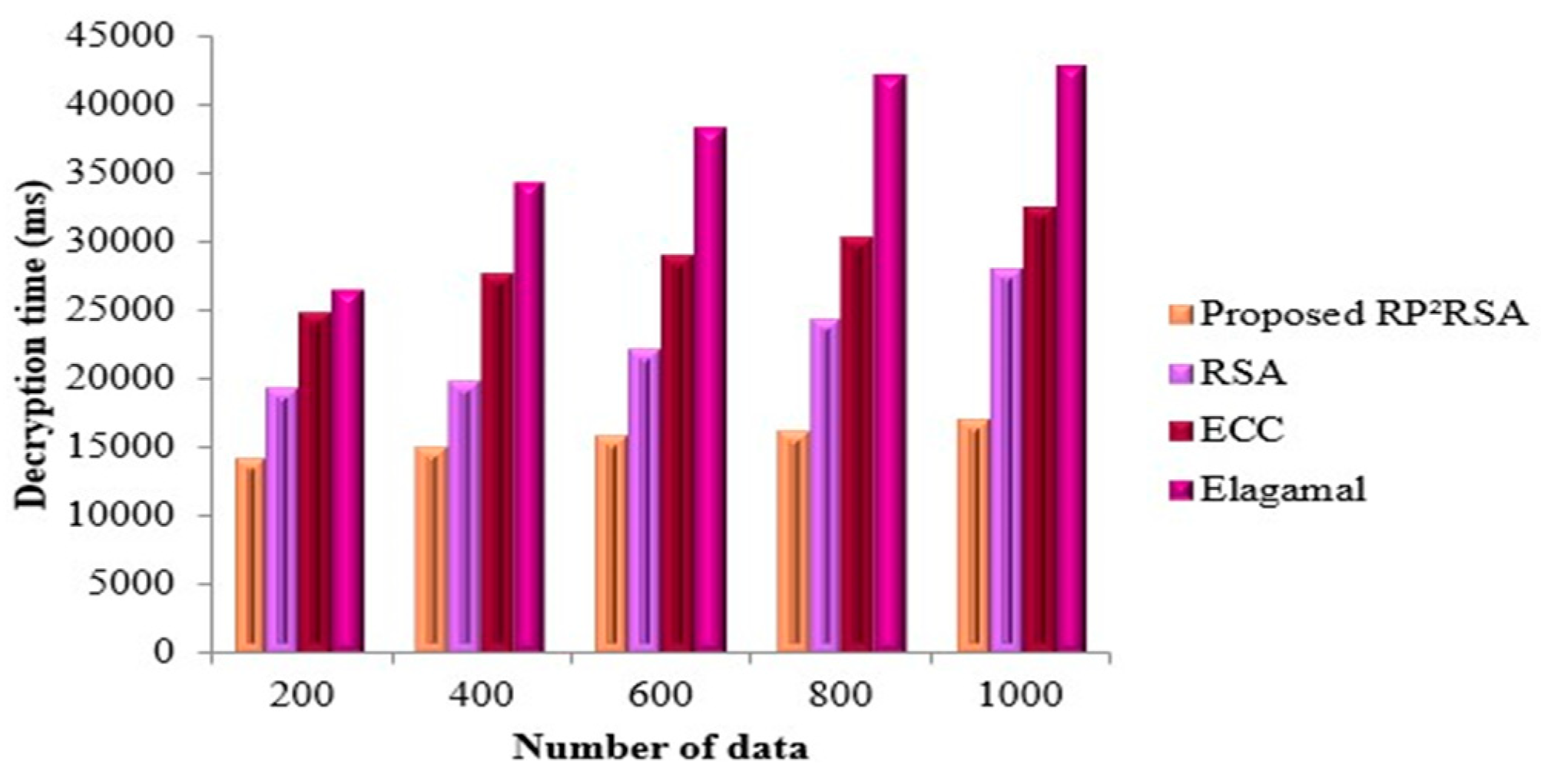
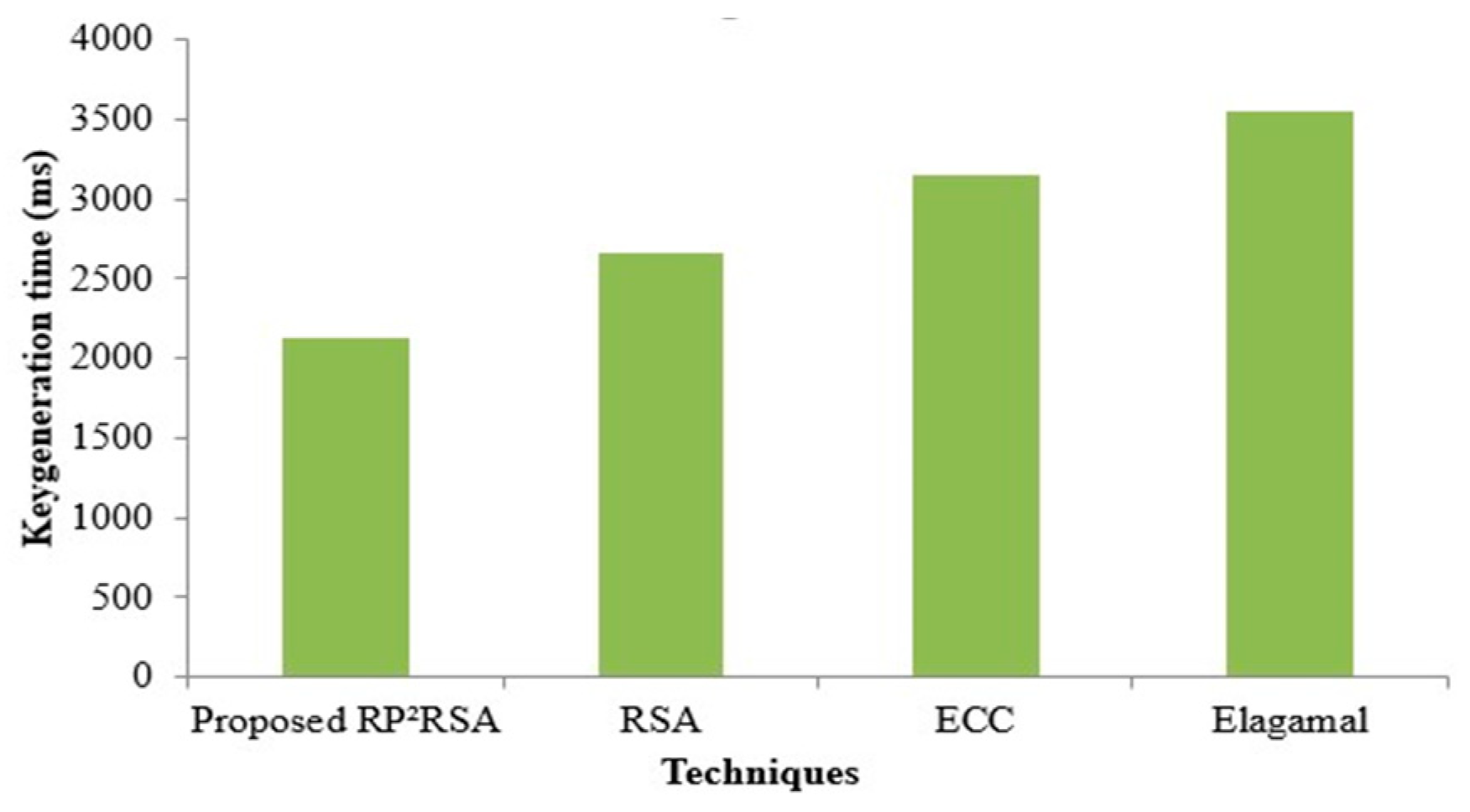
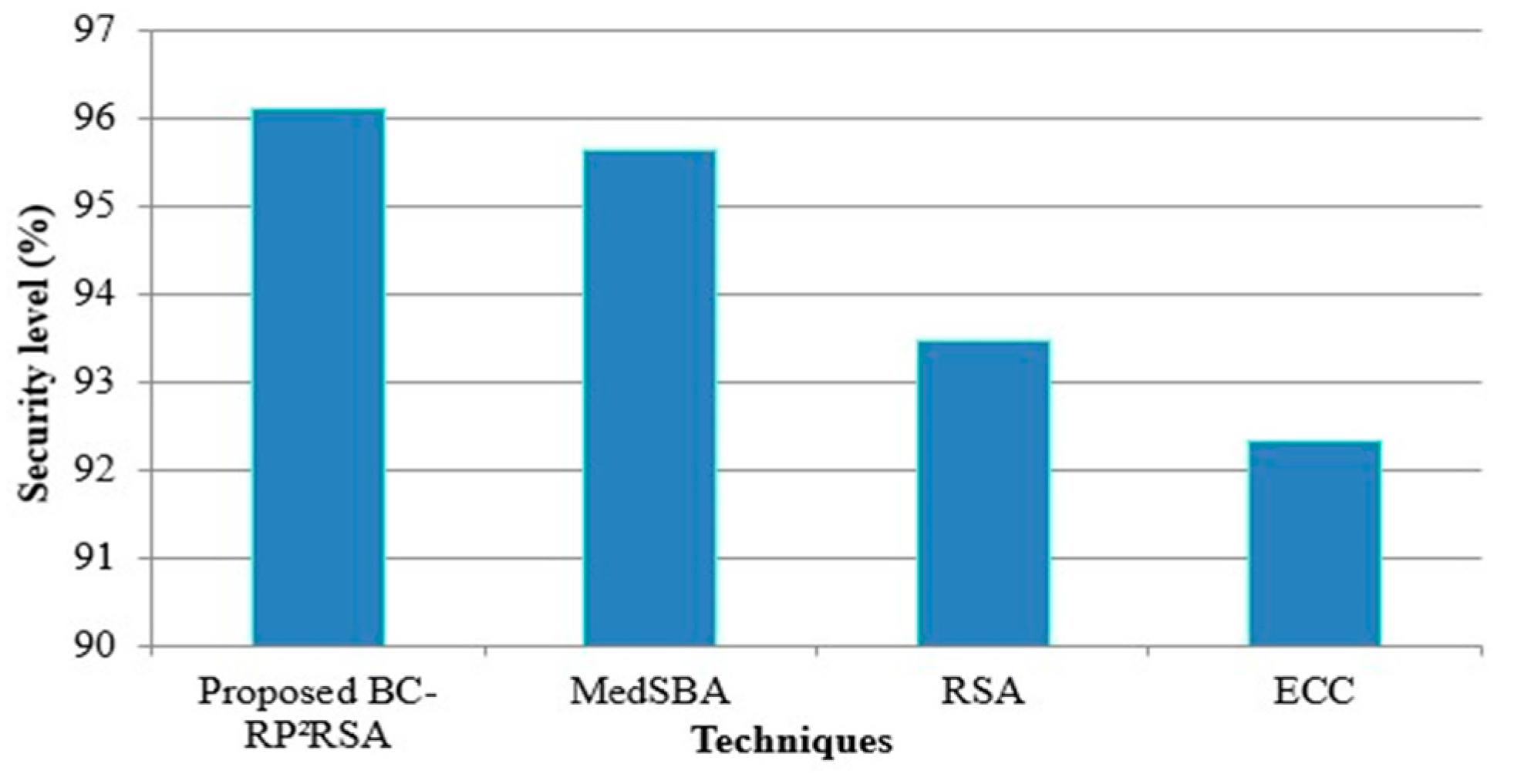
4.1. Performance Evaluation of RP2RSA
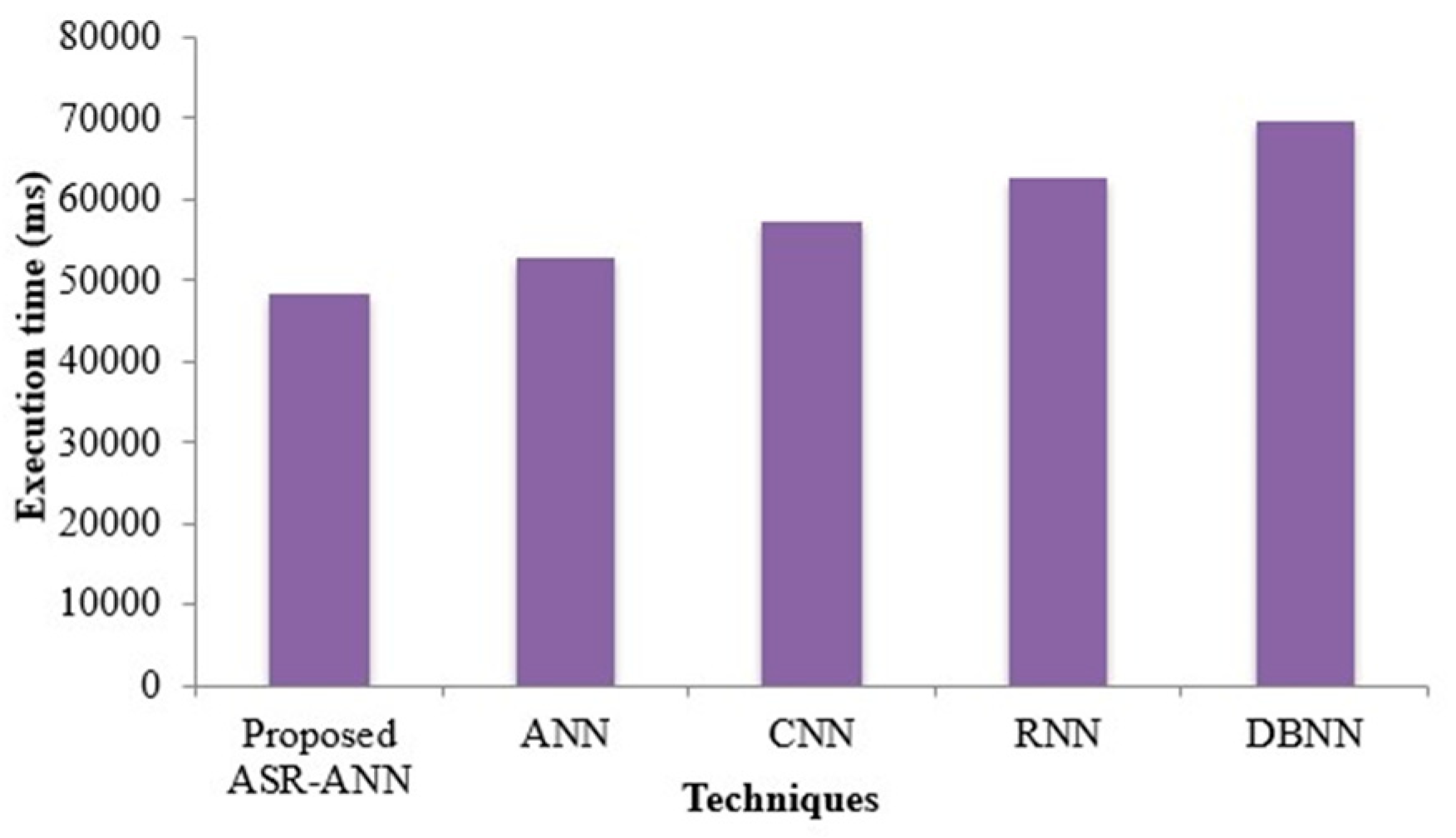
4.2. Superiority Measure of the Proposed Classifier
5. Conclusions
Author Contributions
Funding
Institutional Review Board Statement
Informed Consent Statement
Acknowledgments
Conflicts of Interest
Abbreviations
| RP2-RSA. | Reversed public-private keys combined Rivest–Shamir–Adleman |
| CF-SSOA | Correlation factor induced salp swarm optimization algorithm |
| ASR-ANN | Adapted SignReLU activation function centered artificial neural network |
| IoMT | Internet of Medical Things |
| BC | Blockchain |
| HS | Health Status |
| PID | Patient ID |
| DID | Device ID |
| ANN | Artificial neural network |
| CNN | Convolutional neural network |
| RNN | Recurrent neural network |
| DBNN | Deep belief neural network |
References
- Gatouillat, A.; Badr, Y.; Massot, B.; Sejdić, E. Internet of medical things a review of recent contributions dealing with cyber-physical systems in medicine. IEEE Internet Things J. 2018, 5, 3810–3822. [Google Scholar] [CrossRef]
- Tahir, S.; Bakhsh, S.T.; Abulkhair, M.; Alassafi, M.O. An energy-efficient fog-to-cloud internet of medical things architecture. Int. J. Distrib. Sens. Netw. 2019, 15, 1550147719851977. [Google Scholar] [CrossRef]
- Kumar, M.; Raju, K.S.; Kumar, D.; Goyal, N.; Verma, S.; Singh, A. An efficient framework using visual recognition for IoT based smart city surveillance. Multimed. Tools Appl. 2021, 80, 31277–31295. [Google Scholar] [CrossRef] [PubMed]
- Yang, G.; Jan, M.A.; Rehman, A.U.; Babar, M.; Aimal, M.M.; Verma, S. Interoperability and Data Storage in Internet of Multimedia Things: Investigating Current Trends, Research Challenges and Future Directions. IEEE Access 2020, 8, 124382–124401. [Google Scholar] [CrossRef]
- Babbar, H.; Rani, S.; Masud, M.; Verma, S.; Anand, D.; Jhanjhi, N. Load balancing algorithm for migrating switches in software-defined vehicular networks. Comput. Mater. Contin. 2021, 67, 1301–1316. [Google Scholar] [CrossRef]
- Arora, M.; Verma, D.S.; Kavita, D. An efficient effort and cost estimation framework for Scrum based projects. Int. J. Eng. Technol. 2018, 7, 52–57. [Google Scholar] [CrossRef]
- Sharma, N.; Mangla, M.; Yadav, S.; Goyal, N.; Singh, A.; Verma, S.; Saber, T. A sequential ensemble model for photovoltaic power forecasting. Comput. Electr. Eng. 2021, 96, 107484. [Google Scholar] [CrossRef]
- Limaye, A.; Adegbija, T. HERMIT a benchmark suite for the internet of medical things. IEEE Internet Things J. 2018, 5, 4212–4222. [Google Scholar] [CrossRef]
- Awan, K.A.; Din, I.U.; Almogren, A.; Almajed, H.; Mohiuddin, I.; Guizani, M. NeuroTrust artificial neural network-based intelligent trust management mechanism for large-scale internet of medical things. IEEE Internet Things J. 2020, 8, 15672–15682. [Google Scholar] [CrossRef]
- Mohamed Shakeel, P.; Baskar, S.; Sarma Dhulipala, V.R.; Mishra, S.; Jaber, M.M. Maintaining security and privacy in health care system using learning based deep-q-networks. J. Med. Syst. 2018, 42, 186. [Google Scholar] [CrossRef]
- Ashfaq, Z.; Rafay, A.; Mumtaz, R.; Zaidi, S.M.H.; Saleem, H.; Zaidi, S.A.R.; Mumtaz, S.; Haque, A. A review of enabling technologies for internet of medical things (IOMT) ecosystem. Ain Shams Eng. J. 2022, 13, 101660. [Google Scholar] [CrossRef]
- Khan, S.; Akhunzada, A. A hybrid DL-driven intelligent SDN-enabled malware detection framework for Internet of Medical Things (IoMT). Comput. Commun. 2021, 170, 209–216. [Google Scholar] [CrossRef]
- Alsubaei, F.; Abuhussein, A.; Shiva, S. A Framework for Ranking IoMT Solutions Based on Measuring Security and Privacy, 1st ed.; Springer: Cham, Switzerland, 2019; pp. 205–224. ISBN 978-3-030-02685-1. [Google Scholar]
- Kumar, M.; Mukherjee, P.; Verma, K.; Verma, S.; Rawat, D.B. Improved Deep Convolutional Neural Network based Malicious Node Detection and Energy-Efficient Data Transmission in Wireless Sensor Networks. IEEE Trans. Netw. Sci. Eng. 2021, 9, 3098011. [Google Scholar] [CrossRef]
- Kumar, M.; Verma, S.; Kumar, A.; Ijaz, M.F.; Rawat, D.B. ANAF-IoMT: A Novel Architectural Framework for IoMT Enabled Smart Healthcare System by Enhancing Security Based on RECC-VC. IEEE Trans. Ind. Inform. 2022, 18, 8936–8943. [Google Scholar] [CrossRef]
- Abbasi, A.R.; Mahmoudi, M.R.; Avazzadeh, Z. Diagnosis and clustering of power transformer winding fault types by cross-correlation and clustering analysis of FRA results. IET Gener. Transm. Distrib. 2018, 12, 4301–4309. [Google Scholar] [CrossRef]
- Sun, Y.; Lo, F.P.W.; Lo, B. Security and privacy for the internet of medical things enabled healthcare systems a survey. IEEE Access 2019, 7, 183339–183355. [Google Scholar] [CrossRef]
- Mohan, D.; Alwin, L.; Neeraja, P.; Lawrence, K.D.; Pathari, V. A private ethereum blockchain implementation for secure data handling in internet of medical things. J. Reliab. Intell. Environ. 2021, 8, 379–396. [Google Scholar] [CrossRef]
- Wazid, M.; Das, A.K.; Rodrigues, J.J.; Shetty, S.; Park, Y. IoMT malware detection approaches analysis and research challenges. IEEE Access 2019, 2, 182459–182476. [Google Scholar] [CrossRef]
- Li, Z.; Verma, S.; Jin, M. Power Allocation in Massive MIMO-HWSN Based on the Water-Filling Algorithm. Wirel. Commun. Mob. Comput. 2021, 2021, 8719066. [Google Scholar] [CrossRef]
- Dogra, V. Banking news-events representation and classification with a novel hybrid model using DistilBERT and rule-based features. Turk. J. Comput. Math. Educ. (TURCOMAT) 2021, 12, 3039–3054. [Google Scholar]
- Eze, K.G.; Akujuobi, C.M.; Hunter, S.; Alam, S.; Musa, S.; Foreman, J. A Blockchain-based Security Architecture for the Internet of Things. WSEAS Trans. Inf. Sci. Appl. 2022, 19, 12–22. [Google Scholar] [CrossRef]
- Alshaikhli, M.; Elfouly, T.; Elharrouss, O.; Mohamed, A.; Ottakath, N. Evolution of Internet of Things from blockchain to IOTA: A survey. IEEE Access 2021, 10, 844–866. [Google Scholar] [CrossRef]
- Dehalwar, V.; Kolhe, M.L.; Deoli, S.; Jhariya, M.K. Blockchain-based trust management and authentication of devices in smart grid. Clean. Eng. Technol. 2022, 8, 100481. [Google Scholar] [CrossRef]
- Singh, A.; Nath, P.; Singhal, V.; Anand, D.; Verma, S.; Hong, T.P. A New Clinical Spectrum for the Assessment of Nonalcoholic Fatty Liver Disease Using Intelligent Methods. IEEE Access 2020, 8, 138470–138480. [Google Scholar] [CrossRef]
- Hongwei, L.; Shixin, S.; Haomiao, Y. Identity-based authentication protocol for grid. J. Syst. Eng. Electron. 2008, 19, 860–865. [Google Scholar] [CrossRef]
- Pradhan, N.R.; Singh, A.P.; Verma, S.; Kavita; Kaur, N.; Roy, D.S.; Shafi, J.; Wozniak, M.; Ijaz, M.F. A Novel Blockchain-Based Healthcare System Design and Performance Benchmarking on a Multi-Hosted Testbed. Sensors 2022, 22, 3449. [Google Scholar] [CrossRef]
- Fotopoulos, F.; Malamas, V.; Dasaklis, T.K.; Kotzanikolaou, P.; Douligeris, C. A blockchain-enabled architecture for IoMT device authentication. In Proceedings of the IEEE Eurasia Conference on IOT, Communication and Engineering, Yunlin, Taiwan, 23–25 October 2020. [Google Scholar]
- Vaiyapuri, T.; Binbusayyis, A.; Varadarajan, V. Security, privacy and trust in IoMT enabled smart healthcare system a systematic review of current and future trend. Int. J. Adv. Comput. Sci. Appl. 2021, 12, 731–737. [Google Scholar] [CrossRef]
- Balogh, S.; Gallo, O.; Ploszek, R.; Špaček, P.; Zajac, P. IoT Security Challenges: Cloud and Blockchain, Postquantum Cryptography, and Evolutionary Techniques. Electronics 2021, 10, 2647. [Google Scholar] [CrossRef]
- Alfa, A.A.; Alhassan, J.K.; Olaniyi, O.M.; Olalere, M. Blockchain technology in IoT systems: Current trends, methodology, problems, applications, and future directions. J. Reliab. Intell. Environ. 2021, 7, 115–143. [Google Scholar] [CrossRef]
- Dwivedi, R.; Mehrotra, D.; Chandra, S. Potential of Internet of Medical Things (IoMT) applications in building a smart healthcare system: A systematic review. J. Oral Biol. Craniofac. Res. 2021, 12, 302–318. [Google Scholar] [CrossRef]
- Kumar, R.; Tripathi, R. Towards design and implementation of security and privacy framework for internet of medical things (IoMT) by leveraging blockchain and IPFS technolog. J. Supercomput. 2021, 77, 7916–7955. [Google Scholar] [CrossRef]
- Akhbarifar, S.; Javadi, H.H.S.; Rahmani, A.M.; Hosseinzadeh, M. A secure remote health monitoring model for early disease diagnosis in cloud-based IoT environment. Pers. Ubiquitous Comput. 2020, 24, 1–17. [Google Scholar] [CrossRef] [PubMed]
- Chandrakar, P.; Sinha, S.; Ali, R. Cloud-based authenticated protocol for healthcare monitoring system. J. Ambient. Intell. Humaniz. Comput. 2019, 11, 3431–3447. [Google Scholar] [CrossRef]
- Griggs, K.N.; Ossipova, O.; Kohlios, C.P.; Baccarini, A.N.; Howson, E.A.; Hayajneh, T. Healthcare blockchain system using smart contracts for secure automated remote patient monitoring. J. Med. Syst. 2018, 42, 130. [Google Scholar] [CrossRef] [PubMed]
- SeongHan, S.; Kobara, K.; Chuang, C.C.; Huang, W. A security framework for MQTT. In Proceedings of the 2016 IEEE Conference on Communications and Network Security (CNS), Philadelphia, PA, USA, 17–19 October 2016; IEEE: Piscataway, NJ, USA, 2016; pp. 43–436. [Google Scholar]
- Mohsin, M.; Sardar, M.U.; Hasan, O.; Anwar, Z. IoTRiskAnalyzer: A probabilistic model checking based framework for formal risk analytics of the Internet of Things. IEEE Access 2017, 5, 5494–5505. [Google Scholar] [CrossRef]
- Pournaghi, S.M.; Bayat, M.; Farjami, Y. MedSBA a novel and secure scheme to share medical data based on blockchain technology and attribute-based encryption. J. Ambient. Intell. Humaniz. Comput. 2020, 11, 4613–4641. [Google Scholar] [CrossRef]

| Techniques | Sensitivity (%) | Specificity (%) | Recall (%) |
|---|---|---|---|
| Proposed ASR-ANN | 96.146 | 95.959 | 96.098 |
| ANN | 95.531 | 95.089 | 95.595 |
| CNN | 94.982 | 94.375 | 94.121 |
| RNN | 94.019 | 93.602 | 93.843 |
| DBNN | 93.158 | 92.428 | 92.204 |
| Techniques/Performance Metric | Memory Usage (kb) |
|---|---|
| Proposed ASR-ANN | 165,432 |
| ANN | 198,791 |
| CNN | 213,490 |
| RNN | 246,701 |
| DBNN | 278,932 |
Publisher’s Note: MDPI stays neutral with regard to jurisdictional claims in published maps and institutional affiliations. |
© 2022 by the authors. Licensee MDPI, Basel, Switzerland. This article is an open access article distributed under the terms and conditions of the Creative Commons Attribution (CC BY) license (https://creativecommons.org/licenses/by/4.0/).
Share and Cite
Kumar, M.; Mukherjee, P.; Verma, S.; Kavita; Kaur, M.; Singh, S.; Kobielnik, M.; Woźniak, M.; Shafi, J.; Ijaz, M.F. BBNSF: Blockchain-Based Novel Secure Framework Using RP2-RSA and ASR-ANN Technique for IoT Enabled Healthcare Systems. Sensors 2022, 22, 9448. https://doi.org/10.3390/s22239448
Kumar M, Mukherjee P, Verma S, Kavita, Kaur M, Singh S, Kobielnik M, Woźniak M, Shafi J, Ijaz MF. BBNSF: Blockchain-Based Novel Secure Framework Using RP2-RSA and ASR-ANN Technique for IoT Enabled Healthcare Systems. Sensors. 2022; 22(23):9448. https://doi.org/10.3390/s22239448
Chicago/Turabian StyleKumar, Mohit, Priya Mukherjee, Sahil Verma, Kavita, Maninder Kaur, S. Singh, Martyna Kobielnik, Marcin Woźniak, Jana Shafi, and Muhammad Fazal Ijaz. 2022. "BBNSF: Blockchain-Based Novel Secure Framework Using RP2-RSA and ASR-ANN Technique for IoT Enabled Healthcare Systems" Sensors 22, no. 23: 9448. https://doi.org/10.3390/s22239448
APA StyleKumar, M., Mukherjee, P., Verma, S., Kavita, Kaur, M., Singh, S., Kobielnik, M., Woźniak, M., Shafi, J., & Ijaz, M. F. (2022). BBNSF: Blockchain-Based Novel Secure Framework Using RP2-RSA and ASR-ANN Technique for IoT Enabled Healthcare Systems. Sensors, 22(23), 9448. https://doi.org/10.3390/s22239448






