Securing Session Initiation Protocol
Abstract
1. Introduction
- For the first time, we provide an informal security analysis for the SRP protocol.
- Based on the SRP protocol, we introduce a new authentication scheme that overcomes vulnerabilities and weaknesses discovered in SRP.
- A new protocol is introduced to provide confidentiality and integrity services for SIP.
- The security of the proposed protocols is formally and informally analyzed.
- The proposed protocols are compared with many related protocols in terms of security and performance.
2. Related Work
2.1. Standard-Based Solutions
- (1)
- HTTP Digest
- (2)
- Transport Layer Security
- (3)
- S/MIME
- (4)
- IPSec
- Since IPSec is implemented at the operating system level or kernel layer, many SIP clients do not support it. Thus, IPSec can be utilized to protect signaling traffic between SIP servers but not between servers and clients.
- For applications working on top of IPSec, such as SIP, it is difficult to detect whether IPSec has failed to be set up. As a result, there are advantages for security mechanisms working at layers above the IP layer.
- Deploying IPSec in VoIP systems requires more effort because of its complexity and infrastructure requirements compared to other protocols.
- It does not scale well for large, distributed networks and distributed applications.
2.2. Research-Based Solutions
3. Background
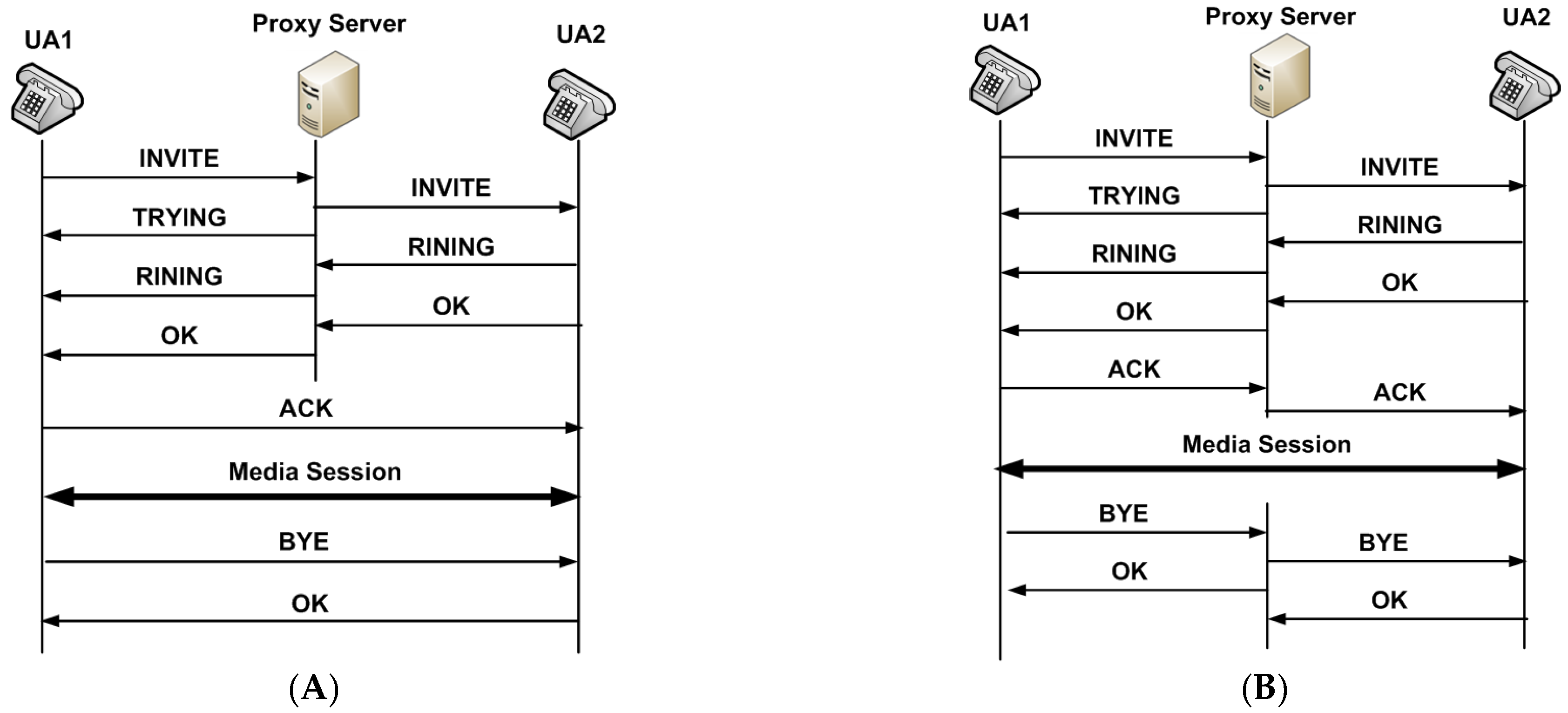
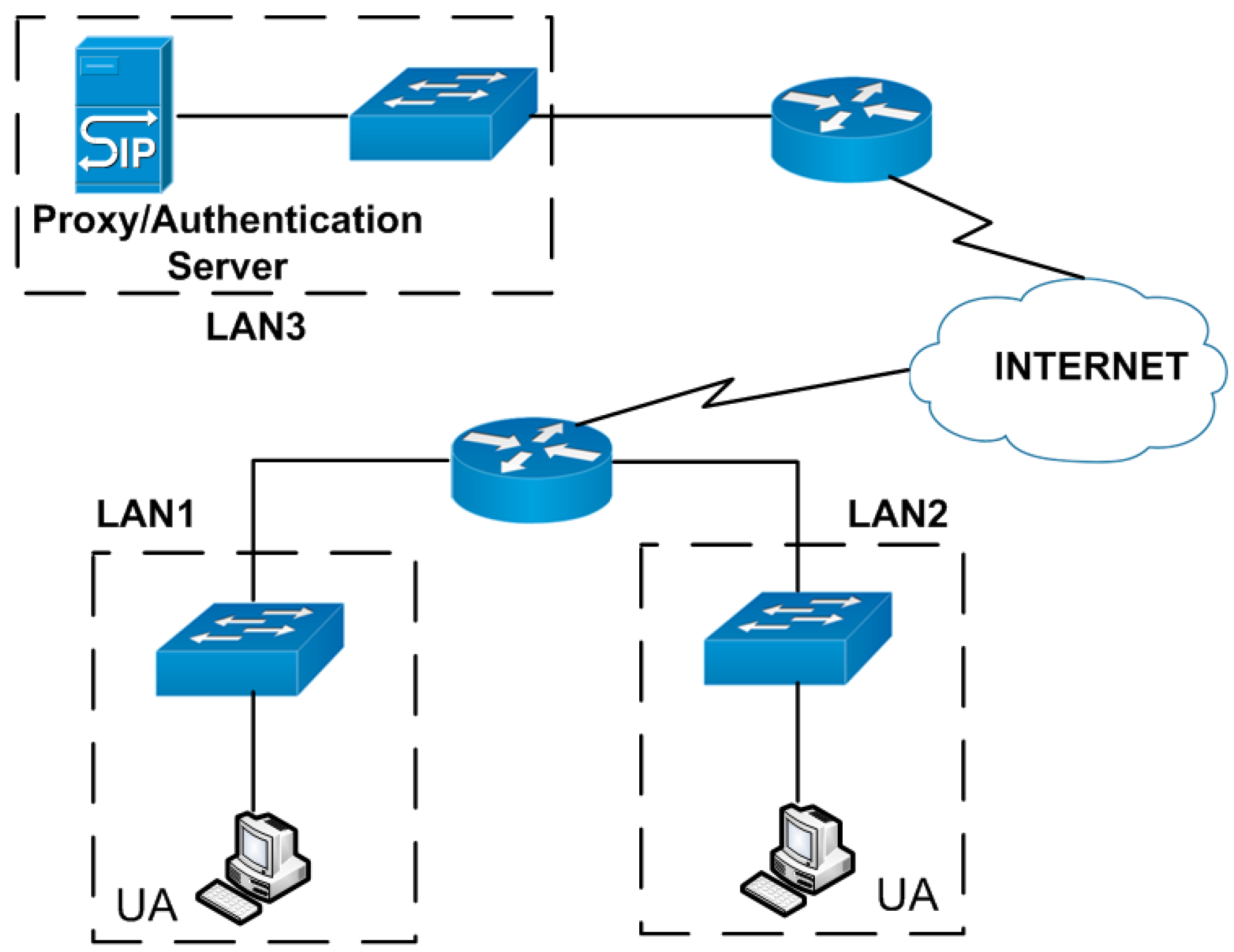
3.1. Session Initiation Protocol
- (1)
- User Agent Client and Server:
- (2)
- Registrar Server
- (3)
- Proxy Server
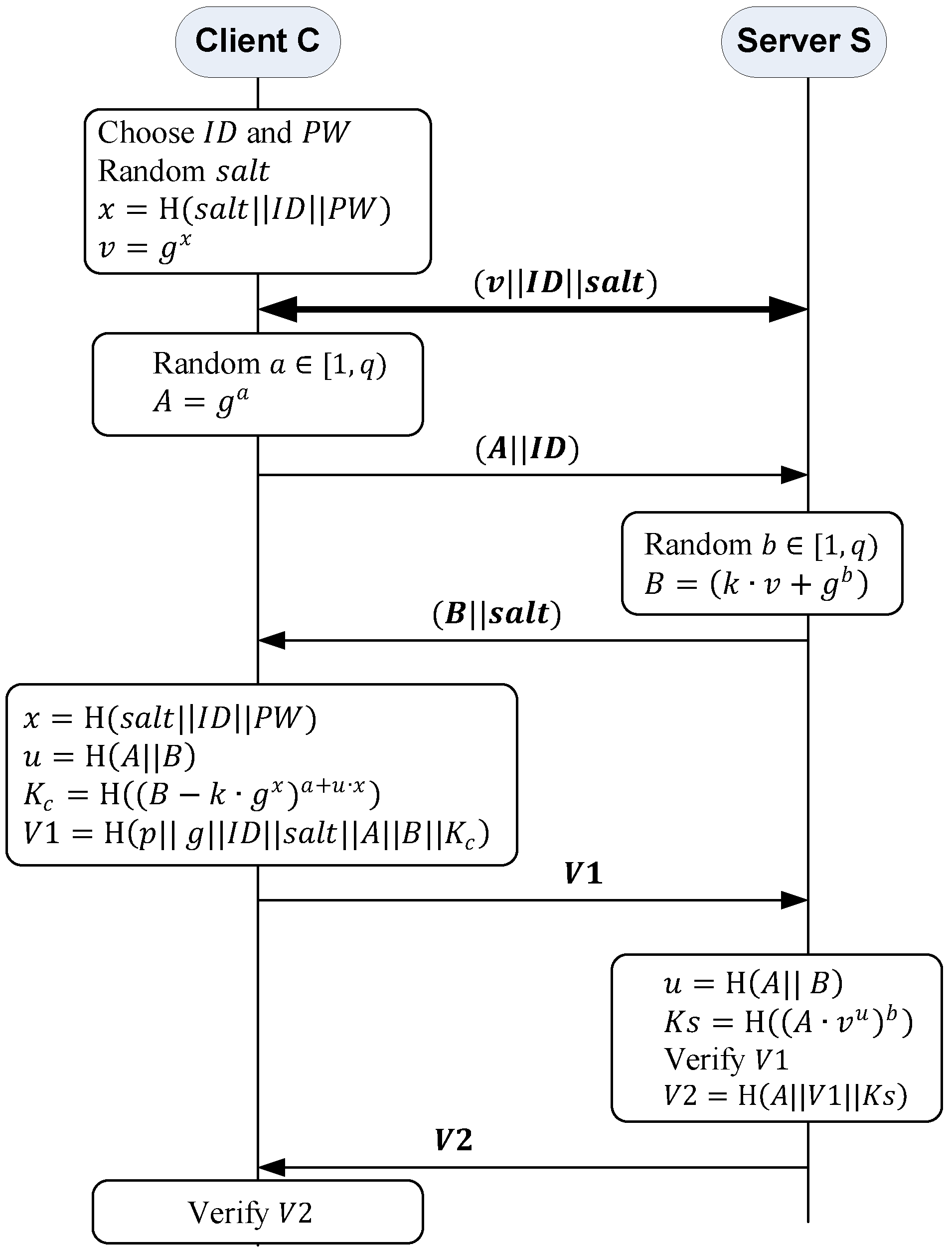
3.2. Secure Remote Password Protocol
4. Security Analysis of SRP
4.1. Offline Password Guessing Attack
- Assuming that the attacker masquerades as a fake server and persuades C to make an authentication attempt.
- C computes the ephemeral public key and sends it with its ID to the attacker.
- To capture of , the attacker starts an authentication session with the actual server by sending and , received from C, to S.
- computes and sends it to the attacker with the salt of client C.
- The attacker generates a random number , guesses any password , and computes their own parameter and exponential residue . Then, they send and to the client .
- The client C computes the message and sends it to the attacker, where and .
- The attacker imitates network failure or informs C that the password is not correct.
- The long-term private password can be guessed by performing the following offline password guessing attack:
- (i)
- The attacker computes , , , and .
- (ii)
- The attacker computes a modified server key as .
- (iii)
- The attacker computes a modified message and checks if .
- (iv)
- If it holds, the attacker has guessed the correct secret password .
- (v)
- If it is not correct, the attacker chooses another password from a dictionary and repeatedly performs the above verification process starting from step i.
4.2. Stolen-Verifier Attack
- The attacker chooses a secret password from the password dictionary.
- The attacker computes and and checks if .
- If it holds, the attacker has guessed the correct secret password .
- If it is not correct, the attacker chooses another password from the password dictionary and repeatedly performs the above verification process.
- An active adversary may eavesdrop the communication flows between C and or persuade C to make an authentication attempt with his server.
- When legal client C wants to login into server S, they send the request message () to .
- generates a random number and computes the ephemeral public key using the stolen-verifier for C.
- sends along with to .
- Upon receiving from , computes and the verification message , where , and sends it back to C as evidence that they have the correct session key.
- C verifies as explained in Section 3.2. Because , C accepts and trusts as a server. Therefore, can obtain the client’s personal information.
4.3. Denning–Sacco Attack
- Assume the attacker intercepts the request message sent by C to S.
- To capture , the attacker starts an authentication session with the actual server by forwarding parameters and to . computes and sends it to the attacker with the salt of client C.
- The attacker can masquerade as a fake server, randomly generate a number , guess any password , and compute his own parameters and . Then, they send and to .
- C computes the message and sends it to the attacker, where and .
- Assuming that the attacker somehow obtained the shared session key from the client, password can be obtained by performing the following offline password guessing attack:
- (i)
- The attacker makes a guess for the secret password from a password dictionary.
- (ii)
- The attacker computes , and and checks if
- (iii)
- If it holds, the attacker has guessed the correct secret password . Otherwise, the attacker repeatedly performs the verification process.
5. Secure SIP
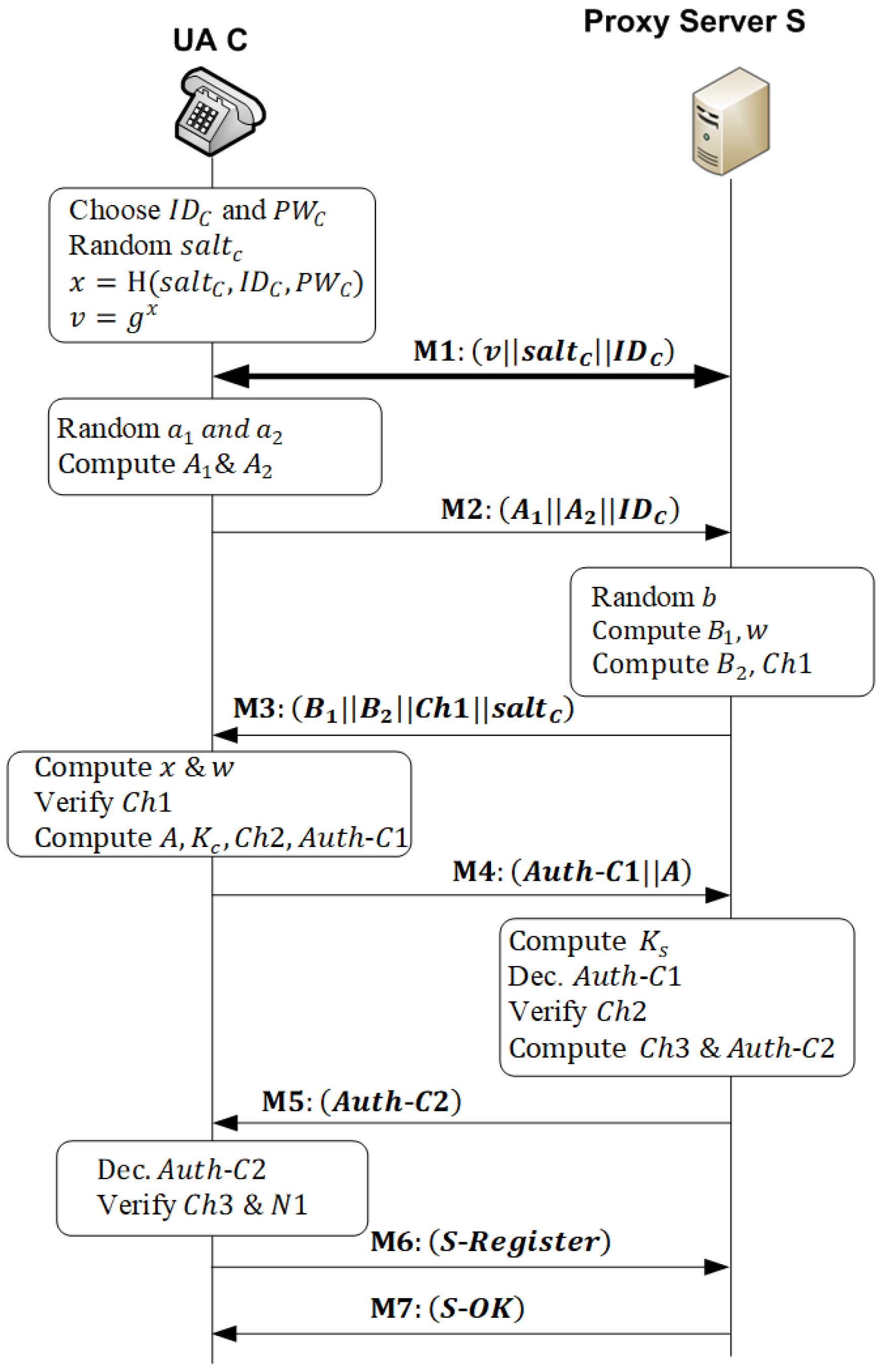
5.1. A-SIP Protocol
- (1)
- Setup Phase
- The user of a client C freely chooses their identity and password . Then, C selects a random password and then computes a verifier and a secret exponent as:
- C establishes a secure connection with and sends , , and to .
- Upon receiving the message , computes the password verifier as , where is the private secret for the server, which is a random bit-string with high entropy. Finally, stores and in its database indexed by .
- (2)
- Login Phase
- C generates two random numbers and from the range . Additionally, it computes two ephemeral public keys and .
- C sends the request message to the proxy server.
- When S receives , it uses to retrieve and . Using , S computes , which is XORed with to obtain . Then, it generates a random number and computes the ephemeral public key and private key . If S does not have credentials of C, it securely communicates with the authentication/registrar server to get them.
- S computes the second ephemeral public key and the first challenge as:
- S sends the message to .
- (3)
- Authentication Phase
- Upon receiving the message , C computes and as:
- 2.
- C checks that the received challenge is equal to the computed challenge. If not true, C terminates the session with and does not complete the authentication process. Otherwise, C starts to compute the second challenge.
- 3.
- C computes the public key A, the session key , and the second challenge as:
- 4.
- C generates a nonce , which is a random number that is difficult for an opponent to guess and represents a unique identifier for this transaction. C encrypts and using to construct the first authenticator that represents the client authenticator. The subsequent message (response) received from S must contain the hash of the nonce .
- 5.
- C sends the challenge message to S
- 6.
- When S receives the message, it computes its session key as:
- 7.
- S compares the second challenge extracted from and the computed challenge . If , S aborts the session with C. Otherwise, S computes the third challenge
- 8.
- S encrypts and using session to construct the server authenticator as:
- 9.
- After receiving the message , C decrypts the message using to extract . Next, it verifies and . If not correct, C terminates the sessions. Otherwise, C assures that the message has been sent by S and the authentication is successful. Using the nonce assures C that this is a response for a fresh message and helps prevent a replay attack.
- (4)
- Registration Phase
- At the end of the authentication phase, C forms the S-Register message aswhere is the standard SIP registration message and .
- On receipt of the S-Register message, S decrypts the message to obtain the Register message and checks . The SIP server processes the Register message to register the URI of the client C ().
- S sends the S-OK message to C, which is computed as:where is the standard SIP OK message, , and is a ticket that C uses for subsequent authentications to obtain VoIP services from S. This is explained in detail in the next section.
- When receiving the S-OK message from S, C decrypts it using the session key and checks . If correct, C accepts the authentication ticket .
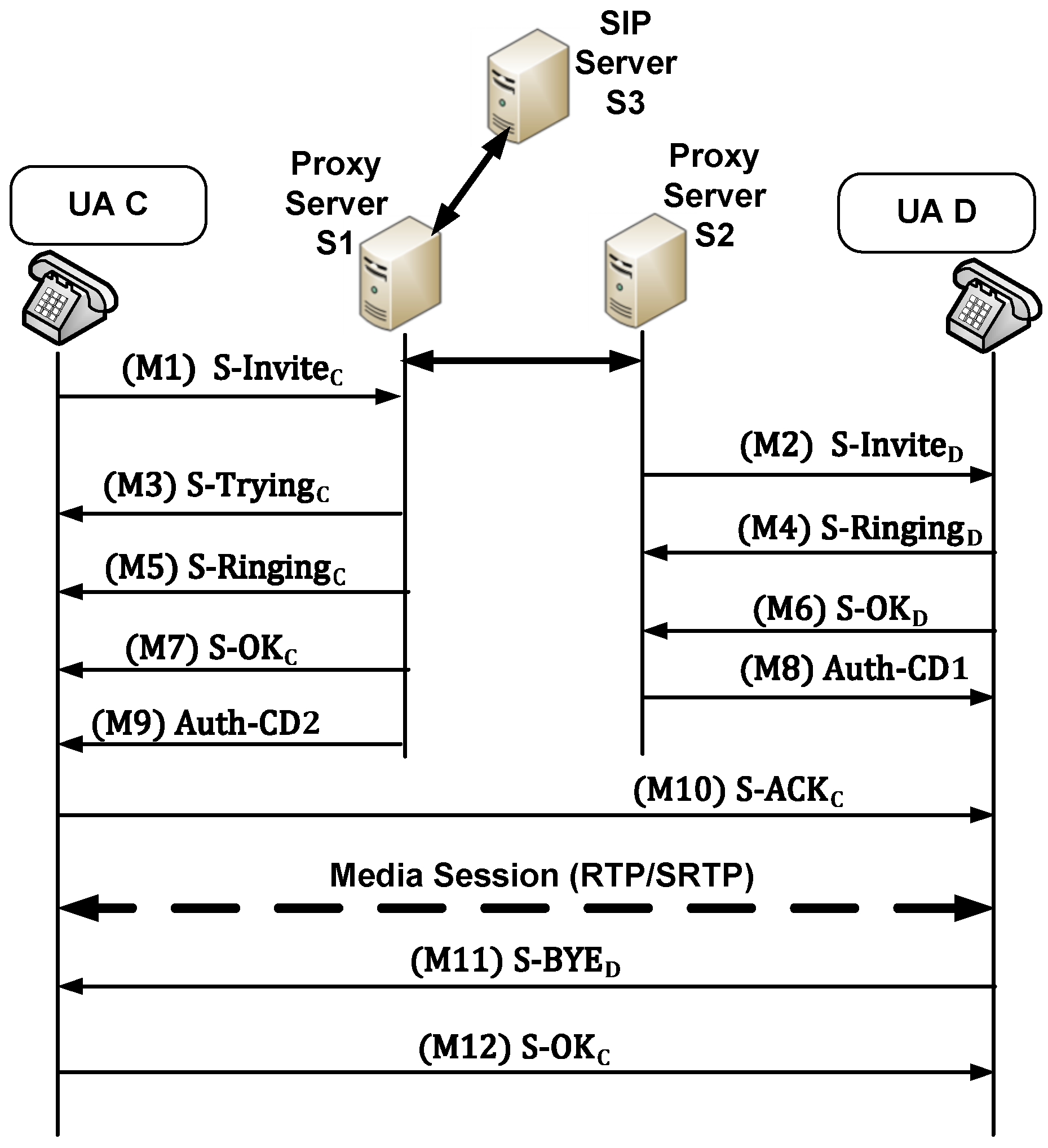
5.2. KP-SIP Protocol
- (1)
- Call Initiation Phase
- (2)
- Teardown Phase
6. Informal Security Analysis
6.1. Offline Password Guessing Attack
- 1.
- During the authentication process, intercepts the request message sent by C to login to .
- 2.
- The attacker forwards to S to obtain . Then, they generate a random number , guesses any password , and computes their own parameter as:
- 3.
- Upon receiving , C computes , , and . Next it compares the received challenge and the computed challenge . If the guessed passwords are not correct, C detects that . Therefore, C terminates the connection with the fake server.
- AD randomly generates and and calculates public keys and and then transmits them to with user identity .
- randomly generates a random number , calculates public keys and , the secret parameter , and the challenge . Next, it sends , , , and to .
- guesses any password and computes other parameters:
- 4.
- Upon receiving , encrypts the message using its key . If the guessed password and secret key are wrong, S detects that . Therefore, does not respond to AD and terminates the session.
6.2. Denning–Sacco Attack
- During the authentication process, intercepts the request message sent from C to . Then, they forward to S to obtain .
- generates a random number , guesses any password , and computes their own parameter as:
- 3.
- To perform the brute-force attack using the compromised session key , must first compute the server session key as . To compute , must obtain from C.
- 4.
- Upon receiving , C computes , , and Ch1. Next, it compares the received and computed challenges ( and . If the guessed password is not correct, C detects that . Therefore, C terminates the connection with the server and does not send the parameter to .
6.3. Stolen-Verifier Attack
6.4. Perfect Forward Secrecy
6.5. Impersonation Attack
6.6. Replay Attack
6.7. Session Teardown Attack
6.8. Registration Hijacking Attack
6.9. Request Spoofing Attack
6.10. Message Tampering Attack
6.11. Man-In-The-Middle Attack
6.12. Re-INVITE Attack
7. Formal Security Analysis
- Weak secret PWc is true.
- Query not attacker(Kc[]) is true.
- Query not attacker(Ks[]) is true.
- Query not attacker(Ksc[]) is true.
- Query not attacker(Kp[]) is true.
- Query inj-event(UserAuthed(id)) ==> inj-event(UserStarted(id)) is true.
- Query inj-event(ServerEnd(id)) ==> inj-event(ServerStarted(id)) is true.
- Query not attacker(Ksc[]) is true.
- Query not attacker(Ksd[]) is true.
- Query not attacker(Kcd1[]) is true.
- Query not attacker(Kcd2[]) is true.
- Query inj-event(C_End(URIc_1)) ==> inj-event(C_End(URIc_1)) is true.
- Query inj-event(C_End(URId_2)) ==> inj-event(C_End(URId_2)) is true.
- Query inj-event(ServerEnd(id)) ==> inj-event(ServerStarted(id)) is true.
8. Performance Analysis
8.1. Performance Comparison
8.2. S-SIP Overhead
9. Conclusions
Author Contributions
Funding
Institutional Review Board Statement
Informed Consent Statement
Conflicts of Interest
Appendix A
| Constructor | Function |
|---|---|
| h | One-way hash function |
| mult | Multiplication of two integers |
| mult3 | Multiplication of three integers |
| div | Integer division |
| concat | Concatenation 2, 3, 4 or 6 values |
| exp | Exponential operation |
| xor | Exclusive-OR |
| sEnc | Symmetric encryption |
| sDec | Symmetric decryption |
| gKey | Converting from the bitstring type to the key type |
| BitKey | Converting from the key type to the bitstring type |
| getfirst | Extract the first of concatenated values |
| getsec | Extract the second of concatenated values |
References
- Schulzrinne, H.; Casner, S.; Frederick, R.; Jacobson, V. RFC 3550-RTP: A Transport Protocol for Real-Time Applications; IETF: Fremont, CA, USA, 2003. [Google Scholar]
- Rosenberg, J.; Schulzrinne, H.; Camarillo, G.; Johnston, A.; Peterson, J.; Sparks, R.; Handley, M.; Schooler, E. RFC 3261-Sip: Session Initiation Protocol; IETF: Fremont, CA, USA, 2002. [Google Scholar]
- Tam, K.; Goh, H. Session initiation protocol. In Proceedings of the 2002 IEEE International Conference on Industrial Technology, 2002, IEEE ICIT ‘02, Bangkok, Thailand, 11–14 December 2002; pp. 1310–1314. [Google Scholar]
- Chiang, W.K.; Chang, W.Y. Mobile-initiated network-executed SIP-based handover in IMS over heterogeneous accesses. Int. J. Commun. Syst. 2010, 23, 1268–1288. [Google Scholar] [CrossRef]
- Cho, K.; Pack, S.; Kwon, T.T.; Choi, Y. An extensible and ubiquitous RFID management framework over next-generation network. Int. J. Commun. Syst. 2010, 23, 1093–1110. [Google Scholar] [CrossRef]
- Keromytis, A.D. A Look at VoIP Vulnerabilities. Usenix Secur. Artic. 2010, 35, 41–50. [Google Scholar]
- Keromytis, A.D. A Comprehensive Survey of Voice over IP Security Research. IEEE Commun. Surv. Tutor. 2012, 14, 514–537. [Google Scholar] [CrossRef]
- Ahson, A.S.; Ilyas, M. Sip Handbook Services, Technologies, And Security of Session Initiation Protocol; CRC Press: Boca Raton, FL, USA, 2009. [Google Scholar]
- Ahson, A.S.; Ilyas, M. VoIP Handbook, Applications, Technologies, Reliability, and Security; CRC Press: Boca Raton, FL, USA, 2009. [Google Scholar]
- Sisalem, D.; Floroiu, J.; Kuthan, J.; Abend, U.; Schulzrinne, H. SIP Security; John Wiley & Sons Ltd.: Hoboken, NJ, USA, 2009. [Google Scholar]
- Franks, J.; Hallam-Baker, P.; Hostetler, J.; Lawrence, S.; Leach, P.; Luotonen, A.; Stewart, L. RFC 2617-HTTP Authentication: Basic and Digest Access Authentication; IETF: Fremont, CA, USA, 1999. [Google Scholar]
- Kent, S.; Seo, K. RFC 4301-Security Architecture for the Internet Protocol; IETF: Fremont, CA, USA, 2005. [Google Scholar]
- Dierks, T.; Rescorla, E. RFC 5246-The Transport Layer Security (TLS) Protocol; IETF: Fremont, CA, USA, 2008. [Google Scholar]
- Ramsdell, B. RFC 3851-Secure/Multipurpose Internet Mail Extensions (S/MIME) Version 3.1 Message Specification; IETF: Fremont, CA, USA, 2004. [Google Scholar]
- Nguyen, K.T.; Laurent-Maknavicius, M.; Oualha, N.J.A.H.N. Survey on secure communication protocols for the Internet of Things. Ad Hoc Netw. 2015, 32, 17–31. [Google Scholar] [CrossRef]
- Haase, B.; Labrique, B. Aucpace: Efficient verifier-based PAKE protocol tailored for the IIOT. IACR Cryptol. Eprint Arch. 2018, 2018, 286. [Google Scholar] [CrossRef]
- Sebek, F.; Petri, O.; Sebek, F. A Comparison of the Password-Authenticated Key Exchange Protocols, SRP-6a and PAKE2+; Technical Report; Kth Royal Institute of Technology, School of Electrical Engineering and Computer Science: Stockholm, Sweden, 2019. [Google Scholar]
- Shin, S.; Kobara, K. Security Analysis of Password-Authenticated Key Retrieval. IEEE Trans. Dependable Secur. Comput. 2017, 14, 573–576. [Google Scholar]
- Jarecki, S.; Krawczyk, H.; Xu, J. OPAQUE: An Asymmetric PAKE Protocol Secure Against Pre-computation Attacks. In Advances in Cryptology—EUROCRYPT 2018, Proceedings of the Annual International Conference on the Theory and Applications of Cryptographic Techniques, Tel Aviv, Israel, 29 April–3 May 2018; Springer International Publishing: Cham, Switzerland, 2018. [Google Scholar]
- Bellovin, S.M.; Merritt, M. Augmented encrypted key exchange: A password-based protocol secure against dictionary attacks and password file compromise. In Proceedings of the CCS93: 1st ACM Conference on Communications and Computing Security, Fairfax, VA, USA, 3–5 November 1993; pp. 244–250. [Google Scholar]
- Boyd, C.; Mathuria, A.; Stebila, D. Protocols for Authentication and Key Establishment; Lecture Notes in Computer Science; Springer: Berlin/Heidelberg, Germany, 2003. [Google Scholar]
- Hao, F.; Ryan, P.Y.A. Password Authenticated Key Exchange by Juggling. In Security Protocols XVI, Proceedings of the 16th International Workshop on Security Protocols, Cambridge, UK, 16–18 April 2008; Springer: Berlin/Heidelberg, Germany, 2008. [Google Scholar]
- Yoneyama, K. Cross-Realm Password-Based Server Aided Key Exchange. In Information Security Applications; Springer: Berlin/Heidelberg, Germany, 2011. [Google Scholar]
- Wu, T.D. The secure remote password protocol. NDSS 1998, 98, 97–111. [Google Scholar]
- Wu, T. RFC 2945-The SRP Authentication and Key Exchange System; IETF: Fremont, CA, USA, 2000. [Google Scholar]
- Taylor, T.W.D.; Mavrogiannopoulos, N.; Perrin, T. RFC 5054-Using the Secure Remote Password (SRP) Protocol for TLS Authentication; IETF: Fremont, CA, USA, 2007. [Google Scholar]
- IEEE Std 1363.2™-2008; IEEE Standard Specification for Password-Based Public-Key Cryptographic Techniques. IEEE Computer Society: Piscataway, NJ, USA, 2008; 140p.
- Tom, W. Official Website for SRP. Available online: http://srp.stanford.edu/ (accessed on 7 March 2022).
- Yang, C.-C.; Wang, R.-C.; Liu, W.-T. Secure authentication scheme for session initiation protocol. Comput. Secur. 2005, 24, 381–386. [Google Scholar] [CrossRef]
- Huang, H.-F. A new efficient authentication scheme for Session Initiation Protocol. In Proceedings of the 9th Joint International Conference on Information Sciences (JCIS-06), Kaohsiung, Taiwan, 8–11 October 2006; Atlantis Press: Amsterdam, The Netherlands, 2006; pp. 402–404. [Google Scholar]
- Jo, H.; Lee, Y.; Kim, M.; Kim, S.; Won, D. Off-Line Password-Guessing Attack to Yang’s and Huang’s Authentication Schemes for Session Initiation Protocol. In Proceedings of the 2009 Fifth International Joint Conference on INC, IMS and IDC, Seoul, Republic of Korea, 25–27 August 2009; pp. 618–621. [Google Scholar]
- Durlanik, A.; Sogukpinar, I. SIP authentication scheme using ECDH. Proc. World Acad. Sci. Eng. Technol. 2005, 8, 350–353. [Google Scholar]
- Wu, L.; Zhang, Y.; Wang, F. A new provably secure authentication and key agreement protocol for SIP using ECC. Comput. Stand. Interfaces 2009, 31, 286–291. [Google Scholar] [CrossRef]
- Koblitz, N. Elliptic curve cryptosystems. Math. Comput. 1987, 48, 203–209. [Google Scholar] [CrossRef]
- Yoon, E.-J.; Yoo, K.-Y.; Kim, C.; Hong, Y.-S.; Jo, M.; Chen, H.-H. A secure and efficient SIP authentication scheme for converged VoIP networks. J. Comput. Commun. 2010, 33, 1674–1681. [Google Scholar] [CrossRef]
- Pu, Q. Weaknesses of SIP Authentication Scheme for Converged VoIP Networks. Cryptology ePrint Archive. Paper 2010/464. Available online: https://eprint.iacr.org/2010/464 (accessed on 7 March 2022).
- Tsai, J.L. Efficient nonce-based authentication scheme for session initiation protocol. Int. J. Netw. Secur. 2009, 8, 312–316. [Google Scholar]
- Yoon, E.-J.; Shin, Y.-N.; Jeon, I.-S.; Yoo, K.-Y. Robust mutual authentication with a key agreement scheme for the session initiation protocol. IETE Tech. Rev. 2010, 27, 203–213. [Google Scholar] [CrossRef]
- Xie, Q. A new authenticated key agreement for session initiation protocol. Int. J. Commun. Syst. 2012, 25, 47–54. [Google Scholar] [CrossRef]
- Farash, M.S.; Attari, M.A. An enhanced authenticated key agreement for session initiation protocol. Inf. Technol. Control 2013, 42, 333–342. [Google Scholar] [CrossRef]
- Zhang, Z.; Qi, Q.; Kumar, N.; Chilamkurti, N.; Jeong, H.-Y. A secure authentication scheme with anonymity for session initiation protocol using elliptic curve cryptography. Multimed. Tools Appl. 2015, 74, 3477–3488. [Google Scholar] [CrossRef]
- Lu, Y.; Li, L.; Peng, H.; Yang, Y. A secure and efficient mutual authentication scheme for session initiation protocol. Peer-Peer Netw. Appl. 2016, 9, 449–459. [Google Scholar] [CrossRef]
- Chaudhry, S.; Khan, I.; Irshad, A.; Ashraf, M.U.; Khan, M.K.; Ahmad, H.F. A provably secure anonymous authentication scheme for Session Initiation Protocol. Secur. Commun. Netw. 2016, 9, 5016–5027. [Google Scholar] [CrossRef]
- Kumari, S.; Karuppiah, M.; Das, A.K.; Li, X.; Wu, F.; Gupta, V. Design of a secure anonymity-preserving authentication scheme for session initiation protocol using elliptic curve cryptography. J. Ambient. Intell. Humaniz. Comput. 2018, 9, 643–653. [Google Scholar] [CrossRef]
- Zhang, L.; Tang, S.; Cai, Z. Efficient and flexible password authenticated key agreement for Voice over Internet Protocol Session Initiation Protocol using smart card. Int. J. Commun. Syst. 2013, 27, 2691–2702. [Google Scholar] [CrossRef]
- Irshad, A.; Sher, M.; Rehman, E.; Ch, S.A.; Hassan, M.U.; Ghani, A. A single round-trip SIP authentication scheme for Voice over Internet Protocol using smart card. Multimed. Tools Appl. 2015, 74, 3967–3984. [Google Scholar] [CrossRef]
- Arshad, H.; Nikooghadam, M. Security analysis and improvement of two authentication and key agreement schemes for session initiation protocol. J. Supercomput. 2015, 71, 3163–3180. [Google Scholar] [CrossRef]
- Tu, H.; Kumar, N.; Chilamkurti, N.; Rho, S. An improved authentication protocol for session initiation protocol using smart card. Peer-Peer Netw. Appl. 2015, 8, 903–910. [Google Scholar] [CrossRef]
- Chaudhry, S.A.; Naqvi, H.; Sher, M.; Farash, M.S.; Hassan, M.U. An improved and provably secure privacy preserving authentication protocol for SIP. Peer-Peer Netw. Appl. 2017, 10, 1–15. [Google Scholar] [CrossRef]
- Nikooghadam, M.; Jahantigh, R.; Arshad, H. A lightweight authentication and key agreement protocol preserving user anonymity. Multimed. Tools Appl. 2017, 76, 13401–13423. [Google Scholar] [CrossRef]
- Ravanbakhsh, N.; Mohammadi, M.; Nikooghadam, M. Perfect forward secrecy in VoIP networks through design a lightweight and secure authenticated communication scheme. Multimed. Tools Appl. 2019, 78, 11129–11153. [Google Scholar] [CrossRef]
- Nikooghadam, M.; Amintoosi, H. Perfect forward secrecy via an ECC-based authentication scheme for SIP in VoIP. J. Supercomput. 2020, 76, 3086–3104. [Google Scholar] [CrossRef]
- Abadi, M.; Blanchet, B.; Comon-Lundh, H. Models and Proofs of Protocol Security: A Progress Report. In Computer Aided Verification, Proceedings of the 21st International Conference on Computer Aided Verification, Grenoble, France, 26 June–2 July 2009; Lecture Notes in Computer Science; Springer: Berlin/Heidelberg, Germany, 2009; pp. 35–49. [Google Scholar]
- Audet, F. The Use of the SIPS URI Scheme in the Session Initiation Protocol (SIP); RFC 5630; IETF: Fremont, CA, USA, 2009. [Google Scholar]
- Abubakar, M.; Jaroucheh, Z.; Al Dubai, A.; Buchanan, B. Blockchain-Based Authentication and Registration Mechanism for SIP-Based VoIP Systems. In Proceedings of the 5th Cyber Security in Networking Conference (CSNet), Abu Dhabi, United Arab Emirates, 12–14 October 2021; pp. 63–70. [Google Scholar]
- Aldahwan, N.; Alghazzawi, D. Use of Blockchain in Public Key Infrastructure (PKI): A Systematic Literature Review. Int. J. Comput. Sci. Inf. Secur. 2020, 18, 106–111. [Google Scholar]
- Johnston, A. SIP: Understanding the Session Initiation Protocol, 3rd ed.; Artech House: Norwood, MA, USA, 2009. [Google Scholar]
- Kulkarni, L. VoIP Security: A Performance and Cost-benefit Analysis. Inf. Technol. Ind. 2021, 8, 34–42. [Google Scholar] [CrossRef]
- Bates, R.J. Securing VoIP: Keeping Your VoIP Network Safe; Elsevier Inc.: Amsterdam, The Netherlands, 2015. [Google Scholar]
- Omar, M.I.; Kiprut, C.W.; Kimwele, M.W. Securing the IP Multimedia Subsystem with IPsec and HTTP Digest. Int. J. Comput. 2017, 26, 117–128. [Google Scholar]
- Farley, R.; Wang, X. VoIP Shield: A transparent protection of deployed VoIP systems from SIP-based exploits. In Proceedings of the 2012 IEEE Network Operations and Management Symposium, Maui, HI, USA, 16–20 April 2012; pp. 486–489. [Google Scholar]
- Basem, B.; Ghalwash, A.Z.; Sadek, R.A. Multilayer Secured SIP Based VoIP Architecture. Int. J. Comput. Theory Eng. 2015, 7, 453–462. [Google Scholar] [CrossRef][Green Version]
- Sherman, A.T.; Lanus, E.; Liskov, M.; Zieglar, E.; Chang, R.; Golaszewski, E.; Wnuk-Fink, R.; Bonyadi, C.J.; Yaksetig, M.; Blumenfeld, I. Formal Methods Analysis of the Secure Remote Password Protocol. In Logic, Language, and Security; Springer: Cham, Switzerland, 2020. [Google Scholar]
- Arshad, H.; Nikooghadam, M. An efficient and secure authentication and key agreement scheme for session initiation protocol using ECC. Multimed. Tools Appl. 2016, 75, 181–197. [Google Scholar] [CrossRef]
- Chen, C.-M.; Xiang, B.; Wu, T.-Y.; Wang, K.-H. An Anonymous Mutual Authenticated Key Agreement Scheme for Wearable Sensors in Wireless Body Area Networks. Appl. Sci. 2018, 8, 1074. [Google Scholar] [CrossRef]
- Wu, F.; Xu, L.; Kumari, S.; Li, X.; Shen, J.; Choo, K.-K.R.; Wazid, M.; Das, A.K. An efficient authentication and key agreement scheme for multi-gateway wireless sensor networks in IoT deployment. J. Netw. Comput. Appl. 2017, 89, 72–85. [Google Scholar] [CrossRef]
- Abbasinezhad-Mood, D.; Nikooghadam, M. Efficient Anonymous Password-Authenticated Key Exchange Protocol to Read Isolated Smart Meters by Utilization of Extended Chebyshev Chaotic Maps. IEEE Trans. Ind. Inform. 2018, 14, 4815–4828. [Google Scholar] [CrossRef]
- Abbasinezhad-Mood, D.; Nikooghadam, M. Design and hardware implementation of a security-enhanced elliptic curve cryptography based lightweight authentication scheme for smart grid communications. Future Gener. Comput. Syst. 2018, 84, 47–57. [Google Scholar] [CrossRef]
- Younes, O. ProVerif Model for S-SIP Protocol. Available online: https://drive.google.com/drive/folders/1Bks5GwfWbt3v1qgqKFH0mREgzhf3J3Bj?usp=sharing (accessed on 20 March 2022).

| Notation | Description |
|---|---|
| Large prime number | |
| Primitive root modulo p (generator) | |
| One-way hash function | |
| Password of client | |
| Session key of entity | |
| Session key shared between and | |
| a, b | High-entropy random numbers |
| || | Concatenation operation |
| Timestamp number i | |
| Lifetime number i | |
| Nonce number i | |
| Bitwise XOR operation | |
| ↔ | Secure channel |
| → | Common channel |
| IDC | ID of entity C |
| E(K, [M]) | Symmetric encryption of M with the key K |
| (M1) (M2) (M3) (M4) (M5) (M6) (M7) |
| (M8) (M9) (M10) (M11) (M12) |
| F1 | F2 | F3 | F4 | F5 | F6 | F7 | F8 | F9 | F10 | F11 | F12 | |
|---|---|---|---|---|---|---|---|---|---|---|---|---|
| [39] | N | Y | Y | Y | N | N | Y | Y | Y | Y | Y | N |
| [45] | Y | Y | Y | N | N | Y | N | Y | Y | Y | Y | Y |
| [41] | Y | Y | Y | N | N | Y | N | Y | N | Y | Y | Y |
| [42] | Y | Y | Y | Y | N | N | Y | Y | N | Y | Y | Y |
| [43] | Y | Y | Y | Y | N | N | N | Y | Y | Y | Y | Y |
| [48] | Y | Y | Y | N | N | N | Y | Y | Y | Y | Y | Y |
| [49] | N | Y | Y | Y | Y | N | Y | Y | Y | Y | Y | Y |
| [50] | N | Y | Y | Y | Y | N | Y | Y | Y | N | Y | Y |
| [51] | Y | Y | Y | Y | Y | Y | Y | Y | Y | N | Y | Y |
| SRP | N | N | N | Y | Y | Y | Y | Y | Y | Y | Y | Y |
| A-SIP | Y | Y | Y | Y | Y | Y | Y | Y | Y | Y | Y | Y |
| Symbol | Operation | Mean (µs) | Stan. Dev. (µs) |
|---|---|---|---|
| One-way hash function (SHA-1) | 16.5 | 4.8 | |
| Elliptic curve point multiplication | 32,646.2 | 365.5 | |
| Elliptic curve point addition | 838.7 | 26.5 | |
| Modular exponentiation | 345.4 | 34.8 | |
| Symmetric Key encryption/decryption | 157.5 | 12.8 | |
| Random number generation | 17.4 | 1.6 |
| Schemes | Side of Operations | Operations | Cost (ms) | Total (ms) |
|---|---|---|---|---|
| [39] | Client | + | 99.001 | 197.620 |
| Server | 98.619 | |||
| [45] | Client | 131.539 | 263.868 | |
| Server | 132.329 | |||
| [41] | Client | 98.022 | 196.044 | |
| Server | 98.022 | |||
| [42] | Client | 65.375 | 130.767 | |
| Server | 65.392 | |||
| [43] | Client | 98.022 | 163.381 | |
| Server | 65.359 | |||
| [48] | Client | 98.860 | 196.882 | |
| Server | 98.022 | |||
| [49] | Client | 98.877 | 197.265 | |
| Server | 98.388 | |||
| [50] | Client | 0.572 | 1.443 | |
| Server | 0.871 | |||
| [51] | Client | 0.465 | 1.527 | |
| Server | 1.062 | |||
| SRP | Client | 13.136 | 26.239 | |
| Server | 13.103 | |||
| A-SIP | Client | 26.363 | 44.002 | |
| Server | 17.639 |
| RTT = 32 ms | RTT = 227 ms | ||||||
|---|---|---|---|---|---|---|---|
| SIP | S-SIP | SRP-TLS | SIP | S-SIP | SRP-TLS | ||
| TA (ms) | Mean | 33.9 | 146.6 | 275.4 | 229.4 | 733.1 | 1389.1 |
| Stan. Dev. | 0.3 | 2.7 | 7.3 | 3.4 | 9.5 | 11.4 | |
| TS (ms) | Mean | 152.3 | 171.9 | 166.9 | 1032.1 | 1149.5 | 1102.8 |
| Stan. Dev. | 2.5 | 3.6 | 6.8 | 12.4 | 14.8 | 14.2 | |
| Overhead (ms) | NA | 132.3 | 256.1 | NA | 621.1 | 1230.4 | |
Publisher’s Note: MDPI stays neutral with regard to jurisdictional claims in published maps and institutional affiliations. |
© 2022 by the authors. Licensee MDPI, Basel, Switzerland. This article is an open access article distributed under the terms and conditions of the Creative Commons Attribution (CC BY) license (https://creativecommons.org/licenses/by/4.0/).
Share and Cite
Younes, O.; Albalawi, U. Securing Session Initiation Protocol. Sensors 2022, 22, 9103. https://doi.org/10.3390/s22239103
Younes O, Albalawi U. Securing Session Initiation Protocol. Sensors. 2022; 22(23):9103. https://doi.org/10.3390/s22239103
Chicago/Turabian StyleYounes, Osama, and Umar Albalawi. 2022. "Securing Session Initiation Protocol" Sensors 22, no. 23: 9103. https://doi.org/10.3390/s22239103
APA StyleYounes, O., & Albalawi, U. (2022). Securing Session Initiation Protocol. Sensors, 22(23), 9103. https://doi.org/10.3390/s22239103






