A Hybrid Spider Monkey and Hierarchical Particle Swarm Optimization Approach for Intrusion Detection on Internet of Things
Abstract
1. Introduction
- Designing a security framework for the IoT application is a problematic task because of the dynamic IoT network nature.
- The security mechanism for IoT is ensured by using an appropriate tool for distribution of architecture, which has the ability to analyze a huge amount of data. This was a challenge.
- The network environment has interconnected devices, which includes poorly designed sensors and authentication measures.
- The hybrid feature selection that combines SMO and HPSO is developed to solve the massive intrusion data classification problem and improve the accuracy rate of attack detection. The local searching phase of conventional SMO is operated in a random manner, which affects the optimal score value. In order to overcome this issue, the hierarchical PSO’s velocity is combined with SMO’s searching process to obtain the optimal feature subset.
- Further, the feature importance with Rosenbrock function is included as gradient for Hybrid SMO-HPSO. Rosenbrock is a parabolic mathematical function which represents the probability density function of any events. In this research, the probability of features contributing to the target class is defined by the Rosenbrock function, so the Hybrid SMO-HPSO does not require any classified instance output to compute the fitness.
- To enhance the accuracy that shows lower classification error, the attacks for NSL-KDD are classified into four types of attack, including DoS, U2R, R2L, and probing attack. The UNSW Dataset classifies the attacks into normal and abnormal classes.
2. Related Works
2.1. Attack Detection Based on Classification
2.2. Attack Detection Based on Optimization Algorithms
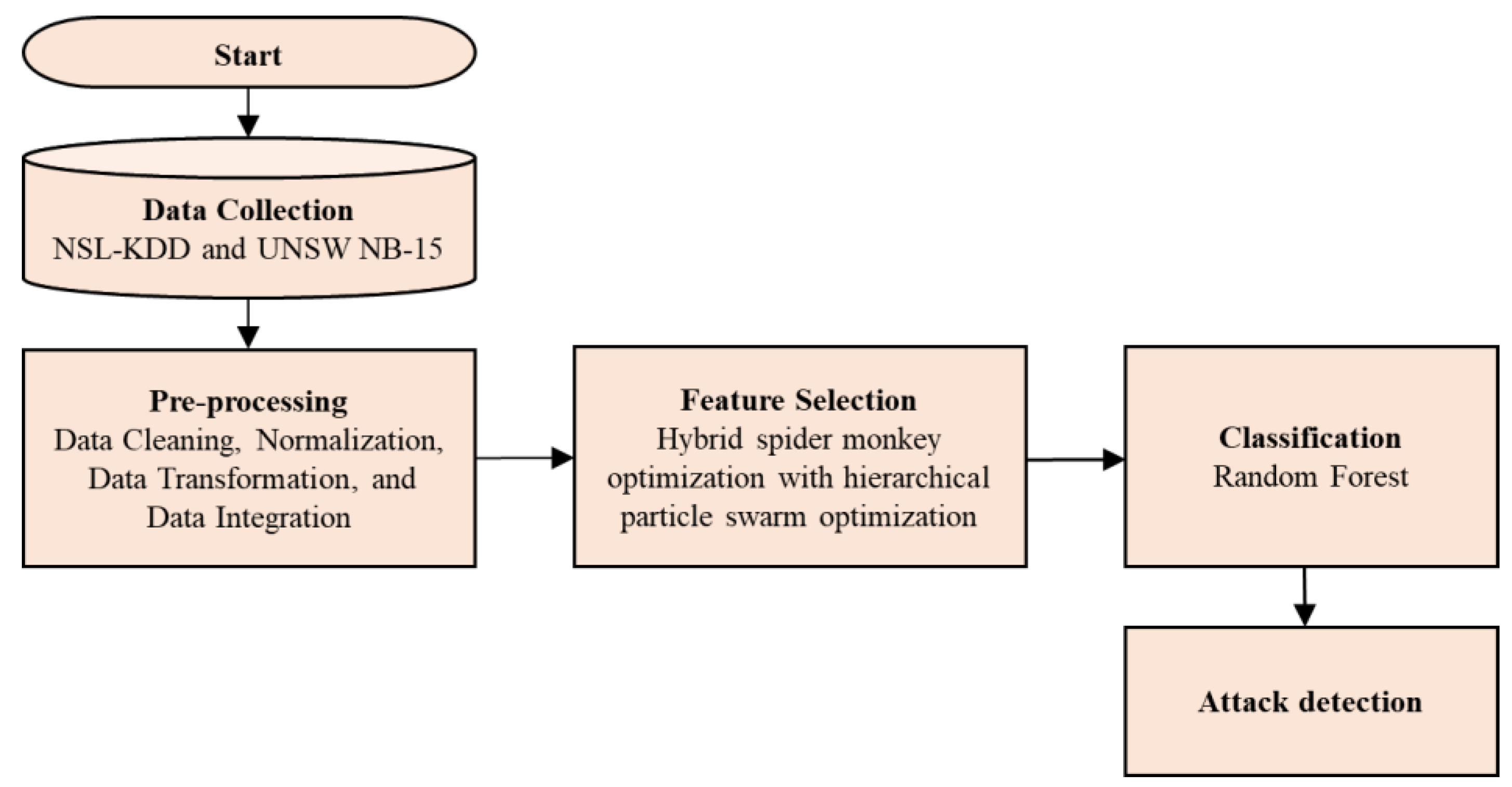
3. Proposed Methodology
3.1. Data Collection
3.2. Preprocessing
3.3. Feature Selection
3.3.1. Spider Monkey Optimisation Algorithm
3.3.2. Particle Swarm Optimization
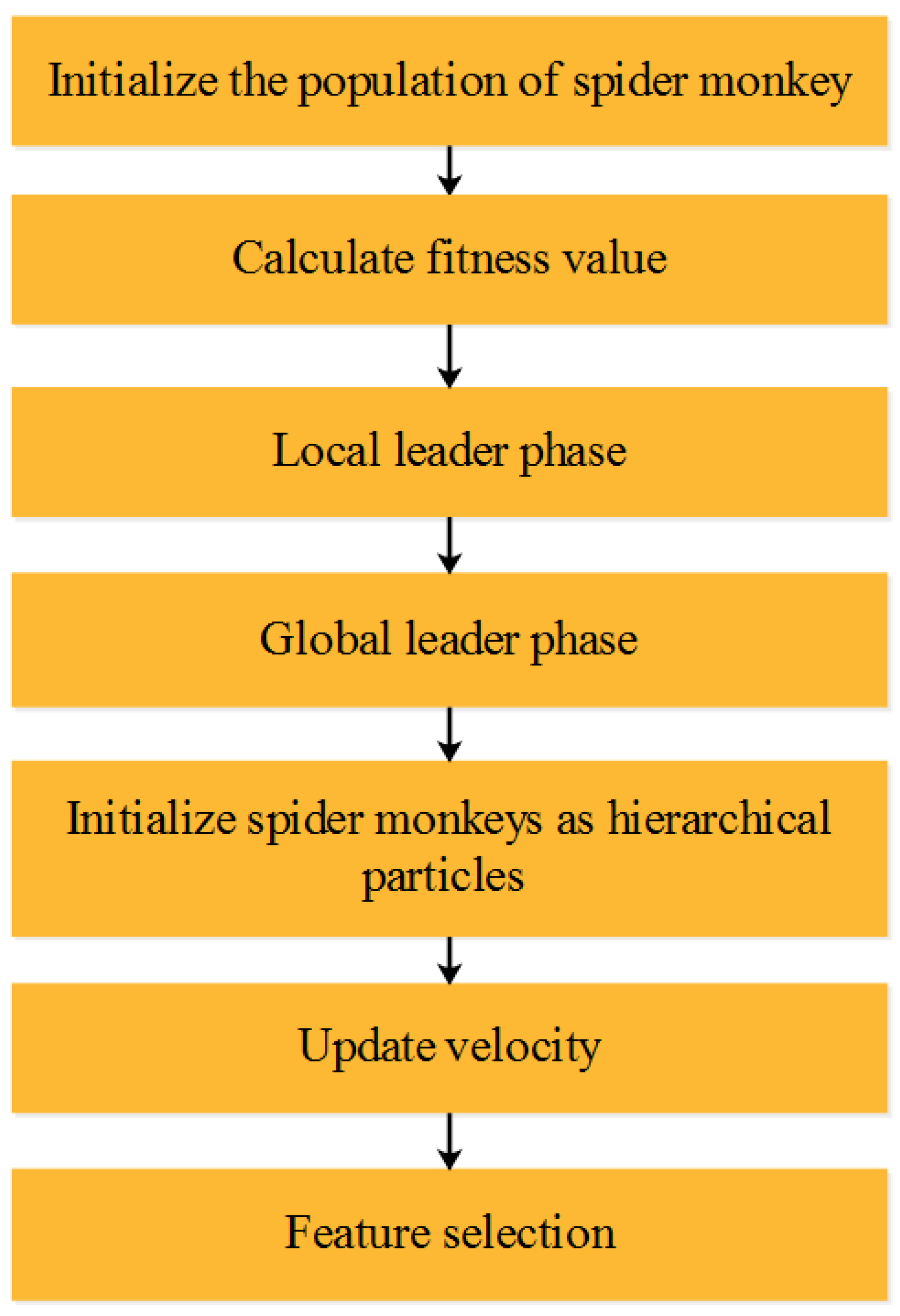
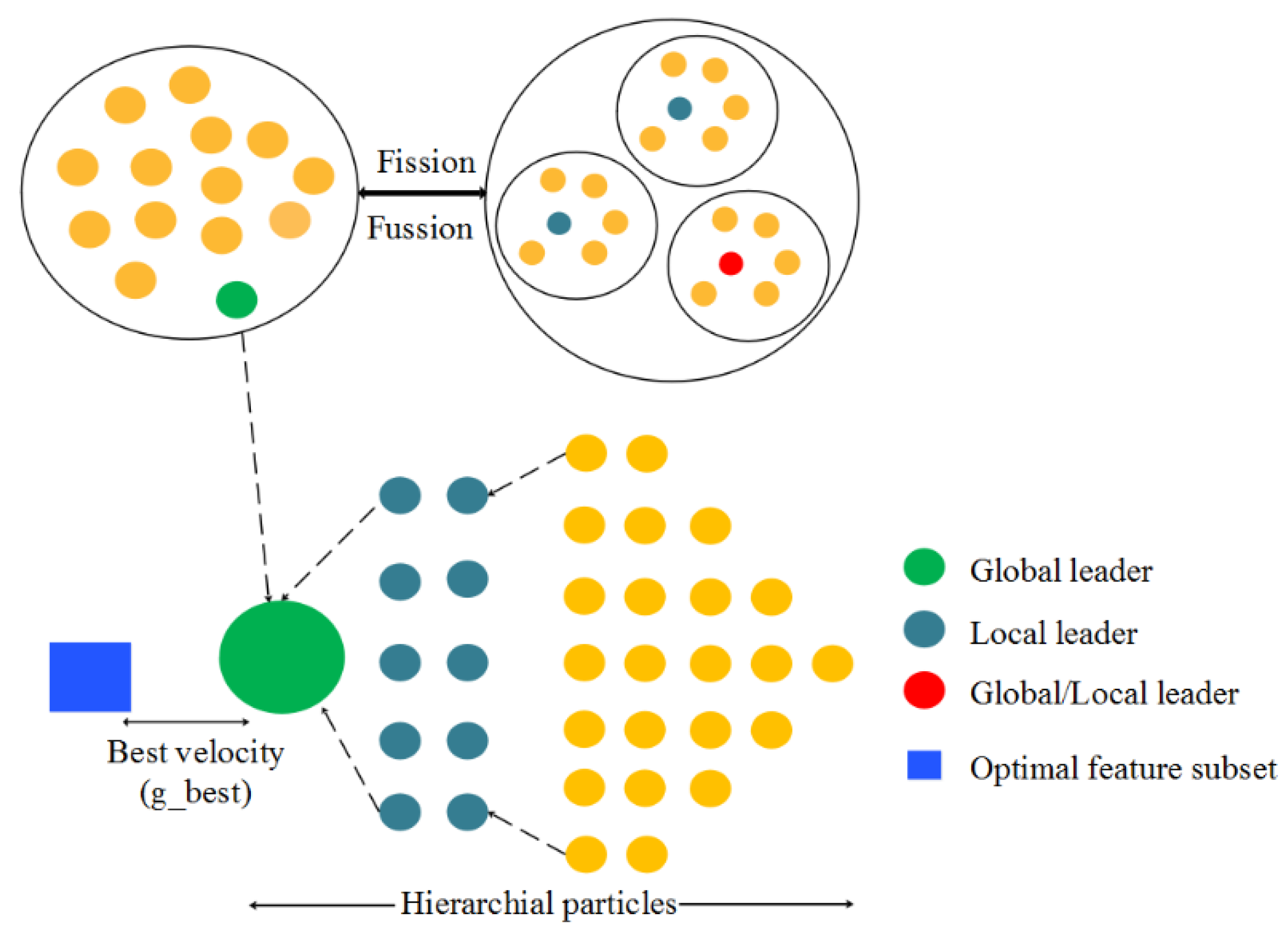
3.3.3. Proposed Hybrid Optimization Algorithm
Population Initialization
Local Leader Phase (LLP)
Global Leader Phase (GLP)
Global Leader Learning (GLL) Phase
Local Leader Learning (LLL) Phase
Local Leader Decision (LLD) Phase
Global Leader Decision (GLD) Phase
| Algorithm 1: Hybrid SMO-HPSO |
| 1: Input: Intrusion detection feature set and population size 2: Output: Optimal feature set 3: Initialize SM Population, Probability, Parameters, Local Leader limit and Global leader limit particles with hierarchy in the population. 4: Calculate the importance of each feature. 5: Evaluate the fitness of all SM. 6: Compute leaders of global and local level leader agents for feature subset. 7: While iteration 8: For 9: Calculate fitness for every particle using Equation (9). 10: Update particle’s local best position as per hierarchical position. 11: Based on hierarchical particle velocity update position of all spider monkeys. 12: End for 13: Select group members by applying greedy selection method 14: Update SM’s global optimal position 15: For 16: Perform local and global leader learning phase using Equations (5) and (6). 17: Update particle’s velocity with hierarchy using Equation (2). 18: Update SM’s global best position. 19: End for 20: End while |
3.4. Classification Using Random Forest
- The trees are grown and are saved as a future reference.
- The RF classifier overcomes the problem of overfitting.
- The important features developed in the model show improvements in accuracy that are generated automatically to classify the attacks.
4. Results and Discussion
4.1. Quantitative Analysis for NSL-KDD Dataset
4.2. Quantitative Analysis for UNSW NB-15 Dataset
4.3. Comparative Analysis
5. Conclusions
Author Contributions
Funding
Institutional Review Board Statement
Informed Consent Statement
Data Availability Statement
Conflicts of Interest
References
- Jia, Y.; Zhong, F.; Alrawais, A.; Gong, B.; Cheng, X. Flowguard: An intelligent edge defense mechanism against IoT DDoS attacks. IEEE Internet Things J. 2020, 7, 9552–9562. [Google Scholar] [CrossRef]
- McDermott, C.D.; Majdani, F.; Petrovski, A.V. Botnet detection in the internet of things using deep learning approaches. In Proceedings of the 2018 International Joint Conference on Neural Networks (IJCNN), Rio de Janeiro, Brazil, 8–13 July 2018; IEEE: Piscataway, NJ, USA, 2018. [Google Scholar] [CrossRef]
- Meidan, Y.; Bohadana, M.; Mathov, Y.; Mirsky, Y.; Shabtai, A.; Breitenbacher, D.; Elovici, Y. N-baiot—Network-based detection of IoT botnet attacks using deep autoencoders. IEEE Pervasive Comput. 2018, 17, 12–22. [Google Scholar] [CrossRef]
- Imamverdiyev, Y.; Abdullayeva, F. Deep learning method for denial of service attack detection based on restricted Boltzmann machine. Big Data 2018, 6, 159–169. [Google Scholar] [CrossRef]
- Habib, M.; Aljarah, I.; Faris, H. A modified multi-objective particle swarm optimizer-based Lévy flight: An approach toward intrusion detection in Internet of Things. Arab. J. Sci. Eng. 2020, 45, 6081–6108. [Google Scholar] [CrossRef]
- Deshmukh-Bhosale, S.; Sonavane, S.S. Design of intrusion detection system for wormhole attack detection in internet of things. In Advanced Computing and Intelligent Engineering: Proceedings of the ICACIE, Bhubaneswar, India, 22–24 December 2018; Pati, B., Panigrahi, C., Buyya, R., Li, K.C., Eds.; Springer: Singapore, 2018; Volume 1, pp. 513–523. [Google Scholar] [CrossRef]
- Jaramillo, L.E.S. Malware detection and mitigation techniques: Lessons learned from Mirai DDOS attack. J. Inf. Syst. Eng. Manag. 2018, 3, 19. [Google Scholar] [CrossRef]
- Aldaej, A. Enhancing cyber security in modern internet of things (IoT) using intrusion prevention algorithm for IoT (IPAI). IEEE Access 2019. [Google Scholar] [CrossRef]
- Li, J.; Liu, M.; Xue, Z.; Fan, X.; He, X. RTVD: A real-time volumetric detection scheme for DDoS in the Internet of Things. IEEE Access 2020, 8, 36191–36201. [Google Scholar] [CrossRef]
- De Souza, C.A.; Westphall, C.B.; Machado, R.B.; Sobral, J.B.M.; dos Santos Vieira, G. Hybrid approach to intrusion detection in fog-based IoT environments. Comput. Netw. 2020, 180, 107417. [Google Scholar] [CrossRef]
- Elmasry, W.; Akbulut, A.; Zaim, A.H. Evolving deep learning architectures for network intrusion detection using a double PSO metaheuristic. Comput. Netw. 2020, 168, 107042. [Google Scholar] [CrossRef]
- Su, T.; Sun, H.; Zhu, J.; Wang, S.; Li, Y. BAT: Deep learning methods on network intrusion detection using NSL-KDD dataset. IEEE Access 2020, 8, 29575–29585. [Google Scholar] [CrossRef]
- Kareem, S.S.; Mostafa, R.R.; Hashim, F.A.; El-Bakry, H.M. An effective feature selection model using hybrid metaheuristic algorithms for iot intrusion detection. Sensors 2022, 22, 1396. [Google Scholar] [CrossRef] [PubMed]
- Awotunde, J.B.; Chakraborty, C.; Adeniyi, A.E. Intrusion detection in industrial internet of things network-based on deep learning model with rule-based feature selection. Wirel. Commun. Mob. Comput. 2021, 2021, 7154587. [Google Scholar] [CrossRef]
- Keserwani, P.K.; Govil, M.C.; Pilli, E.S.; Govil, P. A smart anomaly-based intrusion detection system for the Internet of Things (IoT) network using GWO–PSO–RF model. J. Reliab. Intell. Environ. 2021, 7, 3–21. [Google Scholar] [CrossRef]
- Nie, L.; Wu, Y.; Wang, X.; Guo, L.; Wang, G.; Gao, X.; Li, S. Intrusion detection for secure social internet of things based on collaborative edge computing: A generative adversarial network-based approach. IEEE Transact. Comput. Soc. Syst. 2021, 9, 134–145. [Google Scholar] [CrossRef]
- Jeyaselvi, M.; Dhanaraj, R.K.; Sathya, M.; Memon, F.H.; Krishnasamy, L.; Dev, K.; Ziyue, W.; Qureshi, N.M.F. A highly secured intrusion detection system for IoT using EXPSO-STFA feature selection for LAANN to detect attacks. Clust. Comput. 2022, 1–16. [Google Scholar] [CrossRef]
- Nimbalkar, P.; Kshirsagar, D. Feature selection for intrusion detection system in Internet-of-Things (IoT). ICT Express 2021, 7, 177–181. [Google Scholar] [CrossRef]
- Gao, X.; Shan, C.; Hu, C.; Niu, Z.; Liu, Z. An adaptive ensemble machine learning model for intrusion detection. IEEE Access 2019, 7, 82512–82521. [Google Scholar] [CrossRef]
- Çavuşoğlu, Ü. A new hybrid approach for intrusion detection using machine learning methods. Appl. Intell. 2019, 49, 2735–2761. [Google Scholar] [CrossRef]
- Wu, Y.; Lee, W.; Xu, Z.; Ni, M. Large-scale and robust intrusion detection model combining improved deep belief network with feature-weighted SVM. IEEE Access 2020, 8, 98600–98611. [Google Scholar] [CrossRef]
- Kumar, V.; Sinha, D.; Das, A.K.; Pandey, S.C.; Goswami, R.T. An integrated rule based intrusion detection system: Analysis on UNSW-NB15 data set and the real time online dataset. Clust. Comput. 2020, 23, 1397–1418. [Google Scholar] [CrossRef]
- Ramaiah, M.; Chandrasekaran, V.; Ravi, V.; Kumar, N. An intrusion detection system using optimized deep neural network architecture. Transact. Emerg. Telecommun. Technol. 2021, 32, e4221. [Google Scholar] [CrossRef]
- Ajdani, M.; Ghaffary, H. Design network intrusion detection system using support vector machine. Int. J. Commun. Syst. 2021, 34, e4689. [Google Scholar] [CrossRef]
- Hsu, C.M.; Azhari, M.Z.; Hsieh, H.Y.; Prakosa, S.W.; Leu, J.S. Robust network intrusion detection scheme using long-short term memory based convolutional neural networks. Mob. Netw. Appl. 2021, 26, 1137–1144. [Google Scholar] [CrossRef]
- Kasongo, S.M.; Sun, Y. A deep learning method with filter based feature engineering for wireless intrusion detection system. IEEE Access 2019, 7, 38597–38607. [Google Scholar] [CrossRef]
- Jiang, H.; He, Z.; Ye, G.; Zhang, H. Network intrusion detection based on PSO-XGboost model. IEEE Access 2020, 8, 58392–58401. [Google Scholar] [CrossRef]
- Alazzam, H.; Sharieh, A.; Sabri, K.E. A feature selection algorithm for intrusion detection system based on pigeon inspired optimizer. Exp. Syst. Appl. 2020, 148, 113249. [Google Scholar] [CrossRef]
- Ingre, B.; Yadav, A. Performance analysis of NSL-KDD dataset using ANN. In Proceedings of the 2015 International Conference on Signal Processing and Communication Engineering Systems, Guntur, India, 2–3 January 2015; IEEE: Piscataway, NJ, USA, 2015; pp. 92–96. [Google Scholar] [CrossRef]
- Janarthanan, T.; Zargari, S. Feature selection in UNSW-NB15 and KDDCUP’99 datasets. In Proceedings of the 2017 IEEE 26th International Symposium on Industrial Electronics (ISIE), Edinburgh, UK, 19–21 June 2017; IEEE: Piscataway, NJ, USA, 2017; pp. 1881–1886. [Google Scholar] [CrossRef]


| NSL-KDD Dataset | Abnormal | Normal | Total | |||
|---|---|---|---|---|---|---|
| DoS | Probing | R2L | U2R | |||
| KDD Test+ | 7458 | 2754 | 2421 | 200 | 9711 | 22,544 |
| KDD Train+ | 45,927 | 11,656 | 995 | 52 | 67,343 | 125,973 |
| UNSW Dataset | ||||||
| Type | No. of Records | |||||
| Normal | 2,218,761 | |||||
| Attacks | 321,283 | |||||
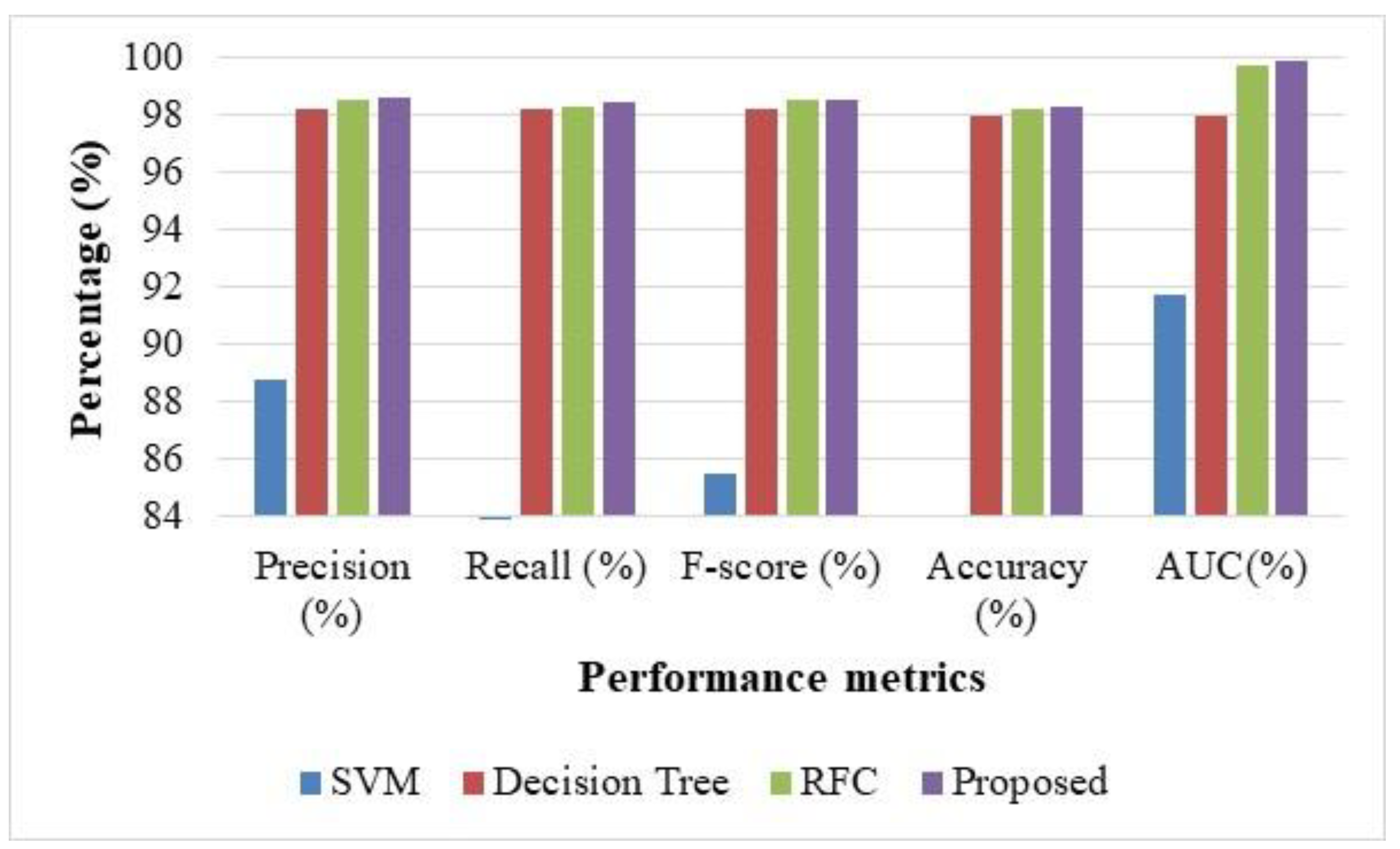
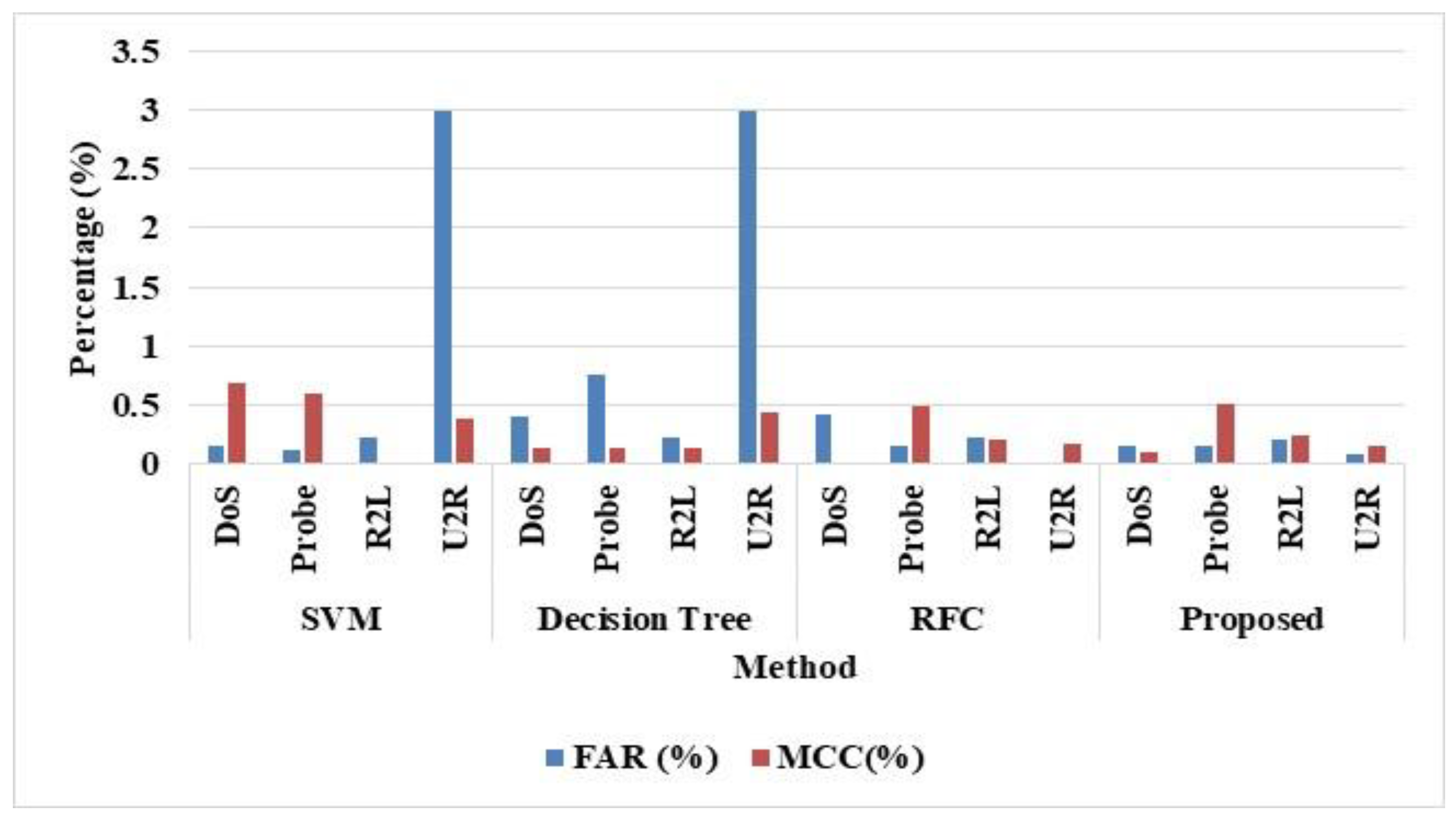
| Methods | Precision (%) | Recall (%) | F-Score (%) | Accuracy (%) | FAR (%) | AUC (%) | MCC (%) |
|---|---|---|---|---|---|---|---|
| SVM | 88.81 | 82.41 | 85.48 | 84.06 | 0.28 | 91.70 | 0.51 |
| Decision Tree | 98.22 | 98.18 | 98.21 | 97.95 | 0.45 | 97.96 | 0.22 |
| RFC | 98.56 | 98.27 | 98.49 | 98.17 | 0.21 | 99.68 | 0.61 |
| Proposed | 98.61 | 98.41 | 98.56 | 98.31 | 0.21 | 99.87 | 0.17 |
| Methods | Class | Precision (%) | Recall (%) | F1 Measure (%) | Accuracy (%) | AUC (%) |
|---|---|---|---|---|---|---|
| SVM | DoS | 97.44 | 82.88 | 89.56 | 91.61 | 97.17 |
| Probe | 87.62 | 91.48 | 89.33 | 92.82 | 97.1 | |
| R2L | 89.31 | 64.09 | 67.11 | 83.37 | 67.2 | |
| U2R | 89.2 | 72.2 | 77.27 | 99.51 | 97.37 | |
| DT | DoS | 99.46 | 99.67 | 99.57 | 99.63 | 99.63 |
| Probe | 98.83 | 98.72 | 98.77 | 99.22 | 98.69 | |
| R2L | 96.79 | 96.24 | 96.51 | 97.55 | 97.58 | |
| U2R | 86.77 | 83.71 | 84.41 | 99.58 | 83.71 | |
| RFC | DoS | 99.86 | 99.71 | 99.82 | 99.81 | 99.96 |
| Probe | 98.92 | 98.71 | 98.81 | 99.26 | 99.67 | |
| R2L | 97.26 | 96.55 | 96.79 | 97.77 | 99.41 | |
| U2R | 96.64 | 85.21 | 89.13 | 99.7 | 97.62 | |
| Proposed | DoS | 99.78 | 99.66 | 99.72 | 99.75 | 99.98 |
| Probe | 99.34 | 99.3 | 99.29 | 99.34 | 99.89 | |
| R2L | 97.19 | 96.64 | 96.69 | 97.85 | 99.66 | |
| U2R | 99.75 | 97.74 | 99.78 | 99.76 | 99.87 |
| Methods | Precision (%) | Recall (%) | F-Score (%) | Accuracy (%) | FAR (%) | AUC (%) | MCC (%) |
|---|---|---|---|---|---|---|---|
| SVM | 89.36 | 85.93 | 88.73 | 85.88 | 0.88 | 94.25 | 0.43 |
| Decision Tree | 90.77 | 88.85 | 90.40 | 88.87 | 1.10 | 95.53 | 0.11 |
| RFC | 92.57 | 91.33 | 91.84 | 91.65 | 0.21 | 98.44 | 0.22 |
| Proposed | 94.19 | 93.32 | 94.12 | 99.18 | 0.15 | 99.78 | 0.19 |
| Authors | Dataset | Method | Accuracy (%) | Precision (%) | Recall (%) | F-Measure (%) |
|---|---|---|---|---|---|---|
| Elmasry et al. [11] | NSL-KDD | DNN | 97.72 | 99.6 | 96.38 | 97.96 |
| LSTM-RNN | 98.8 | 99.7 | 98.18 | 98.94 | ||
| Su et al. [12] | BAT-MC | 84.25 | - | - | - | |
| Gao et al. [19] | Ensemble Learning | 85.2 | 86.5 | 85.2 | 84.9 | |
| Çavuşoğlu [20] | Stacking-ensemble technique | 99.78 | 90 | - | 92.68 | |
| Ramaiah et al. [23] | Optimized Deep Neural Network Architecture | 98 | 98 | 98 | 98 | |
| Hsu et al. [25] | LSTM-based CNN | 98.64 | - | - | - | |
| Kumar et al. [22] | UNSW NB-15 | Integrated rule based Model | 83.8 | - | - | 87.95 |
| Alazzam et al. [28] | Pigeon-Inspired Optimizer | 86.9 | - | 86.6 | 86.4 | |
| Proposed Method | NSL-KDD | SMO-HPSO | 99.175 | 99.015 | 98.335 | 98.87 |
| UNSW NB-15 | 99.18 | 94.19 | 93.32 | 94.12 |
Publisher’s Note: MDPI stays neutral with regard to jurisdictional claims in published maps and institutional affiliations. |
© 2022 by the authors. Licensee MDPI, Basel, Switzerland. This article is an open access article distributed under the terms and conditions of the Creative Commons Attribution (CC BY) license (https://creativecommons.org/licenses/by/4.0/).
Share and Cite
Ethala, S.; Kumarappan, A. A Hybrid Spider Monkey and Hierarchical Particle Swarm Optimization Approach for Intrusion Detection on Internet of Things. Sensors 2022, 22, 8566. https://doi.org/10.3390/s22218566
Ethala S, Kumarappan A. A Hybrid Spider Monkey and Hierarchical Particle Swarm Optimization Approach for Intrusion Detection on Internet of Things. Sensors. 2022; 22(21):8566. https://doi.org/10.3390/s22218566
Chicago/Turabian StyleEthala, Sandhya, and Annapurani Kumarappan. 2022. "A Hybrid Spider Monkey and Hierarchical Particle Swarm Optimization Approach for Intrusion Detection on Internet of Things" Sensors 22, no. 21: 8566. https://doi.org/10.3390/s22218566
APA StyleEthala, S., & Kumarappan, A. (2022). A Hybrid Spider Monkey and Hierarchical Particle Swarm Optimization Approach for Intrusion Detection on Internet of Things. Sensors, 22(21), 8566. https://doi.org/10.3390/s22218566






