Information Security and Privacy in Railway Transportation: A Systematic Review
Abstract
1. Introduction
1.1. Security and Privacy in Railway Transportation
1.2. Contribution and Plan of the Article
2. Research Methodology
2.1. Definition of the Review Scope
- Focus: To gain a broad view of the field, the literature review focuses on all types of academic articles, ranging from theoretical approaches to more practical solutions.
- Goal: This review investigates which procedures and solutions have been proposed by the scientific community to address the security and privacy aspects of railway transportation, which are the challenges identified in the field, and which are the future research directions.
- Organisation: The review is organised using a conceptual structure, i.e., grouping similar ideas from different authors in order to easily guide the reader through the topic.
- Perspective: In this review, we adopt a neutral but critical position regarding the articles studied from the literature.
- Audience: It is intended for researchers, practitioners and stakeholders in the field of railway transportation, information security and/or privacy protection.
- Coverage: This literature review provides exhaustive coverage of the available, published scientific literature.
2.2. Conceptualisation of the Topic
2.3. Literature Search
2.3.1. Database Selection
2.3.2. Keyword Search
2.3.3. Literature Evaluation
- . The publication was written in English.
- . The publication was peer-reviewed (to avoid grey literature).
- . The full-text of the publication was available.
- . The publication was published in a Q1 journal (according to the ISI-JCR) or its number of citations was above the 75th percentile regarding the citations of other articles published that year.
- . The publication was relevant to the subject. In this review, relevancy means that the publication contextualises information security and privacy aspects in railway passenger transportation, and that the keyword terms are properly used in their lexical context. This excludes publications in which the terms only appear in the references section, are tangentially mentioned, or result from typos.
2.3.4. Backward and Forward Search
2.4. Literature Analysis and Synthesis
2.5. Definition of a Research Agenda
3. Results
- Enhanced systems for increasing safety and security in railways: Articles proposing techniques, methods or tools to improve the railway infrastructure from an information security or privacy perspective.
- Cybersecurity issues and challenges in railways: Articles reviewing or describing issues and/or challenges related to information security or privacy in railways.
- Users’ cybersecurity awareness in railway infrastructures: Articles addressing or evaluating the awareness of users on information security or privacy in the railway infrastructure.
3.1. Enhanced Systems for Increasing Safety and Security in Railways
3.2. Cybersecurity Issues and Challenges in Railways
3.3. Users’ Cybersecurity Awareness in Railway Infrastructures
4. Discussion
4.1. Technical Aspects
4.2. Architectures of the Future
4.3. Privacy Challenges
4.4. Cybersecurity Frameworks and Standards
4.5. Training and Awareness
5. Limitations
6. Conclusions and Further Work
- Developing, implementing and deploying IoT devices and WSNs that contain a security layer to minimise the success of malicious attacks. The evaluation of the added overhead, in terms of time and cost, will need to be studied.
- Integrating novel, emerging communication technologies. To prevent using old, vulnerable communication technologies, the latest trends on the topic, including low-power communication, need to be carefully examined. The impact of this migration requires attention, not only from the security perspective, but also in terms of efficiency and cost.
- Embracing AI techniques with security-by-design and privacy-by-design for future-ready operations. Since many decision-making systems are AI-based, the incorporation of security and privacy requirements is mandatory to protect not only the railway services, but also the users. Moreover, AI-based techniques could be used to detect anomalous situations and anticipate incoming attacks.
- Migrating classical data architectures to scalable cloud environments to increase the security of complex applications by sharing responsibilities, e.g., computational capabilities and data security. Consideration of big data technologies with a focus on security and privacy aspects will be desirable.
- Integrating and deploying blockchain-based applications to increase security and limit the impacts of cyberattacks, while bringing resiliency, transparency and data traceability within the system. In this context, using smart contracts might set the conditions to access the blockchain and establish the rules for performing communication among different parties.
- Fostering standardisation initiatives to overcome the alarming current lack of interoperability. Defining common ontologies, protocols and standards is required to unify railway systems, efficiently manage data and hence, homogenise cyberdefence procedures. Relatedly, the adoption of the already-mentioned CLC/TS 50701 standard might be a promising move towards the harmonisation of good practices.
- Developing complete guidelines for risk assessment and risk mitigation in railways. Understanding potential attacks, assessing vulnerabilities and applying the corresponding corrective measures is key to avoiding catastrophic consequences.
- Balancing open and comprehensible data policies with privacy-preserving mechanisms, including the fulfilment of user consent and the ubiquitous nature of intelligent railway transportation services. Additionally, developing information security standards is suitable.
- Educating people on the right use of technology by means of personalised training campaigns targeted at users. These initiatives should clearly make users aware of the cybersecurity concerns and provide the necessary skills to use prevention and mitigation techniques when deemed convenient.
- Make policy makers aware of the need to foster efficient regulations to handle information properly, while always considering privacy and ethical aspects.
Author Contributions
Funding
Institutional Review Board Statement
Informed Consent Statement
Data Availability Statement
Acknowledgments
Conflicts of Interest
Abbreviations
| AI | Artificial Intelligence |
| BTM | Balise Transmission Module |
| CBTC | Communication-Based Train Control |
| CPS | Cyber-Physical Systems |
| DoS | Denial of Service |
| ERTMS | European Rail Traffic Management System |
| ETCS | European Train Control System |
| HSR | High-Speed Railway |
| IACS | Industrial Automation and Control Systems |
| IT | Information Technology |
| ICT | Information and Communication Technologies |
| IoT | Internet of Things |
| ITS | Intelligent Transportation Systems |
| LTE | Long Term Evolution |
| LTE-R | Long Term Evolution for Railway systems |
| MIMO | Multiple-Input Multiple-Output |
| ML | Machine Learning |
| OT | Operational Technology |
| QoS | Quality of Service |
| SIEM | Security Information and Event Management |
| TCAS | Train Collision Avoidance Systems |
| WiMAX | Worldwide Interoperability for Microwave Access |
| WSN | Wireless Sensor Network |
References
- Guerrero-Ibáñez, J.; Zeadally, S.; Contreras-Castillo, J. Sensor Technologies for Intelligent Transportation Systems. Sensors 2018, 18, 1212. [Google Scholar] [CrossRef] [PubMed]
- Butler, L.; Yigitcanlar, T.; Paz, A. Barriers and risks of Mobility-as-a-Service (MaaS) adoption in cities: A systematic review of the literature. Cities 2021, 109, 103036. [Google Scholar] [CrossRef]
- Xue, M.; Yuan, C.; Wu, H.; Zhang, Y.; Liu, W. Machine learning security: Threats, countermeasures, and evaluations. IEEE Access 2020, 8, 74720–74742. [Google Scholar] [CrossRef]
- Solanas, A.; Batista, E.; Casino, F.; Papageorgiou, A.; Patsakis, C. Privacy-Oriented Analysis of Ubiquitous Computing Systems: A 5-D Approach. In Security of Ubiquitous Computing Systems; Springer: Berlin, Germany, 2021; pp. 201–213. [Google Scholar]
- Ometov, A.; Molua, O.L.; Komarov, M.; Nurmi, J. A Survey of Security in Cloud, Edge, and Fog Computing. Sensors 2022, 22, 927. [Google Scholar] [CrossRef]
- Batista, E.; Moncusi, M.A.; López-Aguilar, P.; Martínez-Ballesté, A.; Solanas, A. Sensors for Context-Aware Smart Healthcare: A Security Perspective. Sensors 2021, 21, 6886. [Google Scholar] [CrossRef] [PubMed]
- Sollins, K.R. IoT Big Data Security and Privacy vs. Innovation. IEEE Internet Things J. 2019, 6, 1628–1635. [Google Scholar] [CrossRef]
- Vom Brocke, J.; Simons, A.; Niehaves, B.; Reimer, K.; Plattfaut, R.; Cleven, A. Reconstructing the Giant: On the Importance of Rigour in Documenting the Literature Search Process. In Proceedings of the 17th European Conference on Information Systems (ECIS); AISeL: Verona, Italy, 2009; pp. 2206–2217. [Google Scholar]
- Cooper, H.M. Organizing Knowledge Syntheses: A Taxonomy of Literature Reviews. Knowl. Soc. 1988, 1, 104–126. [Google Scholar] [CrossRef]
- Cherdantseva, Y.; Hilton, J. Information Security and Information Assurance: Discussion about the Meaning, Scope, and Goals. In Standards and Standardization: Concepts, Methodologies, Tools, and Applications; IGI Global: Hershey, PA, USA, 2015; pp. 1204–1235. [Google Scholar]
- International Organization for Standardization. ISO/IEC 27000:2018(E): Information Technology—Security Techniques—Information Security Management Systems—Overview and Vocabulary; Technical Report; International Organization for Standardization: Geneva, Switzerland, 2018. [Google Scholar]
- Jajodia, S.; Samarati, P.; Yung, M. Encyclopedia of Cryptography, Security and Privacy; Springer: Berlin, Germany, 2019. [Google Scholar]
- Ai, B.; Guan, K.; Rupp, M.; Kurner, T.; Cheng, X.; Yin, X.F.; Wang, Q.; Ma, G.Y.; Li, Y.; Xiong, L.; et al. Future railway services-oriented mobile communications network. IEEE Commun. Mag. 2015, 53, 78–85. [Google Scholar] [CrossRef]
- Alawad, H.; Kaewunruen, S. Wireless Sensor Networks: Toward Smarter Railway Stations. Infrastructures 2018, 3, 24. [Google Scholar] [CrossRef]
- Bellini, E.; Marrone, S.; Marulli, F. Cyber Resilience Meta-Modelling: The Railway Communication Case Study. Electronics 2021, 10, 583. [Google Scholar] [CrossRef]
- Cabalquinto, E.; Hutchins, B. “It should allow me to opt in or opt out”: Investigating smartphone use and the contending attitudes of commuters towards geolocation data collection. Telemat. Inform. 2020, 51, 101403. [Google Scholar] [CrossRef]
- Chernov, A.V.; Butakova, M.A.; Karpenko, E.V. Security incident detection technique for multilevel intelligent control systems on railway transport in Russia. In Proceedings of the 2015 23rd Telecommunications Forum Telfor (TELFOR), Belgrade, Serbia, 24–26 November 2015; IEEE: Belgrade, Serbia, 2015; pp. 1–4. [Google Scholar]
- Daly, A.; Hess, S.; Patruni, B.; Potoglou, D.; Rohr, C. Using ordered attitudinal indicators in a latent variable choice model: A study of the impact of security on rail travel behaviour. Transportation 2012, 39, 267–297. [Google Scholar] [CrossRef]
- Dong, P.; Zheng, T.; Du, X.; Zhang, H.; Guizani, M. SVCC-HSR: Providing Secure Vehicular Cloud Computing for Intelligent High-Speed Rail. IEEE Netw. 2018, 32, 64–71. [Google Scholar] [CrossRef]
- Duan, Q.; Quynh, N.V.; Abdullah, H.M.; Almalaq, A.; Duc Do, T.; Abdelkader, S.M.; Mohamed, M.A. Optimal Scheduling and Management of a Smart City Within the Safe Framework. IEEE Access 2020, 8, 161847–161861. [Google Scholar] [CrossRef]
- Falahati, A.; Shafiee, E. Improve Safety and Security of Intelligent Railway Transportation System Based on Balise Using Machine Learning Algorithm and Fuzzy System. Int. J. Intell. Transp. Syst. Res. 2022, 20, 117–131. [Google Scholar] [CrossRef]
- Farooq, J.; Soler, J. Radio Communication for Communications-Based Train Control (CBTC): A Tutorial and Survey. IEEE Commun. Surv. Tutor. 2017, 19, 1377–1402. [Google Scholar] [CrossRef]
- Figueroa-Lorenzo, S.; Goya, J.; Añorga, J.; Adin, I.n.; Mendizabal, J.; Arrizabalaga, S. Alarm Collector in Smart Train Based on Ethereum Blockchain Events-Log. IEEE Internet Things J. 2021, 8, 13306–13315. [Google Scholar] [CrossRef]
- Fraga-Lamas, P.; Fernández-Caramés, T.M.; Castedo, L. Towards the Internet of Smart Trains: A Review on Industrial IoT-Connected Railways. Sensors 2017, 17, 1457. [Google Scholar] [CrossRef]
- Hatzivasilis, G.; Fysarakis, K.; Ioannidis, S.; Hatzakis, I.; Vardakis, G.; Papadakis, N.; Spanoudakis, G. SPD-Safe: Secure Administration of Railway Intelligent Transportation Systems. Electronics 2021, 10, 92. [Google Scholar] [CrossRef]
- Hodge, V.J.; O’Keefe, S.; Weeks, M.; Moulds, A. Wireless Sensor Networks for Condition Monitoring in the Railway Industry: A Survey. IEEE Trans. Intell. Transp. Syst. 2015, 16, 1088–1106. [Google Scholar] [CrossRef]
- Jang, H.S.; Lim, H.; Jeon, J.Y. Control of interior surface materials for speech privacy in high-speed train cabins. Indoor Air 2017, 27, 670–679. [Google Scholar] [CrossRef] [PubMed]
- Kim, S.; Won, Y.; Park, I.H.; Eun, Y.; Park, K.J. Cyber-Physical Vulnerability Analysis of Communication-Based Train Control. IEEE Internet Things J. 2019, 6, 6353–6362. [Google Scholar] [CrossRef]
- Kour, R.; Aljumaili, M.; Karim, R.; Tretten, P. eMaintenance in railways: Issues and challenges in cybersecurity. Proc. Inst. Mech. Eng. Part F J. Rail Rapid Transit 2019, 233, 1012–1022. [Google Scholar] [CrossRef]
- Kour, R.; Karim, R. Cybersecurity workforce in railway: Its maturity and awareness. J. Qual. Maint. Eng. 2021, 27, 453–464. [Google Scholar] [CrossRef]
- Lazarescu, M.T.; Poolad, P. Asynchronous Resilient Wireless Sensor Network for Train Integrity Monitoring. IEEE Internet Things J. 2021, 8, 3939–3954. [Google Scholar] [CrossRef]
- Lopez, I.; Aguado, M. Cyber security analysis of the European train control system. IEEE Commun. Mag. 2015, 53, 110–116. [Google Scholar] [CrossRef]
- Ma, Z.; Chen, X.; Xiao, M.; Karagiannidis, G.K.; Fan, P. Interference Control for Railway Wireless Communication Systems: Techniques, Challenges, and Trends. IEEE Veh. Technol. Mag. 2020, 15, 51–58. [Google Scholar] [CrossRef]
- Mcmahon, P.; Zhang, T.; Dwight, R. Requirements for Big Data Adoption for Railway Asset Management. IEEE Access 2020, 8, 15543–15564. [Google Scholar] [CrossRef]
- Moreno, J.; Riera, J.M.; Haro, L.d.; Rodriguez, C. A survey on future railway radio communications services: Challenges and opportunities. IEEE Commun. Mag. 2015, 53, 62–68. [Google Scholar] [CrossRef]
- Mu, Y.; Rezaeibagha, F.; Huang, K. Policy-Driven Blockchain and Its Applications for Transport Systems. IEEE Trans. Serv. Comput. 2020, 13, 230–240. [Google Scholar] [CrossRef]
- Patil, S.; Patruni, B.; Potoglou, D.; Robinson, N. Public preference for data privacy—A pan-European study on metro/train surveillance. Transp. Res. Part A Policy Pract. 2016, 92, 145–161. [Google Scholar] [CrossRef]
- Potoglou, D.; Robinson, N.; Kim, C.W.; Burge, P.; Warnes, R. Quantifying individuals’ trade-offs between privacy, liberty and security: The case of rail travel in UK. Transp. Res. Part A Policy Pract. 2010, 44, 169–181. [Google Scholar] [CrossRef]
- Pouw, C.A.S.; Toschi, F.; van Schadewijk, F.; Corbetta, A. Monitoring physical distancing for crowd management: Real-time trajectory and group analysis. PLoS ONE 2020, 15, e0240963. [Google Scholar] [CrossRef] [PubMed]
- Rao, J.; Gao, S.; Li, M.; Huang, Q. A privacy-preserving framework for location recommendation using decentralized collaborative machine learning. Trans. GIS 2021, 25, 1153–1175. [Google Scholar] [CrossRef]
- Sikora, P.; Malina, L.; Kiac, M.; Martinasek, Z.; Riha, K.; Prinosil, J.; Jirik, L.; Srivastava, G. Artificial Intelligence-Based Surveillance System for Railway Crossing Traffic. IEEE Sens. J. 2021, 21, 15515–15526. [Google Scholar] [CrossRef]
- Sun, W.; Yu, F.R.; Tang, T.; Bu, B. Energy-Efficient Communication-Based Train Control Systems With Packet Delay and Loss. IEEE Trans. Intell. Transp. Syst. 2016, 17, 452–468. [Google Scholar] [CrossRef]
- Thaduri, A.; Aljumaili, M.; Kour, R.; Karim, R. Cybersecurity for eMaintenance in railway infrastructure: Risks and consequences. Int. J. Syst. Assur. Eng. Manag. 2019, 10, 149–159. [Google Scholar] [CrossRef]
- Wang, Y.; Zhang, W.; Wang, X.; Guo, W.; Khan, M.K.; Fan, P. Improving the Security of LTE-R for High-Speed Railway: From the Access Authentication View. IEEE Trans. Intell. Transp. Syst. 2022, 23, 1332–1346. [Google Scholar] [CrossRef]
- Wu, Y.; Wei, Z.; Weng, J.; Deng, R.H. Position Manipulation Attacks to Balise-Based Train Automatic Stop Control. IEEE Trans. Veh. Technol. 2018, 67, 5287–5301. [Google Scholar] [CrossRef]
- Wu, Y.; Weng, J.; Tang, Z.; Li, X.; Deng, R.H. Vulnerabilities, Attacks, and Countermeasures in Balise-Based Train Control Systems. IEEE Trans. Intell. Transp. Syst. 2017, 18, 814–823. [Google Scholar] [CrossRef]
- Wu, Y.; Ye, D.; Wei, Z.; Wang, Q.; Tan, W.; Deng, R.H. Situation-Aware Authenticated Video Broadcasting Over Train-Trackside WiFi Networks. IEEE Internet Things J. 2019, 6, 1617–1627. [Google Scholar] [CrossRef]
- Zeng, D.; Chawathe, S.S.; Huang, H.; Wang, F.Y. Protecting Transportation Infrastructure. IEEE Intell. Syst. 2007, 22, 8–11. [Google Scholar] [CrossRef]
- Zhang, L.; Cheng, L.; Alsokhiry, F.; Mohamed, M.A. A Novel Stochastic Blockchain-Based Energy Management in Smart Cities Using V2S and V2G. IEEE Trans. Intell. Transp. Syst. 2022, 1, 1–8. [Google Scholar] [CrossRef]
- Zhao, H.; Dai, X.; Ding, L.; Cui, D.; Ding, J.; Chai, T. Resilient Cooperative Control for High-Speed Trains Under Denial-of-Service Attacks. IEEE Trans. Veh. Technol. 2021, 70, 12427–12436. [Google Scholar] [CrossRef]
- Zheng, Q.; Wang, X.; Khurram Khan, M.; Zhang, W.; Gupta, B.B.; Guo, W. A Lightweight Authenticated Encryption Scheme Based on Chaotic SCML for Railway Cloud Service. IEEE Access 2018, 6, 711–722. [Google Scholar] [CrossRef]
- Redmon, J.; Divvala, S.; Girshick, R.; Farhadi, A. You only look once: Unified, real-time object detection. In Proceedings of the IEEE Conference on Computer Vision and Pattern Recognition, Las Vegas, NV, USA, 27–30 June 2016; pp. 779–788. [Google Scholar]
- Sun, Y.; Zhang, R.; Wang, X.; Gao, K.; Liu, L. A Decentralizing Attribute-Based Signature for Healthcare Blockchain. In Proceedings of the 2018 27th International Conference on Computer Communication and Networks (ICCCN), Hangzhou, China, 30 July–2 August 2018; pp. 1–9. [Google Scholar]
- Guo, R.; Shi, H.; Zhao, Q.; Zheng, D. Secure Attribute-Based Signature Scheme With Multiple Authorities for Blockchain in Electronic Health Records Systems. IEEE Access 2018, 6, 11676–11686. [Google Scholar] [CrossRef]
- European Commission. Directive (EU) 2016/1148 of the European Parliament and of the Council of 6 July 2016. Off. J. Eur. Union 2016, L 194/1. Available online: https://www.legislation.gov.uk/eudr/2016/1148/contents (accessed on 29 August 2022).
- ENISA. Railway Cybersecurity Report. 2020. Available online: https://www.enisa.europa.eu/publications/railway-cybersecurity (accessed on 1 September 2022).
- ENISA. Railway Cybersecurity—Good Practices in Cyber Risk Management. 2021. Available online: https://www.enisa.europa.eu/publications/railway-cybersecurity-good-practices-in-cyber-risk-management (accessed on 1 September 2022).
- He, R.; Ai, B.; Wang, G.; Guan, K.; Zhong, Z.; Molisch, A.F.; Briso-Rodriguez, C.; Oestges, C.P. High-Speed Railway Communications: From GSM-R to LTE-R. IEEE Veh. Technol. Mag. 2016, 11, 49–58. [Google Scholar] [CrossRef]
- Shafiullah, G.M.; Ali, A.B.M.S.; Thompson, A.; Wolfs, P.J. Predicting Vertical Acceleration of Railway Wagons Using Regression Algorithms. IEEE Trans. Intell. Transp. Syst. 2010, 11, 290–299. [Google Scholar] [CrossRef]
- Alawad, H.; Kaewunruen, S.; An, M. Learning From Accidents: Machine Learning for Safety at Railway Stations. IEEE Access 2020, 8, 633–648. [Google Scholar] [CrossRef]
- López-Aguilar, P.; Solanas, A. An Effective Approach to the Cross-Border Exchange of Digital Evidence Using Blockchain. In Proceedings of the 9th International Conference on Applications in Electronics Pervading Industry, Environment and Society, Pisa, Italy, 11–13 September 2021; pp. 1–5. [Google Scholar]
- Sharma, P.K.; Park, J.H. Blockchain based hybrid network architecture for the smart city. Future Gener. Comput. Syst. 2018, 86, 650–655. [Google Scholar] [CrossRef]
- Demissie, B.F.; Ranise, S. Assessing the Effectiveness of the Shared Responsibility Model for Cloud Databases: The Case of Google’s Firebase. In Proceedings of the IEEE International Conference on Smart Data Services, Chicago, IL, USA, 5–10 September 2021; pp. 121–131. [Google Scholar]
- Stojkoska, B.R.; Nikolovski, Z. Data compression for energy efficient IoT solutions. In Proceedings of the 2017 25th Telecommunication Forum (TELFOR), Belgrade, Serbia, 21–22 November 2017; pp. 1–4. [Google Scholar]
- Zhang, W.; Cheung, S.; Chen, M. Hiding privacy information in video surveillance system. In Proceedings of the IEEE International Conference on Image Processing 2005, Genoa, Italy, 11–14 September 2005; Volume 3, pp. 2–868. [Google Scholar]
- Hassan, M.U.; Rehmani, M.H.; Chen, J. Differential Privacy Techniques for Cyber Physical Systems: A Survey. IEEE Commun. Surv. Tutor. 2020, 22, 746–789. [Google Scholar] [CrossRef]
- Shi, Y.; Piao, C.; Zheng, L. Differential-Privacy-Based Correlation Analysis in Railway Freight Service Applications. In Proceedings of the 2017 International Conference on Cyber-Enabled Distributed Computing and Knowledge Discovery (CyberC), Nanjing, China, 12–14 October 2017; pp. 35–39. [Google Scholar]
- Bhati, B.S.; Ivanchev, J.; Bojic, I.; Datta, A.; Eckhoff, D. Utility-Driven k-Anonymization of Public Transport User Data. IEEE Access 2021, 9, 23608–23623. [Google Scholar] [CrossRef]
- Riahi Sfar, A.; Challal, Y.; Moyal, P.; Natalizio, E. A Game Theoretic Approach for Privacy Preserving Model in IoT-Based Transportation. IEEE Trans. Intell. Transp. Syst. 2019, 20, 4405–4414. [Google Scholar] [CrossRef]
- National Institute of Standards and Technology. Framework for Improving Critical Infrastructure Cybersecurity. 2018. Available online: https://nvlpubs.nist.gov/nistpubs/CSWP/NIST.CSWP.04162018.pdf (accessed on 1 September 2022).
- International Organization for Standardization and International Electrotechnical Commission. ISO/IEC 27000 Family Standards. Available online: https://www.iso.org/search.html?q=27000 (accessed on 1 September 2022).
- International Society of Automation and International Electrotechnical Commission. ISA/IEC 62443 Series of Standards. 2018. Available online: https://www.isa.org/standards-and-publications/isa-standards/isa-iec-62443-series-of-standards (accessed on 1 September 2022).
- CLC/TS 50701. Railway Applications—Cybersecurity. Available online: https://www.en-standard.eu/clc/ts-50701-2021-railway-applications-cybersecurity/ (accessed on 1 September 2022).
- Taherdoost, H. Understanding Cybersecurity Frameworks and Information Security Standards—A Review and Comprehensive Overview. Electronics 2022, 11, 2181. [Google Scholar] [CrossRef]
- A Body of the European Union. Shift2Rail. 2020. Available online: https://rail-research.europa.eu/about-shift2rail (accessed on 1 September 2022).
- EU Horizon 2020 Research and Innovation Programme. CYbersecurity in the Railway Sector (CYRAIL). 2018. Available online: https://cyrail.eu/ (accessed on 1 September 2022).
- López-Aguilar, P.; Solanas, A. Human Susceptibility to Phishing Attacks Based on Personality Traits: The Role of Neuroticism. In Proceedings of the IEEE 45th Annual Computers, Software, and Applications Conference, Madrid, Spain, 12–16 July 2021; pp. 1363–1368. [Google Scholar]
- Transportation Research Board and National Academies of Sciences, Engineering, and Medicine. Cybersecurity in Transit Systems; The National Academies Press: Washington, DC, USA, 2022. [Google Scholar]
- Anti-Phishing Working Group. Phishing Activity Trends Report—1st Quarter 2022; Technical Report; Anti-Phishing Working Group: USA, 2022. [Google Scholar]
- Belcher, S.; Belcher, T.; Greenwald, E.; Thomas, B. Is the Transit Industry Prepared for the Cyber Revolution? Policy Recommendations to Enhance Surface Transit Cyber Preparedness; Technical Report; San José State University and Mineta Transportation Institute: San Jose, CA, USA, 2020. [Google Scholar]
- Fortune Business Insight. Railway Cyber Security Market Size, Share & COVID-19 Impact Analysis, by Security Type, by Type, and Regional Forecasts, 2021–2028; Technical Report; Fortune Business Insight: Pune, India, 2022. [Google Scholar]
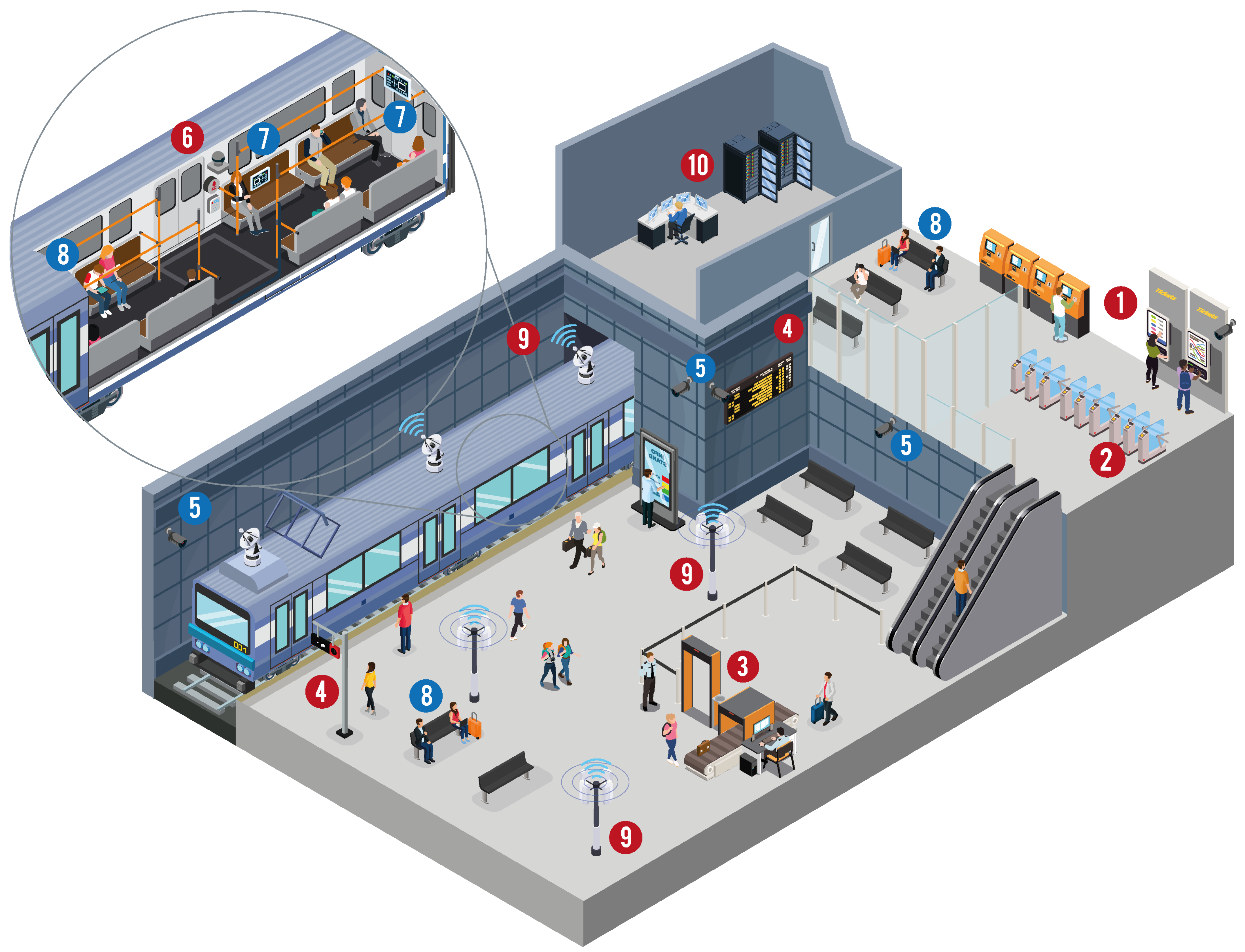
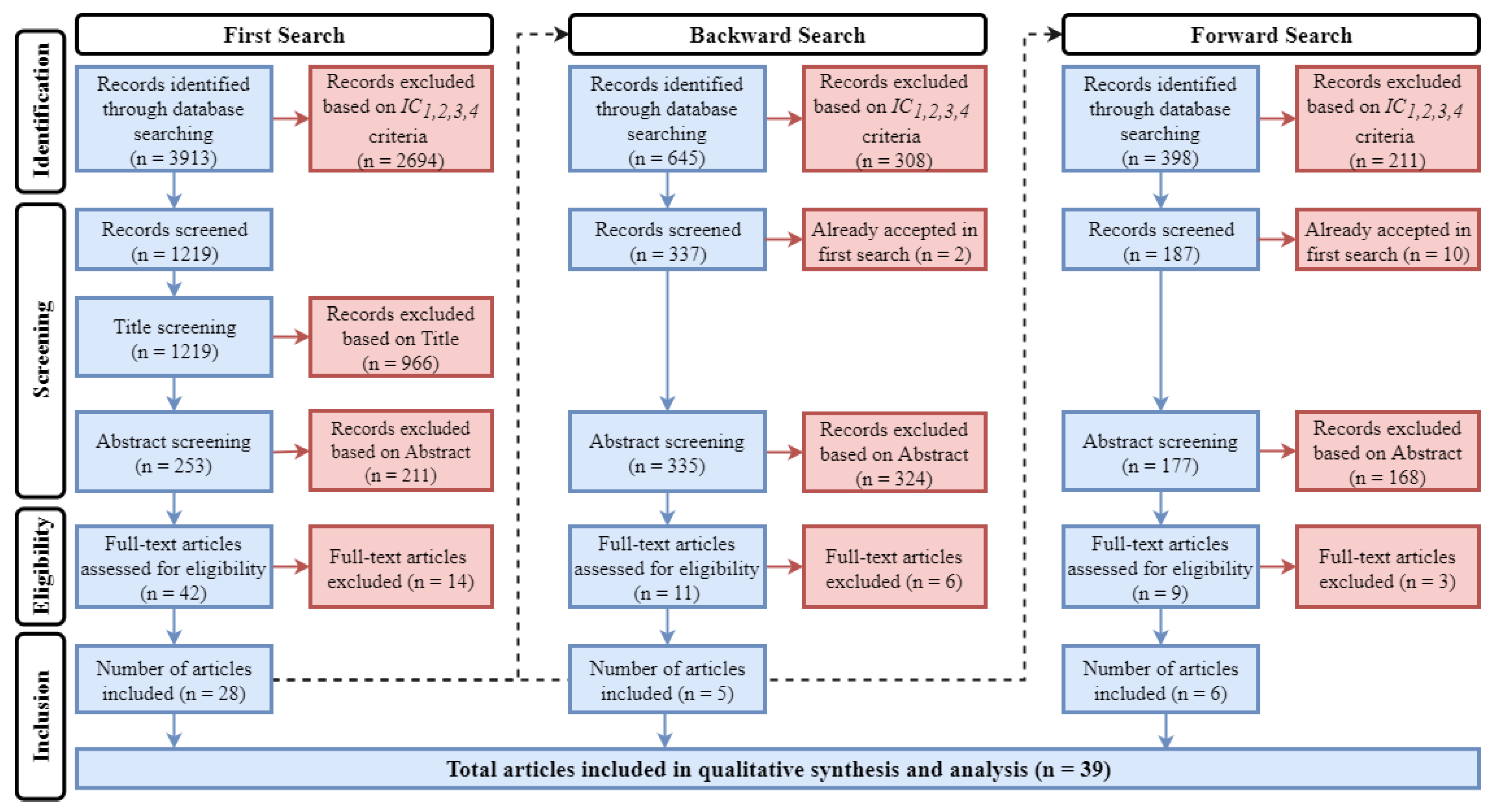
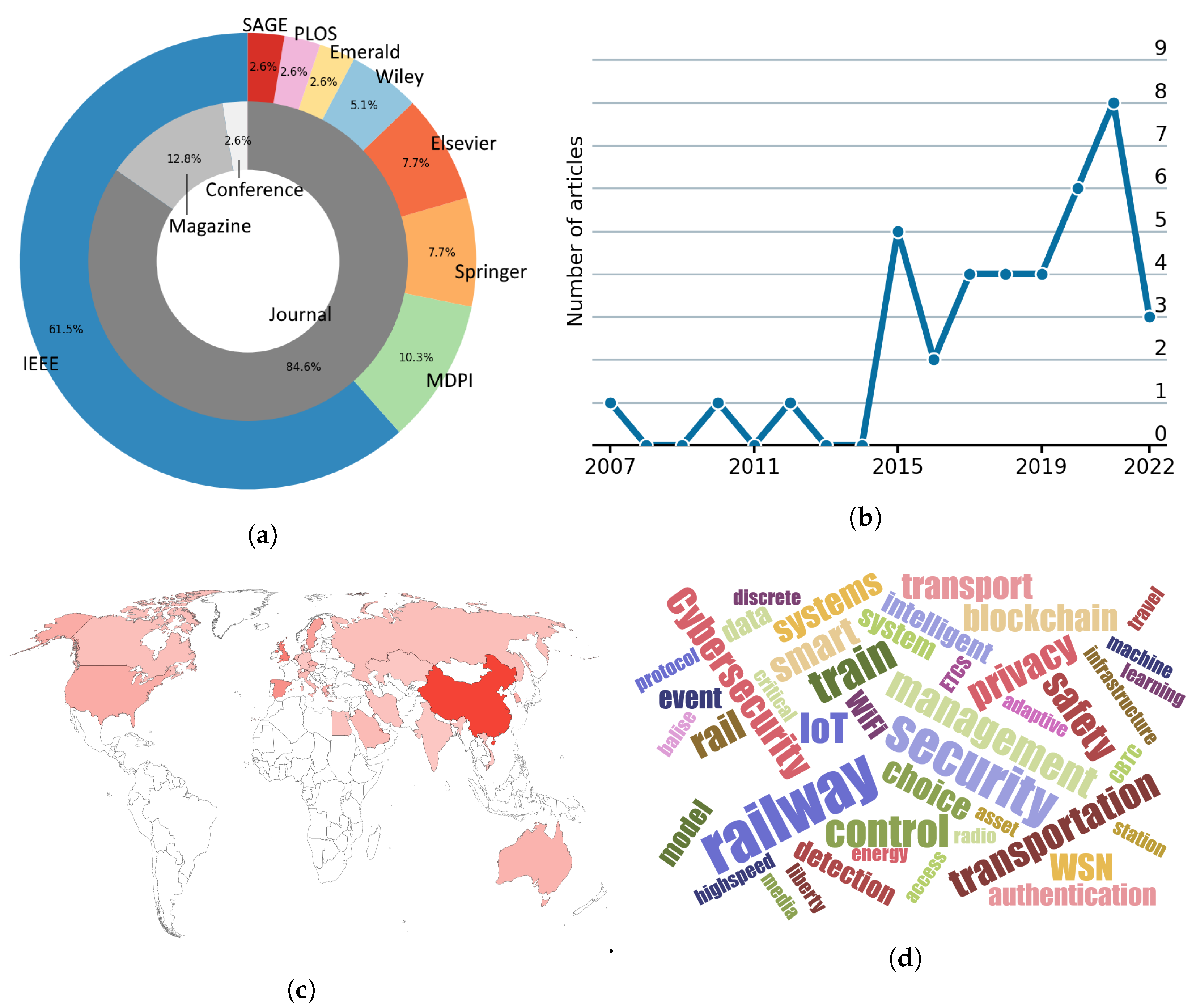
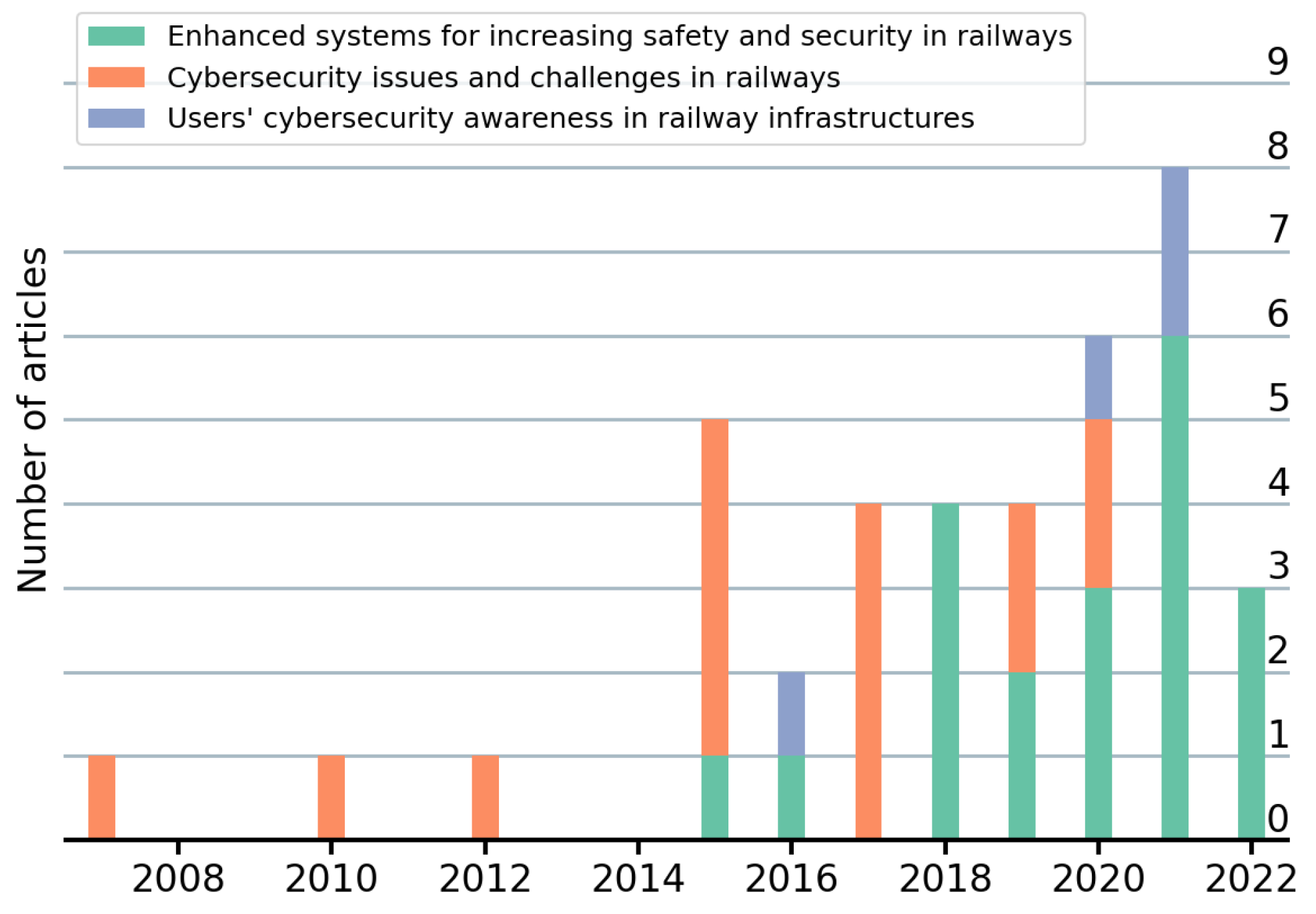

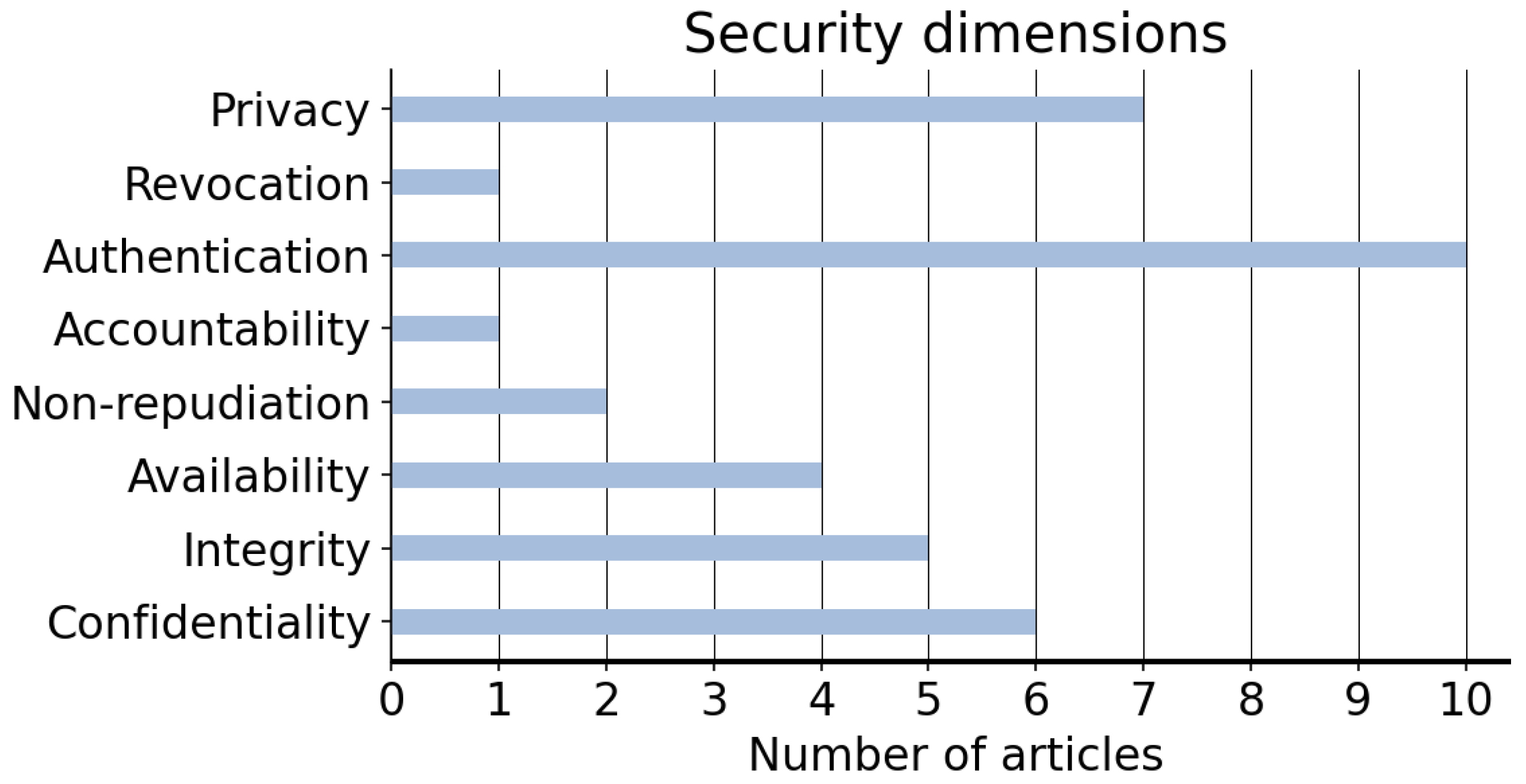
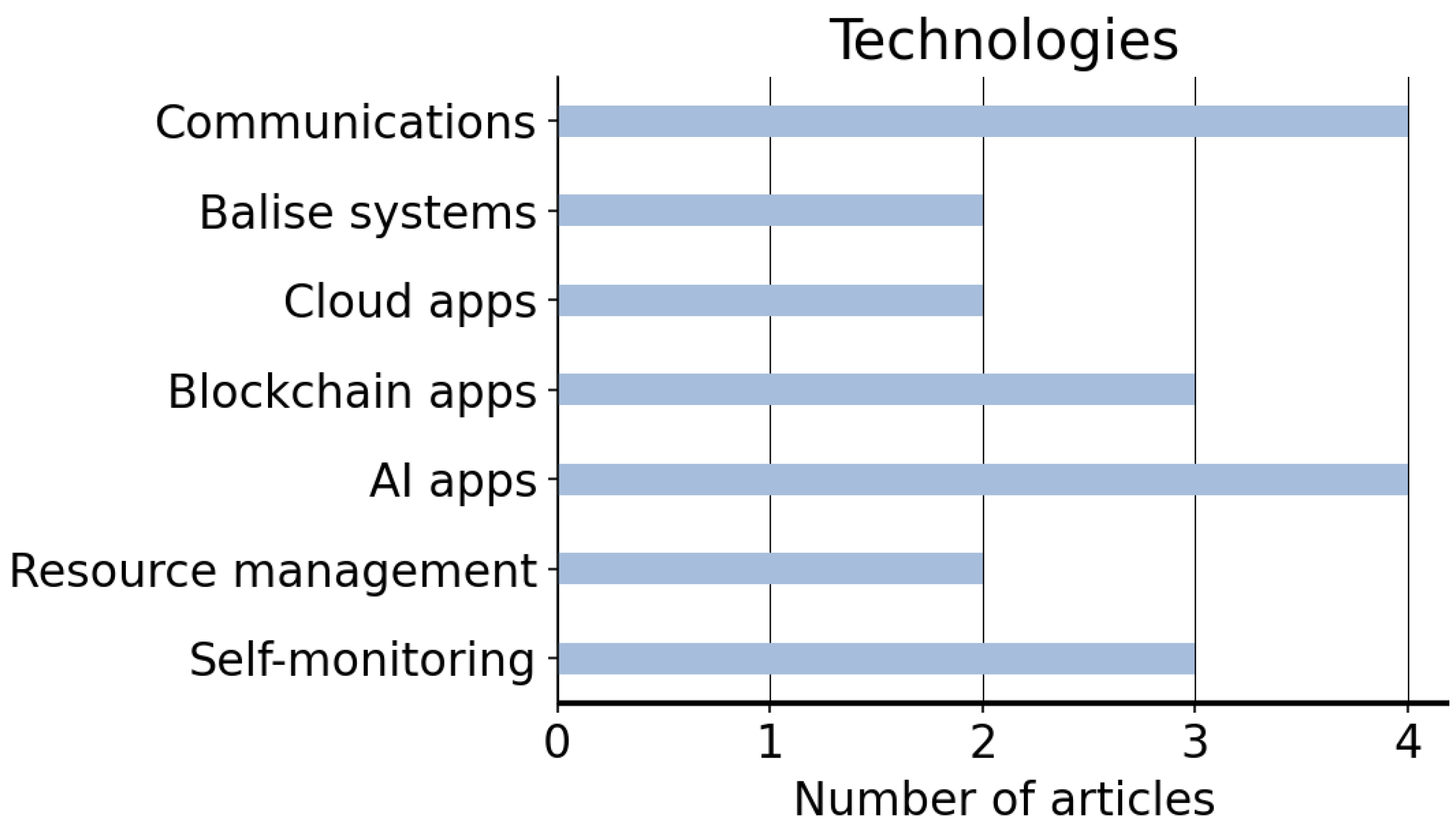
| ID | Research Question | Objective | Discussion |
|---|---|---|---|
| RQ1 | Which are the current procedures and tools to address the information security and privacy aspects of railway transportation? | The purpose is to summarise the current instruments to digitally protect all the actors involved in railway transportation. | Section 3.1 |
| RQ2 | Which are the main challenges that have been identified for making railway transportation more secure and private? | The aim is to collect, organise, classify and summarise the main challenges found in the literature for further discussion. | Section 3.2 |
| RQ3 | Are users aware of the security and privacy aspects involved in railway transportation? | The goal is to assess whether society, according to the analysed literature, is aware of the potential security and privacy issues of their railway transportation usage. | Section 3.3 |
| RQ4 | Are current practices efficient enough to counter the sophistication of cyberattacks? | The goal is to verify whether current procedures and technological solutions are sufficient to efficiently fight cyberattacks. | Section 4 |
| RQ5 | Which technologies or strategies could be used to deal with the identified challenges? | The purpose is to provide a fruitful discussion to improve railway transportation from an information security and privacy perspective. | Section 4 |
| RQ6 | Which issues remain open? | According to the knowledge extracted from the literature, the goal is to pinpoint the main limitations in the field to set the ground for further research. | Section 4 and Section 6 |
| Reference | Title | Source | Year | Search |
|---|---|---|---|---|
| Ai et al. [13] | Future Railway Services-Oriented Mobile Communications Network | IEEE Communications Magazine | 2015 | Backward |
| Alawad et al. [14] | Wireless Sensor Networks: Toward Smarter Railway Stations | Infrastructures | 2018 | First |
| Bellini et al. [15] | Cyber Resilience Meta-Modelling: The Railway Communication Case Study | Electronics | 2021 | First |
| Cabalquinto et al. [16] | It should allow me to opt in or opt out: Investigating smartphone use and the contending attitudes of commuters towards geolocation data collection | Telematics and Informatics | 2020 | First |
| Chernov et al. [17] | Security Incident Detection Technique for Multilevel Intelligent Control Systems on Railway Transport in Russia | Proc. Telecommunications Forum | 2015 | First |
| Daly et al. [18] | Using ordered attitudinal indicators in a latent variable choice model: a study of the impact of security on rail travel behaviour | Transportation | 2012 | First |
| Dong et al. [19] | SVCC-HSR: Providing Secure Vehicular Cloud Computing for Intelligent High-Speed Rail | IEEE Network | 2018 | First |
| Duan et al. [20] | Optimal Scheduling and Management of a Smart City Within the Safe Framework | IEEE Access | 2020 | First |
| Falahati et al. [21] | Improve Safety and Security of Intelligent Railway Transportation System Based on Balise Using Machine Learning Algorithm and Fuzzy System | International Journal of Intelligent Transportation Systems Research | 2022 | Forward |
| Farooq et al. [22] | Radio Communication for Communications-Based Train Control (CBTC): A Tutorial and Survey | IEEE Communications Surveys & Tutorials | 2017 | Backward |
| Figueroa-Lorenzo et al. [23] | Alarm Collector in Smart Train Based on Ethereum Blockchain Events-Log | IEEE Internet of Things Journal | 2021 | First |
| Fraga-Lamas et al. [24] | Towards the Internet of Smart Trains: A Review on Industrial IoT-Connected Railways | Sensors | 2017 | First |
| Hatzivasilis et al. [25] | SPD-Safe: Secure Administration of Railway Intelligent Transportation Systems | Electronics | 2021 | First |
| Hodge et al. [26] | Wireless Sensor Networks for Condition Monitoring in the Railway Industry: A Survey | IEEE Transactions on Intelligent Transportation Systems | 2015 | Backward |
| Jang et al. [27] | Control of interior surface materials for speech privacy in high-speed train cabins | Indoor Air | 2017 | First |
| Kim et al. [28] | Cyber-Physical Vulnerability Analysis of Communication-Based Train Control | IEEE Internet of Things Journal | 2019 | First |
| Kour et al. [29] | eMaintenance in railways: Issues and challenges in cybersecurity | Proc. Institution of Mechanical Engineers, Part F: Journal of Rail and Rapid Transit | 2019 | First |
| Kour et al. [30] | Cybersecurity workforce in railway: its maturity and awareness | Journal of Quality in Maintenance Engineering | 2021 | First |
| Lazarescu et al. [31] | Asynchronous Resilient Wireless Sensor Network for Train Integrity Monitoring | IEEE Internet of Things Journal | 2021 | First |
| Lopez et al. [32] | Cyber Security Analysis of the European Train Control System | IEEE Communications Magazine | 2015 | First |
| Ma et al. [33] | Interference Control for Railway Wireless Communication Systems: Techniques, Challenges, and Trends | IEEE Vehicular Technology Magazine | 2020 | First |
| Mcmahon et al. [34] | Requirements for Big Data Adoption for Railway Asset Management | IEEE Access | 2020 | First |
| Moreno et al. [35] | A Survey on Future Railway Radio Communications Services: Challenges and Opportunities | IEEE Communications Magazine | 2015 | Backward |
| Mu et al. [36] | Policy-Driven Blockchain and Its Applications for Transport Systems | IEEE Transactions on Services Computing | 2020 | First |
| Patil et al. [37] | Public preference for data privacy – A pan-European study on metro/train surveillance | Transportation Research Part A: Policy and Practice | 2016 | First |
| Potoglou et al. [38] | Quantifying individuals’ trade-offs between privacy, liberty and security: The case of rail travel in UK | Transportation Research Part A: Policy and Practice | 2010 | First |
| Pouw et al. [39] | Monitoring physical distancing for crowd management: Real-time trajectory and group analysis | PLOS ONE | 2020 | First |
| Rao et al. [40] | A privacy-preserving framework for location recommendation using decentralized collaborative machine learning | Transactions in GIS | 2021 | First |
| Sikora et al. [41] | Artificial Intelligence-Based Surveillance System for Railway Crossing Traffic | IEEE Sensors Journal | 2021 | First |
| Sun et al. [42] | Energy-Efficient Communication-Based Train Control Systems With Packet Delay and Loss | IEEE Transactions on Intelligent Transportation Systems | 2016 | Backward |
| Thaduri et al. [43] | Cybersecurity for eMaintenance in railway infrastructure: risks and consequences | Intl. Journal of System Assurance Engineering and Management | 2019 | First |
| Wang et al. [44] | Improving the Security of LTE-R for High-Speed Railway: From the Access Authentication View | IEEE Transactions on Intelligent Transportation Systems | 2022 | Forward |
| Wu et al. [45] | Position Manipulation Attacks to Balise-Based Train Automatic Stop Control | IEEE Transactions on Vehicular Technology | 2018 | Forward |
| Wu et al. [46] | Vulnerabilities, Attacks, and Countermeasures in Balise-Based Train Control Systems | IEEE Transactions on Intelligent Transportation Systems | 2017 | First |
| Wu et al. [47] | Situation-Aware Authenticated Video Broadcasting Over Train-Trackside WiFi Networks | IEEE Internet of Things Journal | 2019 | Forward |
| Zeng et al. [48] | Protecting transportation infrastructure | IEEE Intelligent Systems | 2007 | First |
| Zhang et al. [49] | A Novel Stochastic Blockchain-Based Energy Management in Smart Cities Using V2S and V2G | IEEE Transactions on Intelligent Transportation Systems | 2022 | Forward |
| Zhao et al. [50] | Resilient Cooperative Control for High-Speed Trains Under Denial-of-Service Attacks | IEEE Transactions on Vehicular Technology | 2021 | Forward |
| Zheng et al. [51] | A Lightweight Authenticated Encryption Scheme Based on Chaotic SCML for Railway Cloud Service | IEEE Access | 2018 | First |
| Group | List of Articles | Discussion |
|---|---|---|
| Enhanced systems for increasing safety and security in railways | [13,14,19,20,21,23,25,28,31,34,36,40,41,42,44,45,47,49,50,51] | Section 3.1 |
| Cybersecurity issues and challenges in railways | [17,18,22,24,26,27,29,32,33,35,38,39,43,46,48] | Section 3.2 |
| Users’ cybersecurity awareness in railway infrastructures | [15,16,30,37] | Section 3.3 |
Publisher’s Note: MDPI stays neutral with regard to jurisdictional claims in published maps and institutional affiliations. |
© 2022 by the authors. Licensee MDPI, Basel, Switzerland. This article is an open access article distributed under the terms and conditions of the Creative Commons Attribution (CC BY) license (https://creativecommons.org/licenses/by/4.0/).
Share and Cite
López-Aguilar, P.; Batista, E.; Martínez-Ballesté, A.; Solanas, A. Information Security and Privacy in Railway Transportation: A Systematic Review. Sensors 2022, 22, 7698. https://doi.org/10.3390/s22207698
López-Aguilar P, Batista E, Martínez-Ballesté A, Solanas A. Information Security and Privacy in Railway Transportation: A Systematic Review. Sensors. 2022; 22(20):7698. https://doi.org/10.3390/s22207698
Chicago/Turabian StyleLópez-Aguilar, Pablo, Edgar Batista, Antoni Martínez-Ballesté, and Agusti Solanas. 2022. "Information Security and Privacy in Railway Transportation: A Systematic Review" Sensors 22, no. 20: 7698. https://doi.org/10.3390/s22207698
APA StyleLópez-Aguilar, P., Batista, E., Martínez-Ballesté, A., & Solanas, A. (2022). Information Security and Privacy in Railway Transportation: A Systematic Review. Sensors, 22(20), 7698. https://doi.org/10.3390/s22207698







