AntTrust: An Ant-Inspired Trust Management System for Peer-to-Peer Networks
Abstract
1. Introduction
- A novel trust management system, AntTrust, is proposed using a problem-specific heuristic to increase the success rate of good peers and reduce execution time.
- A reward formula is suggested to recompense peers that provide valid contents and honest recommendations.
- A new formula is introduced for the trust calculation between any two peers in the network based on four parameters: local trust value, recommendation, feedback, and friends’ trust values.
- A well-controlled evaluation framework is presented for evaluating the proposed approach.
- Validation of the proposed system is carried out against well-established trust management paradigms.
2. Related Work
3. Algorithm Design
3.1. Ant Inspiration
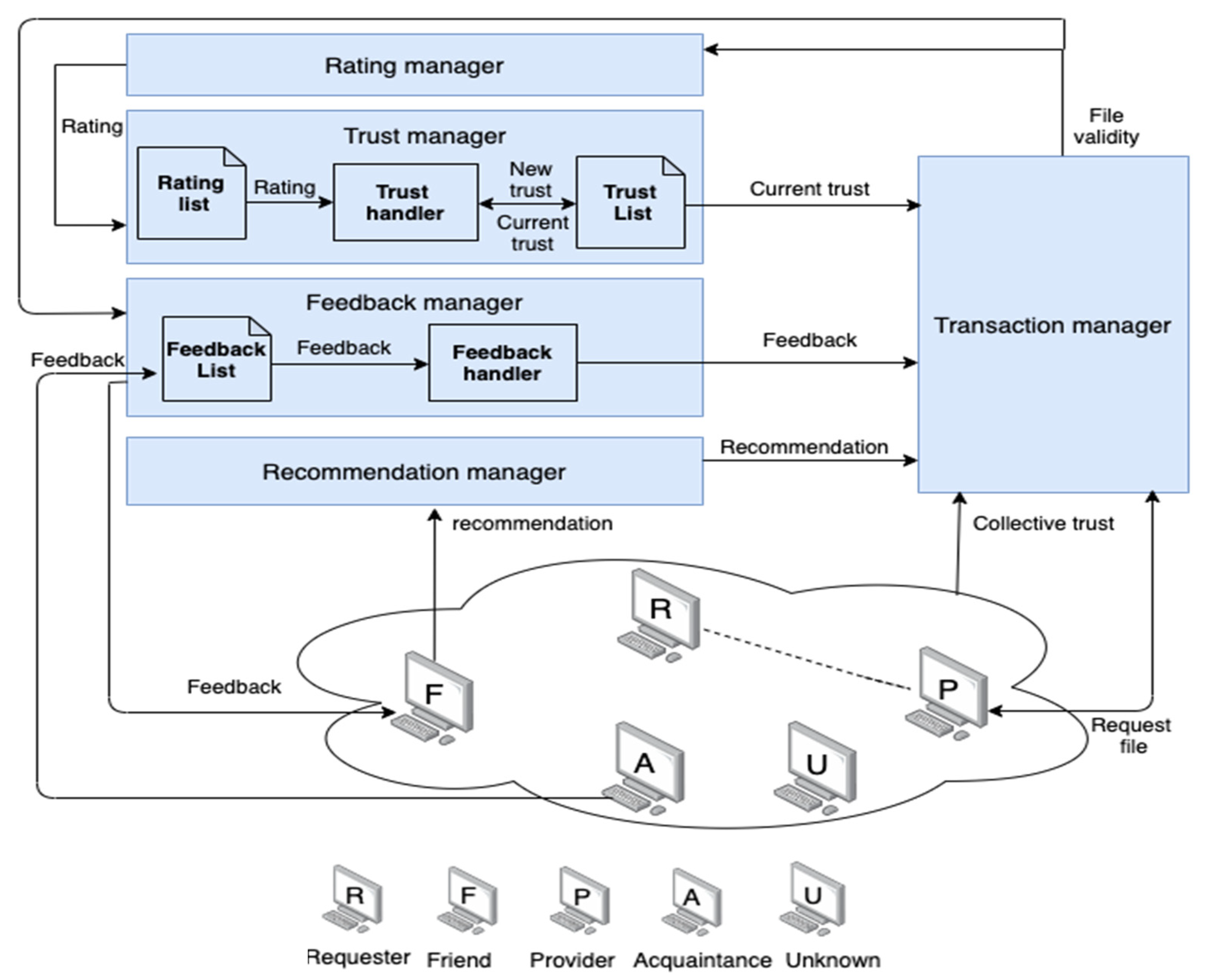
3.2. AntTrust System Architecture
- Rating list (RL): Each peer Pi has an RL, which keeps records of friend IDs, the total number of positive transactions (TP), and the total number of negative transactions (TN) completed with each friend of the peer. The list is dynamically updated once the peer completes a transaction.
- Feedback list (FL): The FL is a two-dimensional matrix maintained by each peer. It keeps track of the total number of positive feedback (TPFoA) events and the total number of negative feedback (TNFoA) events according to the rating received after each transaction performed by a peer’s acquaintance with a friend of the acquaintance, for instance, if peer Pi has n acquaintances and m friends of acquaintances.
- Trust list (TL): This list records the current trust (CT) values of Pi for each of the peer’s friends. The trust value is calculated based on the ratings in the rating list.
- Transaction manager: This component is responsible for selecting the most trustworthy file provider for the requester peer in each transaction by considering four trust parameters (current trust, feedback, recommendations, and collective trust). The Transaction manager receives the current trust located in the trust list (TL) and uses it to select the file provider peer. In the absence of current trust, the selection depends on the recommendation received from the Recommendation manager. In the latter case, feedback (the value received from the Feedback manager) is used to help select a provider peer. If all three of these values are unavailable, the Transaction manager uses collective trust to select a trustworthy file provider. After selecting a trustworthy file provider, the transaction takes place between the requester and the selected file provider. The requester peer then evaluates the received file and submits the file’s validity to the Rating manager and the Feedback manager.
- Rating manager: This component submits either a positive (1) or negative (0) rating for a transaction. These ratings are based on the validity of the received file from the Transaction manager.
- Trust manager: This is the main component in the system. It is responsible for calculating the new trust after each transaction as a function of assigned reward or punishment values. Our system is proactive because it calculates trust after each transaction; thus, there is no need to compute trust before the transaction, which reduces the time taken to calculate trust before any transaction. The calculation of the new trust value differs as a function of the validity of the file received. If the file is valid, the calculation depends on the total number of positive (TP) ratings and the total number of negative (TN) ratings received from the rating list (RL) as a reward to the file provider. If the file is invalid, the calculation is based on subtracting a punishment from the current trust value. The component then records the calculated new trust in the trust list (TL).
- Feedback manager: This component is responsible for exchanging ratings and feedbacks. The feedback list (FL) is used to record the received feedback from acquaintances in a list. The feedback handler is responsible for calculating the feedback using information that is received from the FL whenever necessary as a function of the total number of instances of positive feedback and negative feedback.
- Recommendation manager: This component is responsible for retrieving recommendations about a specific file provider from a friend with current trust values above the best-friend threshold (δf), where δf is a positive real number.
3.3. Definitions
- Requester (Pq): A peer that requests a file in a transaction.
- Provider (Pv): A peer that has the requested file in a transaction.
- Friend: A peer Pj is a friend of peer Pi if Pi has previously received a file or recommendation from Pj. The friendship relationship is transitive for a friend of a friend (FoF) and a friend of a friend of a friend (FoFoF). For simplicity, we assume a maximum friend chain length of three.
- Best friend: A peer Pj is a best friend of peer Pi if the current trust of Pi by Pj is above δf.
- Acquaintance: A peer Pj is an cquaintance of peer Pi if Pi has previously sent a file to Pj.
- Unknown peer: A peer Pj is unknown to peer Pi if Pi has not previously received a file, recommendation, or feedback from Pj (it is neither a friend nor an acquaintance).
- Current trust: This is the last saved trust value in the trust list (TL). During system initialization, all current trust values are set to zero.
3.4. How AntTrust Works
3.4.1. AntTrust Algorithm
- (a)
- File provider selection: Initially, when all peers P in the network have no experience, Pq selects Pv randomly. However, after some transactions have been processed, a list of friends and their current trust values can be generated, and the provider selection process is then based on the file provider selection algorithm presented in Section 3.4.2.
- (b)
- File validation: After Pq receives a file from Pv, Pq rates the transaction based on the validity of the received file based on Equation (1).
- (c)
- File provider recommendation: Consequently, Pq evaluates Pv according to the validity of the received file or the received recommendations. If the file and recommendations are valid, a reward is calculated according to Equation (2) for Pv and all recommender friends Fi, if any, between Pq and Pv.
| Algorithm 1: AntTrust |
| Data: Rating List (RL), Trust List (TL)
Result: send a file to Pq, update RL and TL while num of transaction <= max num of transaction do // 1. File provider selection if Pq request a file then if Pq has previous experience with any Pi then Select Pv based on File provider selection algorithm else Select Pv randomly // 2. File validation if accepted file is valid then Rating= 1 // 3. File provider recommendation if Pv recommended by Fi then Calculate Reward and Trust value of all recommended Fi between the Pq and Pv Calculate Reward and Trust value of Pv else Rating = 0 if Pv recommended by Fi then Calculate the Punishment and Trust value of Fi Calculate the Punishment and Trust value of Pv Send feedback to friends else Go to step 1 end while |
3.4.2. File Provider Selection Algorithm
| Algorithm 2: File provider selection |
| Data: Trust List (TL), Feedback List (FL) Result: select trustworthy provider // Step 1: check Trust list if the number of direct friend providers > 1 then if max Trust value > δt then accept the file from Pv else request and calculate Recommendation from friends with trust value> δf else if the number of direct friend providers = 1 then if Trust value > δt then accept the file from Pv else deny transaction else request and calculate Recommendation from friends with trust value > δf // Step 2: check Recommendation if the number of recommendation > 1 then if max Recommendation > δt then accept the file from Pv else calculate Feedback else if the number of recommendation = 1 then if Recommendation> δt then accept the file from Pv else deny transaction else calculate Feedback // Step 3: check Feedback if the number of Feedback >1 then if max feedback> δt then accept the file from Pv else collect Trust value from all friends else if the number of Feedback = 1 then if feedback > δt then accept the file from Pv else deny transaction else collect Trust value from all friends // Step 4: check Collective trust if the number of Collective trust > 1 then if max collective trust > δt then accept the file from Pv else select a random Pv else if the number of Collective trust = 1 then if Collective trust > δt then accept the file from Pv else deny transaction else select a random Pv |
- Step 1: Based on Current Trust
- Step 2: Based on Recommendation
- Step 3: Based on Feedback
- Step 4: Based on Collective Trust
4. Evaluation Framework
5. Results and Discussions
5.1. Success Rate
5.2. Execution Time
6. Conclusions
Author Contributions
Funding
Institutional Review Board Statement
Informed Consent Statement
Conflicts of Interest
References
- Fu, X.; Yang, Y. Analysis on invulnerability of wireless sensor networks based on cellular automata. Reliab. Eng. Syst. Saf. 2021, 212, 107616. [Google Scholar] [CrossRef]
- Fu, X.; Yang, Y. Modeling and analyzing cascading failures for Internet of Things. Inf. Sci. 2021, 545, 753–770. [Google Scholar] [CrossRef]
- Fu, X.; Yao, H.; Yang, Y. Modeling and Optimizing the Cascading Robustness of Multisink Wireless Sensor Networks. IEEE Trans. Reliab. 2021, 70, 121–133. [Google Scholar] [CrossRef]
- Frahat, R.T.; Monowar, M.M.; Buhari, S.M. Secure and Scalable Trust Management Model for IoT P2P Network. In Proceedings of the 2019 2nd International Conference on Computer Applications & Information Security (ICCAIS), Riyadh, Saudi Arabia, 19–21 March 2019; pp. 1–6. [Google Scholar]
- Wu, Y.; Chen, J.; Qian, L.P.; Huang, J.; Shen, X.S. Energy-aware cooperative traffic offloading via device-to-device cooperations: An analytical approach. IEEE Trans. Mob. Comput. 2016, 16, 97–114. [Google Scholar] [CrossRef]
- Androutsellis-Theotokis, S.; Spinellis, D. A survey of peer-to-peer content distribution technologies. ACM Comput. Surv. 2004, 36, 335–371. [Google Scholar] [CrossRef]
- Bhise, A.M.; Kamble, S.D. Detection and Mitigation of Sybil Attack in Peer-to-peer Network. Int. J. Comput. Netw. Inf. Secur. 2016, 8, 56–63. [Google Scholar] [CrossRef][Green Version]
- Mármol, F.G.; Pérez, G.M.; Skarmeta, A.F.G. TACS, a Trust Model for P2P Networks. Wirel. Pers. Commun. 2008, 51, 153–164. [Google Scholar] [CrossRef]
- Kamvar, S.D.; Schlosser, M.T.; Garcia-Molina, H. The eigentrust algorithm for reputation management in P2P networks. In Proceedings of the 12th International Conference on World Wide Web, Budapest, Hungary, 20–24 May 2003; ACM: New York, NY, USA; pp. 640–651. [Google Scholar]
- Wang, W.; Zeng, G.; Yuan, L. Ant-based Reputation Evidence Distribution in P2P Networks. In Proceedings of the 2006 Fifth International Conference on Grid and Cooperative Computing (GCC’06), Hunan, China, 21–23 October 2006; pp. 129–132. [Google Scholar]
- Xiong, L.; Liu, L. PeerTrust: Supporting Reputation-Based Trust for Peer-to-Peer Electronic Communities. IEEE Trans. Knowl. Data Eng. 2004, 16, 843–857. [Google Scholar] [CrossRef]
- Yang, L.; Qin, Z.; Wang, C.; Liu, Y.; Feng, C. A P2P reputation model based on Ant Colony Algorithm. In Proceedings of the 2010 International Conference on Communications, Circuits and Systems (ICCCAS), Chengdu, China, 28–30 July 2010; pp. 236–240. [Google Scholar]
- Mahdavi, S.; Shiri, M.E.; Rahnamayan, S. Metaheuristics in large-scale global continues optimization: A survey. Inf. Sci. 2015, 295, 407–428. [Google Scholar] [CrossRef]
- Andre, C.; Pinheiro, R.; McNeill, F. The Heuristic Approach and Why We Use It. In Heuristics in Analytics; Wiley: Hoboken, NJ, USA, 2012; pp. 45–68. [Google Scholar]
- Said, G.A.E.N.; Mahmoud, A.; El-Horbarty, E.S. A comparative study of meta-heuristic algorithms for solving quadratic assignment problem. Int. J. Adv. Comput. Sci. Appl. 2014, 5, 1–6. [Google Scholar] [CrossRef]
- Josang, A.; Hayward, R.F.; Simon, P. Trust network analysis with subjective logic. In Proceedings of the Conference of the Twenty-Ninth Australasian Computer Science Conference (ACSW 2006), Sydney, NSW, Australia, 29–31 January 2019; Australian Computer Society: Hobart, Tasmania, Australia, 2006; pp. 85–94. [Google Scholar]
- Kurdi, H.A. HonestPeer: An enhanced EigenTrust algorithm for reputation management in P2P systems. J. King Saud Univ. Comput. Inf. Sci. 2015, 27, 315–322. [Google Scholar] [CrossRef]
- Song, S.; Hwang, K.; Zhou, R.; Kwok, Y.-K. Trusted P2P Transactions with Fuzzy Reputation Aggregation. IEEE Internet Comput. 2005, 9, 24–34. [Google Scholar] [CrossRef]
- Zhou, R.; Hwang, K. PowerTrust: A Robust and Scalable Reputation System for Trusted Peer-to-Peer Computing. IEEE Trans. Parallel Distrib. Syst. 2007, 18, 460–473. [Google Scholar] [CrossRef]
- Chuang, Y.-T.; Li, F.-W. TCR: A trustworthy and churn-resilient academic distribution and retrieval system in P2P networks. J. Supercomput. 2020, 76, 7107–7139. [Google Scholar] [CrossRef]
- Meng, X.; Zhang, G. TrueTrust: A feedback-based trust management model without filtering feedbacks in P2P networks. Peer-to-Peer Netw. Appl. 2020, 13, 175–189. [Google Scholar] [CrossRef]
- Singh, S.K.; Kumar, C.; Nath, P. Local Contribution (LC) and Trustworthiness Factors to Induce Fairness in P2P Networks. Wirel. Pers. Commun. 2019, 107, 303–323. [Google Scholar] [CrossRef]
- Gupta, R.; Singh, Y.N.; Goswami, A. Trust estimation in peer-to-peer network using BLUE. Peer-to-Peer Netw. Appl. 2021, 14, 888–897. [Google Scholar] [CrossRef]
- Awasthi, S.K.; Singh, Y. AbsoluteTrust: Algorithm for Aggregation of Trust in Peer-to-Peer Networks. arXiv 2020, arXiv:1601.01419. [Google Scholar] [CrossRef]
- Alkharji, S.; Kurdi, H.; Altamimi, R.; Aloboud, E. AuthenticPeer++: A Trust Management System for P2P Networks. In Proceedings of the 2017 European Modelling Symposium (EMS), Manchester, UK, 20–21 November 2017; pp. 191–196. [Google Scholar] [CrossRef]
- Selçuk, A.A.; Uzun, E.; Pariente, M.R. A reputation-based trust management system for p2p networks. In Proceedings of the IEEE International Symposium on Cluster Computing and the Grid, 2004. CCGrid 2004, Chicago, IL, USA, 19–22 April 2004; pp. 251–258. [Google Scholar] [CrossRef]
- Liu, J.; Issarny, V. Enhanced Reputation Mechanism for Mobile Ad Hoc Networks. In Trust Management; Jensen, C., Poslad, S., Dimitrakos, T., Eds.; Springer: Berlin/Heidelberg, Germany, 2004; Volume 2995. [Google Scholar]
- Gurtov, A.; Koskela, J.; Korzun, D. Cyclic ranking in single-resource peer-to-peer exchange. Peer-to-Peer Netw. Appl. 2018, 11, 632–643. [Google Scholar] [CrossRef]
- Zikratov, I.A.; Lebedev, I.; Gurtov, A. Trust and Reputation Mechanisms for Multi-agent Robotic Systems. In Progress in Artificial Intelligence and Pattern Recognition; Springer Science and Business Media LLC: Cham, Switzerland, 2014; Volume 8638, pp. 106–120. [Google Scholar]
- Bertino, E.; Ferrari, E.; Squicciarini, A.C. Trust-X: A Peer-to-Peer Framework for Trust Establishment. IEEE Trans. Knowl. Data Eng. 2004, 16, 827–842. [Google Scholar] [CrossRef]
- Selvaraj, C.; Anand, S. Peer profile based trust model for P2P systems using genetic algorithm. Peer-to-Peer Netw. Appl. 2011, 5, 92–103. [Google Scholar] [CrossRef]
- Xu, X. A Trust-based Immune Strategy for File Pollution in P2P Networks. Int. J. Secur. Its Appl. 2015, 9, 271–280. [Google Scholar] [CrossRef]
- Li, J.-Q.; Pan, Q.-K.; Xie, S.-X. Research on Peer Selection in Peer-to-Peer Networks using Ant Colony Optimization. In Proceedings of the 2008 Fourth International Conference on Natural Computation, Washington, DC, USA, 18–20 October 2008; Volume 7, pp. 516–520. [Google Scholar]
- Blum, C. Ant colony optimization: Introduction and recent trends. Phys. Life Rev. 2005, 2, 353–373. [Google Scholar] [CrossRef]
- Bonabeau, E.; Dorigo, M.; Theraulaz, G. Swarm Intelligence: From Natural to Artificial Systems; Oxford University Press: Oxford, UK, 1999. [Google Scholar]
- Bonabeau, E.; Dorigo, M.; Theraulaz, G. Inspiration for optimization from social insect behaviour. Nature 2000, 406, 39–42. [Google Scholar] [CrossRef] [PubMed]
- Deneubourg, J.-L.; Aron, S.; Goss, S.; Pasteels, J.M. The self-organizing exploratory pattern of the argentine ant. J. Insect Behav. 1990, 3, 159–168. [Google Scholar] [CrossRef]
- Dorigo, M.; Bonabeau, E.; Theraulaz, G. Ant algorithms and stigmergy. Future Gener. Comput. Syst. 2000, 16, 851–871. [Google Scholar] [CrossRef]
- Sun, E.C. Progressive organization of co-operating colonies/collections of ants/agents (POOCA) for competent phero-mone-based navigation and multi-agent learning. In Ant Colonies: Behavior in Insects and Computer Applications; Sun, E.C., Ed.; Nova Science Publisher: New York, NY, USA, 2011; pp. 5–7. [Google Scholar]
- Fan, X.; Liu, L.; Li, M.; Su, Z. EigenTrustp++: Attack resilient trust management. In Proceedings of the 8th International Conference on Collaborative Computing: Networking, Applications and Worksharing (CollaborateCom), Pittsburgh, PA, USA, 14–17 October 2012; pp. 416–425. [Google Scholar]
- Kurdi, H.; Alshayban, B.; Altoaimy, L.; Alsalamah, S. TrustyFeer: A Subjective Logic Trust Model for Smart City Peer-to-Peer Federated Clouds. Wirel. Commun. Mob. Comput. 2018, 2018, 1073216. [Google Scholar] [CrossRef]
- Rohr, D.; Kalcher, S.; Bach, M.; Alaqeeli, A.; Alzaid, H.; Eschweiler, D.; Lindenstruth, V.; Sakhar, A.; Alharthi, A.; Almubarak, A.; et al. An energy-efficient multi-GPU supercomputer. In Proceedings of the 16th IEEE International Conference on High Per-formance Computing and Communications, Paris, France, 20–22 August 2014; pp. 42–45. [Google Scholar]
- Kacst High Performance Computing. Available online: https://hpc.kacst.edu.sa (accessed on 17 September 2021).
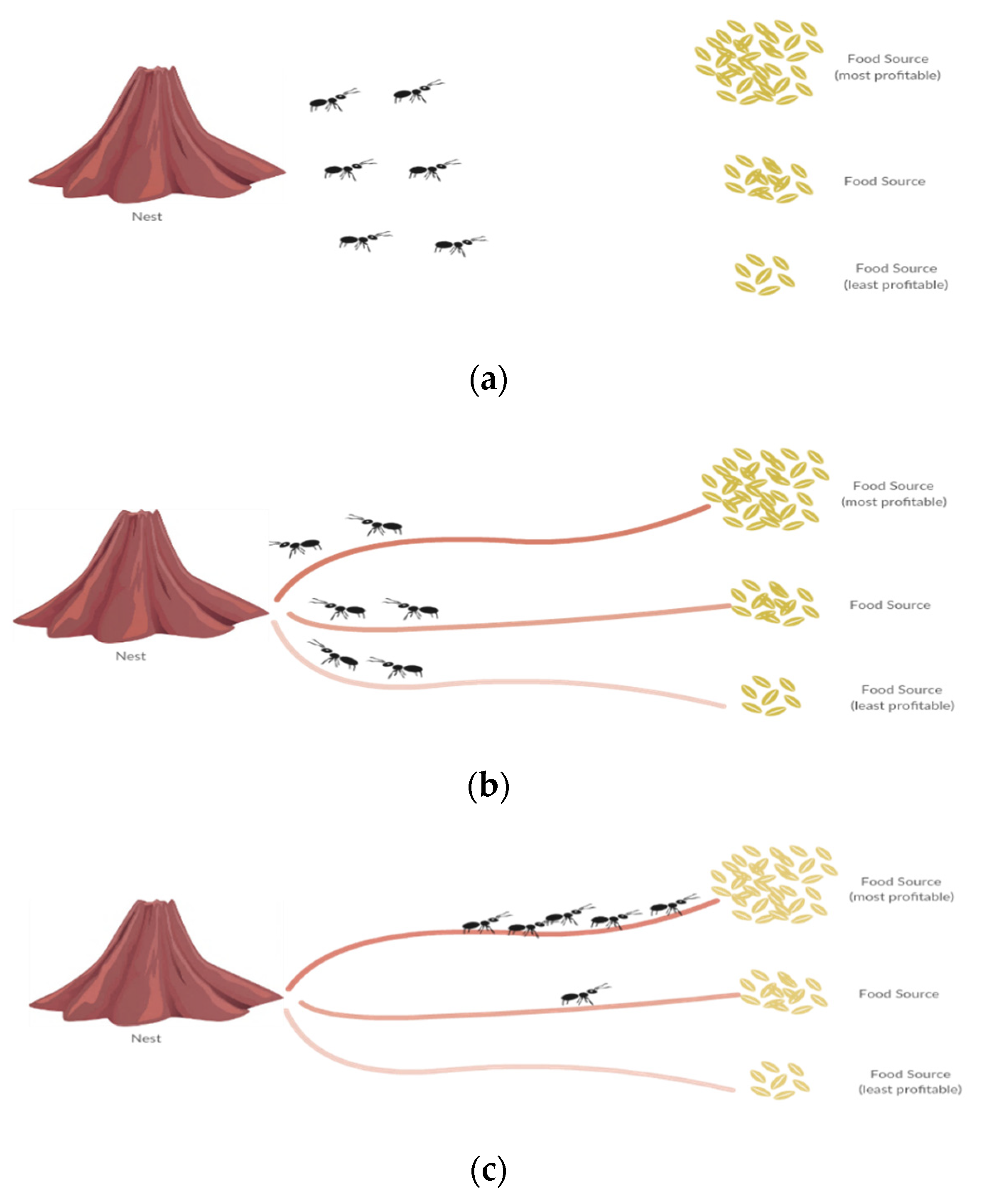
| System | Trust Evaluation | Bioinspiration | Malicious Models | Performance Measures | Evaluation Tool |
|---|---|---|---|---|---|
| Peer profile-based trust [31] | Detect abnormal behavior using anomaly detector based on profile | GA | Selfish peers, traitor attack, Sybil attack, collusion attack |
| N/A |
| TrustIs [32] | Detect malicious peer based on peer reputation, object reputation, and index reputation received from an immune peer | IS | Pure malicious |
| PeerSim |
| AntRep [10] | ACO | AC | N/A |
| FreeNet simulator |
| TACS [8] | ACO | AC | N/A |
| Custom Java-based simulator |
| ACO-based reputation [12] | ACO and combining trust values from different paths | AC | Strategic deception, malicious collusion |
| PeerSim |
| AntPS [33] | ACO with a combination of trust similarity and resource similarity | AC | N/A |
| Query Cycle Simulator |
| Malicious % | AntTrust | EigenTrust | None | TNA-SL | TACS | |||||
|---|---|---|---|---|---|---|---|---|---|---|
| Naive | Collective | Naive | Collective | Naive | Collective | Naive | Collective | Naive | Collective | |
| 132 peers | ||||||||||
| 20 | 93.57 | 92.13 | 92.32 | 85.83 | 76.95 | 57.09 | 84.00 | 82.98 | 91.29 | 90.08 |
| 40 | 91.56 | 94.42 | 72.80 | 90.08 | 40.15 | 77.02 | 74.40 | 75.45 | 81.23 | 80.17 |
| 60 | 92.78 | 92.57 | 73.68 | 72.85 | 57.17 | 41.39 | 60.53 | 69.82 | 61.68 | 60.53 |
| 256 peers | ||||||||||
| 20 | 94.92 | 94.88 | 90.37 | 81.37 | 76.27 | 58.96 | 83.53 | 84.50 | * | * |
| 40 | 92.69 | 96.25 | 82.62 | 91.42 | 39.29 | 76.23 | 69.18 | 70.28 | * | * |
| 60 | 95.04 | 94.07 | 70.20 | 69.94 | 58.88 | 40.81 | 60.71 | 59.92 | * | * |
| 512 peers | ||||||||||
| 20 | 92.71 | 92.98 | 89.90 | 81.74 | 77.59 | 58.59 | 81.65 | 84.32 | * | * |
| 40 | 94.47 | 95.89 | 82.88 | 88.75 | 40.77 | 77.40 | 73.33 | 71.41 | * | * |
| 60 | 94.16 | 96.13 | 75.98 | 70.08 | 58.21 | 41.06 | 64.68 | 60.24 | * | * |
| Malicious % | AntTrust | EigenTrust | None | TNA-SL | TACS | |||||
|---|---|---|---|---|---|---|---|---|---|---|
| Naive | Collective | Naive | Collective | Naive | Collective | Naive | Collective | Naive | Collective | |
| 132 peers | ||||||||||
| 20 | 95.26 | 93.76 | 94.07 | 92.81 | 76.89 | 77.11 | 83.25 | * | * | * |
| 40 | 93.62 | 94.22 | 87.81 | 85.21 | 57.30 | 58.28 | 72.13 | * | * | * |
| 60 | 89.28 | 91.88 | 74.49 | 69.22 | 39.88 | 39.83 | 57.59 | * | * | * |
| 256 peers | ||||||||||
| 20 | 94.66 | 95.60 | 93.55 | 92.41 | 76.72 | 77.17 | 84.27 | * | * | * |
| 40 | 94.06 | 93.72 | 87.67 | 82.33 | 58.19 | 57.99 | 69.95 | * | * | * |
| 60 | 94.02 | 93.69 | 62.86 | 72.84 | 40.19 | 39.49 | 62.39 | * | * | * |
| 512 peers | ||||||||||
| 20 | 95.25 | 93.89 | 93.15 | 90.84 | 76.93 | 77.07 | 82.60 | * | * | * |
| 40 | 95.11 | 94.90 | 84.35 | 85.47 | 58.56 | 59.01 | 71.38 | * | * | * |
| 60 | 94.31 | 95.03 | 71.06 | 70.76 | 40.39 | 40.63 | 60.88 | * | * | * |
| Malicious % | AntTrust | EigenTrust | None | TNA-SL | TACS | |||||
|---|---|---|---|---|---|---|---|---|---|---|
| Naive | Collective | Naive | Collective | Naive | Collective | Naive | Collective | Naive | Collective | |
| 132 peers | ||||||||||
| 20 | 1.49 | 1.48 | 0.92 | 0.90 | 0.52 | 0.52 | 1669.33 | 1228.88 | 59,679.53 | 56,978.25 |
| 40 | 1.48 | 1.43 | 0.90 | 4.38 | 0.51 | 0.59 | 546.72 | 941.26 | 52,061.91 | 52,918.49 |
| 60 | 1.98 | 2.76 | 0.93 | 32.65 | 0.80 | 1.17 | 626.48 | 20,793.53 | 61,600.76 | 53,821.82 |
| 256 peers | ||||||||||
| 20 | 4.15 | 4.19 | 2.29 | 2.53 | 1.06 | 1.05 | 9594.23 | 9119.80 | * | * |
| 40 | 4.17 | 4.39 | 2.22 | 33.19 | 1.03 | 1.87 | 3254.11 | 15,212.95 | * | * |
| 60 | 7.26 | 12.62 | 2.35 | 276.89 | 4.46 | 9.39 | 7501.21 | 16,774.92 | * | * |
| 512 peers | ||||||||||
| 20 | 18.19 | 19.05 | 10.66 | 10.35 | 5.02 | 4.92 | 20,816.17 | 58,293.70 | * | * |
| 40 | 19.15 | 21.17 | 9.99 | 254.18 | 5.04 | 9.13 | 28,986.47 | 73,275.82 | * | * |
| 60 | 30.41 | 49.67 | 10.47 | 2293.28 | 21.83 | 41.85 | 25,337.93 | 78,108.66 | * | * |
| Malicious % | AntTrust | EigenTrust | None | TNA-SL | TACS | |||||
|---|---|---|---|---|---|---|---|---|---|---|
| Naive | Collective | Naive | Collective | Naive | Collective | Naive | Collective | Naive | Collective | |
| 132 peers | ||||||||||
| 20 | 1.94 | 2.27 | 1.28 | 8.45 | 0.74 | 0.91 | 9041.24 | * | * | * |
| 40 | 2.22 | 3.25 | 1.27 | 31.71 | 0.73 | 1.48 | 21,101.89 | * | * | * |
| 60 | 2.29 | 4.92 | 1.32 | 69.02 | 0.69 | 2.24 | 33,176.29 | * | * | * |
| 256 peers | ||||||||||
| 20 | 7.26 | 8.09 | 4.66 | 62.00 | 1.61 | 3.96 | 24,619.67 | * | * | * |
| 40 | 7.42 | 13.71 | 4.59 | 248.70 | 1.56 | 9.98 | 28,800.96 | * | * | * |
| 60 | 7.91 | 23.83 | 4.29 | 574.24 | 1.59 | 21.73 | 36,182.73 | * | * | * |
| 512 peers | ||||||||||
| 20 | 31.87 | 36.51 | 19.43 | 522.13 | 8.74 | 15.10 | 70,962.73 | * | * | * |
| 40 | 34.03 | 60.32 | 19.37 | 2113.92 | 7.30 | 39.16 | 66,033.12 | * | * | * |
| 60 | 36.58 | 97.35 | 19.15 | 4750.10 | 7.33 | 80.78 | 72,107.74 | * | * | * |
Publisher’s Note: MDPI stays neutral with regard to jurisdictional claims in published maps and institutional affiliations. |
© 2022 by the authors. Licensee MDPI, Basel, Switzerland. This article is an open access article distributed under the terms and conditions of the Creative Commons Attribution (CC BY) license (https://creativecommons.org/licenses/by/4.0/).
Share and Cite
Al-Otaiby, N.; Alhindi, A.; Kurdi, H. AntTrust: An Ant-Inspired Trust Management System for Peer-to-Peer Networks. Sensors 2022, 22, 533. https://doi.org/10.3390/s22020533
Al-Otaiby N, Alhindi A, Kurdi H. AntTrust: An Ant-Inspired Trust Management System for Peer-to-Peer Networks. Sensors. 2022; 22(2):533. https://doi.org/10.3390/s22020533
Chicago/Turabian StyleAl-Otaiby, Nehal, Afnan Alhindi, and Heba Kurdi. 2022. "AntTrust: An Ant-Inspired Trust Management System for Peer-to-Peer Networks" Sensors 22, no. 2: 533. https://doi.org/10.3390/s22020533
APA StyleAl-Otaiby, N., Alhindi, A., & Kurdi, H. (2022). AntTrust: An Ant-Inspired Trust Management System for Peer-to-Peer Networks. Sensors, 22(2), 533. https://doi.org/10.3390/s22020533






