1. Introduction
The concept of a verifiable delay function was first proposed in 2018 by Boneh et al. [
1], who proposed several candidate structures for constructing verifiable delay functions and it is an important tool to add time delay in decentralized applications [
2,
3,
4,
5]. To be exact, the verifiable delay function is a function
that takes a prescribed wall-clock time to compute, even on a parallel processor, ond outputs a unique result that can effectively output the verification. In short, even if it is evaluated on a large number of parallel processors and still requires evaluation of
f in a specified number of sequential steps. Most importantly, given an input
x and an output
y, anyone must quickly verify the output
. That is to say, for all
and
, this function
satisfies the following requirements:
The verifiable delay function is a cryptographic function that requires to be computed in
T sequential steps and produces a unique, efficiently and publicly verified output [
6]. Because the verifiable delay function satisfies the characteristic of sequentiality, the iterated value does depend on the order of the iterated elements. Choose the tuple
as the puzzle, and the verifiable delay function is defined as
where
is an RSA modulus [
7],
is a random seed,
is time parameter and knows the group order
.
Although verifiable delay functions have been roughly described in the review of verifiable delay functions published by Boneh et al. [
8], the summary is not comprehensive with the emergence of more candidate structures of verifiable delay functions. In addition, the application of different kinds of verifiable delay functions in the blockchain is not explained in detail. Therefore, this paper makes a more comprehensive and detailed summary.
The verifiable delay function has several important characteristics, such as being
T-sequential, uniqueness and effective verifiability, as shown in
Table 1.
The remainder of this paper is organized as follows.
Section 2 introduces the descriptions of verifiable delay functions.
Section 3 describes verifiable delay functions based on various algebraic assumptions. In
Section 4, verifiable delay functions based on various structural assumptions are introduced in detail.
Section 5 the postquantum-secure verifiable delay function.
Section 6 describes applications of verifiable delay functions combined with blockchain.
Section 7 gives a summary.
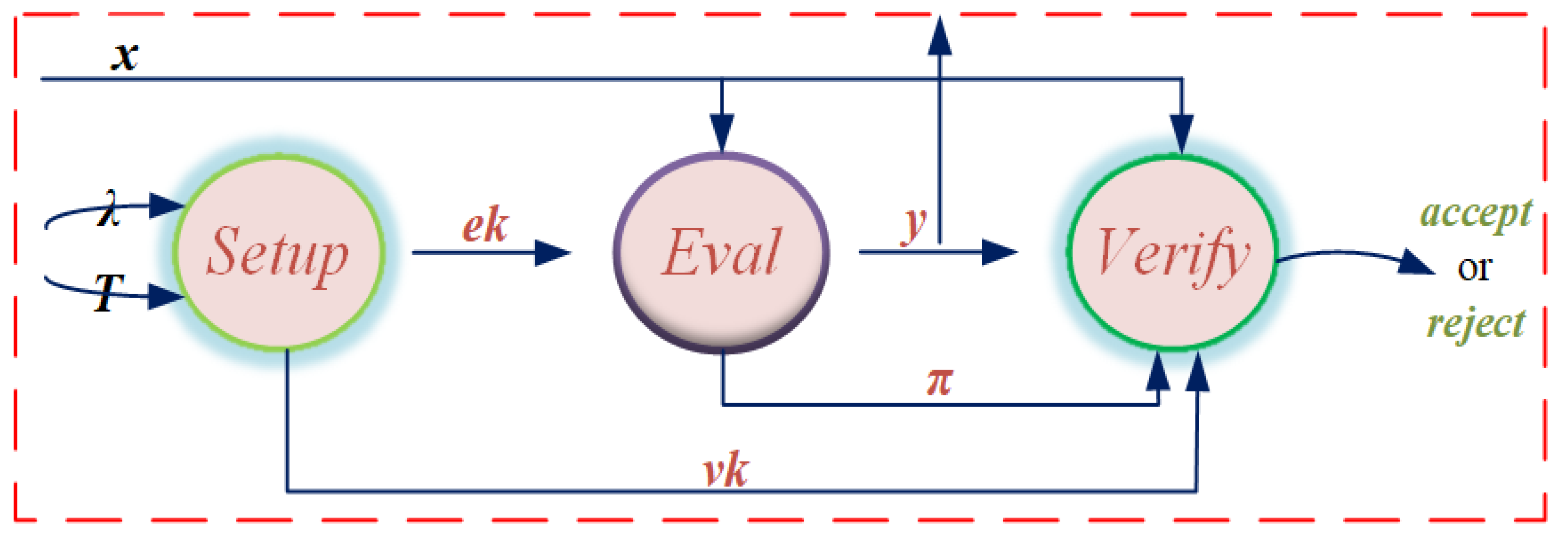
2. Descriptions of Verifiable Delay Functions
The concept of the verifiable delay function first proposed by Boneh and Fisch. The verifiable delay function requires a specified number of sequential steps to evaluate and will produce a function with a unique output that can be validated effectively and publicly. Next, a triple of algorithm (
Setup,
Eval,
Verify) of verifiable delay functions are described as follows [
9]. The algorithm flow is shown in
Figure 1 and the different types of verifiable delay functions are described in
Table 2.
is a randomized algorithm that takes a delay parameter T and a security parameter as input and outputs public parameters composed of the evaluation key and the verification key . Because algorithm is limited by security parameter , the running time cannot be too long. In addition, algorithm usually needs a secret random as a parameter to ensure meaningful security, so it is difficult to avoid that the scheme needs a trusted setup to select the random.
is a slow cryptographic algorithm that takes the evaluation key and a random seed as input and outputs a together with a possibly empty proof . To ensure sequentiality, must run in time T with no more than a polynomial logarithm of T parallel processors.
is a deterministic cryptographic algorithm, in which the algorithm inputs verification key , random seed x, outputs y and proof . If , output ; Otherwise output . is much faster than and it must run in total time polynomial in and .
2.1. Weak Verifiable Delay Functions
Definition 1. (Weak verifiable delay functions.) The system = (, , ) is a weak verifiable delay function if the verifiable delay function allows to achieve parallelism. -sequentiality can only be meaningful for a weak verifiable delay function if is allowed strictly less that on fewer than parallel processors, otherwise the honest computation of would require more parallelism than even the adversary is allowed.
The weak verifiable delay function can be constructed based on the existence of degree
T injective rational maps [
10] that cannot be inverted faster than computing polynomial greatest common denominators of degree
T polynomials.
Injective rational maps. Define the reverse problem of an injective rational map F = () on algebraic sets to , where each is a rational function in ( ), for . An algebraic set is the set of vanish points of some set of polynomial S.
Boneh et. al. abstract weak verifiable delay functions from an injective rational map. First, let F: be a rational function that is an injective map from to . At the same time, is required to be efficiently sampleable and F can be evaluated efficiently for all . If you need to use the injective rational map function F in the verifiable delay function, you must guarantee to prevent brute force attacks, where a delay parameter T and a security parameter as input to the algorithm.
Verifiable delay functions construct a weak verifiable delay function by function family with a security parameter and a delay parameter T as input parameters.
is a randomized algorithm that takes a delay parameter T and a security parameter as input and choose a , then outputs public parameters composed of the .
is a slow cryptographic algorithm that takes the and a random seed as input and compute a together with a possibly empty proof .
is a deterministic cryptographic algorithm, in which the algorithm inputs , random seed , outputs and proof . If , output ; Otherwise output .
In order to ensure that the solution is unique, F is required to be injective on Y.
2.2. Incremental Verifiable Delay Functions
Definition 2. (Incremental verifiable delay functions.) The system = (, , ) is a incremental verifiable delay function if the time parameter T of the verifiable delay function is not uniquely determined and is allowed to be determined in the output π of , which does not generate additional proofs.
Since the verifiable delay function is a sequential function [
11], Boneh et. al. propose the use of tight incremental verifiable computation to construct an incremental verifiable delay function construction. Next, here’s how to build an incremental verifiable delay function with a tight incremental verifiable computation.
Incremental verifiable computation was first proposed by Valiant [
12]. After that, Bitansky et al. [
13] applied it to distributed computions and to other proof systems. The incremental verifiable computation is to guarantee that the prover can generate a proof that a certain state is indeed the current state of the computation at every incremental step of the computation. The proof is updated after every step of the computation to produce a new proof. Iterative sequence functions can be implemented via tight incremental verifiable computation, which captures the primitives required by verifiable delay functions.
Let be an interated sequential function with round function having -sequentiality. An incremental verifiable computation system for an interated sequential function is polynomial time algorithm (, , ) that satisfy completeness, succinctness and soundness.
Succinctness. The length of a proof is bounded by .
Soundness. The soundness satisfied by the incremental verifiable computation is sub-exponential soundness. For all algorithm
running in time
.
Next, we introduce the verifiable delay function construction based on tight incremental verifiable computation. Let a family , where each , is defined by . Here is a (T, )-sequential function on an efficiently sampleable domain of size .
is a randomized algorithm that takes a delay parameter T and a security parameter as input and outputs public parameters composed of the evaluation key , a largest integer k and the verification key . Generate by running (, ).
is a slow cryptographic algorithm that takes the evaluation key , a largest integer k and a random seed x as input and runs (, k, x), and outputs a y together with a possibly empty proof .
is a deterministic cryptographic algorithm, in which the algorithm runs and outputs (, x, y, k,). If , output ; Otherwise output .
Since T is fixed in the public parameters . However, it is also possible to directly assign the T to algorithm. Therefore, a tight incremental verifiable computation based the verifiable delay function is an incremental verifiable delay function.
2.3. Decodable Verifiable Delay Functions
Definition 3. (Decodable verifiable delay functions.) The system = (, , ) is a decodable verifiable delay function if there is an algorithm in the verifiable delay function that can decode input x backwards from output y. If the decoding is efficient then no additional proof π is required [14]. Using a slow and easy to verify function with exponentiation [
15] based calculations in a finite group can be constructed a decodable verifiable delay function. Boneh et al. propose a simple exponentiation-based decodable verifiable delay functions with bounded pre-computation. However, the adversary cannot run a long pre-computation between the time the public parameter
is exposed and the time that the verifiable delay function is computed.
Next, we introduce a decodable verifiable delay function based on an exponentiation in a finite group. Let be the first T odd promes, namely etc. Let P be the product of the primes in L, namely .
is a randomized algorithm that takes a delay parameter T, a security parameter and a preprocessing security parameter b as input and outputs public parameters composed of the evaluation key and the verification key .
In algorithm , let a integer module N multiplicative group := (/N) and a random hash function . The algorithm needs to compute , for then compute . It outputs the evaluation key := (, H, , , ..., ) and the verification key := (, H).
is a slow cryptographic algorithm that takes the evaluation key and a random seed x as input and outputs a y.
In algorithm , using random hash function to map a random seed x to a size of random subset and random subset of values in . At the same time, let be the product of all prime numbers in . Let g be and the seed solution y is simply .
is a deterministic cryptographic algorithm, in which the algorithm inputs verification key , random seed x, outputs y and proof . If , output ; Otherwise output .
In algorithm , let h be and if and only if ∈, where and are calculated by the algorithm .
The preprocessing parameter
b in an exponentiation-based the decodable verifiable delay function ensures the security of the construction. The construction requires a trusted setup [
16,
17], but can be eliminated by choosing a random number large enough.
2.4. Trapdoor Verifiable Delay Functions
Definition 4. (Trapdoor verifiable delay functions.) The system = (, , , ) is a trapdoor verifiable delay function if there is a secret key that can quickly get the output of through the input of . In other words, the trapdoor verifiable delay function can bypass the delay parameter to quickly calculate the result through the trapdoor [18]. Given a pair of Alice’s public-secret keys (
,
), where
is Alice’s public key and
is the secret key. Alice is able to quickly evaluate trap [
19,
20] functions
on
x with a secret key
. Let
T be an implicit time function about the security parameter
and
x be a piece of data. Except for Alice, everyone else can only compute the public evaluation function
with the public key
in
T-sequential steps and the calculation is slow, but the result between
and
is equal. A trapdoor verifiable delay function comsists of four algorihtm (
,
,
,
).
is a key generation algorithm that takes a security parameter as input and outputs Alice’s public key and the secret key . Meanwhile, Alice’s public key is publicly valid, and the secret key is known only to Alice herself.
is a slow cryptographic algorithm that takes an implicit time function T about the security parameter and a piece of data x as input, and uses the secret key to output y together with a possibly empty proof . The function T is a sequence of sequential steps required to compute the same output y without knowledge of the secret key .
is a slow cryptographic algorithm to evaluate the function on x using only the public key . It produces an output y associated with and a possibly empty proof . This procedure is meant to be infeasible in time less than T (this will be expressed precisely in the security requirements).
is a deterministic cryptographic algorithm to verify if y is indeed the correct output for x, associated with the public key and the evaluation time T, possibly with the help of the proof .
The time delay T is a function of the security parameter and T is an input to each algorithm, so the security parameter is implicitly an input to each of these procedures. Generate a public-secret key pair through the key generation algorithm . Given a piece of data x and time delay parameter T, let and . If and = output accept; Otherwise output reject.
3. Verifiable Delay Functions Based on Algebraic Assumptions
3.1. Construction Based on Finite Abelian Groups of Unknown Order
Verifiable delay functions can be constructed by showing Rivests-Shamir-Wagner (RSW) when the time-lock puzzle [
21,
22] is publicly verifiable. To be precise, giving a statistically sound public-coin protocol [
23] to prove that a tuple
satisfies
verifiers do not know the decomposition of
N and its running time is mainly to solve the puzzle, where the time
is a power of two. This construction solves an instance of the time-lock puzzle, and computes a proof of correctness, which allows anyone to efficiently verify the result.
Pietrzak [
24] proposed a verifiable delay function based on finite abelian groups [
25,
26] of unknown order consisting of four algorithm
.
inputs the statistical security parameter output N, where the defines another security parameter specifying the bitlength of an modulus and N is the single bit RSA modulus of public parameters. The is composed of two -bit secure prime numbers p and q randomly selected by the algorithm.
samples a random number and outputs .
Define
as quadratic residues and the signed quadratic residues [
27] are the group
. In a verifiable delay function, calculating
is difficult in
. Pietrzak uses
instead of
. Because
, the probability that a random number in
is also in
is 1/4. Therefore, if one can break the assumption with probability
over
, the assumption can also be broken over
with probability
. Then, they uses
instead of
in the proof. This approach can make the proof more efficient because the multiplication mod
N in
is more convenient and simpler than the ∘ operation in
. Since
and
are isomorphic, it is proved
means
has the same security.
Let random number and in , and and in , where and , and . Although it is not certain whether or , y has a 1/2 probability of getting the correct value. This shows that given an algorithm that calculates in with probability in time T, it is possible to obtain an algorithm that calculates in in time when time T and probability are essentially the same.
is a slow algorithm that takes the
N and a random seed
x and time delay parameter
T as input and outputs a
y together with
, where
is the solution of the RSW time-lock puzzle in
and
is a possibly empty proof that
y has been correctly evaluated. It is derived by applying the Fiat-Shamir heuristic [
28,
29] to the protocol.
is a deterministic cryptographic algorithm to verify if x, y and all are in . If these are not the case output . Otherwise, all and should be calculated, and should be judged. If all the above are satisfied, output .
3.2. Construction Based on Elliptic Curve Cryptography
De Feo et al. [
30] designed a new verifiable delay function using isogenic and bilinear pairs [
31,
32] of super-singular elliptic curves [
33], and this framework is non-interactive in nature, the output can be effectively verified without additional proofs. Before describing this structure, let’s introduce some basic factors of super-singular curves, pairings and isogenies.
Elliptic curves on finite fields are described in detail in [
34,
35,
36] and their use in cryptography is described in detail in [
37,
38,
39]. In addition, the ideal class group of quadratic imaginary fields are explained in [
40] and the maximal orders of quaternion algebras are introduced in [
41,
42].
Let C be an elliptic curve defined over a finite field characterized by p and the order of is , where L is the trace of the Frobenius endomorphism . If and only when p divided L, the curve can be called a super-singular elliptic curve. Each super-singular curve is isomorphic to the curve defined on , and for the fixed prime number p, there are only a finite number of super-singular curves until isomorphism.
Weil pairing [
43]
with bilinear pairs is defined on super-singular curves are used to describe verifiable delay functions. That pairing needs to be satisfied the compatibility condition
for any isogeny
and points
.
Verifiable delay functions from super-singular curves. Let , be groups of prime order N. Let and be non degenerate bilinear pairings, where a pair of bijections and and and are group isomorphisms. Let be any generator of and be the public parameters. The verifiable delay function is the map and the maps are also part of the public parameters. To verify the output, one checks that , where is the point at which calculates the value.
De Feo et al. propose verifiable delay functions for super-singular curves over prime field and , using super-singular elliptic curves for the pairing groups, and isogenies of prime power degree for the maps , . Next, we mainly introduce verifiable delay functions with super-singular curves over a prime field .
Let p be prime so that contains the larger prime factor N. Let degree , or a small prime such that . Take the super-singular elliptic curve , and denote by the Weil pairing on .
is a randomized algorithm that takes a delay parameter T and a security parameter as input. First, a super-singular curve needs to be chosen and a direction needs to be chosen on the horizontal l-isogeny graph to compute a cyclic isogeny of degree and its dual in this algorithm. Next, the algorithm chooses a generator of and compute , where is a non quadratic residue and is a quadratic twist of C. Finally, the algorithm outputs public parameters , where composed of the evaluation key and the verification key , and composed of the map , the cyclic isogeny , generator of and the map of generator .
is a slow cryptographic algorithm that takes the map and a point as input and outputs .
is a deterministic cryptographic algorithm. The algorithm needs to verify that and . If all the above are satisfied, output ; Otherwise, output .
4. Verifiable Delay Functions Based on Structural Assumptions
Ephraim et al. design continuous verifiable delay functions based on a high arity tree [
44], where each intermediate state of the computation can be verified and proofs of the computation can be efficiently merged. It is a verifiable delay function based on the assumption of tree structure constructed on the basis of the repeated square [
45] assumption. The continuous verifiable delay function only depends on the Fiat-Shamir heuristic for a constant round proof system. Next, we introduce continuous verifiable delay functions based on high arity trees.
First, the computational steps correspond to a specific traversal of a -ary tree of height . Each node in the -ary tree is related to a statement of the underlying verifiable delay functions, where the output value and the possible empty proof are the corresponding proofs of correctness. If x is the node’s input, the difficulty is determined by its height in -ary tree and l is root node.
Next, they define a tree structure. Starting from the root node with input and difficulty , divide the tree structure into k segments similar to the verifiable delay functions structure. In a tree-based verifiable delay functions structure, only calculating the input x of a leaf node from the previous state can guarantee that each step of calculation corresponds to the calculation of a single leaf’s statement.
Before introducing continuous verifiable delay functions, let’s review unique verifiable delay functions. Next, the interactive proof that language
corresponding to repeated squares is transformed into unique verifiable delay functions by using the Fiat-Shamir heuristic, where
A unique verifiable delay function is composed of the following four algorithm (, , , ).
is a randomized algorithm that takes a statistical security parameter as input and outputs public parameters composed of the RSA modulus N, the upper bound B, the arity k, a constant d and a hash function , where , and .
takes a statistical security parameter and the public parameters and sample and output a random element such that and .
is a slow cryptographic algorithm that takes a statistical security parameter , the public parameters , a random element and the time delay parameter T as input and outputs a y together with a possibly empty proof .
is a deterministic cryptographic algorithm. If all the above are satisfied, output
. Otherwise, output
. The
is a verification algorithm for Fiat-Shamir transformations defined on the protocol for language
relative to some hash family
. For details of the algorithm, see [
46]. Then, we review the definition of a continuous verifiable delay function and describe it in detail.
Definition 5. (Continuous verifiable delay functions.) Let and . A -continuous verifiable delay function is a tuple (, , , ) such that (, , ) is a (a, B, l, ϵ)-iteratively sequential function, is a B-sound function.
At a high level, the continuous verifiable delay function will iteratively compute each leaf node in a -puzzle tree, where = (N, B, k, d, ) are the public parameters of the underlying unique verifiable delay function and g is the starting point of the tree given by .
Next, we define a frontier. At a high level, for a leaf s, the frontier of s will correspond to the state of the continuous verifiable delay function upon reaching s. Specifically, it will contain all nodes whose values have been computed at that point, but whose parents’ values have not yet been computed.
Definition 6. (Frontier.) For a node s in a (-puzzle tree, the frontier of s, denoted , is the set of pairs for nodes that are left siblings of any of the ancestors of s. We note that s is included as one of its ancestors.
Next, we review the formal details of continuous verifiable delay functions, which is a tuple (, , , ).
is a randomized algorithm that takes a statistical security parameter as input and outputs public parameters composed of the , a constant and a tree height .
takes a statistical security parameter and public parameters as input and outputs a random element v, where g←(, ) is sampled by the algorithm of unique verifiable delay functions.
takes a state v corresponding to a leaf s in the tree and computes the next state corresponding to the next leaf. Each state v will be of the form , where s is the current leaf in the tree, F is the frontier of s and g is the starting point of the tree given by .
verifies the state v by recursively running this verification algorithm and whether is correct. Output if all the check conditions of the continuous verifiable delay function are satisfied; Otherwise output .
The heart of our construction is the functionality which takes a state v corresponding to a leaf s in the tree and computes the next state corresponding to the next leaf. Each state v will be of the form , where s is the current leaf in the tree and F is the frontier of s. Then, (, , will output (g, , ). There are three phases of the algorithm . First, it checks that its input is well-formed. It then computes using , and then computes using both and .
5. Post-Quantum Verifiable Delay Functions
In 2021, Jorge Chavez-Saab et al. [
47] researched the problem of constructing post-quantum secure verifiable delay functions, especially verifiable delay functions based on super-singular isogeny. They propose an arithmetic structure specifically for homologous settings using succinct non-interacting arguments (SNARGs) [
48] to achieve good asymptotic efficiency. This isogeny-based verifiable delay functions has the advantages of post-quantum security [
49], quasi-logarithmic verification, and does not require a trusted setup. Since the
algorithm for postquantum verifiable delay functions involves isogeny walks on super-singular elliptic curves that can be publicly verified through a SNARG-based verification process. Formally, a verifiable delay function is composed of three main algorithm:
takes a delay parameter T and a security parameter as input and outputs public parameters composed of the evaluation key and the verification key .
takes the evaluation key and a certain input x as input and calculates an output y and a possibly empty proof .
The function involves computing walks of length
T in the 2-isogeny graph of super-singular curves on
, where
(which is required to apply Kong’s square root algorithm [
50]) and
. Given a time delay parameter
T, and the evaluator needs to compute a walk of length
T on the 2-isogeny graph, where the exact path is determined by a string
s and the path is not backtracking. Given the two
v-invariant curves
and
, they are 2-isogenous over
if and only if the modular polynomial
vanishes. For a fixed
the next curve in the path can be calculated by finding the root of
. If
is a known root of
=
+
+
+
c then
can rewrite
= (
)(
+ (
a +
)
A +
b +
+
) and focus on finding the roots of the quadratic factor. After the square root is calculated, the evaluator selects the symbol using the input string, resulting in a definite traversal process.
inputs verification key , a certain input x, a output y and a proof . If , output ; Otherwise output .
Since the postquantum verifiable delay functions is constructed over SNARG, a deterministic process and a fixed symbol are required for the SNARG verification process. For the validation process, the evaluator keeps track the results of the evaluation and construct an SNARG, and the values resulting from the evaluation process must be satisfied.
De-Feo et al. proposed a new verifiable delay function framework based on the assumption of elliptic curve cryptography, and instantiated this framework using super-singular elliptic curves and bilinear pairs. The structure of this verifiable delay function is non-interactive in nature, and the output can be effectively verified without additional proofs. However, the only secure way to instantiate a verifiable delay function requires a trusted setup to perform a random isogeny traversal. In fact, this setup needs to start with super-singular elliptic curves with unknown autohomomorphic rings. In order to explain how to implement the proposed verifiable delay function on elliptic curves with commutative self-homomorphic rings, Shani later used the idea of verifiable delay functions based on isogeny and pairing proposed by De-Feo et al. to construct developed a verifiable delay function based on isogeny without pairing. The scheme is a combination of a time-lock puzzle and a trapdoor verifiable delay function.
However, neither scheme is quantum secure. Thus, Chavez-Saab et al. studied the problem of constructing post-quantum secure verifiable delay functions, especially verifiable delay functions based on super-singular isogeny. They propose an arithmetic structure specifically for homologous settings using SNARGs to achieve good asymptotic efficiency. This isogeny-based verifiable delay function has the advantages of post-quantum security, quasi-logarithmic verification, and does not require a trusted setup.
This verifiable delay function construction finds codomain curves, which are computed from any three-point evaluation, so the problem in the verifiable delay function setting could be regarded as a general problem. The precomputation time allowed in the setting is given before learning the isogeny to be evaluated, suggesting that this verifiable delay function construction uses a different isogeny for each input. This verifiable delay function relies on a very weak assumption, so it is more secure. Starting from a public curve means we do not need a trusted setup. Next, we analyze two security properties of post-quantum verifiable delay functions based on super-singular elliptic curves: sequentiality and soundness.
Sequentiality. Any protocol that does not prescribe isogeny walk in some way is insecure in terms of sequentiality. The evaluator can be asked to provide SNARG proof of any large degree of isogeny and consider this to be a good proof of sequentiality even if the output is not unique. However, if the evaluator is free to choose the path, this does not constitute a proof of sequential computation. The sequentiality of post-quantum verifiable delay functions relies on isogeny shortcut problem of De Feo et al.. If no pair of random algorithms (running in total time and (running in parallel time less than T) can win the following sequential game with non-negligible probability, then the post-quantum verifiable delay functions based on super-singular elliptic curves is sequential. The must use secret randomness to choose the starting curve, and the is left with choosing isogeny and generators, both of which can use public randomness. Furthermore, allows for computations, so it can compute isogeny on generators. Therefore, setting aside the choice of starting curve, the can be absorbed into , which proves that the verifiable delay function of the post-quantum is sequential.
Soundness. The soundness of post-quantum verifiable delay functions based on super-singular elliptic curves completely depends on the SNARG proofs. Succinctness and non-interactiveness are achieved by generating SNARG through a transform that acts on any probabilistic checkable proofs. As long as the hash function is collision-resistant, it is straightforward to prove that the soundness of the structure reduces to the soundness of the original probabilistic checkable proofs. Therefore, the post-quantum verifiable delay functions construction based on super-singular elliptic curves is sufficiently soundness.
6. Verifiable Delay Functions Applications
With the proposal of more and more verifiable delay function schemes, the application of verifiable delay function in distributed systems is also well known. Next, as shown in
Figure 2, this paper introduces several particularly important applications. In
Table 3, the blockchain-related applications of verifiable delay functions are described.
Computational Timestamping. Almost all know proof-of-stake [
51] systems face the problem of long-range attack [
52]. In a proof-of-stake protocol, a group of stakeholders has voting rights proportional to their stake at any time. Assume that the majority of stakeholders have no reason to break the system, since the stakeholders themselves are incentivized. However, when too many stakeholders sell their stake, they can collude to create a new longer system to replace history. An external timestamp mechanism [
53] can prove to the user that the true history of the system is much older.
Incremental verifiable delay functions can provide computational evidence that a given version of the state system is older by proving that long-running verifiable delay function computations has been performed on the true history after divergence from the fraud history. This has the potential to detect long-range attack without relying on external timestamping mechanisms. In 2019, Landerreche et al. [
54] presented the first treatment of non-interactive publicly verifiable timestamping schemes and a secure timestamping scheme based on a verifiable delay function is proved. The timestamping scheme [
55] consists of sequence of verifiable delay function proofs linked to each other by a cryptographic hash function, modeled as a sequence of random oracles. Add verifiable delay functions to the sequence to increase the structure, thus preserving the safety guarantees of the structure.
Public Randomness Beacons. Verifiable delay functions are useful for methods of obtaining random numbers from public sources. For example, constructing public randomness beacons [
56] from stock prices, election audit or proof-of-work blockchains [
57]. In the stock market, a strong enough stock trader can change the random output of stock prices by influencing the market trend, which greatly affects the fairness of the stock market [
58]. The verifiable delay function can increase the security of public verifiable nonces by adding a long enough delay to calculate the beacon, which helps ensure that malicious traders do not have enough time to adjust the market. In a proof-of-work blockchain’s computational puzzle solving, miners continuously mine and publish puzzles for monetary rewards. However, similarly powerful enough stock traders may manipulate stock prices, sufficiently powerful miners may manipulate beacon results by refusing to publish blocks [
59] that produce unfavorable beacon outputs.
In addition, the verifiable delay function can also add some random beacon schemes involving multiple parties. For example, in “commit-and-reveal” [
60], the attacker can wait until the end of the reveal phase to decide whether to reveal his or her commitment. If the following three conditions are met: discard the commit phase; integrate everyone’s input at the end of the protocol and put it into the verifiable delay function instead of directly as the result of a random number; set the time parameter T long enough and later than the deadline for the last submission; then even the last-minute submitter has no way of knowing the result of the random number.
Resource Efficient Blockchains. When the blockchain [
61] is forked, the consensus participants will choose to mortgage assets on different forked chains to participate in the block generation for their own interests, so that the forked chain may always exist and there will be more and more forks. Seriously endanger the consistency of the system and the consumption of resources. However, resource-efficient mining suffers from nothing-at-stake attacks. Intuitively, since mining is not computationally expensive, miners can easily try to produce many individual forks.
To prevent nothing-at-stake attacks [
62], random beacons are used to select a new leader at intervals. At the same time, a verifiable delay function can also be used to increase the security of random beacons in the consensus protocol that uses random beacons to select a new leader. Most of the random number schemes used by these protocols remain secure only when there is a majority of honest participants. Utilizing a verifiable delay function can improve the participation of any honest party.
In addition to the electoral scheme, Cohen proposes to combine proof of resources [
63] with an incremental verifiable delay function and use the product of proven resources and induced delay as a measure of blockchain [
64,
65] quality. This scheme prevents nothing-at-stake attacks by simulating the proof-of-work mining process. The timing of mining blocks is unpredictable, and each miner competes with each other to be the first to mine a block. The difference from the proof-of-work [
66] is that this scheme does not actually need to consume too much time resources for parallel computing, and only has certain space resources when entering mining.
Proof of Data Replication. Proof of data replication [
67,
68,
69] is a special type of proof of storage of data that allows a client to verify that it has a unique replica of some data stored on an untrusted server, even if the data is readily available from a public storage source. Proof of data replication is meant to prove that the server has a replica of the data, not that it owns the data. Boneh et al. proposed to provide a publicly verifiable solution using a decodable verifiable delay function that is asymmetric in time. The decodable verifiable delay function prevents the server from dynamically computing the client’s replica when challenged to prove that it correctly stored a replica of the data.
Gritti proposes a publicly verifiable proof of data replication scheme using verifiable delayed functions, and explains the scheme in detail along with a security proof. Given a unique replicator identifier . Then the server divides the file into b-bit sized file blocks Bi and calculate where H is a collision-resistant hash function and . The output value can be obtained by taking the calculated as part of the algorithm input of the decodable verifiable delay function. The server stores all and the client continuously randomly selects i to challenge the server to return . If the server can respond to the corresponding result to the client within the specified time and the client can obtain by decoding in a very short time to complete the verification. If the server does not respond to the client correctly, must be calculated in T steps, but this calculation cannot be completed within the specified time.
Verifiable delay functions are widely used in blockchains. However, verifiable delay functions based on finite groups of unknown order are insecure against an adversary with access to a quantum computer. Quantum computers can easily compute the order of a group using Shor’s algorithm, making it easy to break the application of verifiable delay functions in blockchains. In addition, the post-quantum secure verifiable delay function based on supersingular elliptic curves needs to be verified by SNARG, and the structure is in its infancy and can only be limited to the field of elliptic curves. Therefore, it is an open problem to develop a verifiable delay function that has a simple structure in quantum computers and can be safely applied to blockchain.