Practical Three-Factor Authentication Protocol Based on Elliptic Curve Cryptography for Industrial Internet of Things
Abstract
1. Introduction
1.1. Literature Review
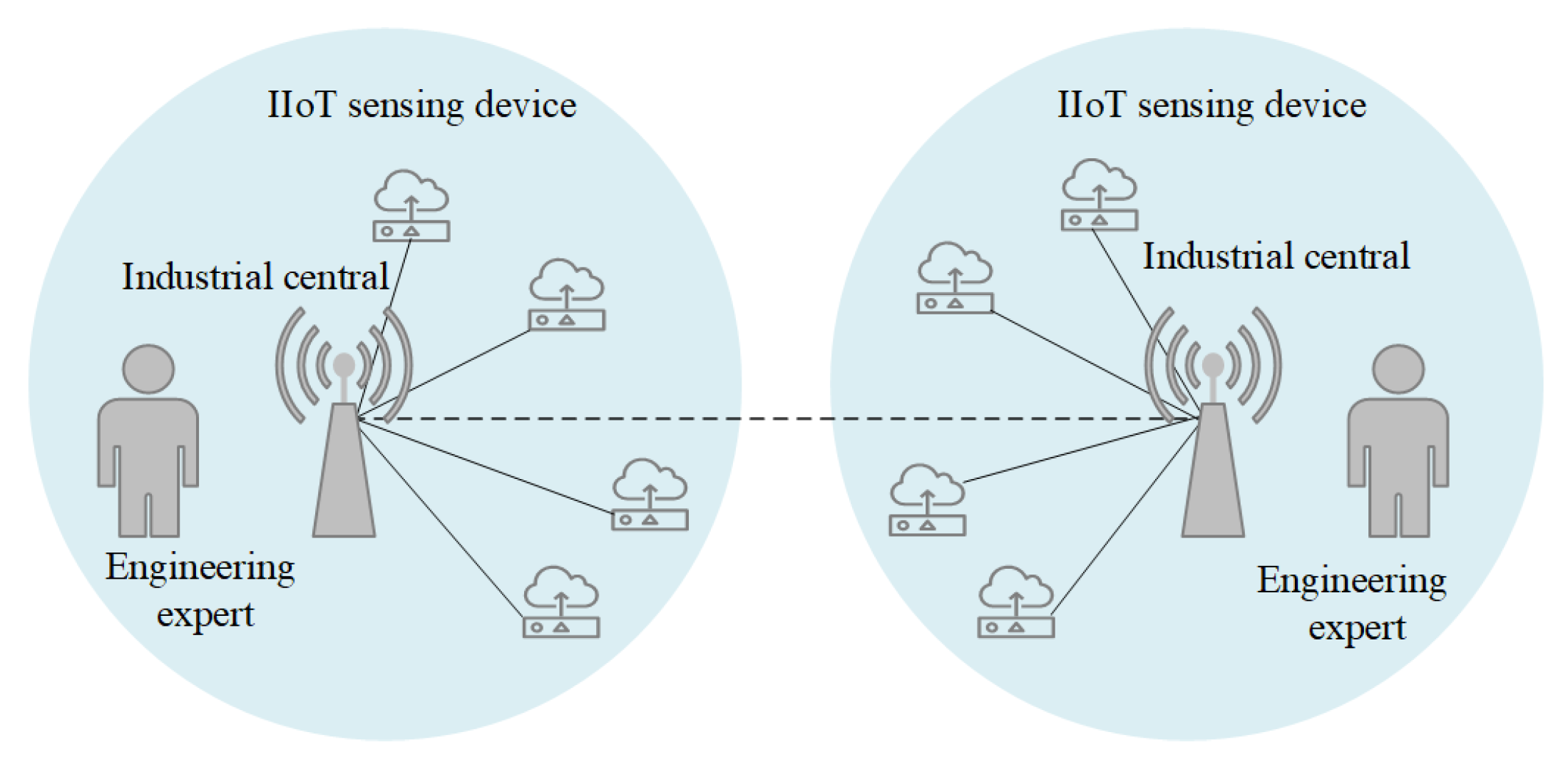
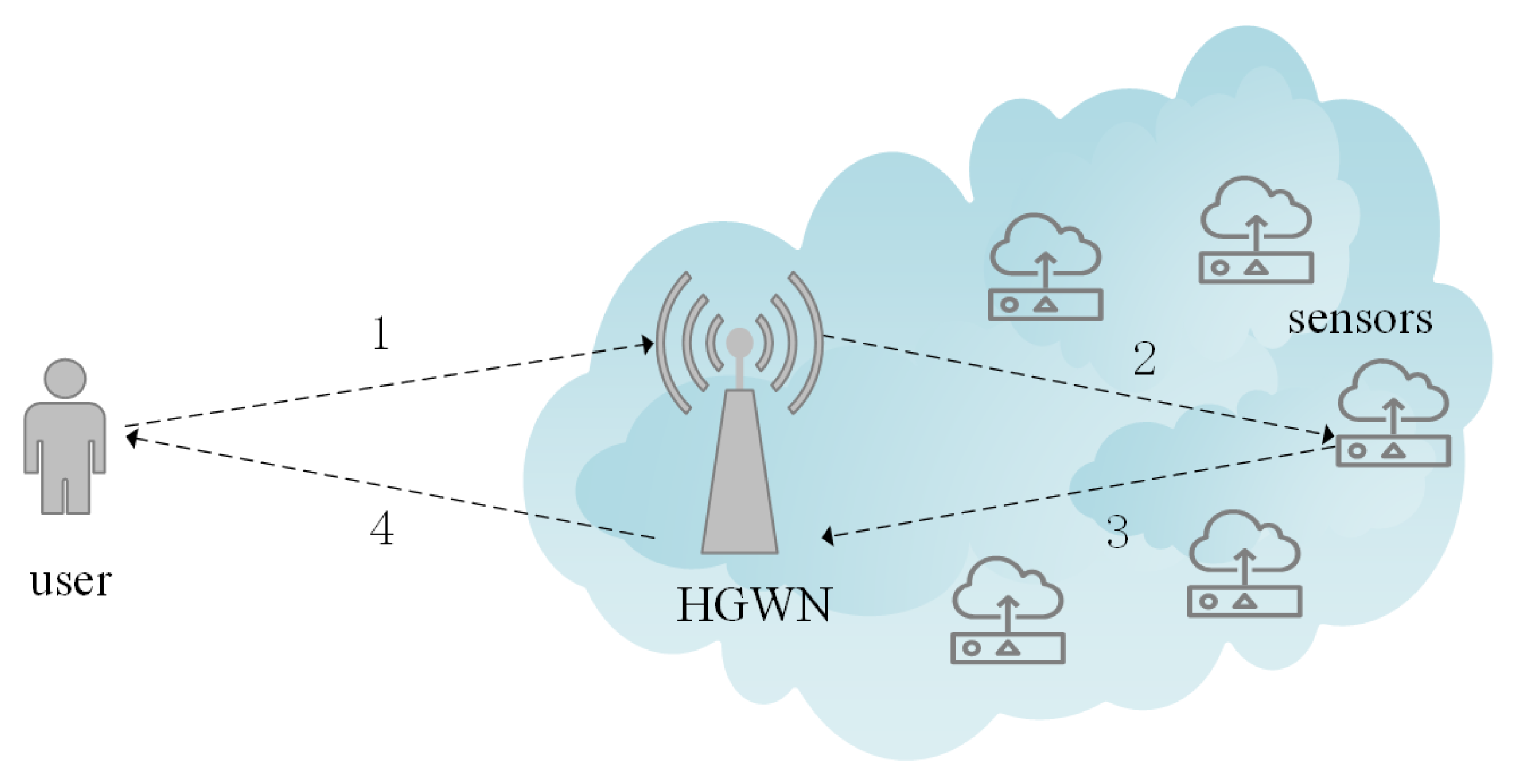
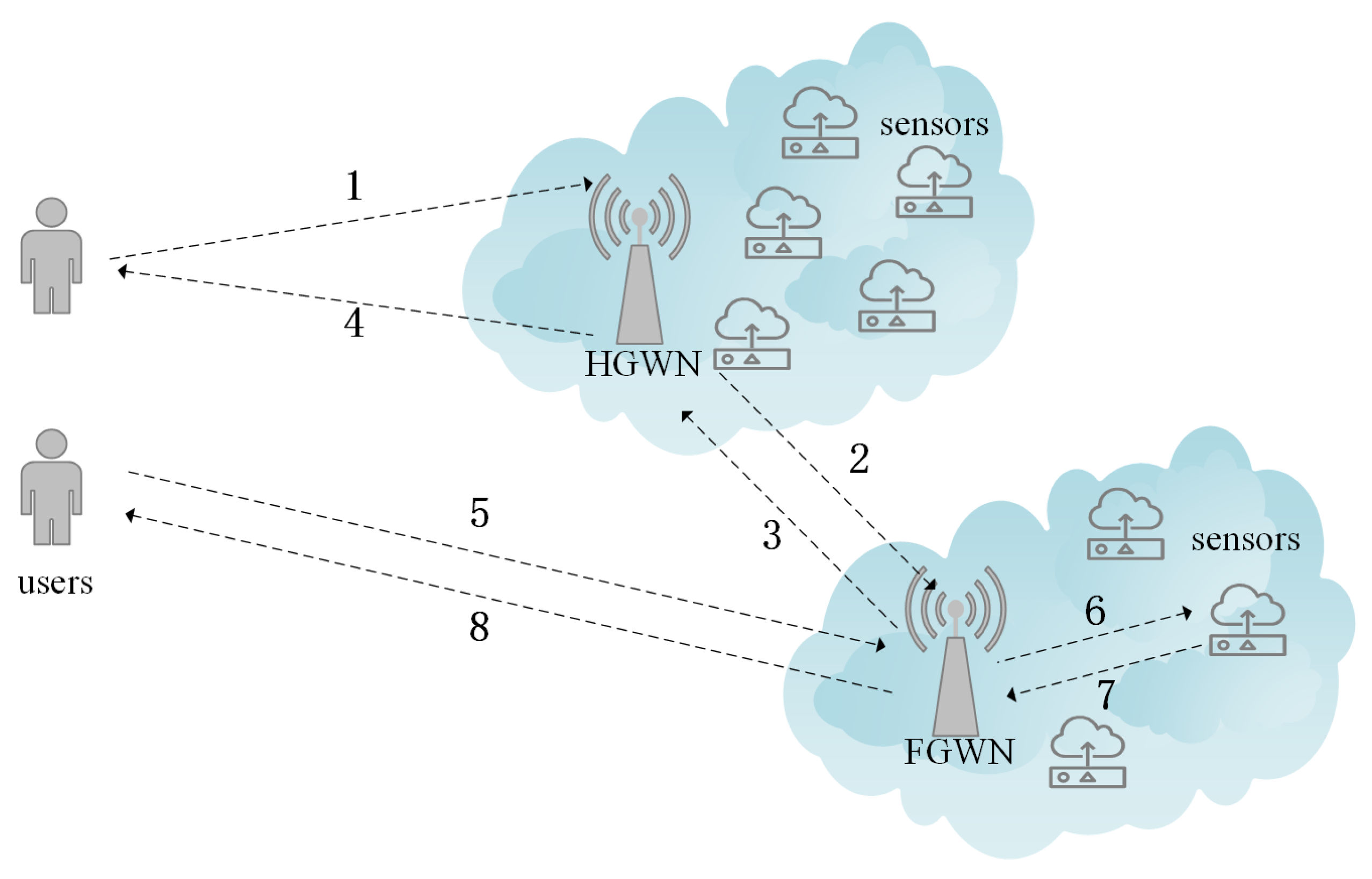
1.2. Network Model
1.3. Motivations and Contributions
2. Preliminaries
2.1. Elliptic Curve Cryptography
- The elliptic curve discrete logarithm problem (ECDLP): Figure 4 demonstrates points distributed over an elliptic curve in finite field . Selecting two points Q and P in Figure 4, where satisfy , where k is between 0 and 96 at random. Given k and P, it is easy to figure out Q by a scalar multiplication and addition rules. Nevertheless, given Q and P, it is difficult to calculate k.
- The elliptic curve Diffie–Hellman problem (ECDHP): It is scarcely possible to find when given and in polynomial time, where a and b are both between 0 and at random.
2.2. Threat Model
- The used one-way hash function is unbreakable.
- In a uniform protocol, an identical format is used by each entity that wishes to communicate.
- An adversary can eavesdrop, intercept, replay, and even modify all the transmitted messages over an open and insecure channel.
2.3. Fuzzy Extractor
- Probabilistic generation function : The original biometric fingerprint is the input of , and then the process outputs biometric identification key data and public parameter, namely .
- Deterministic reproduction procedure : Using the public parameter and the fingerprint reproduces key data , namely .
3. The Proposed Scheme
3.1. Initialization Phase
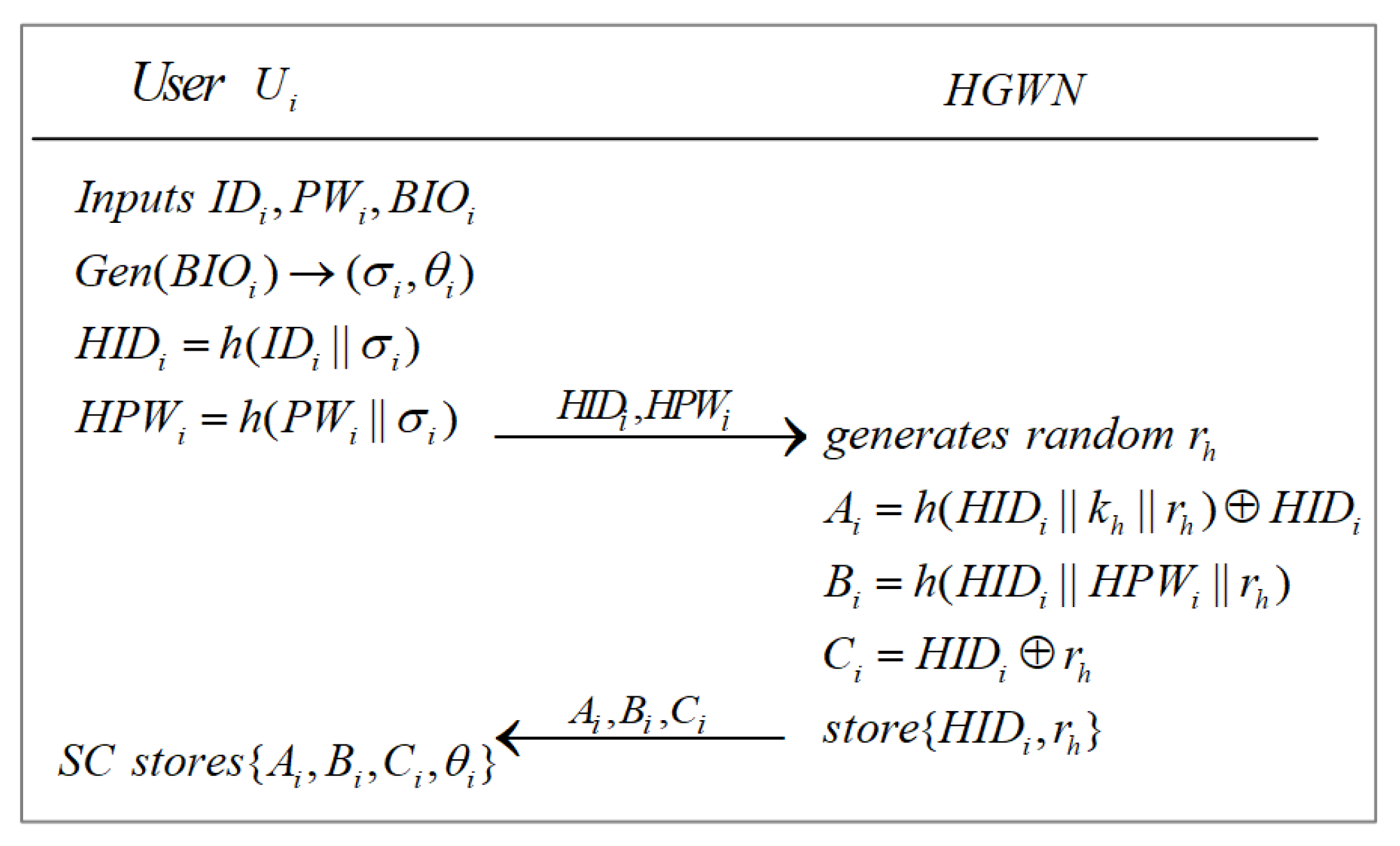
3.2. Registration Phase
3.2.1. User Registration Phase
3.2.2. Sensor Registration Phase
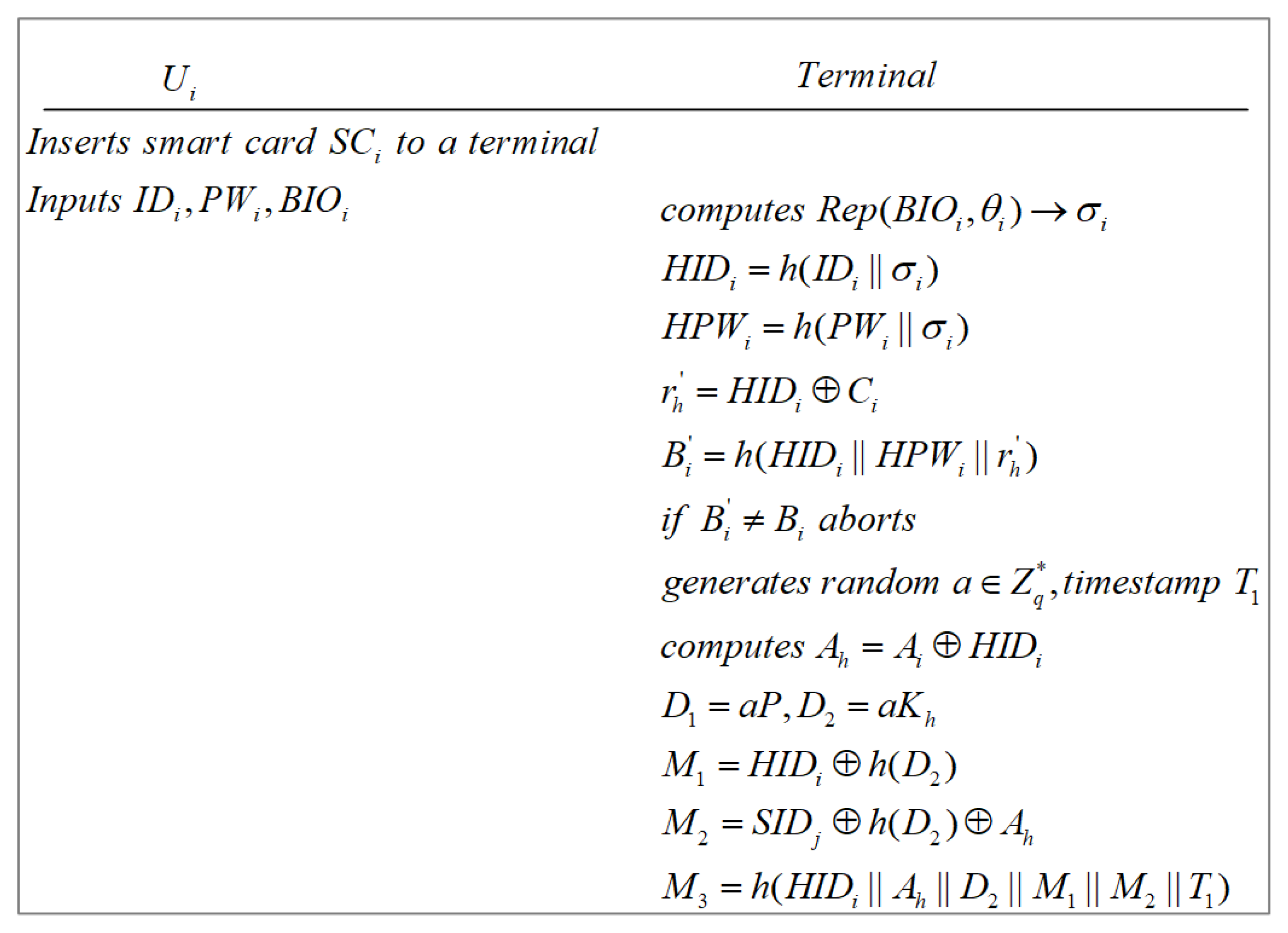
3.3. User Login Phase
3.4. Authentication and Key Agreement Phase
3.4.1. Authentication and Key Agreement in the HGWN
3.4.2. Authentication and Key Agreement in the FGWN
3.5. User Password Update Phase
4. Security Analysis
4.1. Formal Security Proof
4.1.1. Formal Security Model
4.1.2. Security Proof
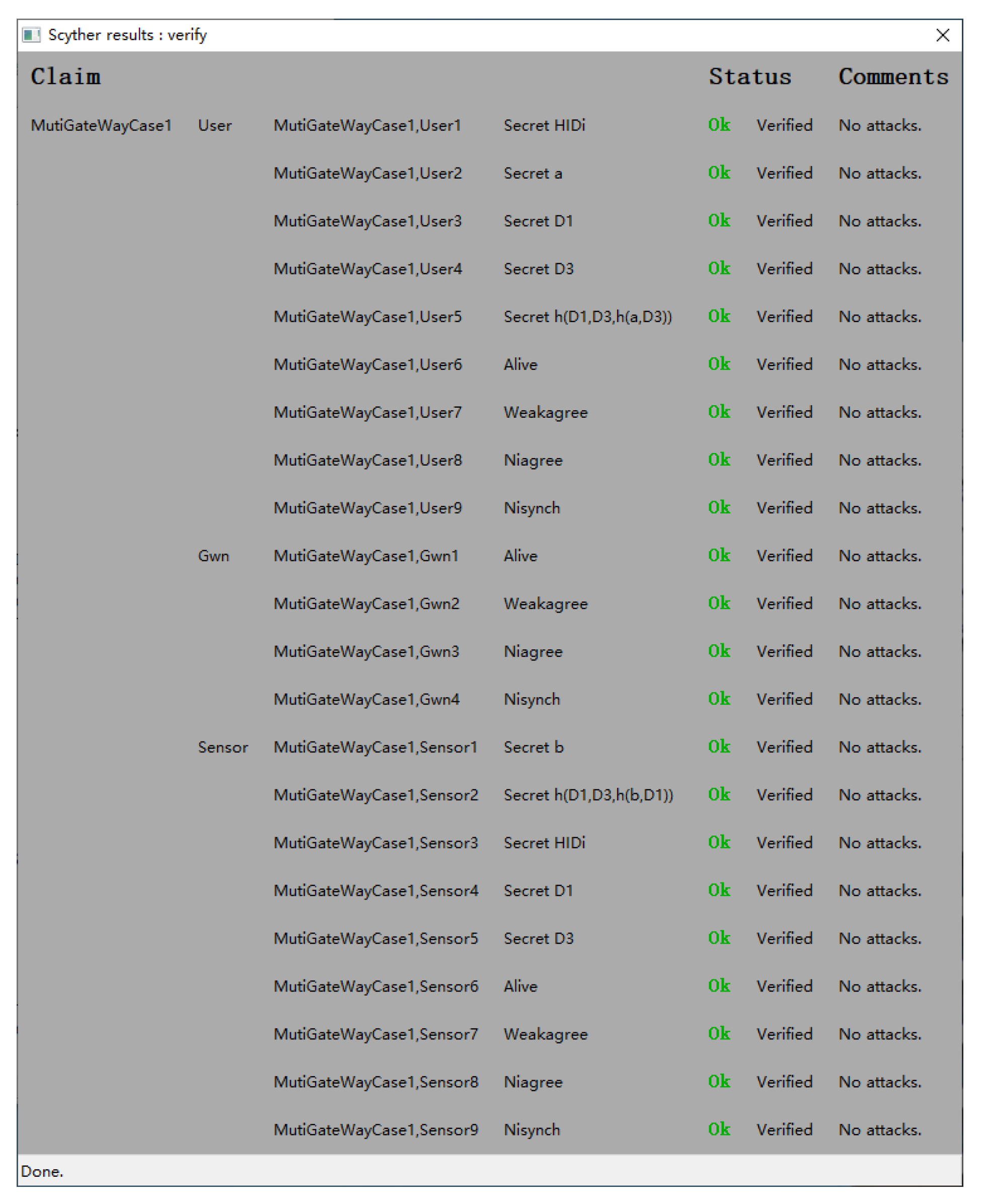
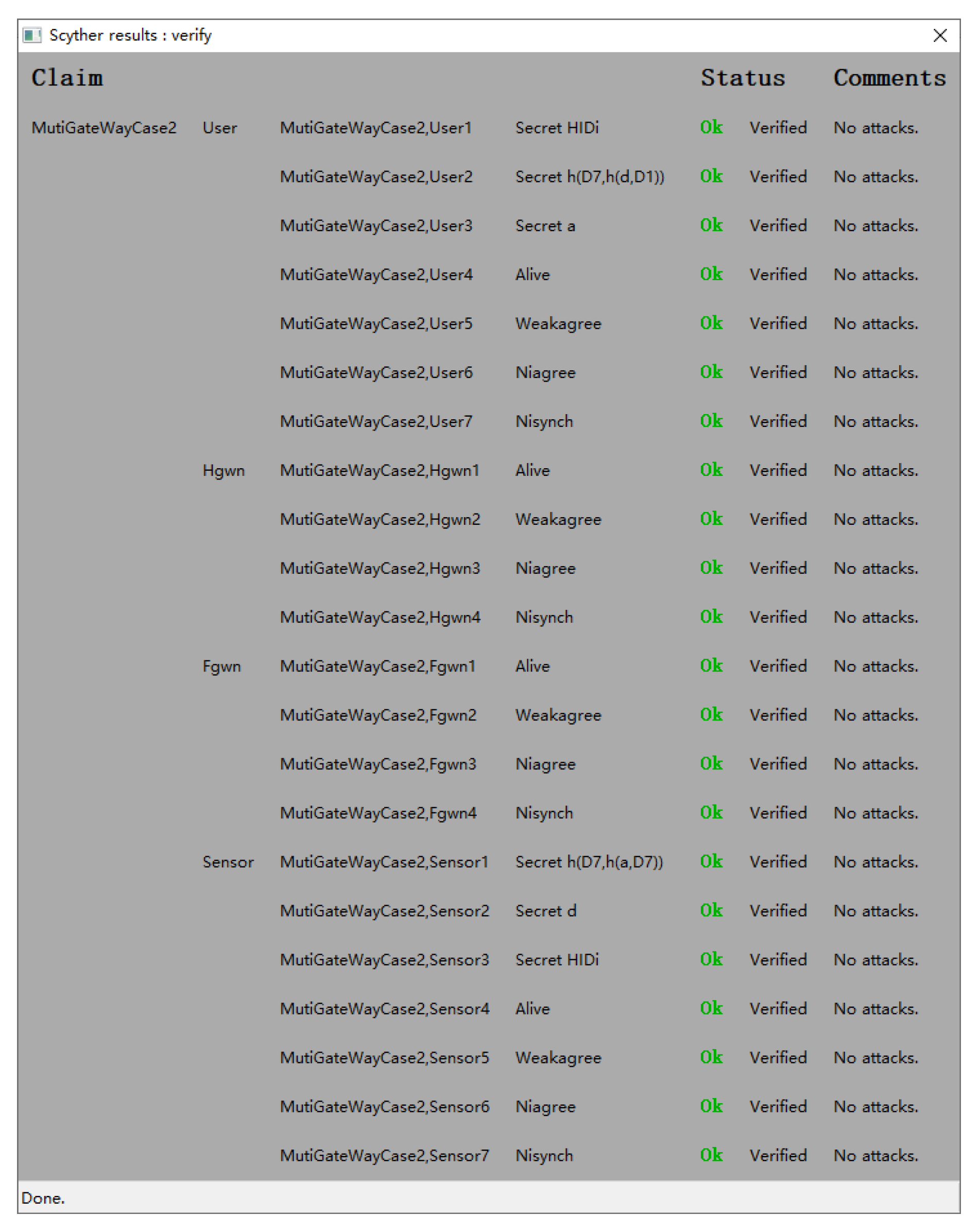
4.2. Formal Verification Using Scyther
4.3. Informal Security Analysis
4.3.1. Mutual Authentication
4.3.2. Session Key Agreement
4.3.3. Forward and Backward Secrecy
4.3.4. User Anonymity and Untraceability
4.3.5. Illegal Login Detection
4.3.6. Stolen Smart Card Attack
4.3.7. Replay Attack
4.3.8. Privileged Insider Attack
4.3.9. Desynchronization Attack
4.3.10. Impersonation Attack
5. Performance and Security Comparison
5.1. Security Features Comparison
5.2. Communication Cost Comparison
5.3. Computation Cost Comparison
6. Conclusions
Author Contributions
Funding
Institutional Review Board Statement
Informed Consent Statement
Data Availability Statement
Acknowledgments
Conflicts of Interest
Abbreviations
| IIoT | Industrial Internet of things |
| WSNs | Wireless sensor networks |
| XOR | Exclusive OR |
| ECC | Elliptic curve cryptography |
| ECDHP | Elliptic curve Diffie–Hellman problem |
| ECDLP | Elliptic curve discrete logarithm problem |
| AES | Advanced Encryption Standard |
| HGWN | Home gateway node |
| FGWN | Foreign gateway node |
| ROM | Random oracle model |
| AKA | Authentication and key agreement |
| SHA-1 | Secure Hash Standard 1 |
| SHA-256 | Secure Hash Standard 256 |
References
- Farag, H.M.; Österberg, P.; Gidlund, M. Congestion Detection and Control for 6TiSCH Networks in IIoT Applications. In Proceedings of the 2020 IEEE International Conference on Communications, ICC 2020, Dublin, Ireland, 7–11 June 2020; pp. 1–6. [Google Scholar]
- Sisinni, E.; Saifullah, A.; Han, S.; Jennehag, U.; Gidlund, M. Industrial Internet of Things: Challenges, Opportunities, and Directions. IEEE Trans. Ind. Inform. 2018, 14, 4724–4734. [Google Scholar] [CrossRef]
- Far, H.A.N.; Bayat, M.; Das, A.K.; Fotouhi, M.; Pournaghi, S.M.; Doostari, M. LAPTAS: Lightweight anonymous privacy-preserving three-factor authentication scheme for WSN-based IIoT. Wirel. Netw. 2021, 27, 1389–1412. [Google Scholar]
- Choudhary, K.; Gaba, G.S.; Butun, I.; Kumar, P. MAKE-IT—A Lightweight Mutual Authentication and Key Exchange Protocol for Industrial Internet of Things. Sensors 2020, 20, 5166. [Google Scholar] [CrossRef] [PubMed]
- Ma, C.; Wang, D.; Zhao, S. Security flaws in two improved remote user authentication schemes using smart cards. Int. J. Commun. Syst. 2014, 27, 2215–2227. [Google Scholar] [CrossRef]
- Sun, D. Security and Privacy Analysis of Vinoth et al.’s Authenticated Key Agreement Scheme for Industrial IoT. Symmetry 2021, 13, 1952. [Google Scholar] [CrossRef]
- Kumari, S.; Khan, M.K.; Atiquzzaman, M. User authentication schemes for wireless sensor networks: A review. Ad Hoc Netw. 2015, 27, 159–194. [Google Scholar] [CrossRef]
- Das, M.L. Two-factor user authentication in wireless sensor networks. IEEE Trans. Wirel. Commun. 2009, 8, 1086–1090. [Google Scholar] [CrossRef]
- Nyang, D.; Lee, M. Improvement of Das’s Two-Factor Authentication Protocol in Wireless Sensor Networks. Cryptology ePrint Archive. 2009. Available online: https://eprint.iacr.org/2009/631 (accessed on 25 August 2022).
- Vaidya, B.; Makrakis, D.; Mouftah, H.T. Improved two-factor user authentication in wireless sensor networks. In Proceedings of the IEEE 6th International Conference on Wireless and Mobile Computing, Networking and Communications, Niagara Falls, ON, Canada, 11–13 October 2010; pp. 600–606. [Google Scholar]
- He, D.; Gao, Y.; Chan, S.; Chen, C.; Bu, J. An Enhanced Two-factor User Authentication Scheme in Wireless Sensor Networks. Ad Hoc Sens. Wirel. Netw. 2010, 10, 361–371. [Google Scholar]
- Turkanovic, M.; Brumen, B.; Hölbl, M. A novel user authentication and key agreement scheme for heterogeneous ad hoc wireless sensor networks, based on the Internet of Things notion. Ad Hoc Netw. 2014, 20, 96–112. [Google Scholar] [CrossRef]
- Yeh, H.; Chen, T.; Liu, P.; Kim, T.; Wei, H. A Secured Authentication Protocol for Wireless Sensor Networks Using Elliptic Curves Cryptography. Sensors 2011, 11, 4767–4779. [Google Scholar] [CrossRef]
- Shi, W.; Gong, P. A New User Authentication Protocol for Wireless Sensor Networks Using Elliptic Curves Cryptography. Int. J. Distrib. Sens. Netw. 2013, 9, 730831. [Google Scholar] [CrossRef]
- Chang, C.; Le, H. A Provably Secure, Efficient, and Flexible Authentication Scheme for Ad hoc Wireless Sensor Networks. IEEE Trans. Wirel. Commun. 2016, 15, 357–366. [Google Scholar] [CrossRef]
- Li, X.; Peng, J.; Niu, J.; Wu, F.; Liao, J.; Choo, K.R. A Robust and Energy Efficient Authentication Protocol for Industrial Internet of Things. IEEE Internet Things J. 2018, 5, 1606–1615. [Google Scholar] [CrossRef]
- Amin, R.; Biswas, G.P. A secure light weight scheme for user authentication and key agreement in multi-gateway based wireless sensor networks. Ad Hoc Netw. 2016, 36, 58–80. [Google Scholar] [CrossRef]
- Das, A.K.; Sutrala, A.K.; Kumari, S.; Odelu, V.; Wazid, M.; Li, X. An efficient multi-gateway-based three-factor user authentication and key agreement scheme in hierarchical wireless sensor networks. Secur. Commun. Netw. 2016, 9, 2070–2092. [Google Scholar] [CrossRef]
- Wu, F.; Xu, L.; Kumari, S.; Li, X.; Shen, J.; Choo, K.R.; Wazid, M.; Das, A.K. An efficient authentication and key agreement scheme for multi-gateway wireless sensor networks in IoT deployment. J. Netw. Comput. Appl. 2017, 89, 72–85. [Google Scholar] [CrossRef]
- Srinivas, J.; Mukhopadhyay, S.; Mishra, D. Secure and efficient user authentication scheme for multi-gateway wireless sensor networks. Ad Hoc Netw. 2017, 54, 147–169. [Google Scholar] [CrossRef]
- Wang, D.; Li, W.; Wang, P. Measuring Two-Factor Authentication Schemes for Real-Time Data Access in Industrial Wireless Sensor Networks. IEEE Trans. Ind. Inform. 2018, 14, 4081–4092. [Google Scholar] [CrossRef]
- Bellare, M.; Rogaway, P. Random Oracles are Practical: A Paradigm for Designing Efficient Protocols. In Proceedings of the 1st ACM Conference on Computer and Communications Security, CCS’93, Fairfax, VA, USA, 3–5 November 1993; pp. 62–73. [Google Scholar]
- Cremers, C.J.F. The Scyther Tool: Verification, Falsification, and Analysis of Security Protocols. In Proceedings of the 20th International Conference, CAV 2008, Princeton, NJ, USA, 7–14 July 2008; Lecture Notes in Computer Science. Springer: Berlin/Heidelberg, Germany, 2008; Volume 5123, pp. 414–418. [Google Scholar]
- Koblitz, N. Elliptic Curve Cryptosystems. Math. Comput. 1987, 48, 203–209. [Google Scholar] [CrossRef]
- Miller, V.S. Use of Elliptic Curves in Cryptography. In Proceedings of the Advances in Cryptology—CRYPTO ’85, Santa Barbara, CA, USA, 18–22 August 1985; Lecture Notes in Computer Science. Williams, H.C., Ed.; Springer: Berlin/Heidelberg, Germany, 1985; Volume 218, pp. 417–426. [Google Scholar]
- Dolev, D.; Yao, A.C. On the security of public key protocols. IEEE Trans. Inf. Theory 1983, 29, 198–207. [Google Scholar] [CrossRef]
- Dodis, Y.; Reyzin, L.; Smith, A.D. Fuzzy Extractors: How to Generate Strong Keys from Biometrics and Other Noisy Data. In Proceedings of the Advances in Cryptology—EUROCRYPT, Interlaken, Switzerland, 2–6 May 2004; Lecture Notes in Computer Science. Springer: Berlin/Heidelberg, Germany, 2004; Volume 3027, pp. 523–540. [Google Scholar]
- Canetti, R.; Krawczyk, H. Analysis of Key-Exchange Protocols and Their Use for Building Secure Channels. In Proceedings of the EuroCrypt, Innsbruck, Austria, 6–10 May 2001; Pfitzmann, B., Ed.; Springer: Berlin/Heidelberg, Germany, 2001; Volume 2045, pp. 453–474. [Google Scholar]
- Srinivas, J.; Das, A.K.; Kumar, N.; Rodrigues, J.J.P.C. Cloud Centric Authentication for Wearable Healthcare Monitoring System. IEEE Trans. Dependable Secur. Comput. 2020, 17, 942–956. [Google Scholar] [CrossRef]
- Challa, S.; Das, A.K.; Odelu, V.; Kumar, N.; Kumari, S.; Khan, M.K.; Vasilakos, A.V. An efficient ECC-based provably secure three-factor user authentication and key agreement protocol for wireless healthcare sensor networks. Comput. Electr. Eng. 2018, 69, 534–554. [Google Scholar] [CrossRef]
- Lee, C.; Chen, C.; Wu, P.; Chen, T. Three-factor control protocol based on elliptic curve cryptosystem for universal serial bus mass storage devices. IET Comput. Digit. Tech. 2013, 7, 48–56. [Google Scholar] [CrossRef]
- Dang, Q.H. Secure hash standard. In US Doc/NIST FIPS Publication 180-4; NIST: Gaithersburg, MD, USA, 2015. [Google Scholar]





| Symbol | Description |
|---|---|
| System administrator | |
| ith user node | |
| jth sensor node | |
| Smart card of | |
| Home gateway node | |
| Foreign gateway node | |
| Identity of | |
| Identity of | |
| Password of | |
| Biometric information of | |
| Private key and public key of | |
| Private key and public key of | |
| Random numbers | |
| Random numbers | |
| P | A point on the elliptic curve |
| Timestamps | |
| Acceptable maximum transmission delay | |
| Session key | |
| One-way hash function | |
| ⊕ | Exclusive-or operation |
| Concatenation operation | |
| Fuzzy extractor probabilistic generation procedure | |
| Fuzzy extractor deterministic reproduction procedure |
| Security Properties | [13] | [17] | [18] | [19] | [20] | Ours |
|---|---|---|---|---|---|---|
| Mutual authentication | × | ✓ | ✓ | ✓ | ✓ | ✓ |
| Session key agreement | ✓ | ✓ | ✓ | × | × | ✓ |
| Forward and backward secrecy | × | × | × | × | × | ✓ |
| User anonymity | ✓ | × | × | × | × | ✓ |
| Untraceability property | × | × | ✓ | × | × | ✓ |
| Illegal login detection | × | ✓ | ✓ | × | ✓ | ✓ |
| Stolen smart card attack | × | × | ✓ | ✓ | ✓ | ✓ |
| Replay attack | ✓ | ✓ | ✓ | ✓ | ✓ | ✓ |
| Insider attack | ✓ | ✓ | ✓ | × | ✓ | ✓ |
| Desynchronization attack | × | × | ✓ | ✓ | × | ✓ |
| Impersonation attack | × | × | ✓ | × | ✓ | ✓ |
| Scheme | Number of Messages | Communication Cost (bits) | |
|---|---|---|---|
| [13] | Case-1 | 2 | 1504 |
| [17] | Case-1 | 4 | 2528 |
| Case-2 | 5 | 3008 | |
| [18] | Case-1 | 3 | 2784 |
| Case-2 | 6 | 4704 | |
| [19] | Case-1 | 4 | 2688 |
| Case-2 | 8 | 4480 | |
| [20] | Case-1 | 4 | 2368 |
| Case-2 | 7 | 3904 | |
| Ours | Case-1 | 4 | 2848 |
| Case-2 | 8 | 4416 |
| Symbol | Description | Approximate Computation Time (s) |
|---|---|---|
| Hash function | 0.00032 | |
| ECC point multiplication | 0.0171 | |
| ECC point addition | 0.0044 | |
| Symmetric encryption/decryption | 0.0056 | |
| Fuzzy extractor function | 0.0171 |
Publisher’s Note: MDPI stays neutral with regard to jurisdictional claims in published maps and institutional affiliations. |
© 2022 by the authors. Licensee MDPI, Basel, Switzerland. This article is an open access article distributed under the terms and conditions of the Creative Commons Attribution (CC BY) license (https://creativecommons.org/licenses/by/4.0/).
Share and Cite
Zhao, X.; Li, D.; Li, H. Practical Three-Factor Authentication Protocol Based on Elliptic Curve Cryptography for Industrial Internet of Things. Sensors 2022, 22, 7510. https://doi.org/10.3390/s22197510
Zhao X, Li D, Li H. Practical Three-Factor Authentication Protocol Based on Elliptic Curve Cryptography for Industrial Internet of Things. Sensors. 2022; 22(19):7510. https://doi.org/10.3390/s22197510
Chicago/Turabian StyleZhao, Xingwen, Dexin Li, and Hui Li. 2022. "Practical Three-Factor Authentication Protocol Based on Elliptic Curve Cryptography for Industrial Internet of Things" Sensors 22, no. 19: 7510. https://doi.org/10.3390/s22197510
APA StyleZhao, X., Li, D., & Li, H. (2022). Practical Three-Factor Authentication Protocol Based on Elliptic Curve Cryptography for Industrial Internet of Things. Sensors, 22(19), 7510. https://doi.org/10.3390/s22197510





