1. Introduction
Currently, wireless networks are becoming increasingly pervasive, extending their reach to uncharted territories such as farms, manufacturing plants, retail stores, warehouses, and autonomous vehicles, to name a few, aiming to provide access to a multitude of objects and unleash the full potential of the Internet of Things (IoT) [
1,
2,
3,
4,
5,
6,
7]. To create a smart environment, IoT technology has led to a growing interconnection between devices at a scale and speed never seen before [
8,
9]. This unprecedented number of over-the-air connections poses significant challenges to the design of next-generation wireless networks due to the need to support (i) a massive amount of concurrent connections and data traffic, (ii) highly heterogeneous and stringent quality-of-service (QoS) requirements, and (iii) efficient and fair use of scarce network resources (e.g., energy and bandwidth) [
10]. In this effort, it is envisaged that Wireless Local Area Networks (WLANs) will play an important role in the deployment and dissemination of IoT applications because Wi-Fi devices have been widely adopted and can operate in the unlicensed spectrum [
11]. However, current Wi-Fi networks (e.g., IEEE 802.11ac/ax) face many challenges in IoT scenarios, which generally consist of large-scale networks deployed over areas that are wider than traditional WLANs [
12]. Moreover, as the number of competing stations increases, traditional IEEE 802.11 networks become less efficient due to a higher probability of data packet collisions, leading to significant performance degradation. Motivated by such IoT features, the IEEE 802.11ah amendment [
13] was developed to operate on sub-GHz frequency channels in order to support higher network coverage. In addition, it introduces a number of other features that allow up to 8191 stations to be associated with a single access point under higher energy efficiency, which makes it an attractive wireless access technology for IoT applications.
The IEEE 802.11ah standard inherited the physical layer of the IEEE 802.11ac, with adaptations to operate at frequencies below 1 GHz, and channel bandwidths ranging from 1 MHz to 16 MHz, with the 1 MHz and 2 MHz bands being widely adopted. In particular, many new features were incorporated into the MAC sub-layer in order to provide better support for energy consumption and channel access under dense network scenarios, such as the mechanisms of the restricted access window (RAW), traffic indication map (TIM), and target wake time (TWT), along with reduced frame headers and faster association and authentication procedures. In fact, the RAW mechanism is one of the main innovations implemented to handle dense scenarios, by which stations are grouped into “RAW groups,” which are further divided into RAW slots. Only stations assigned to a given RAW slot can compete for channel access during the occurrence of this specific time slot. The assignment of stations to RAW groups and RAW slots, as well as their number and time duration, are all specified by the base station in the so-called RAW Parameter Set (RPS) transmitted in the beginning of each beacon interval (whose time duration can also be changed dynamically).
Due to the importance and growing interest in this standard [
14,
15,
16], a number of works have proposed analytical models to evaluate the performance of IEEE 802.11ah networks, especially with respect to the operation of the RAW mechanism. However, in general, previous analytical models have either included features that are not specified in the IEEE 802.11ah standard or have not been validated against some independently-developed simulator that is widely adopted by the networking community. In fact, many previous works have validated their results based on their own customized simulators, whose accuracy and compliance to standard specifications have not been demonstrated. In this sense, the validation of an analytical model against a standard-compliant, well-known simulator is key to establishing its prediction accuracy.
Section 2 discusses a number of works related to the analytical modeling of IEEE 802.11ah networks, especially regarding the consideration of the RAW mechanism.
Previously, we have proposed an analytical model for the operation of an IEEE 802.11ah station within its assigned RAW slot under saturated traffic and ideal channel conditions [
17]. The proposed model was based on a discrete-time Markov chain formulation that explicitly takes into account the issue of RAW slot time completion, i.e., the moment after which the station can no longer access the channel and thus must wait for its assigned RAW slot in the next beacon interval to contend for channel access again. While the numerical results obtained with the previous analytical model showed close agreement with simulations carried out in the ns-3 simulator [
18] and based on an independently-derived IEEE 802.11ah module [
19], it still contains some limitations. In particular, its key parameter, the “probability of RAW slot time completion”, did not explicitly consider its dependence on the effective time length of a given RAW slot, and the average throughput expression was not general enough to consider different RAW groups with corresponding RAW slots. Moreover, the performance of the analytical model was not compared against other analytical models proposed in the literature, which is a key step to determining the actual efficacy and strength of our analytical model.
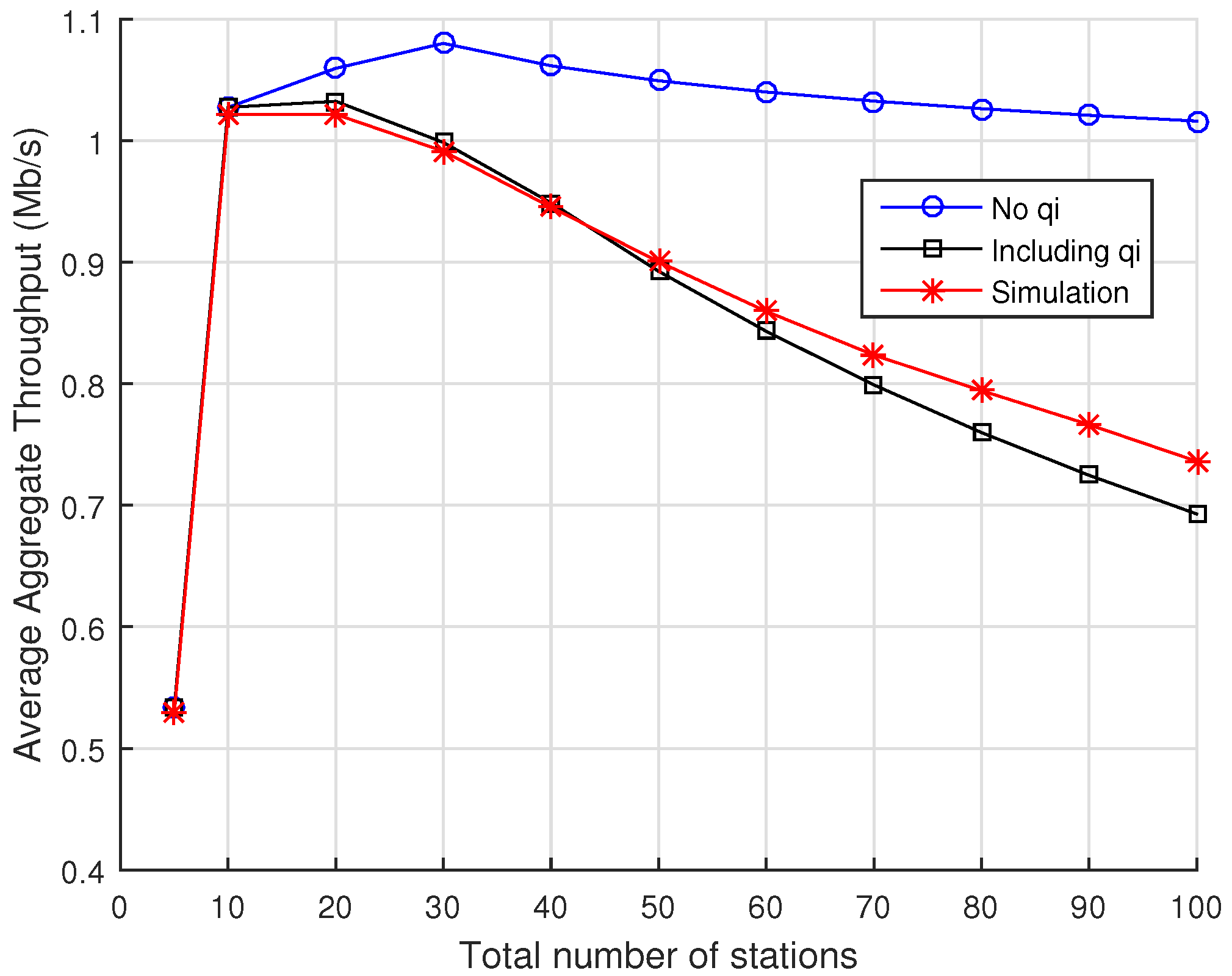
Considering the aforementioned limitations, in this paper, we extend our analytical model by introducing important modifications. First, we improve the analytical model by explicitly considering the impact of the effective time length of a station’s RAW slot in the probability of “RAW slot time completion”. Second, the importance of this probability to the performance of our analytical model is demonstrated in a specific section dedicated to comparisons with computer simulations by considering two cases for our model: when such probability is taken into account, and when it is removed from the model. Third, the analytical development for the computation of the average aggregate throughput is made more general by allowing the consideration of different RAW groups with corresponding RAW slots. Fourth, we compare the average aggregate throughput predicted by our analytical model with results provided by two well-known analytical models available in the literature: Zheng’s model [
20] is one of the first works that addresses synchronized grouping of stations, and it is based on a mean value analysis approach, while Sangeetha’s model [
21] is a more recent work that follows an approach similar to ours, based on a discrete-time Markov chain model for a station’s backoff operation. We chose these models for comparison because they are fully-specified analytical models that make different assumptions regarding protocol behavior and treat the event of RAW slot time completion differently, which is key for comparison with our model. Incidentally, it is worth mentioning that Ali et al. [
22] have proposed an analytical model that contains a probability parameter that plays a similar role to the one we proposed independently [
17] for the “RAW slot time completion”. Unfortunately, their work does not provide an explicit expression for the computation of this probability (represented by the parameter
in the transition probabilities of their Markov Chain in Equations (7), (8), (11) and (12) in [
22]), which makes it unsuitable for comparison.
In summary, this paper extends our previous work by providing the following key contributions:
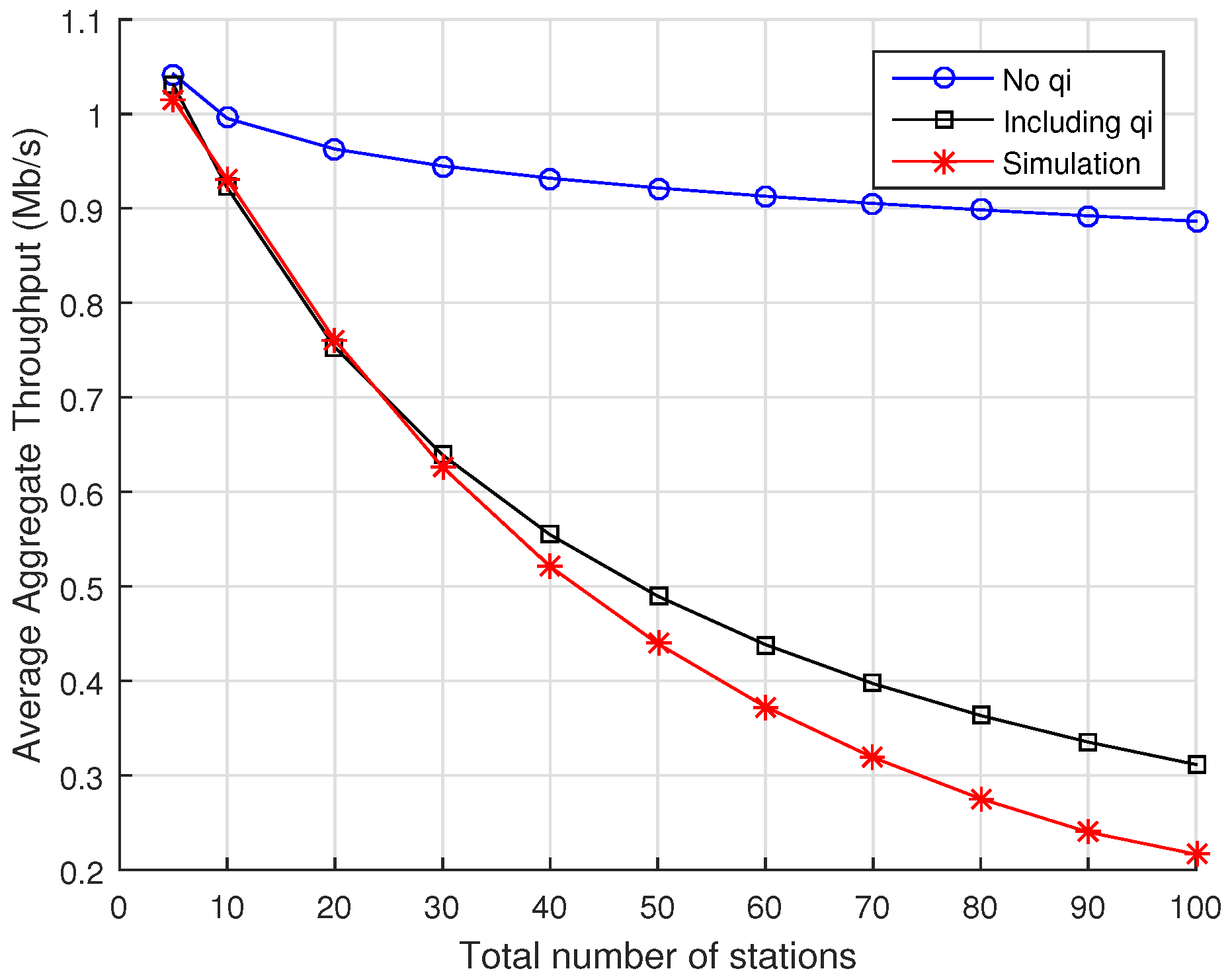
The analytical model is improved to consider the impact of the effective time length of a station’s RAW slot into the probability of “RAW slot time completion”, which is a key parameter designed to better reflect the station’s dynamics in its assigned RAW slot;
The key role of the probability of “RAW slot time completion” to our model is demonstrated via comparison with computer simulations by considering the cases when such probability is either included or not in the model;
We derive a general expression for the computation of the average aggregate throughput over a set of RAW groups and corresponding RAW slots;
Numerical results of the new analytical model are compared with ns-3 simulations based on the well-known IEEE 802.11ah module independently developed by Le Tian et al. [
19,
23];
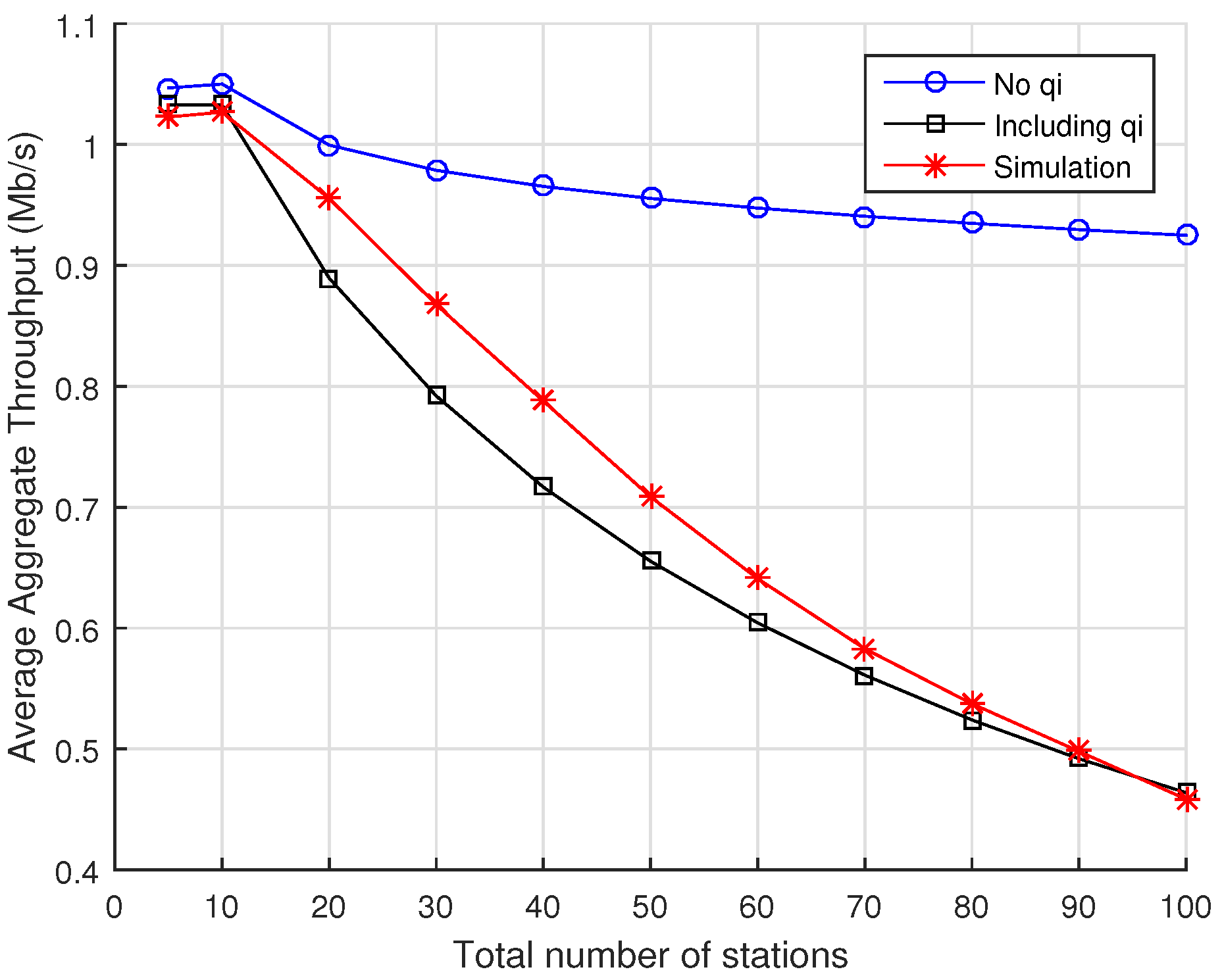
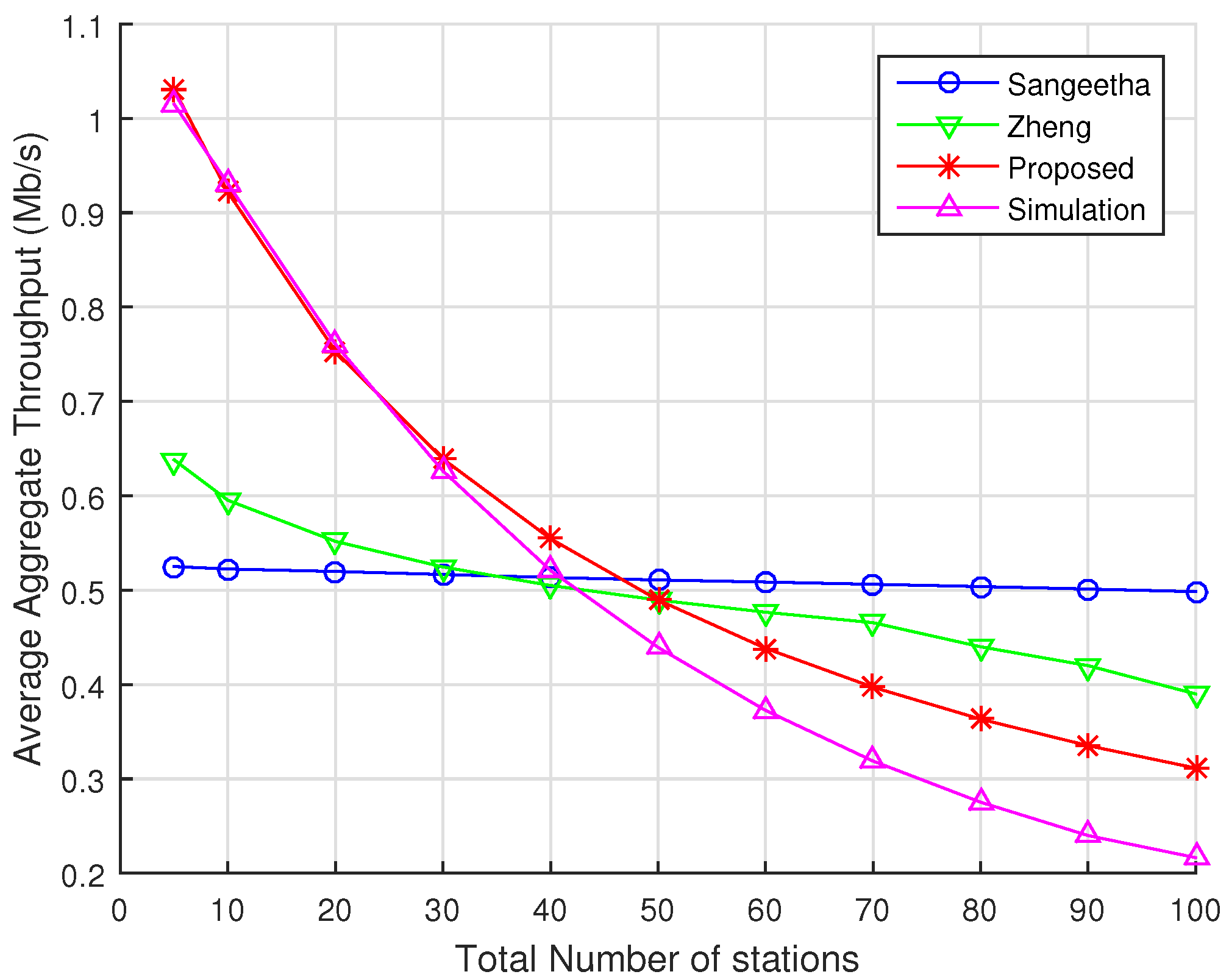
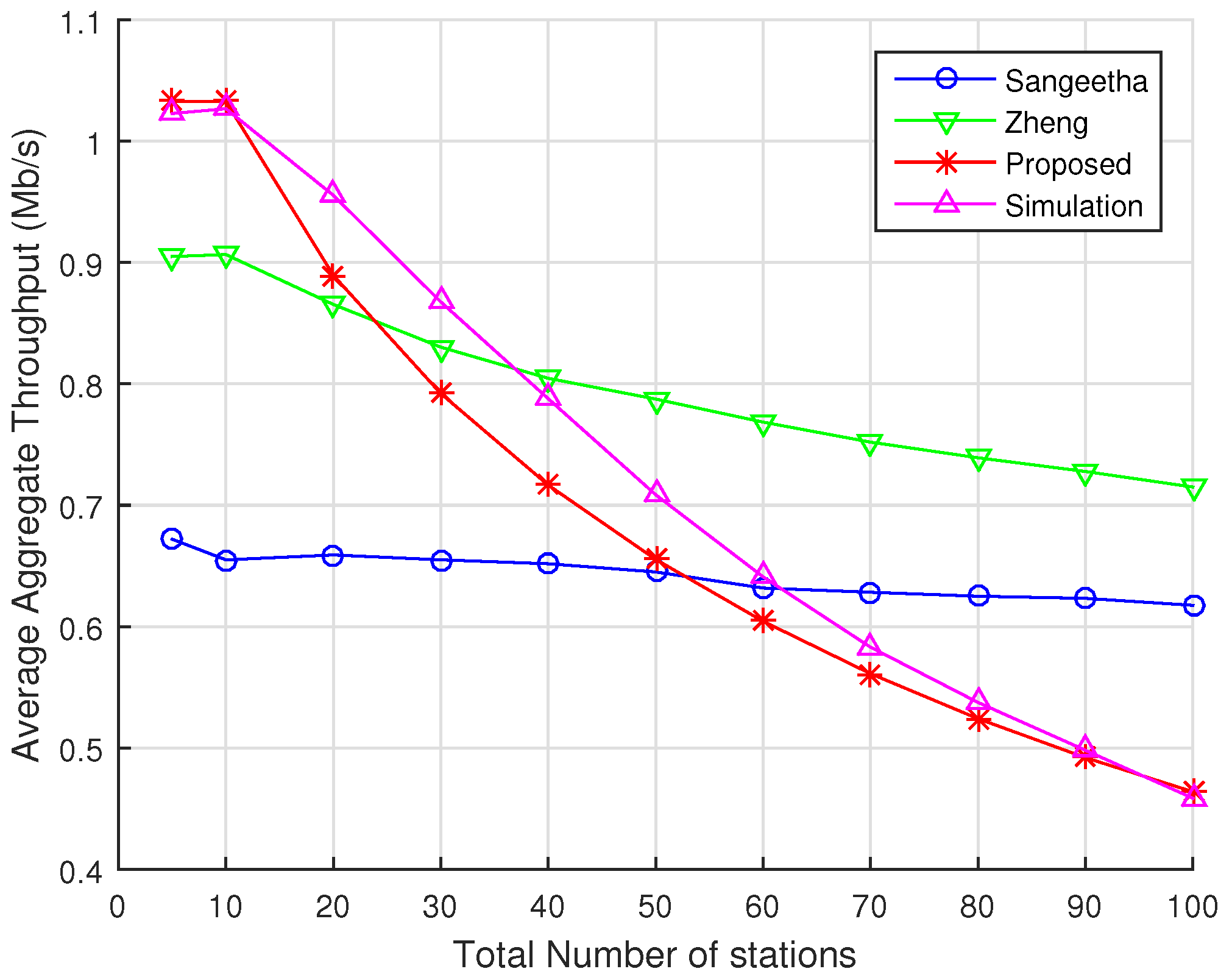
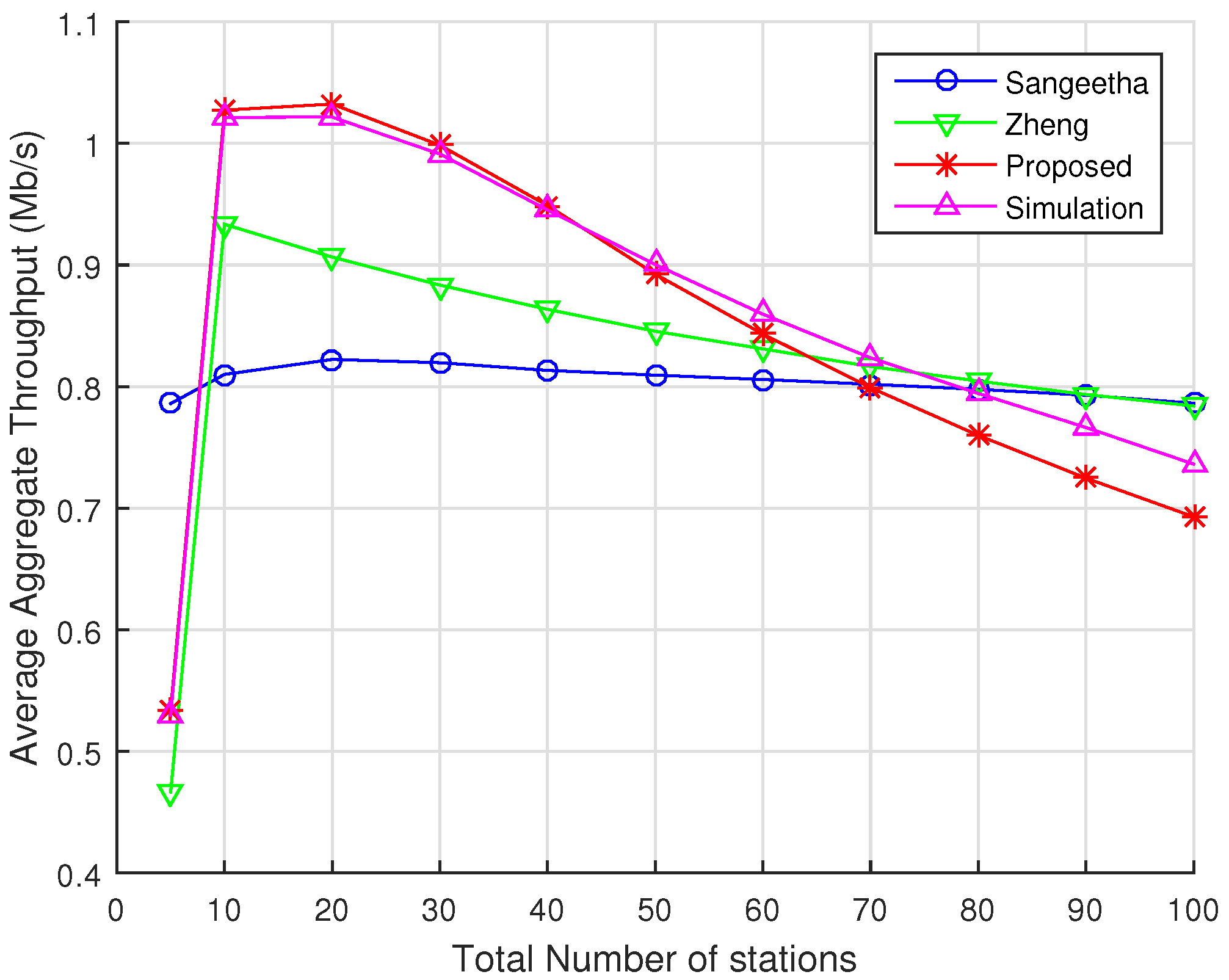
The prediction accuracy of our new analytical model is shown to be significantly better than the prediction delivered by two other well-known analytical models available in the literature.
The rest of the paper is organized as follows:
Section 2 discusses related works, while
Section 3 provides an overview of the main features of the IEEE 802.11ah.
Section 4 details our analytical model, and in
Section 5, we provide a brief description of the two analytical models we use to compare with our own.
Section 6 presents the numerical results, while the conclusions of our paper and a discussion of future works are presented in
Section 7 and
Section 8, respectively.
2. Related Work
The analytical modeling of IEEE 802.11ah networks using the RAW mechanism has been a topic of growing interest in the past few years. In the following, we present the main analytical models proposed to date.
Zheng et al. [
20] proposed an analytical model based on mean value analysis (MVA) to estimate the average network throughput under saturated traffic conditions. They considered both the cases for the
cross slot boundary (CSB) mechanism: if enabled, it allows a station to proceed with a packet transmission that can exceed the station’s allocated RAW slot time. Otherwise, a Markov chain model was proposed to estimate the number of mini-slots occupied by the last data transmission in the RAW slot, so that the duration of the next RAW slot can be calculated. They validated their analytical model with simulation results drawn from their own customized simulator.
Qutab-ud-din et al. [
24] analyzed the performance of the RAW mechanism when the CSB is disabled and proposed four possible backoff schemes in the holding period to improve the throughput and energy efficiency of saturated IEEE 802.11ah networks. They used Zheng’s [
20] analytical model as a benchmark to validate their simulation model developed in the OMNET++ simulator. Therefore, no new analytical model was actually proposed. Mahesh and Harigovindan [
25] also used Zheng’s model to propose a grouping scheme based on the average transmission time requirements of devices with the assignment of a priority level to each defined group. Then, they extended Zheng’s analytical model to deal with the average throughput of a single group. They evaluated the average aggregate data transfer by comparing their proposed grouping scheme with uniform grouping using the ns-3 simulator.
Raeesi et al. [
26] proposed an analytical model that assumes saturated traffic conditions to estimate the throughput and energy consumption for both basic and four-way handshake mechanisms. They investigated the performance gains obtained with the RAW mechanism compared to the regular operation of the distributed coordination function (DCF). However, their model does not consider the number of nodes as a parameter, and the probability of packet collisions is an input value, not a function of the number of nodes and channel contention. Moreover, the RAW mechanism is not represented in the model. Raeesi et al. [
27] also worked on the scenario of multiple IEEE 802.11ah access points with a relatively high number of associated stations. Unfortunately, the proposed analytical model only deals with a theoretical maximum throughput that assumes no packet collisions (i.e., the backoff contention window never increases) and, again, the RAW mechanism is not incorporated in the model.
Park et al. [
28] developed an algorithm to estimate the number of devices in the uplink access of IEEE 802.11ah networks in order to determine the optimal duration of the RAW slot. However, they used the original analytical model for the IEEE 802.11 DCF provided by Bianchi [
29] to represent the behavior of traffic-saturated stations in the IEEE 802.11ah network. Therefore, the analytical model does not take into account the RAW mechanism explicitly. Moreover, they compared the performance of the uplink total success probability delivered by their algorithm with the legacy (fixed) scheme via analysis and simulations, based on their own simulator.
Sangeetha et al. [
21] adopted a discrete-time Markov chain model for the backoff operation of a station in its assigned RAW slot under saturated and non-saturated traffic conditions, using Bianchi’s approach [
29] to compute the average throughput. Their model focuses on the case when the CSB is disabled and assumes that the backoff counter stops at the end of the RAW slot to resume its operation in the next assigned RAW slot, starting from the frozen backoff counter value. Thus, when the backoff counter reaches the value 1, the station checks whether the remaining time within the RAW slot is enough to transmit the whole data packet. If not, the station goes to a “defer state” and waits for its next assigned RAW slot in the following beacon interval. However, the described freezing of the backoff counter value is not defined in the standard. Instead, the station is supposed to discard the backoff counter value at the end of a RAW slot and start a new one in the beginning of the next RAW slot. The proposed analytical model was validated based on the ns-3 simulator. Later, they extended their analytical model to address the grouping of stations according to traffic priority [
30].
Ali et al. [
31] studied the efficiency of the RAW mechanism under non-ideal channel conditions and non-saturated traffic by proposing a Markov chain and an M/G/1 queue-based analytical model. In [
22], Ali et al. [
22] proposed a discrete-time Markov chain model for IEEE 802.11ah to evaluate the performance of heterogeneous IoT networks with different QoS traffic demands. They considered the case of a disabled CSB and used the same idea as Sangeetha et al. [
21] regarding a “defer state” (alternatively named as “delay state”) in case the remaining time within a RAW slot is not enough for data packet transmission. Nevertheless, unlike Sangeetha’s work, the backoff counter is reset in the beginning of every RAW slot. In addition, similar to our previous work [
17], they defined a state transition probability to capture the ending of a RAW slot at any given moment during a station’s backoff operation, which makes it return to an initial state for the following RAW slot. Unfortunately, their work did not provide an expression to compute this probability or a technique to estimate it, which makes their work unsuitable for comparison. Also using the idea of a defer state, Bardala and Harigovindan [
32] proposed a discrete Markov chain for the backoff operation of a station in a RAW slot. In their work, the station checks for sufficient residual time for transmission at each state of the backoff counter. If the residual time is not sufficient for the transmission, the station goes to a defer state. They also proposed a RAW grouping scheme for a multi-rate network that groups the stations based on their data rate. They used the model to analyze the aggregate throughput of the network for the case where the stations are randomly grouped; then, they compared it with the aggregate throughput obtained with their proposed grouping scheme. They validated their model with ns-3 simulations.
Khorov et al. [
33] proposed a discrete-time Markov chain model to find the probability distribution of the time needed for an arbitrary station to successfully transmit its frame when the CSB is disabled. Based on that, they developed the probability distribution for the time needed by all stations to transmit their packets successfully in order to determine the minimum duration of a RAW slot to improve channel efficiency. In [
34], they adopted the approach from [
33] for the case when the CSB is enabled and and studied the influence of enabling the CSB option. Later, they extended their work to a more general scenario [
35], with various traffic patterns and RAW configurations, and analyzed network performance in terms of throughput, energy consumption, and packet loss ratio. For that, they proposed a Markov chain model based on the time slot status, i.e., whether it is occupied by a successful transmission, packet collision, or idle state, and defined absorbing conditions to model the completion time of a RAW slot. They validated their model based on a simulator designed by themselves, i.e., not widely adopted by the networking community. In [
36], Bankov et al. extended the model from [
35] for the scenario where the IEEE 802.11ah network has energy-harvesting sensor stations. They studied how to optimize the RAW parameters, such as the duration and number of groups, that provide the required probability of data delivery and minimize the amount of consumed channel resources in a network with a high number of energy-harvesting sensor devices.
Nawaz et al. [
37] presented a model where a RAW group is divided into two sub-groups and the duration of RAW slots in each sub-group is chosen according to the size of the group to improve network throughput. They showed that overall throughput is improved by assigning a relatively smaller RAW slot duration to a larger size group. They also used Bianchi’s model [
29] to compute the network throughput and validated the model with their own simulator. Lakshmi and Sikdar [
38] proposed a fair scheduling grouping scheme with different traffic patterns. Their proposal is to assign a weight to the groups according their amount of service, i.e., the amount of data the stations of the group generate per second. In this way, the groups that received higher weights should get more access to the channel than the groups with lower weights. They also used Bianchi’s model [
29] to compute the network throughput, and they validated their model using the ns-3 module of Le Tian et al. [
19]. Finally, Kai et al. [
39] used Bianchi’s approach to formulate throughput and energy efficiency expressions and designed a traffic distribution-based grouping scheme to balance the energy efficiency and fairness guarantees among groups in heterogeneous IEEE 802.11ah networks. They proposed the Optimal Traffic Grouping Algorithm (OTGA) based on an integer nonlinear programming problem and validated their solution with simulations carried out on a simulator designed by themselves.
Station grouping ideas to optimize the protocol performance are also being extensively explored in works related to IEEE 802.11ah. Chang et al. [
40] argued that the grouping mechanism performance is related to the different traffic demands of the devices, so the groups must be adapted to the demands of traffic. In this way, they proposed a grouping scheme based on load balancing and verified an improvement in the efficiency in the use of the channel and in throughput. Finally, Dong et al. [
41] and Yoon et al. [
42] developed grouping schemes according to the geographical location of the devices to avoid collisions related to the hidden terminal problem. Le Tian et al. [
43] designed the Traffic-Aware RAW Optimization Algorithm (TAROA), a real-time grouping algorithm for dynamic and heterogeneous traffic. In its original version, TAROA derives its optimal parameters based on saturated state simulations using an improved version of their IEEE 802.11ah ns-3 module [
23], and it only supports homogeneous stations under the same modulation and coding scheme (MCS) and average packet size. Their follow-up work [
44] allows non-saturated conditions and stations with different MCS and average packet sizes.
3. Overview of the IEEE 802.11ah
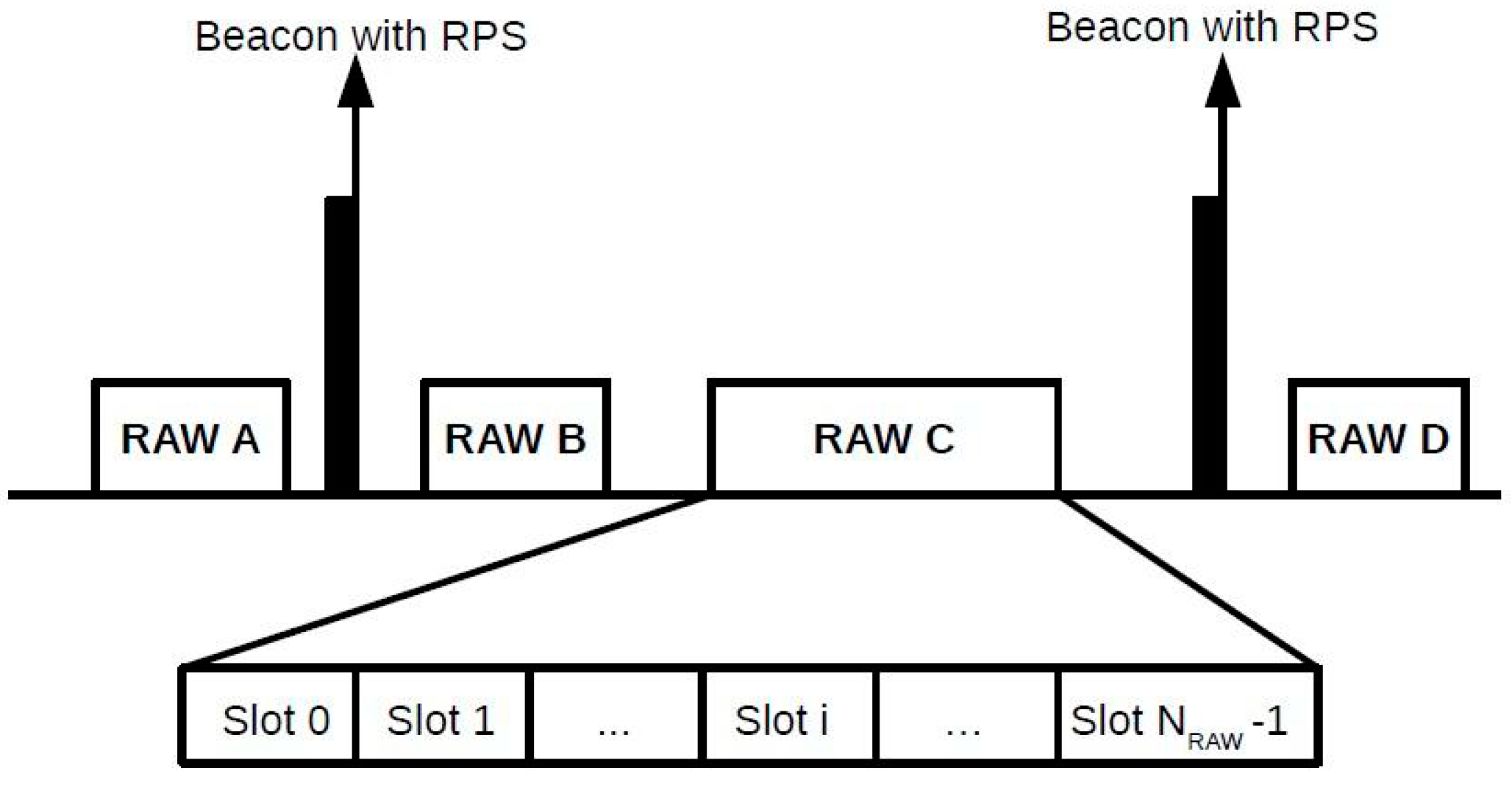
The release of the IEEE 802.11ah standard has introduced several new features that aim to facilitate the widespread deployment of IoT applications. As in traditional IEEE 802.11 power save mode, time is divided into beacon intervals, which can have one or more RAW groups, and each RAW group also has its time divided into one or more RAW slots, which are assigned to stations. Only the stations assigned to a given RAW slot can attempt to access the channel during that RAW slot. The beacon intervals can also have periods that are not occupied by RAW groups, in which all stations in the network can attempt channel access. Each beacon interval is preceded by the
RAW Parameter Set (RPS) beacon that carries RAW information. The RPS specifies characteristics such as which stations belong to the RAW group, the RAW duration, and the number of RAW slots. In addition, the standard defines the
Cross Slot Boundary (CSB), which indicates if a data packet transmission may exceed the RAW slot duration or not. If the CSB is disabled, a data packet transmission time cannot cross the RAW slot limit. Otherwise, a data packet transmission is permitted to cross the current RAW slot boundary even if it occupies the channel for the next RAW slot period. With the CSB disabled, the RAW slot is divided into two periods: the free access period, in which the stations can attempt to access the channel, and the holding period
, which is a period that is unavailable for stations to contend for channel access because there is not enough time for a packet transmission. The standard also defines a guard period
between RAW slots to prevent a transmission from one RAW slot to overlap the following RAW slot due to the propagation delay. The RAW mechanism is shown in
Figure 1, which shows that a beacon interval can have one or more RAW groups, and each RAW group can be divided into one or more RAW slots.
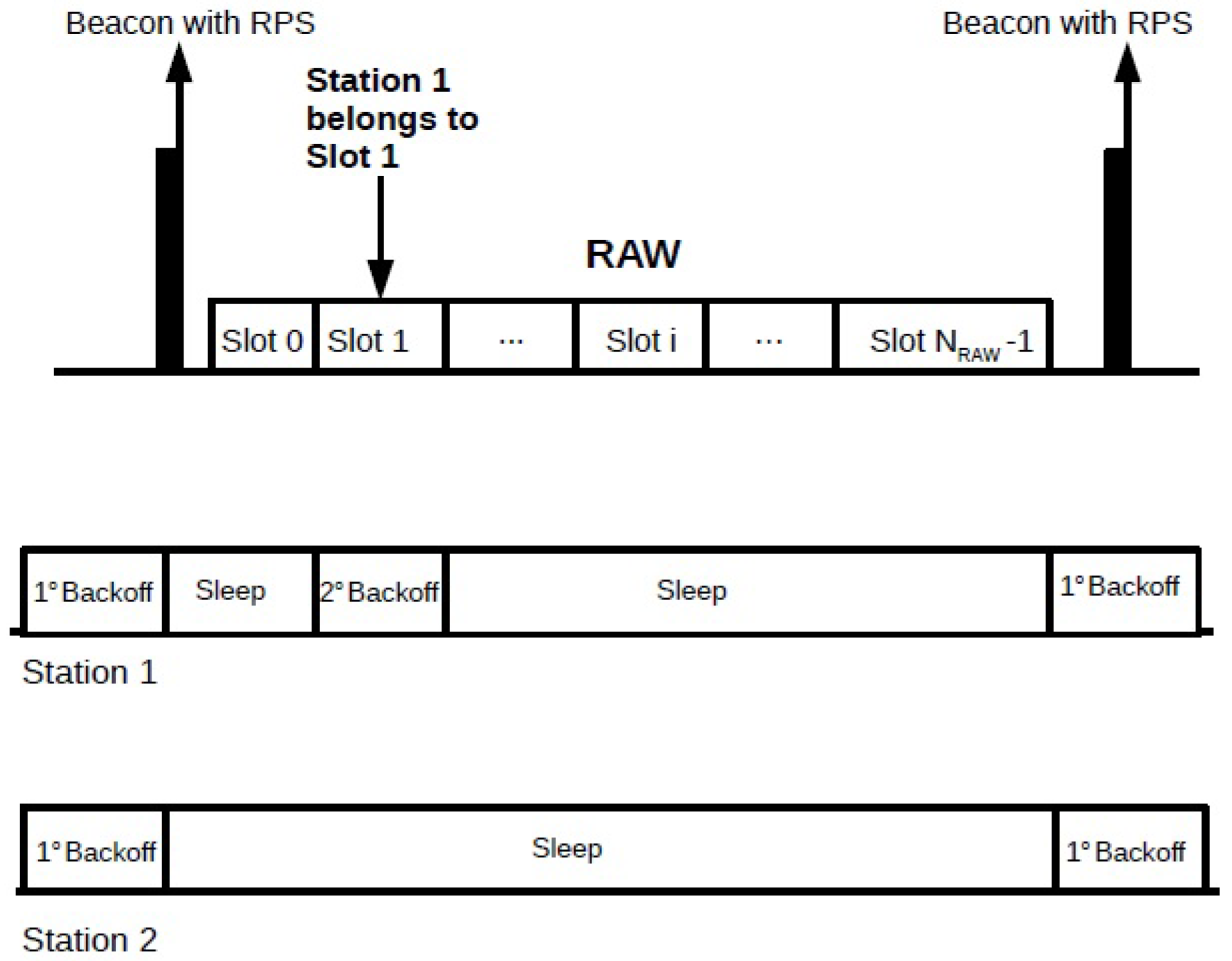
Unlike the other IEEE 802.11 standards, each station uses two backoff functions according to the Enhanced Distributed Channel Access (EDCA). The first backoff function is used in periods that are not occupied by RAW groups, and all stations in the network are allowed to freely access the channel. The second backoff function is activated inside the RAW slot the station was assigned to. The stations execute the first backoff function during the period of free access to the channel and suspend it in the beginning of the occurrence of a RAW group. When a RAW group period starts, the stations that are not assigned to this RAW group go into the sleep state and save the state at which their first backoff function has stopped, so they can resume it at the end of the time allocated to this RAW group. The stations assigned to the RAW group wake up and start the second backoff function within their assigned RAW slot. When the assigned RAW slot ends, the stations go back to sleep for the rest of the RAW group period. If the RAW slot ends during the execution of the second backoff process, the stations must discard the state in which they were stopped and start a new backoff function in the next assigned RAW slot. Inside its assigned RAW slot, the station selects a random backoff interval according to the binary exponential backoff (BEB) algorithm, which sets it according to
where
generates an integer value uniformly distributed in the interval
, where
, and
and
are the minimum and maximum contention window sizes, respectively. According to the BEB algorithm, when the channel is idle, the backoff counter is decremented and, if the channel is busy, this counter freezes until the channel is idle again for a time interval greater than or equal to DIFS. Initially, the contention window size is set to the minimum value and, for each unsuccessful transmission attempt, the minimum contention window increases exponentially according to
, where
and
m is the maximum number of re-transmission attempts, i.e.,
. Finally, when the backoff counter reaches the value zero, the station can transmit its data packet.
Figure 2 shows an example of when the two different backoff functions are activated. Station 1 belongs to the single RAW group shown in the figure, between beacons, where it is assigned to RAW slot 1. Suppose that there is a second station not assigned to this RAW group; then, when the occurrence of the RAW group begins, both stations stop the first backoff counter and go to sleep. During the occurrence of the RAW group period, station 1 wakes up to perform the second backoff within RAW slot 1 and sleeps during the remaining RAW period, while station 2 remains in sleep state during the whole RAW group period because it does not belong to this RAW group. Both stations return the execution of the first backoff function at the end of the time allocated to the RAW group.
4. Analytical Model
In this section, we present an analytical model to evaluate the average aggregate throughput of a single-hop IEEE 802.11ah network that is based on a discrete-time Markov chain model. The model describes the backoff operation of a station within its assigned RAW slot. It is assumed that there are n stations in the network operating in the basic access mode, i.e., without RTS/CTS control frames, which are evenly distributed among a certain number of RAW slots. Furthermore, we assume ideal channel conditions (i.e., no channel errors) and saturated traffic, i.e., all stations always have a data frame ready for transmission in their buffers. The beacon interval has a fixed length and contains only one RAW group with a fixed duration, i.e., a single RAW group occupies the whole beacon interval. Therefore, the model does not consider the periods when all stations can contend for channel access altogether (in-between RAW groups). The Cross Slot Boundary (CSB) is assumed to be disabled, and a station can transmit multiple data frames in its assigned RAW slot as long as their transmission times fit into the RAW slot. Finally, based on the analytical model, we derive an expression to compute the average aggregate throughput to evaluate network throughput performance.
4.1. Markov Model for Backoff Operation
We model the backoff operation of a station when it is active within its assigned RAW slot according to the two-dimensional discrete-time Markov model shown in
Figure 3, where each state represents the backoff counter value and each line represents a backoff stage, i.e., the number of transmission attempts. Similar to the basic IEEE 802.11 DCF, in the beginning of the Markov chain, the station chooses a random backoff value if the channel is sensed idle for a time period greater than or equal to a DIFS time interval, defined in the standard. While the channel is perceived idle, the backoff counter is decremented. Otherwise, the counter is frozen while the channel is sensed busy. The station transmits its data packet when the backoff counter reaches the value 0. If a packet collision occurs, the contention window size is doubled, and the station selects another random value according to Equation (
1), moving to the next backoff stage, as long as the number of re-transmission attempts does not exceed the maximum number
m. If the RAW slot ends in any state, the station returns to the beginning of the Markov chain.
Let
denote the stochastic process that represents the backoff counter value at time
t for a station assigned to a RAW slot and
denote the stochastic process that represents the backoff stage, i.e., the number of packet transmission attempts so far. Let
p denote the probability of data packet collision, which is assumed to be constant and independent of the number of transmission attempts. Let
g denote the “freezing” probability of the backoff counter when the channel is perceived to be busy, according to the DCF mechanism. We assume that it is constant and independent of the backoff stage. Since the RAW slot time can finish at any time during the backoff operation of a station, we represent the occurrence of this event with a transition probability
departing from every state
and returning to the “start” state. We assume that
is constant at each stage
i and the stages are independent of each other. We also assume that the event of RAW slot completion time is independent of the events of freezing the backoff counter value and the occurrence of packet collisions. Finally, let
denote the minimum contention window size and
,
. Hence, the one-step transition probabilities
are given by
The first equation indicates that the backoff counter advances if the channel is idle and the RAW slot time is not over; the second equation indicates that the backoff counter remains in the same state (frozen) if the channel is busy and the RAW slot time is not over; the third equation contains the probability of ending the RAW slot and return to a new backoff process in the following RAW slot; and the fourth equation represents a successful data frame transmission, which leads to the beginning of a new backoff operation for the next data frame in queue. The fifth equation indicates that a collision has occurred, and the station goes to the next backoff stage; the sixth equation describes the transition probability due to a failed data frame transmission in the last backoff stage: the data frame is discarded and a new backoff operation is initiated for the following data frame in the queue.
4.2. Markov Chain Solution
Let
denote the steady-state probability of state
in the Markov chain, i.e.,
Using the transition probabilities defined previously, we get
where
and
Since a station transmits a packet when it reaches any state
, for
, the steady-state packet transmission probability is given by
If
n denotes the number of stations competing for the channel in a RAW slot, then a packet collision occurs if one or more of the
remaining stations transmit a packet at the same time. Assuming that all stations transmit packets independently of each other, the packet collision probability
p will be given by
Similarly, the probability
g of a busy channel is the probability of having at least another node transmitting over the channel, i.e.,
The steady-state probabilities of the states of the Markov chain can then be computed by numerical calculation using the normalization condition
and Equation (
5). Finally, we need to compute the probability
of RAW slot time completion, upon which the station cancels its backoff operation and waits for the next RAW slot in the following beacon interval. Given the complexity in deriving a closed-form expression for the probability of RAW slot time completion
, we extend our previous work [
17] by proposing a new heuristic expression for the probability
, which aims to represent this probability more realistically and obtain a more accurate model. The development for the computation of the probability
is introduced next.
4.3. RAW Slot Time Completion Probability
The derivation of the probability of RAW slot time completion is not a trivial task because it depends on a number of events whose characterizations are not easily obtained. Because of that, we adopt a heuristic approach for its computation by considering some key aspects and assumptions. First, we notice that the higher the number of transmission attempts for a given data packet, the longer the time a station spends in backoff and, consequently, the higher the chances of RAW slot time completion during the transmission attempt of that specific data packet. Therefore, for any data packet a station attempts to transmit, we assume that the chances of RAW slot time completion increase in proportion to the number of stages traversed during backoff.
However, during the execution of a given RAW slot, and under traffic saturation, the station may transmit multiple data packets while contending for channel access with other stations assigned to the same RAW slot. Hence, if we assume that the IEEE 802.11ah operation is fair, each of the n contending stations should receive an equal “share” of channel access time within a given RAW slot, i.e., each station should get a fraction of the total RAW slot time for channel access. In this sense, a station is unable to transmit more data packets once its “share” of channel access time is over. As a result, while the station may have performed the backoff algorithm for a number of consecutive data packets, the RAW slot will finish during backoff operation in the transmission attempt of a specific data packet. In other words, such an event determines in which packet transmission attempt the completion of the RAW slot time actually occurs.
Finally, we note that the RAW slot to which the station was assigned occupies a certain amount of time within the beacon interval. Therefore, the ratio between the RAW slot time and the beacon time interval provides an estimate for the probability of finding the station within its RAW slot at any given time. Based on such observations and assumptions, we are interested in the probability of the event of RAW slot time completion during the execution of the
i-th backoff stage for a given packet, i.e., we are interested in the probability of the joint conditional event
{RAW slot ends, STA’s fraction of RAW ends, RAW ends in this backoff stage | stage
i}, where STA refers to the station performing backoff. From the Markov chain in
Figure 3, the probability
of RAW slot time completion during backoff stage
of attempting a given packet transmission will be given by
which can be rewritten as
Since the end of a RAW slot does not depend on the operation of any given station (its duration is defined by the access point), we have
where
,
,
, and
are the RAW slot time, the holding time (assuming the CSB is disabled), the guard interval between RAW slots, and the beacon interval, respectively. Note that the shorter the RAW slot time
is, the higher the chances of RAW slot time completion. Now, assuming that the end of a station’s fair share of channel access is not dependent on the specific backoff stage the station is currently performing, we have
Since it is assumed that each station occupies
of the RAW slot time
, at last, for any data packet a station attempts to transmit, the chances of RAW slot time completion are assumed to increase in proportion to the number of backoff stages traversed. Therefore,
Finally, from Equations (
10)–(
13), we obtain
4.4. Throughput Computation
In this section, we compute the average aggregate throughput within a beacon interval, i.e., the sum average throughput across all RAW slots contained in all RAW groups defined within the beacon interval. Different from our previous work [
17], the computation of the average aggregate throughput is extended and presented in more detail. First, we explain how the effective throughput for a given RAW slot is computed and, based on that, we show how the overall average aggregate throughput can be computed for a complete set of RAW groups and RAW slots. We assume that only the basic access mechanism is used (i.e., no RTS/CTS frames). Let us first consider the average throughput over a single RAW slot
i. Using Bianchi’s approach [
29], let
denote the number of stations within RAW slot
i and
denote the probability that a frame is transmitted over the channel during the RAW slot
i, i.e.,
, and let
denote the conditional probability of a successful DATA frame transmission within the RAW slot
i, given by
Hence, the probability of a successful DATA frame transmission is
, the probability that a slot is empty is
, and the probability of DATA collision is
. If
denotes the average length of a DATA frame payload, the throughput over a given RAW slot
i is given by
where
is the duration of a mini-slot (as defined by the standard),
is the time the channel is busy due to a successful DATA frame transmission, and
is the time interval the channel is busy due to collisions. The values of
and
are calculated according to
and
where
H is the length of the header of a DATA frame, which contains PHY and MAC layer headers,
is the propagation delay,
and
are the transmission rates for the header and payload fields, respectively,
and
refer to the duration of the ACK and ACK timeout, and
and
are specified in the IEEE 802.11ah standard.
Now, we are interested in obtaining the effective throughput within a beacon interval corresponding to the data received from stations allocated to RAW slot
i. In this case, we must take into account the time the stations spend waiting for the end of other RAW slots to which they were not assigned. Note that, from the point of view of the access point, it will receive an amount of data from stations allocated to different RAW slots over a period of time. Therefore, over the duration of a beacon interval, the AP will receive a certain amount of data from stations allocated to RAW slot
i. Hence, the effective throughput
, over a beacon interval, for stations assigned to RAW slot
i is
where
and
refer to the holding and guard periods, respectively. The average aggregate throughput
, in a given beacon interval, can be obtained by adding the effective throughput
of each RAW slot
i across all RAW groups
l in the beacon interval, i.e.,
where
is the number of RAW slots within each RAW group
l, and
r is the number of RAW groups within the beacon interval. In this work, we consider
, i.e., the scenario of a single RAW group in a beacon interval. As a final note, Equation (
20) assumes that there are no free access periods between RAW groups.
5. Analytical Models Used in Comparison
In this section, we briefly present the main features of two analytical models available in the literature that we use to compare with our model. From
Section 2, we can identify two main lines of work: those that follow a mean value analysis, as originally used by Zheng et al. [
20], and others that propose Markov chain models. In this second group, however, there are works that adopt Bianchi’s [
29] original model without considering any specific features of the IEEE 802.11ah standard. Therefore, we selected Sangeetha et al. model [
21] due to their effort to represent some of the key characteristics of IEEE 802.11ah. In addition, Zheng’s and Sangeetha’s works make different assumptions regarding protocol behavior, and they treat the event of RAW slot time completion differently, which is key for comparison with our model.
First, we present the model introduced by Zheng et al. [
20], who used mean value analysis (MVA) to study the efficiency of the RAW mechanism in single-hop networks. In their work, they denote the RAW mechanism of the IEEE 802.11ah as the Group-Synchronized Distributed Coordination Function (GS-DCF). We chose Zheng’s model to compare with our model because it is one of the first works on IEEE 802.11ah, and many papers have used GS-DCF to model the RAW mechanism. Another work we use for performance comparison is the one by Sangeetha et al. [
21]. Their work is based on Bianchi’s approach to model the operation of a station according to a discrete-time Markov chain, based on which they derive the average throughput and delay performance of IEEE 802.11ah single-hop networks under the RAW-based channel access mechanism. Among the reasons to choose Sangeetha’s model for performance comparison, we mention the fact that they adopt a modeling approach similar to ours, but it is different in terms of assumptions regarding protocol behavior, and the fact that it is a recent work on the analytical modeling of IEEE 802.11ah. It is also worth mentioning that both analytical models make similar assumptions as ours, such as saturated traffic and ideal channel conditions, and they consider that stations are equally divided among RAW slots.
5.1. Zheng et al. Analytical Model
Zheng et al. [
20] use a totally different approach from ours to model IEEE 802.11ah networks. Their model is based on mean value analysis to obtain the conditional packet collision probability
p. According to their model, given that a station has a data frame ready for transmission, the probability
to transmit it in an idle slot is given by
where
and
are the average number of backoff mini-slots and transmission attempts experienced by one packet, respectively. For each packet, the number of transmission attempts follows a truncated geometric distribution with success probability
. Thus,
and
can be obtained as follows:
and
where
is the number of packet transmission attempts before the packet is dropped.
It is important to note that this model does not consider the periods of time when the backoff counter is frozen due to channel activity. However, similar to our approach, a collision happens if more than one station transmits in the same slot. Thus, the conditional collision probability
p is given by
where
g is the number of stations in a RAW slot. Then, assuming that the number of backoff mini-slots a station has to traverse before transmitting follows a geometric distribution, and if
denotes the number of backoff mini-slots a station waits for its TXOP, they obtained
where
. Let
denote the duration of the backoff counters, in mini-slots, between consecutive TXOPs in a RAW slot.
is equal to the minimum backoff counter duration value among all
g STAs’ backoff counters in the RAW slot, and it also follows a geometric distribution with parameter
. Hence,
Based on Equations (
25) and (
26), they derived the distribution for the duration of multiple transactions in a RAW slot and the distribution for the number of transactions from all stations in a given RAW slot. Finally, the throughput expression in a given RAW slot was given by
where
L is the packet transmission time,
is the total duration of a RAW group,
M is the random variable that indicates the number of transactions within a RAW slot,
is the expected number of transactions in the RAW slot, and
is the probability of a successful transmission in a RAW group, following Bianchi’s approach. We refer the reader to [
20] for the complete throughput expression and further details. Their model was validated based on simulation results derived from a simulator designed by themselves. Their analysis compared their results with the standard IEEE 802.11 DCF, and they showed the benefits of using the grouping scheme in dense networks, as opposed to allowing all stations to have access to the channel altogether.
The main difference between Zheng’s model and ours is that, when using the mean value analysis approach, Zheng’s model computes the average number of transactions, i.e., packet transmissions within a RAW slot and the average duration of these transactions, to obtain their results. However, this approach does not include the event of freezing backoff when the channel is perceived busy. Furthermore, their model assumes that a station saves its backoff counter value when the RAW slot ends and resumes its backoff operation in the next assigned RAW slot. In reality, in the beginning of a RAW slot, the backoff function is renewed for all the STAs assigned to that particular RAW slot. In our model, a station discards its backoff counter at the end of a RAW slot and starts a new backoff process in the beginning of its next assigned slot.
5.2. Sangeetha et al. Analytical Model
Sangeetha et al. [
21] modeled the behavior of a station in its backoff process within a RAW slot. They proposed an analytical model similar to ours, based on a discrete-time Markov chain, and used Bianchi’s approach for throughput computation. Similar to Zheng’s model, Sangeetha et al. assume that, at the end of a RAW slot, the station stores the value of the backoff counter in which it has stopped, and it resumes its backoff operation from that saved value in the beginning of its next RAW slot (the one it was assigned to). Because of their assumption, the backoff counter is frozen with probability 1 when the station is outside its designed RAW slot. According to their analytical model, the probability that the backoff is frozen inside the RAW slot
i is
where
is the available access period for STAs within RAW slot
i,
is the total duration of the RAW group period,
is the transmission probability in the RAW slot
i, and
n is the number of stations within RAW slot
i. When the RAW slot ends, the station remains in the same backoff state with probability 1 and continues the backoff process in the next assigned RAW slot.
A defer state is also defined in the Markov chain to represent the idea that if the backoff counter reaches the value 1, it only decrements to zero if there is sufficient time for a successful packet transmission. Otherwise, the station goes to the
defer state with probability
where
is the duration of a successful transmission. They presented the Markov chain solution and provided a throughput computation based on Bianchi’s approach. They evaluated the average throughput and packet delay performances and validated their model with simulations in the ns-3 simulator, according to the PHY and MAC layer parameters of IEEE 802.11 and IEEE 802.11ah.
The main differences between our model and Sangeetha’s are the same as those we pointed out regarding Zheng’s model, i.e., the way they handle the event of RAW slot time completion. In both cases, they modify the backoff process that is originally defined in the standard and simplify it by assuming that the station saves the value of its backoff counter at the time the RAW slot ends, and it resumes its operation at the same backoff counter value at the beginning of its next assigned RAW slot. Differently from them, we model the actual backoff process as defined by the standard, where a station must discard the backoff counter value in which the RAW slot completion happens and initiates a new backoff process in the beginning of is next assigned RAW slot.
8. Future Works
While there are a number of works that have investigated the performance of IEEE 802.11ah networks under different scenarios regarding the size of the network, type of traffic, and configuration of key parameters, such as the number and size of RAW slots and RAW groups, most of the previous work has focused on static scenarios. In other words, the majority of the previous work assumes that stations are already associated/authenticated to a given access point and do not change location with time (i.e., there is no mobility). Consequently, most previous work does not handle the arrival/departure of a station to/from an IEEE 802.11ah network or the real-time allocation (or re-arrangement) of stations to new RAW slots or RAW groups as a result of their movement or channel state conditions. This is very important because some IoT applications target mobile devices (e.g., robots, UAVs, industrial machines, etc.), which require special attention, especially under dynamic channel conditions: the channel state experienced by a group of static stations is likely to be very different from the channel conditions perceived by mobile stations. Moreover, the mobility of some stations may affect the performance of other stations due to the well-known hidden/exposed terminal problem, which needs to be handled during the re-allocation of RAW slots and RAW groups. Given the importance of such a problem, our research group is currently working on solutions for dynamic scenarios, especially regarding new algorithms for re-allocation of stations to new RAW groups and/or RAW slots with the goal of achieving higher network performance.
Another main challenge in the deployment of IoT applications is the fact that most wireless devices are powered with conventional batteries, which typically require frequent replacements. As IoT applications are diverse, ranging from healthcare to agriculture and industrial environments, the connected devices can be located in places that are difficult to access, where maintenance and the frequent replacement of batteries make the operation of such devices inefficient and expensive. In addition, billions of batteries are expected to be discarded every year, which has a negative impact on the environment. A promising solution to address this issue is to integrate radio-frequency (RF) energy harvesting technologies into IoT systems, which is a more environmentally friendly solution that can extend the lifetime of IoT devices and even replace battery power completely, in some cases [
45,
46]. However, this is a challenging integration due to the characteristics of energy harvesting technologies and the different power requirements of IoT devices. Although there are different approaches in the literature for modifications in MAC-layer protocols to reduce energy consumption, there is still a gap to understand possible MAC improvements to enable RF energy harvesting in IoT systems and ensure the energy self-sustainability of the network [
47]. Moreover, to date, most works have tackled the introduction of RF energy harvesting only in traditional Wi-Fi networks [
48,
49,
50,
51], and only recently has there been some effort to introduce energy harvesting into IEEE 802.11ah networks [
36]. Therefore, there is still a need to address RF energy harvesting in IEEE 802.11ah networks and, because of that, our future work aims to integrate RF energy harvesting in the operation of IEEE 802.11ah networks. For that, we intend to exploit its RAW and
target wake-up time (TWT) mechanisms in the design of innovative grouping strategies that can deliver a more sustainable and energy-efficient operation of the network.