An Architecture for Reliable Transportation of Delicate Goods
Abstract
1. Introduction
2. Market Analysis
3. Technical and Domain Contextualization
3.1. The Main Scenario
3.2. Technical Options
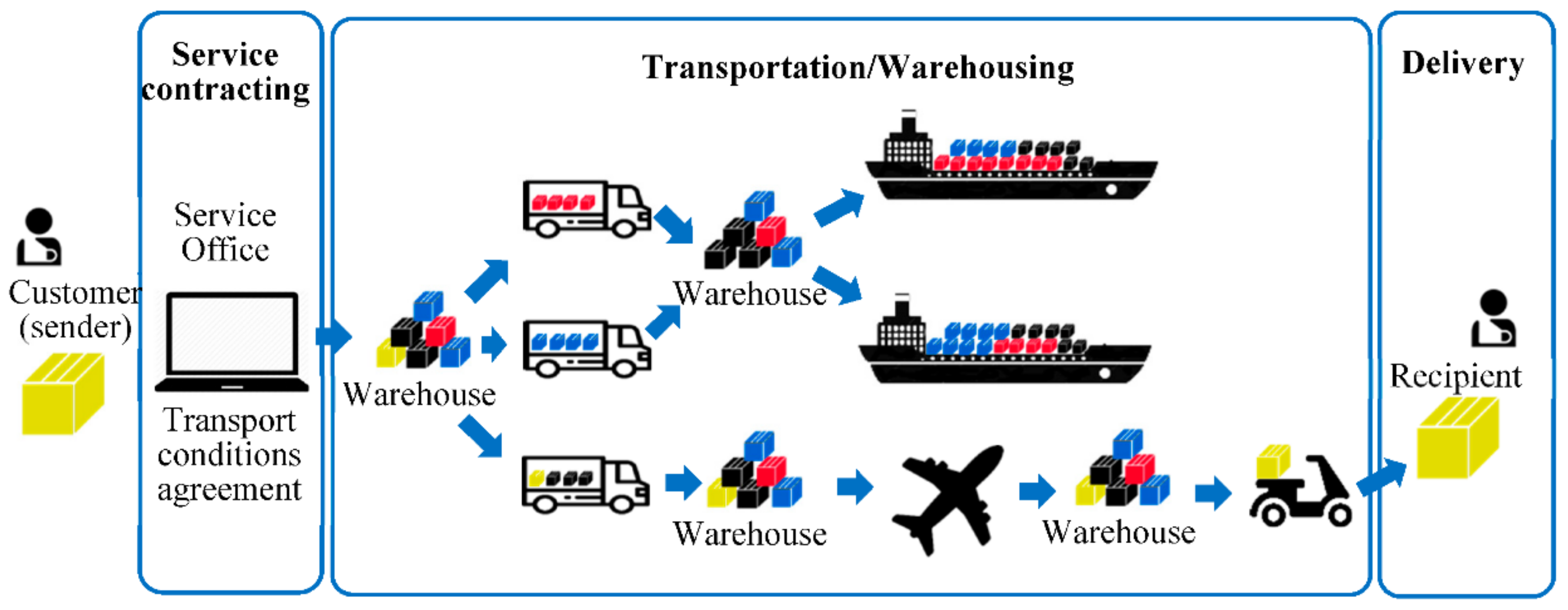
4. The Main Scenario
- The definition of the transport and shipping contract.
- Transporting the merchandise from operator to operator.
- Delivery of the merchandise to the recipient.
4.1. High Level Architecture
4.2. The Monitoring Device
Device Types and Topologies
- Type A—devices are continuously advertising or advertising periodically, with it being possible to define the power of the transmission signal.
- Type B—the advertise mode is activated by pressing a button and the device stays on that mode for a limited time.
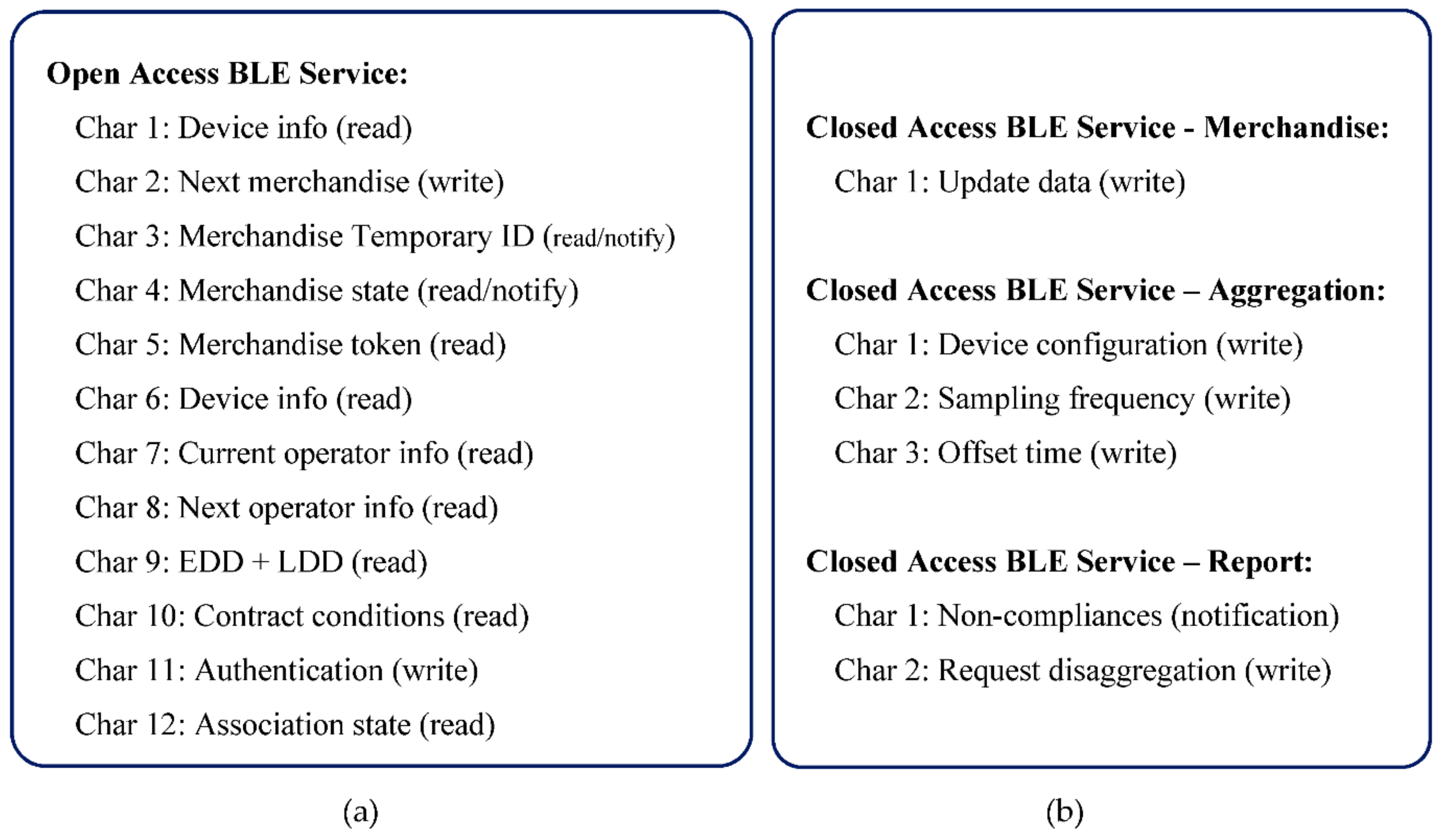
4.3. Bluetooth Low Energy—Services, Characteristics and Access Modes
- The peripheral device is placed in advertise mode that transmits the indication that the device is available, possibly with information about the available services (each service has its own identifier).
- The central device is placed in scan mode looking for advertise signals. It can be pre-configured to only search for peripherals that advertise certain services.
- If the peripheral device is found, the central can then request the connection.
- The connection then takes place, which may involve security procedures, with different levels of implementation—some of which are used in the proposed architecture.
- The central can read/write in the characteristics available with these types of access or enable the characteristics that can be used on the notification mode.
- The peripheral device can notify the central device via characteristics of this type (already enabled).
- The connection between devices can be closed by any of the devices.
5. Workflow
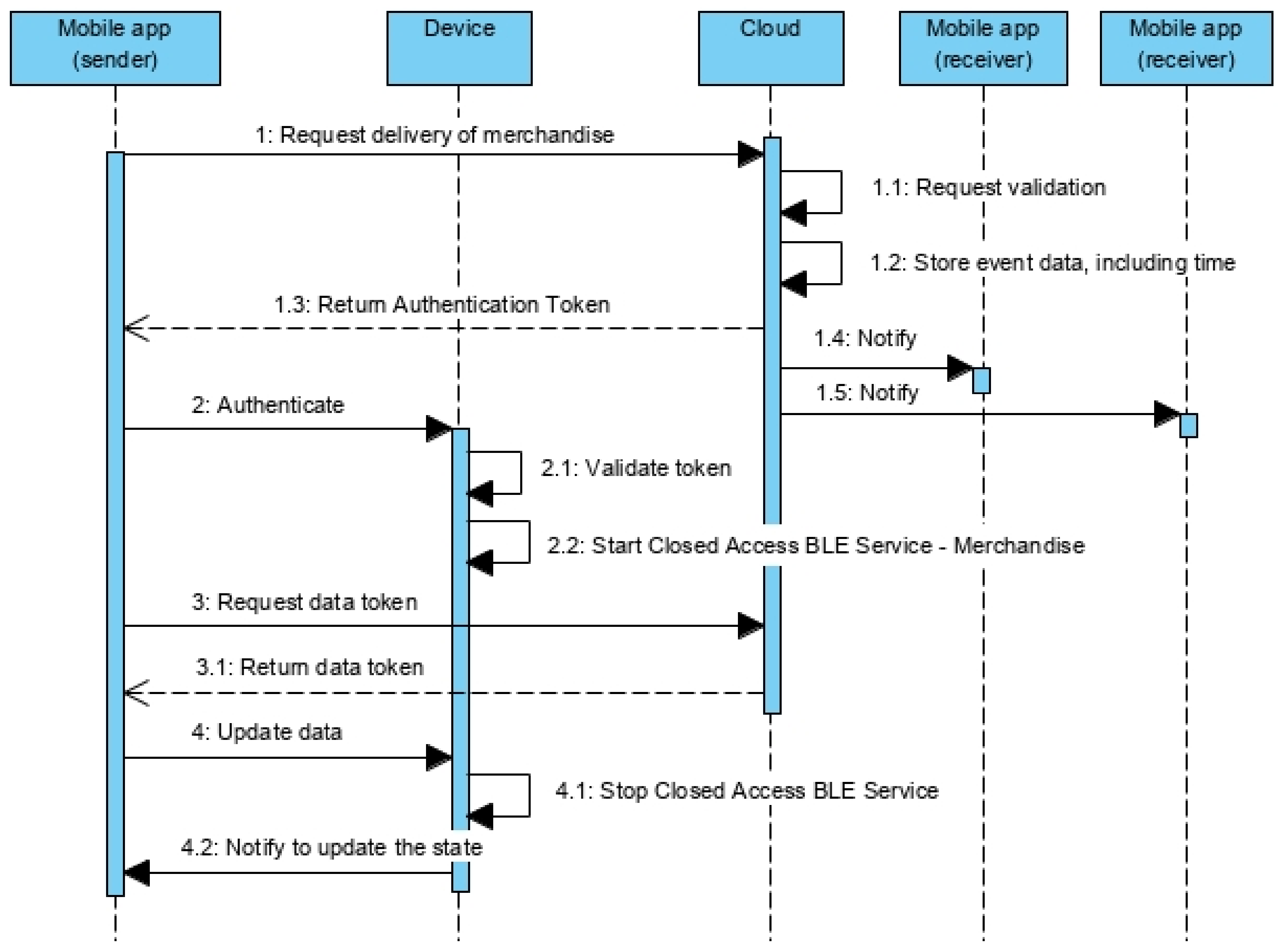
5.1. Service Initialization
- DEPOSITED—Indicates that the operator deposited the merchandise to be received by the next operator.
- RECEIVED—Indicates that the operator received the merchandise.
5.2. Merchandise Transmission
- Characteristic 1: Device info (read)—Supplies information about the device to which the mobile is connected. It is a representative characteristic, which in an applied context, may require to be broken down into several, depending on the information to be made available about the device.
- Characteristic 2: Next merchandise (write)—it implements an iterator to access merchandise information and token, one by one.
- Characteristic 3: Merchandise Temporary ID (read)—Supplies the merchandise temporary identifier.
- Characteristic 4: Merchandise state (read)—Supplies the state of the merchandise (DEPOSITED/RECEIVED).
- Characteristic 5: Merchandise token (read)—Allows to read the Merchandise Token pointed by the iterator, including the Data Token (non-compliance measures).
- Characteristic 6–10: These characteristics allow to read information about a merchandise, namely information about: the device attached to the merchandise, current operator, next operator (if exist), Earlier and Later Deliver Dates and contract conditions. On topologies (a) and (b), the device information is the same of the characteristic one.
- Characteristic 11: Authentication (write)—Allows to write the authentication token to activate the Closed Access BLE Services. The token is requested using the mobile app, for operations such as associate/dissociate merchandise to a container, or confirm the receipt of merchandise. Based on the requested operation, it is returned a token that, once authenticated, will turn on the related BLE service.
- Characteristic 12: Used to get the association state among central and terminal devices on type (c) star topologies (see Section 5.3).
5.2.1. Merchandise Deliver Protocol
5.2.2. Merchandise Receipt Protocol
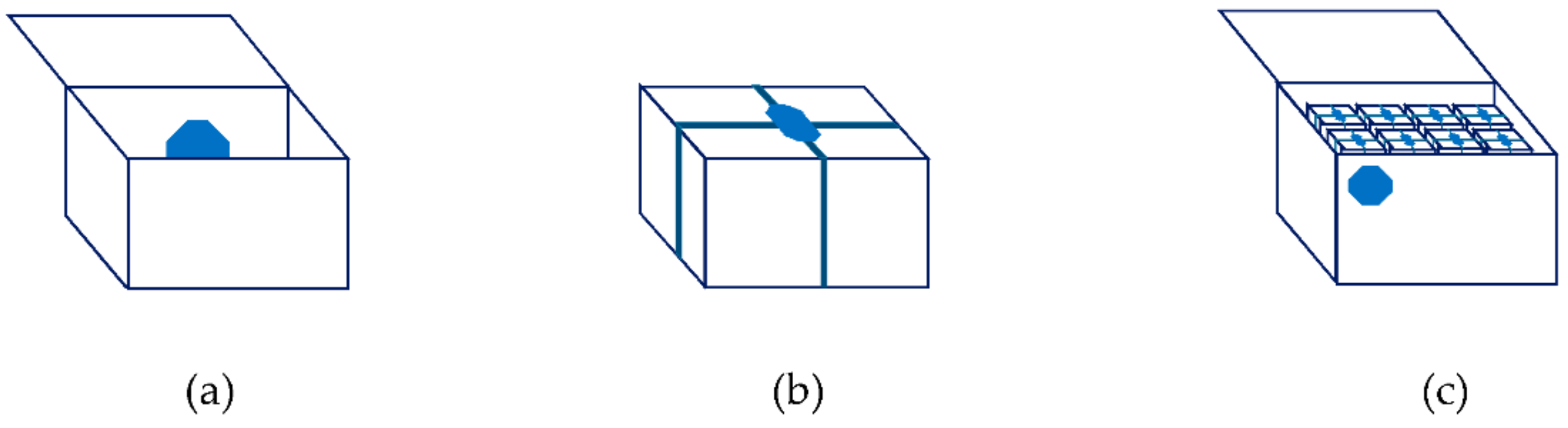
5.3. Merchandise Aggregation and Disaggregation
- Inside a container there might exist several monitoring devices, associated to merchandises with distinct transport requirements.
- Getting access to the merchandise inside the container might not be easy or even possible, without extra work or without jeopardizing the remaining goods.
- Type B devices probably will not be accessible to activate the advertise mode, which means that it may not be possible to collect the data related with the non-compliances, until the merchandise is removed from the container—too late to restore the optimal transport conditions and/or maybe to save the merchandise.
- It may not even be possible to access type A devices from outside the container, using a simple smartphone.
- If there are many devices inside the container, it might not be easy to access a specific one.
5.3.1. Type (c) Topology
5.3.2. Aggregation Protocol
5.3.3. Disaggregation Protocol
5.3.4. Report Protocol between Terminal Devices and Central
5.4. Deliver of Merchandise
6. Discussion, Conclusions and Future Work
- Relegating real-time communication to a non-critical requirement—can be critical for specific contexts and an additional added value, but for the vast majority of situations it is of no practical use.
- Supporting the solution with viable technologies, assuming in a pragmatic way that a communications infrastructure on a global scale, with acceptable usage costs (for the problem in question), is not yet a reality.
- Assuming a pragmatic stance regarding the usefulness of information (considering the goals of the solution) and the moments when it is actually necessary—when the merchandise and the responsibility for it passes from one operator to another.
Author Contributions
Funding
Institutional Review Board Statement
Informed Consent Statement
Acknowledgments
Conflicts of Interest
References
- ITF. Key Transport Statistics. 2019. Available online: https://www.itf-oecd.org/key-transport-statistics-2019-2018-data (accessed on 12 July 2020).
- Shashi Cerchione, R.; Singh, R.; Centobelli, P.; Shabani, A. Food cold chain management: From a structured literature review to a conceptual framework and research agenda. Int. J. Logist. Manag. 2018, 29, 792–821. [Google Scholar] [CrossRef]
- Aramyan, L.H.; Lansink, A.G.J.M.O.; Van Der Vorst, J.G.A.J.; Kooten, O.V. Performance measurement in agri-food supply chains: A case study. Supply Chain Manag. 2007, 12, 304–315. [Google Scholar] [CrossRef]
- Cerchione, R.; Esposito, E. A systematic review of supply chain knowledge management research: State of the art and research opportunities. Int. J. Prod. Econ. 2016, 182, 276–292. [Google Scholar] [CrossRef]
- Beef Report—Brazilian Livestock Profile 2020; ABIEC: Brasília, Brazil, 2020; p. 33.
- Rodrigue, J.; Notteboom, T. The Cold Chain and Its Logistics, The Geography of Transport Systems. Available online: https://transportgeography.org/contents/applications/cold-chain-logistics/ (accessed on 25 March 2021).
- UWT. The 4 Most Common Cold Chain Logistics Problems Truckers Face and Tis For Solving Them. Available online: https://unitedworldtransportation.com/4-common-cold-chain-logistics-problems-truckers-face-tips-solving/ (accessed on 25 March 2021).
- Magalhães, F.; Sonneveld, S.; Woods, D.; Basso, R. Six Strategies for Beating Brazil’s Supply Chain Complexities. Consumer Products, Supply Chain Management, Operations. 14 April 2017. Available online: https://www.bcg.com/publications/2017/consumer-products-six-strategies-beating-brazil-supply-chain-complexities (accessed on 25 March 2021).
- Ashok, A.; Brison, M.; LeTallec, Y. Improving cold chain systems: Challenges and solutions. Vaccine 2017, 35, 2217–2223. [Google Scholar] [CrossRef]
- Badiani, A.A.; Patel, J.A.; Ziolkowski, K.; Nielsen, F.B.H. Pfizer: The miracle vaccine for COVID-19? Public Health Pract. 2020, 1, 100061. [Google Scholar] [CrossRef]
- Chung, J.Y.; Thone, M.N.; Kwon, Y.J. COVID-19 vaccines: The status and perspectives in delivery points of view. Adv. Drug Deliv. Rev. 2021, 170, 1–25. [Google Scholar] [CrossRef]
- Boudjelal, M.; Almajed, F.; Ahmed, M.; Salman Naif, K.; Alharbi, M.C.J.M.; Gene Olinger, M.; Mariwan Baker, A.; Hill, V.S.; Alaskar, A. COVID-19 vaccines: Global challenges and prospects forum recommendations. Int. J. Infect. Dis. 2021, 105, 448–451. [Google Scholar] [CrossRef] [PubMed]
- Ambrosus. Available online: https://ambrosus.com (accessed on 5 September 2020).
- Christidis, K.; Devetsikiotis, M. Blockchains and smart contracts for the internet of things. IEEE Access 2016, 4, 2292–2303. [Google Scholar] [CrossRef]
- Huh, S.; Cho, S.; Kim, S. Managing IoT devices using blockchain platform, 2017. In Proceedings of the 19th International Conference on Advanced Communication Technology (ICACT), Bongpyeong, Korea, 17–20 February 2017; pp. 464–467. [Google Scholar] [CrossRef]
- Wood, G. Ethereum: A Secure Decentralised Generalised Transaction Ledger EIP-150 REVISION (759dccd-2017-08-07). 2017. Available online: https://ethereum.github.io/yellowpaper/paper.pdf (accessed on 3 September 2020).
- Buterin, V. Ethereum: A Next-Generation Smart Contract and Decentralized Application Platform. 2014. Available online: https://github.com/ethereum/wiki/wiki/White-Paper (accessed on 3 September 2020).
- Tikhomirov, S. Ethereum: State of Knowledge and Research Perspectives. 2017. Available online: http://orbilu.uni.lu/bitstream/10993/32468/1/ethereum-sok.pdf (accessed on 3 September 2020).
- Montes, J.M.; Ramirez, C.E.; Gutierrez, M.C.; Larios, V.M. Smart Contracts for supply chain applicable to Smart Cities daily operations. In Proceedings of the 2019 IEEE International Smart Cities Conference (ISC2), Casablanca, Morocco, 14–17 October 2019; pp. 565–570. [Google Scholar] [CrossRef]
- Wang, S.; Ouyang, L.; Yuan, Y.; Ni, X.; Han, X.; Wang, F. Blockchain-enabled smart contracts: Architecture, applications, and future trends. IEEE Trans. Syst. Man Cybern. Syst. 2019, 49, 2266–2277. [Google Scholar] [CrossRef]
- ModSense One. Available online: https://modum.io/solutions/modsense-one (accessed on 5 September 2020).
- Roambee. Available online: https://www.roambee.com/shipment-monitoring/ (accessed on 5 September 2020).
- Bluetooth SIG. Specification of the Bluetooth System-Covered Core Package Version: 4.0.; Bluetooth SIG: Washington, DC, USA, 2010. [Google Scholar]
- Bluetooth SIG. Bluetooth Core Specification: 5.2.; Bluetooth SIG: Washington, DC, USA, 2019. [Google Scholar]
- Ratasuk, R.; Mangalvedhe, N.; Ghosh, A.; Vejlgaard, B. Narrowband LTE-M System for M2M Communication. In Proceedings of the 2014 IEEE 80th Vehicular Technology Conference (VTC2014-Fall), Vancouver, BC, Canada, 14–17 September 2014; pp. 1–5. [Google Scholar] [CrossRef]
- Khalifeh, A.; Aldahdouh, K.A.; Darabkh, K.A.; Al-Sit, W. A Survey of 5G Emerging Wireless Technologies Featuring LoRaWAN, Sigfox, NB-IoT and LTE-M. In Proceedings of the 2019 International Conference on Wireless Communications Signal Processing and Networking (WiSPNET), Chennai, India, 21–23 March 2019; pp. 561–566. [Google Scholar] [CrossRef]
- Zayas, A.D.; Merino, P. The 3GPP NB-IoT system architecture for the Internet of Things. In Proceedings of the 2017 IEEE International Conference on Communications Workshops (ICC Workshops), Paris, France, 21–25 May 2017; pp. 277–282. [Google Scholar] [CrossRef]
- Wang, Y.E.; Lin, X.; Adhikary, A.; Grovlen, A.; Sui, Y.; Blankenship, Y.; Razaghi, H.S. A Primer on 3GPP narrowband internet of things. IEEE Commun. Mag. 2017, 55, 117–123. [Google Scholar] [CrossRef]
- Chen, J.; Hu, K.; Wang, Q.; Sun, Y.; Shi, Z.; He, S. Narrowband internet of things: Implementations and applications. IEEE Internet Things J. 2017, 4, 2309–2314. [Google Scholar] [CrossRef]
- Chen, M.; Miao, Y.; Hao, Y.; Hwang, K. Narrow band internet of things. IEEE Access 2017, 5, 20557–20577. [Google Scholar] [CrossRef]
- Cellular vs. Satellite: Understanding the Differences, Global Data Systems. Available online: https://www.getgds.com/resources/blog/connectivity/cellular-vs-satellite-understanding-the-differences (accessed on 5 September 2020).
- Rappaport, T.S.; Xing, Y.; Kanhere, O.; Ju, S.; Madanayake, A.; Mandal, S.; Trichopoulos, G.C. Wireless communications and applications above 100 GHz: Opportunities and challenges for 6G and beyond. IEEE Access 2019, 7, 78729–78757. [Google Scholar] [CrossRef]
- Letaief, K.B.; Chen, W.; Shi, Y.; Zhang, J.; Zhang, Y.A. The roadmap to 6G: AI empowered wireless networks. IEEE Commun. Mag. 2019, 57, 84–90. [Google Scholar] [CrossRef]
- Yang, P.; Xiao, Y.; Xiao, M.; Li, S. 6G wireless communications: Vision and potential techniques. IEEE Netw. 2019, 33, 70–75. [Google Scholar] [CrossRef]
- Liu, J.; Chen, C.; Ma, Y.; Xu, Y. Energy analysis of device discovery for bluetooth low energy. In Proceedings of the IEEE 77th Vehicular Technology International Conference, Dresden, Germany, 2–5 September 2013. [Google Scholar]
- Siva, J.; Yang, J.; Poellabauer, C. Connection-less BLE performance evaluation on smartphones. In Proceedings of the 16th International Conference on Mobile Systems and Pervasive Computing (MobiSPC 2019), Halifax, NS, Canada, 19–21 August 2019; pp. 51–58. [Google Scholar]
- Siekkinen, M.; Hiienkari, M.; Nurminen, J.K.; Nieminen, J. How low energy is bluetooth low energy? Comparative measurements with ZigBee/802.15.4. In Proceedings of the 2012 IEEE Wireless Communications and Networking Conference Workshops (WCNCW), Paris, France, 1 April 2012; pp. 232–237. [Google Scholar]
- Czurak, P.; Maj, C.; Szermer, M.; Zabierowski, W. Impact of Bluetooth low energy on energy consumption in Android OS. In Proceedings of the 2018 XIV-th International Conference on Perspective Technologies and Methods in MEMS Design (MEMSTECH), Lviv, Ukraine, 18–22 April 2018; pp. 255–258. [Google Scholar]
- Sikora, A.; Krzysztoń, M.; Marks, M. Application of Bluetooth low energy protocol for communication in mobile networks. In Proceedings of the 2018 International Conference on Military Communications and Information Systems (ICMCIS), Warsaw, Poland, 18–22 April 2018; pp. 1–6. [Google Scholar]
- nRF52832 Product Specification v1.4; Nordic Semiconductors: Trondheim, Norway, 2017.
- Zhang, Y.; Weng, J.; Dey, R.; Fu, X. Bluetooth Low Energy (BLE) security and privacy. In Encyclopedia of Wireless Networks; Shen, X., Lin, X., Zhang, K., Eds.; Springer: Cham, Switzerland, 2019. [Google Scholar] [CrossRef]
- Irannezhad, E. Is blockchain a solution for logistics and freight transportation problems? Transp. Res. Proc. 2020, 48, 290–306. [Google Scholar] [CrossRef]
- Raja Wasim, A.; Haya, H.; Raja, J.; Khaled, S.; Mohammed, O. Blockchain applications and architectures for port operations and logistics management. Res. Transp. Bus. Manag. 2021, 100620. [Google Scholar] [CrossRef]
- Rejeb, A.; Keogh, J.G.; Treiblmaier, H. Leveraging the internet of things and blockchain technology in supply chain management. Future Internet 2019, 11, 161. [Google Scholar] [CrossRef]
- Rivero-García, A.; Santos-González, I.; Caballero-Gil, C.; Molina-Gil, J.; Hernández-Goya, C.; Caballero-Gil, P. Blockchain-based ubiquitous transport and logistics monitoring system. Proceedings 2019, 31, 9. [Google Scholar] [CrossRef]
- Sergi, I.; Montanaro, T.; Benvenuto, F.L.; Patrono, L. A smart and secure logistics system based on IoT and cloud technologies. Sensors 2021, 21, 2231. [Google Scholar] [CrossRef]
- Bartle, J.R.; Lutte, R.K.; Leuenberger, D.Z. Sustainability and air freight transportation: Lessons from the global pandemic. Sustainability 2021, 13, 3738. [Google Scholar] [CrossRef]









Publisher’s Note: MDPI stays neutral with regard to jurisdictional claims in published maps and institutional affiliations. |
© 2021 by the authors. Licensee MDPI, Basel, Switzerland. This article is an open access article distributed under the terms and conditions of the Creative Commons Attribution (CC BY) license (https://creativecommons.org/licenses/by/4.0/).
Share and Cite
Matos, P.; Rufino, J.; Lopes, R. An Architecture for Reliable Transportation of Delicate Goods. Sensors 2021, 21, 2645. https://doi.org/10.3390/s21082645
Matos P, Rufino J, Lopes R. An Architecture for Reliable Transportation of Delicate Goods. Sensors. 2021; 21(8):2645. https://doi.org/10.3390/s21082645
Chicago/Turabian StyleMatos, Paulo, José Rufino, and Rui Lopes. 2021. "An Architecture for Reliable Transportation of Delicate Goods" Sensors 21, no. 8: 2645. https://doi.org/10.3390/s21082645
APA StyleMatos, P., Rufino, J., & Lopes, R. (2021). An Architecture for Reliable Transportation of Delicate Goods. Sensors, 21(8), 2645. https://doi.org/10.3390/s21082645






