Blockchain-Based Access Control Scheme for Secure Shared Personal Health Records over Decentralised Storage
Abstract
1. Introduction
1.1. Motivation
1.2. Contributions
- The proposed SC-ABSE scheme removes trusted PKGs by achieving high privacy protection of users’ SKs to ensure the consistent confidentiality of outsourced encrypted data in the IPFS storage. Moreover, it supports a secure multikeyword searchable fine-grained access control by providing one-to-many encryption to prevent unauthorised users from disclosing medical data in decentralised IPFS storage.
- The lightweight key generation algorithm is proposed in the SC-ABSE scheme in comparison with other existing schemes due to a reduced number of pairing operations in which it is a more constant secret key (SK). However, the smart contract is used to auto-enforce the synchronisation of nodes. Any modification in user key distributions can be detected automatically.
- The lightweight outsourcing mechanism is proposed in the SC-ABSE scheme by enabling the blockchain node’s user–patient to encrypt their medical data using the advanced encryption standard (AES) and then only encrypt the symmetric key file and the keyword using attribute-based encryption. This approach reduces the computational complexity of the encryption algorithm by turning into constant ciphertext.
- The lightweight retrieving mechanism is proposed in the SC-ABSE scheme by designing a more secure and efficient token generation algorithm in comparison to other existing schemes. This is due to shifting almost all of the computational complexity processes of the pairing operations to the search part of the IPFS storage entity. Generally, medical data decryption does not depend on the number of attributes in the access control policies.
- The proposed scheme is proven to be secure against CKAs and keyword secrecy under the hardness assumptions of DBDH and DL problems, respectively, in the standard model. Moreover, the formal security verification method using the Automated Validation of Internet Security Protocols and Applications (AVISPA) tool verifies that the reinforced security validation of the proposed scheme withstands replay and MIM attacks.
- A series of comprehensive experimental investigations are performed in terms of computational costs, storage costs, communication costs, throughput, and latency transactions, demonstrating that the proposed scheme achieves a higher level of security with less computational complexity costs than other existing state-of-the-art schemes.
1.3. Organisation
2. Related Work
2.1. Blockchain-Based Searchable Encryption
2.2. Blockchain-Based Ciphertext Policy Attribute-Based Encryption
3. Preliminaries
3.1. Bilinear Groups and Hardness Assumption Problems
- Bilinearity: For all ∈ . and ∈ , we have .
- Nondegeneracy: ∈ . exists such that .
- Computability: For any ∈ , an efficient polynomial-time algorithm must exist to compute the pairing .
3.2. Access Control
- If the set of attributes is successfully satisfied with the tree access structure policy , then .
- If is a nonleaf node recursively computed on for the entire children of node , then can return 1 if and only if as a minimum children return 1.
- If is a leaf node, then can return 1 if and only if .
3.3. Functional Encryption of the SC-ABSE Scheme
- . This algorithm takes a security parameter of and a set of universal attributes as input. Then, it generates a public key PK and a master key MK.
- . This algorithm takes a defined attribute set and MK as input. This algorithm outputs the for users in the healthcare user node (HUN).
- . This algorithm takes the public key ) of users in the HUN, medical data of the patients (MD), the keyword (kw) and a specified access structure as input. This algorithm outputs the encrypted medical data (), the symmetric encryption key for medical data (SKE) and the encrypted indexed data (I). Then, it returns the tuple of to IPFS storage.
- . This algorithm takes the final secret decrypting keys of users in the HUN , a set of attributed (S) and given interesting keywords as input. Afterwards, the algorithm outputs corresponding token .
- . This algorithm takes the given index with token and access structure policy as input. Then, it matches the indexed keywords for the corresponding encrypted medical data with received interested token whatever S (resp., ) has satisfied with (resp., ). Then, it sends the encrypted ciphertext of the relevant tuple file results to the requester.
- . This algorithm is takes the relevant search results of encrypted medical data (MD*) and a symmetric encryption key for medical data () as input. Then, the requester recovers the message .
4. Proposed SC-ABSE Scheme
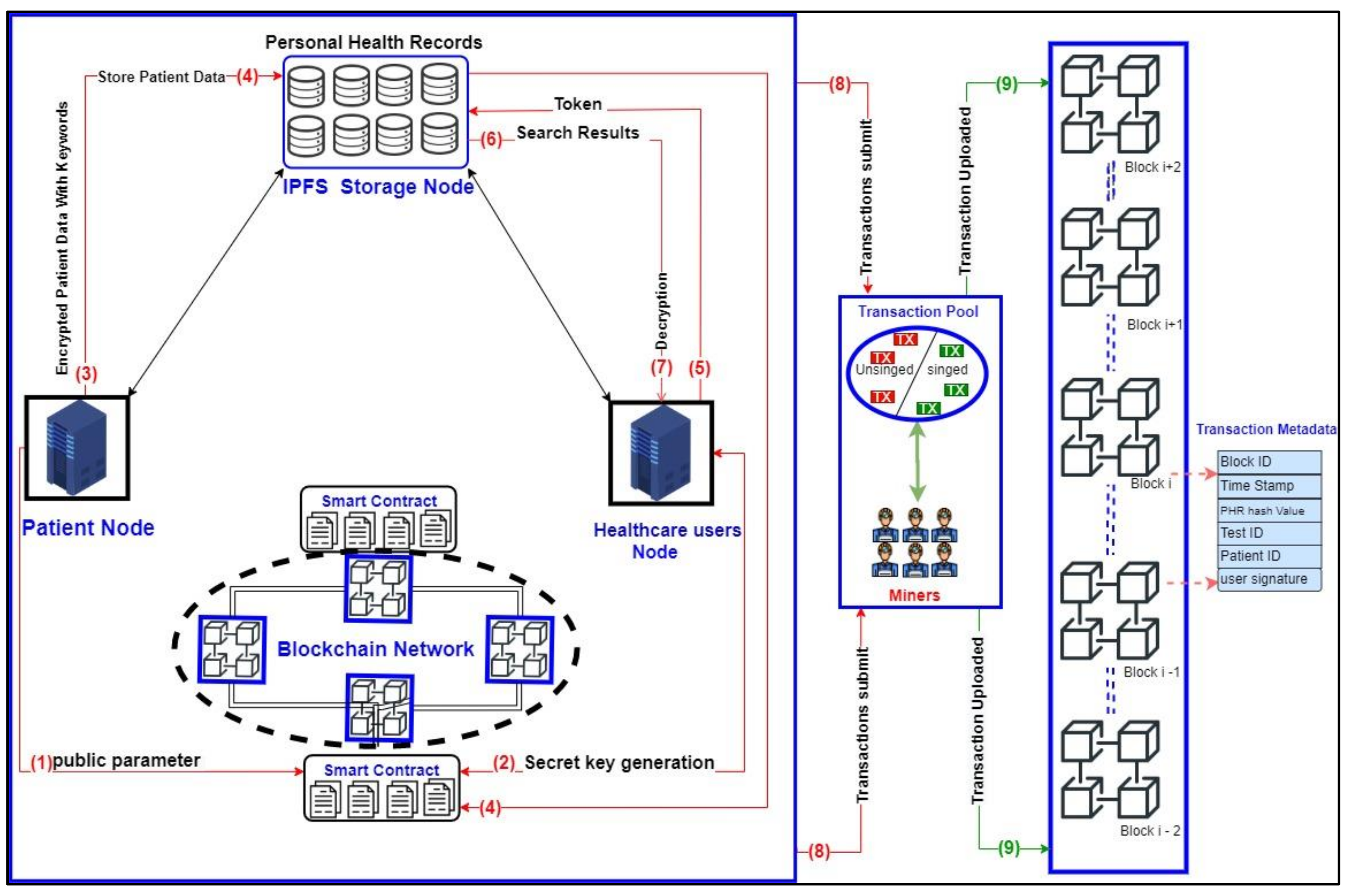
4.1. System Model
- (1)
- The patient node (PN) initialises the system by executing the setup algorithm with the aid of the smart contract to generate public parameters, such as PK and MK whilst publishing PK and keeping MK secret.
- (2)
- The PN generates the final SK associated with the attribute set for each user participating in the HUN by using a smart contract to execute the SK generation algorithm.
- (3)
- The patient in the node encrypts his medical data using AES and then encrypts the symmetric key using ABE, generates the keyword for that encrypted data, encrypts it with the ABE algorithm and sends the tuple of the file, including encrypted medical data, the symmetric encryption key for medical data and the encrypted indexed keyword data to be stored in the outsourced IPFS.
- (4)
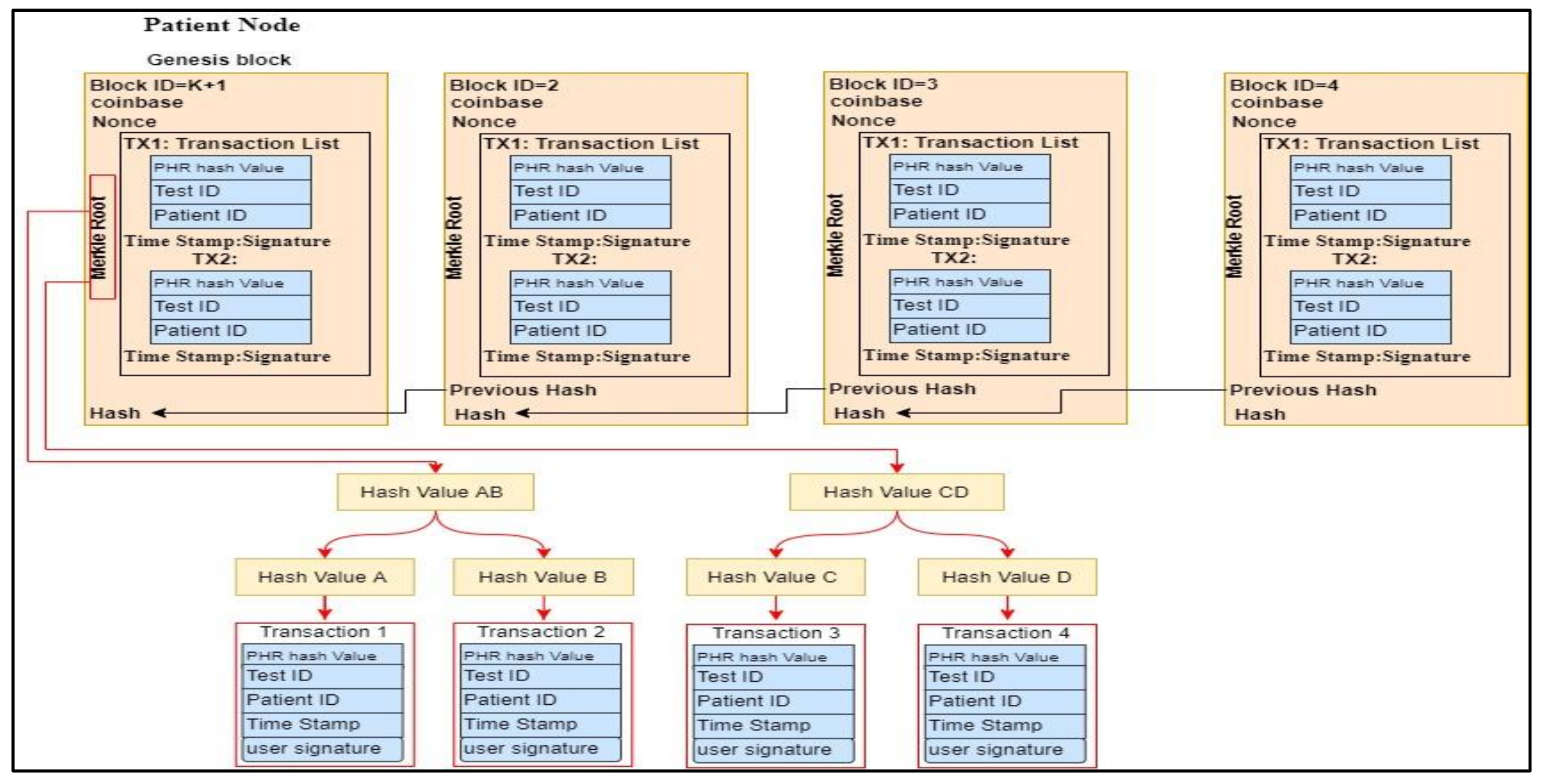
- Upon receiving the tuple file from the patient, the IPFS stores the file into distributed node storage and returns the hash value for that file in the form of a transaction and adds it into the transaction pool for confirmation by the miners to append the transaction to the blockchain where each node will have that copy of the transaction. Meanwhile, hash values are stored in the form of a distributed hash table (DHT) smart contract.
- (5)
- The users in the healthcare user’s node search the patient ID via a transaction uploaded to the main blockchain network and generate a token by encrypting keywords of interest using the final SK received from the PN to obtain patient data and then send the attributes and token to the IPFS node.
- (6)
- Upon receiving the token and attributes from the healthcare users, the IPFS searches the keywords if the attributes and token have been satisfied with an access policy and index keywords, respectively. Then, the IPFS sends the tuple file to the users.
- (7)
- After receiving the tuple, the user in the HUN must derive the corresponding symmetric key to decrypt patient data.
- (8)
- Unconfirmed transactions are uploaded for validation by the miners.
- (9)
- Each transaction is signed and appended to the main blockchain network.
4.2. Security Requirements and Threats
- CKA resistance: The proposed scheme can prove its security resistance by formalising the CKA’s provable security indistinguishability. Assuming that the adversary is an IPFS storage, it can access any structure policy throughout the decryption process but cannot obtain information about the actual medical data stored there.
- Keyword secrecy resistance: It ensures that malicious users in the HUN cannot compromise anything from the patient’s medical data attached to the keyword or token search mechanism.
- Tamper-proof resistance: The proposed scheme stores medical information, such as diagnostic results or patient history in the IPFS. The adversary intends perhaps to either alter some of the data or replace the existing with another data.User collusion attack resistance: SKs for users of the HUN are generated by the PN. Adversary users can generate a token by combining collusively with each other using their own SKs, attempting to retrieve patient data stored in the IPFS.
- Replay and man-in-the-middle (MIM) attack resistance: Transactions are issued by the PN when the patient users upload data to the IPFS node. An adversary may copy an authorised user transaction from the blockchain or retrieve messages sent by an authorised user. Then, replay or MIM attacks occur when an adversary can change the communication messages on the PN to obtain the patient data stored in IPFS.
4.3. Smart Contracts
- The PN creates the main contract to execute the SC-ABSE and generate public parameters (PK, MK and SK) for users in the HUN.
- The main contract requires the users in the PN to perform encrypted index keywords and store patient medical data into the IPFS.
- For users in the HUN side, when they wish to retrieve outsourced data in IPFS, the main contract can perform an aspect of the token generated, searched, and decrypted.
4.4. Security Model of SC-ABSE
4.4.1. Chosen Keyword Attacks
- Setup: The C executes the algorithm in the system initialisation phase of the proposed scheme to generate public and master keys. Then, the C sends the public keys to the A and keeps the master keys secret.
- Query Phase 1: The C establishes the list of the keyword list , whereas all the lists are initially empty. In addition, the A receives a response as a polynomial number of queries from the C as follows:
- SK generation query : The C executes the algorithm to obtain for users in the HUN, where is a set of attributes if then, the C outputs ⊥.
- GenerationToken Query : The C executes the algorithm to generate (Token) and send it to the A. Finally, if is satisfied with the access structure policy , then the C adds the keyword to list .
- Challenge: The A chooses two equivalent keywords in which that to the list of the keywords . Afterwards, the C chooses and returns over execute the algorithm to produce a keyword index and send it to A. Finally, the C sets =and sends it to A.
- Query phase 2: It is a comparable to query as phase 1. However, the A may continue query towards GenerationToken Query keyword except if . Otherwise, the A is incapable of querying.
- Guess: The A guesses , where and it has to be returned by the A. The A wins the experiment game only if , where the output of the game is defined to be 1. Then, we can write . If the output of the game is 0, then the adversary loses the game.
4.4.2. Keyword Secrecy
- Setup: The C runs the algorithm in the system initialisation phase of the proposed scheme to generate the public and master keys. Then, the C sends the public keys to the A and keeps the master keys secret.
- Query Phase 1: The A issues the below algorithms in polynomial times.
- SK generation query: The C runs the algorithm to obtain for users in the HUN, where is a set of attributes if . Then, the C outputs ⊥. Otherwise, the C inserts keywords into the list of established medical data queries.
- GenerationTokenQuery: The algorithm is run by the C to generate T by giving the SK and set of kw. The C sends the token to the A only if the . attribute set satisfies the access structure policy. .
- Challenge: The A selects the and passes it to the C, whereas the C must choose the keyword set from the medical data space and run the algorithm to send the index to the A.
- Guess: The A guesses the distinguishable keywords by outputting the keyword set . The A can win a security game by defining the following experiment if and only if .
4.5. Concrete Construction
4.5.1. System Initialisation Phase
4.5.2. Secret Key Generation Phase
4.5.3. Upload Health Data Phase
- Step 1: The patient users define a keyword as for each health data fileand selects random elements to generate index , where represents the keyword in , where this keyword is embedded in .
- Step 2: The patient users randomly select AES symmetric key from the key space and encrypt each file via Equation (7).
- Step 3: The patient users protect the keyword in the file and the symmetric key encryption of file under the access policy structure . Consequently, the users select the polynomial of for every individual node in the access policy structure by starting from the root node in a top-down manner. For every individual node , the degree of the polynomial is set as , where is the threshold value of the individual node x. To define the points of the polynomials and fully, the root node and node need to start these algorithms as and , respectively, and then randomly select the elements and . The set of leaf nodes in is as , and the index along with and are encrypted by giving the tree access structure and computing it with whereby . Then, the patient users randomly choose the element of by computing the following exponents as . Finally, can be performed by Equation (8).
- Step 4: The patient users upload the file tuple, including encrypted health data , encrypted symmetric key encryption for medical data () and the encrypted indexed data whereby to be stored in decentralised storage. IPFS receives the users’ tuple file and places the file location and then returns the hash value of that file to be stored in the DHT of the PN. Then, the PN submits an unconfirmed transaction to the miner’s pool for validation purposes and broadcasts it on the blockchain’s main network.
4.5.4. Access Health Data Phase
- Step 1: The leaf node is , and only if . Then, it computes with Equation (9). Otherwise,
- Step 2: The nonleaf node is, and the arbitrary set of children is . If the set of children in node does not exist, then . Otherwise, it calls the recursive algorithm to compute the following: , where .
- Step 3: IPFS verifies if Equation (10) holds, and then IPFS sends relevant results, including encrypted medical data containing the keyword and corresponding symmetric encryption key , to users. Otherwise, it returns ⊥, where .
4.5.5. Correctness
5. Security Analysis
5.1. Semantic Security Proof
- 1.
- Setup: The A selects an access structure policy and submits it to . Then, the selects a consistent element and presumes by setting the parameter as follows:
- 2.
- Query Phase 1: The A establishes the list of , and the keeps a list of the for each data user, whereas all the lists are initially empty. In addition, the receives a response as a polynomial number of queries from A as follows:
- SK generation query: The A runs the algorithm to generate for the users in the HUN. Then, the checks whether the set of an attribute in satisfies policy or not; if not, then for any attribute it is set as in Equation (22), and then the A returns , where to set the attribute (s) towards the .
- GenerationToken Query : It is comparable to a query of . The has to generate , where ∈ attributes. The needs to select a random element of by creating the search token via Equation (23) and checks whether the attribute satisfies or not; if yes, then adds the keywords to list by sending to the A.
- 3.
- Challenge: The A returns two equivalent keywords to the in which to the list of the keywords . In addition, the selects a random element of to generate encrypted index . Then, the gives the encrypted index , keyword health data file , and public key to the A. Then, the must select the random value of by assuming that if and only if and the element of encrypted index in the encryption algorithm presented in Section 4.5.3 are selected randomly and correctly.
- 4.
- Query phase 2. The A continues his query to the oracles, and the responds to a query that is identical to the procedure in phase 1.
- 5.
- Guess: The A guesses , where . The simulator checks whether or not. If yes, then the output is equal to 1; otherwise, the output is 0.
- Setup: The chooses universal attribute set and random elements . Then, the generates the public parameters of the system , , and by executing the algorithm. Then, the gives the to A and keeps the MKs secret.
- Query phase 1: The A makes a query to the oracle SK generation Query . Then, the executes the algorithm to generate for the users in the HUN. Finally, the gives to the A.
- Challenge: The A declares that Phase 1 is over. Then, the runs the algorithm to generate and selects a random element of to generate index . Then, sets the keyword by whereby . Then, returns the , and the to the A.
- Guess: The A guesses the distinguishable keywords .
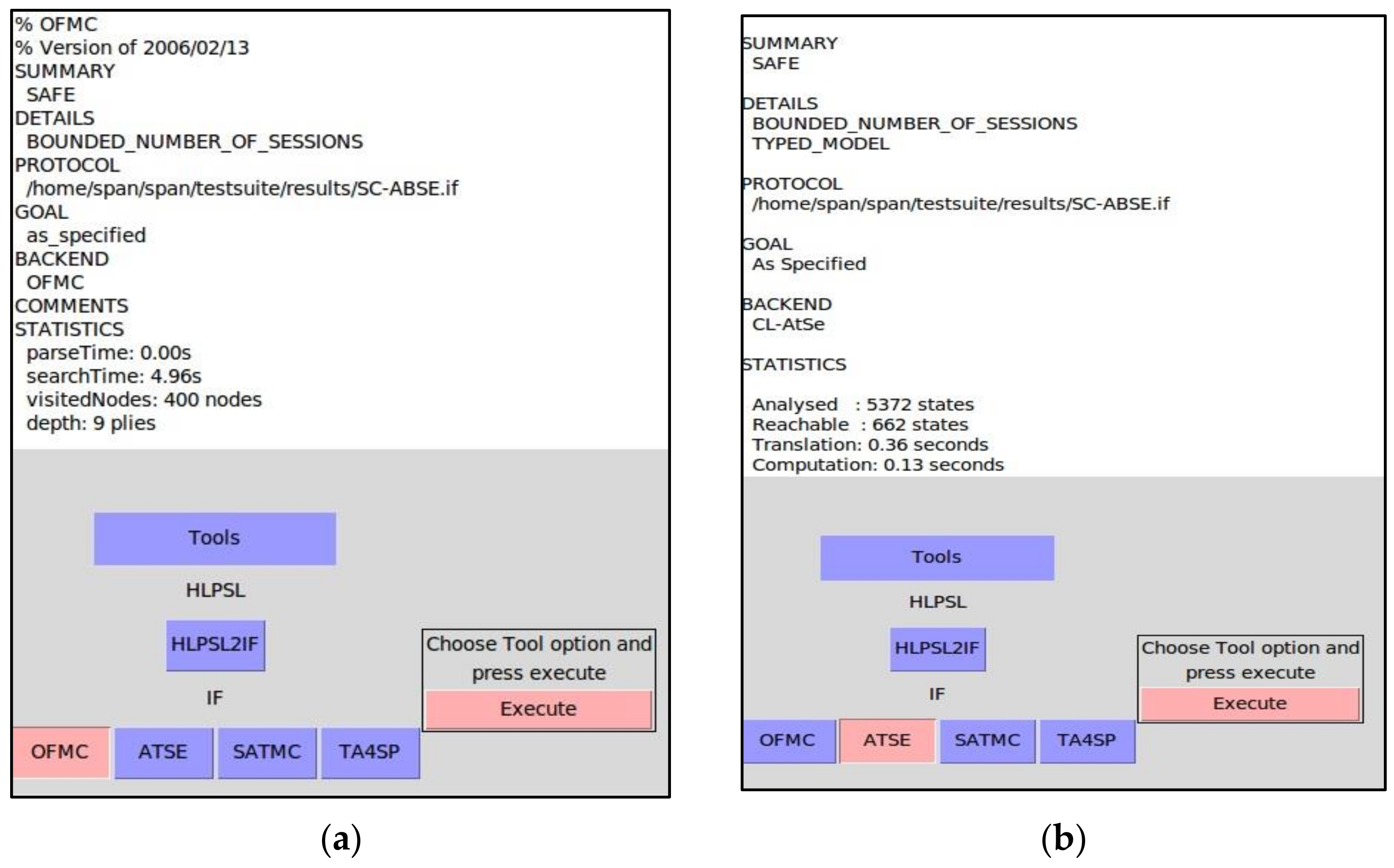
5.2. Security Validation of the Proposed SC-ABSE Scheme in AVISPA
- “secrecy_of sec_1”: The user in the HUN communicates with the PN to obtain the SK and sends it via a secure channel.
- “secrecy_of sec_2”: The PN node communicates with the IPFS node and sends a tuple of encrypted medical data in a secure channel.
- “secrecy_of sec_3”: The users in the HUN communicates with IPFS and sends a token to IPFS via a secure channel to retrieve the medical data.
- “authentication_on patient_ipfsnode_tta,tsv,tidi”: The users in the PN authenticate with IPFS node to upload the file.
- “authentication_on healthcareusersnode_ipfsnode_tta,tsv,tidi”: The users in the HUN authenticate with the IPFS node to retrieve the medical data.
- “authentication_on patient_healthcareusersnode_tsn”: The PN authenticates the users in the HUN with an appropriate attribute to generate their SK.
- “authentication_on patient_ipfsnode_ti, r1”: A request to upload the tuple file is made.
6. Performance Analysis
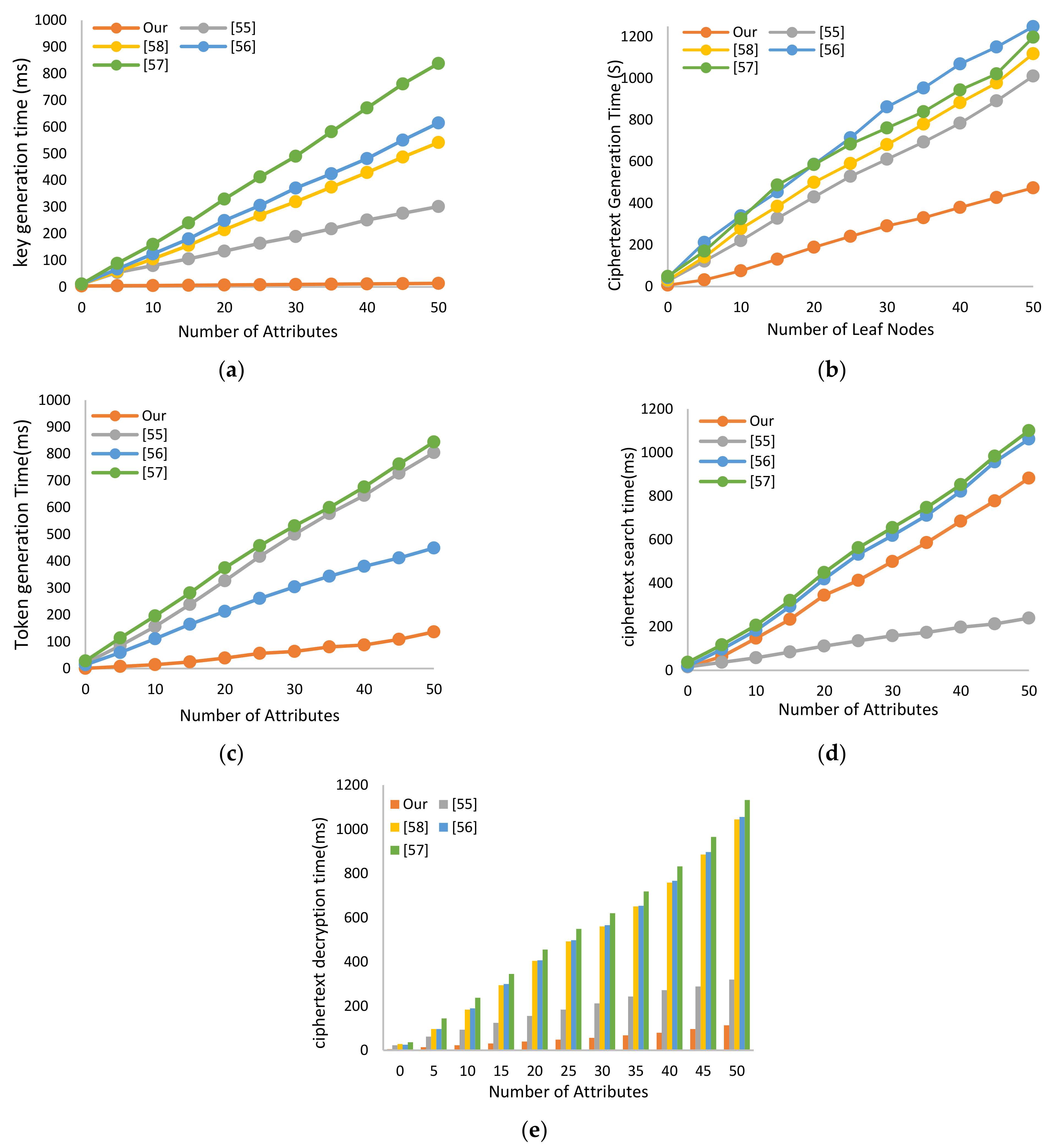
6.1. Computational Complexity Analysis
6.1.1. Computation Overhead
6.1.2. Storage Cost and Communication Overhead
6.2. Blockchain Network Simulation
6.2.1. Simulation Setup
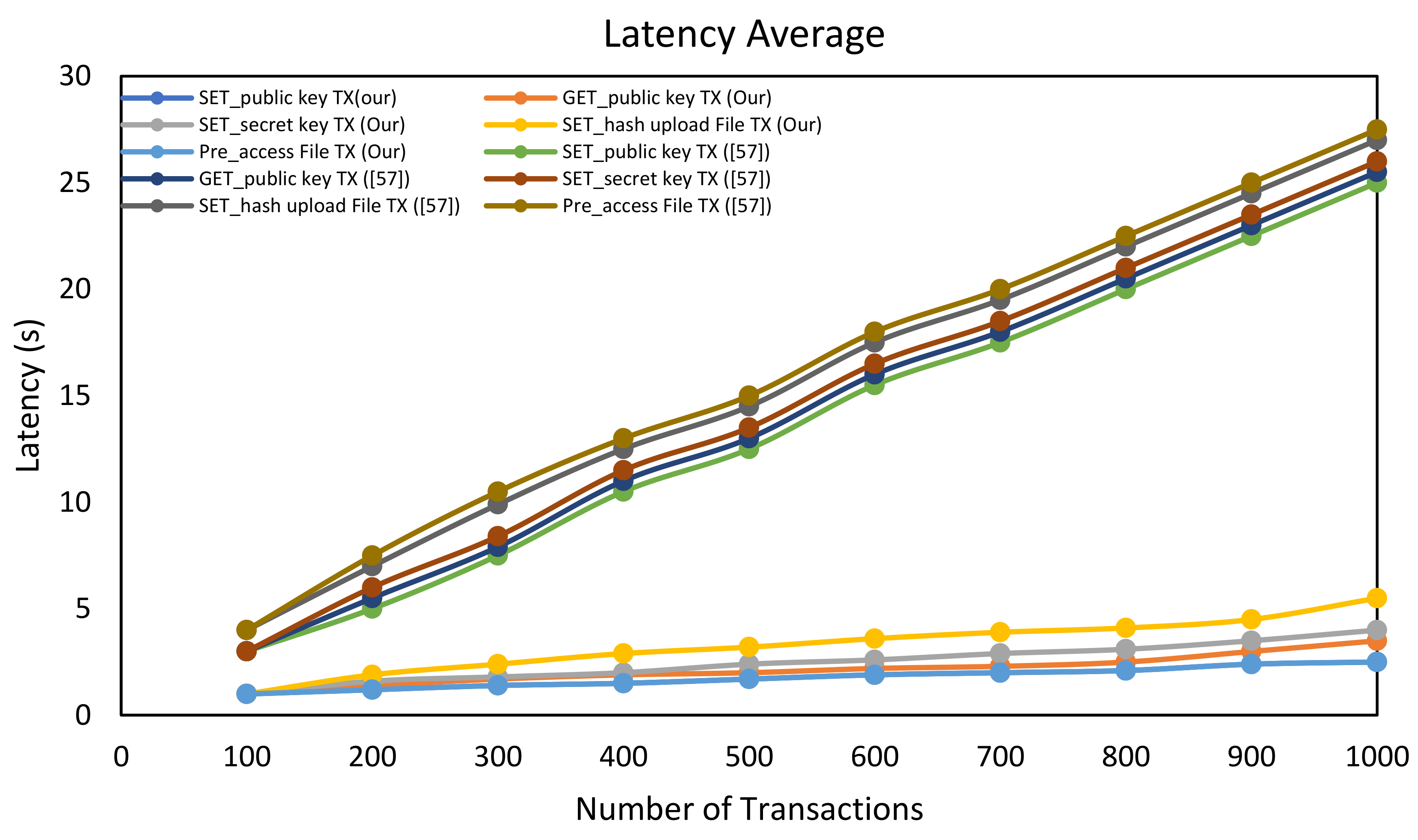
6.2.2. Throughput and Latency Measurements
7. Conclusions and Open Directions
Author Contributions
Funding
Institutional Review Board Statement
Informed Consent Statement
Data Availability Statement
Acknowledgments
Conflicts of Interest
Appendix A





References
- Khezr, S.; Rachid, B.; Abdulsalam, Y. Blockchain-based Model for Sharing Activities of Daily Living in Healthcare Applications. In Proceedings of the 2020 IEEE Int. Conf. on Dependable, Autonomic and Secure Computing, Int. Conf. on Pervasive Intelligence and Computing, Calgary, AB, Canada, 17–22 August 2020; pp. 627–633. [Google Scholar]
- Justinia, T. Blockchain Technologies: Opportunities for Solving Real-World Problems in Healthcare and Biomedical Sciences. Acta Inform. Med. 2019, 27, 284. [Google Scholar] [CrossRef]
- Gul, M.J.; Subramanian, B.; Paul, A.; Kim, J. Blockchain for public health care in smart society. Microprocess. Microsyst. 2021, 80, 103524. [Google Scholar] [CrossRef]
- Mayer, A.H.; da Costa, C.A.; Righi, R.D.R. Electronic health records in a blockchain: A systematic review. Health Inform. J. 2020, 26, 1273–1288. [Google Scholar] [CrossRef]
- Hasselgren, A.; Kralevska, K.; Gligoroski, D.; Pedersen, S.A.; Faxvaag, A. Blockchain in healthcare and health sciences—A scoping review. Int. J. Med. Inform. 2020, 134, 104040. [Google Scholar] [CrossRef]
- Hussien, H.M.; Yasin, S.M.; Udzir, S.N.I.; Zaidan, A.A.; Zaidan, B.B. A systematic review for enabling of develop a blockchain technology in healthcare application: Taxonomy, substantially analysis, motivations, challenges, recommendations and future direction. J. Med. Syst. 2019, 43, 320. [Google Scholar] [CrossRef]
- Mazlan, A.A.; Daud, S.M.; Sam, S.M.; Abas, H.; Rasid, S.Z.A.; Yusof, M.F. Scalability Challenges in Healthcare Blockchain System—A Systematic Review. IEEE Access 2020, 8, 23663–23673. [Google Scholar] [CrossRef]
- Xu, J.; Xue, K.; Li, S.; Tian, H.; Hong, J.; Hong, P.; Yu, N. Healthchain: A blockchain-based privacy preserving scheme for large-scale health data. IEEE Internet Things J. 2019, 6, 8770–8781. [Google Scholar] [CrossRef]
- Nizamuddin, N.; Salah, K.; Azad, M.A.; Arshad, J.; Rehman, M.H. Decentralized document version control using ethereum blockchain and IPFS. Comput. Electr. Eng. 2019, 76, 183–197. [Google Scholar] [CrossRef]
- Nguyen, D.C.; Pathirana, P.N.; Ding, M.; Seneviratne, A. Blockchain for secure ehrs sharing of mobile cloud based e-health systems. IEEE Access 2019, 7, 66792–66806. [Google Scholar] [CrossRef]
- Pournaghi, S.M.; Bayat, M.; Farjami, Y. MedSBA: A novel and secure scheme to share medical data based on blockchain technology and attribute-based encryption. J. Ambient Intell. Humaniz. Comput. 2020, 11, 4613–4641. [Google Scholar] [CrossRef]
- Iqbal, J.; Umar, A.I.; Amin, N.; Waheed, A. Efficient and secure attribute-based heterogeneous online/offline signcryption for body sensor networks based on blockchain. Int. J. Distrib. Sens. Netw. 2019, 15, 1550147719875654. [Google Scholar] [CrossRef]
- Wang, H.; Song, Y. Secure cloud-based EHR system using attribute-based cryptosystem and blockchain. J. Med. Syst. 2018, 42, 152. [Google Scholar] [CrossRef]
- Thwin, T.T.; Vasupongayya, S. Blockchain-based access control model to preserve privacy for personal health record systems. Secur. Commun. Netw. 2019. [Google Scholar] [CrossRef]
- Khatoon, A. A blockchain-based smart contract system for healthcare management. Electronics 2020, 9, 94. [Google Scholar] [CrossRef]
- Xia, Q.I.; Sifah, E.B.; Asamoah, K.O.; Gao, J.; Du, X.; Guizani, M. MeDShare: Trust-less medical data sharing among cloud service providers via blockchain. IEEE Access 2017, 5, 14757–14767. [Google Scholar] [CrossRef]
- Fan, K.; Wang, S.; Ren, Y.; Li, H.; Yang, Y. Medblock: Efficient and secure medical data sharing via blockchain. J. Med. Syst. 2018, 42, 136. [Google Scholar] [CrossRef] [PubMed]
- Zhao, Y.; Cui, M.; Zheng, L.; Zhang, R.; Meng, L.; Gao, D.; Zhang, Y. Research on electronic medical record access control based on blockchain. Int. J. Distrib. Sens. Netw. 2019, 15, 1550147719889330. [Google Scholar] [CrossRef]
- Abouelmehdi, K.; Beni-Hessane, A.; Khaloufi, H. Big healthcare data: Preserving security and privacy. J. Big Data 2018, 5, 1. [Google Scholar] [CrossRef]
- Hathaliya, J.J.; Tanwar, S. An exhaustive survey on security and privacy issues in Healthcare 4.0. Comput. Commun. 2020, 153, 311–335. [Google Scholar] [CrossRef]
- Song, D.X.; Wagner, D.; Perrig, A. Practical techniques for searches on encrypted data. In Proceedings of the 2000 IEEE Symposium on Security and Privacy, Berkeley, CA, USA, 14–17 May 2000; pp. 44–55. [Google Scholar]
- Curtmola, R.; Garay, J.; Kamara, S.; Ostrovsky, R. Searchable symmetric encryption: Improved definitions and efficient constructions. J. Comput. Secur. 2011, 19, 895–934. [Google Scholar] [CrossRef]
- Wang, C.; Cao, N.; Li, J.; Ren, K.; Lou, W. Secure ranked keyword search over encrypted cloud data. In Proceedings of the IEEE 30th International Conference on Distributed Computing Systems, Genoa, Italy, 21–25 June 2010; pp. 253–262. [Google Scholar]
- Cao, N.; Wang, C.; Li, M.; Ren, K.; Lou, W. Privacy-preserving multi-keyword ranked search over encrypted cloud data. IEEE Trans. parallel Distrib. Syst. 2013, 25, 222–233. [Google Scholar] [CrossRef]
- Alderman, J.; Martin, K.M.; Renwick, S.L. Multi-level access in searchable symmetric encryption. In Proceedings of the International Conference on Financial Cryptography and Data Security, Sliema, Malta, 3–7 April 2017; Springer: Cham, Switzerland, 2017; pp. 35–52. [Google Scholar]
- Liu, C.; Zhu, L.; Chen, J. Efficient searchable symmetric encryption for storing multiple source dynamic social data on cloud. J. Netw. Comput. Appl. 2017, 86, 3–14. [Google Scholar] [CrossRef]
- Emura, K.; Ito, K.; Ohigashi, T. Secure-channel free searchable encryption with multiple keywords: A generic construction, an instantiation, and its implementation. J. Comput. Syst. Sci. 2020, 114, 107–125. [Google Scholar] [CrossRef]
- Chen, L.; Zhang, N.; Sun, H.M.; Chang, C.C.; Yu, S.; Choo, K.K.R. Secure search for encrypted personal health records from big data NoSQL databases in cloud. Computing 2020, 102, 1521–1545. [Google Scholar] [CrossRef]
- Mihailescu, M.I.; Nita, S.L.; Racuciu, C. Multi-level access using searchable symmetric encryption with applicability for earth sciences. Scientific Bulletin “Mircea cel Batran”. Nav. Acad. 2020, 23, 213A–220A. [Google Scholar]
- Li, H.; Zhang, F.; He, J.; Tian, H. A searchable symmetric encryption scheme using blockchain. arXiv 2017, arXiv:1711.01030. [Google Scholar]
- Li, H.; Tian, H.; Zhang, F.; He, J. Blockchain-based searchable symmetric encryption scheme. Comput. Electr. Eng. 2019, 73, 32–45. [Google Scholar] [CrossRef]
- Zhang, Y.; Deng, R.H.; Shu, J.; Yang, K.; Zheng, D. TKSE: Trustworthy keyword search over encrypted data with two-side verifiability via blockchain. IEEE Access 2018, 6, 31077–31087. [Google Scholar] [CrossRef]
- Jiang, P.; Guo, F.; Liang, K.; Lai, J.; Wen, Q. Searchain: Blockchain-based private keyword search in decentralised storage. Future Gener. Comput. Syst. 2020, 107, 781–792. [Google Scholar] [CrossRef]
- Chen, L.; Lee, W.K.; Chang, C.C.; Choo, K.K.R.; Zhang, N. Blockchain based searchable encryption for electronic health record sharing. Future Gener. Comput. Syst. 2019, 95, 420–429. [Google Scholar] [CrossRef]
- Chen, Y.; Ding, S.; Xu, Z.; Zheng, H.; Yang, S. Blockchain-based medical records secure storage and medical service framework. J. Med. Syst. 2019, 43, 5. [Google Scholar] [CrossRef] [PubMed]
- Cao, S.; Zhang, G.; Liu, P.; Zhang, X.; Neri, F. Cloud-assisted secure eHealth systems for tamper-proofing EHR via blockchain. Inf. Sci. 2019, 485, 427–440. [Google Scholar] [CrossRef]
- Goyal, V.; Pandey, O.; Sahai, A.; Waters, B. Attribute-based encryption for fine-grained access control of encrypted data. In Proceedings of the 13th ACM Conference on Computer and Communications Security, Alexandria, VA, USA, 30 October 2006; pp. 89–98. [Google Scholar]
- Bethencourt, J.; Sahai, A.; Waters, B. Ciphertext-policy attribute-based encryption. In Proceedings of the 2007 IEEE Symposium on Security and Privacy (SP’07), Berkeley, CA, USA, 20–23 May 2007; pp. 321–334. [Google Scholar]
- Lewko, A.; Okamoto, T.; Sahai, A.; Takashima, K.; Waters, B. Fully secure functional encryption: Attribute-based encryption and (hierarchical) inner product encryption. In Annual International Conference on the Theory and Applications of Cryptographic Techniques; Springer: Berlin/Heidelberg, Germany, 2010; pp. 62–91. [Google Scholar]
- Balu, A.; Kuppusamy, K. An expressive and provably secure ciphertext-policy attribute-based encryption. Inf. Sci. 2014, 276, 354–362. [Google Scholar] [CrossRef]
- Pirretti, M.; Traynor, P.; McDaniel, P.; Waters, B. Secure attribute-based systems. J. Comput. Secur. 2010, 18, 799–837. [Google Scholar] [CrossRef]
- Nita, S.L.; Mihailescu, M.I. A Searchable Encryption Scheme Based on Elliptic Curves. In Proceedings of the Workshops of the International Conference on Advanced Information Networking and Applications, Caserta, Italy, 15–17 April 2020; Springer: Cham, Switzerland, 2020; pp. 810–821. [Google Scholar]
- Hur, J.; Noh, D.K. Attribute-based access control with efficient revocation in data outsourcing systems. IEEE Trans. Parallel Distrib. Syst. 2010, 22, 1214–1221. [Google Scholar] [CrossRef]
- Yin, H.; Zhang, J.; Xiong, Y.; Ou, L.; Li, F.; Liao, S.; Li, K. CP-ABSE: A ciphertext-policy attribute-based searchable encryption scheme. IEEE Access 2019, 7, 5682–5694. [Google Scholar] [CrossRef]
- Sun, J.; Ren, L.; Wang, S.; Yao, X. Multi-keyword searchable and data verifiable attribute-based encryption scheme for cloud storage. IEEE Access 2019, 7, 66655–66667. [Google Scholar] [CrossRef]
- Wang, S.; Yao, L.; Chen, J.; Zhang, Y. KS-ABESwET: A Keyword Searchable Attribute-Based Encryption Scheme with Equality Test in the Internet of Things. IEEE Access 2019, 7, 80675–80696. [Google Scholar] [CrossRef]
- Sultan, N.H.; Kaaniche, N.; Laurent, M.; Barbhuiya, F.A. Authorised keyword search over outsourced encrypted data in cloud environment. IEEE Trans. Cloud Comput. 2019. early access. [Google Scholar] [CrossRef]
- Zhang, L.; Hu, G.; Mu, Y.; Rezaeibagha, F. Hidden ciphertext policy attribute-based encryption with fast decryption for personal health record system. IEEE Access 2019, 7, 33202–33213. [Google Scholar] [CrossRef]
- Li, M.; Yu, S.; Ren, K.; Lou, W. September. Securing personal health records in cloud computing: Patient-centric and fine-grained data access control in multi-owner settings. In International Conference on Security and Privacy in Communication Systems; Springer: Berlin/Heidelberg, Germany, 2010; pp. 89–106. [Google Scholar]
- Li, M.; Yu, S.; Zheng, Y.; Ren, K.; Lou, W. Scalable and secure sharing of personal health records in cloud computing using attribute-based encryption. IEEE Trans. parallel Distrib. Syst. 2012, 24, 131–143. [Google Scholar] [CrossRef]
- Prince, P.B.; Lovesum, S.J. Privacy Enforced Access Control Model for Secured Data Handling in Cloud-Based Pervasive Health Care System. SN Comput. Sci. 2020, 1, 1–8. [Google Scholar] [CrossRef]
- Xu, L.; Xu, C.; Liu, J.K.; Zuo, C.; Zhang, P. Building a dynamic searchable encrypted medical database for multi-client. Inf. Sci. 2020, 527, 394–405. [Google Scholar] [CrossRef]
- Guo, R.; Shi, H.; Zheng, D.; Jing, C.; Zhuang, C.; Wang, Z. Flexible and efficient blockchain-based ABE scheme with multi-authority for medical on demand in telemedicine system. IEEE Access 2019, 7, 88012–88025. [Google Scholar] [CrossRef]
- Liu, X.; Ma, W.; Cao, H. MBPA: A Medibchain-Based Privacy-Preserving Mutual Authentication in TMIS for Mobile Medical Cloud Architecture. IEEE Access 2019, 7, 149282–149298. [Google Scholar] [CrossRef]
- Wang, S.; Zhang, D.; Zhang, Y. Blockchain-based personal health records sharing scheme with data integrity verifiable. IEEE Access 2019, 7, 102887–102901. [Google Scholar] [CrossRef]
- Niu, S.; Chen, L.; Wang, J.; Yu, F. Electronic Health Record Sharing Scheme With Searchable Attribute-Based Encryption on Blockchain. IEEE Access 2019, 8, 7195–7204. [Google Scholar] [CrossRef]
- Sun, J.; Yao, X.; Wang, S.; Wu, Y. Blockchain-Based Secure Storage and Access Scheme For Electronic Medical Records in IPFS. IEEE Access 2020, 8, 59389–59401. [Google Scholar] [CrossRef]
- Wang, S.; Wang, X.; Zhang, Y. A secure cloud storage framework with access control based on blockchain. IEEE Access 2019, 7, 112713–112725. [Google Scholar] [CrossRef]
- Miao, Y.; Ma, J.; Liu, X.; Wei, F.; Liu, Z.; Wang, X.A. m 2-ABKS: Attribute-based multi-keyword search over encrypted personal health records in multi-owner setting. J. Med. Syst. 2016, 40, 246. [Google Scholar] [CrossRef]
- Zheng, Q.; Xu, S.; Ateniese, G.A. VABKS: Verifiable attribute-based keyword search over outsourced encrypted data. In Proceedings of the IEEE INFOCOM 2014-IEEE Conference on Computer Communications, Toronto, ON, Canada, 27 April–2 May 2014; pp. 522–530. [Google Scholar]
- Ali, M.; Sadeghi, M.R. Provable secure lightweight attribute-based keyword search for cloud-based Internet of Things networks. Trans. Emerg. Telecommun. Technol. 2020, e3905. [Google Scholar] [CrossRef]
- The AVISPA Project. Available online: http://www.avispa-project.org/ (accessed on 2 February 2021).
- Armando, A.; Basin, D.; Boichut, Y.; Chevalier, Y.; Compagna, L.; Cuéllar, J.; Drielsma, P.H.; Héam, P.C.; Kouchnarenko, O.; Mantovani, J.; et al. The AVISPA tool for the automated validation of internet security protocols and applications. In International Conference on Computer Aided Verification; Springer: Berlin/Heidelberg, Germany, 2005; pp. 281–285. [Google Scholar]
- Chatterjee, S.; Das, A.K. An effective ECC-based user access control scheme with attribute-based encryption for wireless sensor networks. Secur. Commun. Netw. 2015, 8, 1752–1771. [Google Scholar] [CrossRef]
- Ding, S.; Cao, J.; Li, C.; Fan, K.; Li, H. A novel attribute-based access control scheme using blockchain for IoT. IEEE Access 2019, 7, 38431–38441. [Google Scholar] [CrossRef]
- Hsu, C.L.; Chen, W.X.; Le, T.V. An Autonomous Log Storage Management Protocol with Blockchain Mechanism and Access Control for the Internet of Things. Sensors 2020, 20, 6471. [Google Scholar] [CrossRef] [PubMed]
- Kim, M.; Yu, S.; Lee, J.; Park, Y.; Park, Y. Design of secure protocol for cloud-assisted electronic health record system using blockchain. Sensors 2020, 20, 2913. [Google Scholar] [CrossRef] [PubMed]
- SPAN: Security Protocol ANimator for AVISPA. Available online: http://people.irisa.fr/Thomas.Genet/span/ (accessed on 2 February 2021).
- Enron Email Dataset. Available online: https://www.cs.cmu.edu/~enron/ (accessed on 11 November 2020).
- Type-A Pairings-PBC. Available online: https://crypto.stanford.edu/pbc/manual/ch08s03.html (accessed on 11 November 2020).
- Pairing Based Cryptography (PBC) Library. Available online: https://crypto.stanford.edu/pbc/ (accessed on 11 November 2020).
- Ethereum Blockchain Network. Available online: https://geth.ethereum.org/getting-started/private-net (accessed on 11 November 2020).
- Clique Proof-of-Authority Consensus Protocol. Available online: https://github.com/ethereum/go-ethereum/tree/master/consensus/clique (accessed on 11 November 2020).
- Eth-Crypto Library for Ethereum. Available online: https://github.com/pubkey/eth-crypto (accessed on 11 November 2020).
- Caliper Benchmark Tool for Ethereum Configuration. Available online: https://hyperledger.github.io/caliper/v0.4.2/ethereum-config/ (accessed on 11 November 2020).

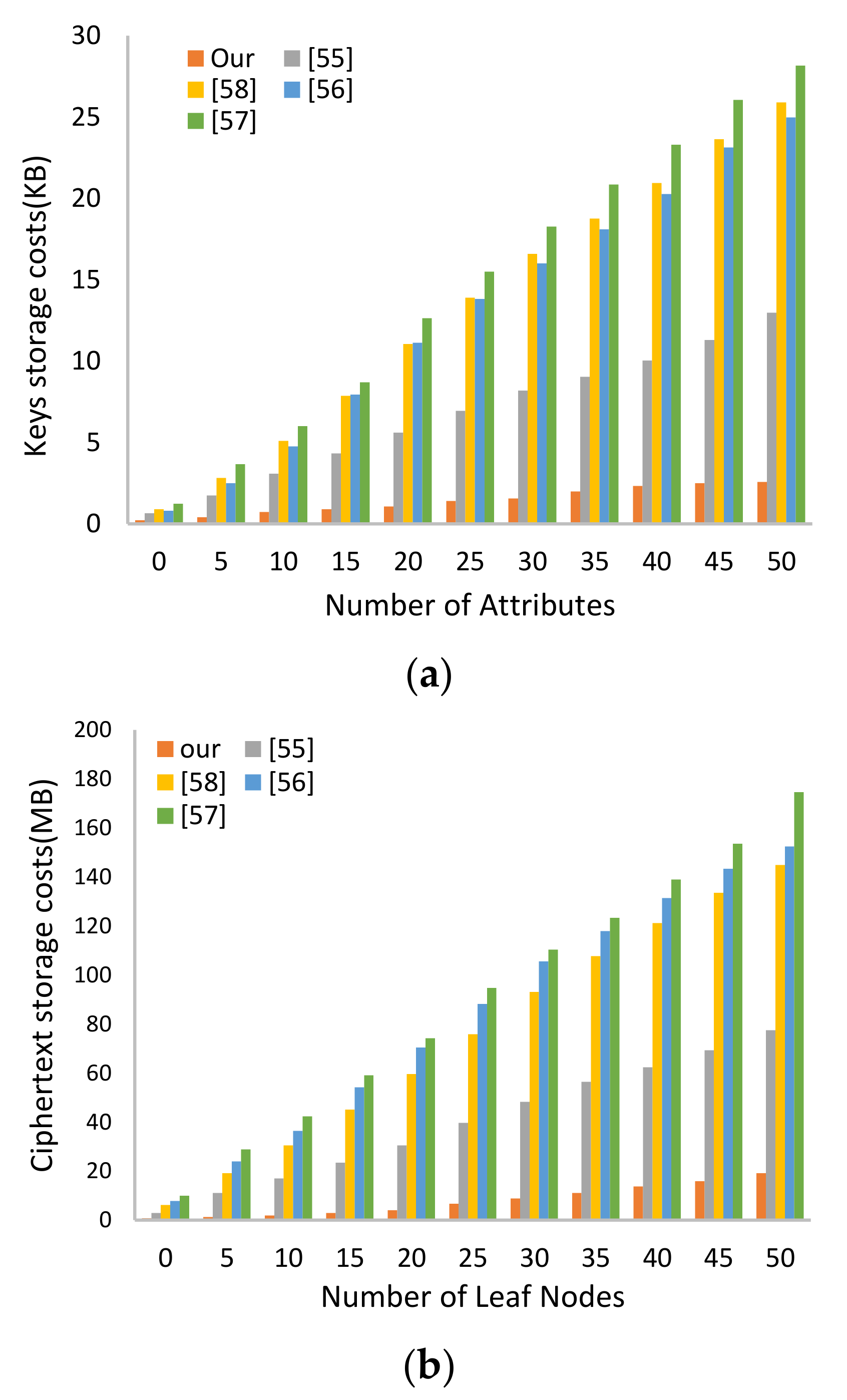
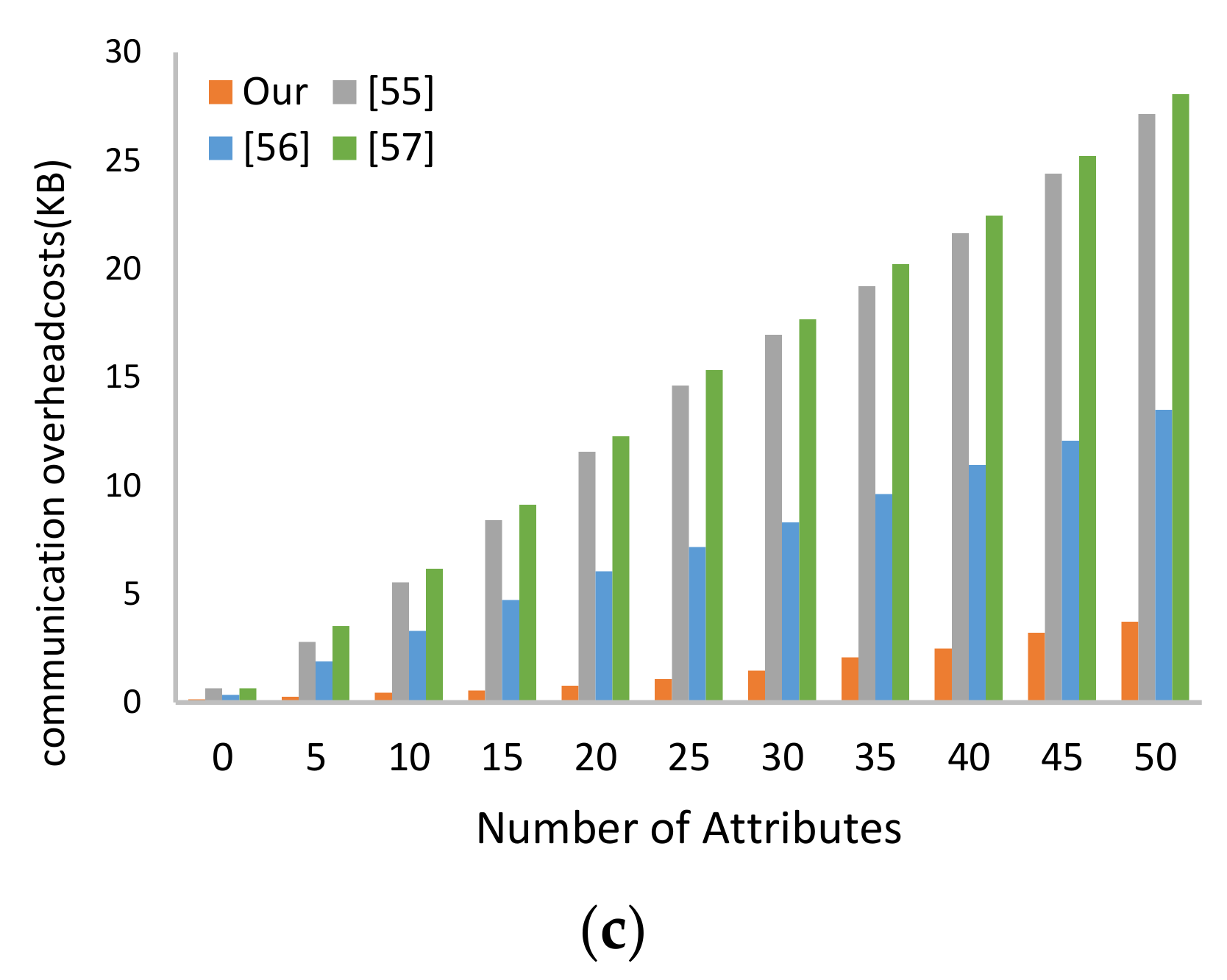
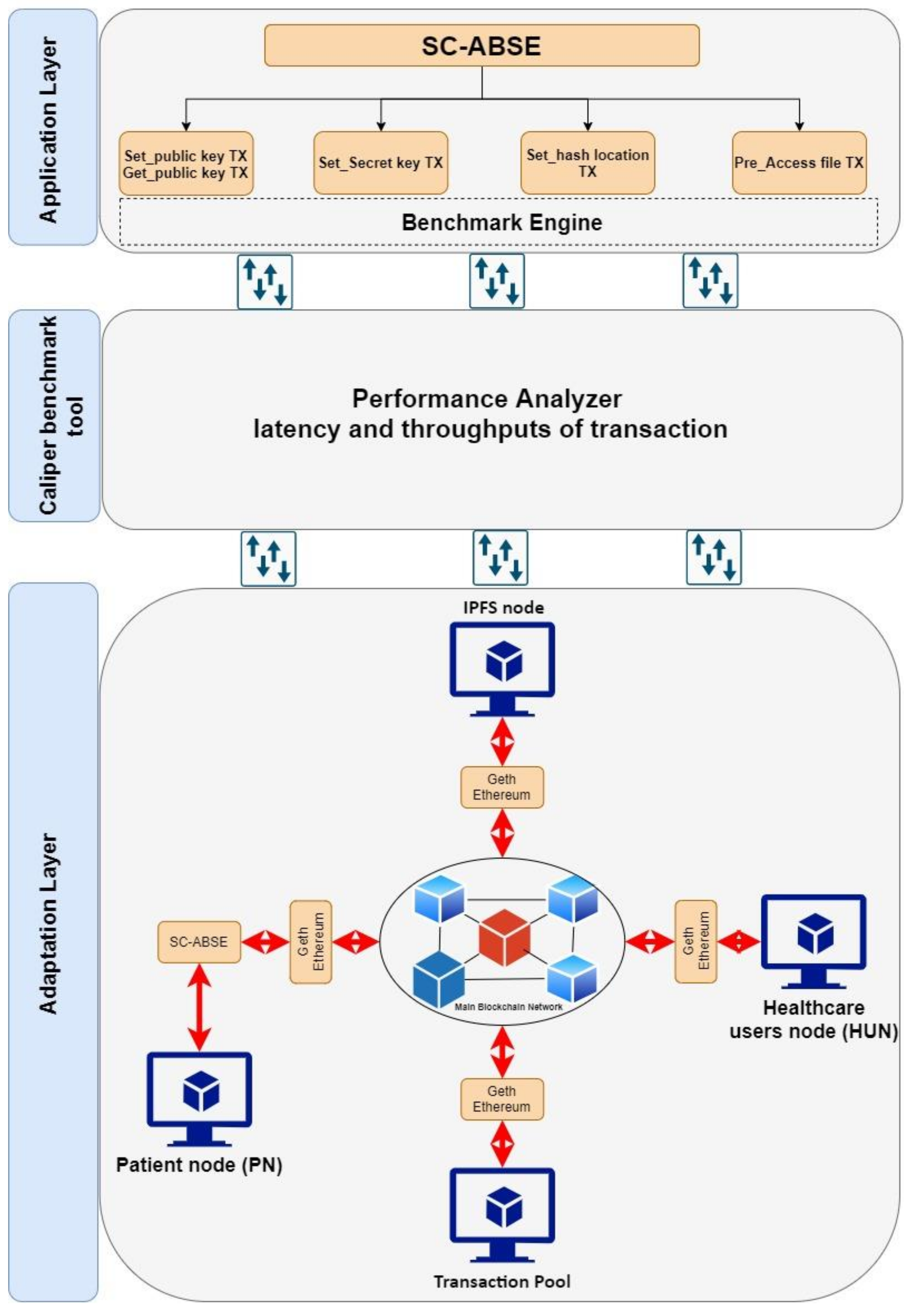
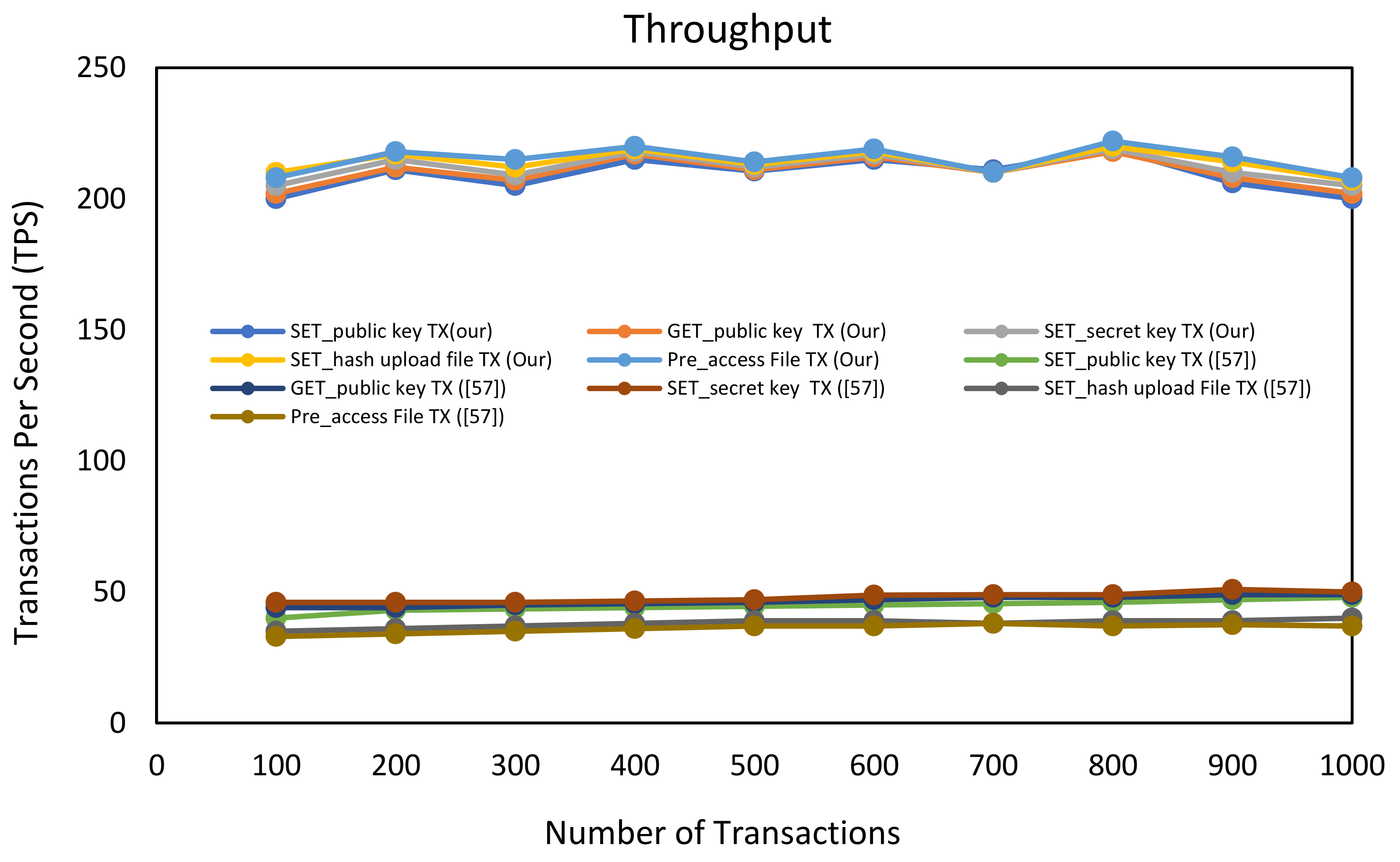
| Functionality Features | [55] | [56] | [57] | [58] | [59] | Current Study |
|---|---|---|---|---|---|---|
| Lightweight key generation | × | × | × | × | × | √ |
| Lightweight outsourcing mechanism | √ | × | × | × | × | √ |
| Lightweight token generation | × | × | × | × | × | √ |
| lightweight retrieving mechanism | × | × | × | × | × | √ |
| Multiowner search | × | × | × | × | √ | √ |
| Multikeyword search | × | × | × | × | √ | √ |
| Fine-grained keyword search | × | × | × | × | × | √ |
| Decentralised storage | × | × | √ | × | × | √ |
| Blockchain based | √ | √ | √ | √ | × | √ |
| Eliminates trusted PKG | × | × | × | × | × | √ |
| Security Properties | ||||||
| Keyword secrecy (KS) in the standard model | × | × | × | × | × | √ |
| Chosen-keyword attack(CKA) in the standard model | × | × | × | × | × | √ |
| Man-in-the-middle attack in the AVISPA toolset | × | × | × | × | × | √ |
| Replay attack in the AVISPA toolset | × | × | × | × | × | √ |
| Tamper-proof resistance | × | × | × | × | × | √ |
| User collusion attack resistance | × | × | × | × | × | √ |
| Entities | Description |
|---|---|
| Blockchain (BC) | Establishes and registers each node entity, such as the patient, the HUN and the IPFS on the network. To impose an agreement on each entity node, a smart contract is used for auditing purposes of all record requests and access activities. |
| Patient Node (PN) | Initialises system security parameters, for instance, public key (PK), master keys (MK), and final for the users in the HUN associated with defined attributes set . The patient node users choose an access structure to encrypted personal information and build the corresponding keyword index and upload the result of the ciphertext attached with an index to the IPFS storage. |
| Healthcare Users Node (HUN) | The users in the HUN require enough attributes to access the outsourcing ciphertext in IPFS by fulfilling the access structure policy. |
| IPFS Node | Stores the outsourced encrypted medical data of patients |
| Transactions pool | Contains the unconfirmed transactions for uploading and access medical data stored in the IPFS |
| Notations | Explanation |
|---|---|
| Multiplicative cyclic bilinear groups | |
| Collision-resistant hash functions | |
| Generator of the group | |
| Bilinear map | |
| PK | Public key |
| MK | Master key |
| SK | Secret key |
| SKE | Symmetric key algorithm |
| Access structure policy | |
| A number set of the attribute | |
| Set of medical files | |
| Set of keywords for medical file | |
| Set of keywords included in medical file | |
| Set of Submitted keyword for medical file | |
| Set of attributes for users in the HUN | |
| Token generation query for a conjunctive keyword | |
| Index set of conjunctive keywords |
| Number | Notations | Explanation |
|---|---|---|
| 1 | Number of medical attributes or data users | |
| 2 | Number of leaf nodes in an access tree | |
| 3 | , | Exponential operation time in and |
| 4 | Pairing operation time | |
| 5 | Hash operation time | |
| 6 | Length of an element in and | |
| 7 | Length of an element in | |
| 9 | SKE | Symmetric key algorithm |
| Scheme | Key Generation | Searchable Ciphertext Generation | Search Token Generation | Data Retrieving | Decryption |
|---|---|---|---|---|---|
| [55] | SKE + | ||||
| [58] | _________ | _____________ | |||
| [56] | |||||
| [57] | |||||
| Ours | ( | SKE + |
| Scheme | Key Length | Searchable Ciphertext Length | Search Token Length |
|---|---|---|---|
| [55] | |||
| [58] | + | _________ | |
| [56] | + | ||
| [57] | + | ||
| Our | ( |
| Network Deployment | Specifications |
|---|---|
| Blockchain network | Ethereum docker container |
| Consensus protocol | Clique proof-of-authority |
| Network analyser | Caliper benchmark tool |
| Smart Contract Deployment | Specifications |
| Programming languages | Vscode Solidity 0.8.0 |
| Cryptographic library | Cryptographic Javascript-functions for the Ethereum (Eth-crypto) library |
Publisher’s Note: MDPI stays neutral with regard to jurisdictional claims in published maps and institutional affiliations. |
© 2021 by the authors. Licensee MDPI, Basel, Switzerland. This article is an open access article distributed under the terms and conditions of the Creative Commons Attribution (CC BY) license (http://creativecommons.org/licenses/by/4.0/).
Share and Cite
Hussien, H.M.; Yasin, S.M.; Udzir, N.I.; Ninggal, M.I.H. Blockchain-Based Access Control Scheme for Secure Shared Personal Health Records over Decentralised Storage. Sensors 2021, 21, 2462. https://doi.org/10.3390/s21072462
Hussien HM, Yasin SM, Udzir NI, Ninggal MIH. Blockchain-Based Access Control Scheme for Secure Shared Personal Health Records over Decentralised Storage. Sensors. 2021; 21(7):2462. https://doi.org/10.3390/s21072462
Chicago/Turabian StyleHussien, Hassan Mansur, Sharifah Md Yasin, Nur Izura Udzir, and Mohd Izuan Hafez Ninggal. 2021. "Blockchain-Based Access Control Scheme for Secure Shared Personal Health Records over Decentralised Storage" Sensors 21, no. 7: 2462. https://doi.org/10.3390/s21072462
APA StyleHussien, H. M., Yasin, S. M., Udzir, N. I., & Ninggal, M. I. H. (2021). Blockchain-Based Access Control Scheme for Secure Shared Personal Health Records over Decentralised Storage. Sensors, 21(7), 2462. https://doi.org/10.3390/s21072462






