A Smart Contract-Based Dynamic Consent Management System for Personal Data Usage under GDPR
Abstract
:1. Introduction
1.1. Dynamic Consent Management
- DR1: Key stakeholders and roles identification–Who are the key stakeholders and what are their legitimate roles and responsibilities?
- DR2: User-centric dynamic consent management–How should data subjects be systematically empowered to control their personal data collection and usage consent?
- DR3: Consent and rights expression–How can individual consent and rights be explicitly and systematically expressed in a human/machine-readable format?
- DR4: Consent and data usage activity history accessibility–How should data subjects be given access to their personal data collection and usage activity history?
- DR5: Consent violation notification–How should data subjects be notified, and regulators be informed, about the consent agreement violation?
- DR6: Consent agreement withdrawal–What should be done when the consent agreement clauses are violated or the purpose of the acquired consent is no longer valid?
1.2. Our Contributions
- We propose a smart-contract-based dynamic consent management system architecture backed by blockchain technology for legal personal data usage based on GDPR.
- We propose user-centric dynamic consent management schemes that leverage smart contracts to enable users to take control of their consent on the personal data collection and usage throughout the data lifecycle. Consent rights can be delegated and audited by users by tracking the log events on the blockchain. Users get notified about any consent agreement clause violation and can withdraw the related consent.
- We integrate decentralized IPFS [18] nodes with our system to store data off-chain. The transactions history and access log data are recorded on the blockchain to enforce trust and provide tamper-proof data provenance, accountability, and traceability.
- A prototype of our system was designed and implemented on top of the Quorum blockchain platform [19] to determine its feasibility. The acceptability and reliability of the system were assessed by experimental testing and validation processes. The implemented code and artifacts have been made publicly available (https://github.com/mlecjm/sc-dcms, accessed on 25 November 2021).
- We present the security and privacy analysis of the system and evaluate its performance in terms of smart contract algorithm complexity, transaction throughput and latency, computing resource usage, and storage network bandwidth utilization.
2. Background and Related Work
2.1. Blockchain and Smart Contract
- Public blockchain networks are permissionless blockchain networks that enable parties to transact securely in trustless environments. In public blockchain networks such as Bitcoin [20] and Ethereum [21], everyone can join the network anonymously, and all participants having a copy of the ledger can create, verify, and validate transactions.
- Private blockchain networks are permissioned blockchain networks restricted to well-known and previously registered participants of an organization, which are authorized to access and use the network. Compared to public blockchain networks, private blockchain networks are more scalable and take less time for the network to reach a consensus, resulting in faster transactions. However, it is argued that they are not truly decentralized.
- Consortium blockchain networks, also known as hybrid or federated blockchain networks, are semi-decentralized blockchain networks, which combine public and private blockchain features. A consortium blockchain network is open only to a selected group of organizations or individuals that have decided to share the ledger among themselves for transactions. Some examples are R3 Corda and Quorum.
2.2. Blockchain-Enabled Dynamic Consent Management
3. Proposed System Model
3.1. Key Stakeholders and Roles Identification
- Data subject (DS) is a natural or legal person who owns and shares the data while defining privacy and security preferences, and dynamically manages consents (i.e., agree/deny, view, update, and withdraw) to collect and use personal data. Data subjects can also delegate consent rights and audit data collection and usage activity history, so they can withdraw given consent at any time if needed.
- Data controller (DC) is a natural or legal person, public authority, or agency that determines why and how the personal data should be collected and/or used. DC safeguards shared personal data while providing tools for users to dynamically manage consent agreements and control access to their data.
- Data processor (DP) refers to a party (i.e., a natural or legal person, public authority, or agency) that processes personal data on behalf of data controllers. A DP requests for consent and access rights before collecting and/or processing personal data, while recording processing activity history on the blockchain.
- Regulator (RG) denotes the supervisory authorities (i.e., the Office of the Data Protection Commissioner in the European Union) who regulate and control data protection regulations compliance and audit the transaction history to resolve conflicts. The regulator can assign, approve, and revoke membership profile roles.
3.2. Consent Requirements and Model Definition
3.3. System Architecture
- Personal Data Layer provides SC-enabled decentralized applications (Dapps) and services for personnel data management, such as data searching, provisioning, and processing features used to perform data analysis. To enable end users to interact with lower layers, Dapps rely on standard Application Program Interfaces (APIs).
- Dynamic Consent Management Layer is a middleware layer to feature dynamic consent management using SCs on top of the blockchain. It consists of the following components:
- (1)
- User profile management is in charge of managing the identities, profiles, and roles of participant users. It comprises two sub-components: (a) identity and profile manager, which is in charge of managing the identity and membership profile of participant users; and (b) profile role manager, which manages user role requests, approval, and revocation processes, while mapping user profiles to corresponding roles.
- (2)
- Consent agreement management manages data subjects’ consents throughout the data life cycle. It consists of the following: (a) consent requester, which manages consent requests to collect and use personal data; (b) consent agreement, which allows data subjects to systematically provide and manage varied types of consent agreements on each requested personal dataset; (c) consent tracker, which traces and tracks the consent transaction logs stored on the blockchain ledger, making all stakeholders accountable for their activities; (d) consent updater, which enables data subjects to update and adapt their consent agreement preferences (i.e., withdraw or revoke consent) based on the evolving context.
- (3)
- Smart contract code generator produces SCs based on predefined contract templates and consent agreement policies. It is composed of the following: (a) data/transaction format checks for provisioned data and transaction formats’ mutual compatibility; (b) source code generator creates the consent-agreements-related SCs to ensure contractual reliability in a machine-readable source code; (c) code verifier and validator checks for compatibility, correctness, and validity of the generated SCs to ensure that they can operate without errors and security vulnerabilities; and (d) compliance checker verifies privacy and security policies against legal compliance before the SC is published and deployed on the blockchain.
- (4)
- Security and privacy management comprises: (a) security manager, which provides data security-related features, like authentication, authorization, and confidentiality; (b) access control manager, which authorizes or denies access to personal data depending on access control policies and rules embedded in consent agreement contracts; (c) privacy manager, which helps users define and manage their privacy preferences; and (d) audit manager, which enables users to audit the history in terms of who requested (and granted) access to their data, when the data were used, and by whom. The user profile, security, and privacy management components extend the generic permissioned features provided by the lower layer.
- Distributed Ledger Technology and secure storage layer provides (1) a Quorum-blockchain-based [16] immutable transaction shared ledger and state database, maintained by a consensus of peer nodes in a consortium blockchain network, and (2) a P2P secure data storage system. This layer provides an operating environment for running SCs that enforces the consent agreement requirements.
- (1)
- Quorum blockchain [16] comprises two core sub-components: (a) a Quorum node, which is a lightweight forked version of the go-Ethereum client (known as geth) that was modified for supporting contract and transaction privacy, and (b) a private transaction manager (PTM) module that is divided into two sub-modules, namely the transaction manager (TM) and enclave. The TM manages private transactions by allowing access to encrypted transaction data and exchanging encrypted payloads between participant nodes. The enclave is a distributed ledger protocol that provides cryptographic methods for participants’ authentication, transaction authenticity, and historical data security. It works with the TM to leverage privacy by managing the symmetric key generation, data encryption, and decryption independently.
- (2)
- Secure data storage (SDS) orchestrates the data storage and access in a distributed storage system. SDS nodes store off-chain all the shared personal data and consent agreement forms in a peer-to-peer data storage network using IPFS protocol [15]. The hashed indexes of the data are recorded on a blockchain ledger and access is controlled using SCs. These nodes ensure the reliability, accessibility, and integrity of the data.
3.4. User Profile and Personal Data Management
3.4.1. User Profile Creation and Role Approval
- (1)
- Sign up for a membership user account of the consortium blockchain network, which results in the creation of a user profile;
- (2)
- Use the user-profile-associated information to request approval for the specific role(s) in the system;
- (3)
- The role approval requests are approved by the regulator(s) after verifying the identities of the requesters and the regulatory compliance requirements;
- (4)
- Upon receiving the role approval, the user profile status becomes active to use and manage in the system.
3.4.2. Personal Data Management
3.5. Smart-Contract-Based Dynamic Consent Management
3.5.1. Consent Expression
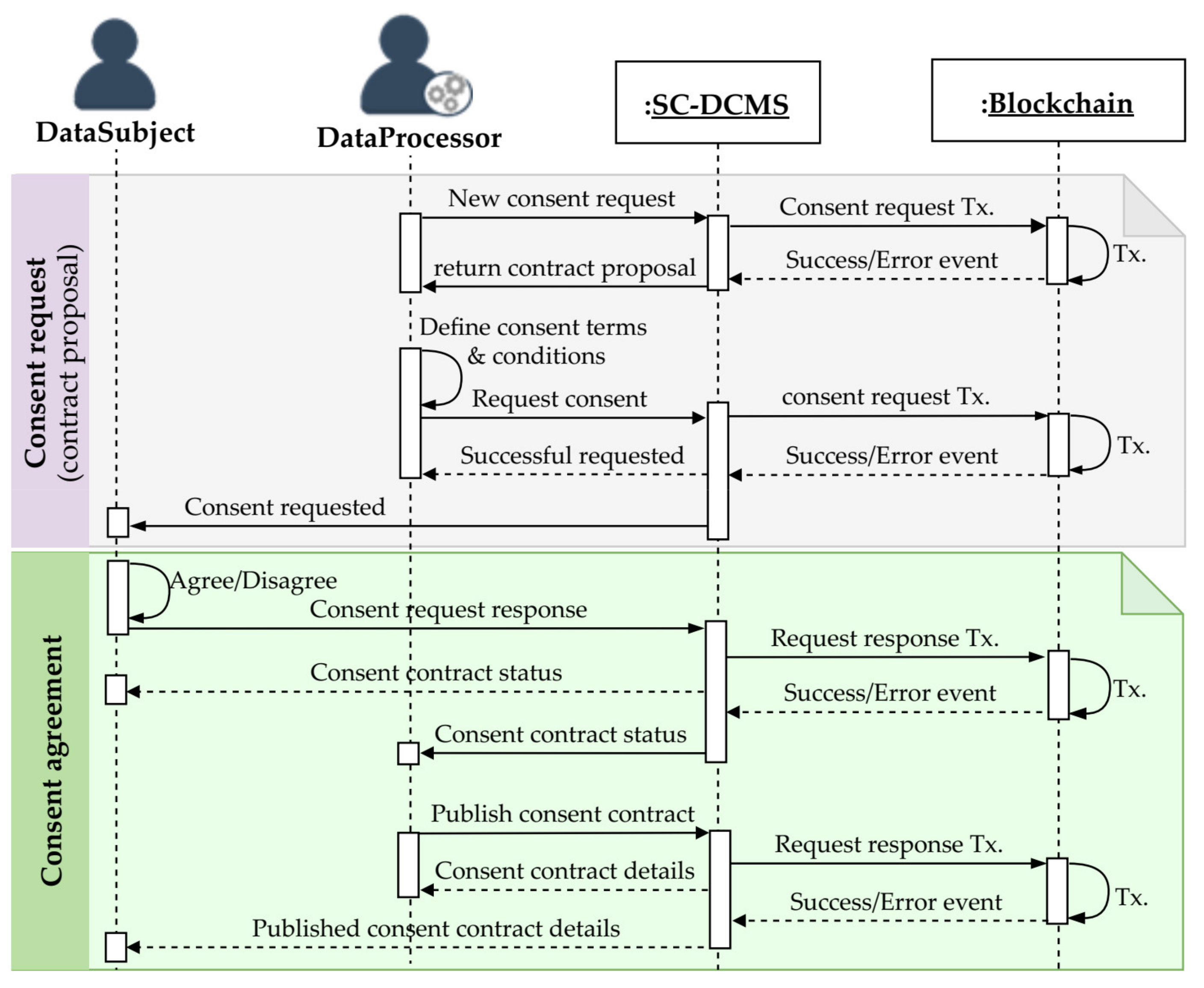
3.5.2. Consent Request and Agreement
| Algorithm 1 Consent agreement request |
 |
| Algorithm 2 Consent agreement |
 |
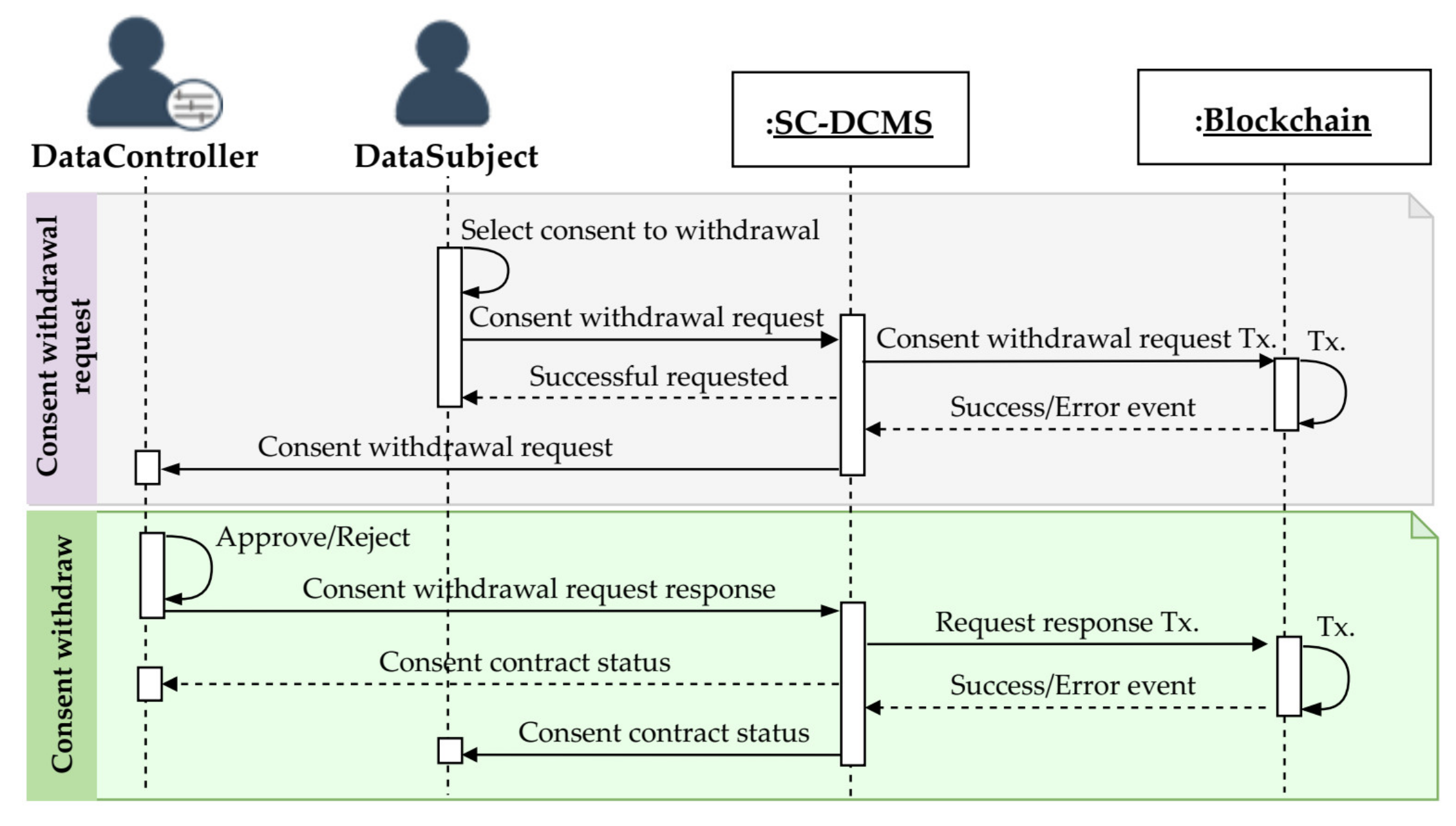
3.5.3. Consent Withdrawal
| Algorithm 3 Consent withdrawal |
 |
4. Implementation and Experiments
4.1. Consent Contract Generation
4.2. Implementation Details
5. Evaluation
5.1. Security and Privacy Analysis
5.2. Satisfying Design Requirements
- Key stakeholders and roles identification: Four key stakeholder participants were identified to fulfill DR1. Their legitimate roles and responsibilities are described in Section 3.1. Each participant user must sign up for a membership user profile and get authorized before joining the network and using the system.
- User-centric dynamic consent management: DR2 is satisfied by our proposed user-centric and paperless consent management system enabled by smart contracts. It enables data subjects to dynamically control their consent on the personal data collection and usage over its lifecycle.
- Consents and rights expression: Individual consents, and related rights are systematically and explicitly expressed in a human/machine-readable format to satisfy DR3. Furthermore, it allows users to delegate their consent rights if required.
- Consent and data usage activity history accessibility: The blockchain-based shared immutable leger is used for traceability and accountability of consents and data usage transaction records. Thus, data subjects can easily view and audit data collection and usage activity history to satisfy DR4.
- Consent violation notification: To fulfil DR5, our system provides consent agreement terms violation detection, notification, and reporting mechanisms using SCs.
- Consent agreement withdrawal: The proposed consent withdrawal mechanism satisfies DR6 (Article 7.3) by providing users the possibility to withdraw a given consent agreement when the purpose for which the personal data was collected is no longer valid or the consent agreement terms are violated.
5.3. Performance Evaluation
- (1)
- Computation time and space complexity: The complexity of our proposed algorithms is assessed to determine their efficiency in terms of computation time and space consumption. Considering Table 5, the complexity of a newUserProfile creation and roleApproval transaction is O(1), which means only a single read-write operation is required to verify if a given record does not exist before writing it to the blockchain. The computation complexity of addNewData and newConsentRequest transactions is also O(1), whereas the complexity of newConsentAgreement, newConsentWithdrawalRequest, and consentWithdrawal transaction is O(2), indicating that two read-write operations are required. In general, the first read operation is to check if the given record already exists in the ledger to avoid duplication, and the second is to collect required information to perform the transaction. For write operations, the first is to write the pushed transaction output data to the blockchain and the second is to update the status of related records in the ledger. The complexity of a smart contract algorithm affects the transaction execution time and latency. The evaluation has revealed that our proposed algorithms have a linear time complexity, which increases linearly with the size of input transactions. Table 6 provides the time and space complexity of a transaction and block in average values. For simplicity, the number of transactions per block is set by default to one. The space complexity of major SCs of our system is given in Table 7.
- (2)
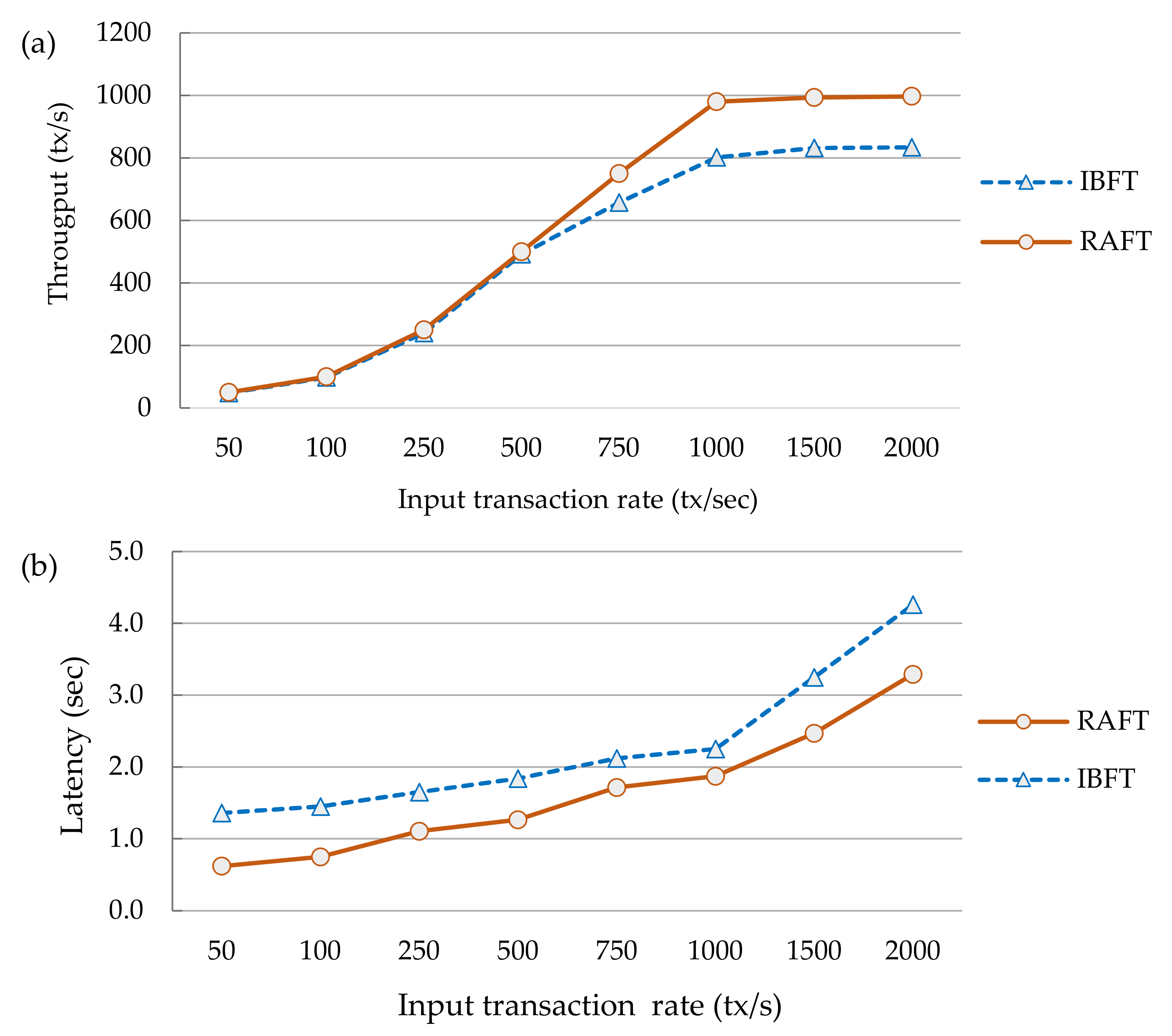
- Effect of input transaction rate variation on the transaction throughput and latency: The transaction throughput refers to the number of transactions processed per second (TPS) by the blockchain network [47,50], which is computed using Equation (1):where denotes successfully executed transactions, n is the number of input transactions, refers to the transaction execution time, and is the transaction completion time. The transaction latency is the time elapsed between the transaction submission and the response reception—after the transaction is successfully included in a block, committed, and confirmed on the blockchain [47,50]. Equation (2) is used to calculate the transaction latency.To understand the impact of the input transaction rate variation on the transaction throughput and latency, in our experiment, we generated a variable workload ranging from 50 to 2000 tx/s input transaction rates to stress-test the system. As read operations do not change the state of the ledger, our focus was on write transaction workloads that randomly update a selected key-value store of the deployed private contracts. The private transaction event generator scripts were launched from a client console to be broadcast to all the peer nodes. The experiment was repeated for three rounds for the Quorum blockchain network running with IBFT and RAFT consensus protocols. Later, we calculated the average transaction throughput and latencies. The plots in Figure 7a,b respectively depict the comparison between the IBFT and RAFT transaction throughput and latency. We observed that the throughput was scaling linearly for low transaction submission rates up to 802 and 980 tx/s for the IBFT and RAFT consensus, respectively. Beyond this, the throughput did not increase much until it reached a maximum point of 834 tx/s for IBFT and 1000 tx/s for RAFT, and then started to generate a lot of errors. In contrast, both consensus algorithms showed that the latency scaled linearly for all the input transaction rates. As can be seen, RAFT slightly over-performs IBFT.
- (3)
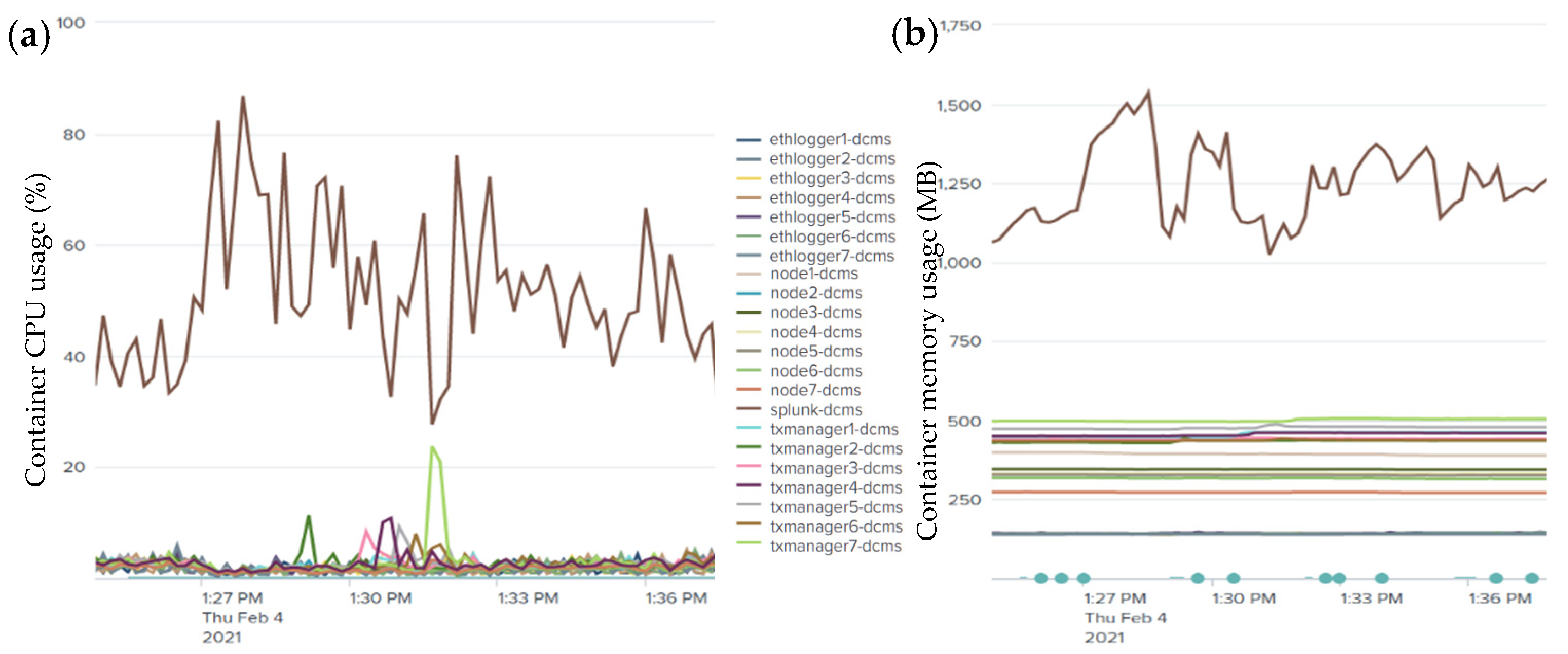
- Effect of input transaction rate variation on the computing resource consumption: We monitored in real time the system performance to evaluate the impact of input transaction rate variations on the CPU and memory of the system utilization by the containers deployed in our infrastructure, as shown in Figure 8a,b. It can be seen that the system has a moderate resource consumption, requiring less than 500 MB of memory and 10% of CPU utilization on average to keep the nodes running. However, the Splunk server container (SSC) used more resources as compared to the others. This is because it was monitoring and reporting the health state and metrics of the deployed infrastructure every 3 to 5 s continuously. We observed that the resource usage scaled with the variations in the transaction workload. SSC reached a peak of 87% and 1525 MB whereas one of the remaining nodes went up by 23% and 512 MB of the average CPU and memory usage, respectively.
- (4)
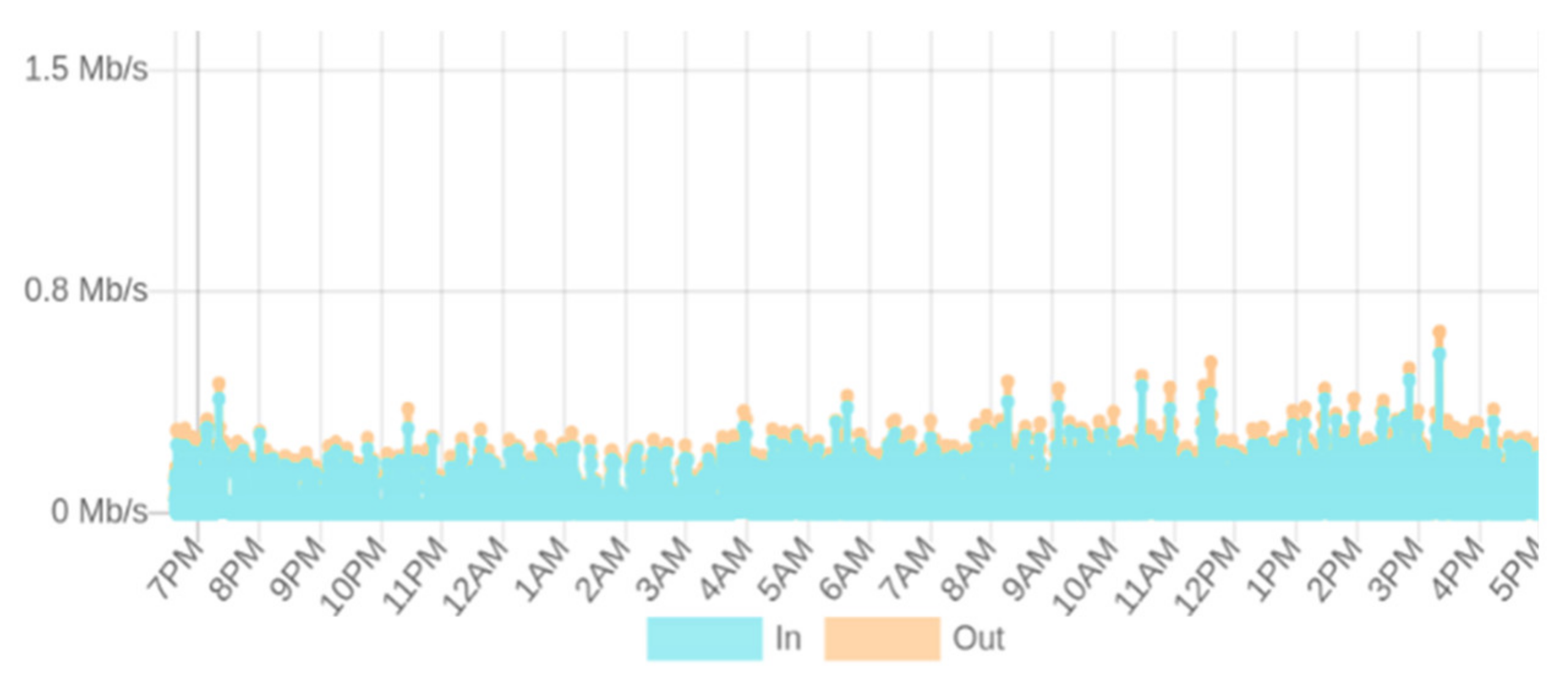
- Effect of input transaction rate variation on the storage network bandwidth consumption: The bandwidth utilization was monitored for the IPFS storage network traffic to investigate the impact of the transaction workload variations on the bandwidth usage. Figure 9 gives a summary of the input and output network bandwidth utilization of the IPFS-based storage system.
6. Limitations and Open Challenges
- System complexity and key management: The complexity of our proposed solution makes the key management very challenging, as it is integrated with several systems and platforms. Efficient and user-friendly key management schemes are required to take advantage of the permissioned blockchain-enabled security and privacy features.
- GDPR and immutable nature of blockchain: Withdrawing consent under GDPR might require, in some cases, deleting stored personal data for users to exercise their rights to be forgotten (Article 17). However, this remains a complex and challenging issue because of the immutable nature of blockchain wherein further research is required to be effectively applied and implemented [53,54].
- Smart contract vulnerabilities: Developing completely correct and bug-free smart contracts is very challenging. As SCs are gain in popularity, this will raise new security issues and challenges. Efficient smart contract vulnerability and security auditing solutions are very critical.
- Smart contract adaptability and upgradability: As SCs are immutably stored on a blockchain once deployed, they cannot be updated or upgraded for patching bugs or security vulnerabilities. This becomes a major challenge when adapting to evolving privacy, security, and legal compliance policies.
- Automated security and privacy policies verification and GDPR compliance checking: There is still an urgent need for user-friendly audit engines to automatically verify security, privacy, and legal compliance policies more efficiently.
7. Conclusions and Future Work
- The experiments in this study were performed on a single server with nodes running in containers. In the future, we plan to consider using a cluster or cloud computing services to deploy our solution and conduct in-depth performance and scalability analyses for a variable number of nodes and batch sizes.
- Novel efficient and user-friendly key management approaches are worthy of further investigation.
- Future research can try to develop systematic auditable and privacy-preserving proof of compliance schemes for consent revocations that require personal data deletion by data controllers.
Author Contributions
Funding
Institutional Review Board Statement
Informed Consent Statement
Acknowledgments
Conflicts of Interest
References
- Ekong, I.; Chukwu, E.; Chukwu, M. COVID-19 mobile positioning data contact tracing and patient privacy regulations: Exploratory search of global response strategies and the use of digital tools in Nigeria. JMIR mHealth uHealth 2020, 8, e19139. [Google Scholar] [CrossRef]
- Almeida, B.A.; Doneda, D.; Ichihara, M.Y.; Barral-Netto, M.; Matta, G.C.; Rabello, E.T.; Gouveia, F.C.; Barreto, M. Personal data usage and privacy considerations in the COVID-19 global pandemic. Saúde Colet 2020, 25, 2487–2492. [Google Scholar] [CrossRef] [PubMed]
- Park, O.; Park, Y.J.; Park, S.Y.; Kim, Y.M.; Kim, J.; Lee, J.; Park, E.; Kim, D.; Jeon, B.H.; Ryu, B.; et al. Contact transmission of Covid-19 in South Korea: Novel investigation techniques for tracing contacts. Osong Public Health Res. Perspect. 2020, 2487–2492. [Google Scholar]
- Ienca, M.; Vayena, E. On the responsible use of digital data to tackle the COVID-19 pandemic. Nat. Med. 2020, 26, 463–464. [Google Scholar] [CrossRef] [Green Version]
- Voigt, P.; Von dem Bussche, A. The Eu General Data Protection Regulation (GDPR): A Practical Guide, 1st ed.; Springer International Publishing: Cham, Switzerland, 2017. [Google Scholar]
- Teare, H.J.; Teare, H.J.; Morrison, M.; Whitley, E.A.; Kaye, J. Towards ‘Engagement 2.0′: Insights from a study of dynamic consent with biobank participant. Digit. Health 2015, 1. [Google Scholar] [CrossRef] [Green Version]
- Kaye, J.; Whitley, E.A.; Lund, D.; Morrison, M.; Teare, H.; Melham, K. Dynamic consent: A patient interface for twenty-first century research networks. Eur. J. Hum. Genet. 2015, 23, 141–146. [Google Scholar] [CrossRef] [Green Version]
- Steinsbekk, K.S.; Myskja, B.K.; Solberg, B. Broad consent versus dynamic consent in biobank research: Is passive participation an ethical problem? Eur. J. Hum. Genet. 2013, 21, 897–902. [Google Scholar] [CrossRef] [PubMed] [Green Version]
- Scott, A.S.; Goldsmith, M.; Teare, H. Wider Research Applications of Dynamic Consent. In IFIP International Summer School on Privacy and Identity Management; Springer: Cham, Switzerland, 2018. [Google Scholar]
- Budin-Ljøsne, I.; Budin-Ljøsne, I.; Teare, H.J.; Kaye, J.; Beck, S.; Bentzen, H.B.; Caenazzo, L.; Collett, C.; D’Abramo, F.; Felzmann, H.; et al. Dynamic Consent: A potential solution to some of the challenges of modern biomedical research. BMC Med. Ethics 2017, 18, 1–10. [Google Scholar] [CrossRef]
- Asghar, M.R.; Russello, G. Flexible and Dynamic Consent-Capturing. In International Workshop on Open Problems in Network Security; Springer: Berlin/Heidelberg, Germany, 2011; pp. 119–131. [Google Scholar]
- Prictor, M.; Lewis, M.A.; Newson, A.J.; Haas, M.; Baba, S.; Kim, H.; Kokado, M.; Minari, J.; Molnar-Gabor, F.; Yamamoto, B.; et al. Dynamic Consent: An Evaluation and Reporting Framework. J. Empir. Res. Hum. Res. Ethic 2020, 15, 175–186. [Google Scholar] [CrossRef]
- Mont, M.C.; Sharma, V.; Pearson, S. EnCoRe: Dynamic Consent, Policy Enforcement and Accountable Information Sharing within and across Organisations. Available online: https://www.hpl.hp.com/techreports/2012/HPL-2012-36.pdf (accessed on 25 November 2021).
- Tokas, S.; Owe, O. A Formal Framework for Consent Management. In International Conference on Formal Techniques for Distributed Objects, Components; Springer: Cham, Switzerland, 2020; Volume 12136, pp. 169–186. [Google Scholar]
- Genestier, P.; Zouarhi, S.; Limeux, P.; Excoffier, D.; Prola, A.; Sandon, S.; Temerson, J.M. Blockchain for consent management in the eHealth environment: A nugget for privacy and security challenges. J. Int. Soc. Telemed. Ehealth 2017, 5, GKR–e24. [Google Scholar]
- Camilo, J. Blockchain-based consent manager for GDPR compliance. In Open Identity Summit 2019; Gesellschaft für Informatik: Bonn, Germany, 2019; pp. 165–170. [Google Scholar]
- Rupasinghe, T.; Burstein, F.; Rudolph, C. Blockchain based Dynamic Patient Consent: A Privacy-Preserving Data Acquisition Architecture for Clinical Data Analytics. In Proceedings of the International Conference on Information Systems 2019, Munich, Germany, 15–18 December 2019. [Google Scholar]
- InterPlanetary File System. Available online: https://github.com/ipfs-shipyard/ipfs-desktop (accessed on 25 November 2021).
- Quorum: A Permissioned Implementation of Ethereum Supporting Data Privacy. Available online: https://github.com/ConsenSys/quorum (accessed on 25 November 2021).
- Nakamoto, S. Bitcoin: A peer-to-peer electronic cash system. Decentralized Bus. Rev. 2008, 21260. Available online: https://www.ussc.gov/sites/default/files/pdf/training/annual-national-training-seminar/2018/Emerging_Tech_Bitcoin_Crypto.pdf (accessed on 25 November 2021).
- Wood, G. Ethereum: A secure decentralised generalised transaction ledger. Ethereum Proj. Yellow Pap. 2014, 151, 1–32. [Google Scholar]
- Xu, X. A Taxonomy of Blockchain-Based Systems for Architecture Design. In Proceedings of the 2017 IEEE International Conference on Software Architecture (ICSA), Gothenburg, Sweden, 3 April 2017; pp. 243–252. [Google Scholar]
- Androulaki, E.; Barger, A.; Bortnikov, V.; Cachin, C.; Christidis, K.; De Caro, A.; Enyeart, D.; Ferris, C.; Laventman, G.; Manevich, Y.; et al. Hyperledger Fabric: A Distributed Operating System for Permissioned Blockchains. In Proceedings of the Thirteenth EuroSystem Conference, Porto, Portugal, 23 April 2018; pp. 1–15. [Google Scholar]
- Jaiman, V.; Urovi, V.A. Consent Model for Blockchain-Based Health Data Sharing Platforms. IEEE Access 2020, 8, 143734–143745. [Google Scholar] [CrossRef]
- Madine, M.M.; Battah, A.A.; Yaqoob, I.; Salah, K.; Jayaraman, R.; Al-Hammadi, Y.; Pesic, S.; Ellahham, S. Blockchain for Giving Patients Control over Their Medical Records. IEEE Access IEEE Access 2020, 8, 193102–193115. [Google Scholar] [CrossRef]
- Madine, M.M.; Salah, K.; Jayaraman, R.; Yaqoob, I.; Al-Hammadi, Y.; Ellahham, S.; Calyam, P. Fully Decentralized Multi-Party Consent Management for Secure Sharing of Patient Health Records. IEEE Access 2020, 8, 225777–225791. [Google Scholar] [CrossRef]
- Albanese, G.; Calbimonte, J.P.; Schumacher, M.; Calvaresi, D. Dynamic consent management for clinical trials via private blockchain technology. J. Ambient. Intell. Humaniz. Chomput. 2020, 11, 4909–4926. [Google Scholar] [CrossRef]
- Mamo, N.; Martin, G.M.; Desira, M.; Ellul, B.; Ebejer, J.P. Dwarna: A blockchain solution for dynamic consent in biobanking. Eur. J. Hum. Genet. 2019, 28, 609–626. [Google Scholar] [CrossRef] [Green Version]
- Bhaskaran, K.; Ilfrich, P.; Liffman, D.; Vecchiola, C.; Jayachandran, P.; Kumar, A.; Lim, F.; Nandakumar, K.; Qin, Z.; Ramakrishna, V.; et al. Double-Blind Consent-Driven Data Sharing on Blockchain. In Proceedings of the IEEE International Conference on Cloud Engineering (IC2E), Orlando, FL, USA, 17–20 April 2018; pp. 385–391. [Google Scholar]
- Rantos, K.; Drosatos, G.; Kritsas, A.; Ilioudis, C.; Papanikolaou, A.; Filippidis, A.P. A blockchain-based platform for consent management of personal data processing in the IoT ecosystem. Secur. Commun. Netw. 2019, 2019, 1–15. [Google Scholar] [CrossRef]
- Rantos, K.; Drosatos, G.; Demertzis, K.; Ilioudis, C.; Papanikolaou, A.; Kritsas, A. ADvoCATE: A Consent Management Platform for Personal Data Processing in the Iot Using Blockchain Technology. In Innovative Security Solutions for Information Technology and Communications; Springer: Cham, Switzerland, 2018; pp. 300–313. [Google Scholar]
- Agarwal, R.R.; Kumar, D.; Golab, L.; Keshav, S. Consentio: Managing Consent to Data Access Using Permissioned Blockchains. In Proceedings of the 2020 IEEE International Conference on Blockchain and Cryptocurrency (ICBC), IEEE, Toronto, ON, Canada, 2 May 2020; pp. 1–9. [Google Scholar]
- Lakhan, A.; Mohammed, M.A.; Rashid, A.N.; Kadry, S.; Panityakul, T.; Abdulkareem, K.H.; Thinnukool, O. Smart-Contract Aware Ethereum and Client-Fog-Cloud Healthcare System. Sensors 2021, 21, 4093. [Google Scholar] [CrossRef] [PubMed]
- Pandit, H.J.; Debruyne, C.; O’Sullivan, D.; Lewis, D. GConsent-a Consent Ontology Based on the GDPR. In European Semantic Web Conference; Springer: Cham, Switzerland, 2019. [Google Scholar]
- Xacml v3. 0 Core and Hierarchical Role-Based Access Control (RBAC) Profile Version 1.0: Committee Specification 02; Rissanen, E. (Ed.) Organization for the Advancement of Structured Information Standards (OASIS): Burlington, MA, USA, 2014. [Google Scholar]
- JSON Profile of XACML 3.0 Version 1.0, vol. 1: Candidate OASIS Standard 01; Brossard, D. (Ed.) Organization for the Advancement of Structured Information Standards (OASIS): Burlington, MA, USA, 2014; p. 11. [Google Scholar]
- Cakeshop. Available online: https://github.com/ConsenSys/cakeshop (accessed on 25 November 2021).
- Tessera. Available online: https://github.com/consensys/tessera (accessed on 25 November 2021).
- Constellation. A Self-Managing Peer-to-Peer System. Available online: https://bit.ly/3kaVrmv (accessed on 25 November 2021).
- Istanbul Byzantine Fault Tolerant. Available online: https://bit.ly/3kAw51J (accessed on 25 November 2021).
- Ongaro, D.; Ousterhout, J. In Search of an Understandable Consensus Algorithm. In Proceedings of the USENIX Annual Technical Conference ({USENIX} {ATC} 14, Philadelphia, PA, USA, 19–20 June 2014; pp. 305–319. [Google Scholar]
- cAvisior. Available online: https://github.com/google/cadvisor (accessed on 25 November 2021).
- Quorum Reporting. Available online: https://github.com/ConsenSys/quorum-reporting (accessed on 25 November 2021).
- Splunk App for Quorum. Available online: https://splk.it/3qg6myV (accessed on 25 November 2021).
- So, S.; Lee, M.; Park, J.; Lee, H.; Oh, H. VeriSmart: A Highly Precise Safety Verifier for Ethereum Smart Contracts. In Proceedings of the IEEE Symposium on Security and Privacy (SP), San Francisco, CA, USA, 30 July 2020; pp. 1678–1694. [Google Scholar]
- Tikhomirov, T.; Voskresenskaya, E.; Ivanitskiy, I.; Takhaviev, R.; Marchenko, E.; Alexandrov, Y. Smartcheck: Static Analysis of Ethereum Smart Contracts. In Proceedings of the 1st International Workshop on Emerging Trends in Software Engineering for Blockchain, Gothenburg, Sweden, 27 May 2018; pp. 9–16. [Google Scholar]
- Baliga, A.; Subhod, I.; Kamat, P.; Chatterjee, S. Performance evaluation of the quorum blockchain platform. arXiv 2018, arXiv:1809.03421. Available online: https://arxiv.org/pdf/1809.03421.pdf (accessed on 25 November 2021).
- Bieker, F.; Friedewald, M.; Hansen, M.; Obersteller, H.; Rost, M. A Process for Data Protection Impact Assessment Under the European General Data Protection Regulation. In Annual Privacy Forum; Springer: Cham, Switzerland, 2016; pp. 21–37. [Google Scholar]
- Health Information and Quality Authority. Guidance on Privacy Impact Assessment in Health and Social Care: Version 2.0. 2017. Available online: https://bit.ly/2Yqp2kf (accessed on 25 November 2021).
- Mazzoni, M.; Corradi, A.; Di Nicola, V. Performance evaluation of permissioned blockchains for financial applications: The ConsenSys Quorum case study. Blockchain Res. Appl. 2021, 100026. [Google Scholar] [CrossRef]
- Egberts, A. The Oracle Problem—An Analysis of How Blockchain Oracles Undermine the Advantages of Decentralized Ledger Systems. SSRN 3382343. Available online: https://papers.ssrn.com/sol3/papers.cfm?abstract_id=3382343 (accessed on 25 November 2021).
- Caldarelli, G. Understanding the Blockchain Oracle Problem: A Call for Action. Information 2020, 11, 509. [Google Scholar] [CrossRef]
- Politou, E.; Alepis, E.; Patsakis, C. Forgetting personal data and revoking consent under the GDPR: Challenges and proposed solutions. J. Cybersecur. 2018, 4, tyy001. [Google Scholar] [CrossRef]
- Lee, Y.K.; Jeong, J. Securing biometric authentication system using blockchain. ICT Express 2021, 7, 322–326. [Google Scholar] [CrossRef]
- Ranise, S.; Siswantoro, H. Automated Legal Compliance Checking by Security Policy Analysis. In International Conference on Computer Safety, Reliability and Security; Springer: Cham, Switzerland, 2017; Volume 10489, pp. 361–372. [Google Scholar]
- Torre, D.; Soltana, G.; Sabetzadeh, M.; Briand, L.C.; Auffinger, Y.; Goes, P. Using Models to Enable Compliance Checking Against the GDPR: An Experience Report. In Proceedings of the ACM/IEEE International Conference on Model Driven Engineering Languages and Systems (MoDELS), Munich, Germany, 15–20 September 2019; pp. 1–11. [Google Scholar] [CrossRef] [Green Version]




| Features | Ethereum 1 | Hyperledger Fabric 2 | R3 Corda 3 | Ripple 4 | Quorum 5 |
|---|---|---|---|---|---|
| Targeted industry | Cross-industry | Cross-industry | Financial | Financial | Cross-industry |
| Mode of operation (ledger) | Permissionless (public) | Permissioned (private) | Permissioned (private) | Permissionless (public) | Permissioned (public/private) |
| Consortium network support | X | √ | √ | X | √ |
| Decentralization | Decentralized | Partially | Partially | Decentralized | Decentralized |
| Transaction/smart contract privacy | X/X | √/√ | √/√ | X/X | √/√ |
| Consensus protocols | PoW/PoS | Pluggable | Notary-based | Probabilistic voting | Pluggable |
| Transaction throughput | ~20 tps | >2000 tps | ~170 tps | ~1500 tps | ~1000 tps |
| Smart contract support | √ | √ | √ | √ | √ |
| Blockchain oracle | √ | √ | √ | √ | √ |
| Cryptocurrency | ETH | N/A | N/A | XRP | ETH |
| Paper | Legal Basis | User-Centric | Consent Agreement/Delegation | Auditability/ Withdrawal | Privacy/Security | SC Language | Blockchain Platform | Type of Network | Use of IPFS 3 | Implementation | Performance Evaluation |
|---|---|---|---|---|---|---|---|---|---|---|---|
| [11] | DPD 1 | √ | √/√ | X/√ | X/X | X | X | X | X | X | X |
| [12] | - | √ | √/X | - | - | X | X | X | X | X | X |
| [13] | - | √ | √/X | X/√ | √/√ | X | X | X | X | √ | X |
| [14] | GDPR | √ | √/X | √/X | √/√ | X | X | X | X | X | X |
| [15] | - | √ | √/X | X/√ | - | - | HLF 2 | Private | X | Prototype | X |
| [16] | GDPR | √ | √/X | - | X | X | - | - | X | X | X |
| [17] | GDPR | √ | √/X | √/X | - | - | - | - | X | X | X |
| [24] | - | √ | √/X | √/X | X/√ | Solidity | Ethereum | Public | X | Prototype | √ |
| [25,26] | - | √ | √/X | √/X | √/√ | Solidity | Ethereum | Public | √ | Prototype | √ |
| [27] | GDPR | √ | √/X | √/√ | X/√ | JavaScript | HLF | Private | X | √ | X |
| [28] | GDPR | √ | √/X | √/√ | √/√ | JavaScript | HLF | Private | X | Prototype | X |
| [29] | - | √ | √/X | √/√ | √/√ | Go | HLF | Private | X | Prototype | X |
| [30,31] | GDPR | √ | √/X | √/X | X/√ | Solidity | Ethereum | Public | X | Prototype | X |
| [32] | GDPR | √ | √/X | √/√ | X/√ | Go | HLF | Private | X | Prototype | √ |
| [33] | X | X | X/X | X/X | X/√ | Solidity | Ethereum | Public | X | Prototype | √ |
| Our work | GDPR | √ | √/√ | √/√ | √/√ | Solidity | Quorum | Consortium | √ | Prototype | √ |
| Notation | Description |
|---|---|
| DS, DC, DP, RG | data subject, data controller, data processor, regulator |
| RQT, PT | requester, participants |
| CC, CR, RC | consent contract, consent request, request creation |
| RS, PD, OP | resource, personal data, operation |
| CXT, Legalb, Prd | context, legal basis, period of usage |
| CST, Territory | constraint, territory of use |
| A, a, AG, CA | account, address, agreement, consent agreement |
| CW, CWR, SC, v | consent withdrawal, consent withdrawal request, smart contract, version |
| id, dsign, status, purp, rsn | identifier, digital signature, status, purpose of use, reason |
| tstamp, startTime, endTime | timestamp, starting time, ending time |
| OS, IPFS, EVM | operating system, interplanetary file system, Ethereum virtual machine |
| Hardware | Description |
| CPU | AMD® Ryzen 7 1700-8 Core |
| GPU/RAM/SSD | NV132/64 GB/2 TB |
| Network interface | I211 Gigabit Network |
| Software | Description |
| OS | Ubuntu 20.04.2 LTS, 64bit |
| Network generation | Docker-compose v1.25.0 |
| Quorum version | Quorum 20.10.0 |
| Consensus protocol | IBFT, RAFT |
| Number of nodes | 7 |
| Splunk Enterprise Server | v8.0.4 |
| Splunk App for Quorum | v1.0.9 |
| Client | Geth/node-raft/v1.9.7(quorum-v20.10.0)/linux-amd64/go1.13.15 |
| Nodejs/Npm/Cakeshop | v10.19.0/v6.14.4/v0.11.0 |
| Solidity compiler EVM | Constantinople |
| IPFS | go-ipfs v0.7.0 |
| Type of Transaction | R1 | W2 |
|---|---|---|
| newUserProfile | O(1) | O(1) |
| roleApproval | O(1) | O(1) |
| addNewData | O(1) | O(1) |
| newConsentRequest | O(1) | O(1) |
| newConsentAgreement | O(2) | O(2) |
| newConsentWithdrawalRequest | O(2) | O(2) |
| consentWithdrawal | O(2) | O(2) |
| Parameter | IBFT | RAFT |
|---|---|---|
| Transaction latency (sec) | 0.0018 | 0.0015 |
| Transaction size (KB) | 2.380 | 2.378 |
| Block size (KB) | 4.247 | 4.245 |
| Number of transactions per block | 1 | 1 |
| Default block time (sec) | 1 | 0.05 |
| Smart Contract | Value |
|---|---|
| PersonalDataMgr (KB) | 10.149 |
| UserProfileMgr (KB) | 12.438 |
| ConsentAgreementMgr (KB) | 18.117 |
Publisher’s Note: MDPI stays neutral with regard to jurisdictional claims in published maps and institutional affiliations. |
© 2021 by the authors. Licensee MDPI, Basel, Switzerland. This article is an open access article distributed under the terms and conditions of the Creative Commons Attribution (CC BY) license (https://creativecommons.org/licenses/by/4.0/).
Share and Cite
Merlec, M.M.; Lee, Y.K.; Hong, S.-P.; In, H.P. A Smart Contract-Based Dynamic Consent Management System for Personal Data Usage under GDPR. Sensors 2021, 21, 7994. https://doi.org/10.3390/s21237994
Merlec MM, Lee YK, Hong S-P, In HP. A Smart Contract-Based Dynamic Consent Management System for Personal Data Usage under GDPR. Sensors. 2021; 21(23):7994. https://doi.org/10.3390/s21237994
Chicago/Turabian StyleMerlec, Mpyana Mwamba, Youn Kyu Lee, Seng-Phil Hong, and Hoh Peter In. 2021. "A Smart Contract-Based Dynamic Consent Management System for Personal Data Usage under GDPR" Sensors 21, no. 23: 7994. https://doi.org/10.3390/s21237994
APA StyleMerlec, M. M., Lee, Y. K., Hong, S.-P., & In, H. P. (2021). A Smart Contract-Based Dynamic Consent Management System for Personal Data Usage under GDPR. Sensors, 21(23), 7994. https://doi.org/10.3390/s21237994








