SEE-TREND: SEcurE Traffic-Related EveNt Detection in Smart Communities
Abstract
1. Smart Cities and Smart Communities
1.1. Smart Cities
- First, the Smart Cities will adopt an anticipatory governance style aligned with the real needs of the citizens;
- Second, they provide their citizens with timely access to high-quality information and services;
- Third, they rely on a broad-based participation of the citizens in the co-creation, in partnership with the local government, of services needed by the community.
1.2. Smart Communities
1.3. Smart Mobility—A Key Service in Smart Cities and Smart Communities
2. SEE-TREND—Motivation
- 1.
- Detects existing traffic conditions and discovers discernible trends in the traffic flow; this allows SEE-TREND to predict imminent traffic events and to alert interested parties to their likely occurrence;
- 2.
- Intelligently disseminates relevant traffic-related information using a recently-developed information decay model. This model developed by [45], captures the rate at which the value of traffic-related information decays as a function of time and distance;
- 3.
- Is secure, privacy-aware and non-intrusive. Being non-intrusive, the deployment of SEE-TREND will not adversely affect the durability and structural integrity of our roadways, as ILDs do.
Our Contributions
- We have developed techniques for setting up and managing secure data collection. SEE-TREND collects traffic-related data from vehicles participating in the traffic flow. Since, in general, these data are highly correlated, there is no need to collect data from all passing cars, especially in dense traffic. In support of privacy and security of data collection, every message will be associated anonymously with a physical vehicle, eliminating the need for IDs or pseudonyms;
- SEE-TRENDS detects trends in the traffic flow by aggregating the collected data: SEE-TREND aggregates traffic flow data collected from participating vehicles and uses the resulting information to anticipate trends in the traffic flow and to infer the likely occurrence of traffic events including imminent slowdowns and congestion;
- SEE-TRENDS enables efficient traffic-related information dissemination. SEE-TREND provides two integrated modalities for information dissemination. For non time-critical information dissemination, SEE-TREND relies on vehicles in the oncoming traffic; however, time-critical messages are disseminated directly by the SEE-TREND roadside infrastructure. One of our key objectives is to further extend the model of information decay both in time and distance [45]. Such a model can be used to optimize the dissemination of relevant traffic-related information thus reducing network traffic;
- SEE-TRENDS supports information dissemination in planned evacuations and emergencies. SEE-TREND allows emergency management personnel to disseminate important information to drivers. This feature of the system is vital during large-scale evacuations, allowing emergency managers to alert drivers to estimated travel times, to the availability of resources, and to contraflow policies.
3. State of the Art
3.1. The Vehicle Model
- GPS receiver;
- A short-range, DSRC-compliant, wireless transceiver;
- A tamper-resistant Event Data Recorder (EDR). The EDR is responsible for recording mobility attributes including acceleration, deceleration, lane changes, etc. [46]. Each such transaction is associated with an instantaneous GPS reading (in its 2006 ruling [47], the NHTSA has mandated that starting September 2010 an EDR will have to be installed in vehicles with an unloaded weight of less than 5000 lbs). All of the vehicle’s sub-assemblies feed their readings into the EDR [48,49].
3.2. Vehicular Networks
3.3. Security and Privacy Issues in VANET
3.4. Intelligent Transportation Systems
3.5. Smartphone-Based Systems
4. The Details of SEE-TRENDS
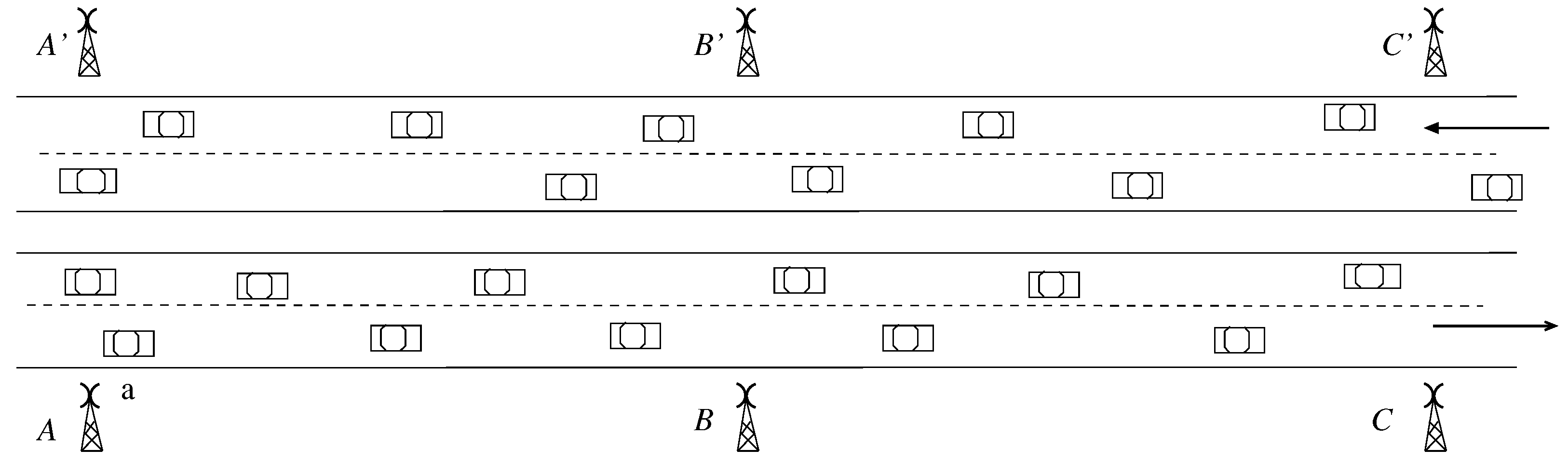
4.1. The TMU—The Workhorse of SEE-TRENDS
4.2. Secure Data Exchange between Adjacent TMUs
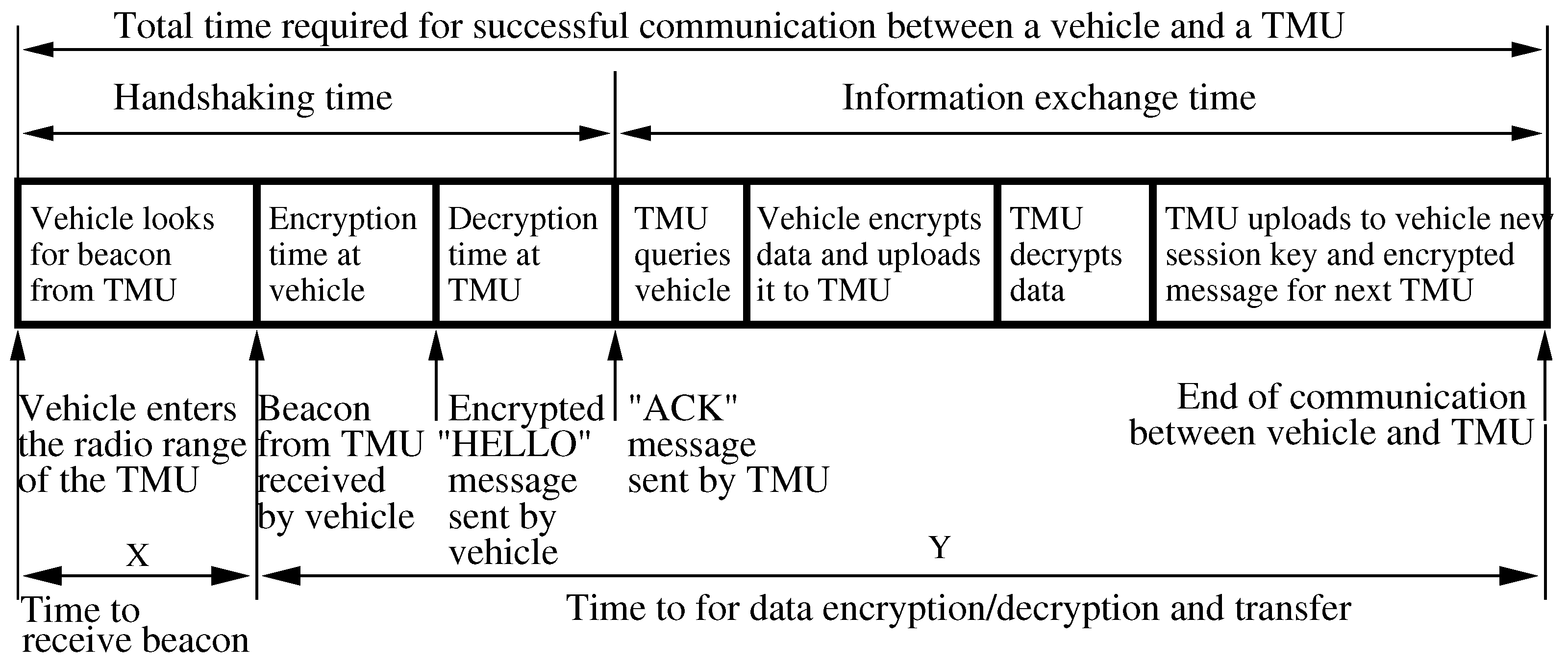
4.3. Secure Vehicle to TMU Communication
- encrypted with the one-time key , or else
- Only if the vehicle is “new” and does not have a session key .
- First, dropping off its EDR data along with encrypted data from the previous TMU;
- Second, downloading any notification and warning messages that the TMU has available.
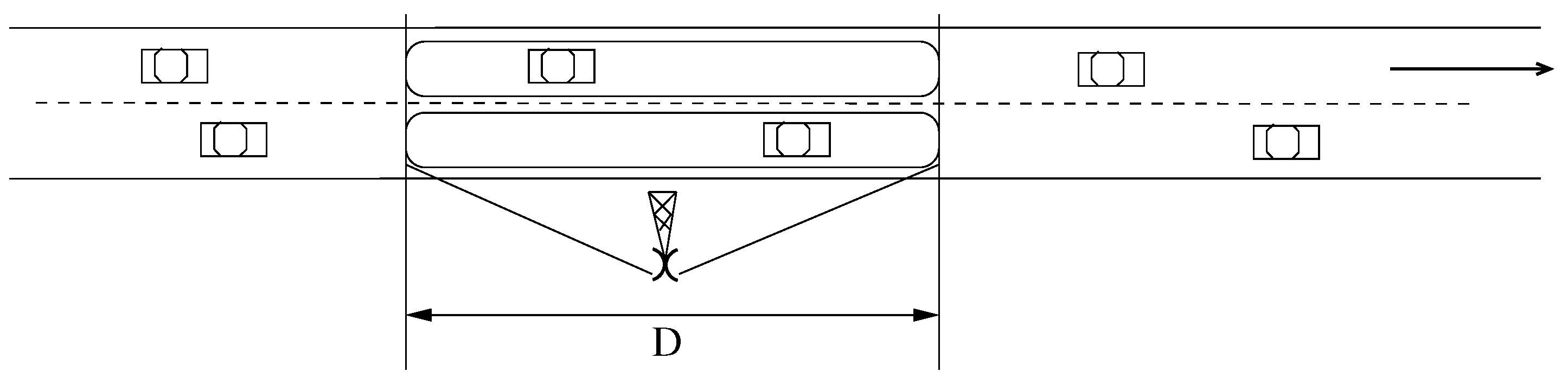
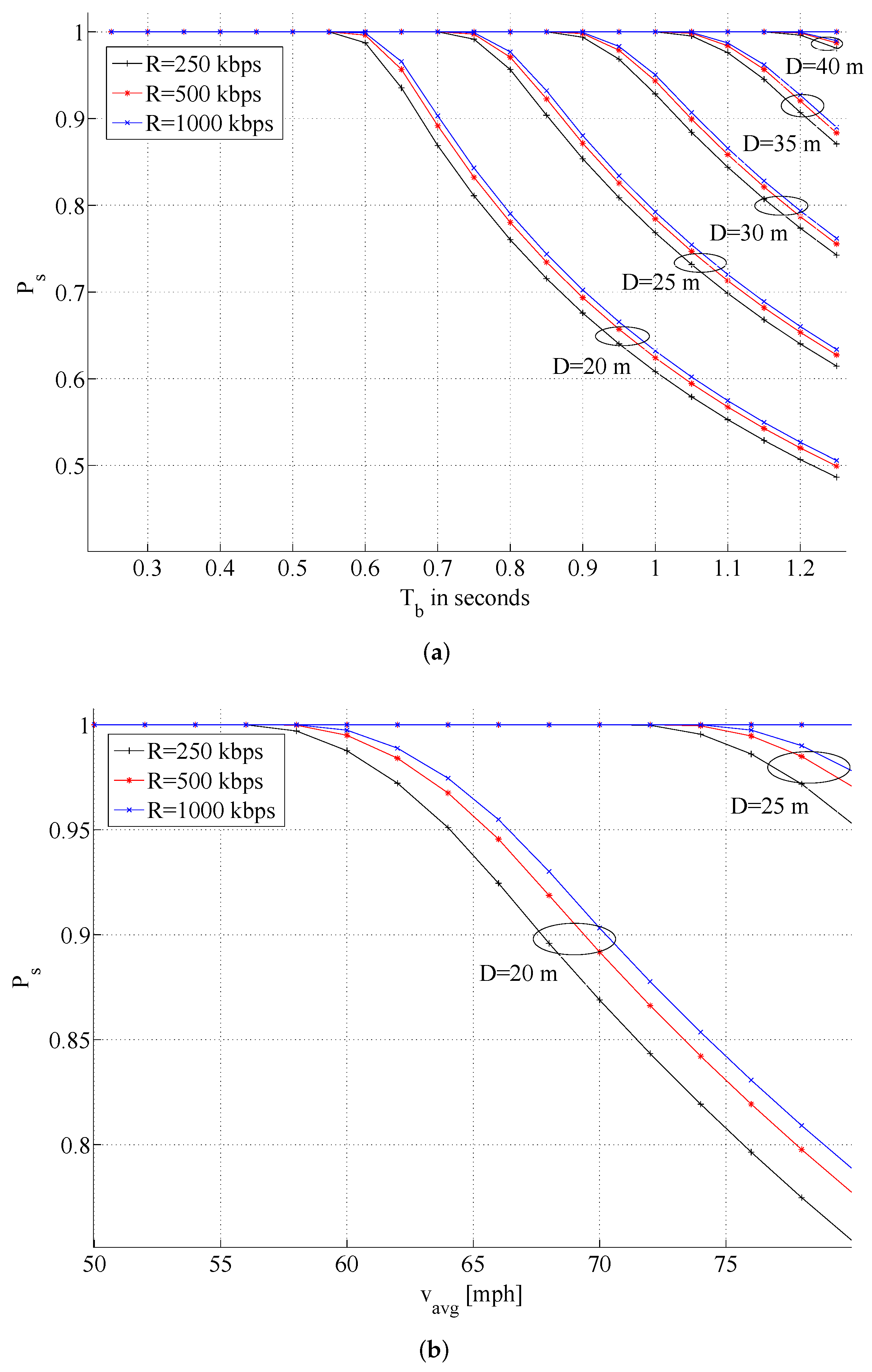
4.4. Reasoning about the TMU Coverage Area
4.5. Role-Based Vehicle to TMU Communications
4.6. Enabling Probabilistic Data Collection
4.7. Implementing Security Solutions in SEE-TREND
4.8. Making SEE-TREND Fault-Tolerant
5. Enabling Efficient Traffic-Related Information Dissemination in SEE-TREND
5.1. Non Time-Critical Information Dissemination
5.2. Time-Critical Information Dissemination
5.3. Enabling Role-Based Information Dissemination
5.4. Supporting Information Dissemination in Planned Evacuations and Emergencies
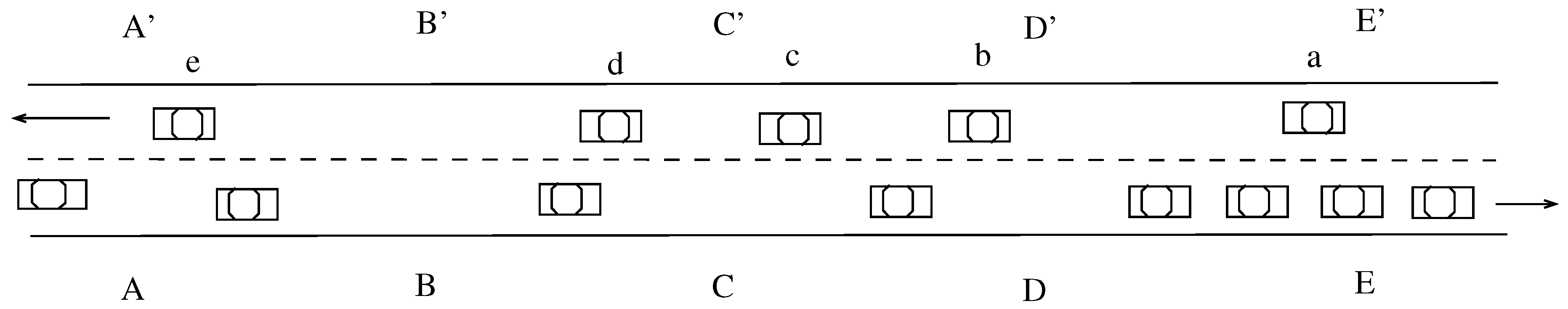
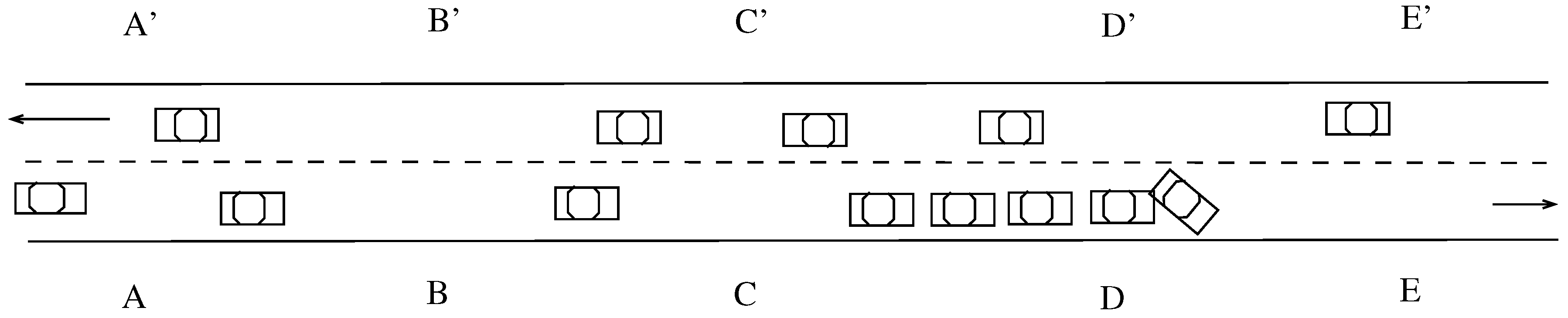
6. A Case Study: Pothole Detection
- If x’s EDR has a record for a suspected road section at location , then we need to compute the a posteriori probability of having an actual road condition at this location, update our beliefs, aswhere is computed as before. The term is industry–dependent and reflects how the probability of successfully detecting a road condition given that one actually exists.
- If x’s EDR shows that x has significantly decelerated around location p, , this means that there might be a pothole at location p that the driver wanted to avoid or reduce its effect on their vehicle.where is computed as described before. The term represents the probability that a driver slows down when he sees a pothole. This depends on many factors including driver response.
- If x’s EDR shows nothing about p, then either p is clear or x’s driver avoided the pothole.
- First, we recompute the a posteriori probability of having a temporary incident at p that forced x to change lanes as , where is the probability of changing lanes at location y given an incident at location j and can be computed as above;
- Furthermore, x may have changed lanes at p; we compute the a posteriori probability of having a pothole based on this new evidence: , , where is the probability of changing lanes at location y given a pothole at location j and can be computed as above.
- for some threshold T, infer the presence of a pothole at location . The larger the value of the threshold T, the more conservative the TMU is;
- and , then infer the presence of a temporary incident at location where is the initial belief of having a temporary incident.
7. Concluding Remarks and Challenges Ahead
- First, our goal is to build a distributed system that detects existing traffic conditions and anticipates discernible trends in highway traffic flow. This allows our system to predict traffic events and to alert interested parties to their likely occurrence;
- Second, we will intelligently disseminate relevant traffic-related information using a decay model of the value of information based on time and distance;
- Third, SEE-TREND is a secure, privacy-aware, and non-intrusive system.
- Emergency vehicle preemption is one of the well-known causes of congestion. It is important to extend role-based interaction between emergency vehicles and SEE-TREND, while limiting the impact on traffic flow;
- Yet another intriguing question is: What is the most efficient way to manage contraflow, while reserving one incoming lane for ambulances, fire trucks, and the like?
- What are the tradeoffs between TMU energy and the quality of collected data in a planned evacuation?
- Fault tolerance is a key issue in emergencies and planned evacuations. We will investigate ways in which fault tolerance will be increased in support of such events.
Author Contributions
Funding
Institutional Review Board Statement
Informed Consent Statement
Acknowledgments
Conflicts of Interest
References
- Gates, B. The Road Ahead; Viking Penguin: New York, NY, USA, 1995. [Google Scholar]
- National Academies of Sciences, Engineering, and Medicine. Information Technology and the U.S. Workforce: Where Are We and Where Do We Go from Here? National Academies Press: Washington, DC, USA, 2017. [Google Scholar]
- United Nations. World Urbanization Prospects: The 2014 Revision, Highlights. Department of Economic and Social Affairs; Population Division, United Nations: New York, NY, USA, 2014. [Google Scholar]
- Harrison, C.; Donnelly, I.A. The theory of smart cities. In Proceedings of the 55th Annual Meeting of the International Society for the Systems Sciences (ISSS’2011), Hull, UK, 17–22 July 2011. [Google Scholar]
- Hatch, D. Singapore Strives to Become the Smartest City is Using Data to Redefine What it Means to Be a 21st-Century Metropolis. 2013. Available online: https://drjdbij2merew.cloudfront.net/GOV/GOV_Mag_Feb13.pdf (accessed on 11 October 2021).
- Lakakis, K.; Kyriakou, K. Creating and intelligent transportation system for smart cities: Performance evaluation of spatial-temporal algorithms for traffic prediction. In Proceedings of the 14th International Conference on Environmental Science and Technology, Rhodes, Greece, 3–5 September 2015. [Google Scholar]
- Litman, T. Autonomous vehicle implementation predictions: Implications for transport planning. In Proceedings of the 2015 Transportation Research Board Annual Meeting, Washington, DC, USA, 11–15 January 2015. [Google Scholar]
- Townsend, A.M. Smart Cities: Big Data, Civic Hackers, and the Quest for a New Utopia; W. W. Norton: New York, NY, USA, 2013. [Google Scholar]
- Iqbal, A.; Olariu, S. A survey of enabling technologies for smart communities. Smart Cities 2021, 4, 54–77. [Google Scholar] [CrossRef]
- European Commission. Analysis of the Value of New Generation of eGovernment Services and How Can the Public Sector Become an Agent of Innovation through ICT; Publications Office of the European Union: Luxemburg, 2016. [Google Scholar] [CrossRef]
- Johansson, D.; Lassinantti, J.; Wiberg, M. Mobile e-Services and Open Data in e-Government Processes—Concept and Design. In Proceedings of the 12th International Conference on Mobile Web and Intelligent Information Systems, MobiWis’2015, Rome, Italy, 24–26 August 2015; pp. 149–160. [Google Scholar]
- Johansson, D.; Lassinantti, J.; Wiberg, M. Mobile e-Services and Open Data in e-Government Processes—Transforming Citizen Involvement. In Proceedings of the 17th ACM International Conference on Information Integration and Web-Based Applications and Services, iiWAS’2015, Brussels, Belgium, 11–13 December 2015. [Google Scholar]
- Shiroishi, Y.; Uchiyama, K.; Suzuki, N. Society 5.0: For Human Security and Well-Being. IEEE Comput. 2018, 51, 91–95. [Google Scholar] [CrossRef]
- Eltoweissy, M.; Azab, M.; Olariu, S.; Gracanin, D. A new paradigm for a marketplace of services: Smart communities in the IoT era. In Proceedings of the International Conference on Innovation and Intelligence for Informatics, Computing, and Technologies (3ICT’2019), Sakhier, Bahrain, 22–23 September 2019; pp. 173–186. [Google Scholar]
- Olariu, S. A survey of vehicular cloud computing: Trends, applications, and challenges. IEEE Trans. Intell. Transp. Syst. 2020, 21, 2648–2663. [Google Scholar] [CrossRef]
- National Research Council. Computational Technology for Effective Health Care: Immediate Steps and Strategic Directions; National Academies Press: Washington, DC, USA, 2009. [Google Scholar]
- Zhao, W.; Luo, X.; Qiu, T. Smart Healthcare. Appl. Sci. 2017, 7, 1176. [Google Scholar] [CrossRef]
- Cicirelli, F.; Fortino, G.; Giordano, A.; Guerrieri, A.; Spezzano, G.; Vinci, A. On the design of smart homes: A framework for activity recognition in home environment. J. Med. Syst. 2016, 40, 1–17. [Google Scholar] [CrossRef]
- Curzon, J.; Almehmadi, A.; El-Khatib, K. A survey of privacy enhancing technologies for smart cities. Pervasive Mob. Comput. 2019, 55, 76–95. [Google Scholar] [CrossRef]
- Faria, R.; Brito, L.; Baras, K.; Silva, J. Smart mobility: A survey. In Proceedings of the IEEE International Conference on Internet of Things for the Global Community, (IoTGC’2017), Funchal, Portugal, 10–13 July 2017. [Google Scholar]
- USDOT. The Smart/Connected City and its Implications for Connected Transportation. 2014. Available online: https://www.its.dot.gov/itspac/Dec2014/Smart_Connected_City_FINAL_111314.pdf (accessed on 11 October 2021).
- NHTSA National Highway Traffic Safety Administration. Traffic Safety Facts—Pedestrians—DOT-HS-812-375. 2017. Available online: https://www.nhtsa.gov/road-safety/pedestrian-safety/2015PedestriansTrafficSafetyFactSheet.pdf (accessed on 11 October 2021).
- NHTSA National Highway Traffic Safety Administration. Traffic Safety Facts—Children—DOT-HS-812-491. 2018. Available online: https://crashstats.nhtsa.dot.gov/Api/Public/ViewPublication/812491 (accessed on 11 October 2021).
- Zhao, W.; Lun, R.; Gordon, C.; Fofana, B.M.; Espy, D.D.; Reinthal, M.A.; Ekelman, B.; Goodman, G.D.; Niederriter, J.E.; Luo, X. A human-centered activity tracking system: Toward a healthier workplace. IEEE Trans. Hum.-Mach. Syst. 2017, 47, 343–355. [Google Scholar] [CrossRef]
- Maglio, P.; Spohrer, J. Fundamentals of service science. J. Acad. Mark. Sci. 2008, 36, 18–20. [Google Scholar] [CrossRef]
- Spohrer, J.; Maglio, P.; Bailey, J.; Gruhl, D. Toward a science of service systems. IEEE Comput. 2007, 40, 71–77. [Google Scholar] [CrossRef]
- Maglio, P.; Vargo, S.; Caswell, N.; Spohrer, J. The service system is the basic abstraction of service science. Inf. Syst. E-Bus. Manag. 2009, 7, 395–406. [Google Scholar] [CrossRef]
- Olariu, S.; Eltoweissy, M.; Younis, M. ANSWER: AutoNomouS netWorked sEnsoR system. J. Parallel Distrib. Comput. 2007, 67, 111–124. [Google Scholar] [CrossRef]
- Olariu, S. Vehicular Crowdsourcing for Congestion Support in Smart Cities. Smart Cities 2021, 4, 662–685. [Google Scholar] [CrossRef]
- U.S. National Science Foundation. Smart and Connected Communities. 2019. Available online: https://www.nsf.gov/publications/pub_summ.jsp?ods_key=nsf18520 (accessed on 11 October 2021).
- Herrmann, A.; Liu, M.; Pilla, F.; Shorten, R. A new take on protecting cyclists in smart cities. IEEE Trans. Intell. Transp. Syst. 2018, 19, 3992–3999. [Google Scholar] [CrossRef]
- NHTSA National Highway Traffic Safety Administration. Pedestrian and Bicyclists Safety. 2019. Available online: https://www.nhtsa.gov/sites/nhtsa.dot.gov/files/documents/14046-pedestrian_bicyclist_safety_resources_030519_v2_tag.pdf (accessed on 11 October 2021).
- Aljohani, M.; Olariu, S.; Alali, A.; Jain, S. A survey of parking solutions in Smart Cities. IEEE Trans. Intell. Transp. Syst. 2021, 20, 1–18. [Google Scholar] [CrossRef]
- Ranjini, R.; Manivannan, D. A comparative review on car parking technologies. Int. J. Eng. Technol. 2013, 5, 1763–1767. [Google Scholar]
- NHTSA National Highway Traffic Safety Administration. Traffic Safety Facts Annual Report Tables. 2019. Available online: https://cdan.nhtsa.gov/tsftables/Introduction.pdf (accessed on 11 October 2021).
- NHTSA National Highway Traffic Safety Administration. Traffic Safety Facts. 2019. Available online: https://crashstats.nhtsa.dot.gov/Api/Public/ViewPublication/813206 (accessed on 11 October 2021).
- Texas Transportation Institute. 2021 Urban Mobility Report. 2021. Available online: https://static.tti.tamu.edu/tti.tamu.edu/documents/mobility-report-2021.pdf (accessed on 11 October 2021).
- USDOT. 2015-2019 Strategic Plan Intelligent Transportation Systems (ITS). 2015. Available online: http://www.its.dot.gov/strategicplan.pdf (accessed on 11 October 2021).
- California Partners for Advanced Transit and Highways. PATH. Available online: www-path.eecs.berkeley.edu (accessed on 11 October 2021).
- NHTSA National Highway Traffic Safety Administration. Early Estimate of Motor Vehicle Traffic Fatalities for the First Half of 2021. DOT HS 813 199. 2021. Available online: https://crashstats.nhtsa.dot.gov/Api/Public/ViewPublication/813199 (accessed on 11 October 2021).
- Olariu, S.; Weigle, M.C. (Eds.) Vehicular Networks: From Theory to Practice; CRC Press/Taylor & Francis: Boca Raton, FL, USA, 2009. [Google Scholar]
- Wu, X.; Michalopoulos, P.; Liu, H.X. Stochasticity of freeway operational capacity and chance-constrained ramp metering. Transp. Res. Part C 2010, 18, 741–756. [Google Scholar] [CrossRef]
- Seo, T.; Bayen, A.; Kusakabe, T.; Asakura, Y. Traffic state estimation on highway: A comprehensive survey. Annu. Rev. Control 2017, 43, 128–151. [Google Scholar] [CrossRef]
- van Erp, P.B.; Knoop, V.L.; Hoogendoorn, S.P. Macroscopic traffic state estimation using relative flows from stationary and moving observers. Transp. Res. Part B Methodol. 2018, 114, 281–299. [Google Scholar] [CrossRef]
- Olariu, S.; Mohrekesh, S.; Wang, X.; Weigle, M.C. On aggregating information in actor networks. SIGMOBILE Mob. Comput. Commun. Rev. 2014, 18, 85–96. [Google Scholar] [CrossRef]
- NHTSA National Highway Traffic Safety Administration. Event Data Recorders. Federal Motor Vehicle Safety Standards 215 Part 49, Code of Federal Regulations Part 563. 2006. Available online: https://www.nhtsa.gov/fmvss/event-data-recorders-edrs (accessed on 11 October 2021).
- NHTSA National Highway Traffic Safety Administration. 2006 Ruling. 2006. Available online: http://www.injurysciences.com/Documents/NHTSA%20Issues%20Final%20Rules%20for%20Automotive%20EDRs.pdf (accessed on 11 October 2021).
- Gabauer, D.J.; Gabler, H.C. Comparison of Roadside Crash Injury Metrics Using Event Data Recorders. 2008. Available online: http://www.sciencedirect.com/science/article/pii/S000145750700139X (accessed on 11 October 2021).
- Sapper, D.; Cusack, H.; Staes, L. Evaluation of Electronic Data Recorders for Incident Investigation, Driver Performance, and Vehicle Maintenance: Final Report; US-DOT, Office of Research: Washington, DC, USA, 2009. [Google Scholar]
- Comes, C. Clear Shows Off WiMAX Capabilities at Chicago Auto Show. WiMAX.com. 2010. Available online: http://bit.ly/974xmY (accessed on 11 October 2021).
- Reardon, M. Chrysler Takes Wi-Fi on the Road. cNet News. 2008. Available online: http://news.cnet.com/8301-10784_3-9978037-7.html (accessed on 11 October 2021).
- Gruener, W. Chrysler to Put WiMax into its Cars. TG Daily. 2008. Available online: http://www.tgdaily.com/mobility-features/35601-chrysler-to-put-wimax-into-its-cars (accessed on 11 October 2021).
- Car2Car Consortium. Car-2-Car. Available online: www.car-2-car.de (accessed on 11 October 2021).
- Hull, B.; Bychkovsky, V.; Zhang, Y.; Chen, K.; Goraczko, M. CarTel: A Distributed Mobile Sensor Computing System. In Proceedings of the ACM SenSys, Boulder, CO, USA, 31 October 2006; Association for Computing Machinery: New York, NY, USA, 2006. [Google Scholar]
- USDOT. Connected Vehicles. 2017. Available online: https://www.its.dot.gov/research_areas/connected_vehicle.htm (accessed on 11 October 2021).
- US Department of Transporation. Analysis. Modeling, and Simulation for Traffic Incident Management Applications; Technical Report FHWA-HOP-12-045; Federal Highway Administration: Washington, DC, USA, 2012. [Google Scholar]
- Florin, R.; Olariu, S. On a Variant of the Mobile Observer Method. IEEE Trans. Intell. Transp. Syst. 2017, 18, 441–449. [Google Scholar] [CrossRef]
- Florin, R.; Olariu, S. Towards real-time density estimation using vehicle-to-vehicle communications. Transp. Res. Part B Methodol. 2020, 138, 435–456. [Google Scholar] [CrossRef]
- Popescu, O.; Sarwar, S.M.; Popescu, D.C.; El-Tawab, S.; Abdel-Wahab, M. Automatic Incident Detection in Based on V2I Communication and Aggregation of Traffic Parameters. IEEE Intell. Syst. Mag. 2017, 9, 64–75. [Google Scholar]
- Ishihara, S.; Nakamura, N.; Niimi, Y. Demand-based location-dependent data dissemination in VANETs. In Proceedings of the ACM Mobicom, Miami, FL, USA, 30 September 2013; Association for Computing Machinery: New York, NY, USA, 2013; pp. 219–221. [Google Scholar]
- Luan, T.; Shen, S.; Bai, F. Integrity-Oriented Content Transmission in Highway Vehicular Ad Hoc Networks. In Proceedings of the IEEE INFOCOM, Turin, Italy, 14–19 April 2013; Institute of Electrical and Electronics Engineers: Piscataway, NJ, USA, 2013. [Google Scholar]
- Park, M.; Gwon, G.; Seo, S.W.; Jeong, H.Y. RSU-Based Distributed Key Management (RDKM) for Secure Vehicular Multicast Communications. IEEE J. Sel. Areas Commun. 2011, 29, 644–658. [Google Scholar] [CrossRef]
- Zhou, T.; Sharif, H.; Hempel, M.; Mahasukhon, P.; Wang, W.; Ma, T. A Novel Adaptive Distributed Cooperative Relaying MAC Protocol for Vehicular Networks. IEEE J. Sel. Areas Commun. 2011, 29, 72–82. [Google Scholar] [CrossRef]
- Yan, G.; Wen, D.; Olariu, S.; Weigle, M.C. Security challenges in vehicular cloud computing. IEEE Trans. Intell. Transp. Syst. 2013, 4, 6–16. [Google Scholar] [CrossRef]
- Yan, G.; Olariu, S.; Wang, J.; Arif, S. Towards providing scalable and robust privacy in vehicular networks. IEEE Trans. Parallel Distrib. Syst. 2014, 25, 1895–1906. [Google Scholar]
- Calandriello, G.; Papadimitratos, P.; Hubaux, J.P.; Lioy, A. Efficient and robust pseudonymous authentication in VANET. In VANET ’07: Proceedings of the Fourth ACM International Workshop on Vehicular Ad Hoc Networks; ACM: New York, NY, USA, 2007; pp. 19–28. [Google Scholar]
- Xie, H.; Kulik, L.; Tanin, E. Privacy-Aware Traffic Monitoring. IEEE Trans. Intell. Transp. Syst. 2010, 11, 61–70. [Google Scholar]
- Bai, F.; Chen, W.; Letaief, K.B.; Cao, Z. Low Complexity Outage Optimal Distributed Channel Allocation for Vehicle-to-Vehicle Communications. IEEE J. Sel. Areas Commun. 2011, 29, 161–170. [Google Scholar] [CrossRef]
- Nzounta, J.; Rajgure, N.; Wang, G.; Borcea, C. VANET Routing on city roads using real-time vehicular traffic information. IEEE Trans. Veh. Technol. 2009, 58, 3609–3626. [Google Scholar] [CrossRef]
- Roess, R.P.; Prassas, E.S.; McShane, W.R. Traffic Engineering, 4th ed.; Pearson Prentice Hall: Prentice-Hall, NJ, USA, 2011. [Google Scholar]
- Saad, W.; Han, Z.; Hjørungnes, A.; Niyato, D.; Hossain, E. Coalition Formation Games for Distributed Cooperation Among Roadside Units in Vehicular Networks. IEEE J. Sel. Areas Commun. 2011, 29, 48–60. [Google Scholar] [CrossRef]
- US Federal Highway Administration. Traffic Incident Management Handbook. 2000. Available online: http://www.itsdocs.fhwa.dot.gov/JPODOCS/REPT_MIS/13286.pdf (accessed on 11 October 2021).
- Chung, J.M.; Kim, M.; Park, Y.S.; Choi, M.; Lee, S.; Oh, H.S. Time Coordinated V2I Communications and Handover for WAVE Networks. IEEE J. Sel. Areas Commun. 2011, 29, 545–558. [Google Scholar] [CrossRef]
- Daganzo, C.F. Fundamentals of Transportation and Traffic Operations; Elsevier: New York, NY, USA, 1997. [Google Scholar]
- May, A.D. Traffic Flow Fundamentals; Prentice Hall: Hoboken, NJ, USA, 1990. [Google Scholar]
- de Dios Ortúzar, J.; Willumsen, L.G. Modelling Transport; Wiley: Hoboken, NJ, USA, 2002. [Google Scholar]
- Sreedevi, I.; Black, J. Loop Detectors. California Center for Innovative Transportation. 2001. Available online: http://www.calccit.org/itsdecision/serv_and_tech/Traffic_Surveillance/road-based/in-road/loop_report.html (accessed on 11 October 2021).
- Fontaine, M. Traffic Monitoring. In Vehicular Networks, from Theory to Practice; Olariu, S., Weigle, M., Eds.; CRC Press: Boca Raton, FL, USA, 2009; pp. 1.1–1.28. [Google Scholar]
- V-DOT Virginia Department of Transportation. Virginia Smart Road. Available online: http://www.virginiadot.org/projects/constsal-smartrd.asp (accessed on 11 October 2021).
- 511 Traffic. Latest Traffic News. Available online: http://traffic.511.org/LatestNews (accessed on 11 October 2021).
- NHTSA National Highway Traffic Safety Administration. An Analysis of Recent Improvements to Vehicle Safety. 2012. Available online: http://www-nrd.nhtsa.dot.gov/Pubs/811572.pdf (accessed on 11 October 2021).
- Bayen, A.; Butler, J.; Patire, A. Mobile Millenium Final Report; Technical Report UCB-ITS-CWP-2011-6; California Center for Innovative Transportation: Berkeley, CA, USA, 2011. [Google Scholar]
- Hofleitner, A.; Herring, R.; Abbeel, P.; Bayen, A. Learning the Dynamics of Arterial Traffic from Probe Data Using Dynamic Bayesian Network. IEEE Trans. Intell. Transp. Syst. 2012, 13, 1679–1693. [Google Scholar] [CrossRef]
- Nakano, K.; Olariu, S.; Schwing, J.L. Broadcast-efficient protocols for mobile radio networks. IEEE Trans. Parallel Distrib. Syst. 1999, 10, 1276–1289. [Google Scholar] [CrossRef]
- Daniel, A.; Popescu, D.C.; Olariu, S. A Study of Beaconing Mechanism for Vehicle-to-Infrastructure Communications. In Proceedings of the IEEE ICC 2012 Workshop on Intelligent Vehicular Networking: V2V/V2I Communications and Applications—WIVN 2012, Ottawa, ON, Canada, 10–15 June 2012; pp. 8736–8740. [Google Scholar]
- Qutaiba, I. Design, Implementation and Optimisation of an Energy Harvesting System for Vehicular Ad-Hoc Networks’ Road Side Units. IET Intell. Transp. Syst. 2014, 8, 298–307. [Google Scholar]
- Del Corso, D.; Passerone, C.; Reyneri, L.; Sansoe, C.; Speretta, S.; Tranchero, M. Design of a University Nano-Satellite: The PiCPoT Case. IEEE Trans. Aerosp. Distrib. Syst. 2011, 47, 1985–2007. [Google Scholar] [CrossRef]
- Crimmins, D.M.; Patty, C.T.; Beliard, M.A.; Baker, J.; Jalbert, J.C.; Komerska, R.J.; Chappell, S.G.; Blidberg, D.R. Long-Endurance Test Results of the Solar-Powered AUV System. In Proceedings of the OCEANS 2006, Boston, MA, USA, 18–21 September 2006. [Google Scholar]
- Reddy, T.B.; Linden, D. Linden’s Handbook of Batteries, 4th ed.; McGraw-Hill: New York, NY, USA, 2011. [Google Scholar]
- Boxwell, M. The Solar Electricity Handbook; Code Green Publishing: Warwickshire, UK, 2010. [Google Scholar]
- Kenney, J.B. Dedicated Short-range Communications (DSRC) Standards in the United States. Proc. IEEE 2011, 99, 1162–1182. [Google Scholar] [CrossRef]
- Tsai, H.M.; Tonguz, O.K.; Saraydar, C.; Talty, T.; Ames, M.; Macdonald, A. ZigBee-based intra-car wireless sensor networks: A case study. IEEE Wirel. Commun. 2007, 14, 67–77. [Google Scholar] [CrossRef]
- Sha-Mohammad, S.A.; Abdel-Wahab, H.A.; Popescu, D.C. A study of IEEE 802.11 standard for use in vehicle to infrastructure communication. In Proceedings of the IEEE Globecom, Atlanta, GA, USA, 9–13 December 2013. [Google Scholar]
- Tufail, A.; Fraser, M.; Hammad, A.; Hyung, K.K.; Yoo, S.W. An Empirical Study to Analyze the Feasibility of WIFI for VANET. In Proceedings of the 12th International Conference on Computer Supported Cooperative Work in Design—CSCWD’08, Xi’an, China, 16–18 April 2008; pp. 553–558. [Google Scholar]
- Lee, J.S.; Su, Y.W.; Shen, C.C. A Comparative Study of Wireless Protocols: Bluetooth, UWB, ZigBee, and Wi-Fi. In Proceedings of the 33rd Annual IEEE Conference on Industrial Electronics Society—IECON’07, Taipei, Taiwan, 5–8 November 2007; pp. 46–51. [Google Scholar]
- Wheeler, A. Commercial applications of wireless sensor networks using ZigBee. IEEE Commun. Mag. 2007, 45, 70–77. [Google Scholar] [CrossRef]
- Weigle, M.C.; Olariu, S. Intelligent Highway Infrastructure for Planned Evacuations. In Proceedings of the 1st International Workshop on Research Challenges in Next Generation Networks for First Responders and Critical Infrastructures (NetCri), New Orleans, LA, USA, 11–13 April 2007; pp. 594–599. [Google Scholar]
- Barria, J.A.; Thajchayapong, S. Detection and classification of traffic anomalies using microscopic traffic variables. IEEE Trans. Intell. Transp. Syst. 2011, 12, 695–704. [Google Scholar] [CrossRef]
- El-Tawab, S.; Alhafdhi, A.; Treeumnuk, D.; Popescu, D.; Olariu, S. Physical layer aspects of information exchange in the NOTICE architecture. IEEE Intell. Transp. Syst. 2015, 7, 8–18. [Google Scholar] [CrossRef]
- Feller, W. An Introduction to Probability Theory and Its Applications, 1st ed.; John Wiley and Sons: Hoboken, NJ, USA, 1960; Volume I. [Google Scholar]
- Harden, B.; Moreno, S. Thousands Fleeing Rita Jam Roads From Coast; Washington Post: Washington, DC, USA, 2005. [Google Scholar]
- Feldstein, D.; Stiles, M. Too Many People and No Way Out; Houston Chronicle: Houston, TX, USA, 2005. [Google Scholar]
- US Department of Transportation. Catastrophic Hurricane Evacuation Plan Evaluation: A Report to Congress. 2006. Available online: http://www.fhwa.dot.gov/reports/hurricanevacuation/ (accessed on 11 October 2021).
- US Department of Transporation. Intelligent Transportation Systems for Planned Special Events: A Cross-Cutting Study; Technical Report FHWA-JPO-08-056; Federal Highway Administration: Washington, DC, USA, 2008.
- Ahmed, S.; Cook, A. Application of time-series analysis techniques to freeway incident detection. Transp. Res. Rec. 1982, 841, 19–21. [Google Scholar]
- Levin, M.; Krause, G.M. Incident detection algorithms. Transp. Res. Rec. 1989, 722, 49–64. [Google Scholar]
- Michalopoulos, P. Automatic incident detection through video image processing. Traffic Eng. Control 1993, 34, 66–75. [Google Scholar]
- Persaud, B.; Hall, F.; Hall, L. Congestion identification aspects of the McMaster incident detection algorithm. Transp. Res. Rec. 1990, 1287, 167–175. [Google Scholar]
- Stephanedes, Y.; Chassiakos, A. Freeway incident detection through filtering. Transp. Res. 1993, 1C, 219–233. [Google Scholar] [CrossRef]
- Besag, J. On the Statistical Analysis of Dirty Pictures. J. R. Stat. Society. Ser. B Methodol. 1986, 48, 259–302. [Google Scholar] [CrossRef]
- Florin, R.; Syedmeysam, A.; Ghazizadeh, A.; Olariu, S. Big Data in the Parking Lot. In Big Data Management and Processing; Li, K.C., Jiang, H., Zomaya, A.Y., Eds.; Taylor and Francis: Boca Raton, FL, USA, 2017; pp. 425–450. [Google Scholar]
- Zomaya, A.; Clements, M.; Olariu, S. A framework for reinforcement-based scheduling in parallel processor systems. IEEE Trans. Parallel Distrib. Syst. 1998, 9, 249–260. [Google Scholar] [CrossRef][Green Version]
- Olariu, S.; Schwing, J.L.; Zhang, J. Fundamental algorithms on reconfigurable meshes. In Proceedings of the 29th Allerton Conference on Communications, Control and Computing, Monticello, IL, USA, 27–29 September 1991; pp. 811–820. [Google Scholar]
- Olariu, S.; Schwing, J.L.; Jingyuan, Z. Fast computer vision algorithms for reconfigurable meshes. Image Vis. Comput. 1992, 10, 610–616. [Google Scholar] [CrossRef]
- Olariu, S.; Schwing, J.L.; Zhang, J. Optimal parallel algorithms for problems modeled by a family of intervals. IEEE Trans. Parallel Distrib. Syst. 1992, 3, 364–374. [Google Scholar] [CrossRef]
- Olariu, S.; Schwing, J.L. A novel deterministic sampling sheme with applications to broadcast-efficient sorting on the reconfigurable mesh. J. Parallel Distrib. Comput. 1996, 32, 215–222. [Google Scholar] [CrossRef]
- Hennessy, J.L.; Patterson, D.A. Computer Architecture a Quantitative Approach, 6th ed.; Morgan Kaufman: Burlington, MA, USA, 2019. [Google Scholar]
- Bhagavathi, D.; Looges, P.J.; Olariu, S.; Schwing, J.L. A fast selection algorithms on meshes with multiple broadcasting. IEEE Trans. Parallel Distrib. Syst. 1994, 5, 772–778. [Google Scholar] [CrossRef]
- Lin, R.; Olariu, S.; Schwing, J.L.; Zhang, J. Sorting in O(1) time on a reconfigurable meshe of size N × N. In Proceedings of the EWPC’92, Parallel Computing: From Theory to Sound Practice, Barcelona, Spain, 23–24 March 1992; pp. 16–27. [Google Scholar]
- Lin, R.; Olariu, S. Reconfigurable buses with shift switching: Concepts and applications. IEEE Trans. Parallel Distrib. Syst. 1995, 6, 93–102. [Google Scholar] [CrossRef]
- Nakano, K.; Olariu, S. A survey on leader election protocols for radio networks. In Proceedings of the International Symposium on Parallel Architectures, Algorithms and Networks, I-SPAN’02, Makati City, Philippines, 22–24 May 2002; pp. 71–76. [Google Scholar]

| Acronym | Description |
|---|---|
| AID | Automated Incident Detection |
| CPS | Cyber Physical System |
| DEM | Distributed Expectation Maximization |
| DSRC | Dedicated Short-Range Communications |
| EDR | Event Data Recorder |
| GPS | Global Positioning System |
| ICT | Information and Communications Technology |
| ILD | Inductive Loop Detector |
| ITS | Intelligent Transportation Systems |
| MANET | Mobile Ad hoc Networks |
| NHTSA | National Highway Traffic Safety Administration |
| PATH | California Partners for Advanced Transit and Highways |
| TMC | Traffic Monitoring Centers |
| TMU | Traffic Monitoring Unit |
| US-DOT | United States Department of Transportation |
| VANET | Vehicular Ad hoc Networks |
| V2I | Vehicle-to-Infrastructure |
| V2V | Vehicle-to-Vehicle |
Publisher’s Note: MDPI stays neutral with regard to jurisdictional claims in published maps and institutional affiliations. |
© 2021 by the authors. Licensee MDPI, Basel, Switzerland. This article is an open access article distributed under the terms and conditions of the Creative Commons Attribution (CC BY) license (https://creativecommons.org/licenses/by/4.0/).
Share and Cite
Olariu, S.; Popescu, D.C. SEE-TREND: SEcurE Traffic-Related EveNt Detection in Smart Communities. Sensors 2021, 21, 7652. https://doi.org/10.3390/s21227652
Olariu S, Popescu DC. SEE-TREND: SEcurE Traffic-Related EveNt Detection in Smart Communities. Sensors. 2021; 21(22):7652. https://doi.org/10.3390/s21227652
Chicago/Turabian StyleOlariu, Stephan, and Dimitrie C. Popescu. 2021. "SEE-TREND: SEcurE Traffic-Related EveNt Detection in Smart Communities" Sensors 21, no. 22: 7652. https://doi.org/10.3390/s21227652
APA StyleOlariu, S., & Popescu, D. C. (2021). SEE-TREND: SEcurE Traffic-Related EveNt Detection in Smart Communities. Sensors, 21(22), 7652. https://doi.org/10.3390/s21227652







