The Impact of Artificial Intelligence on Data System Security: A Literature Review
Abstract
:1. Introduction
2. Literature Trends: AI and Systems Security
- (I)
- Machine learning is a myriad of technologies that allow computers to carry out algorithms based on gathered data and distinct orders, providing the machine the capabilities to learn without instructions from humans, adjusting its own algorithm to the situation, while learning and recoding itself, such as Google and Siri when performing distinct tasks ordered by voice [19]. As well, video surveillance that tracks unusual behavior [20];
- (II)
- Deep learning constitutes the ensuing progress of machine learning, in which the machine carry out tasks directly from pictures, text, and sound, through a wide set of data architecture that entails numerous layers in order to learn and characterize data with several levels of abstraction imitating thus how the natural brain processes information [21]. This is illustrated, for example, in forming a certificate database structure of university performance key indicators, in order to fix issues such as identity authentication [21];
- (III)
- Neural networks are composed of a pattern recognition system that machine/deep learning operates to perform learning from observational data, figuring out its own solutions such as an auto-steering gear system with a fuzzy regulator, which enables to select optimal neural network models of the vessel paths, to obtain in this way control activity [22];
- (IV)
- Natural language processing machines analyze language and speech as it is spoken, resorting to machine learning and natural language processing, such as developing a swarm intelligence and active system, while mounting friendly human-computer interface software for users, to be implemented in educational and e-learning organizations [23];
- (V)
- Expert systems are composed of software arrangements that assist in achieving answers to distinct inquiries provided either by a customer or by another software set, in which expert knowledge is set aside in a particular area of the application that includes a reasoning component to access answers, in view of the environmental information and subsequent decision making [24].
- (a)
- Cyber security, in terms of computer crime, behavior research, access control, and surveillance, as for example the case of computer vision, in which an algorithmic analyses images, CAPTCHA (Completely Automated Public Turing test to tell Computers and Humans Apart) techniques [6,7,12,19,25,26,27,28,29,30,31,32,33,34,35,36,37,38];
- (b)
- Information management, namely in supporting decision making, business strategy, and expert systems, for example, by improving the quality of the relevant strategic decisions by analyzing big data, as well as in the management of the quality of complex objects [2,4,5,11,14,24,39,40,41,42,43,44,45,46,47,48,49,50,51,52,53,54,55,56,57,58,59,60];
- (c)
- Societies and institutions, regarding computer networks, privacy, and digitalization, legal and clinical assistance, for example, in terms of legal support of cyber security, digital modernization, systems to support police investigations and the efficiency of technological processes in transport [8,9,10,15,17,18,20,21,23,28,61,62,63,64,65,66,67,68,69,70,71,72,73];
- (d)
3. Materials and Methods
4. Discussion
4.1. Business Decision Making
4.2. Electronic Commerce Business
4.3. AI Social Applications
4.4. Neural Networks
4.5. Data Security and Access Control Mechanisms
5. Conclusion and Future Research Directions
Future Research Issues
Author Contributions
Funding
Institutional Review Board Statement
Informed Consent Statement
Data Availability Statement
Acknowledgments
Conflicts of Interest
Appendix A
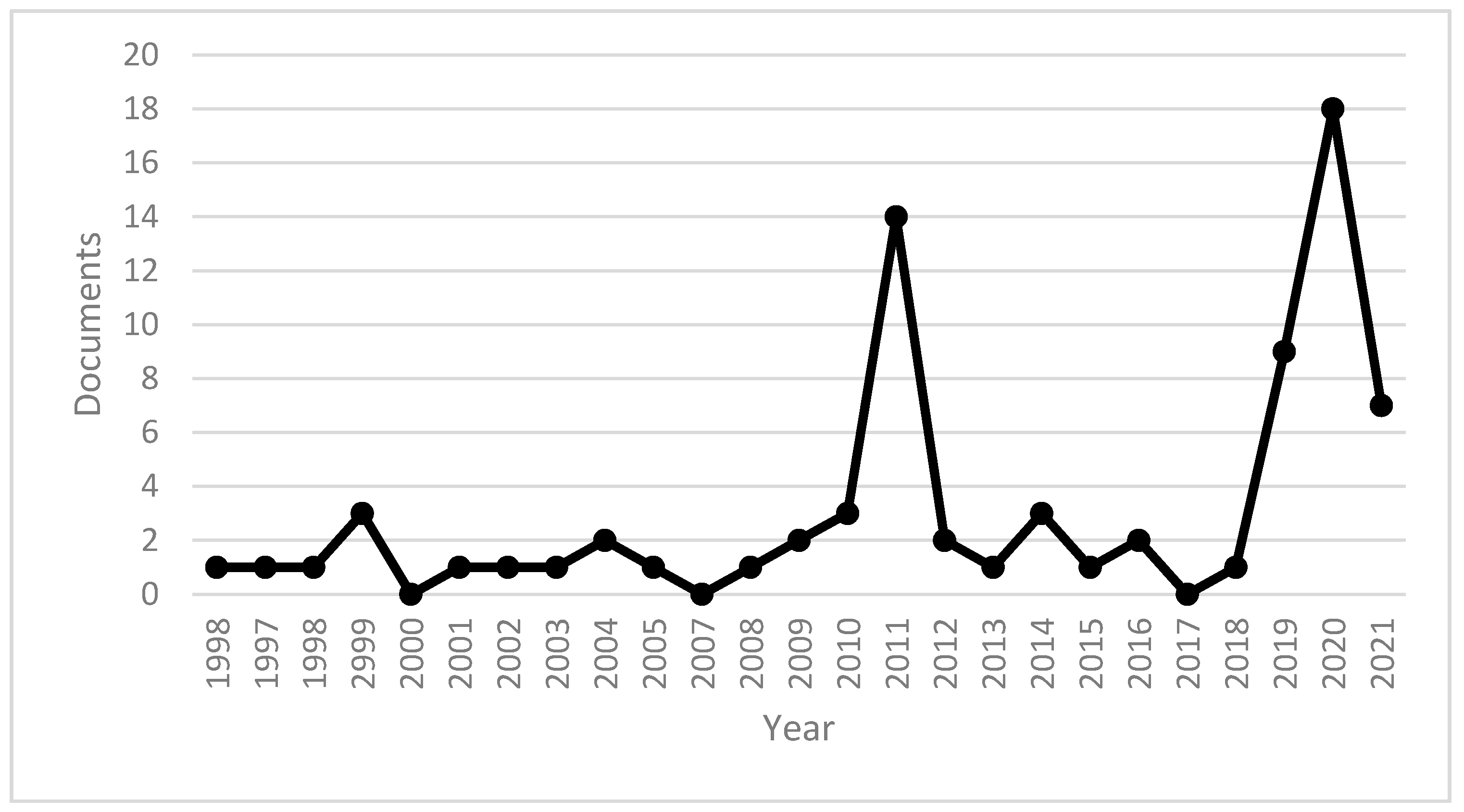
| Documents | ≤2010 | 2011 | 2012 | 2013 | 2014 | 2015 | 2016 | 2017 | 2018 | 2019 | 2020 | 2021 | Total | |
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| An lntelligent Tree-Based lntrusion Detection Model for Cybe... | 2021 | - | - | - | - | - | - | - | - | - | - | - | 1 | 1 |
| Trailblazing the Artificial lntelligence for Cybersecurity D... | 2020 | - | - | - | - | - | - | - | - | - | - | - | 1 | 1 |
| Legal Remedies for a Forgiving Society: Children’s rights, d... | 2020 | - | - | - | - | - | - | - | - | - | - | - | 1 | 1 |
| The Challenges and Opportunities in the Digitalization ofCo... | 2020 | - | - | - | - | - | - | - | - | - | - | - | 3 | 3 |
| New perspectives from technology adoption in senior cohousin... | 2020 | - | - | - | - | - | - | - | - | - | - | - | 1 | 1 |
| From Alexa to Siri and the GDPR: the gendering ofVirtual Pe... | 2020 | - | - | - | - | - | - | - | - | - | 2 | 3 | - | 5 |
| A Research on the Vulnerabilities of PLC using Search Engine | 2019 | - | - | - | - | - | - | - | - | - | 1 | - | - | 1 |
| lnformation Technology as the Basis for Transformation into... | 2019 | - | - | - | - | - | - | - | - | - | - | 4 | 3 | 7 |
| Modeling the Effectiveness of Solutions for Technogenic Safe... | 2019 | - | - | - | - | - | - | - | - | - | - | 6 | 1 | 7 |
| he Neuron Network Model ofHuman Personality for… | 2019 | - | - | - | - | - | - | - | - | - | - | 4 | 4 | |
| Regulatory alternatives for AI | 2019 | - | - | - | - | - | - | - | - | - | - | 1 | 2 | 3 |
| Malicious web domain identification using online… | 2019 | - | - | - | - | - | - | - | - | - | 2 | 5 | 3 | 10 |
| Ontology-based information security compliance… | 2018 | - | - | - | - | - | - | - | - | - | 1 | 4 | - | 5 |
| Gesture-based animated CAPTCHA | 2016 | - | - | - | - | - | - | - | - | 1 | 2 | - | 3 | |
| A case-based reasoning system for aiding detection and class... | 2016 | - | - | - | - | - | - | - | 11 | 7 | 8 | 9 | 4 | 39 |
| CANN: An intrusion detection system based on combining clust... | 2015 | - | - | - | - | - | 6 | 26 | 43 | 57 | 67 | 68 | 23 | 290 |
| Real time BIG data analytic: Security concern and challenges... | 2014 | - | - | - | - | - | - | 2 | 1 | - | 1 | 2 | - | 6 |
| Detecting and tracking of multi pie moving objects for intell... | 2014 | - | - | - | - | - | - | - | 2 | 1 | 4 | - | - | 7 |
| Application of business intelligence to the power system… | 2013 | - | - | - | - | - | - | - | - | 1 | - | - | - | 1 |
| Generating Shareable Statistical Databases for Business Valu... | 2012 | - | - | - | - | 1 | 1 | 1 | 1 | 1 | 1 | - | - | 6 |
| Study on security of electronic commerce information system | 2011 | - | - | - | - | - | - | - | - | - | - | 1 | - | 1 |
| The research on information safety problem of digital campus... | 2011 | - | - | 1 | - | - | - | - | - | - | - | - | - | 1 |
| VOIP voice network technology security strategies | 2011 | - | - | 1 | - | - | - | - | 1 | 1 | - | - | 3 | |
| Research on the Internet banking security based on dynamic p... | 2011 | - | - | - | - | - | - | - | 1 | - | - | - | - | 1 |
| Analysis of coai mine safety monitoring data based … | 2011 | - | - | - | - | - | - | - | 1 | - | - | - | - | 1 |
| The improvement of digital signature algorithm based on… | 2011 | - | - | - | - | 3 | 1 | 2 | 1 | 2 | 1 | 1 | - | 11 |
| lntelligent mobile safety system to educational organization | 2010 | - | - | - | 1 | - | - | - | - | - | - | - | - | 1 |
| A web-based multi-perspective decision support system for in... | 2010 | - | 1 | - | 3 | 6 | 5 | 1 | 2 | 2 | 4 | 1 | 1 | 27 |
| A generic analytical target cascading optimization system… | 2010 | 2 | 3 | - | 3 | 3 | 1 | 1 | 5 | 2 | 2 | 1 | - | 24 |
| A decision-theoretic approach to dynamic sensor selection in... | 2009 | 3 | 3 | 2 | 3 | 3 | 3 | 4 | 1 | 2 | 4 | 1 | - | 29 |
| Privacy issues in Aml spaces | 2009 | - | - | - | - | - | - | - | - | - | 1 | 1 | - | 2 |
| Effective information value calculation for interruption man... | 2008 | 1 | - | - | 1 | 1 | - | - | - | - | - | - | - | 3 |
| A logical architecture for active network management | 2006 | 4 | - | - | - | 2 | 1 | 1 | - | - | 1 | - | - | 9 |
| Auditing in the e-commerce era | 2004 | 10 | 2 | 5 | 3 | 3 | 1 | 4 | 2 | 3 | 2 | 1 | 36 | |
| Predictive model on the likelihood of online purchase in e-e... | 2002 | 1 | - | - | - | - | - | - | - | - | - | - | - | 1 |
| Internet commerce security: lssues and models for contrai eh... | 2001 | 2 | - | - | - | 2 | - | - | - | - | 1 | - | - | 6 |
| A survey of distributed enterprise network and systems manag... | 1999 | 42 | 2 | 2 | 2 | 1 | 3 | 1 | 1 | 2 | - | - | - | 56 |
| An open secure Mobile Agent framework for systems… | 1999 | 42 | 1 | - | 1 | 1 | - | - | - | 1 | - | 1 | - | 36 |
| MetaMorph: An adaptive agent-based architecture for intellig... | 1999 | 117 | 5 | 8 | 6 | 3 | 6 | 4 | - | 5 | 2 | 2 | - | 161 |
| AICAMS: Artificial intelligence crime analysis and managemen... | 1998 | 10 | 2 | 4 | 2 | - | - | 2 | 2 | 1 | - | 2 | 27 | |
| lmposing security constraints on agent-based decision suppor... | 1997 | 21 | - | - | - | - | 1 | 1 | 1 | 2 | - | - | 26 | |
| An empirical study ofthe use ofbusiness expert systems | 1988 | 7 | - | - | - | - | - | - | - | - | - | - | - | 7 |
| Total | 252 | 19 | 32 | 31 | 22 | 25 | 54 | 73 | 94 | 98 | 117 | 53 | 870 |
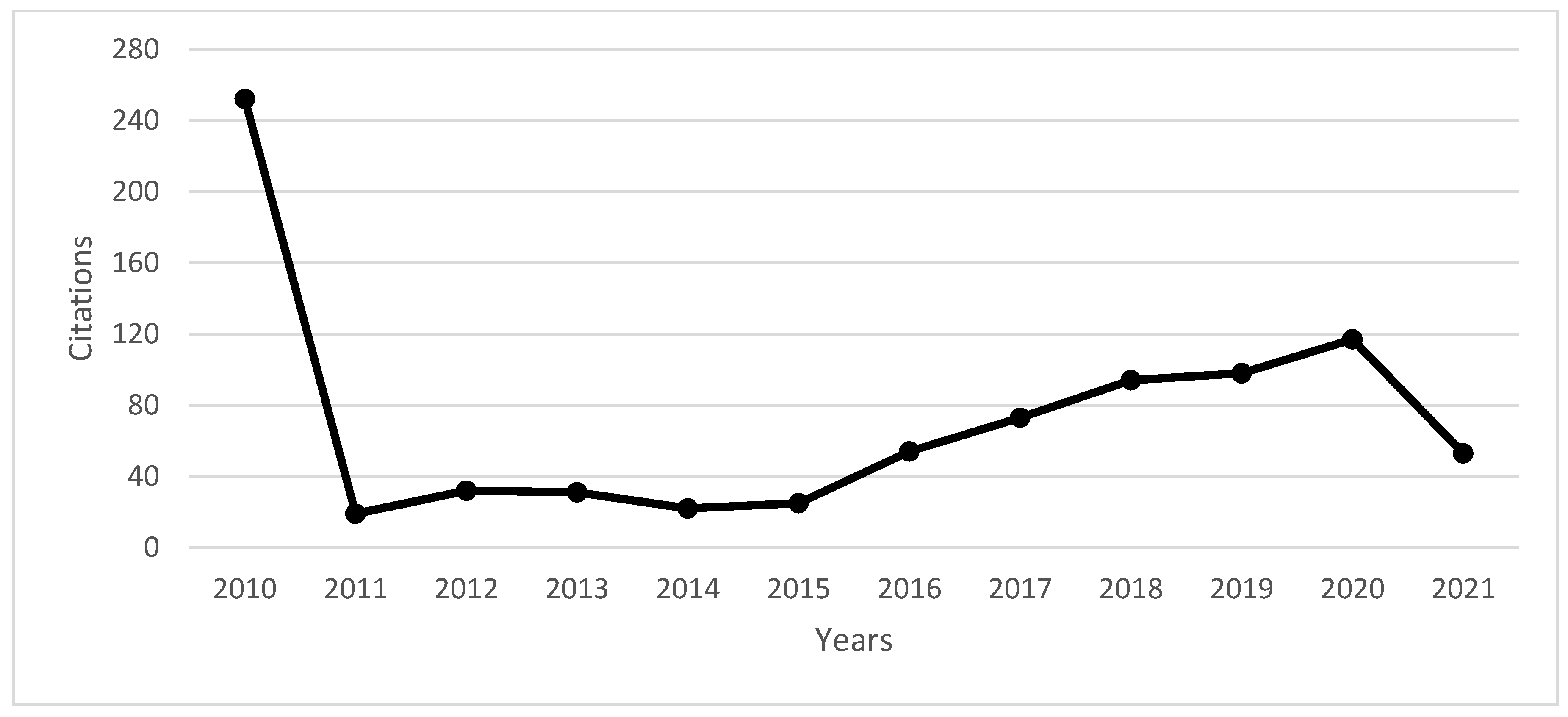
| Documents | ≤2010 | 2011 | 2012 | 2013 | 2014 | 2015 | 2016 | 2017 | 2018 | 2019 | 2020 | 2021 | Total | |
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| Trailblazing the Artificial lntelligence for Cybersecurity D... | 2020 | - | - | - | - | - | - | - | - | - | - | - | 1 | 1 |
| The Challenges and Opportunities in the Digitalization of Co... | 2020 | - | - | - | - | - | - | - | - | - | - | - | 1 | 1 |
| lnformation Technology as the Basis for Transformation into... | 2019 | - | - | - | - | - | - | - | - | - | - | 2 | - | 2 |
| Modeling the Effectiveness ofSolutions for Technogenic Safe... | 2019 | - | - | - | - | - | - | - | - | - | - | 1 | 1 | 2 |
| Malicious web domain identification using online credibility... | 2019 | - | - | - | - | - | - | - | - | - | 2 | 2 | 2 | 4 |
| Gesture-based animated CAPTCHA | 2016 | - | - | - | - | - | - | - | - | - | - | 1 | - | 1 |
| A case-based reasoning system for aiding detection and class... | 2016 | - | - | - | - | - | - | - | - | 1 | - | - | - | 1 |
| The research on information safety problem of digital campus... | 2011 | - | - | - | - | - | - | - | - | - | - | 1 | 1 | |
| A generic analytical target cascading optimization system... | 2010 | 1 | 3 | 1 | 1 | 2 | 1 | 1 | - | - | - | 10 | ||
| A decision-theoretic approach to dynamic sensor selection in... | 2009 | 1 | 1 | - | - | - | - | - | - | 1 | - | - | - | 3 |
| A logical architecture for active network management | 2006 | 1 | - | - | - | 1 | 1 | - | - | - | - | - | - | 3 |
| Auditing in the e-commerce era | 2004 | - | - | - | 1 | - | - | - | - | - | - | 1 | ||
| MetaMorph: An adaptive agent-based architecture for intellig... | 1999 | 7 | - | - | - | - | - | - | - | - | - | - | - | 7 |
| AICAMS: Artificial intelligence crime analysis and managemen... | 1998 | 12 | - | - | - | - | 1 | 1 | - | - | 1 | - | - | 15 |
| An empirical study of the use ofbusiness expert systems | 1988 | 11 | - | - | - | - | - | - | 1 | - | - | - | - | 12 |
| Total | 32 | 2 | 3 | 1 | 2 | 3 | 3 | 2 | 3 | 3 | 6 | 6 | 64 |
References
- Sheptunov, S.A.; Sukhanova, N.V. The Problems of Design and Application of Switching Neural Networks in Creation of Artificial Intelligence. In Proceedings of the 2020 International Conference Quality Management, Transport and Information Security, Information Technologies (IT&QM&IS), Yaroslavl, Russia, 7–11 September 2020; Institute of Electrical and Electronics Engineers: Piscataway, NJ, USA, 2020; pp. 428–431. [Google Scholar]
- Kim, M.S. The Design of Industrial Security Tasks and Capabilities Required in Industrial Site. In Proceedings of the 2021 21st ACIS International Semi-Virtual Winter Conference on Software Engineering, Artificial Intelligence, Networking and Parallel/Distributed Computing, SNPD-Winter, Ho Chi Minh City, Vietnam, 28–30 January 2021; ACIS International: Mt. Pleasant, MI, USA, 2021; pp. 218–223. [Google Scholar]
- Melville, N.; McQuaid, M. Generating shareable statistical databases for business value: Multiple imputation with multimodal perturbation. Inf. Syst. Res. 2012, 23, 559–574. [Google Scholar] [CrossRef]
- Zhu, F.; Li, G. Study on Security of Electronic Commerce Information System. In Proceedings of the 2011 2nd International Conference on Artificial Intelligence, Management Science and Electronic Commerce (AIMSEC 2011), Zhengzhou, China, 8–10 August 2011; Institute of Electrical and Electronics Engineers: Piscataway, NJ, USA, 2011; pp. 1546–1549. [Google Scholar]
- Hu, X.; Wang, K. Bank Financial Innovation and Computer Information Security Management Based on Artificial Intelligence. In Proceedings of the 2020 2nd International Conference on Machine Learning, Big Data and Business Intelligence (MLBDBI) Taiyuan, China, 23–25 October 2020; Institute of Electrical and Electronics Engineers: Piscataway, NJ, USA, 2020; pp. 572–575. [Google Scholar]
- Singh, J. Real Time BIG Data Analytic: Security Concern and Challenges with Machine Learning Algorithm. In Proceedings of the 2014 Conference on IT in Business, Industry and Government: An International Conference by CSI on Big Data (CSIBIG), Indore, India, 8–9 March 2014; Excellent Publishing House: New Delhi, India, 2014. [Google Scholar]
- Choi, H.; Young, K.J. Practical Approach of Security Enhancement Method Based on the Protection Motivation Theory. In Proceedings of the 2021 21st ACIS International Semi-Virtual Winter Conference on Software Engineering, Artificial Intelligence, Networking and Parallel/Distributed Computing (SNPD-Winter), Ho Chi Minh City, Vietnam, 28–30 January 2021; ACIS International: Mt. Pleasant, MI, USA, 2021; pp. 96–97. [Google Scholar]
- Sun, Y.; Men, T.; Huang, G. Analysis and Design of China’s E-Bank CAPTCHA. In WIT Transactions on Information and Communication Technologies; WIT Press: Southampton, UK, 2014; Volume 61, pp. 1343–1350. [Google Scholar]
- Popkova, E.; Alekseev, A.N.; Lobova, S.V.; Sergi, B.S. The theory of innovation and innovative development. AI scenarios in russia. Technol. Soc. 2020, 63, 101390. [Google Scholar] [CrossRef]
- Zhong, X.; Ji, G. RETRACTED ARTICLE: Research on the Development Measures of Housing Security System. In Proceedings of the 2011 2nd International Conference on Artificial Intelligence, Management Science and Electronic Commerce (AIMSEC), Zhengzhou, China, 8–10 August 2011; Institute of Electrical and Electronics Engineers: Piscataway, NJ, USA, 2011; pp. 586–588. [Google Scholar]
- Workman, M. Validation of a biases model in strategic security decision making. Inf. Manag. Comput. Secur. 2012, 20, 52–70. [Google Scholar] [CrossRef]
- Li, F. The Research on Information Safety Problem of Digital Campus Network. In Proceedings of the 2011 2nd International Conference on Artificial Intelligence, Management Science and Electronic Commerce (AIMSEC 2011), Zhengzhou, China, 8–10 August 2011; Institute of Electrical and Electronics Engineers: Piscataway, NJ, USA, 2011; pp. 828–831. [Google Scholar]
- Sukhanova, N.V.; Sheptunov, S.A.; Glashev, R.M. The Neuron Network Model of Human Personality for Use in Robotic Systems in Medicine and Biology. In Proceedings of the 2019 IEEE International Conference Quality Management, Transport and Information Security, Information Technologies IT and QM and IS, Sochy, Russia, 23–27 September 2019; Institute of Electrical and Electronics Engineers: Piscataway, NJ, USA, 2019; pp. 11–16. [Google Scholar]
- Ekenberg, L.; Danielson, M.; Boman, M. Imposing security constraints on agent-based decision support. Decis. Support Syst. 1997, 20, 3–15. [Google Scholar] [CrossRef]
- Loideain, N.N.; Adams, R. From alexa to siri and the GDPR: the gendering of virtual personal assistants and the role of data protection impact assessments. Comput. Law Secur. Rev. 2020, 36, 105366. [Google Scholar] [CrossRef]
- Khelvas, A.; Demyanova, D.; Gilya-Zetinov, A.; Konyagin, E.; Khafizov, R.; Pashkov, R. Adaptive Distributed Video Surveillance System. In Proceedings of the 2020 International Conference on Technology and Entrepreneurship—Virtual (ICTE-V), Bologna, Italy, 20–23 September 2020. [Google Scholar]
- Brahan, J.W.; Lam, K.P.; Chan, H.; Leung, W. AICAMS: Artificial intelligence crime analysis and management system. Knowl. Based Syst. 1998, 11, 355–361. [Google Scholar] [CrossRef]
- Nikolskaia, K.; Naumov, V. Ethical and Legal Principles of Publishing Open Source Dual-Purpose Machine Learning Algorithms. In Proceedings of the 2020 IEEE International Conference Quality Management, Transport and Information Security, Information Technologies, IT and QM and IS, Yaroslavl, Russia, 7–11 September 2020; Institute of Electrical and Electronics Engineers: Piscataway, NJ, USA, 2020; pp. 56–58. [Google Scholar]
- Hu, Z.; Chiong, R.; Pranata, I.; Bao, Y.; Lin, Y. Malicious web domain identification using online credibility and performance data by considering the class imbalance issue. Ind. Manag. Data Syst. 2019, 119, 676–696. [Google Scholar] [CrossRef]
- Angioni, M.; Musso, F. New perspectives from technology adoption in senior cohousing facilities. TQM J. 2020, 32, 761–777. [Google Scholar] [CrossRef]
- Huang, L.; Ye, C. Research of Secure University E-Government Based on PKI. In Proceedings of the 2011 2nd International Conference on Artificial Intelligence, Management Science and Electronic Commerce (AIMSEC), Zhengzhou, China, 8–10 August 2011; Institute of Electrical and Electronics Engineers: Piscataway, NJ, USA, 2011; pp. 7174–7177. [Google Scholar]
- Sedova, N.A.; Sedov, V.A.; Dudareva, O.V.; Bazhenov, R.I.; Lavrushina, E.G. An Autosteering Gear System with a Fuzzy Regulator Adjusted by a Neural Network. In Proceedings of the Proceedings of the 2019 IEEE International Conference Quality Management, Transport and Information Security, Information Technologies IT and QM and IS, Sochy, Russia, 23–27 September 2019; Institute of Electrical and Electronics Engineers: Piscataway, NJ, USA, 2019; pp. 197–202. [Google Scholar]
- Chen, L. Intelligent mobile safety system to educational organization. In Proceedings of the ICE-B 2010 International Conference on e-Business, Athens, Greece, 26–28 July 2010; pp. 55–62. [Google Scholar]
- Beheshtian-Ardekani, M.; Salchenberger, L.M. An empirical study of the use of business expert systems. Inf. Manag. 1988, 15, 183–190. [Google Scholar] [CrossRef]
- Lv, X. Information Security Risk Evaluation for E-Campus. In Proceedings of the 2011 2nd International Conference on Artificial Intelligence, Management Science and Electronic Commerce (AIMSEC 2011), Zhengzhou, China, 8–10 August 2011; Institute of Electrical and Electronics Engineers: Piscataway, NJ, USA, 2011; pp. 2153–2154. [Google Scholar]
- An, W.; Wang, H. Design for the Configuration Software of Coalmine Security Monitoring. In Proceedings of the 2011 2nd International Conference on Artificial Intelligence, Management Science and Electronic Commerce (AIMSEC), Zhengzhou, China, 8–10 August 2011; Institute of Electrical and Electronics Engineers: Piscataway, NJ, USA, 2011; pp. 2947–2950. [Google Scholar]
- He, Q.; Chen, G. Research of Security Audit of Enterprise Group Accounting Information System Under Internet Environment. In Proceedings of the 2011 2nd International Conference on Artificial Intelligence, Management Science and Electronic Commerce (AIMSEC), Zhengzhou, China, 8–10 August 2011; Institute of Electrical and Electronics Engineers: Piscataway, NJ, USA, 2011; pp. 516–519. [Google Scholar]
- Zhang, Q.; Li, Z.; Song, C. The Improvement of Digital Signature Algorithm Based on Elliptic Curve Cryptography. In Proceedings of the 2011 2nd International Conference on Artificial Intelligence, Management Science and Electronic Commerce (AIMSEC), Zhengzhou, China, 8–10 August 2011; Institute of Electrical and Electronics Engineers: Piscataway, NJ, USA, 2011; pp. 1689–1691. [Google Scholar]
- Xiong, Y. Research on the internet banking security based on dynamic password. In Proceedings of the 2011 2nd International Conference on Artificial Intelligence, Management Science and Electronic Commerce (AIMSEC), Zhengzhou, China, 8–10 August 2011; Institute of Electrical and Electronics Engineers: Piscataway, NJ, USA, 2011; pp. 4746–4749. [Google Scholar]
- Stafford, T.F. Platform-Dependent Computer Security Complacency: the Unrecognized Insider Threat. IEEE Trans. Eng. Manag. 2021, 1–12. [Google Scholar] [CrossRef]
- Bellavista, P.; Corradi, A.; Stefanelli, C. An open secure mobile agent framework for systems management. J. Netw. Syst. Manag. 1999, 7, 323–339. [Google Scholar] [CrossRef]
- Samtani, S.; Kantarcioglu, M.; Chen, H. Trailblazing the artificial intelligence for cybersecurity discipline: A multi-disciplinary research roadmap. ACM Trans. Manag. Inf. Syst. 2020, 11, 17. [Google Scholar] [CrossRef]
- Gao, L.; Zheng, D. Analysis on Code Stability and Fault Tolerance. In Proceedings of the 2011 2nd International Conference on Artificial Intelligence, Management Science and Electronic Commerce (AIMSEC), Zhengzhou, China, 8–10 August 2011; Institute of Electrical and Electronics Engineers: Piscataway, NJ, USA, 2011; pp. 155–159. [Google Scholar]
- Dhieb, N.; Ghazzai, H.; Besbes, H.; Massoud, Y. Scalable and Secure Architecture for Distributed IoT Systems. In Proceedings of the 2020 IEEE Technology and Engineering Management Conference (TEMSCON), Virtual, 3–6 June 2020. [Google Scholar]
- Cheong, M.; Leins, K.; Coghlan, S. Computer Science Communities: Who is Speaking, and Who is Listening to the Women? Using an Ethics of Care to Promote Diverse Voices. In Proceedings of the FAccT 2021 ACM Conference on Fairness, Accountability, and Transparency, Virtual, 3–10 March 2021; pp. 106–115. [Google Scholar]
- Prakash, U.M.; Thamaraiselvi, V.G. Detecting and Tracking of Multiple Moving Objects for Intelligent Video Surveillance Systems. In Proceedings of the 2nd International Conference on Current Trends in Engineering and Technology (ICCTET), Coimbatore, India, 8 July 2014; Institute of Electrical and Electronics Engineers: Piscataway, NJ, USA, 2014; pp. 253–257. [Google Scholar]
- Spaan, M.T.J.; Lima, P.U. A Decision-Theoretic Approach to Dynamic Sensor Selection in Camera Networks. In Proceedings of the ICAPS 2009 19th International Conference on Automated Planning and Scheduling, Thessaloniki, Greece, 19–23 September 2009; pp. 297–304. [Google Scholar]
- Lei, X. Cyber-Security Analysis for Process Control Oriented Information System. In Proceedings of the 2011 2nd International Conference on Artificial Intelligence, Management Science and Electronic Commerce (AIMSEC), Zhengzhou, China, 8–10 August 2011; Institute of Electrical and Electronics Engineers: Piscataway, NJ, USA, 2011; pp. 289–292. [Google Scholar]
- Cherviakov, L.M.; Sheptunov, S.A.; Oleynik, A.V.; Bychkova, N.A. Digitalization of Quality Management of the Strategic Decision-Making Process. In Proceedings of the 2020 IEEE International Conference Quality Management, Transport and Information Security, Information Technologies (IT and QM and IS), Yaroslavl, Russia, 7–11 September 2020; Institute of Electrical and Electronics Engineers: Piscataway, NJ, USA; pp. 193–196. [Google Scholar]
- Qu, T.; Huang, G.Q.; Zhang, Y.; Dai, Q.Y. A generic analytical target cascading optimization system for decentralized supply chain configuration over supply chain grid. Int. J. Prod. Econ. 2010, 127, 262–277. [Google Scholar] [CrossRef]
- Titov, A.A.; Rogov, A.A. Mathematical Support of Modeling Methods in Quality Management Problems of Complex System and Processes. In Proceedings of the 2019 IEEE International Conference Quality Management, Transport and Information Security, Information Technologies (IT and QM and IS), Sochy, Russia, 23–27 September 2019; Institute of Electrical and Electronics Engineers: Piscataway, NJ, USA; pp. 308–311. [Google Scholar]
- El-Gayar, O.F.; Fritz, B.D. A web-based multi-perspective decision support system for information security planning. Decis. Support Syst. 2010, 50, 43–54. [Google Scholar] [CrossRef]
- Tagiltseva, J.A.; Kuzina, E.L.; Bortnik, O.A.; Shlikov, E.E.; Magomedov, S.S.; Vasilenko, M.A.; Drozdov, N.A. Modeling the Effectiveness of Solutions for Technogenic Safety in the Electrical Industry. In Proceedings of the 2019 IEEE International Conference Quality Management, Transport and Information Security, Information Technologies (IT and QM and IS), Sochy, Russia, 23–27 September 2019; Institute of Electrical and Electronics Engineers: Piscataway, NJ, USA; pp. 100–105. [Google Scholar]
- Jacome-Grajales, N.; Escobedo-Briones, G.; Roblero, J.; Arroyo-Figueroa, G. Application of Business Intelligence to the Power System Process Security. In Proceedings of the 2013 3rd International Conference on Innovative Computing Technology (INTECH), London, UK, 29–31 August 2013; pp. 258–262. [Google Scholar]
- Fenz, S.; Neubauer, T. Ontology-based information security compliance determination and control selection on the example of ISO 27002. Inf. Comput. Secur. 2018, 26, 551–567. [Google Scholar] [CrossRef] [Green Version]
- Canal, G.; Borgo, R.; Coles, A.; Drake, A.; Huynh, D.; Keller, P.; Sklar, E.I. Building trust in human-machine partnerships. Comput. Law Secur. Rev. 2020, 39, 105489. [Google Scholar] [CrossRef]
- Sarne, D.; Grosz, B.J.; Owotoki, P. Effective Information Value Calculation for Interruption Management in Multi-Agent Scheduling. In Proceedings of the ICAPS 2008 18th International Conference on Automated Planning and Scheduling, Sydney, Australia, 14–18 September 2008; pp. 313–321. [Google Scholar]
- Lee, P.; Yau, C.; Tan, K.; Chee, M. Predictive Model on the Likelihood of Online Purchase in E-Commerce Environment. In Proceedings of the Annual Meeting of the Decision Sciences Institute, San Diego, CA, USA, 23–26 November 2002; pp. 569–574. [Google Scholar]
- Hansen, J.V. Internet commerce security: Issues and models for control checking. J. Oper. Res. Soc. 2001, 52, 1159–1164. [Google Scholar] [CrossRef]
- Almeida, F.; Duarte Santos, J.; Augusto Monteiro, J. The challenges and opportunities in the digitalization of companies in a post-COVID-19 world. IEEE Eng. Manag. Rev. 2020, 48, 97–103. [Google Scholar] [CrossRef]
- Al-Omari, M.; Rawashdeh, M.; Qutaishat, F.; Alshira’H, M.; Ababneh, N. An intelligent tree-based intrusion detection model for cyber security. J. Netw. Syst. Manag. 2021, 29, 20. [Google Scholar] [CrossRef]
- Gaglio, S.; Gatani, L.; Lo Re, G.; Urso, A. A logical architecture for active network management. J. Netw. Syst. Manag. 2006, 14, 127–146. [Google Scholar] [CrossRef] [Green Version]
- Stathaki, C.; Xenakis, A.; Skayannis, P.; Stamoulis, G. Studying the Role of Proximity in Advancing Innovation Partnerships at the Dawn of Industry 4.0 Era. In Proceedings of the European Conference on Innovation and Entrepreneurship (ECIE), Rome, Italy, 17–18 September 2020; pp. 651–658. [Google Scholar]
- Martin-Fiatin, J.; Znaty, S.; Hubaux, J. A survey of distributed enterprise network and systems management paradigms. J. Netw. Syst. Manag. 1999, 7, 9–26. [Google Scholar] [CrossRef] [Green Version]
- Maturana, F.; Shen, W.; Norrie, D.H. MetaMorph: An adaptive agent-based architecture for intelligent manufacturing. Int. J. Prod. Res. 1999, 37, 2159–2173. [Google Scholar] [CrossRef]
- Lee, T.; Kim, S.; Kim, K. A research on the vulnerabilities of PLC using search engine. In Proceedings of the ICTC 2019 10th International Conference on ICT Convergence: ICT Convergence Leading the Autonomous Future, Jeju City, South Korea, 16–18 October 2019; pp. 184–188. [Google Scholar]
- Haddlesey, P. Artificial Intelligence; The Housing Assistance Council: Washington, DC, USA, 2003; pp. 18–20. [Google Scholar]
- Martynov, V.V.; Shavaleeva, D.N.; Zaytseva, A.A. Information Technology as the Basis for Transformation Into a Digital Society and Industry 5.0. In Proceedings of the 2019 IEEE International Conference Quality Management, Transport and Information Security, Information Technologies (IT and QM and IS), Sochy, Russia, 23–27 September 2019; Institute of Electrical and Electronics Engineers: Piscataway, NJ, USA; pp. 539–543. [Google Scholar]
- Zhao, N.; Yen, D.C.; Chang, I. Auditing in the e-commerce era. Inf. Manag. Comput. Secur. 2004, 12, 389–400. [Google Scholar] [CrossRef]
- Schneiderman, R. Outsourcing: How safe is your job? Electron. Des. 2004, 52, 48–54. [Google Scholar]
- Kseniia, N.; Minbaleev, A. Legal Support of Cybersecurity in the Field of Application of Artificial Intelligence Technology. In Proceedings of the 2020 IEEE International Conference Quality Management, Transport and Information Security, Information Technologies (IT and QM and IS), Yaroslavl, Russia, 7–11 September 2020; Institute of Electrical and Electronics Engineers: Piscataway, NJ, USA; pp. 59–62. [Google Scholar]
- Kafeza, E.; Kafeza, I. Privacy issues in AmI spaces. Int. J. Netw. Virtual Organ. 2009, 6, 634–650. [Google Scholar] [CrossRef]
- Efimova, O.V.; Baboshin, E.B.; Igolnikov, B.V.; Dmitrieva, E.I. Promising Digital Solutions for the Efficient Technological and Managerial Processes on Transport. In Proceedings of the 2020 IEEE International Conference Quality Management, Transport and Information Security, Information Technologies (IT and QM and IS), Yaroslavl, Russia, 7–11 September 2020; Institute of Electrical and Electronics Engineers: Piscataway, NJ, USA; pp. 92–95. [Google Scholar]
- Zhao, W.; Li, S. Analysis of Coal Mine Safety Monitoring Data Based on Column-Oriented Database. In Proceedings of the 2011 2nd International Conference on Artificial Intelligence, Management Science and Electronic Commerce (AIMSEC), Zhengzhou, China, 8–10 August 2011; Institute of Electrical and Electronics Engineers: Piscataway, NJ, USA, 2011; pp. 1920–1922. [Google Scholar]
- Grandhi, L.S.; Grandhi, S.; Wibowo, S. A Security-UTAUT Framework for Evaluating Key Security Determinants In Smart City Adoption by the Australian City Councils. In Proceedings of the 2021 21st ACIS International Semi-Virtual Winter Conference on Software Engineering, Artificial Intelligence, Networking and Parallel/Distributed Computing, SNPD-Winter, Ho Chi Minh City, Vietnam, 28–30 January 2021; ACIS International: Mt. Pleasant, MI, USA; pp. 17–22. [Google Scholar]
- Saya, W.P. The building of intelligence. AFE Facil. Eng. J. 2005, 32, 7–11. [Google Scholar]
- Hong, T.; Hofmann, A. Data Integrity Attacks Against Outage Management Systems. IEEE Trans. Eng. Manag. 2021. [Google Scholar] [CrossRef]
- Clarke, R. Regulatory alternatives for AI. Comput. Law Secur. Rev. 2019, 35, 398–409. [Google Scholar] [CrossRef]
- La Fors, D.K. Legal remedies for a forgiving society: Children’s rights, data protection rights and the value of forgiveness in AI-mediated risk profiling of children by dutch authorities. Comput. Law Secur. Rev. 2020, 38, 105430. [Google Scholar] [CrossRef]
- Shumilov, A.; Philippovich, A. Gesture-based animated CAPTCHA. Inf. Comput. Secur. 2016, 24, 242–254. [Google Scholar] [CrossRef]
- Lin, W.; Ke, S.; Tsai, C. CANN: An intrusion detection system based on combining cluster centers and nearest neighbors. Knowl. Based Syst. 2015, 78, 13–21. [Google Scholar] [CrossRef]
- De Fátima Stankowitz, R.; Salvação, P.M.; Lima, E.B.; de Medeiros Amaro, M.L.; Morales, H.M.P. Proposal of an Electronic Health Record Integrated to an Artificial Intelligence System for Early Detection of Sepsis. Towards the Digital World and Industry X.0. In Proceedings of the 29th International Conference of the International Association for Management of Technology (IAMOT), Cairo, Egypt, 13–17 September 2020; pp. 918–927. [Google Scholar]
- Gómez-Vallejo, H.J.; Uriel-Latorre, B.; Sande-Meijide, M.; Villamarín-Bello, B.; Pavón, R.; Fdez-Riverola, F.; Glez-Peña, D. A case-based reasoning system for aiding detection and classification of nosocomial infections. Decis. Support Syst. 2016, 84, 104–116. [Google Scholar] [CrossRef]
- Maksim, B.; Pavel, W.; Irina, V.; Mikhail, S.; Margarita, C. Development of a Software Library for Game Artificial Intelligence. In Proceedings of the 2020 IEEE International Conference Quality Management, Transport and Information Security, Information Technologies (IT and QM and IS), Yaroslavl, Russia, 7–11 September 2020; Institute of Electrical and Electronics Engineers: Piscataway, NJ, USA; pp. 188–192. [Google Scholar]
- Sharif, M.; Kausar, A.; Park, J.; Shin, D.R. Tiny Image Classification Using Four-Block Convolutional Neural Network. In Proceedings of the ICTC 2019—10th International Conference on ICT Convergence: ICT Convergence Leading the Autonomous Future, Jeju City, South Korea, 16–18 October 2019; pp. 1–6. [Google Scholar]
- Yang, Y.; Zeng, H.; Li, Z. The Video Surveillance System Based on DSP and Wireless Network. In Proceedings of the 2011 2nd International Conference on Artificial Intelligence, Management Science and Electronic Commerce (AIMSEC); Zhengzhou, China, 8–10 August 2011, Institute of Electrical and Electronics Engineers: Piscataway, NJ, USA, 2011; pp. 2657–2659. [Google Scholar]
- Zhang, Y.; Huang, H. VOIP Voice Network Technology Security Strategies. In Proceedings of the 2011 2nd International Conference on Artificial Intelligence, Management Science and Electronic Commerce (AIMSEC), Zhengzhou, China, 8–10 August 2011; Institute of Electrical and Electronics Engineers: Piscataway, NJ, USA, 2011; pp. 3591–3594. [Google Scholar]
- Rosário, A.; Vilaça, F.; Raimundo, R.; Cruz, R. Literature review on health knowledge management in the last 10 years (2009–2019). Electron. J. Knowl. Manag. 2021, 18, 338–355. [Google Scholar] [CrossRef]
- Raimundo, R.; Rosário, A. Blockchain system in the higher education. Eur. J. Investig. Health Psychol. Educ. 2021, 11, 21. [Google Scholar] [CrossRef]
- Rosário, A.; Fernandes, F.; Raimundo, R.; Cruz, R. Determinants of Nascent Entrepreneurship Development. In Handbook of Research on Nascent Entrepreneurship and Creating New Ventures; Carrizo Moreira, A., Dantas, J.G., Eds.; IGI Global: Hershey, PA, USA, 2021; pp. 172–193. [Google Scholar]
- Kayes, A.S.M.; Kalaria, R.; Sarker, I.H.; Islam, M.S.; Watters, P.A.; Ng, A.; Hammoudeh, M.; Badsha, S.; Kumara, I. A Survey of Context-Aware Access Control Mechanisms for Cloud and Fog Networks: Taxonomy and Open Research Issues. Sensors 2020, 20, 2464. [Google Scholar] [CrossRef] [PubMed]

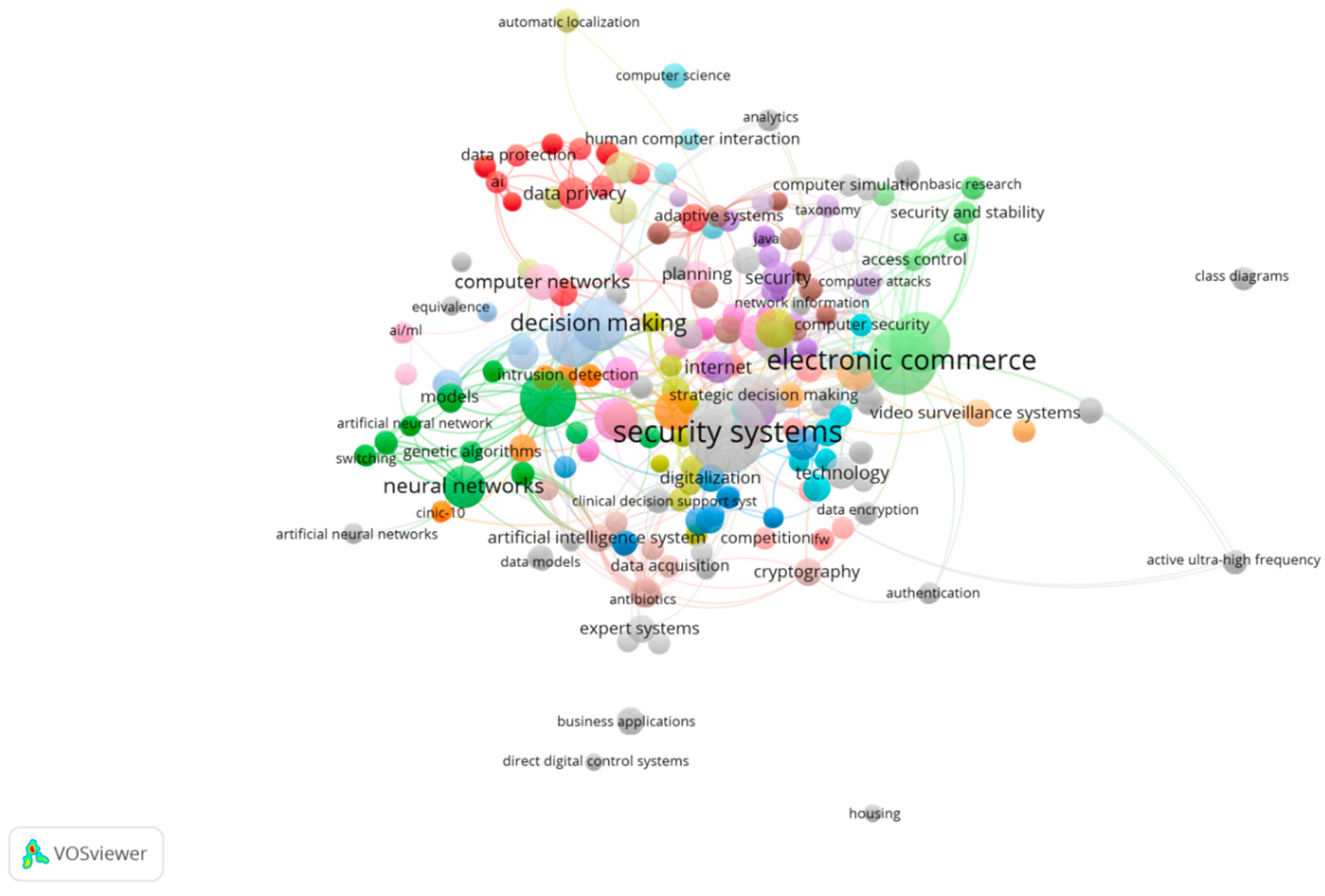
| Database Scopus | Screening | Publications |
|---|---|---|
| Meta-search | Keyword: Artificial Intelligence | 382,586 |
| Inclusion Criteria | Keyword: Artificial Intelligence; Security | 15,916 |
| Keyword: Artificial Intelligence; Security Business, Management, and Accounting | 401 | |
| Screening | Keyword: Artificial Intelligence; Security Business, Management, and Accounting Exact Keyword: Security of Data; Security Systems Published until June 2021 | 77 |
| Title | SJR | Best Quartile | H Index |
|---|---|---|---|
| Information Systems Research | 3.510 | Q1 | 159 |
| International Journal of Production Economics | 2.410 | Q1 | 185 |
| Information and Management | 2.150 | Q1 | 162 |
| Knowledge-Based Systems | 1.590 | Q1 | 121 |
| Decision Support Systems | 1.560 | Q1 | 151 |
| Industrial Management and Data Systems | 0.990 | Q1 | 103 |
| Technology In Society | 0.820 | Q1 | 51 |
| Computer Law and Security Review | 0.820 | Q1 | 38 |
| Journal of the Operational Research Society | 0.750 | Q1 | 108 |
| IEEE Transactions on Engineering Management | 0.700 | Q1 | 92 |
| ACM Transactions on Management Information Systems | 0.600 | Q1 | 29 |
| Journal of Network and Systems Management | 0.490 | Q2 | 35 |
| Information and Computer Security | 0.330 | Q2 | 49 |
| TQM Journal | 0.540 | Q2 | 67 |
| IEEE Engineering Management Review | 0.300 | Q3 | 20 |
| International Journal of Production Research | 0.270 | Q3 | 19 |
| International Journal of Networking and Virtual Organizations | 0.170 | Q4 | 19 |
| Electronic Design | 0.100 | Q4 | 7 |
| Proceedings of the European Conference on Innovation and Entrepreneurship Ecie | 0.130 | -* | 6 |
| Icaps 2008 Proceedings of the 18th International Conference on Automated Planning and Scheduling | -* | -* | 19 |
| Wit Transactions on Information and Communication Technologies | -* | -* | 13 |
| Proceedings Annual Meeting of the Decision Sciences Institute | -* | -* | 9 |
| Proceedings of the 2014 Conference on IT In Business Industry and Government An International Conference By Csi on Big Data Csibig 2014 | -* | -* | 8 |
| 2nd International Conference on Current Trends In Engineering and Technology Icctet 2014 | -* | -* | 7 |
| ICE B 2010 Proceedings of the International Conference on E Business | -* | -* | 6 |
| AFE Facilities Engineering Journal | -* | -* | 2 |
| 2011 2nd International Conference on Artificial Intelligence Management Science and Electronic Commerce Aimsec 2011 Proceedings | -* | -* | -* |
| Proceedings of the 2020 IEEE International Conference Quality Management Transport and Information Security Information Technologies IT and Qm and Is 2020 | -* | -* | -* |
| Proceedings of the 2019 IEEE International Conference Quality Management Transport and Information Security Information Technologies IT and Qm and Is 2019 | -* | -* | -* |
| Proceedings 2021 21st Acis International Semi Virtual Winter Conference on Software Engineering Artificial Intelligence Networking and Parallel Distributed Computing Snpd Winter 2021 | -* | -* | -* |
| Ictc 2019 10th International Conference on ICT Convergence ICT Convergence Leading the Autonomous Future | -* | -* | -* |
| 2013 3rd International Conference on Innovative Computing Technology Intech 2013 | -* | -* | -* |
| 2020 IEEE Technology and Engineering Management Conference Temscon 2020 | -* | -* | -* |
| 2020 International Conference on Technology and Entrepreneurship Virtual Icte V 2020 | -* | -* | -* |
| Facct 2021 Proceedings of the 2021 ACM Conference on Fairness Accountability and Transparency | -* | -* | -* |
| HAC | -* | -* | -* |
| Icaps 2009 Proceedings of the 19th International Conference on Automated Planning and Scheduling | -* | -* | -* |
| Information Management and Computer Security | -* | -* | -* |
| Information Management Computer Security | -* | -* | -* |
| Proceedings 2020 2nd International Conference on Machine Learning Big Data and Business Intelligence Mlbdbi 2020 | -* | -* | -* |
| Toward the Digital World and Industry X 0 Proceedings of the 29th International Conference of the International Association for Management of Technology Iamot 2020 | -* | -* | -* |
Publisher’s Note: MDPI stays neutral with regard to jurisdictional claims in published maps and institutional affiliations. |
© 2021 by the authors. Licensee MDPI, Basel, Switzerland. This article is an open access article distributed under the terms and conditions of the Creative Commons Attribution (CC BY) license (https://creativecommons.org/licenses/by/4.0/).
Share and Cite
Raimundo, R.; Rosário, A. The Impact of Artificial Intelligence on Data System Security: A Literature Review. Sensors 2021, 21, 7029. https://doi.org/10.3390/s21217029
Raimundo R, Rosário A. The Impact of Artificial Intelligence on Data System Security: A Literature Review. Sensors. 2021; 21(21):7029. https://doi.org/10.3390/s21217029
Chicago/Turabian StyleRaimundo, Ricardo, and Albérico Rosário. 2021. "The Impact of Artificial Intelligence on Data System Security: A Literature Review" Sensors 21, no. 21: 7029. https://doi.org/10.3390/s21217029
APA StyleRaimundo, R., & Rosário, A. (2021). The Impact of Artificial Intelligence on Data System Security: A Literature Review. Sensors, 21(21), 7029. https://doi.org/10.3390/s21217029







