A Blockchain-Based Distributed Paradigm to Secure Localization Services †
Abstract
:1. Introduction
- (i)
- Definition of the entities and trackers concept as elements able to exchange their role when they operate within a specific wireless-based environment;
- (ii)
- Formalization of data exchange methods between entities and trackers, and trackers and blockchain-based distributed ledgers, in terms of both device identification and communication protocols;
- (iii)
- Formalization of the data structures involved in the entities and trackers, and trackers and blockchain-based distributed ledger communications.
- (i)
- A comprehensive discussion of the context and the scientific background in which the paradigm proposed in the present work is placed;
- (ii)
- An extended formalization of the notions of entities and trackers, able to interchange their roles, which operate within the wireless-based environment to provide secure localization services;
- (iii)
- A timely definition of the interaction model and communication protocols between entities, trackers and the blockchain-based distributed ledger, with the goal of reliably and permanently recording tracking information in a verifiable fashion and respecting their privacy;
- (iv)
- The identification of specific heuristics and strategies, to reconstruct the entities movements by means of the history of positions stored on the distributed ledger;
- (v)
- A series of experiments aimed to verify and evaluate the practical feasibility of the proposed IoE paradigm in a real-world scenario;
- (vi)
- An in-depth analysis and coverage of the potential usage applications, future developments and implementation directions of such a paradigm.
2. Background and Related Work
2.1. Mobile Environment
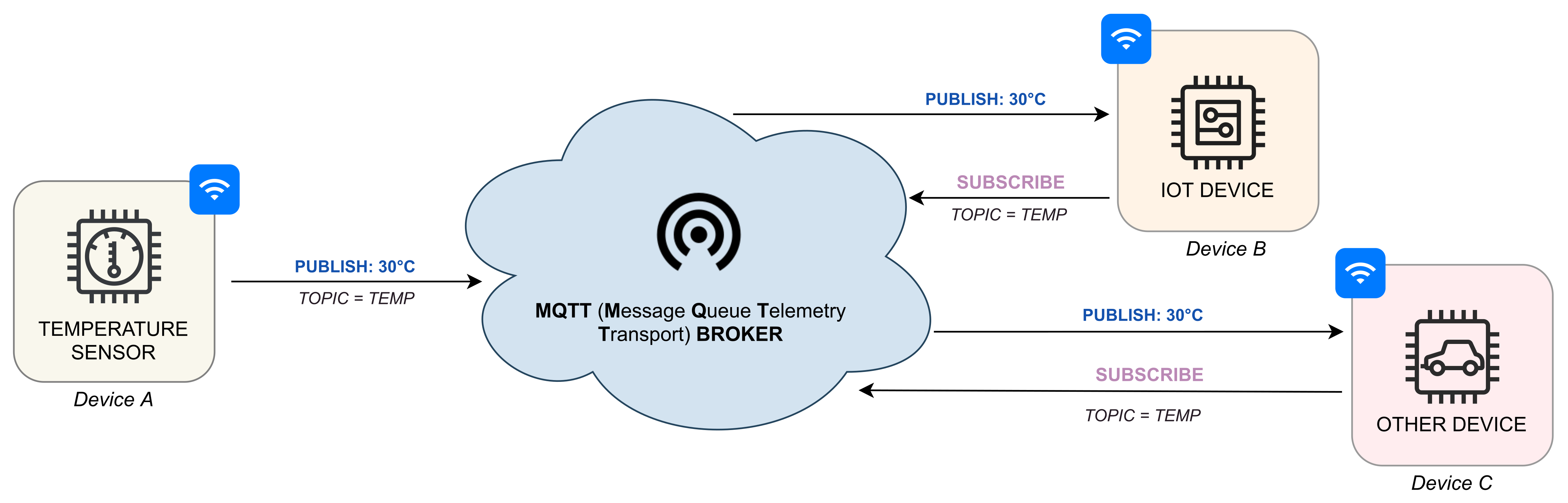
2.2. IoT Environment
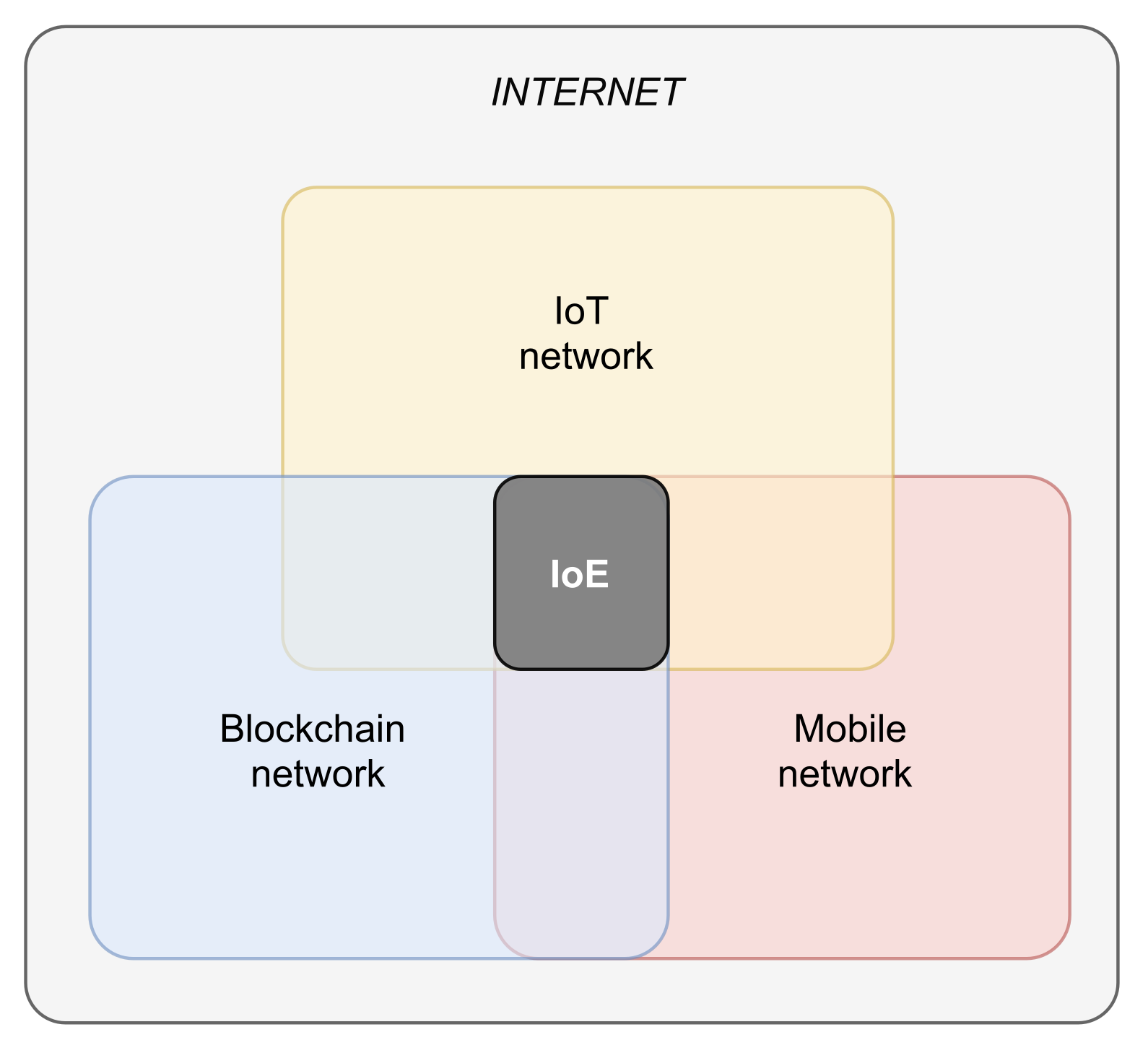
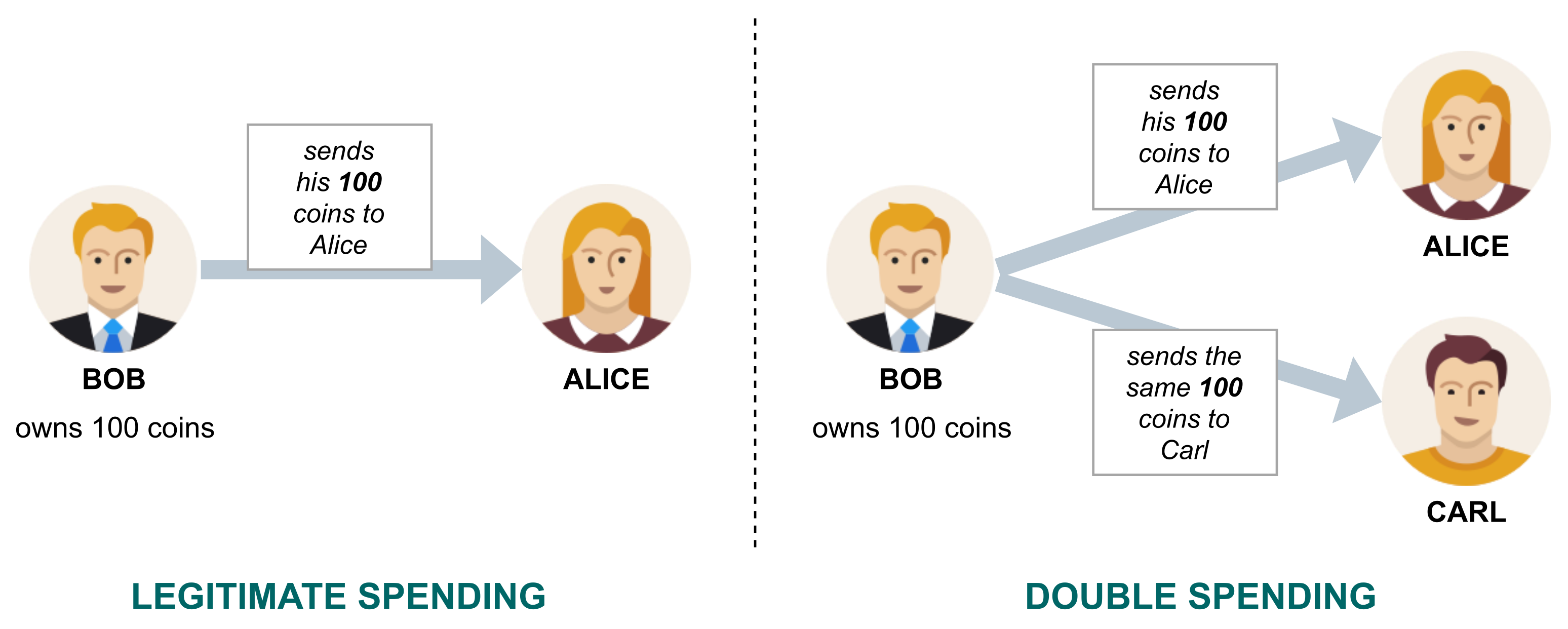
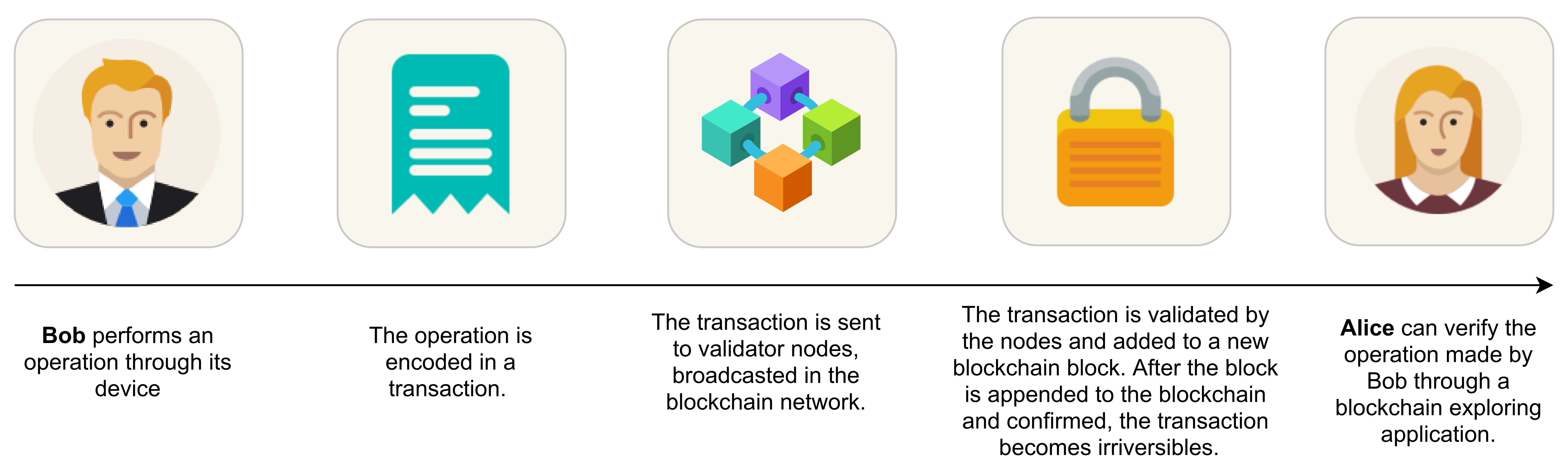
2.3. Blockchain Environment
- IoT-IoT: characterized by low latency and a high level of security, since the involved IoT devices operate between them for most of the time, by exploiting the canonical protocols and by limiting the blockchain use for storing only a few information;
- IoT-Blockchain: by following this strategy, all the IoT information is stored on the blockchain, assuring its immutability and traceability, but increasing the bandwidth consumption and the latency-time;
- Hybrid Paradigm: this last strategy combines the two previous ones, performing part of the activities directly between the IoT devices, and limiting the interaction with the blockchain to the data storage activity.
2.4. Security Aspects
2.5. Localization Data Encoding
2.6. Related Work
3. Formal Notation
- (i)
- We denote as a set of entities, and we use to indicate such information related to an entitye;;
- (ii)
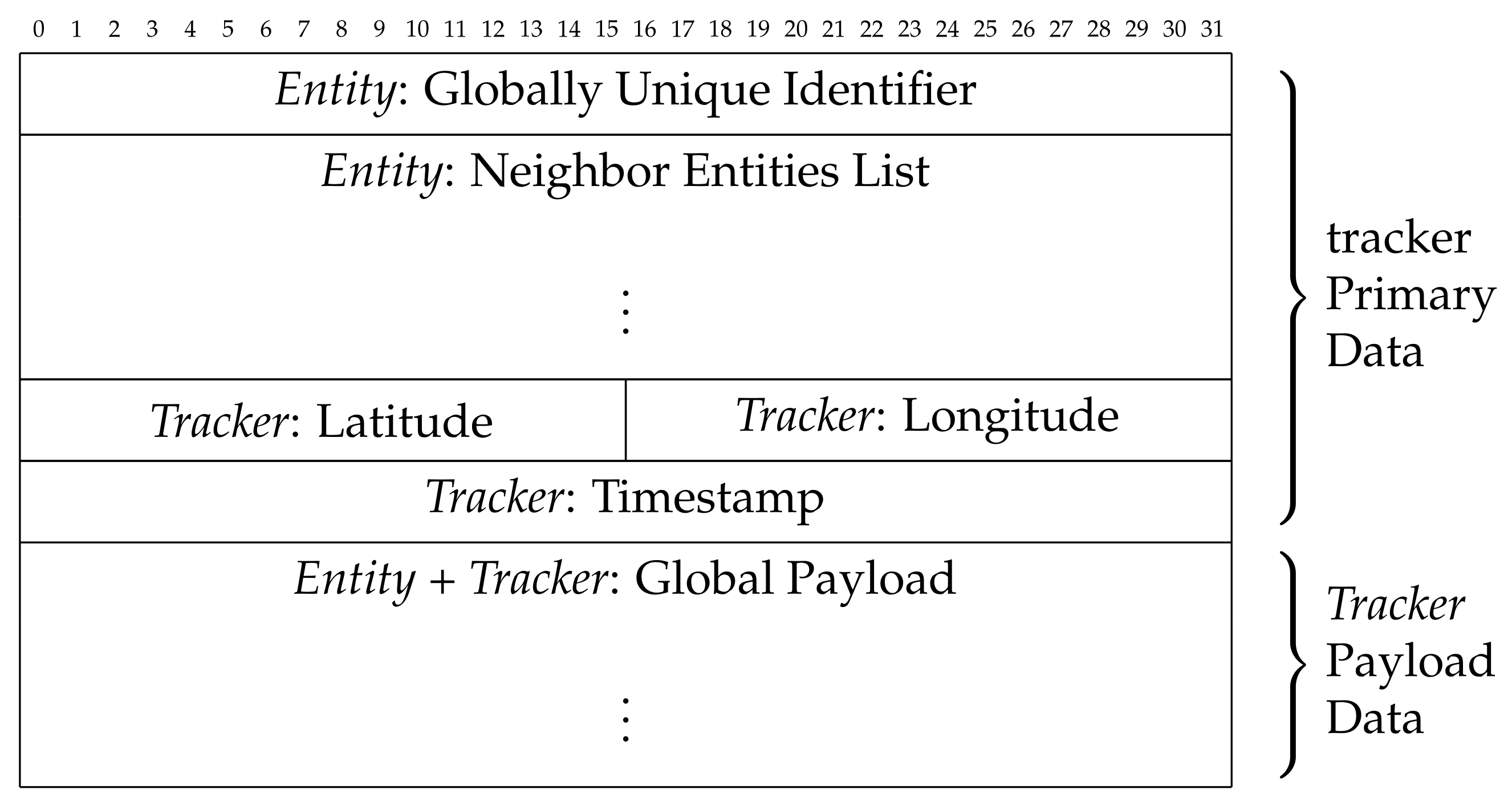
- We denote as the entities in E detected by a tracker device within seconds after detecting an entity (then ), and we use to indicate such information related to an entitye;
- (iii)
- We denote as a set of geographic locations, with , , and we use to indicate such information related to an entitye when a tracker device detects it;
- (iv)
- We denote as a set of timestamps, with , and we use to indicate the timestamp related to detecting an entitye by a tracker device;
- (v)
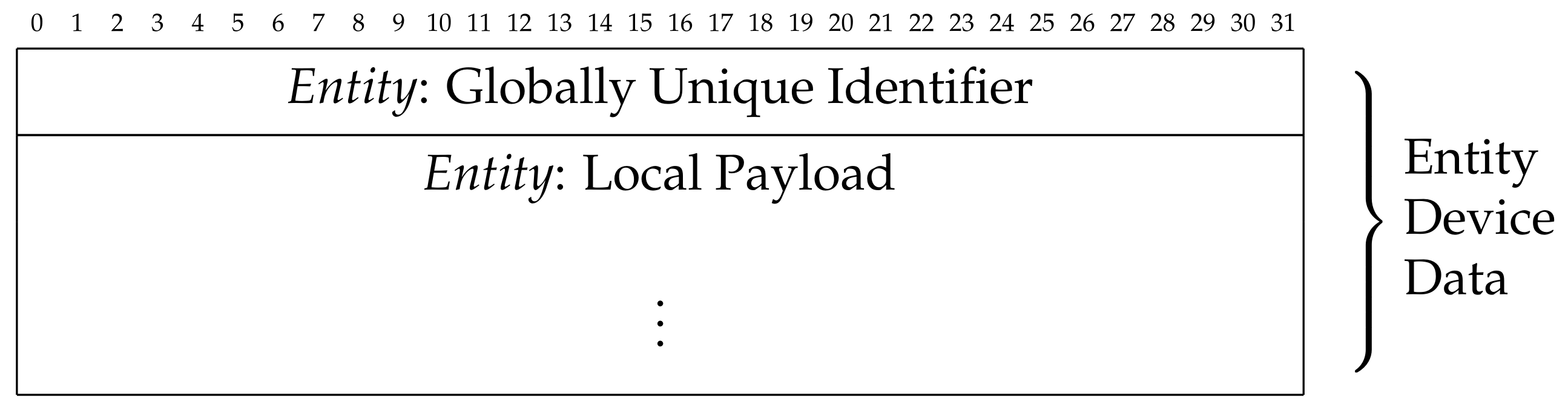
- We denote as a set of (i.e. Globally Unique IDentifiers, whose structure is formally defined in the RFC-4122 and explained in Section 4.1), using the notation to indicate the associated with an entitye, and the notation to indicate the associated with a tracker device;
- (vi)
- We denote as a payload, with , and we use to indicate a payload related to an entitye;
- (vii)
- We denote as a set of registration made on a blockchain-based distributed ledger, with , and we use and to indicate, respectively, a registration related to an entitye and all the registrations associated with that entity.
4. Approach Formulation
- (i)
- Elements Definition: it introduces the concept of entity and tracker in the IoE environment, as well as the method to assign them a Globally Unique Identifier, outlining some possible operative scenarios;
- (ii)
- Elements Detection: the detection process of an entity device is here described, from the detection-time by a tracker device to the recording-time of the collected data on a blockchain-based distributed ledger, focusing on the characteristics of the state-of-the-art wireless technologies able to perform these activities;
- (iii)
- Elements Communication: it formalizes the data structures and the software procedures able to merge the information related to the involved entity and tracker devices, generating the data structure that represents the information to store on the blockchain-based distributed ledger;
- (iv)
- Elements Localization: extensively, it describes the activities made to trace an entity, introducing some baseline strategies and a series of localization rules aimed to exploit the available information on the blockchain, directly or indirectly.
4.1. Elements Definition
- (i)
- The entity device has limited or absent hardware resources (e.g., CPU, memory, etc.), then it performs the identification process by exploiting passive technologies like RFID (Radio-Frequency IDentification). In this first scenario, the tracker device must be able to manage the identification process adopted by the entity;
- (ii)
- The entity device has hardware resources to adopt active technologies for the identification process (e.g., 6LoWPAN and ZigBee, both defined by the technical standard IEEE 802.15.4). This is the most common scenario, where the entity device uses canonical wireless technologies and the tracker device does not need any additional capability to interact with it;
- (iii)
- The entity device can perform processes that require considerable hardware/software resources. Such a scenario allows us to move on the IoE-side some processes usually performed on the tracker-side, and it also allows the IoE device to handle complex processes related to its sensors.
4.2. Elements Detection
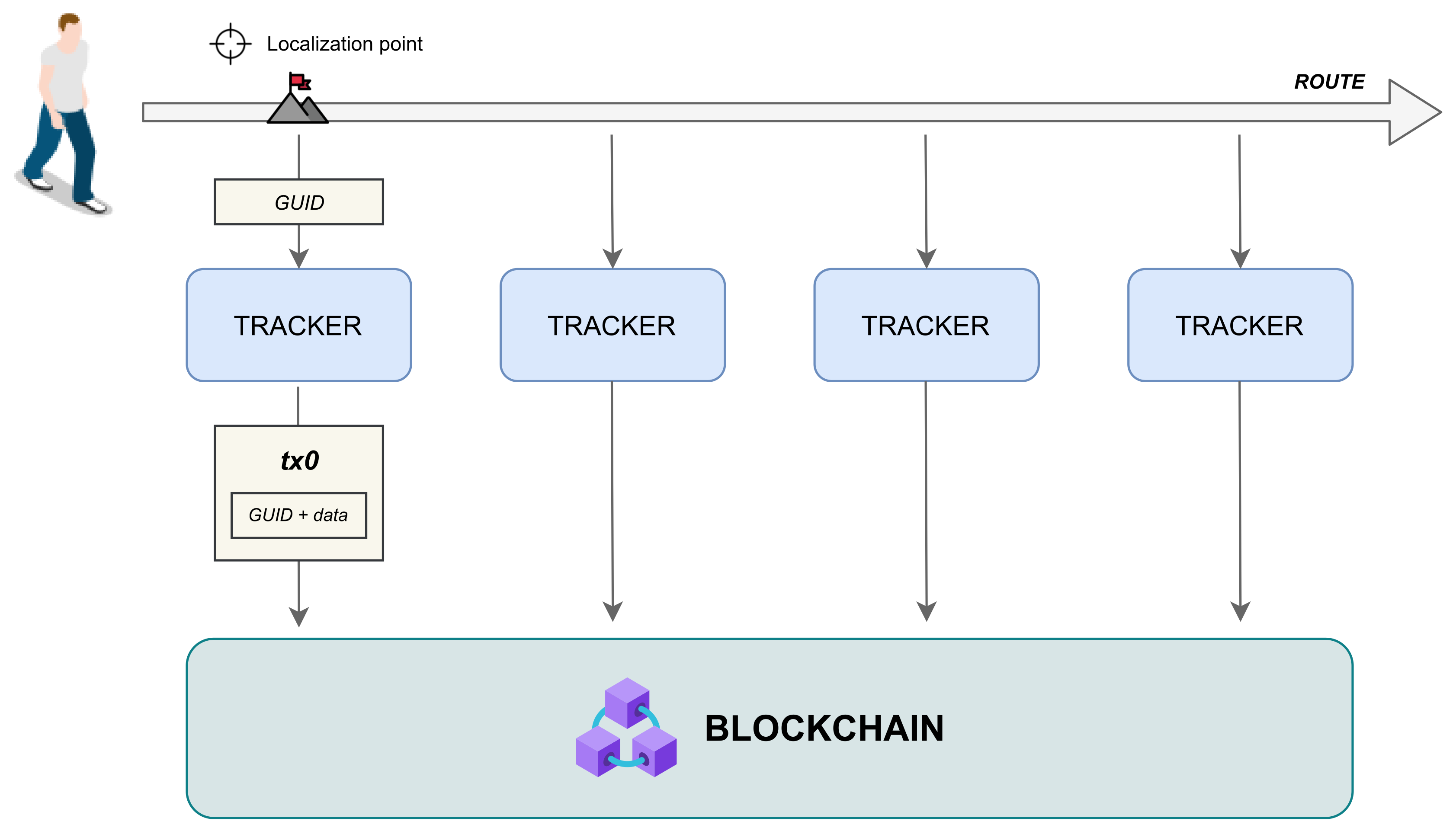
4.3. Elements Communication
- entity-side: it provides to broadcast the device GUID along with the payload (i.e., local sensors data) by using the built-in wireless device functionality;
- tracker-side: it performs a listening activity aimed to detect and recognize (distinguishing them from the other devices through the mechanism adopted in the implementation phase, for instance, a specific GUID preamble) entities within its wireless coverage area;
- tracker-side: it appends the e-health device data (i.e., primary and payload data) with the data transmitted by the entity device (i.e., GUID and payload), building a data packet suitable for registration on the blockchain-based distributed ledger;
- tracker-side: it submits the defined data packet on the blockchain-based distributed ledger to perform an immutable registration of the entity device activity;
- tracker-side: it waits to receive from the blockchain-based distributed ledger the registration acknowledge of the submitted packet; otherwise, it repeats the submission.
4.4. Elements Localization
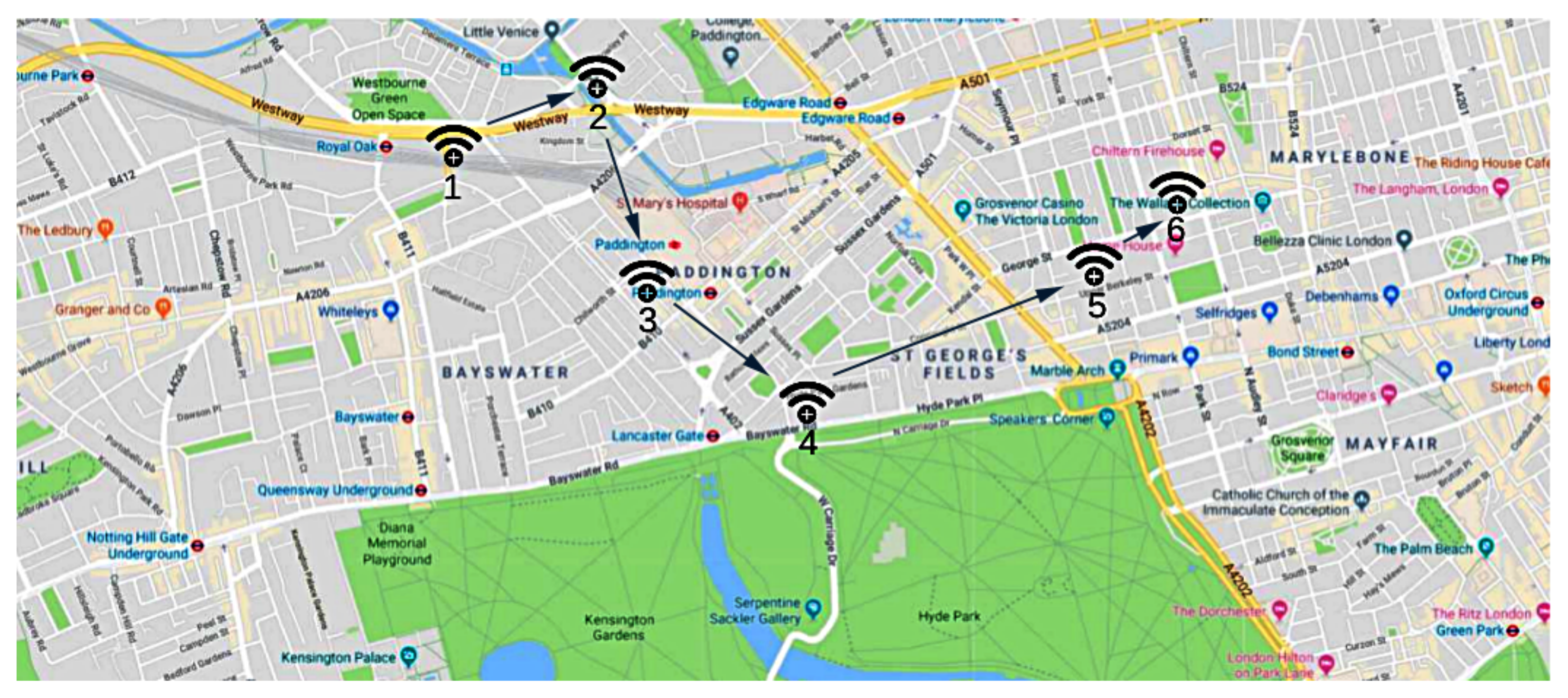
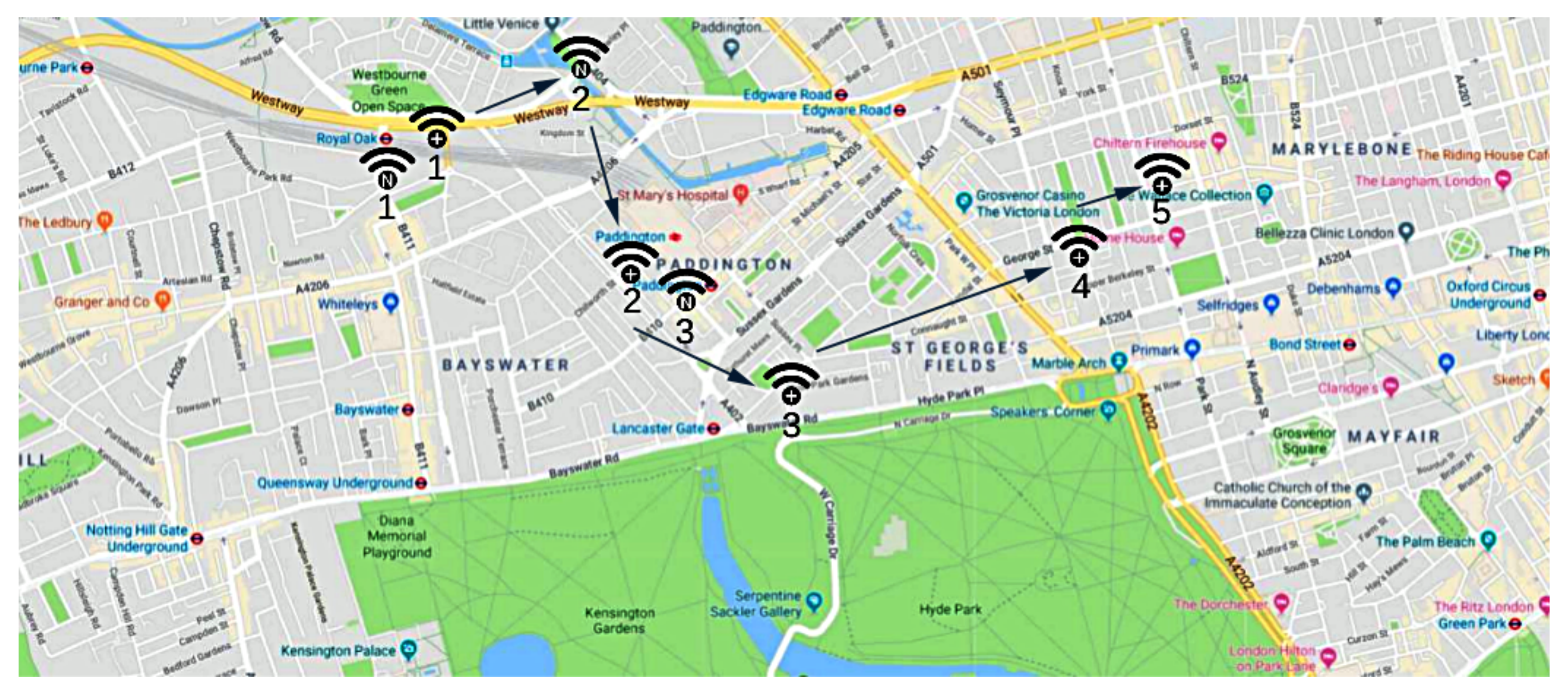
- Direct Tracing: by following this strategy, the movements of an entitye, from its first introduction in the IoE environment, are traced by using the information and in , according to the formalization given in Section 3.Figure 8 shows this process, and presents six detection points l of an entitye, chronologically numbered by using the timestamp information t. In more detail, we first query the blockchain-based distributed ledger to extract all the registrations , and then we number each location (i.e., latitude and longitude) along the chronological sequence given by the timestamp information .More formally, given a series of entity locations , we introduce a Trace Location Set to store all the locations in the chronological order determined by the timestamp information , as formalized in Equation (1).
Algorithm 1 Blockchain-based distributed ledger data gathering. Require:e = Entity, R = Blockchain-based distributed ledger registrations
Ensure: = Registrations related to entity e- 1:
- procedure getEntityRegistrations(e, R)
- 2:
- for each r in R do
- 3:
- 4:
- if then
- 5:
- 6:
- end if
- 7:
- end for
- 8:
- return
- 9:
- end procedure
- The localization resolution is directly related to the e-health device that has detected the entity. We can obtain a high-resolution localization when the e-health device runs a localization service (e.g., GPS) an its location is near the detected entity. Instead, we obtain a low-resolution localization when the localization data are related to another device. For instance, this happens when the e-health device operates in the mobile network but without any active localization service. In this case the location could refer to the mobile network cell.
- 2.
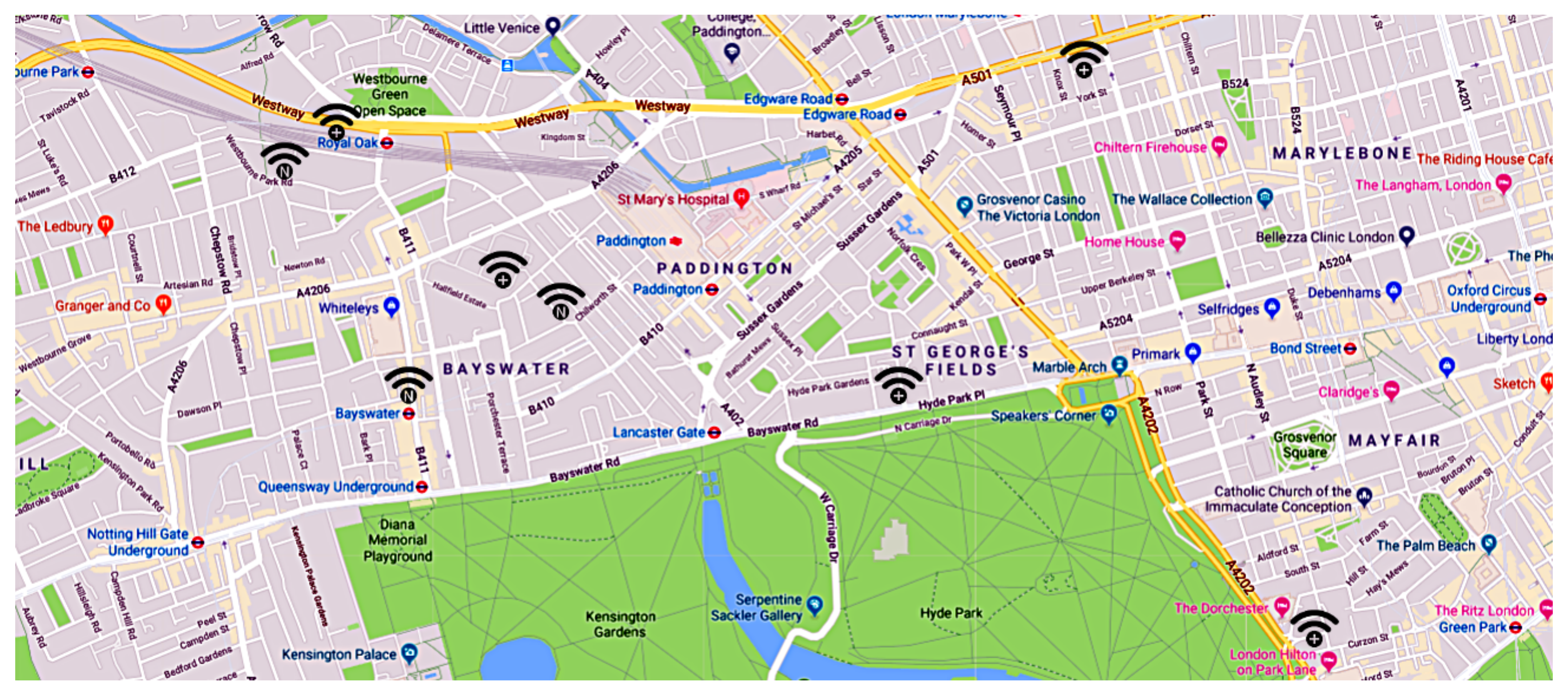
- Interpolate Tracing: in this strategy, we take into account the information , , and in . When applicable, the information contains the other entities detected by the e-health device within seconds from the detection of e (the entity under analysis), as described in Section 3.We exploit the new information to reconstruct the entity movements by interpolating the data with the same data of the entities in (neighbor entities). Figure 9 graphically shows this process, where + denotes the entity under analysis and N a neighbor entity in .In the example of interpolate tracing shown in Figure 9, we can observe how the first localization of the entity + includes a neighbor N that we found another time in the third location of the location chronology of +. This represents a naive example of interpolate tracing, based on the reasonable probability that such a configuration indicates that the neighbor entity is somehow related to the primary entity under analysis, especially when this pattern repeats over time. In other words, it is very likely that in the second localization of N, the entity + was also present and that it has not been detected for some reasons such as, for instance, a temporary e-health device overload, or because the entity device was out of the wireless e-health range. This pattern, repeated over time, could underline interesting connections between entities, as well as the last location of a missing entity.More formally, given the Trace Location Set previously defined and given a series of entity locations , at each location (with ) we extract from the set a subset of valuable neighbor entities by following the criterion in Equation (2).We can generalize the previous criterion by varying the distance between the step (i.e., where we extract the valuable neighbor entities from ) and the previous and next step that we take into account. Denoting as such a distance (i.e., the number of considered locations), we can re-formalize the former criterion as shown in Equation (3).We underline that we do not infringe the privacy of the involved neighbor entities since the entity data are collected anonymously into the blockchain-based distributed ledger.
- 3.
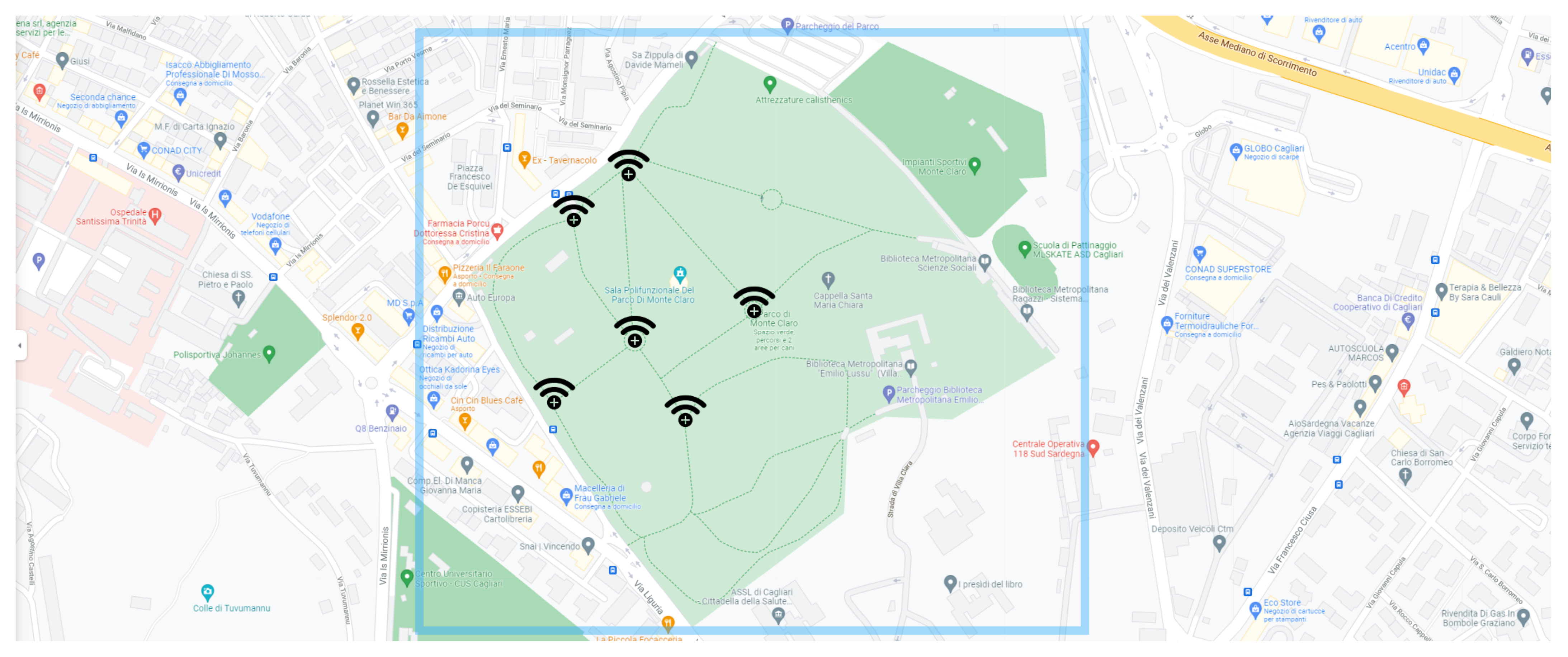
- Spread Tracing: this last baseline criterion exploits all the neighbor entities in , with and , where denotes the entity under analysis.As valuable neighbor entities of , we add all the entities in their locations L have as neighbor entity, as shown in Equation (4).The result can be expressed as the tracing matrix shown in Equation (5), where each row refers to a different valuable entitye. In other words, each matrix-row refers to a different valuable entity e, and it reports the locations l where the entitye has the entity as a neighbor in .After ordering the matrix row elements by location and counting how many entities are involved in each matrix column, we can evaluate the probability that the entitye was in a specific position, although a e-health device has not detected it. Figure 10 graphically shows this criterion, where the grid-size (i.e., square-side) represents a tolerance value, which we denoted as . This means that all the entity detections that occur in the same grid square refer to the same matrix row index (i.e., Equation (5)).
5. Experimental Findings
- (i)
- definition of entities and trackers;
- (ii)
- detection of the entities within the wireless coverage area of the trackers;
- (iii)
- communication of data made by the trackers on a remote blockchain-based distributed ledger;
- (iv)
- localization of entities by applying the baseline strategies formalized in this paper.
5.1. Setup of the Experiments
5.2. Results and Discussion
6. Potential Applications, Limitations and Future Directions
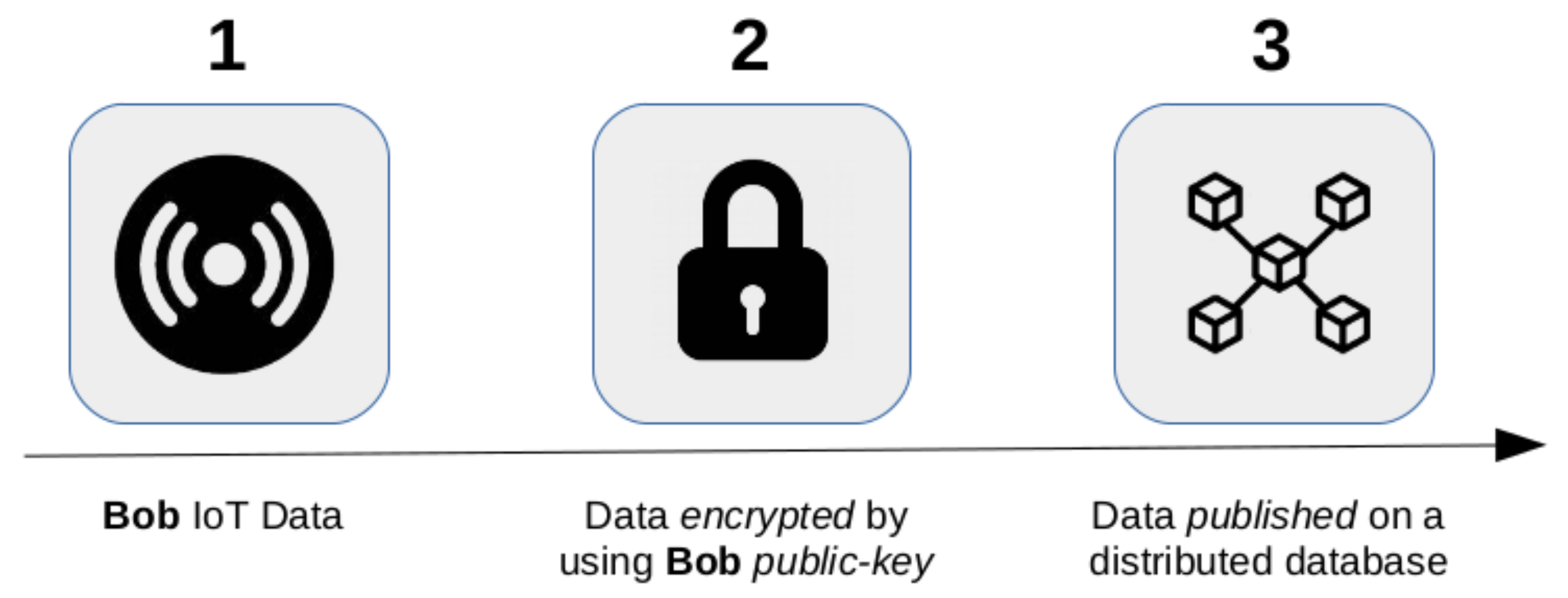
6.1. Secure Payload Storing
6.2. IoE Technology Spread
- (i)
- Designing transparent and straightforward procedures of integration of the needed IoE functionalities in the existing e-health devices. This can be achieved, for instance, by integrating these as a service in the new devices, by recurring to a well-documented firmware/software upgrade process, or by making available an application (in those cases where the trackers or the entities are implemented in devices that allow us this solution, e.g., smartphones, tablets, etc.);
- (ii)
- Making effective campaigns of information aimed to underline the advantages for each user that joins the IoE network, empathizing the gained opportunity to exchange data between a large community of users, a massive amount of valuable data that they can exploit in many contexts, such as that of localization taken into account in this paper;
- (iii)
- Offering benefits to the users that join their devices to the IoE network as trackers, allowing the system to perform the entity detection and the distributed-ledger registration tasks. Such benefits could include the free use of some services related to the IoE network, such as, for instance, the services used for remote data storage.
7. Conclusions
Author Contributions
Funding
Institutional Review Board Statement
Informed Consent Statement
Data Availability Statement
Conflicts of Interest
References
- Bonneau, J.; Miller, A.; Clark, J.; Narayanan, A.; Kroll, J.A.; Felten, E.W. SoK: Research Perspectives and Challenges for Bitcoin and Cryptocurrencies. In Proceedings of the 2015 IEEE Symposium on Security and Privacy, San Jose, CA, USA, 17–21 May 2015; pp. 104–121. [Google Scholar] [CrossRef]
- Nakamoto, S. Bitcoin: A peer-to-peer electronic cash system. Decentralized Bus. Rev. 2008, 21260. [Google Scholar]
- Saia, R.; Carta, S.; Recupero, D.R.; Fenu, G. Internet of entities (ioe): A blockchain-based distributed paradigm for data exchange between wireless-based devices. In Proceedings of the 8th International Conference on Sensor Networks, SENSORNETS, Prague, Czech Republic, 26–27 February 2019; SciTePress: Setúbal, Portugal, 2019; pp. 77–84. [Google Scholar]
- Kaufman, B.; Aazhang, B. Cellular networks with an overlaid device to device network. In Proceedings of the IEEE 42nd Asilomar Conference on Signals, Systems and Computers, Pacific Grove, CA, USA, 26–29 October 2008; pp. 1537–1541. [Google Scholar] [CrossRef]
- Yang, L.T.; Di Martino, B.; Zhang, Q. Internet of everything. Mob. Inf. Syst. 2017, 2017. [Google Scholar] [CrossRef] [Green Version]
- Gerla, M.; Lee, E.K.; Pau, G.; Lee, U. Internet of vehicles: From intelligent grid to autonomous cars and vehicular clouds. In Proceedings of the 2014 IEEE World Forum on Internet of Things (WF-IoT), Seoul, Korea, 6–8 March 2014; pp. 241–246. [Google Scholar]
- Shao, J.; Xie, G.; Wang, L. Leader-following formation control of multiple mobile vehicles. IET Control Theory Appl. 2007, 1, 545–552. [Google Scholar] [CrossRef]
- Danezis, G.; Meiklejohn, S. Centrally banked cryptocurrencies. arXiv 2015, arXiv:1505.06895. [Google Scholar]
- Wood, G. Ethereum: A secure decentralised generalised transaction ledger. Ethereum Proj. Yellow Pap. 2014, 151, 1–32. [Google Scholar]
- Pilkington, M. 11 Blockchain technology: Principles and applications. In Research Handbook on Digital Transformations; Edward Elgar Publishing: Cheltenham, UK, 2016; p. 225. [Google Scholar]
- Kuo, T.T.; Kim, H.E.; Ohno–Machado, L. Blockchain distributed ledger technologies for biomedical and health care applications. J. Am. Med. Inf. Assoc. 2017, 24, 1211–1220. [Google Scholar] [CrossRef] [PubMed] [Green Version]
- Biswas, K.; Muthukkumarasamy, V. Securing smart cities using blockchain technology. In Proceedings of the 2016 IEEE 18th International Conference on High Performance Computing and Communications; IEEE 14th International Conference on Smart City; IEEE 2nd International Conference on Data Science and Systems (HPCC/SmartCity/DSS), Sydney, NSW, Australia, 12–14 December 2016; pp. 1392–1393. [Google Scholar]
- Xu, Q.; Aung, K.M.M.; Zhu, Y.; Yong, K.L. A blockchain-based storage system for data analytics in the internet of things. In New Advances in the Internet of Things; Springer: Cham, Switzerland, 2018; pp. 119–138. [Google Scholar]
- Lin, I.C.; Liao, T.C. A Survey of Blockchain Security Issues and Challenges. IJ Netw. Secur. 2017, 19, 653–659. [Google Scholar]
- Bartoletti, M.; Lande, S.; Podda, A.S. A proof-of-stake protocol for consensus on bitcoin subchains. In Proceedings of the International Conference on Financial Cryptography and Data Security, Sliema, Malta, 3–7 April 2017; pp. 568–584. [Google Scholar]
- Longo, R.; Podda, A.S.; Saia, R. Analysis of a consensus protocol for extending consistent subchains on the bitcoin blockchain. Computation 2020, 8, 67. [Google Scholar] [CrossRef]
- Croman, K.; Decker, C.; Eyal, I.; Gencer, A.E.; Juels, A.; Kosba, A.; Miller, A.; Saxena, P.; Shi, E.; Sirer, E.G. On scaling decentralized blockchains. In Proceedings of the International Conference on Financial Cryptography and Data Security, Christ Church, Barbados, 22–26 February 2016; Springer: Berlin/Heidelberg, Germany, 2016; pp. 106–125. [Google Scholar]
- Abbasi, A.G.; Khan, Z. VeidBlock: Verifiable identity using blockchain and ledger in a software defined network. In Proceedings of the 10th International Conference on Utility and Cloud Computing, Austin, TX, USA, 5 December 2017; pp. 173–179. [Google Scholar]
- Yuan, Y.; Wang, F.Y. Towards blockchain-based intelligent transportation systems. In Proceedings of the 2016 IEEE 19th International Conference on Intelligent Transportation Systems (ITSC), Rio de Janeiro, Brazil, 1–4 November 2016; pp. 2663–2668. [Google Scholar]
- Muftic, S. Blockchain Identity Management System Based on Public Identities Ledger. US Patent 9,635,000, 25 April 2017. [Google Scholar]
- Ainsworth, R.T.; Shact, A. Blockchain (distributed ledger technology) solves VAT fraud. Boston Univ. Sch. Law Law Econ. Res. Pap. 2016, 16–41. [Google Scholar] [CrossRef] [Green Version]
- Reyna, A.; Martín, C.; Chen, J.; Soler, E.; Díaz, M. On blockchain and its integration with IoT. Challenges and opportunities. Future Gen. Comput. Syst. 2018, 88, 173–190. [Google Scholar] [CrossRef]
- Saia, R.; Carta, S.; Recupero, D.R. A Probabilistic-driven Ensemble Approach to Perform Event Classification in Intrusion Detection System. In Proceedings of the 10th International Joint Conference on Knowledge Discovery, Knowledge Engineering and Knowledge Management, KDIR, Seville, Spain, 18–20 September 2018; SciTePress: Setúbal, Portugal, 2018; pp. 139–214. [Google Scholar]
- Carta, S.; Medda, A.; Pili, A.; Recupero, D.R.; Saia, R. Forecasting e-commerce products prices by combining an autoregressive integrated moving average (ARIMA) model and google trends data. Future Internet 2019, 11, 5. [Google Scholar] [CrossRef] [Green Version]
- Saia, R.; Carta, S. Evaluating the benefits of using proactive transformed-domain-based techniques in fraud detection tasks. In Future Generation Computer Systems; Elsevier: Amsterdam, The Netherlands, 2019; pp. 18–32. [Google Scholar]
- Bilge, L.; Strufe, T.; Balzarotti, D.; Kirda, E. All your contacts are belong to us: Automated identity theft attacks on social networks. In Proceedings of the 18th International Conference on World Wide Web, Madrid, Spain, 20–24 April 2009; pp. 551–560. [Google Scholar]
- Arachchilage, N.A.G.; Love, S.; Beznosov, K. Phishing threat avoidance behaviour: An empirical investigation. Comput. Hum. Behav. 2016, 60, 185–197. [Google Scholar] [CrossRef] [Green Version]
- Mouton, F.; Leenen, L.; Venter, H.S. Social engineering attack examples, templates and scenarios. Comput. Secur. 2016, 59, 186–209. [Google Scholar] [CrossRef] [Green Version]
- Liu, P.; LaPorta, T.F.; Kotapati, K. Cellular Network Security. In Computer and Information Security Handbook; Elsevier: Amsterdam, The Netherlands, 2009; pp. 183–203. [Google Scholar]
- Traynor, P.; Enck, W.; McDaniel, P.; Porta, T.L. Mitigating attacks on open functionality in SMS-capable cellular networks. IEEE/ACM Trans. Netw. 2009, 17, 40–53. [Google Scholar] [CrossRef]
- Firoozjaei, M.D.; Yu, J.; Choi, H.; Kim, H. Privacy-preserving nearest neighbor queries using geographical features of cellular networks. Comput. Commun. 2017, 98, 11–19. [Google Scholar] [CrossRef]
- Moore, T. The promise and perils of digital currencies. IJCIP 2013, 6, 147–149. [Google Scholar] [CrossRef]
- Courtois, N.T.; Bahack, L. On subversive miner strategies and block withholding attack in bitcoin digital currency. arXiv 2014, arXiv:1402.1718. [Google Scholar]
- Eyal, I.; Sirer, E.G. Majority is not enough: Bitcoin mining is vulnerable. Commun. ACM 2018, 61, 95–102. [Google Scholar] [CrossRef]
- Bartoletti, M.; Pompianu, L.; Bellomy, B. A journey into Bitcoin metadata. J. Grid Comput. 2018, 17, 3–22. [Google Scholar] [CrossRef]
- Bartoletti, M.; Pompianu, L. An analysis of Bitcoin OP_RETURN metadata. In Proceedings of the Financial Cryptography Workshops, LNCS, Sliema, Malta, 7 April 2017; Springer: Berlin/Heidelberg, Germany, 2017; Volume 10323, pp. 218–230. [Google Scholar]
- Cachin, C. Architecture of the hyperledger blockchain fabric. In Proceedings of the Workshop on Distributed Cryptocurrencies and Consensus Ledgers, Chicago, IL, USA, 25 July 2016. [Google Scholar]
- Podda, A.S.; Pompianu, L. An overview of blockchain-based systems and smart contracts for digital coupons. In Proceedings of the IEEE/ACM 42nd International Conference on Software Engineering Workshops, Seoul, Korea, 27 June–19 July 2020; pp. 770–778. [Google Scholar]
- Perboli, G.; Musso, S.; Rosano, M. Blockchain in logistics and supply chain: A lean approach for designing real-world use cases. IEEE Access 2018, 6, 62018–62028. [Google Scholar] [CrossRef]
- Chang, S.E.; Chen, Y.C.; Lu, M.F. Supply chain re-engineering using blockchain technology: A case of smart contract based tracking process. In Technological Forecasting and Social Change; Elsevier: Amsterdam, The Netherlands, 2019; pp. 1–11. [Google Scholar]
- Shah, D.; Patel, D.; Adesara, J.; Hingu, P.; Shah, M. Exploiting the capabilities of blockchain and machine learning in education. In Augmented Human Research; Springer: Berlin/Heidelberg, Germany, 2021; pp. 1–12. [Google Scholar]
- Chen, J.; Wang, W.; Zhou, Y.; Ahmed, S.; Syed, H.; Wei, W. Exploiting 5G and blockchain for medical applications of drones. IEEE Netw. 2021, 35, 30–36. [Google Scholar] [CrossRef]
- Jones, A.R.; Quah, E.E.L.; Nielsen, D.J.; Eminovic, L. Creating a Globally Unique Identifier of a Subscriber Device. US Patent 8,213,935, 3 July 2012. [Google Scholar]
- Leach, P.; Mealling, M.; Salz, R. A universally unique identifier (uuid) urn namespace. RFC 2005, 4122, 1–32. [Google Scholar] [CrossRef]
- Mironov, I. Hash functions: Theory, attacks, and applications. Microsoft Res. Silicon Val. Campus. Noviembre De 2005. [Google Scholar]
- Manku, G.S.; Bawa, M.; Raghavan, P. Symphony: Distributed Hashing in a Small World. In Proceedings of the USENIX Symposium on Internet Technologies and Systems, Seattle, WA, USA, 26–28 March 2003; p. 10. [Google Scholar]
- Al-Sarawi, S.; Anbar, M.; Alieyan, K.; Alzubaidi, M. Internet of Things (IoT) communication protocols. In Proceedings of the 2017 8th International Conference on Information Technology (ICIT), Odisha, India, 21–23 December 2017; pp. 685–690. [Google Scholar]
- Uzcátegui, R.A.; De Sucre, A.J.; Acosta-Marum, G. Wave: A tutorial. IEEE Commun. Mag. 2009, 47, 126–133. [Google Scholar] [CrossRef]
- Gomez, C.; Oller, J.; Paradells, J. Overview and evaluation of bluetooth low energy: An emerging low-power wireless technology. Sensors 2012, 12, 11734–11753. [Google Scholar] [CrossRef]
- Mulligan, G. The 6LoWPAN architecture. In Proceedings of the 4th Workshop on Embedded Networked Sensors, Cork, Ireland, 25–26 June 2007; ACM: New York, NY, USA, 2007; pp. 78–82. [Google Scholar]
- Kuzlu, M.; Pipattanasomporn, M.; Rahman, S. Review of communication technologies for smart homes/building applications. In Proceedings of the Innovative Smart Grid Technologies-Asia (ISGT ASIA), Bangkok, Thailand, 3–6 November 2015; pp. 1–6. [Google Scholar]
- Kinney, P. Zigbee technology: Wireless control that simply works. Commun. Des. Conf. 2003, 2, 1–7. [Google Scholar]
- Cerruela García, G.; Luque Ruiz, I.; Gómez-Nieto, M.Á. State of the art, trends and future of Bluetooth low energy, near field communication and visible light communication in the development of smart cities. Sensors 2016, 16, 1968. [Google Scholar] [CrossRef]
- Jia, X.; Feng, Q.; Fan, T.; Lei, Q. RFID technology and its applications in Internet of Things (IoT). In Proceedings of the 2012 2nd International Conference on Consumer Electronics, Communications and Networks (CECNet), Yichang, China, 21–23 April 2012; pp. 1282–1285. [Google Scholar]
- Raza, U.; Kulkarni, P.; Sooriyabandara, M. Low power wide area networks: An overview. IEEE Commun. Surv. Tutor. 2017, 19, 855–873. [Google Scholar] [CrossRef] [Green Version]
- Novo, O.; Beijar, N.; Ocak, M.; Kjällman, J.; Komu, M.; Kauppinen, T. Capillary networks-bridging the cellular and iot worlds. In Proceedings of the 2015 IEEE 2nd World Forum on Internet of Things (WF-IoT), Milan, Italy, 14–16 December 2015; pp. 571–578. [Google Scholar]
- Simmons, G.J. Symmetric and asymmetric encryption. ACM Comput. Surv. (CSUR) 1979, 11, 305–330. [Google Scholar] [CrossRef]
- Bakhtiari, S.; Safavi-Naini, R.; Pieprzyk, J. Cryptographic Hash Functions: A Survey; Technical Report 95–09; Department of Computer Science, University of Wollongong: Wollongong, Australia, 1995; Volume 4. [Google Scholar]
- Rivest, R. The MD4 message-digest algorithm. Conf. Theory Appl. Cryptogr. 1990, 11, 303–311. [Google Scholar]
- Bellare, M.; Rogaway, P. Optimal asymmetric encryption. In Proceedings of the Workshop on the Theory and Application of Cryptographic Techniques, Perugia, Italy, 9–12 May 1994; Springer: Berlin/Heidelberg, Germany, 1994; pp. 92–111. [Google Scholar]
- Mendel, F.; Rijmen, V. Cryptanalysis of the Tiger hash function. In Proceedings of the International Conference on the Theory and Application of Cryptology and Information Security, Kuching, Malaysia, 2–6 December 2007; Springer: Berlin/Heidelberg, Germany, 2007; pp. 536–550. [Google Scholar]
- Stallings, W. The Whirlpool secure hash function. Cryptologia 2006, 30, 55–67. [Google Scholar] [CrossRef]
- Tseng, L.; Yao, X.; Otoum, S.; Aloqaily, M.; Jararweh, Y. Blockchain-based database in an IoT environment: Challenges, opportunities, and analysis. Clust. Comput. 2020, 23, 2151–2165. [Google Scholar] [CrossRef]
- Carrara, G.R.; Burle, L.M.; Medeiros, D.S.; de Albuquerque, C.V.N.; Mattos, D.M. Consistency, availability, and partition tolerance in blockchain: A survey on the consensus mechanism over peer-to-peer networking. Ann. Telecommun. 2020, 75, 163–174. [Google Scholar] [CrossRef]
- Iqbal, M.; Matulevičius, R. Comparison of blockchain-based solutions to mitigate data tampering security risk. In Proceedings of the International Conference on Business Process Management, Vienna, Austria, 1–6 September 2019; Springer: Cham, Switzerland, 2019; pp. 13–28. [Google Scholar]
- Raikwar, M.; Gligoroski, D.; Kralevska, K. SoK of used cryptography in blockchain. IEEE Access 2019, 7, 148550–148575. [Google Scholar] [CrossRef]
- Hao, K.; Xin, J.; Wang, Z.; Cao, K.; Wang, G. Blockchain-based outsourced storage schema in untrusted environment. IEEE Access 2019, 7, 122707–122721. [Google Scholar] [CrossRef]
- Huang, B.; Zhang, R.; Lu, Z.; Zhang, Y.; Wu, J.; Zhan, L.; Hung, P.C. BPS: A reliable and efficient pub/sub communication model with blockchain-enhanced paradigm in multi-tenant edge cloud. J. Parallel Distrib. Comput. 2020, 143, 167–178. [Google Scholar] [CrossRef]
- Kranz, M. Industrial applications are the juicy part of the Internet of Things. Lond. Sch. Econ. Political Sci. 2017. [Google Scholar]
| Wireless | Frequency | Data | Operative | Power | Security | Literature |
|---|---|---|---|---|---|---|
| Technology | Range | Rate | Range | Consumption | Protocols | Reference |
| BLE | 2.4 GHz | 1 MBps | 15 ÷ 30 m | low | E0, Stream, AES-128 | [49] |
| 6LoWPAN | 868 MHz ÷ 2.4 GHz | 250 KBps | 10 ÷ 100 m | low | AES | [50] |
| Z-Wave | 868 MHz ÷ 908 MHz | 40 KBps | 30 ÷ 100 m | low | AES-128 | [51] |
| ZigBee | 2.4 GHz | 250 KBps | 10 ÷ 100 m | low | AES | [52] |
| NFC | 868 MHz ÷ 902 MHz | 106 ÷ 424 KBps | 0 ÷ 1 m | Ultra-low | RC4 | [53] |
| RFID | 125 KHz ÷ 928 MHz | 4 MBps | 0 ÷ 200 m | Ultra-low | RSA, AES | [54] |
| SigFox | 125 KHz ÷ 860 MHz | 100 ÷ 600 Bps | 10 ÷ 50 Km | low | no-specific | [55] |
| 2G/3G | 380 MHz ÷ 1.9 GHz | 10 MBps | Several Kms | High | RC4 | [56] |
| Experiment | Number | Number | Number | Average | Ethereum | Litecoin | Binance |
|---|---|---|---|---|---|---|---|
| of | of | of | Communication Time | Average Cost per | Average Cost per | Average Cost per | |
| Identifier | Entities | Trackers | Detections | per Tracker (s) | Tracker (USD) | Tracker (USD) | Tracker (USD) |
| 1 | 6 | 2 | 3 | 7.88 | 11.10 | 0.02 | 0.41 |
| 2 | 6 | 4 | 7 | 9.19 | 12.95 | 0.03 | 0.47 |
| 3 | 6 | 6 | 10 | 8.75 | 12.33 | 0.03 | 0.45 |
| 4 | 8 | 2 | 5 | 13.13 | 18.50 | 0.04 | 0.68 |
| 5 | 8 | 4 | 10 | 13.13 | 18.50 | 0.04 | 0.68 |
| 6 | 8 | 6 | 14 | 12.25 | 17.27 | 0.04 | 0.63 |
| 7 | 10 | 2 | 6 | 15.75 | 22.20 | 0.05 | 0.81 |
| 8 | 10 | 4 | 14 | 18.38 | 25.90 | 0.06 | 0.95 |
| 9 | 10 | 6 | 19 | 16.63 | 23.43 | 0.05 | 0.86 |
| Experiment | Number | Number | Number | Average | Ethereum | Litecoin | Binance |
|---|---|---|---|---|---|---|---|
| of | of | of | Communication Time | Average Cost per | Average Cost per | Average Cost per | |
| Identifier | Entities | Trackers | Detections | per Tracker (s) | Tracker (USD) | Tracker (USD) | Tracker (USD) |
| 10 | 6 | 2 | 6 | 15.75 | 22.20 | 0.05 | 0.81 |
| 11 | 6 | 4 | 13 | 17.06 | 24.05 | 0.05 | 0.88 |
| 12 | 6 | 6 | 19 | 16.63 | 23.43 | 0.05 | 0.86 |
| 13 | 8 | 2 | 9 | 23.63 | 33.30 | 0.07 | 1.22 |
| 14 | 8 | 4 | 18 | 23.63 | 33.30 | 0.07 | 1.22 |
| 15 | 8 | 6 | 25 | 21.88 | 30.83 | 0.07 | 1.13 |
| 16 | 10 | 2 | 12 | 31.50 | 44.40 | 0.10 | 1.62 |
| 17 | 10 | 4 | 25 | 32.81 | 46.25 | 0.10 | 1.69 |
| 18 | 10 | 6 | 35 | 30.63 | 43.17 | 0.09 | 1.58 |
Publisher’s Note: MDPI stays neutral with regard to jurisdictional claims in published maps and institutional affiliations. |
© 2021 by the authors. Licensee MDPI, Basel, Switzerland. This article is an open access article distributed under the terms and conditions of the Creative Commons Attribution (CC BY) license (https://creativecommons.org/licenses/by/4.0/).
Share and Cite
Saia, R.; Podda, A.S.; Pompianu, L.; Reforgiato Recupero, D.; Fenu, G. A Blockchain-Based Distributed Paradigm to Secure Localization Services. Sensors 2021, 21, 6814. https://doi.org/10.3390/s21206814
Saia R, Podda AS, Pompianu L, Reforgiato Recupero D, Fenu G. A Blockchain-Based Distributed Paradigm to Secure Localization Services. Sensors. 2021; 21(20):6814. https://doi.org/10.3390/s21206814
Chicago/Turabian StyleSaia, Roberto, Alessandro Sebastian Podda, Livio Pompianu, Diego Reforgiato Recupero, and Gianni Fenu. 2021. "A Blockchain-Based Distributed Paradigm to Secure Localization Services" Sensors 21, no. 20: 6814. https://doi.org/10.3390/s21206814
APA StyleSaia, R., Podda, A. S., Pompianu, L., Reforgiato Recupero, D., & Fenu, G. (2021). A Blockchain-Based Distributed Paradigm to Secure Localization Services. Sensors, 21(20), 6814. https://doi.org/10.3390/s21206814










