Denial-of-Service Attack on IEC 61850-Based Substation Automation System: A Crucial Cyber Threat towards Smart Substation Pathways
Abstract
1. Introduction
2. IEC 61850: Linking Digital Substation Era
2.1. Communication Standards towards SAS
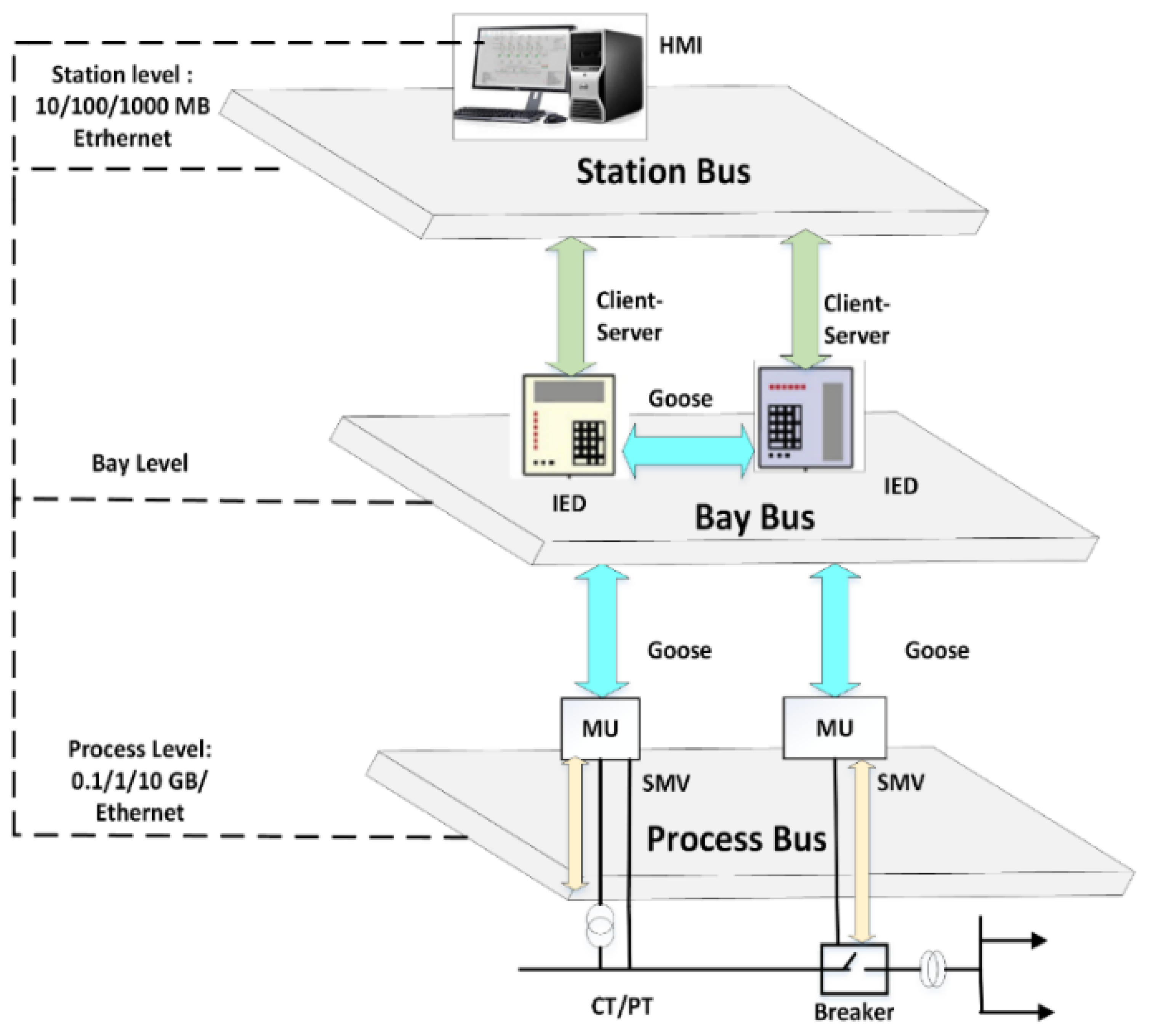
2.2. Communication Architecture and Its Three Levels
2.3. Transmission Protocols for IEC 61850
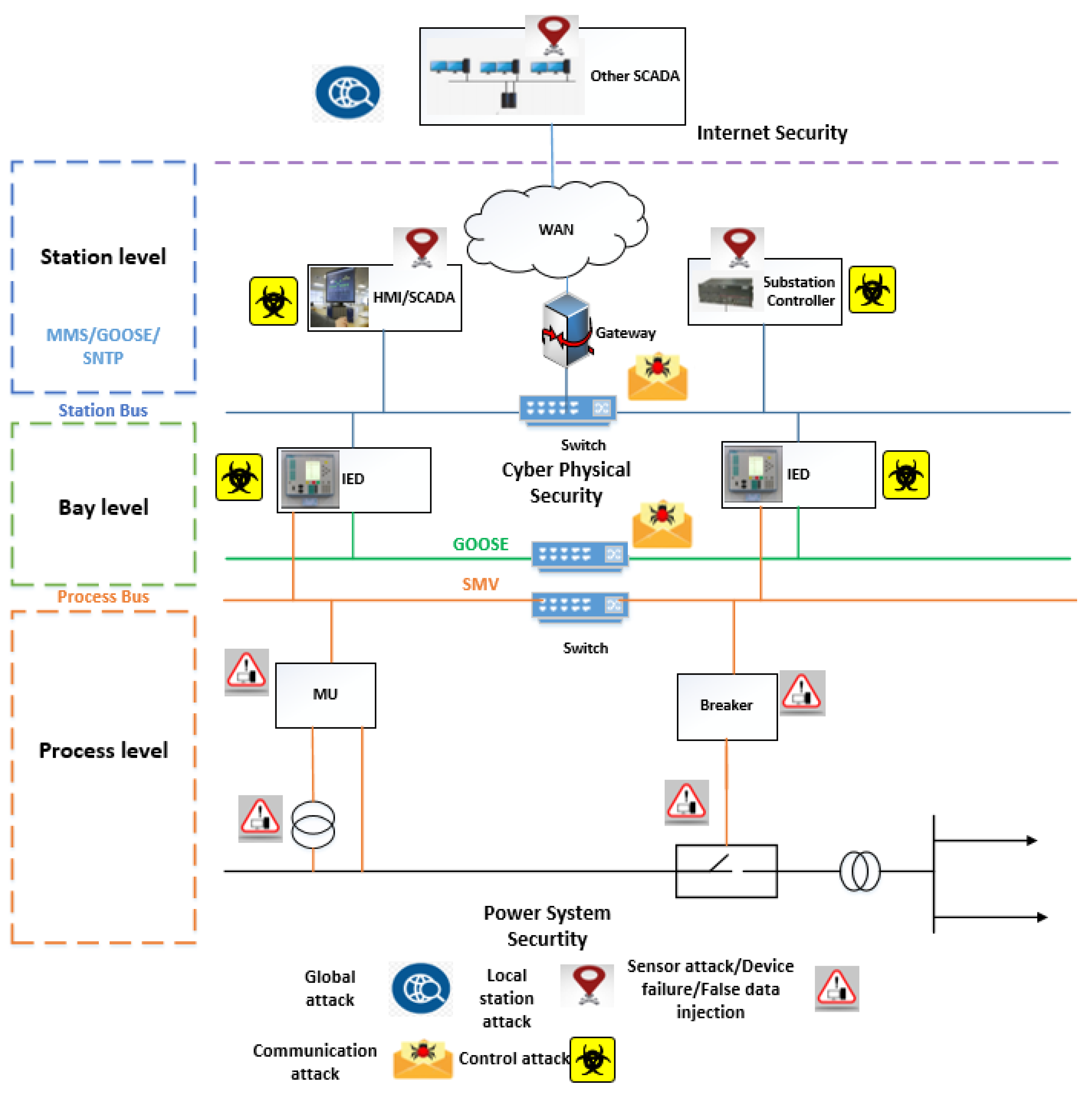
3. Security Attacks on IEC 61850—A DoS Attack on Substation
3.1. DoS Attack on Substation—A Definition
3.2. DoS Attacks—IEDs, FTP, SYN-Flood
3.3. Other Forms of DoS Attacks—Exploitation of GOOSE and SMV
4. Results and Discussion
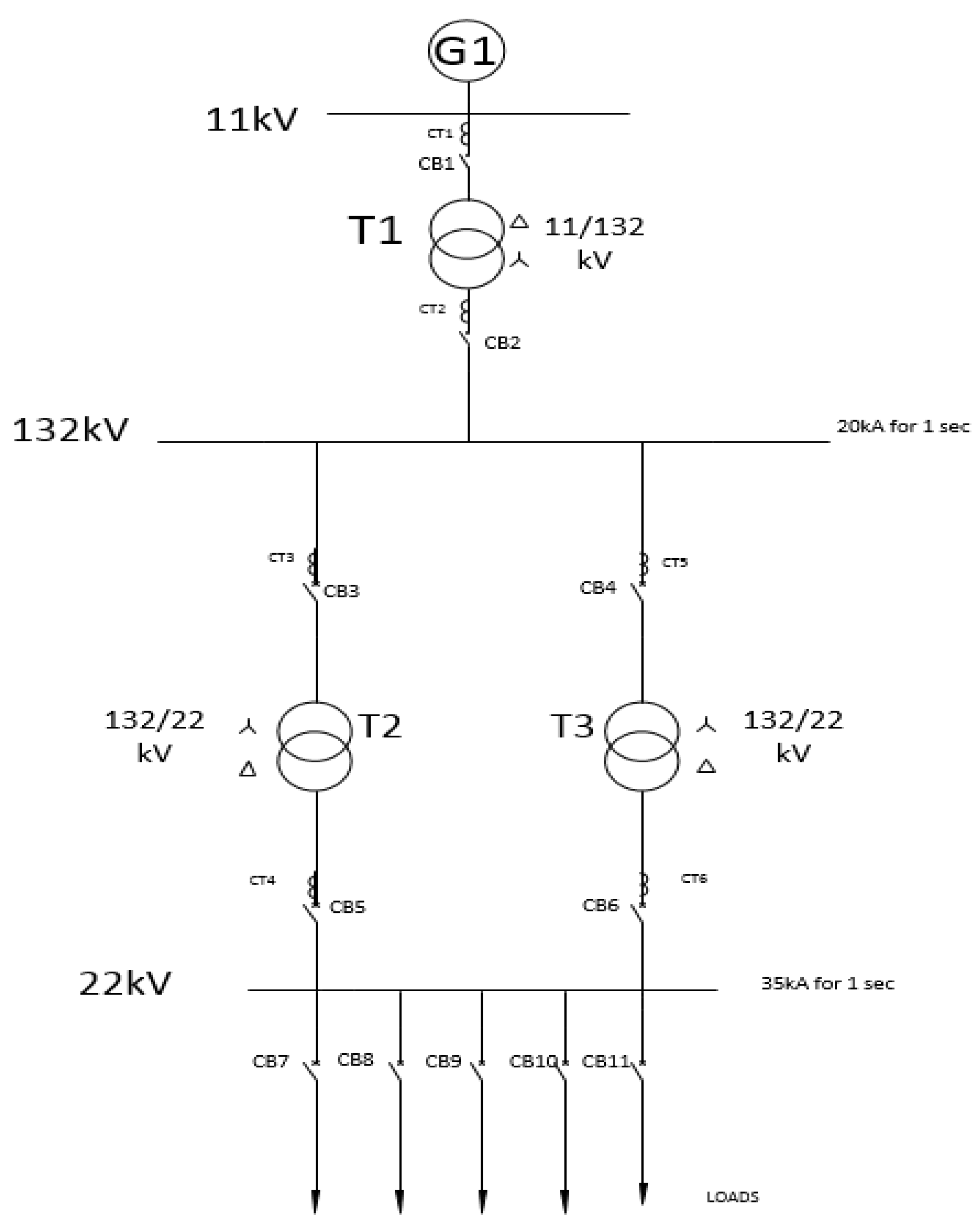
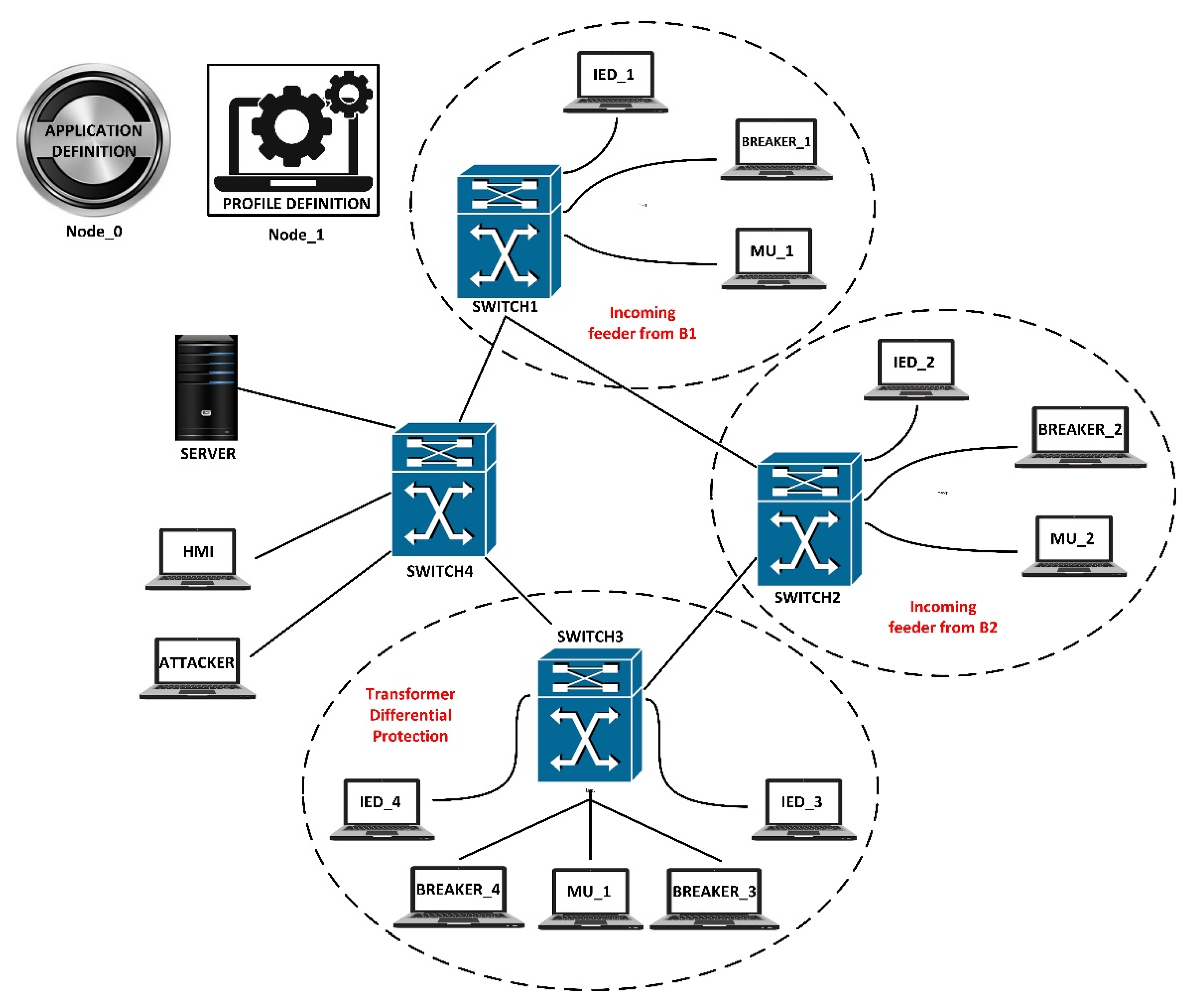
4.1. Test Case
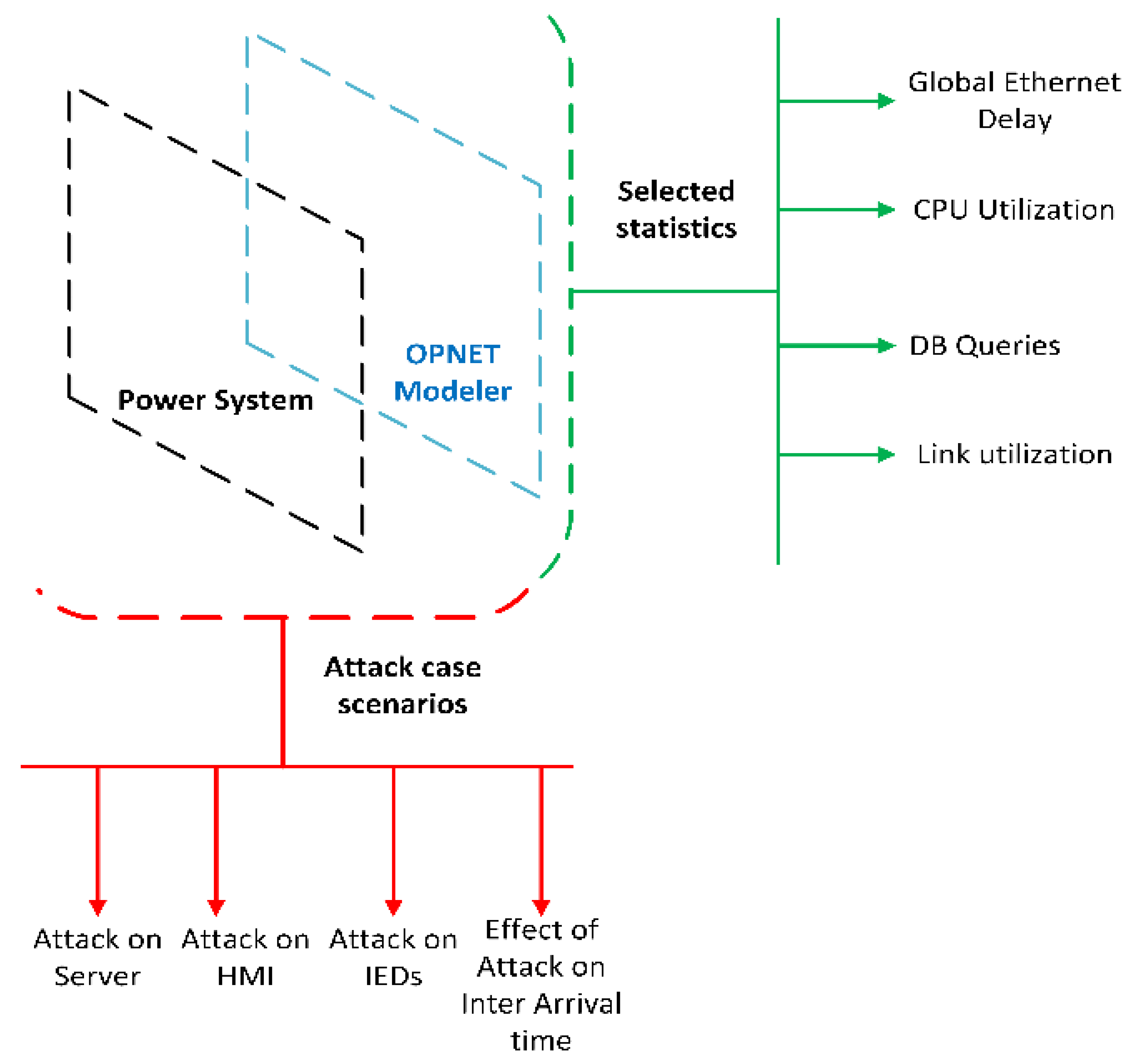
4.2. OPNET Network
4.3. Components of the OPNET Model and Their Functions
4.4. Case Studies
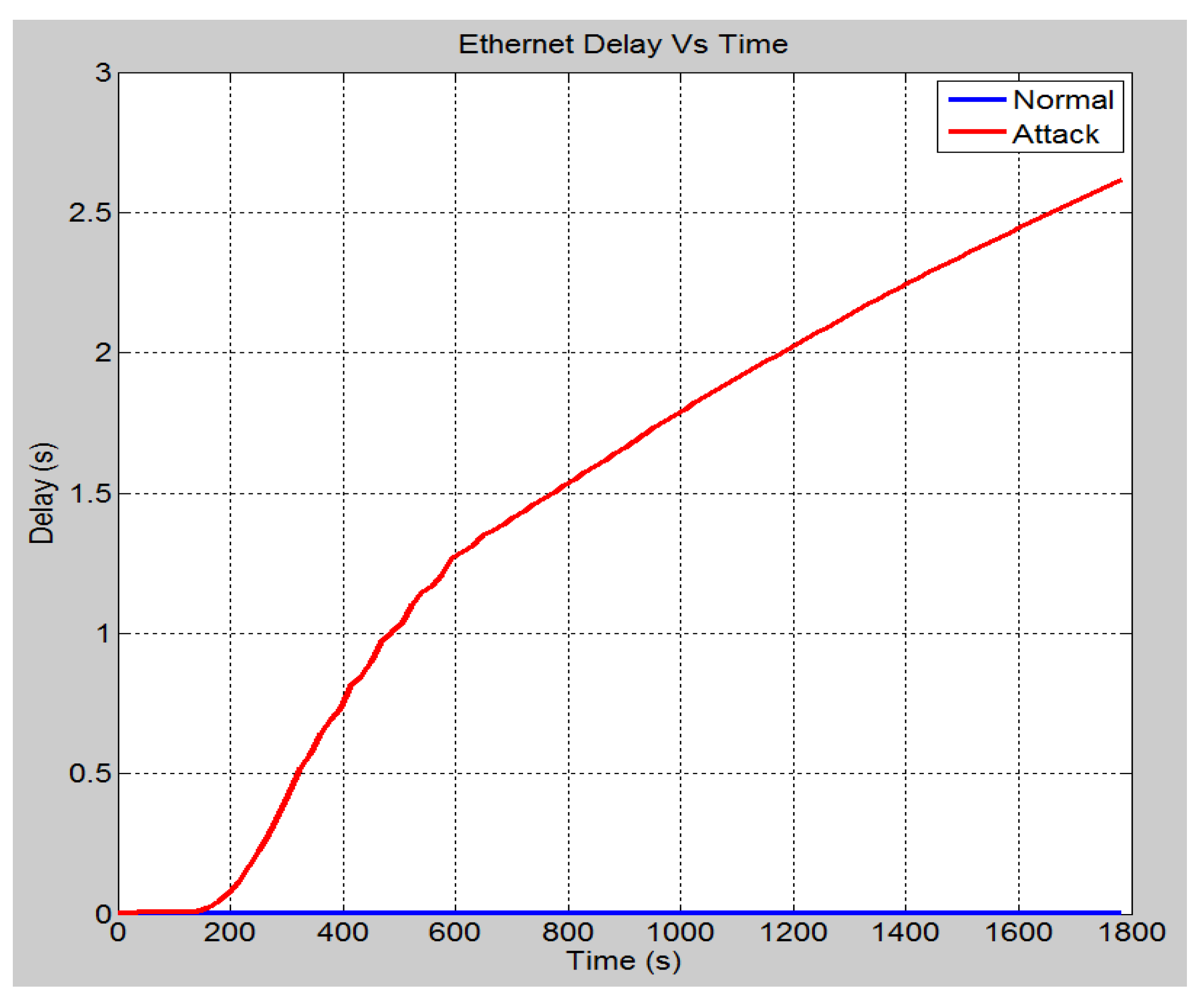
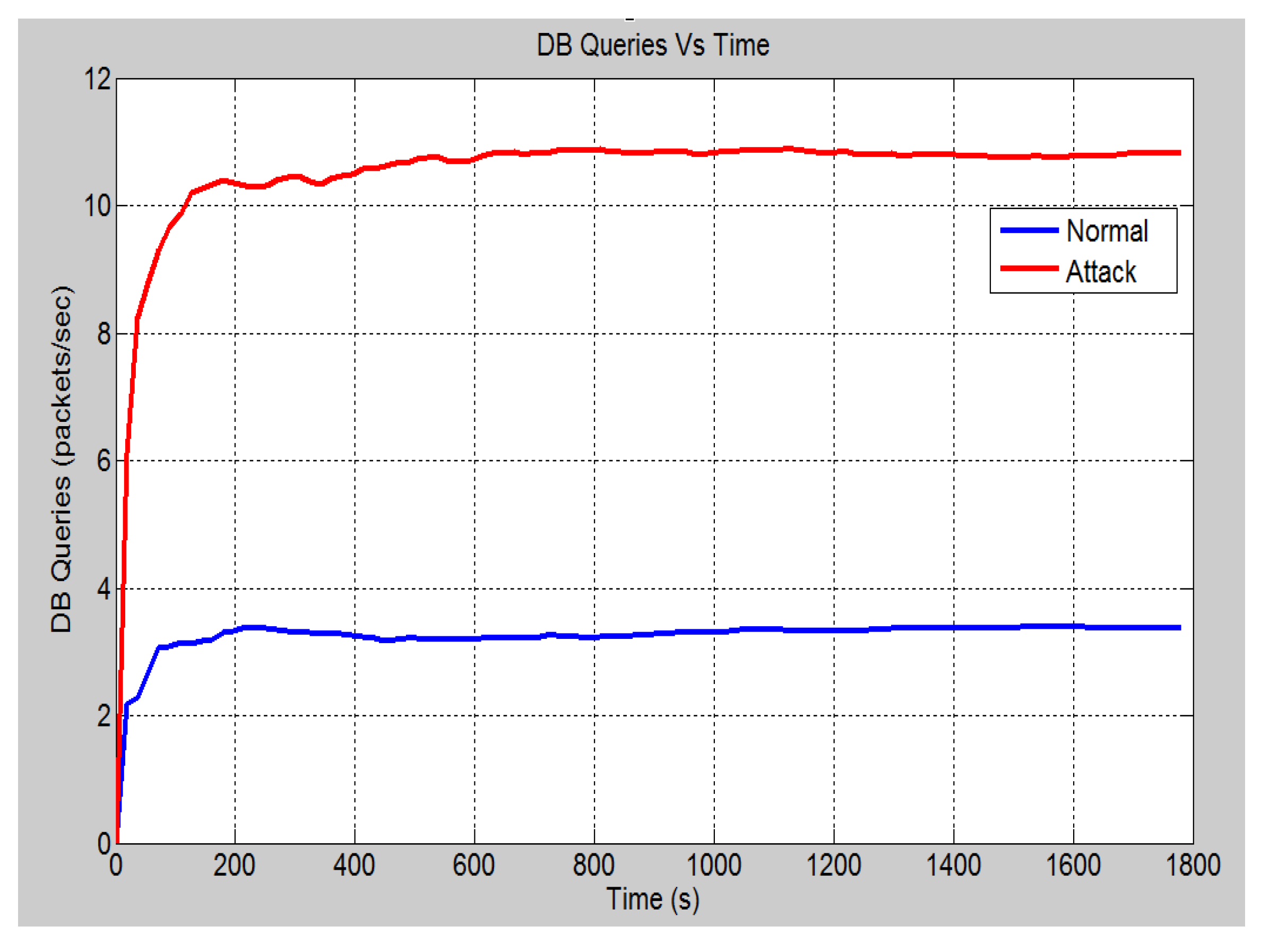
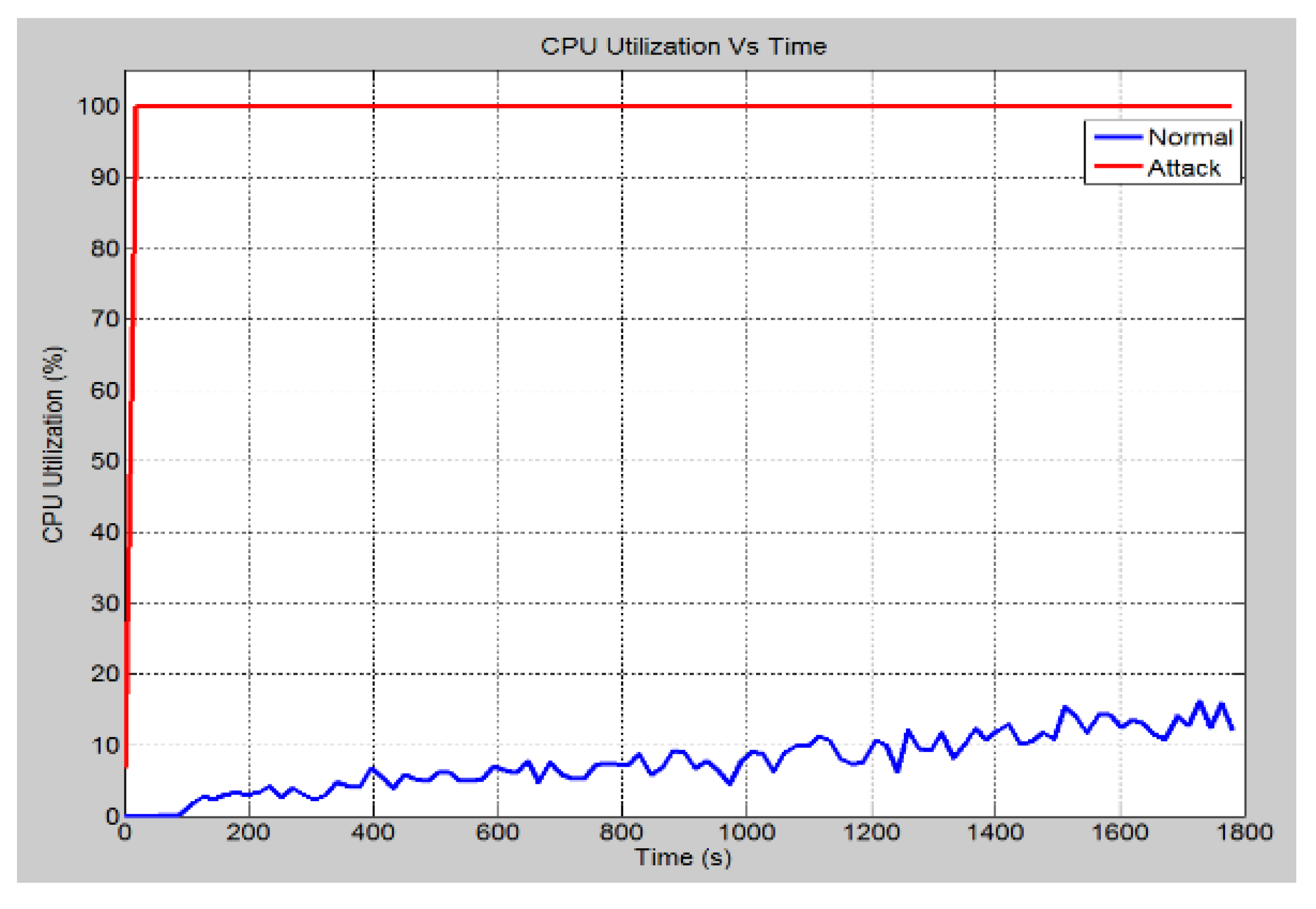
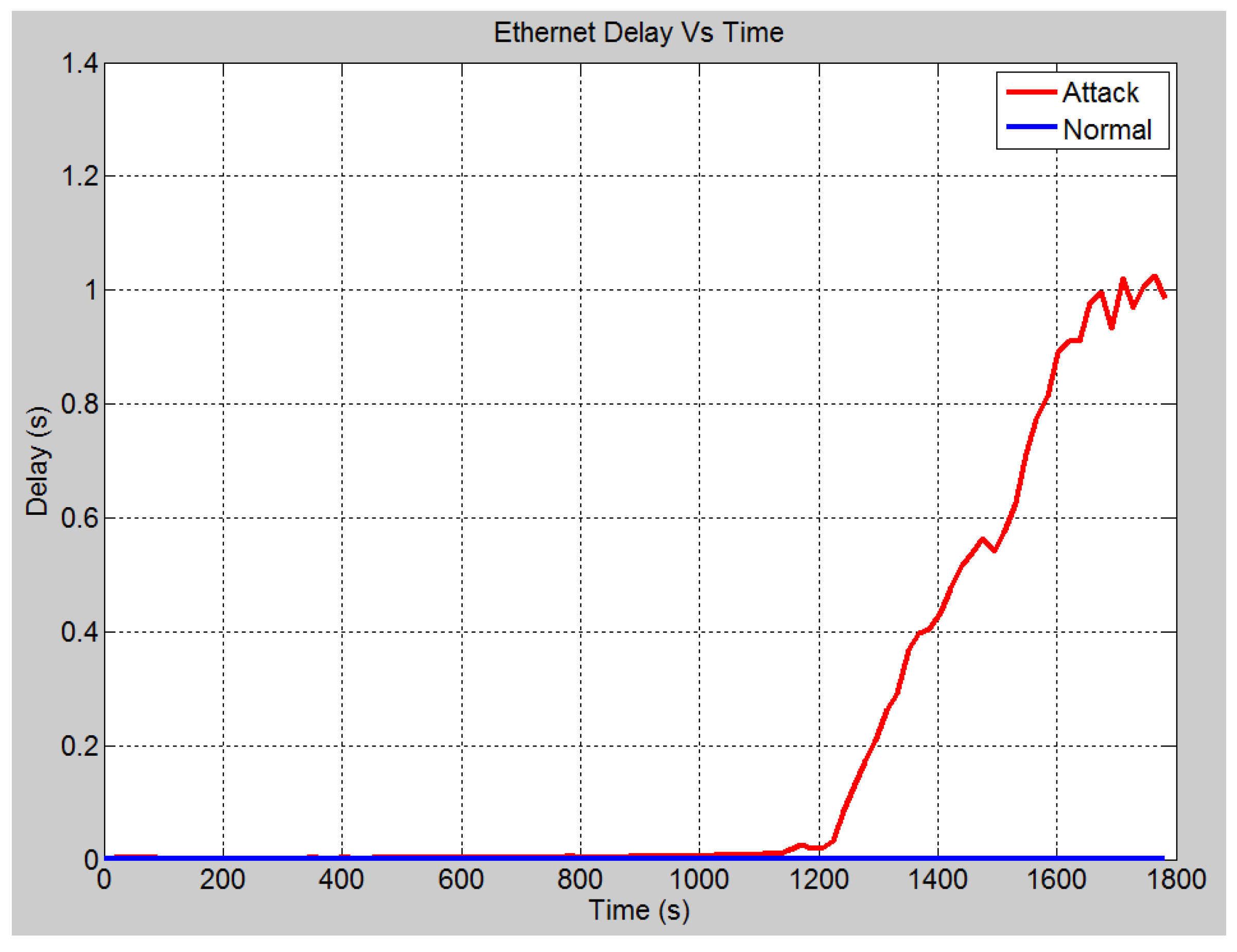
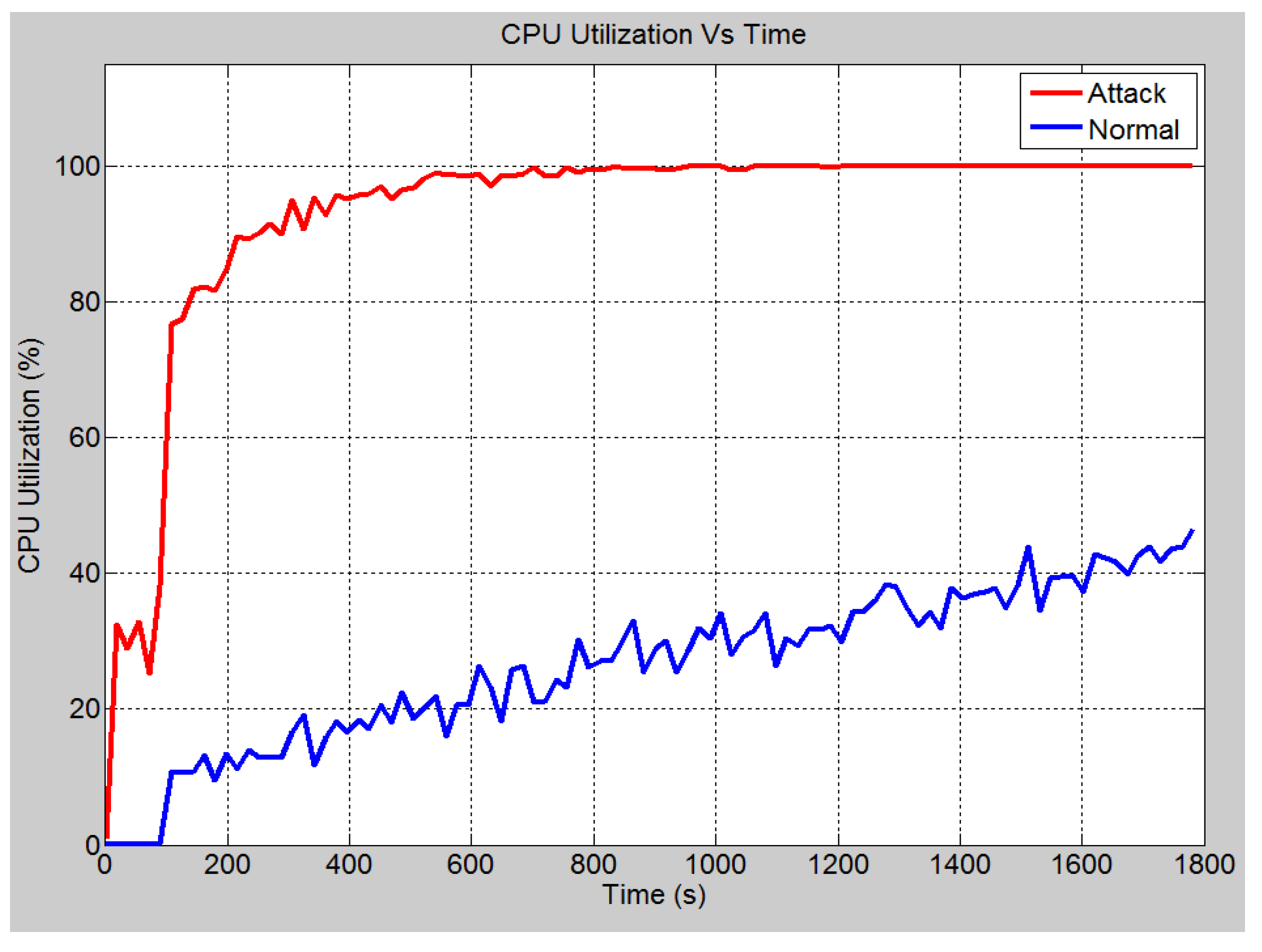
4.4.1. Case 1: DOS Attack on Server
4.4.2. Case 2: DoS Attack on HMI
4.4.3. Case 3: DoS Attack on IEDs
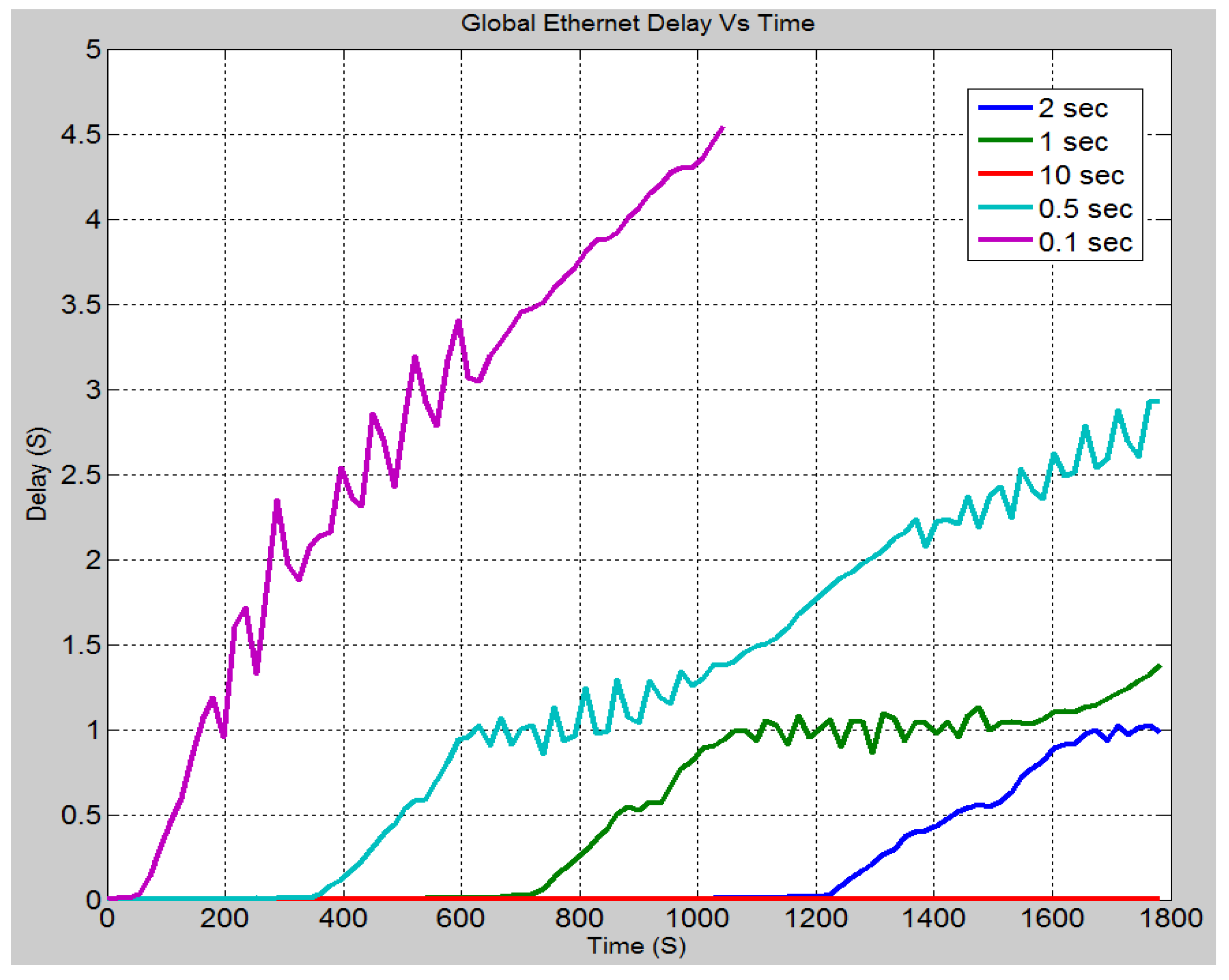
4.4.4. Case 4: Effect of Varying Inter-Arrival Times
5. Conclusions
Author Contributions
Funding
Institutional Review Board Statement
Informed Consent Statement
Data Availability Statement
Conflicts of Interest
References
- Greer, C.; Wollman, D.A.; Prochaska, D.E.; Boynton, P.A.; Mazer, J.A.; Nguyen, C.; Fitzpatrick, G.J.; Nelson, T.L.; Koepke, G.H.; Hefner, A.R., Jr. NIST Framework and Roadmap for Smart Grid Interoperability Standards, Release 3.0; Special Publication (NIST SP): Gaithersburg, MD, USA, 2014. [Google Scholar]
- Case, D.U. Analysis of the Cyber-Attack on the Ukrainian Power Grid. Available online: https://africautc.org/wp-content/uploads/2018/05/E-ISAC_SANS_Ukraine_DUC_5.pdf (accessed on 23 September 2021).
- Lars Fischer, M.U.O.; Morrill, D.; Döring, M.; Haesen, E. Study on the Evaluation of Risks of Cyber-Incidents and on Costs of Preventing Cyber-Incidents in the Energy Sector; European Commission: Berlin, Germany, 2018. [Google Scholar]
- NIST, U. Guidelines for Smart Grid Cyber Security (vol. 1 to 3); NIST IR: Gaithersburg, MD, USA, 2010. [Google Scholar]
- Mackiewicz, R.E. Overview of IEC 61850 and Benefits. In Proceedings of the 2006 IEEE Power Engineering Society General Meeting, Montreal, QC, Canada, 18–22 June 2006; p. 8. [Google Scholar]
- Cai, Y.; Chen, Y.; Li, Y.; Cao, Y.; Zeng, X. Reliability Analysis of Cyber–Physical Systems: Case of the Substation Based on the IEC 61850 Standard in China. Energies 2018, 11, 2589. [Google Scholar] [CrossRef]
- Hong, J.; Liu, C.-C.; Govindarasu, M. Integrated anomaly detection for cyber security of the substations. IEEE Trans. Smart Grid 2014, 5, 1643–1653. [Google Scholar] [CrossRef]
- Farquharson, J.; Wang, A.; Howard, J. Smart Grid Cyber Security and substation Network Security. In Proceedings of the 2012 IEEE PES Innovative Smart Grid Technologies (ISGT), Washington, DC, USA, 16–20 January 2012. [Google Scholar]
- Cleveland, F. IEC TC57 WG15: IEC 62351 Security Standards for the Power System Information Infrastructure. Available online: http://www.collegioingegnerivenezia.it/images/Articoli_Pubblicazioni/2016_Cybersecurity/WhitePaperSecurityStandardsIEC_TC57_March_2014.pdf (accessed on 23 September 2021).
- Piggin, R. Development of industrial cyber security standards: IEC 62443 for scada and industrial control system security. In Proceedings of the IET Conference on Control and Automation 2013: Uniting Problems and Solutions, Birmingham, UK, 4–5 June 2013. [Google Scholar]
- Rosinger, C.; Uslar, M.; Specht, M.; Dänekas, C.; Trefke, J.; Rohjans, S.; González, J.M.; Bleiker, R. Smart Grid Security: IEC 62351 and Other Relevant Standards; Standardization in Smart Grids; Springer: Berlin/Heidelberg, Germany, 2013; pp. 129–146. [Google Scholar]
- Yang, Y.; McLaughlin, K.; Gao, L.; Sezer, S.; Yuan, Y.; Gong, Y. Intrusion detection system for IEC 61850 based smart substations. In Proceedings of the IEEE Power and Energy Society General Meeting (PESGM), Boston, MA, USA, 17–21 July 2016; pp. 1–5. [Google Scholar] [CrossRef]
- Yang, Y.; Xu, H.-Q.; Gao, L.; Yuan, Y.-B.; McLaughlin, K.; Sezer, S. Multidimensional Intrusion Detection System for IEC 61850-Based SCADA Networks. IEEE Trans. Power Deliv. 2017, 32, 1068–1078. [Google Scholar] [CrossRef]
- Hong, J.; Chen, Y.; Liu, C.-C.; Govindarasu, M. Cyber-Physical Security Testbed for Substations in a Power Grid; Cyber Physical Systems Approach to Smart Electric Power Grid; Springer: Berlin/Heidelberg, Germany, 2015; pp. 261–301. [Google Scholar]
- Kwon, Y.; Lee, S.; King, R.; Lim, J.I.; Kim, H.K. Behavior Analysis and Anomaly Detection for a Digital Substation on Cyber-Physical System. Electronics 2019, 8, 326. [Google Scholar] [CrossRef]
- Sun, C.-C.; Hahn, A.; Liu, C.-C. Cyber security of a power grid: State-of-the-art. Int. J. Electr. Power Energy Syst. 2018, 99, 45–56. [Google Scholar] [CrossRef]
- IEC 61850: Power Utility Automation. Available online: https://library.e.abb.com/public/e60d48adcd3d4cf885c421fd489b25dc/P246_IEC_61850_in_Substation_Communication_OnlineTraining_756526ENf.pdf (accessed on 28 September 2003).
- Janssen, M.C.; Apostolov, A. IEC 61850 impact on substation design. In Proceedings of the 2008 IEEE/PES Transmission and Distribution Conference and Exposition, Chicago, IL, USA, 21–24 April 2008; pp. 1–7. [Google Scholar]
- Apostolov, A.; Tholomier, D. Impact of IEC 61850 on Power System Protection. In Proceedings of the 2006 IEEE PES Power Systems Conference and Exposition), Atlanta, GA, USA, 29 October–1 November 2006; pp. 1053–1058. [Google Scholar]
- Shawon, M.H.; Muyeen, S.M.; Ghosh, A.; Islam, S.M.; Baptista, M.S. Multi-Agent Systems in ICT Enabled Smart Grid: A Status Update on Technology Framework and Applications. IEEE Access 2019, 7, 97959–97973. [Google Scholar] [CrossRef]
- Pal, A.; Dash, R. A Paradigm Shift in Substation Engineering: IEC 61850 Approach. Procedia Technol. 2015, 21, 8–14. [Google Scholar] [CrossRef]
- Sidhu, T.S.; Yin, Y. Modelling and Simulation for Performance Evaluation of IEC61850-Based Substation Communication Systems. IEEE Trans. Power Deliv. 2007, 22, 1482–1489. [Google Scholar] [CrossRef]
- Yin, Z.-L.; Liu, W.-S.; Yang, Q.-X.; Qin, Y.-L. Generic Substation Event Model-Based on IEC 61850. Autom. Electr. Power Syst. 2005, 29, 45–50. [Google Scholar]
- Dehalwar, V.; Kalam, A.; Kolhe, M.L.; Zayegh, A. Review of IEEE 802.22 and IEC 61850 for real-time communication in Smart Grid. In Proceedings of the 2015 International Conference on Computing and Network Communications (CoCoNet), Trivandrum, India, 16–19 December 2015; pp. 571–575. [Google Scholar]
- Brunner, C. IEC 61850 for power system communication. In Proceedings of the 2008 IEEE/PES Transmission and Distribution Conference and Exposition, Chicago, IL, USA, 21–24 April 2008; pp. 1–6. [Google Scholar]
- Kanabar, P.M.; Kanabar, M.G.; El-Khattam, W.; Sidhu, T.S.; Shami, A. Evaluation of communication technologies for IEC 61850 based distribution automation system with distributed energy resources. In Proceedings of the 2009 IEEE Power & Energy Society General Meeting, Calgary, AB, Canada, 26–30 July 2009. [Google Scholar]
- Wei, D.; Lu, Y.; Jafari, M.; Skare, P.; Rohde, K. An integrated security system of protecting Smart Grid against cyber attacks. In Proceedings of the 2010 Innovative Smart Grid Technologies (ISGT), Gaithersburg, MD, USA, 19–21 January 2010. [Google Scholar]
- Yang, Y.; Jiang, H.T.; McLaughlin, K.; Gao, L.; Yuan, Y.; Huang, W.; Sezer, S. Cybersecurity test-bed for IEC 61850 based smart substations. In Proceedings of the 2015 IEEE Power & Energy Society General Meeting, Denver, CO, USA, 26–30 July 2015; pp. 1–5. [Google Scholar]
- Elgargouri, A.; Elmusrati, M. Analysis of Cyber-Attacks on IEC 61850 Networks. In Proceedings of the 2017 IEEE 11th International Conference on Application of Information and Communication Technologies (AICT), Moscow, Russia, 20–22 September 2017; pp. 1–4. [Google Scholar]
- Krushna, C.; Magesh, S. Analysis of vulnerabilities in the protocols used in SCADA systems. Int. J. Adv. Res. Comput. Eng. Technol. 2015, 4, 1014–1019. [Google Scholar]
- Kang, B.; Maynard, P.; McLaughlin, K.; Sezer, S.; Andren, F.; Seitl, C.; Kupzog, F.; Strasser, T. Investigating cyber-physical attacks against IEC 61850 photovoltaic inverter installations. In Proceedings of the 2015 IEEE 20th Conference on Emerging Technologies & Factory Automation (ETFA), Luxembourg, 8–11 September 2015; pp. 1–8. [Google Scholar]
- Rashid, M.T.A.; Yussof, S.; Yusoff, Y.; Ismail, R. A review of security attacks on IEC61850 substation automation system network. In Proceedings of the 6th International Conference on Information Technology and Multimedia, Putrajaya, Malaysia, 18–20 November 2014; pp. 5–10. [Google Scholar]
- Maynard, P.; McLaughlin, K.; Haberler, B. Towards Understanding Man-in-the-middle Attacks on IEC 60870-5-104 SCADA Networks. In Proceedings of the 2nd International Symposium for ICS & SCADA Cyber Security Research 2014 (ICS-CSR 2014), Sankt Pölten, Austria, 11–12 September 2014. [Google Scholar]
- Al Sukkar, G.; Saifan, R.; Khwaldeh, S.; Maqableh, M.; Jafar, I. Address Resolution Protocol (ARP): Spoofing Attack and Proposed Defense. Commun. Netw. 2016, 08, 118–130. [Google Scholar] [CrossRef]
- Youssef, T.A.; El Hariri, M.; Bugay, N.; Mohammed, O.A. IEC 61850: Technology standards and cyber-threats. In Proceedings of the 2016 IEEE 16th International Conference on Environment and Electrical Engineering (EEEIC), Florence, Italy, 7–10 June 2016; pp. 1–6. [Google Scholar]
- Habib, H.F.; Lashway, C.R.; Mohammed, O.A. On the adaptive protection of microgrids: A review on how to mitigate cyber attacks and communication failures. In Proceedings of the 2017 IEEE Industry Applications Society Annual Meeting, Cincinnati, OH, USA, 1–5 October 2017. [Google Scholar]
- Hong, J.; Liu, C.-C.; Govindarasu, M. Detection of cyber intrusions using network-based multicast messages for substation automation. In Proceedings of the ISGT 2014, Washington, DC, USA, 19–22 February 2014; pp. 1–5. [Google Scholar]
- Habib, H.F.; Lashway, C.R.; Mohammed, O.A. A Review of Communication Failure Impacts on Adaptive Microgrid Protection Schemes and the Use of Energy Storage as a Contingency. IEEE Trans. Ind. Appl. 2017, 54, 1194–1207. [Google Scholar] [CrossRef]
- Liu, S.; Liu, X.P.; El Saddik, A. Denial-of-Service (dos) attacks on load frequency control in smart grids. In Proceedings of the 2013 IEEE PES Innovative Smart Grid Technologies Conference (ISGT), Washington, DC, USA, 24–27 February 2013; pp. 1–6. [Google Scholar]
- Markovic-Petrovic, J.D.; Stojanovic, M.D. Analysis of SCADA system vulnerabilities to DDoS attacks. In Proceedings of the 2013 11th International Conference on Telecommunications in Modern Satellite, Cable and Broadcasting Services (TELSIKS), Nis, Serbia, 16–19 October 2013; Volume 02, pp. 591–594. [Google Scholar]
- Premaratne, U.; Samarabandu, J.; Sidhu, T.S.; Beresh, R.; Tan, J.-C. An Intrusion Detection System for IEC61850 Automated Substations. IEEE Trans. Power Deliv. 2010, 25, 2376–2383. [Google Scholar] [CrossRef]
- Hahn, A.; Ashok, A.; Sridhar, S.; Govindarasu, M. Cyber-Physical Security Testbeds: Architecture, Application, and Evaluation for Smart Grid. IEEE Trans. Smart Grid 2013, 4, 847–855. [Google Scholar] [CrossRef]
- Choi, K.; Chen, X.; Li, S.; Kim, M.; Chae, K.; Na, J. Intrusion Detection of NSM Based DoS Attacks Using Data Mining in Smart Grid. Energies 2012, 5, 4091–4109. [Google Scholar] [CrossRef]
- Wang, H.; Zhang, D.; Shin, K.G. Detecting SYN flooding attacks. In Proceedings of the Twenty-First Annual Joint Conference of the IEEE Computer and Communications Societies, New York, NY, USA, 23–27 June 2002; Volume 3, pp. 1530–1539. [Google Scholar]
- Rashid, M.T.A.; Yussof, S.; Yusoff, Y. Trust System Architecture for Securing GOOSE Communication in IEC 61850 Substation Network. Int. J. Secur. Appl. 2016, 10, 289–302. [Google Scholar] [CrossRef]
- Premnath, A.P.; Jo, J.-Y.; Kim, Y. Application of NTRU Cryptographic Algorithm for SCADA Security. In Proceedings of the 2014 11th International Conference on Information Technology: New Generations, Las Vegas, NV, USA, 7–9 April 2014; pp. 341–346. [Google Scholar]
- Kush, N.; Ahmed, E.; Branagan, M.; Foo, E. Poisoned GOOSE: Exploiting the GOOSE protocol. In Proceedings of the 12th Australasian Information Security Conference, Auckland, New Zealand, 20–23 January 2014; Volume 149, pp. 17–22. [Google Scholar]
- Skeie, T.; Johannessen, S.; Brunner, C. Ethernet in substation automation. IEEE Control. Syst. 2002, 22, 43–51. [Google Scholar] [CrossRef]
- Kiuchi, M.; Serizawa, Y. Security technologies, usage and guidelines in SCADA system networks. In Proceedings of the IEEE ICCAS-SICE, Fukuoka, Japan, 18–21 August 2009; pp. 4607–4612. [Google Scholar]
- InformIT: Books, Ebooks, and Digital Learning. Available online: https://www.informit.com (accessed on 23 September 2021).
- Bou-Harb, E.; Fachkha, C.; Pourzandi, M.; Debbabi, M.; Assi, C. Communication security for smart grid distribution networks. IEEE Commun. Mag. 2013, 51, 42–49. [Google Scholar] [CrossRef]







| Communication Architecture | Service | Message Type | Application Type | Time Requirement (Milli-Second) | Communication Mapping |
|---|---|---|---|---|---|
| Client–Server (SCADA) | ACS | 2 | Moderate speed | 100 | Ethernet TCP/IP |
| 5 | File Transfer | >=1000 | |||
| Publisher–subscriber | GOOSE, GSSE | 1A | Trip | 3–100 | Ethernet |
| 1B | Others | 20–100 | |||
| SMV | 4 | Measurement data | 3–10 | Ethernet | |
| TS | 6 | Synchronization | N/A | Ethernet UDP/IP |
| Attack on IEC 61850 | Types of Attack | Action on the SAS | Effects on SAS | Ref. |
|---|---|---|---|---|
| Security Attacks on IEC 61850 Network | Malformed Packet Attack | Transmits malformed packets to IEDs | Communication failure among the IEDs | [29] |
| DoS (Denial of Service) Attack | Floods the targeted IED with false messages | Consumes link bandwidth and increase the CPU utilization rate | [30,31] | |
| Address Resolution Protocol (ARP) Spoofing Attack | Fools a receiver into thinking it is being communicated to by a trusted source | IED will communicate with the attacker’s laptop instead of SCADA | [32] | |
| Man in the Middle (MITM) Attack | An attacker in the substation level redirects communication traffic between the IED and SCADA to a malicious laptop | Malicious control commands are sent remotely and changes the protection settings of IEDs | [33,34] | |
| Configuration Tampering | Alters the configured IED description (CID) file within the IED | Disruption of the communication protocols and monitoring system | [35] | |
| Security Attacks on IEC 61850 Messages (exploitation of GOOSE and SMV) | GOOSE and SV Modification Attack | The content of the captured network packets are modified | IEDs can be accessed by hackers and can be a victim of performing malicious acts | [36] |
| GOOSE and SV DoS Attacks | Attacker sends oversized or large number of GOOSE and SMV in the network | Failure of the IEDs to respond to authorized users | [37] | |
| GOOSE and SV Replay Attack | Attacker captures network packets transmitted among the hosts and replays back without any change in the message to obtain a similar response | Causes false tripping of the breaker and can lead to catastrophic situation | [38] |
| Statistics Name | Definition |
|---|---|
| Global ethernet delay [48] | The global ethernet delay statistic is used to demonstrate the end-to-end delay of all the packets that are received by every station. In other words, it represents the time taken for a packet to travel from the source to the destination. |
| CPU utilization [49] | The CPU utilization statistic is used to show the CPU usage of a particular node in the network. The CPU usage models the IP packet forwarding delays and application processing delays. |
| Data-base queries [50] | A DB query is an inquiry by a client device to the server (database) to obtain information in a manner that can be read. In the results, the DB query statistic is measured in terms of traffic received in packets per second. |
| Link Utilization [51] | The link utilization statistic displays the percentage of the available channel bandwidth being consumed by the flow of traffic within the network. |
Publisher’s Note: MDPI stays neutral with regard to jurisdictional claims in published maps and institutional affiliations. |
© 2021 by the authors. Licensee MDPI, Basel, Switzerland. This article is an open access article distributed under the terms and conditions of the Creative Commons Attribution (CC BY) license (https://creativecommons.org/licenses/by/4.0/).
Share and Cite
Ashraf, S.; Shawon, M.H.; Khalid, H.M.; Muyeen, S.M. Denial-of-Service Attack on IEC 61850-Based Substation Automation System: A Crucial Cyber Threat towards Smart Substation Pathways. Sensors 2021, 21, 6415. https://doi.org/10.3390/s21196415
Ashraf S, Shawon MH, Khalid HM, Muyeen SM. Denial-of-Service Attack on IEC 61850-Based Substation Automation System: A Crucial Cyber Threat towards Smart Substation Pathways. Sensors. 2021; 21(19):6415. https://doi.org/10.3390/s21196415
Chicago/Turabian StyleAshraf, Suleman, Mohammad H. Shawon, Haris M. Khalid, and S. M. Muyeen. 2021. "Denial-of-Service Attack on IEC 61850-Based Substation Automation System: A Crucial Cyber Threat towards Smart Substation Pathways" Sensors 21, no. 19: 6415. https://doi.org/10.3390/s21196415
APA StyleAshraf, S., Shawon, M. H., Khalid, H. M., & Muyeen, S. M. (2021). Denial-of-Service Attack on IEC 61850-Based Substation Automation System: A Crucial Cyber Threat towards Smart Substation Pathways. Sensors, 21(19), 6415. https://doi.org/10.3390/s21196415








