Carrier Diversity Incorporation to Low-Complexity Near-ML Detection for Multicarrier Systems over V2V Radio Channel
Abstract
1. Introduction
1.1. Objectives and Contributions
- It assimilates the linear data precoding stage so that the operation is obtained with equivalent channel matrices that maintain the band structure. This makes it possible to extract the channel diversity, which significantly improves performance while demanding low complexity;
- It uses an improved search order that enables the decoder to find the optimal solution in fewer iterations. Furthermore, the detector’s maximum search size can be set to an amount of operations that will not have a significant impact on performance.
1.2. Abbreviations and Acronyms
1.3. Organization
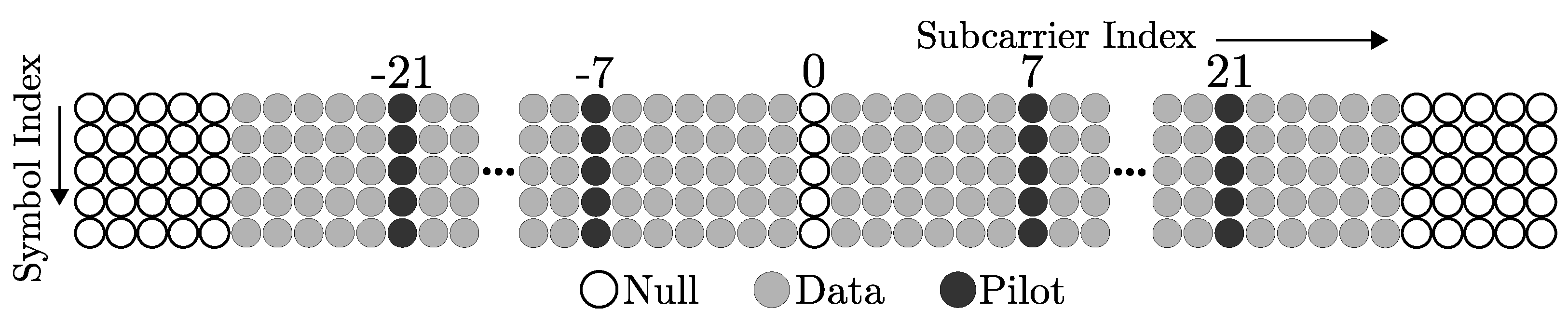
2. System Model
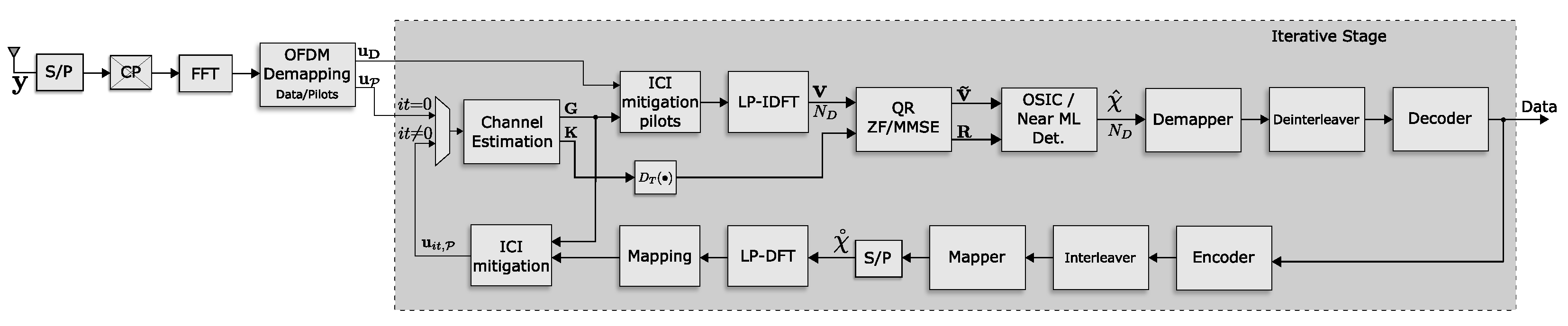
3. Proposed Receiver
3.1. Channel Estimation
3.2. DFT Dispersion
3.3. Non-Linear Detection on DFTS-OFDM System
Maximum Likelihood Detection Criteria
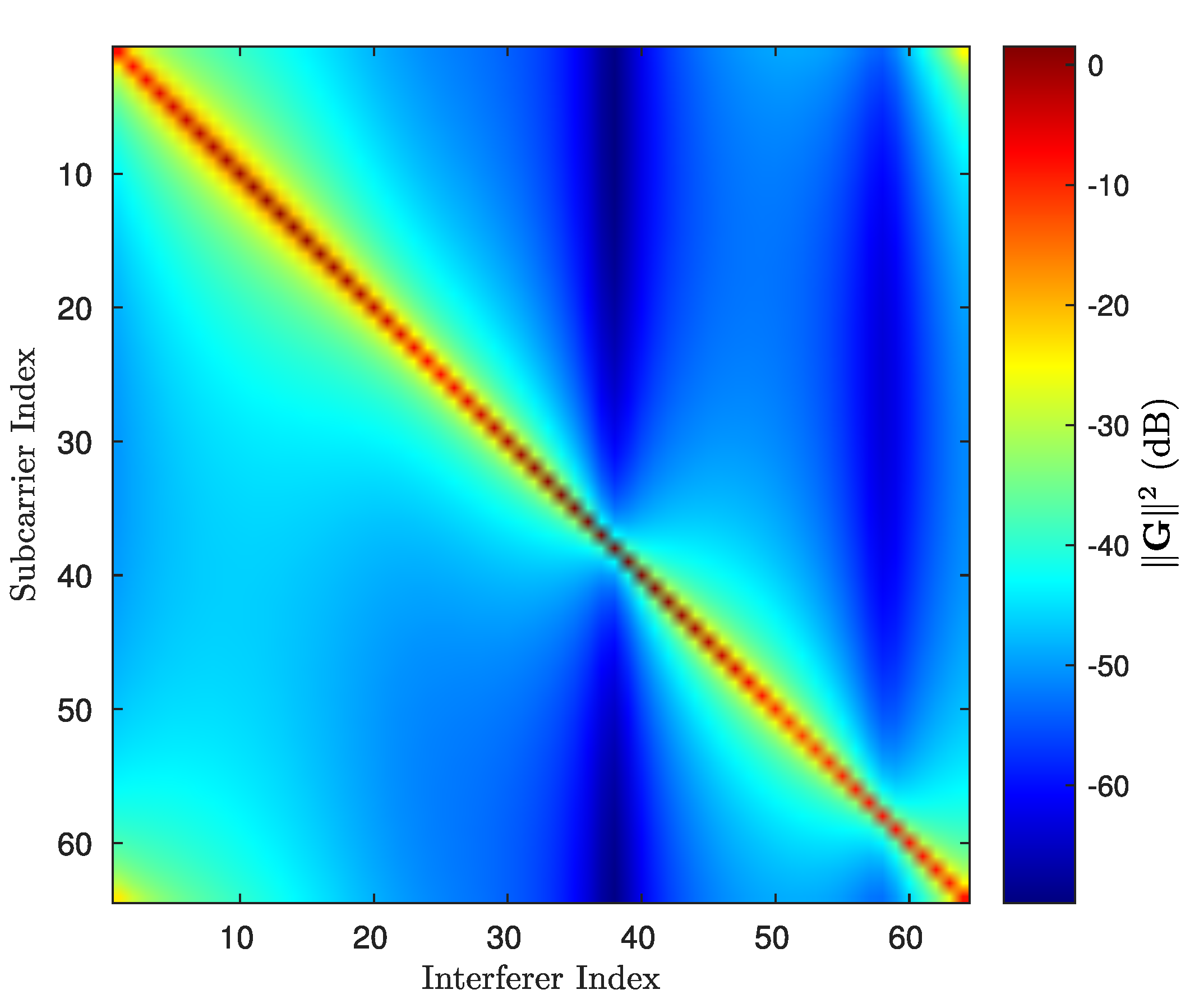
3.4. ICI Mitigation
4. Low Complexity Non-Linear Detection
4.1. Sorted QR Decomposition
4.2. Two Approaches for Non-Linear Data Detection
4.2.1. OSIC Detection
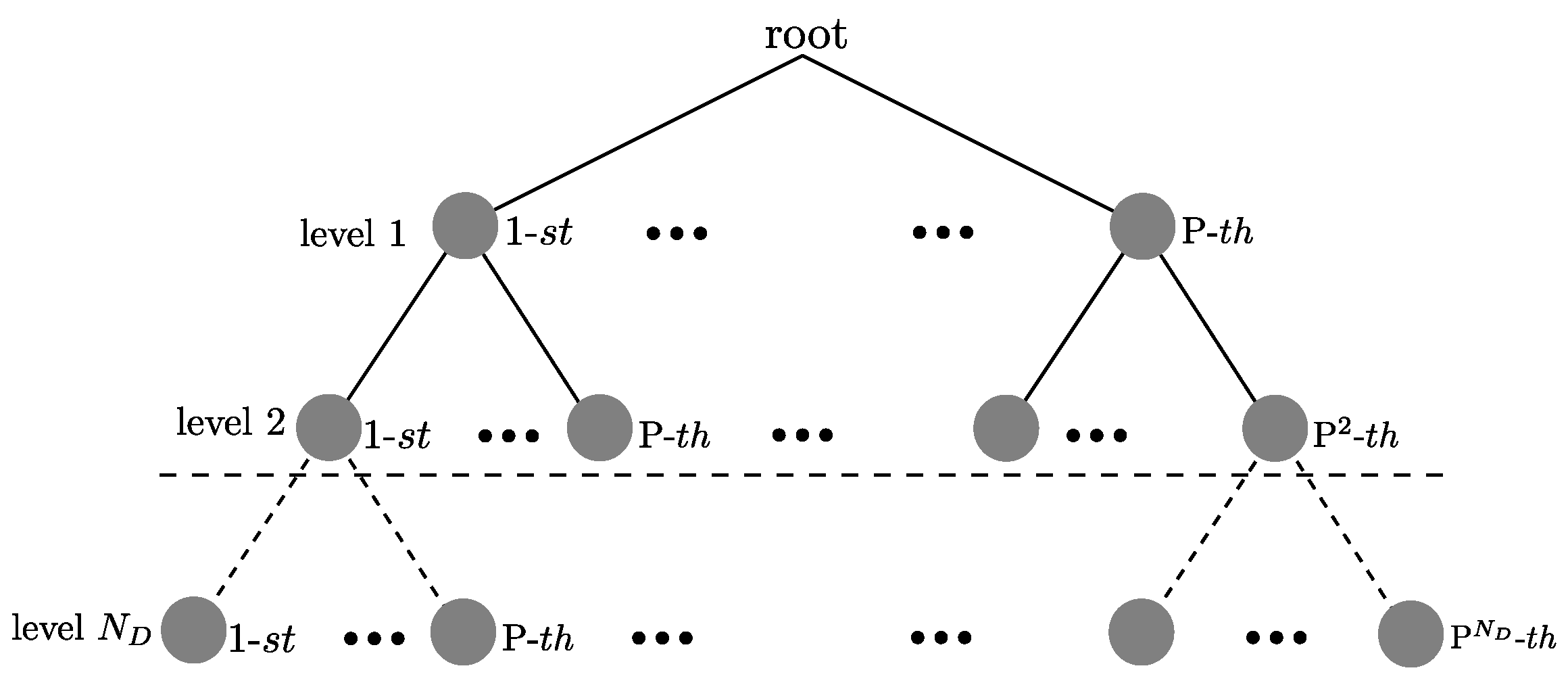
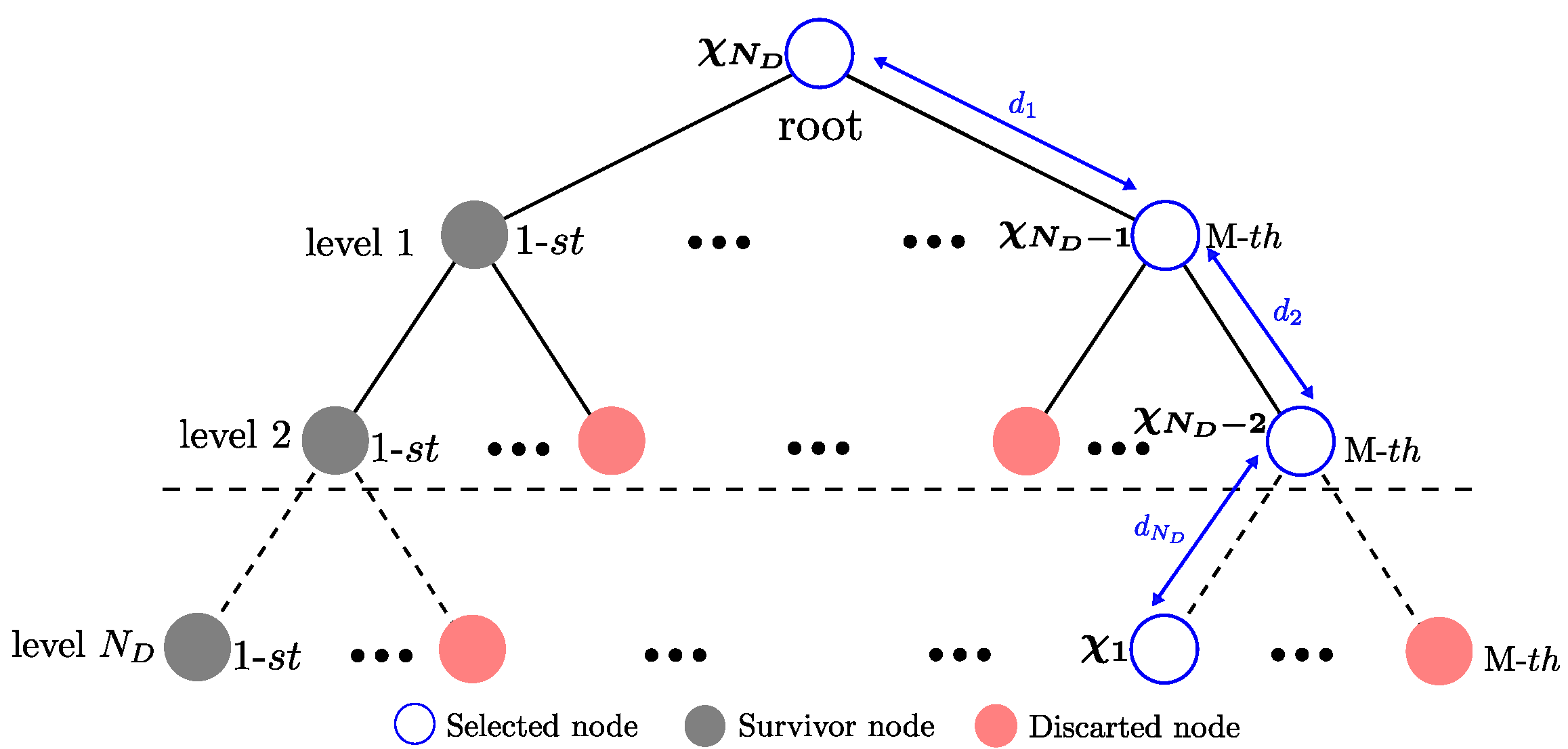
4.2.2. Near ML Detection
| Algorithm 1: Recursive near ML detector for V2V system. |
 |
5. Computational Structure
6. Computational Complexity
- An OFDM system with data subcarriers;
- modulation scheme with unitary average power per symbol;
- is the maximum number of surviving branches per level in the Near ML V2V algorithm;
- The dimensions of is for the ZF criterion and for the MMSE criterion;
- The algorithms were performed for 2000 channel realizations, and the complex operations employed were counted independently for each algorithm and finally averaged;
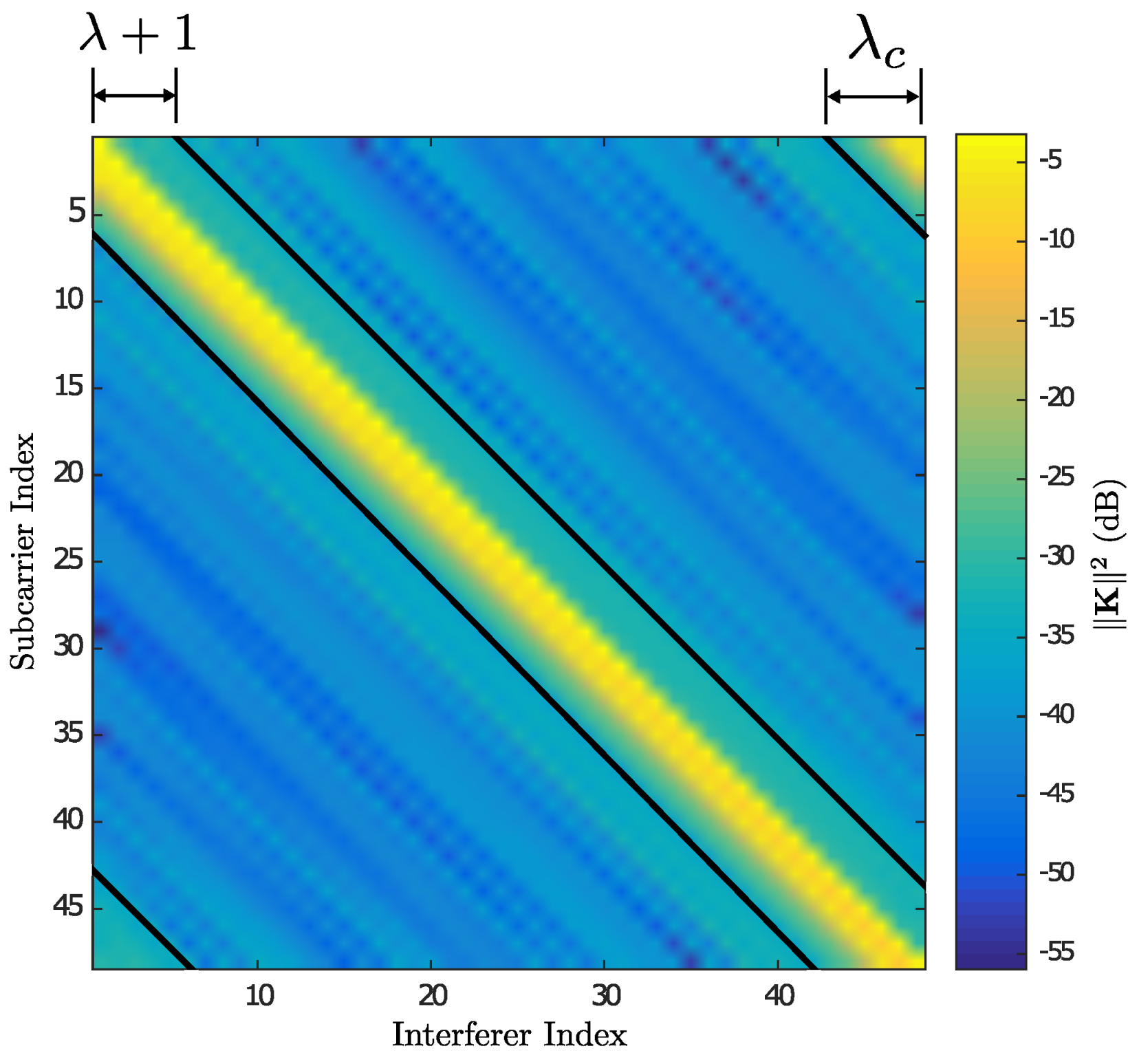
- Based on simulations results, it was determined the number bands for truncating matrix .
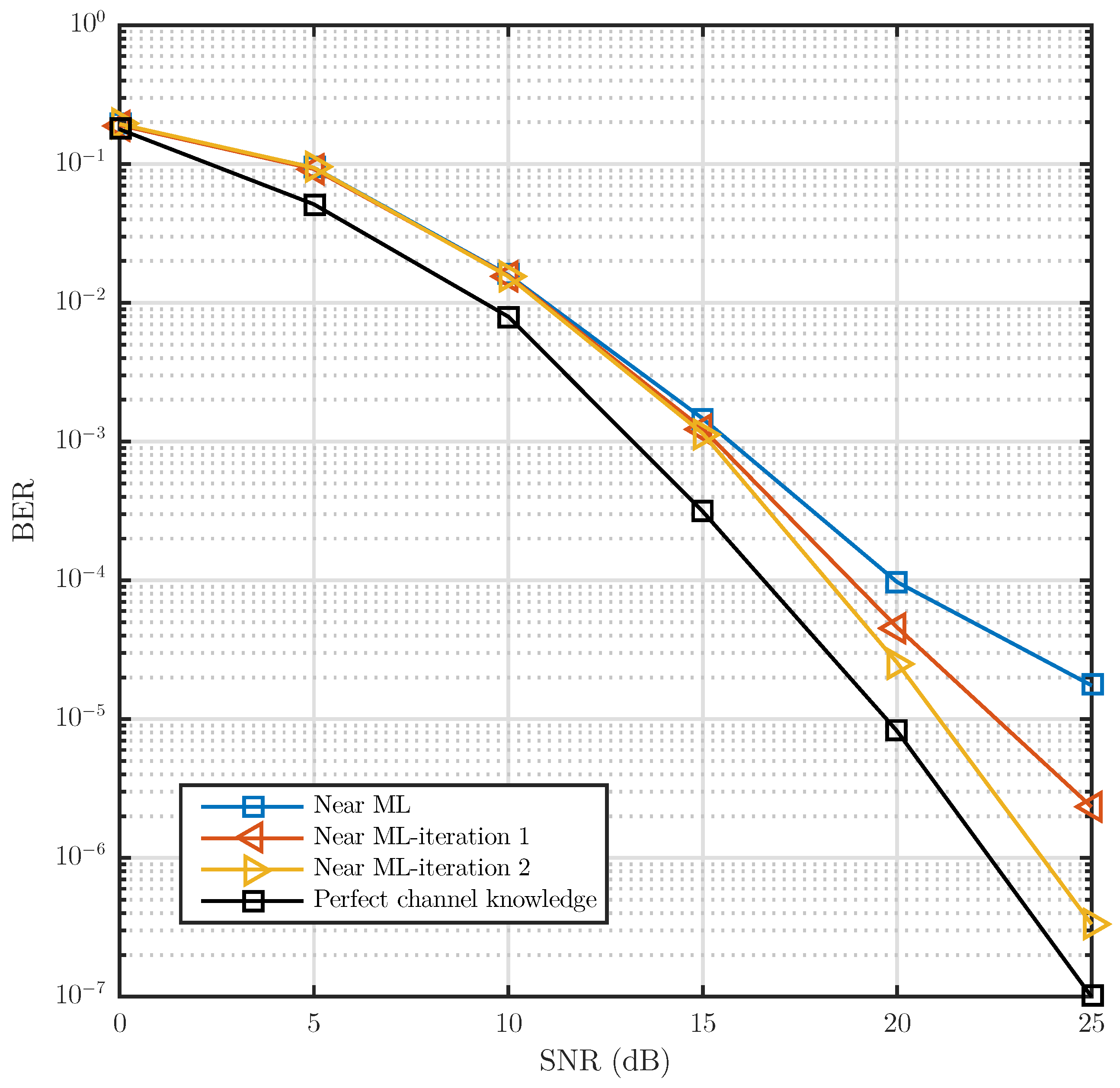
7. Simulations Results
8. Conclusions
Author Contributions
Funding
Institutional Review Board Statement
Informed Consent Statement
Data Availability Statement
Acknowledgments
Conflicts of Interest
References
- Mecklenbrauker, C.F.; Molisch, A.F.; Karedal, J.; Tufvesson, F.; Paier, A.; Bernado, L.; Zemen, T.; Klemp, O.; Czink, N. Vehicular Channel Characterization and Its Implications for Wireless System Design and Performance. Proc. IEEE 2011, 99, 1189–1212. [Google Scholar] [CrossRef]
- Acosta-Marum, G.; Ingram, M.A. Six time- and frequency- selective empirical channel models for vehicular wireless LANs. IEEE Veh. Technol. Mag. 2007, 2, 4–11. [Google Scholar] [CrossRef]
- Zemen, T.; Bernado, L.; Czink, N.; Molisch, A.F. Iterative Time-Variant Channel Estimation for 802.11p Using Generalized Discrete Prolate Spheroidal Sequences. IEEE Trans. Veh. Technol. 2012, 61, 1222–1233. [Google Scholar] [CrossRef]
- Zemen, T.; Molisch, A.F. Adaptive Reduced-Rank Estimation of Nonstationary Time-Variant Channels Using Subspace Selection. IEEE Trans. Veh. Technol. 2012, 61, 4042–4056. [Google Scholar] [CrossRef]
- Ku, M.; Huang, C. A Refined Channel Estimation Method for STBC/OFDM Systems in High-Mobility Wireless Channels. IEEE Trans. Wirel. Commun. 2008, 7, 4312–4320. [Google Scholar] [CrossRef]
- Ahmed, S.; Sellathurai, M.; Lambotharan, S.; Chambers, J.A. Low-complexity iterative method of equalization for single carrier with cyclic prefix in doubly selective channels. IEEE Signal Process. Lett. 2006, 13, 5–8. [Google Scholar] [CrossRef][Green Version]
- Tang, Z.; Leus, G. A novel receiver architecture for single-carrier transmission over time-varying channels. IEEE J. Sel. Areas Commun. 2008, 26, 366–377. [Google Scholar] [CrossRef][Green Version]
- Rugini, L.; Banelli, P.; Leus, G. Simple equalization of time-varying channels for OFDM. IEEE Commun. Lett. 2005, 9, 619–621. [Google Scholar] [CrossRef]
- Kim, S.I.; Oh, H.S.; Choi, H.K. Mid-amble aided OFDM performance analysis in high mobility vehicular channel. In Proceedings of the 2008 IEEE Intelligent Vehicles Symposium, Eindhoven, The Netherlands, 4–6 June 2008; pp. 751–754. [Google Scholar] [CrossRef]
- Lin, C.S.; Sun, C.K.; Lin, J.C.; Chen, B.C. Performance evaluations of channel estimations in IEEE 802.11p environments. In Proceedings of the 2009 International Conference on Ultra Modern Telecommunications Workshops, St. Petersburg, Russia, 12–14 October 2009; pp. 1–5. [Google Scholar] [CrossRef]
- IEEE Draft Standard for Information Technology-Telecommunications and Information Exchange between Systems-Local and Metropolitan Area Networks-Specific Requirements-Part 11: Wireless LAN Medium Access Control (MAC) and Physical Layer (PHY) Specifications Amendment: Wireless Access in Vehicular Environments; IEEE Unapproved Draft Std P802.11p /D11.0; IEEE: Piscataway, NJ, USA, 2010.
- Damen, M.O.; Gamal, H.E.; Caire, G. On maximum-likelihood detection and the search for the closest lattice point. IEEE Trans. Inf. Theory 2003, 49, 2389–2402. [Google Scholar] [CrossRef]
- Hassibi, B.; Vikalo, H. On the sphere-decoding algorithm I. Expected complexity. IEEE Trans. Signal Process. 2005, 53, 2806–2818. [Google Scholar] [CrossRef]
- Hwang, S.J.; Schniter, P. Efficient Sequence Detection of Multicarrier Transmissions over Doubly Dispersive Channels. EURASIP J. Adv. Signal Process. 2006, 2006, 093638. [Google Scholar] [CrossRef]
- Guo, Z.; Nilsson, P. Reduced complexity Schnorr-Euchner decoding algorithms for MIMO systems. IEEE Commun. Lett. 2004, 8, 286–288. [Google Scholar] [CrossRef]
- Moroga, H.; Yamamoto, T.; Adachi, F. Iterative Overlap TD-QRM-ML Block Signal Detection for Single-Carrier Transmission without CP Insertion. In Proceedings of the 2012 IEEE Vehicular Technology Conference (VTC Fall), Yokohama, Japan, 6–9 May 2012; pp. 1–5. [Google Scholar] [CrossRef]
- Temma, K.; Yamamoto, T.; Adachi, F. Improved 2-Step QRM-ML Block Signal Detection for Single-Carrier Transmission. In Proceedings of the 2011 IEEE Vehicular Technology Conference (VTC Fall), San Francisco, CA, USA, 5–8 September 2011; pp. 1–5. [Google Scholar] [CrossRef]
- Vlachos, E.; Lalos, A.S.; Berberidis, K. Low-Complexity OSIC Equalization for OFDM-Based Vehicular Communications. IEEE Trans. Veh. Technol. 2017, 66, 3765–3776. [Google Scholar] [CrossRef]
- Zhang, Y.; Peng, K.; Song, J.; Wu, Y. Quasi-Cyclic Spatially Coupled LDPC Code for Broadcasting. IEEE Trans. Broadcast. 2020, 66, 187–194. [Google Scholar] [CrossRef]
- Dai, L.; Fang, Y.; Yang, Z.; Chen, P.; Li, Y. Protograph LDPC-Coded BICM-ID with Irregular CSK Mapping in Visible Light Communication Systems. IEEE Trans. Veh. Technol. 2021. [Google Scholar] [CrossRef]
- Padala, S.K.; D’Souza, J. Performance of Spatially Coupled LDPC Codes over Underwater Acoustic Communication Channel. In Proceedings of the 2020 National Conference on Communications (NCC), Kharagpur, India, 21–23 February 2020; pp. 1–5. [Google Scholar] [CrossRef]
- Arena, F.; Pau, G.; Severino, A. A Review on IEEE 802.11p for Intelligent Transportation Systems. J. Sens. Actuator Netw. 2020, 9, 22. [Google Scholar] [CrossRef]
- Pena-Campos, F.; Carrasco-Alvarez, R.; Longoria-Gandara, O.; Parra-Michel, R. Estimation of Fast Time-Varying Channels in OFDM Systems Using Two-Dimensional Prolate. IEEE Trans. Wirel. Commun. 2013, 12, 898–907. [Google Scholar] [CrossRef]
- Slepian, D. Prolate spheroidal wave functions, Fourier analysis and uncertainty-IV: Extensions to many dimensions; generalized prolate spheroidal functions. Bell Syst. Tech. J. 1964, 43, 3009–3057. [Google Scholar] [CrossRef]
- Hijazi, H.; Ros, L. Joint data QR-detection and Kalman estimation for OFDM time-varying Rayleigh channel complex gains. IEEE Trans. Commun. 2010, 58, 170–178. [Google Scholar] [CrossRef]
- Golub, G.H.; Loan, C.F.V. Matrix Computations, 4th ed.; An Optional Note; Johns Hopkins University Press: Baltimore, MD, USA, 2016. [Google Scholar]
- Wu, K.; Sang, L.; Xiong, C.; Zhang, X.; Yang, D. Novel QRM-MLD algorithm for V-BLAST systems with permuted channel matrix. In Proceedings of the 2009 IEEE 20th International Symposium on Personal, Indoor and Mobile Radio Communications, Tokyo, Japan, 13–16 September 2009; pp. 2484–2488. [Google Scholar] [CrossRef]
- Parra-Michel, R.; Vázquez Castillo, J.; Vela-Garcia, L.R.; Kontorovich, V.; Peña-Campos, F. A Channel Model and Simulation Technique for Reproducing Channel Realizations with Predefined Stationary or Non-Stationary PSD. IEEE Trans. Wirel. Commun. 2018, 17, 5409–5424. [Google Scholar] [CrossRef]




| QR Decomposition | Number of Rotations with Banded Matrix | Number of Rotations with Full Matrix | Complexity |
|---|---|---|---|
| ZF | 37,900 | 114,020 | |
| MMSE | 59,650 | 172,780 |
| Method | Complexity | Normalized Cost | |
|---|---|---|---|
| ML | 5.43 | Inf | |
| LMMSE | 1.5802 | 179.7970 | |
| Near ML Proposed | 1.0110 | 1.0110 | |
| OSIC Proposed | 1 | 1 | |
Publisher’s Note: MDPI stays neutral with regard to jurisdictional claims in published maps and institutional affiliations. |
© 2021 by the authors. Licensee MDPI, Basel, Switzerland. This article is an open access article distributed under the terms and conditions of the Creative Commons Attribution (CC BY) license (https://creativecommons.org/licenses/by/4.0/).
Share and Cite
Del Puerto-Flores, J.A.; Peña-Campos, F.; Parra-Michel, R.; Del-Valle-Soto, C. Carrier Diversity Incorporation to Low-Complexity Near-ML Detection for Multicarrier Systems over V2V Radio Channel. Sensors 2021, 21, 6067. https://doi.org/10.3390/s21186067
Del Puerto-Flores JA, Peña-Campos F, Parra-Michel R, Del-Valle-Soto C. Carrier Diversity Incorporation to Low-Complexity Near-ML Detection for Multicarrier Systems over V2V Radio Channel. Sensors. 2021; 21(18):6067. https://doi.org/10.3390/s21186067
Chicago/Turabian StyleDel Puerto-Flores, Jose Alberto, Fernando Peña-Campos, Ramón Parra-Michel, and Carolina Del-Valle-Soto. 2021. "Carrier Diversity Incorporation to Low-Complexity Near-ML Detection for Multicarrier Systems over V2V Radio Channel" Sensors 21, no. 18: 6067. https://doi.org/10.3390/s21186067
APA StyleDel Puerto-Flores, J. A., Peña-Campos, F., Parra-Michel, R., & Del-Valle-Soto, C. (2021). Carrier Diversity Incorporation to Low-Complexity Near-ML Detection for Multicarrier Systems over V2V Radio Channel. Sensors, 21(18), 6067. https://doi.org/10.3390/s21186067







