Abstract
The Internet of Things (IoT) is an emerging technology in underwater communication because of its potential to monitor underwater activities. IoT devices enable a variety of applications such as submarine and navy defense systems, pre-disaster prevention, and gas/oil exploration in deep and shallow water. The IoT devices have limited power due to their size. Many routing protocols have been proposed in applications, as mentioned above, in different aspects, but timely action and energy make these a challenging task for marine research. Therefore, this research presents a routing technique with three sub-sections, Tri-Angular Nearest Vector-Based Energy Efficient Routing (TANVEER): Layer-Based Adjustment (LBA-TANVEER), Data Packet Delivery (DPD-TANVEER), and Binary Inter Nodes (BIN-TANVEER). In TANVEER, the path is selected between the source node and sonobuoys by computing the angle three times with horizontal, vertical, and diagonal directions by using the nearest vector-based approach to avoid the empty nodes/region. In order to deploy the nodes, the LBA-TANVEER is used. Furthermore, for successful data delivery, the DPD-TANVEER is responsible for bypassing any empty nodes/region occurrence. BIN-TANVEER works with new watchman nodes that play an essential role in the path/data shifting mechanism. Moreover, achievable empty regions are also calculated by linear programming to minimize energy consumption and throughput maximization. Different evaluation parameters perform extensive simulation, and the coverage area of the proposed scheme is also presented. The simulated results show that the proposed technique outperforms the compared baseline scheme layer-by-layer angle-based flooding (L2-ABF) in terms of energy, throughput, Packet Delivery Ratio (PDR) and a fraction of empty regions.
1. Introduction
The Earth’s surface, around 71.2% is covered by ocean. Approximately half of the population of this world lives under 100 km of seaside areas. Furthermore, the ocean has been a source of nutrition products, and over time, has begun playing a vital role in the areas of defense, carriage, natural resources, and leisure. While water is indispensable for all humankind, a surprisingly massive area of the total volume of the ocean remains unexplored, i.e., less than 10% of it has been studied [1]. It is difficult for human beings to monitor volatile underwater events and high-water pressure. Because of the reasons mentioned earlier, unmanned exploration is necessary. As a result, Internet of Things-enabled acoustic sensor and actor networks (I-ASANs) have attracted the interest of researchers of late.
In the last 10 years, much research has been conducted underwater for multiple purposes [2]. Due to potential underwater applications, this research is not limited to the exploration of finding minerals, oils, and monitoring of aquatic life but also is an experimental laboratory for acoustic experiments. Today, many real-time problems have been experimented on under water such that to predict floods and tsunami, scientific and commercial offshore exploration is conducted in deep and shallow water, etc.
Many routing protocols work successfully in terrestrial wireless sensor networks (TWSNs) that cannot work steadily in underwater domains due to different communication channels like radio signals, which do not propagate underwater as this is only possible for acoustic signals. The topology of ASANs [3] is usually dynamic compared to TWSNs due to the deployment of frequent nodes and their localization. As these nodes move with mobile water [4], so energy is limited, and it is difficult to recharge the power resources in deep water. Therefore, high propagation delay and deployment cost, low bandwidth, and packet loss ratio are significant challenges in ASANs [5].
All the above challenges can be resolved if the data is smooth and sent rapidly towards the destination. Many well-known routing protocols are worked in this regard, like vector-based flooding [5] and angle-based flooding [6,7] which calculate the angle with multi-sink architecture for reliable data delivery, but the efficient way does not achieve due to week support of intermediate nodes. The unavailability of the next intermediate nodes mean empty regions are created in the network, as well as data loss of previous nodes. In an upward direction, every sensor node computes the angle that is π/2. On the basis of the angle, as mentioned earlier, the nodes forward the data packets. Data packets that reach any one of the surface sinks will be considered successfully delivered to the destination. The empty region is defined as the area in which nodes (usually present around the sink called sink neighboring nodes) fail to send the information towards the destination and create empty regions in this area. For these regions, the network traffic is stopped for the time being and isolate some part of the network. Ultimately data packet delivery and throughput is decreased and an extra energy tax is used for rescue the network especially in a large-scale area network like under water. Many secondary and rescue nodes are introduced inside the sink to recover the data [7,8].
In [8], the watchman nodes are introduced to the recovery of lost data from the empty region of the underwater network in which the watchman was continuously monitoring the node’s location and its energy status. However, these two approaches follow the monitoring approach, where the status of every node is checked by watchman nodes and corresponding angles of forwarding. The related parameters of the watchman are at distance from the node and angle cone for angle-based flooding. Both these parameters have a significant reason for high propagation and end-to-end delay, respectively. Thus, to avoid the empty region, multiple parameters need to be considered for forwarding the data packets in a well-disciplined manner. Hence, energy-efficient routing schemes are required, which have the ability to take robust short and quick routing paths between source and master stations and also avoid empty regions.
To make the scheme energy efficient, geographic routing [9] is best suited as it is frequently used due to its scalability and simplicity; also, it does not need and complete route information between two junctions. Angle-based routing is easily coped with transmitting data by circling more multiple neighbors’ nodes by computing the angles. For this, priorities are defined for different parameters like the shortest distance and energy. The nodes with the highest priority receive the data and are able to send it further. The rest of the node does not receive data because acknowledgment is received with the highest priority nodes.
Furthermore, geographical routing has a major reason to create the empty region because one node at a time is selected for transmission, and angle-based routing selects those nodes that cover with angle cone, but it consumes a lot of time and energy to compute the angle with every flooding spell. In this way, both routing schemes need to work together to cope with multiple parameters to improve energy and avoidance of empty regions.
Our Contributions. Motivated by the above consideration of energy-efficient and angle-based scenarios [6,7], we proposed the Tri-Angular Nearest Vector-Based Energy Efficient Routing (TANVEER) with its three sub-sections having exclusive features like layer-based adjustment, data-packet delivery, and binary internodes. The TANVEER, by nature, uses both angle and energy-efficient approaches for reliable communication. The layer-based adjustment of TANVEER, (LBA-TANVEER) first assigns the IDs of the nodes to all deployed nodes in the form of layers from anchored to surface of the water so that each node is easily identified with its status to detection of empty node or group of empty nodes called empty regions. All the adjustments of layers will be static throughout the network’s lifetime. Secondly, the immediate data packet delivery (DPD-TANVEER) starts whenever the empty regions are detected; the recovery process of data is done by binary inter nodes (BIN-TANVEER). The BIN is presented with the novel nodes called watchman nodes that enable data recovery from the empty regions based on the nearest vector angle is made. The contribution of our proposed scheme is given as follows: The TANVEER summarizes three metrics (three sides of angle calculation, energy, and the number of nodes) to select the nearest vector with a triangular approach to forwarding the data packets towards the sink. It selects the node which is closest to the nearest vector by flooding the tri-angular zone and finds out the closest path for the destination. The data are forwarded in the form of layer by layer manner so that each layer maintains the traffic smoothly before and after the communication. The LBA-TANVEER uses the multi-sink architecture at the surface of the water, while the topmost layer consists of ordinary sensor nodes. The watchman node with both left-right directions to rescue the empty regions are present in each layer. The DPD-TANVEER uses the same path provided by the LBA-TANVEER. The BIN-TANVEER adjusts the watchman nodes and follows the empty region’s occurrence and transfers the data through BIN towards sink through bypass the empty regions successfully. The BIN is only active when it needs, while the rest of the time, it just monitors the occurrence of empty nodes.
The rest of the paper is organized as the related latest underwater routing schemes are described in Section 2. The problem is explained in Section 3, while the proposed model and TANVEER are described in Section 4 and Section 5, respectively. Section 6, Section 7 and Section 8 deal with the proposed LBA-TANVEER, DPD-TANVEER, and BIN-TANVEER. The achievable regions are shown in Section 9 while the simulation and discussion of results are in Section 10. Trade-offs of the performance of the scheme are compared in Section 11, and Section 12 leads the conclusion.
2. Related Work
In this section, we summarized the different latest routing protocols in the field of ASANs with its possible pros and cons. The detailed summary of these routing protocols is given in Table 1, where each routing protocol has its achievements and limitations.

Table 1.
Summary of possible Underwater Acoustic Sensor Network routing schemes as discussed in related work.
Most of the routing schemes use the direction-based flooding in which a path is established between source and destination, but the link quality does not consider directional flooding-based routing (DFR) [10]. Packets are sent according to the link quality by bypass the empty nodes while flooding. In those nodes that have a smooth path between source and master station, the packets are sent, otherwise flooding is again propagated. The main feature of the DFR is allowed at least one node participation during the detection of empty regions inside the network. It is only possible when links of the route are error-prone in terms of packet loss.
For long-term underwater environments, efficient data delivery still challenges when the nodes are sparse to each other and unpaired acoustic channels for transmission. For this, the anycast network architecture has been discussed. Two types of topology controls have been introduced in [11,12], as centralized and distributed (CTC) and (DTC). Both topologies are work with a depth control mechanism in which the data packet delivery ratio is achieved up to 90%. It is interesting to see that this technique is experimented with for both types of underwater environment, by mean very sparse and dense networks. Centralized and distributed depth adjustment with DA + CTC and DA + DTC are simulated with sonobuoys as taking as sink and provide robust communication without any occurrence of empty regions due to hybrid (centralized and distributed) approach and overall improved network lifetime.
In [9], geographic and opportunistic routing work with depth adjustment is used for communication recovery (GEDAR) when the empty region comes into existence. These strategies are mostly used with the location-based application, where oil and minerals need to be explored. Basically, provide the exact location of the occurrence of the empty region by following the greedy-based approach. As the name implies for the opportunistic routing, it always finds the early realization of the area of the node where the gaps are near. It transfers the data packets by next forwarder selection of the set for GEDAR. The limitation of location-oriented problems of the destination nodes fix the depth adjustment for each hop. As the empty regions are located, it calculates the new depth for the sonobuoys for the delivery of data. The use of multi-purpose sonobuoys in each expect neighboring node is calculated with the next hope depth so that the chances of empty regions are minimum as expected. By calculating the depth at each node, the selection of neighboring sets has some trade-offs, because it does not ensure about the GEDAR finds the good and opportunistic set of neighboring nodes, the unexpected delays come with minimum throughput.
The depth control routing protocol (DCR) [11] has a similar working nature, as discussed in GEDAR. The major difference between GEDAR and DCR is the moving style of the nodes. The vertical node movement is introduced in DCR to control the topology of the network. To know in advance the greedy approach, the DCR works better where the greedy mechanism of routing fails by using SEA-SWARM architecture. The determination of empty regions is not possible without checking the status of its neighboring nodes, so the main focus of depth control adjustment increases the lifetime and throughput ratio of the network. However, the long route by depth adjustment for neighbors may follow the network in large end-to-end delays.
Void aware pressure routing (VAPR) [12,13] used for monitoring purposes have 4G mechanisms, including space and time. By deploying the on-board pressure gauges at the surface of the ocean, it works directly to send the data packets to the master station. For this, VAPR uses three parameters like hop count, sequence number, and depth information for making the direct path to the closest sonobuoys. The central theme behind the pressure routing is worked in the presence of an empty region, and it is because the location and depth directly control the onboard surface station via an alternate route. Additionally, this scheme increases the network delays when the route is calculated on-board station.
Layer-by-layer angle-based flooding (L2-ABF) is introduced in [6,7] in which every node calculates its flooding angle towards the destination to forward the data packets in the layer hierarchy. The layered approach is used for the deployment of nodes so that there is no need for explicit location information about the nodes. Once the nodes have been deployed, the IDs are assigned that are static throughout the network lifetime. L2-ABF provides a 3D communication zone for its flooding so that both ends must complete the end-to-end delivery.
Another approach AHH-VBF is adaptive hop-by-hop vector-based forwarding (AHH-VBF) [13], in which the radius information instead of angle is used. By using radius information, it quickly reduces the consumption of energy issues because the radius information is done by using acoustic wavelengths. Therefore, there is no need to take extra calculations between source and destination. This scheme enhances the rapid data packet forwarding ratio, reduces the delay, and makes an energy-efficient scheme.
For the selection of nodes and their route towards the destination, the hop-by-hop dynamic addressing-based routing protocol for pipeline monitoring is discussed (H2-DARPPM) [14]. The parametric value for the selection of nodes is energy consumption. It uses the dynamic addressing scheme to each node address so that the PDR is increased, but this approach is costly for network topology.
In [15], the vector-based void avoidance (VBVA) works for mobile underwater sensor networks to address the void routing problem. It works with two novel features vector shift and back pressure to handle the void empty regions. For the empty regions that occur in the boundary of the network, the vector shift is used to deal with these regions; meanwhile, bask pressure is used to avoid the concave empty regions. The primary strategy is that it does not need any prior information about the network due to VBVA’s work with an on-demand approach. It is the first void empty region protocol that works with 3-dimensional topology with mobile nodes. The simulation results show that the PDR is achieved and minimizes the Packet Lose Ratio (PLR).
An energy-efficient watchman-based algorithm (EE-WBA) [16] uses a novel node called watchman node that applies in a distributed based network for detection and avoidance of empty regions near the sink neighboring nodes. Those nodes that died early due to high deprecation of the bottom nodes can rescue with the help of watchman nodes. Watchman nodes are dedicated nodes that deploy for this task. The data are transfer successfully from dying nodes to watchman nodes and the responsibility of the data storage to the sink comes from watchman nodes.
Another article in which introduced the approach for reliable data delivery underwater. The neighbor node approaches distinct energy efficient mates (NADEEM) [17] with two invariants like fallback and transmission. Both these are following the greedy approach to forwarding the data among the nodes of the network. The neighboring node is only eligible to send the data when the route towards the destination is not avoided. Five parameters are considered for this work like PDR, PLR, energy consumption, throughput, and a fraction of void nodes for simulation. The proposed technique performed better than the baseline approach GEDAR [9] in terms of void nodes and corresponding consumption of energy. The major limitation of this work, the route is not every time clear with respect to void nodes, so most of the time, NADEEM does not detect the void nodes.
3. Problem Explanation
The underwater topology is randomly deployed where the source and sonobuoys are far apart from each other. Therefore, the energy consumption of nodes is deprecated. Forwarding nodes try to transmit the data, but early deprecation of nodes (that bear the total traffic of the source and intermediate nodes) creates empty regions. Furthermore, when the node starts data forwarding and does not know the exact location where empty regions exist [38]. Mostly, the data are not forwarded due to the presence of empty regions inside the route information. The proper angle towards the node does not consider while forwarding; as a result, the delay and low PDR come into exists. The empty gaps near the sink’s neighboring nodes are needed to fix, as these sink neighboring nodes are responsible for covering these void holes successfully at both ends. However, the empty regions can also be covered by the adjustment of nodes depth level. The adjustment of the node’s depth is based on angle and movement as described in Figure 1. The movement and alignment of nodes are discussed in the literature and in the baseline approach that is taken for comparison, i.e., angle-based approach where each node is aligned up to some angle and with layer-based hierarchy. Moreover, the overhead cache is increased when, for each iteration, the angle needs to be computed. Another problem is that by checking the continuous energy status of nodes, like sink neighboring nodes, is not possible as per some opportunistic routing protocols do this easily [39]. Additionally, most of the previous approach where these issues try to enhance the energy of sink neighboring nodes, is all in vain. The reason is that the energy of the overall network is decreased when a large amount of this material is considered to be dedicated to particular sink neighboring nodes in the underwater acoustic environment. Therefore, the energy sources our primary check for the proposed technique. This approach is also successful in sparse and dense water areas.
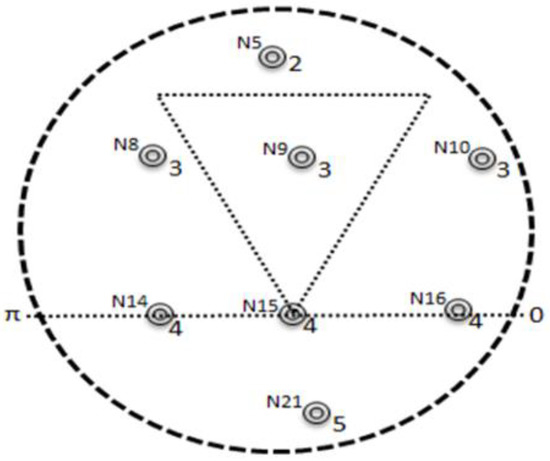
Figure 1.
Description of angle adjustment discussed in L2-ABF [7].
For the problems mentioned above, therefore, we need an energy-efficient technique for like TANVEER with its three subsections like LBA-TANVEER, DPD-TANVEER, and BIN-TANVEER. The LBA is used to control the empty region’s occurrence by using the location of the node and its energy status, while for reliable data delivery the DPD-TANVEER works out. To rescue the data of empty regions before and after the node’s deprecation, the BIN-TANVEER is used. Furthermore, the detail of the proposed system model is presented in the next section.
4. Proposed Model
The proposed system model consists of multi-sink architecture that provides communication with all IoT enabled sensor nodes [40]. Nodes are not randomly deployed but in a novel layer-by-layer hierarchy in which every node obtains a unique ID that is static unless the communication is not started. These nodes are responsible for collecting and transmitting the data to each other and send them to the sink of neighboring nodes. Sink neighboring nodes further send to sonobuoys that are present at the surface of the water. Some nodes are placed at the bottom of the ocean that are usually called anchored nodes. The purpose of adjustment of nodes in a layer-by-layer manner is basically to support the dynamic environment of water, as water is a very remote and shallow area, and it is believed that the unmanned effort is required so it is necessary to set the criteria to control these nodes random movements that continuously happened from water currents [6,7]. By assigning the IDs and its mechanism we introduce the LBA-TANVEER in which the whole mechanism is presented.
The medium of communication between anchored and sonobuoys is the acoustic channel, as this is the practice of all ASANs. At the terrestrial environment, the sonobuoys used an audio signal to send the data to the base station further [41]. It has been assumed that packets received at any sink would be consider successfully received at all sinks by using the edge of the multi-sink model. For example, if the node ‘i’ sends data to another node ‘j’ with energy ‘E’ and vice versa, it first calculates the angle by using the tri-angular approach and sends the data accordingly, and then the consumption of energy at this event is the same at both ends.
In our work, we made some consideration of this and it is because our focus was on the energy efficiency of the model and avoidance of empty regions [42,43]. (i) The first and foremost consideration is that to sends data for one node to another, it first calculates the angle coordinates on the base of the vector localization service [26,40,41,42,43,44]. (ii) All ordinary nodes send the data packet to sonobuoys simultaneously, and the sink node can receive multiple packets at the same time without any loss of data and collision. (iii) The vertical movements of nodes are negligible; by the way, the horizontal movement of nodes is considered with water current [45,46]. (iv) All the nodes have unique IDs assigned by LBA and will not change in the rest of the network lifetime. (v) The BINs are deployed near sink neighboring nodes so that loss of data inside the empty regions are recovered. (vi) The finding of empty regions is usually near to sink neighboring nodes so that the BIN is also deployed near the sink zone. Figure 2 presents the proposed model in which anchored nodes deployed at bottom that initiates the communication through relay nodes with a mixture of founding empty nodes by using tri-angular calculation. The layer adjustments start from bottom to top so that the communication starts from the first sent by anchored (bottom) and received at the end by sink nodes (top).
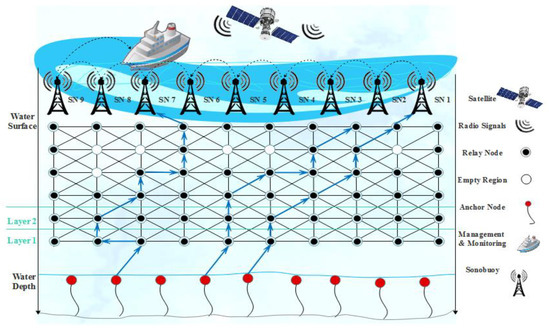
Figure 2.
Proposed model of Tri-Angular Nearest Vector-Based Energy Efficient Routing (TANVEER).
5. The Tri-Angular Nearest Vector-Based Energy Efficient Routing (TANVEER)
To ensure reliable data delivery between source and sonobuoys, TANVEER considers three basic parameters for forwarding the data among the nodes such as angle, energy, and number of nodes. These three parameters play a part and parcel role to implement the said idea. These parameters improve the performance of the algorithm and make it energy efficient. The occurrence of empty regions is usually found around the sink neighboring nodes. Three types of formats are present for nodes communication as horizontal, vertical, and diagonal according to the availability of the next node. Firstly, all the nodes are assigned in a layer-based adjustment in which each corresponding upward and downward layer have equal distance. Data are delivered through the angle base approach. Basically, every node computes the angle three times in all possible directions and moves forward for the next node. The data delivery and recovery are only performed on the decided routing path; furthermore, for the recovery process, the binary inter-nodes are introduced where the angle does not make it possible to compute. In order to minimize collision and loss of data packet, one node transmits a one data packet at a time. The detail of each phase is described in the following subsections.
5.1. Empty Regions Selection
An optimal way to select the empty regions is based upon the number of resources used in the acoustic environment. The energy is one of the most fundamental resources where nodes are enabled to join the network and process the data communication towards the sonobuoys [47,48,49]. The section of empty regions ‘Ser’ is directly based upon the node’s energy ‘En’, where ‘i’ is the total number of empty regions selected (i varies from 0 to N; where ‘N’ is the total number of nodes inside the empty regions) every node, before forwarding the data packets computes angle three times for three directions like (horizontal ‘x’, vertical ‘y’, and diagonal ‘z’). Multiple neighbor’s nodes with respect to angle are also selected when there is no empty region throughout the routing path from the anchored node to sonobuoys. Additionally, the related mathematical equation is used to selection of total number of empty regions as in Equation (1):
This equation boosts the concept of smooth delivery of data (when there is no void nodes [50,51,52]) and trace out the empty region on the routing path. It fits for medium and large-scale networks because when the number of nodes increases, the ratio of occurrence of empty regions ‘Er’ also increases [53,54]. Selection of the multiple number of nodes increased the data packet ratio and throughput of the network. Another factor that needs to be discussed is the packet acknowledgement (PACK) that helps to select the next layer and node, once the layer will be selected, that is obviously select by PACK, it is easily select the next data forwarder node. This selection leads the routing path through bypassing the empty regions [40] until the data are received to sonobuoys. Basically, the PACK is defined as and is the confirmation of the receiving of beacon or hello packet message. It is the practice of acoustic communication before sending the data to check which nodes are alive/part of the network [55]. If the packet is sent by the node of the first layer (N (l1) to the node of the second layer (N (l2) with the difference between layer (D), it first computes the angle with all coordinates to create an existing routing path between these layers with a possible direction. The selection of angle direction would be considered, where there is no ‘Er’ throughout the path. If the consecutive layers are selected for forwarding the data, all layers are responsible for providing their number of nodes to make the route robust. For example, the path was found to be smooth from anchored node to the first layer, and ‘Er’ occurs in the sink neighboring nodes area. The corresponding angle changes the direction of the vector for the flooding of data. The route vector can change at any stage by avoiding the ‘Er’ occurrence, as this is only done to handle the exceptional case. The corresponding mathematical Equation (2) below describes the selection of layers and nodes and routing path with angle:
where ‘Sn*’ is the closest optimized sink in which the total number of nodes with the difference of empty regions that selects for data delivery as in Equation (3):
5.2. Energy Efficient Nearest Vector Selection
Nearest vector selection is based on the number of nodes and angle calculation, as discussed earlier. The angle will be calculated in three consecutive adjacent directions. The movement of the angle vector is only selected when there is the next forwarder node, and its neighbor node is available without any empty zone. The next forwarder node further computes the angle again and repeat the aforementioned process in order to avoid the empty nodes. Energy is an essential part of underwater communication, especially in the IoT enabled environment [56]. Due to acoustic communication, the nodes are deprecated their energy value continuously. Furthermore, mobile water and dynamic topology also have an effect on the overall health of the network. As the path becomes longer by selecting the number of nodes towards the sonobuoys, then the nearest vector path is selected. It is because; by computing the angle thrice only those nodes are selected that cover the angled cone and have the next link with forwarder nodes Moreover, a detailed survey of underwater ad hoc networks is presented in [46,47,48,49] where various methods of underwater communication are discussed. For every nearest vector it selects according to the availability of the node ‘Nv’, and angle coordinates ‘A(x, y, z)’, in such a way that ‘Nv ∈ A (x, y, z)’ but not empty regions ‘Nv ∄ Er’ towards the ‘Sn’, Equation (4) becomes:
After the selection of nearest vectors from the set of nodes, the routing path is established towards the sonobuoys, near to it, if the sudden node dies and is able to create the ‘Er’, the routing path is changed to ‘PCHG’ and calculates the angle once again. The ‘PCHG’ mechanism is defined as it is the alternate adjustment for routing path while the next forwarder acknowledges even received the ‘Nv’ nodes, and its frequency ‘f’ is the proper set of ‘Tn’. If ‘Tn’ is less than ‘Nv’, the ‘Sn’ directly available to receive the packet such that ‘Nv ∝ f’ and according to the path selection mechanism, so the difference ‘D’ between the nearest sonobuoys and the node is basically as in Equation (5):
PCHG will be implemented through the expression as in Equation (6):
It is a bi-conditional structure that means the path does not change if and only if the ‘ACK’ is continuously received with sonobuoys ‘Sn’. The available nodes from ‘0 to Nv’ the minimum selection of total frequency of nodes ‘f’ is subtracted with 1 from the total number of nodes by calculating the angle coordinates to change the path ‘PCHG’. Ultimately it sets the path change, and the route again receives the packet from the node (1 is used for this node that holds the data packet before getting the node of the empty region). Meanwhile, by changing the path, it has the opportunity to select more nodes to forward the data packet further; the detail of this strategy is discussed in Algorithms 1 and 2. Additionally, if the nodes cannot be selected (or there is no availability) at the top of the layer near to water surface, the packet is discarded, and the alternate novel approach is used as discussed in Algorithm 3, in which extra watchman nodes are deployed around the edges and near the sonobuoys to rescue the discarded data packets and minimize the occurrence of packet loss ratio.
6. Layer-Based Adjustment (LBA)-TANVEER
Most of the experiments have been done in deep and shallow water deploying nodes for different purposes such as oil exploration and mineral findings and for some safety-critical applications like [43,44,45,46,47,50,53]. When the environment is enough complex, then the deployment of nodes in random order is not the rational decision; therefore, to avoid as well as accurate detection of empty regions between the nodes the layer-based adjustment of the nodes is aligned for our experiment. All the nodes are deployed in equal layers with multi-sink architecture in such a way that every layer assigned with a unique ‘ID’. Each sensor node gets a layer ‘ID’ by broadcasting the ‘Hello Packet (HP)’ from the sonobuoys. As all the sensor nodes are below the sonobuoys, so it is easy to attempt the layer ‘ID’ so that each node will be uniquely identified by receiving the ‘HP’. In order for each rebroadcasting mechanism, the decrement is applied by the total layer count field of the ‘HP’. The numbering of the ‘layer-ID’ is assigned in ascending order from top (sonobuoys) to bottom (anchored nodes) so that the first layer is the closest layer towards sonobuoys and so on, and this is continued until the whole nodes of the network are assigned a ‘layer-ID’.
Initially, the ‘layer-ID’ will be static until the sonobuoys send the next update after a specific time interval. The nodes that directly receive the ‘HP’ from sonobuoys will be considered the first layer, and with the decrement of one in the total layer, count field rebroadcast the packet for other below nodes of the first layer. Hence the second decrement is for assigning the ‘ID’ for the second layer nodes until the total layer count field becomes zero. As the counter field becomes zero, the further broadcasting of ‘HP’ is stopped. All sonobuoys that usually present on the surface of the water have fixed static ‘layer-ID’ that is ‘0′. Broadcasting is started with the total layer count field value that is ‘9′, and the ordinary nodes that is ‘N1 to N6′ received the ‘HP’ directly from the sonobuoys and were assigned the ‘layer-ID ‘1′. with the decrement of 1 the nodes ‘N7 to N12′ received ‘HP’ from the upper layer nodes and were assigned the ‘layer-ID ‘2’’.
Meanwhile, this will continue until the nodes of the last layer get ‘ID’. In case the nodes received multiple ‘HP’, the Tri-angular nearest vector approach is used to compare the value of the ‘Max-Layer-count’ field of ‘HP’. If the field value is the same, take one ‘HP’ into account and discard the other ‘HP’, and with different ‘Max-Layer-count’ field values, the nodes chose only the packets with greater value in the field and discarded other packets. Figure 3 presents the overall scenario of LBA-TANVEER, and Algorithm 1 discusses the assigning of layers ‘ID’ in LBA.
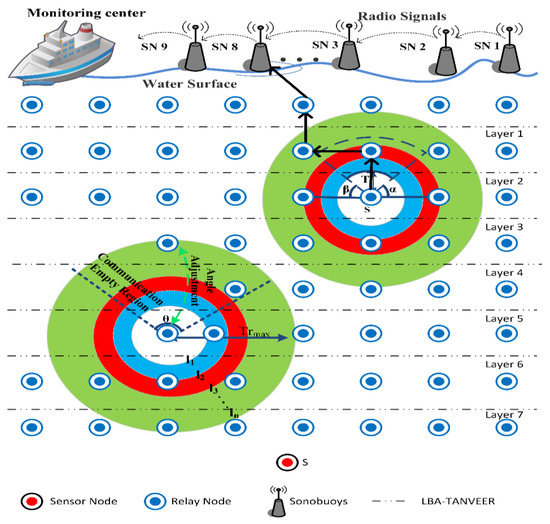
Figure 3.
Layers-Based Adjustment (LBA) to ordinary nodes.
| Algorithm 1: Layer-Based Adjustment of Nodes. |
| 1. Procedure ASSIGNING LAYERS (Source, Sonobuoys (Sn)) 2. Total Layers (TL) = 9 3. IF HP: Hello Packet notification having seq Layer-ID 4. If Own-Layer-ID = 00 5. For n = 1 6. if n 7. 8. HP. Add (seq Layer-ID (N ID (x), (y), (z))) 9. 10. Assigning Layer-ID 11. end if 12. End For 13. IF (Own-Layer-ID ≤ n) 14. Discard HP 15. Else 16. Own-Layer-ID = n 17. n + + 18. Broadcast HP further 19. End IF 20. End IF 21. End If 22. End for 23. No further broadcast for this Sink-HP 24. End Procedure |
7. Data Packet Delivery (DPD)-TANVEER
Any sensor and actor nodes want to begin the transmission; firstly, they check the remaining energy values ‘Re’ of the corresponding nodes and calculate the angle for flooding data packets. ‘PACK’ is already defined in such a way that the data packet is only sent when the next forwarder nodes are available to receive the data as well as sends the proper acknowledgments. The angle calculation is based on three attempts as the horizontal with the same layer nodes, vertical for the upper layer and diagonal to support horizontal and vertical communication. The nearest vector is only calculated in order to respond to the tri-angle strategy in such a way that which path is best for forwarding the data packet throughout the sonobuoys. The adjustments of layers are made during packet acknowledgment via Equation (2) and the shortest path without considering the empty regions of Equation (3) play our role. If the forwarder layer does not receive acknowledgment due to empty regions, the path change mechanism will be applying according to Equation (6) in which the path will only be changed when ‘Er’ is present with the neighboring node where the data are being received by the sonobuoys. Another reason for path change is also described if the next forwarder node is not available for another node, then it automatically considers the packet to be discarded. Algorithm 2 describes the data packet forwarding towards the sonobuoys via the nearest vector-based node’s availability. In this algorithm the node ‘ni’ want to send the packet node ‘nj’ with the distance ‘Dij’ from ‘l1 to l2′ without considering the ‘Er’, the total frequency of nodes ‘fn’ is basically from source to sonobuoys is, ‘Tfn = D(ni, l1) ∗ D(nj, l2) − P (Er)’, where ‘Sn’ is the total number of nodes available in each layer to find the closest next forwarding nodes with short distance as defined in Equation (5). In order to define the flooding zone, we are assuming that by using the basic linear formula ‘θ = 90 ± 10 K’ the nodes have the capability of computing the angle. Here, ‘K’ is a variable and has a finite set of values, ‘K {1, 2, 3}’.
| Algorithm 2: Angle Based-Data Packet delivery. |
| 1. Procedure ACQUIRE ANGLE FOR NEXT NODE (Sourceni, Sn (PACK) 2. For 3. Tfn = D(ni, l1) ∗ D(nj, l2) − P (Er) then 4. θ = A (x, y, z) 5. Adjust angle for corresponding nodes ni → nj 6. End For 7. n 8. j 9. While θ = 90 ± 3K do 10. 11. If Ni and D (Sn) = (N (ln-l1) then 12. PCHG = 13. For Ni 14. Nj 15. End While 16. End For 17. Else 18. Modify θ = A (x, y, z) CHG 0 < θ < π 19. End if 20. For Er do 21. for Re (Ni then 22. Compute distance for nearest neighbor vector node then 23. if Nv: Tfn = D(ni, l1) ∗ D(nj, l2) − P (Er) do 24. Dissemination of data packet delivery until Er PCHG 25. end if 26. end for 27. End For 28. End if 29. End Procedure |
After this, if there is no outcome in terms of packet receiving the source node this will increase the value of ‘K’, as the value of ‘K’ is increased the flooding zone is also increased under the angle condition that is (0 < θ < π). The value of ‘K’ is helpful to control the amount of energy consumption of the said node and end-to-end delay. The nodes movement directly depends on the base of the decided value of ‘K’. In the case of multiple nodes inside the zone, all nodes will calculate their priorities and send ‘HP’ to the source node, and the data are forwarded by highest priority node. The priority queue that is considered is of maximum 5 that will save the source node information, the advantage of this strategy is the next time data that will be sent without calculating angle zone, but this will only be kept in a specific interval of time to maintain the priority acknowledgment, otherwise it will again compute the appropriate angle. Usually, for the medium and small-scale network, this would not happen, and once the angle has been computed, it will remain the same and be used for the rest of the network lifetime. Hence, every sensor node knows its base angle that is ‘π/2′ in the upward, horizontal and diagonal direction and it is also a built-in hardware module; by the way, according to the environmental situation every node have enough capability to compute and increasing the flooding zone by changing the value of ‘K’. Here it is important to know that on every attempt the previously calculated area will be added into the newly defined zone to take advantage of mobility. Further, Figure 4 presents the computed angle with the value of ‘K’, and Algorithm 2 discuss the angle-based data packet delivery, i.e.; DPD-TANVEER, while tri-angular adjustment of horizontal ‘A(x)’, vertical ‘A(y)’ and diagonal ‘A(z)’ and the scenario of DPD-TANVEER are discussed in Figure 5 and Figure 6, respectively.
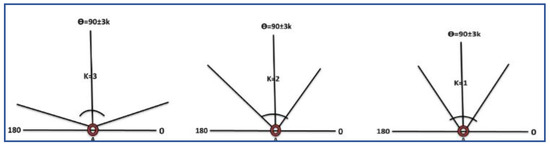
Figure 4.
Possibility of angle flooding zone when Node Uses K = 1, 2 and 3.
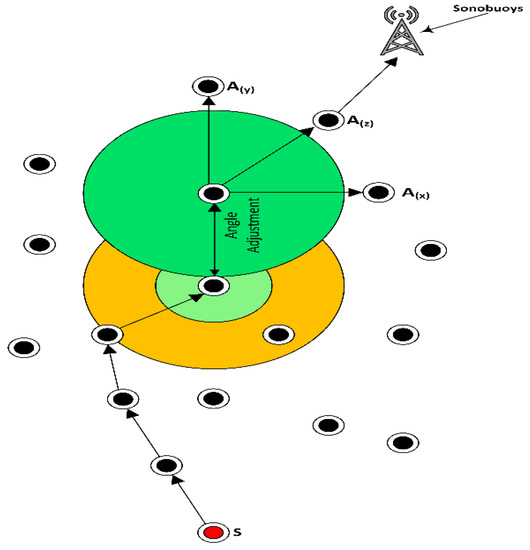
Figure 5.
Tri-angular adjustment of horizontal A(x), vertical A(y) and diagonal A(z) with reference to Figure 4.
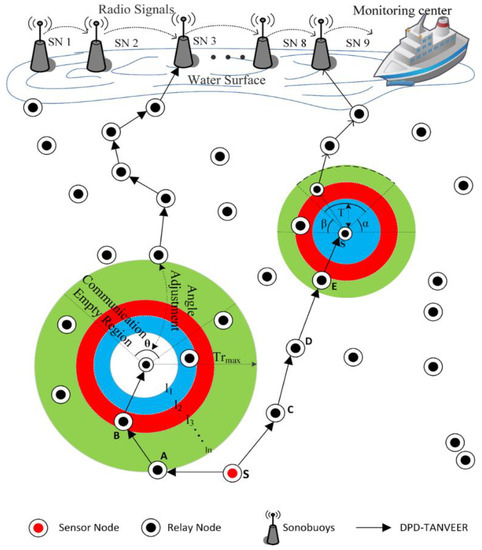
Figure 6.
Mechanism of Data Packet Delivery (DPD)-TANVEER.
8. Binary Inter Nodes (BIN)-TANVEER
As the data packet delivery is increased, the probability of the empty regions inside the network is also increased [45,46,57]. Therefore, the BIN-TANVEER is used to ensure the packets that are not delivered to the next nodes due to empty regions is must be delivered to the desired destination via the path change mechanism. For this, we introduced ‘Binary Inter Nodes’ called watchman nodes inside each layer. These watchman nodes are responsible for controlling the communication at both ends, like the left and right of the network. Figure 7 illustrates the proper mechanism of BIN-TANVEER. For example, the source node ‘S’ wants to send the data packet to the nearest nodes, and it first obtains the information of the above two layers with all corresponding neighbor nodes. Up to two layers, those nodes that are closer to each other are ‘n1, n2, n3′, and ‘n4′. In the first layer, the ‘n2′ node is nearest with respect to energy, and TANVEER further explores to the next node to ‘n2 like n3 and n4′ for other next two layers. The angle is computed for the best three possible directions towards the destination with the value of ‘k’, as discussed in Algorithm 2. As ‘n4′ shows the empty region, it moves toward the nearest node in a relevant direction with a reference of the calculated angle. The possible routes of movements are horizontal with the same layer or vertical, and the diagonal path is available for the next upper layer according to the availability of the nodes. If the data are delivered and ‘n4′ becomes an empty node, then BIN-TANVEER works.
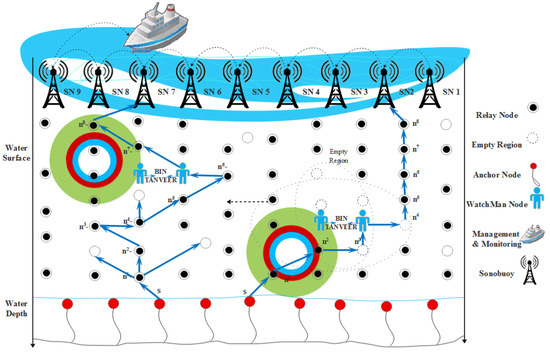
Figure 7.
Working mechanism of binary inter nodes (BIN)-TANVEER with watchman nodes.
It takes the data from the empty node like ‘n4′ and delivers them to the next available node. The recovery procedure works with looking forward to the least number of layer count and tries to find out the next nearest node in order to proposed mechanism energy efficient with all aspects. In this way, instead of dropping the packets and increasing the packet loss ratio of the overall network, BIN nodes are responsible for doing this every time. Therefore, they come into contact or active only when the empty regions are detected. Meanwhile, the detection of empty regions is done by receiving the ‘PACK’ of the nodes as in Equation (6), and ‘PCHG’ is basically the function of BIN-TANVEER, and it used for the recovery procedure. In an exceptional case, if the availability of the node is not present around the empty regions, then BIN sends a data packet greedily to sonobuoys. Otherwise, it transfers the information to the nearest node for successful data communication among the network nodes. Figure 7 shows the working of BIN-TANVEER and Figure 8 represents the transmission adjustment of watchman, while Algorithm 3 depicts the proposed mechanism. Moreover, the flowchart of proposed scheme and its sub-sections are illustrated in Figure 9.
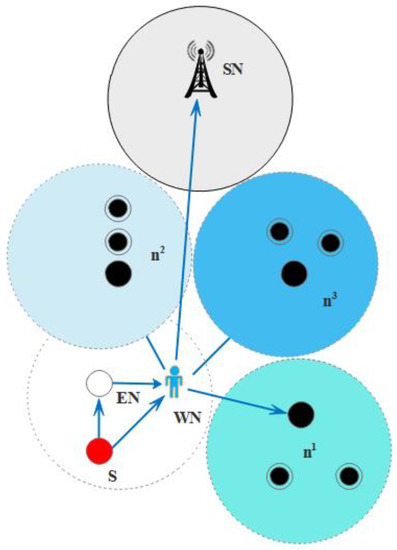
Figure 8.
Possible transmission adjustment of Watchman Node (WN) with Empty Node (EN).
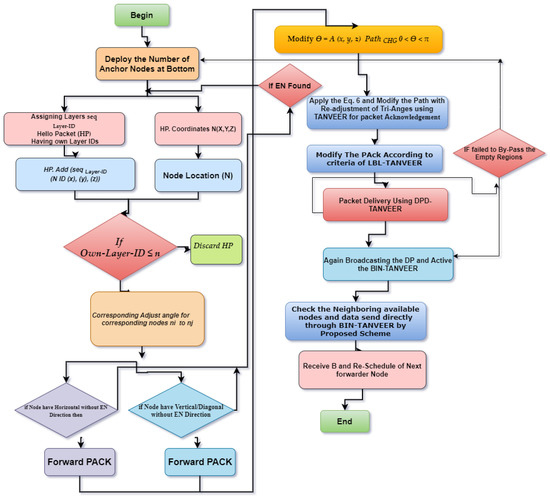
Figure 9.
Flowchart of the proposed scheme.
| Algorithm 3: Empty Regions Recovery Using Binary Inter-Nodes. |
| 1. Procedure FORWARD THE DATA PACKETS (θ) (Source, Sonobuoys) 2. IF Empty region or node = 0 then 3. Compute the angle with A (x, y, z) 4. Select the appropriate nodes 5. Forward the data packets () 6. ELSE 7. For Nv: Tfn = D(ni, l1) ∗ D(nj, l2) P (Er) do 8. Modify θ = A (x, y, z) CHG 0 < θ < π 9. If 10. 11. Re-schedule angle and forwards the data packets () 12. Proposed mechanism () 13. END IF 14. End For 15. End If 16. End Procedure |
9. Achievable Regions
In order to calculate the achievable regions inside the network in an optimized manner, we used a linear programming approach in this section. To obtain the optimal result, the mathematical technique linear programming is used as same as [17]. The objective function that we analyzed through linear programming, minimum energy consumption, and maximum throughput is discussed in Figure 10 and Figure 11.
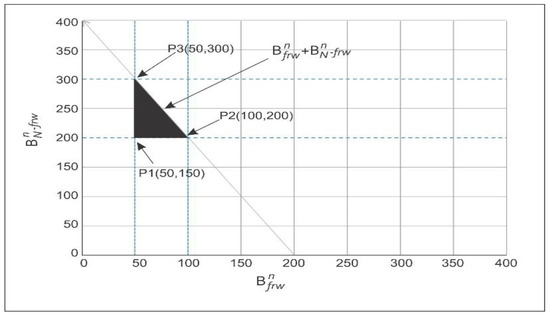
Figure 10.
Possible feasible region of throughput maximization.
9.1. Minimization of Energy Consumed
To achieve an optimized result to calculate the energy consumed, the linear-based functions and constraints are the best way starting from the objective function and followed by linear constraints. The objective function of the minimization of energy consumed is defined as:
The linear function of energy consumed minimum is given in Equations (8)–(10).
Equation (8) deals with the required energy to start the transmission and consumption should be less than the initial amount of energy of the node. Equation (9) discusses the next layer node that has the minimum energy consumption. Equation (10) is about the transmission range with its maximum transmission range of the node. The proposed scheme of calculation of the energy consumed per node is in Equation (11) as follows where energy consumed includes both starting and ending value of energy per node i.e.,:
where,
‘Est’ is the amount of energy when the transmission is started and, ‘Ptx’ is the transmission power.
‘Eend’ is the amount of energy when the transmission is ended, while ‘Prcv’ is the transmission power.
Graphical expression: Graphical analysis is present in order to clear the picture of the feasible empty regions. For example, data size = 100 bytes, data rate = 60 kbps, Ptx = {0.5,1, 1.5, 2}W and Prcv = {0.015,0.025, 0.05,…..,0.1}W, then feasible region for energy minimization is computed as per the aforementioned constraints in Equations (8)–(10):
The boundary of the feasible region can be plotted in Figure 10 from the above equations:
P1 (1, 0.1) = 1.1 J
P2 (1, 0.3) = 1.3 J
P3 (4, 0.3) = 4.3 J
P4 (4, 0.1) = 4.1 J
Hence by selecting any values from these plotting points obtain the available minimization of energy consumption.
9.2. Maximum of Network Throughput
As network throughput is the major parameter to determine the efficiency of the network. To improve the network throughput same linear programming approach is used as discussed in energy minimization. The related expression is as follows in Equation (18):
The following constraints are as follows:
Equation (19) deals the required energy to start the transmission, and consumption should be less than the initial amount of energy of the node and Equation (20) discussed the next layer node that has the minimum energy consumption. Equation (21) is about the transmission range with its maximum transmission range of the node. Equation (22) shows that the distance between two nodes ‘i’ and ‘j’ is minimum for successful communication. The proposed scheme of calculation of the maximum throughput is the bandwidth assigned for the next forwarder node in the case of empty regions and is in Equation (23) such that ‘B_frw^n’ and for non-forwarding node is ‘B_(N-frw)^n’. The overall bandwidth is calculated for the aforementioned equations are below where bandwidth is assigned for 150–300 KHz as from [17].
The boundary of the feasible region can be plotted in Figure 11 from the above equations are:
P1 (50, 200) = 250 K Hz
P2 (100, 200) = 300 K Hz
P3 (50, 300) = 350 K Hz
P4 (250, 300) = 550 K Hz
Hence by selecting any values from these plotting points obtain the maximized throughput.
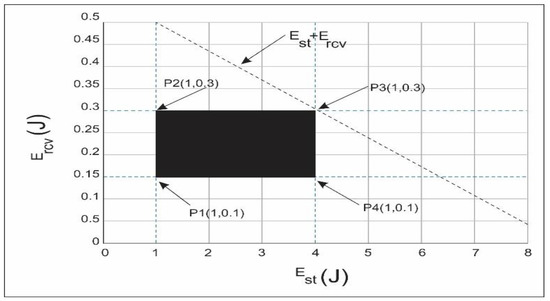
Figure 11.
Possible feasible region of energy minimization.
10. Simulation Results and Discussion
The proposed scheme TANVEER, LBA-TANVEER, DPD-TANVEER, and BIN-TANVEER was evaluated in NS-3 (with AquaSim Framework) against related parameters like packet delivery ratio, packet loss ratio, the fraction of empty region and network throughput. The energy consumption of the network was also measured. All these parameters were compared with the baseline approach L2-ABF [7]. Additionally, our major focus was on the other two constraints like minimization of energy consumption and maximum traffic throughput to achieve reliable data communication in order to reduce void hole occurrence [41,42,43,44,45,46]. Therefore, the analysis of transmission range and energy per data packet was conducted in the result section.
10.1. Performance Control Parameters
The performance control parameters directly affect the performance of the network system like transmission range, data rate, energy deviation, and payload of data packets. The nodes were randomly deployed in the form of the layer with the area of 2000 m × 2000 m × 2000 m. The 600 nodes were used, including 40 sink nodes, and the transmission range varied from 150 m to 400 m. The data rate is 16 to 32 kbps for performance evaluation against baseline approach L2-ABF, and the deviation of energy for empty regions was 32, 64, 128 kbps. The data packet payload was set to 100–200 bytes. The value of energy consumption was Pt = 2 W, Pr = 0.2 W and Pi = 0.02 W for transmission, reception and idle energy of BIN nodes, respectively. Table 2 presents the constraints used in the simulation environment.

Table 2.
Simulation Evaluation Constraints.
10.2. Fraction of Empty Regions
The fraction of empty nodes becomes compact, then the empty region is created inside the network so the result would be conducted according to empty regions occurrence and compared with L2-ABF. The heterogeneous relation comes into existence in all approaches like TANVEER and its sub-sections, and as the nodes increase the occurrence ratio of empty regions increased. Firstly, the maximum fraction can be observed with respect to DPD-TANVEER, which is under half of the network nodes.
However, a small upward sliding was observed from 300 to 500 nodes. After this, an increasing trend presents in which a number of nodes remained constant in this area. The decrement is because of DPD-TANVEER when the empty regions are infrequent amount then, for the time being, data are shifted towards the watchman nodes and then again revert to the ordinary nodes. The ordinary nodes further transmit the data to sonobuoys. If there are no further empty nodes, the multiple occurrences of the empty node on the same path is tackled by the help of BIN-TANVEER as watchman nodes. Watchman nodes present in each layer in order to minimize the end-to-end delay. This will help to save not only the time delay but also achieve the purpose of nodes in layers order as it is done in LBA-TANVEER. Both techniques have little similarity in results due to the layer-by-layer angle approach used in L2-ABF and tri-angular approach in TANVEER. The BIN-TANVEER beats the baseline approach as the fraction of empty nodes does not handle by ABF, because of the extra supplementary nodes used like BIN. The direct transmission is sent to the forwarding nodes by calculating the angle, while on the other hand, the DPD-TANVEER handles this situation work with BIN-TANVEER and bypasses the empty regions, as shown in Figure 12.
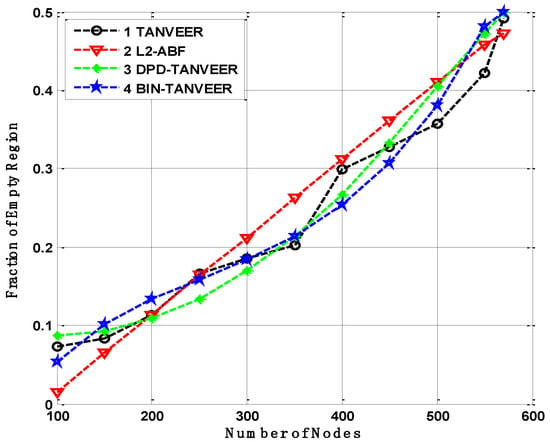
Figure 12.
Fraction of empty regions occurrence in TANVEER vs L2-ABF.
10.3. Packet Delivery Ratio
It is assumed that the delivery ratio is directly proportional to the number of nodes increased in the network [57]. Therefore, the density plays a part and parcel role in the underwater environment. It is clear that the BIN-TANVEER has the highest PDR results due to the functional nature of the proposed mechanism. As BIN is working for the rescue nodes to avoid the data loss, hence the PDR is achieved at the desired amount even in the density of the network. When the trap of the empty region is going to start the avoidance of data loss, alternative nodes in the form of BIN are considered the best substitute to deliver the data to nearby sonobuoys. Meanwhile, the TANVEER describes the average success ratio of packet transmissions, i.e., it is neither high nor low, because it operates is single parameter total packet delivered to the sonobuoys. The dynamic topology of the network is also affecting the efficiency of data transmission due to nodes movements.
As compared to the baseline approach of L2-ABF with the proposed technique is shown in Figure 13. The energy consumption of both techniques is slightly high due to the means of data transmission. The data forwarding in L2-ABF is based on angle cone calculation, whereas TANVEER computed the angle thrice. It also requires more energy for some recovery mechanism. The DPD-TANVEER has achieved the desired results because it considers the only paths that ensure bypassing the empty regions causes high PDR.
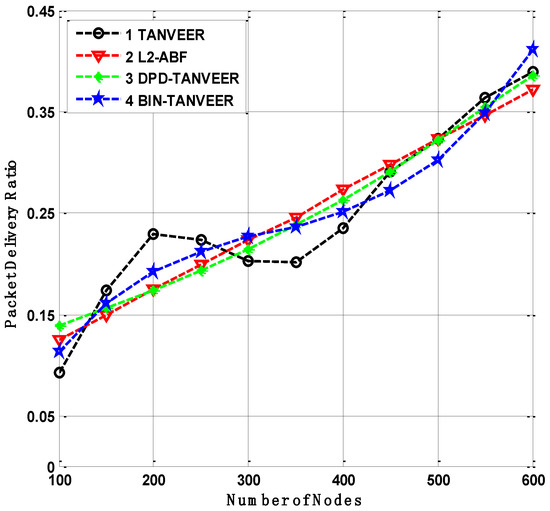
Figure 13.
Packet delivery analysis of TANVEER vs. L2-ABF.
10.4. Energy Consumption
The comparison of energy consumption is displayed in Figure 14, where the energy is delivering a single packet towards the destination. It observed that the minimum energy consumption for the DPD-TANVEER is when it could bypass the empty regions and directly sends the data packets to the sonobuoys, so it is slightly lower than L2-ABF. The minimum possible energy consumption for each packet is 0.3 J with DPD-TAANVEER and 0.4 J of L2-ABF. This is only due to singe angle-based measuring for the dissemination of the data packets.
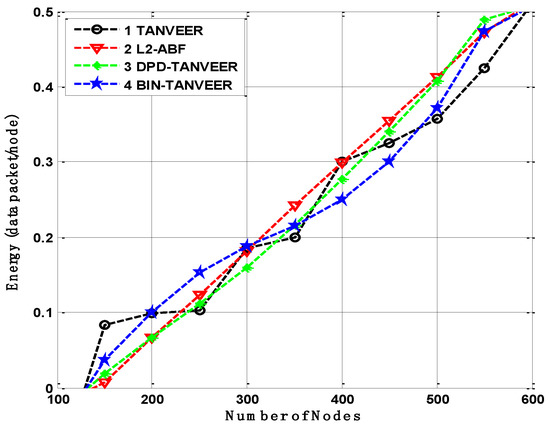
Figure 14.
Energy consumption of TANVEER vs L2-ABF.
The BIN-TANVEER is comparatively higher, saving the amount of energy, as these nodes only come into contact when the empty regions need to be rescued. It is lower than the other two proposed schemes as well as a baseline approach. The foremost reason is the alternative route adjustment for the nearby sonobuoys increase the amount of energy for the time being to perform recovery data from the empty nodes. Nonetheless, this amount is not a sufficient reason for the high consumption of energy requirement as L2-ABF is considered the battery resources comparatively higher than the technique as mentioned above.
10.5. Throughput
Figure 15 presents the throughput of the network that indicates the successful packets delivery from source to sonobuoys, and it is measured in bits/second (bps). The TANVEER have streamline throughput for 250 number of nodes with the throughput of 130 bps. As the number of nodes increased, the occurrence of empty regions starts, and the nodes are willing to finding the alternate path. In this situation, the TANVEER suddenly decreased up to 110 bps and then again increased up to 260 bps for the next 100 number of nodes, at this point, it was smooth throughout the network’s lifetime and achieved 370 bps for full number of nodes that are used under experiment. The DPD/BIN-TANVEER both depict the same behavior that started from 40 nodes with 45 bps and achieved 400 bps with 500 nodes, the reason is that as the empty region is found inside the network the routing path is changed and serve as BIN-TANVEER and the ratio of DPD is increased for the time being. In this case, the TANVEER consumes little more energy, but throughput is reached at 370 bps.
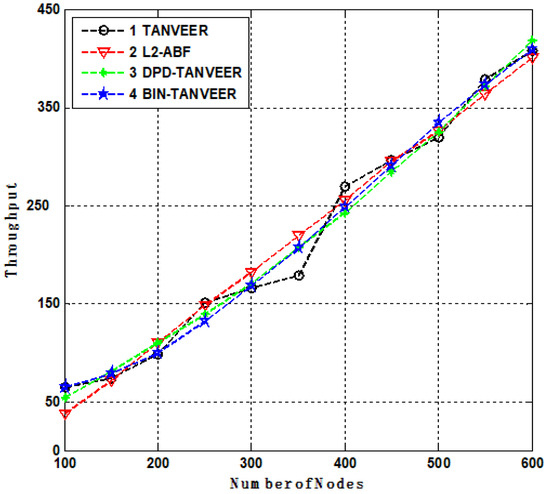
Figure 15.
Throughput Analysis of TANVEER.
10.6. Influence of Coverage Area
From Figure 16, in order to verify the coverage area of the TANVEER, BIN-TANVEER, and DPD-TANVEER, we have conducted simulation against the number of nodes and coverage area. The slip of the area is also shown beside the simulation graph. From Figure 13, TANVEER has the highest coverage area among all other sub-sections, including the baseline approach. For example, the L2-ABF works with 500 nodes, and the quantity of nodes with TANVEER is 100 more nodes in order to cover the simulation environment and network volume.
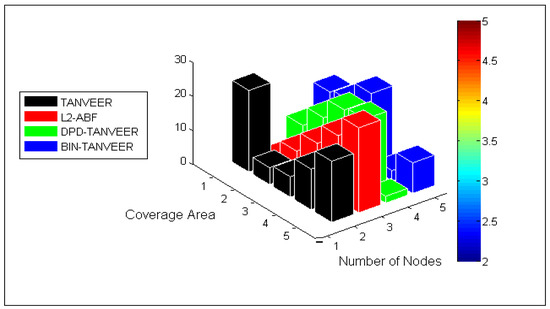
Figure 16.
Analysis of coverage area.
L2-ABF used an angled approach while TANVEER works with tri-angular vector-based approach, and the DPD mechanism is more robust than the L2-ABF approach. Furthermore, the BIN technique that is novel in nature is only introduced with TANVEER, and the alternate path coped with binary internodes, hence the coverage area from source to sonobuoys was maximum as desired and that is depicted in Figure 16.
11. Comparative Performance Trade-Offs
The comparative performance analysis is presented in this section of our proposed scheme with a baseline approach. Our proposed scheme consists of the following: TANVEER, DPD-TANVEER, and BIN-TANVEER; furthermore, the LBA is another additional layout for deploying the number of nodes. The comparative approach L2-ABF is considered the angle-based flooding without knowing in advance either the next forwarder nodes is enough available for flooding or not, which is the reason every time the angle must be computed for forwarding the data.
Therefore, the overall consumption of energy is increased and there is minimum throughput. However, in the dense region, usually, the nodes not much consume energy near the anchored node, so the occurrence of empty region is not much observed in L2-ABF. On the other hand, TANVEER makes an angle for forwarding the data packets, and then it remains stable with the value of K and three possible directions. In the worst case, if the empty region is detected on one side of the network, the change mechanism shifted the delivery of data on the other side of the angle. In addition, we may know in advance about the availability of the next forwarding nodes that ready to take and send the data towards the sonobuoys. Also, it tries to select the nodes with minimum neighbor set in order to optimize the routing path with the cost of low-energy and end-to-end delay. In this case, with DPD-TANVEER achieved high PDR and throughput by avoiding the fraction of empty regions. The watchman nodes in BIN take data from both sides in case of empty nodes and adjust the transmission range towards the sonobuoys, but it increases the energy consumption. The related performance trade-offs are discussed in Table 3.

Table 3.
Overall performance trade-offs.
12. Conclusions and Future Work
In this paper, we have proposed TANVEER, with its three sub-sections LBA-TANVEER, DPD-TANVEER, and BIN-TANVEER, as a routing protocol to overcome the issues of minimum throughput and maximum energy consumption in the acoustic environment. The TANVEER improve energy consumption, PDR, and throughput through bypassing the empty regions, whereas LBA-TANVEER is used to assign the node ‘ID’ to accurate detection of empty regions. However, the use of LBA-TANVEER helps to control the topology of the network. On the other hand, DPD-TANVEER uses a path change mechanism with the help of the next availability of forwarder node and improved the data delivery ratio of the network. Moreover, it has a high throughput as compared to TANVEER. Finally, BIN-TANVEER uses watchman-based adjustment of finding the empty nodes and set the watchman-based transmission towards the sonobuoys. During the empty regions of DPD-TANVEER it fails to find out any forwarder and sends the data packet to the node that is going to die. In this case, BIN takes the data from the dying node and sends it to the nearest node in order to ensure that the next selected nodes are not further empty. All the results are performed in extensive simulation against the fraction of empty region, throughput, end-to-end delay, and packet delivery ratio. The output of simulation depicts that the proposed scheme performed well against the baseline approach in different parameters like energy, throughput, and PDR. Furthermore, the major parameter of avoidance of empty regions was also achieved as compared to L2-ABF.
In future work, we planned to handle the occurrence of empty regions using an artificial intelligence technique in which nodes itself memorize the remaining energy and are replaced with their nearest neighboring node. Furthermore, the transmission range and its adjustment of the nodes is done by using a heuristics technique, so in this way, it will improve parameters such as link quality, nodes status, and energy consumption.
Author Contributions
U.D. and S.Y. have proposed the research conceptualization. The methodology is performed by M.I. and T.A. The technical and theoretical framework is prepared by, A.A. and A.G. The technical review and improvement have been performed by F.B. The overall technical support, guidance and project administration is done by W.G. and T.A. All authors have read and agreed to the published version of the manuscript.
Funding
This research was funded by the AGH University of Science and Technology, grant No. 16.16.120.773.
Institutional Review Board Statement
Not applicable.
Informed Consent Statement
Not applicable.
Data Availability Statement
Not applicable.
Acknowledgments
The authors acknowledge the support from the, Najran University, Kingdom of Saudi Arabia, University of Okara, University of Sahiwal, and COMSATS University Islamabad Pakistan, Including Lahore and Sahiwal Campuses.
Conflicts of Interest
The authors declare that there is no conflict of interest.
References
- Gkikopouli, A.; Nikolakopoulos, G.; Manesis, S. A survey on underwater wireless sensor networks and applications. In Proceedings of the 2012 20th Mediterranean Conference on Control & Automation (MED), Barcelona, Spain, 3–6 July 2012; pp. 1147–1154. [Google Scholar]
- Davis, A.; Chang, H. Underwater wireless sensor networks. In Proceedings of the 2012 Oceans, Hampton Roads, VA, USA, 14–19 October 2012; pp. 1–5. [Google Scholar]
- Xu, Y.; Liu, F. Application of wireless sensor network in water quality monitoring. In Proceedings of the 2017 IEEE International Conference on Computational Science and Engineering (CSE) and IEEE International Conference on Embedded and Ubiquitous Computing (EUC), Guangzhou, China, 21–24 July 2017; Volume 2, pp. 368–371. [Google Scholar]
- Zhu, Y.J.; Xu, P.F. Development and Applications of Underwater Acoustic Communication Networks. Commun. Technol. 2012, 6. Available online: https://en.cnki.com.cn/Article_en/CJFDTotal-TXJS201206013.htm (accessed on 17 May 2021).
- Jing, H. Coverage Holes Recovery Algorithm Based On Nodes Balance Distance Of Underwater Wireless Sensor Network. Int. J. Smart Sens. Intell. Syst. 2014, 7, 1890–1907. [Google Scholar] [CrossRef]
- Ali, T.; Jung, L.T.; Ameer, S. Flooding control by using angle-based cone for UWSNs. In Proceedings of the 2012 International Symposium on Telecommunication Technologies, Kuala Lumpur, Malaysia, 26–28 November 2012; pp. 112–117. [Google Scholar]
- Ali, T.; Jung, L.T.; Faye, I. Delay Efficient Layer by Layer Angle Based Flooding Protocol (L2-ABF) for Underwater Wireless Sensor Networks. Available online: http://www.iiis.org/CDs2012/CD2012ADII/ICTA_2012/PapersPdf/CT004EM.pdf (accessed on 17 May 2021).
- Byun, J.; Cho, Y.H.; Im, T.; Ko, H.L.; Shin, K.; Kim, J.; Jo, O. Iterative Learning for Reliable Link Adaptation in the Internet of Underwater Things. IEEE Access 2021, 9, 30408–30416. [Google Scholar] [CrossRef]
- Coutinho, R.W.; Boukerche, A.; Vieira, L.F.; Loureiro, A.A. GEDAR: Geographic and opportunistic routing protocol with depth adjustment for mobile underwater sensor networks. In Proceedings of the 2014 IEEE International Conference on communications (ICC), Sydney, NSW, Australia, 10–14 June 2014; pp. 251–256. [Google Scholar]
- Hwang, D.; Kim, D. DFR: Directional flooding-based routing protocol for underwater sensor networks. In Proceedings of the OCEANS 2008, Quebec City, QC, Canada, 15–18 September 2008; pp. 1–7. [Google Scholar]
- Coutinho, R.W.; Vieira, L.F.; Loureiro, A.A. DCR: Depth-Controlled routing protocol for underwater sensor networks. In Proceedings of the 2013 IEEE Symposium on Computers and Communications (ISCC), Split, Croatia, 7–10 July 2013; pp. 453–458. [Google Scholar]
- Noh, Y.; Lee, U.; Wang, P.; Choi, B.S.C.; Gerla, M. VAPR: Void-aware pressure routing for underwater sensor networks. IEEE Trans. Mob. Comput. 2012, 12, 895–908. [Google Scholar] [CrossRef]
- Zhou, Z.; Yao, B.; Xing, R.; Shu, L.; Bu, S. E-CARP: An energy efficient routing protocol for UWSNs in the internet of underwater things. IEEE Sens. J. 2015, 16, 4072–4082. [Google Scholar] [CrossRef]
- Yu, H.; Yao, N.; Wang, T.; Li, G.; Gao, Z.; Tan, G. WDFAD-DBR: Weighting depth and forwarding area division DBR routing protocol for UASNs. Ad Hoc Netw. 2016, 37, 256–282. [Google Scholar] [CrossRef]
- Kamaruddin, A.; Ngadi, M.A.; Harun, H. An energy efficient void avoidance opportunistic routing protocol for underwater sensor. Telkomnika 2019, 17, 1948–1956. [Google Scholar] [CrossRef]
- Draz, U.; Ali, T.; Yasin, S. Cloud Based Watchman Inlets for Flood Recovery System Using Wireless Sensor and Actor Networks. In Proceedings of the 2018 IEEE 21st International Multi-Topic Conference (INMIC), Karachi, Pakistan, 1–2 November 2018; pp. 1–6. [Google Scholar]
- Javaid, N. NADEEM: Neighbor-node Approaching Distinct Energy Efficient Mates for reliable dat a delivery in IoT enabled underwater WSNs. Trans. Emerg. Telecommun. Technol. ETT 2019. [Google Scholar] [CrossRef]
- Yan, H.; Shi, Z.J.; Cui, J.H. DBR: Depth-based routing for underwater sensor networks. In Proceedings of the International Conference on Research in Networking, Singapore, 5–9 May 2008; pp. 72–86. [Google Scholar]
- Rahman, M.A.; Lee, Y.; Koo, I. EECOR: An energy-efficient cooperative opportunistic routing protocol for Underwater acoustic sensor networks. IEEE Access 2017, 5, 14119–14132. [Google Scholar] [CrossRef]
- Huang, C.J.; Wang, Y.W.; Liao, H.H.; Lin, C.F.; Hu, K.W.; Chang, T.Y. A power-efficient routing protocol for underwater wireless sensor networks. Appl. Soft Comput. 2011, 11, 2348–2355. [Google Scholar] [CrossRef]
- Kheirabadi, M.T.; Mohamad, M.M. Greedy routing in underwater acoustic sensor networks: A survey. Int. J. Distrib. Sens. Netw. 2013, 9, 701834. [Google Scholar] [CrossRef]
- Barbeau, M.; Blouin, S.; Cervera, G.; Garcia-Alfaro, J.; Kranakis, E. Location-free link state routing for underwater acoustic sensor networks. In Proceedings of the 2015 IEEE 28th Canadian Conference on Electrical and Computer Engineering (CCECE), Halifax, NS, Canada, 3–6 May 2015; pp. 1544–1549. [Google Scholar]
- Khan, A.; Ali, I.; Rahman, A.U.; Imran, M.; Mahmood, H. Co-EEORS: Cooperative energy efficient optimal relay selection protocol for underwater wireless sensor networks. IEEE Access 2018, 6, 28777–28789. [Google Scholar] [CrossRef]
- Wang, J.; Shi, W.; Xu, L.; Zhou, L.; Niu, Q. Design of optical-acoustic hybrid underwater wireless sensor network. J. Netw. Comput. Appl. 2017, 92, 59–67. [Google Scholar] [CrossRef]
- Park, K.H.; Imran, M.A.; Casari, P.; Kulhandjian, H.; Chen, H.; Abdi, A.; Dalgleish, F. IEEE Access Special Section Editorial: Underwater Wireless Communications and Networking. IEEE Access 2019, 7, 52288–52294. [Google Scholar] [CrossRef]
- Jin, Z.; Ji, Z.; Su, Y. An Evidence Theory Based Opportunistic Routing Protocol for Underwater Acoustic Sensor Networks. IEEE Access 2018, 6, 71038–71047. [Google Scholar] [CrossRef]
- Karim, O.A.; Javaid, N.; Sher, A.; Wadud, Z.; Ahmed, S. QL-EEBDG: QLearning based energy balanced routing in underwater sensor networks. EAI Endorsed Trans. Energy Web 2018, 5, e15. [Google Scholar]
- Ali, T.; Jung, L.T.; Faye, I. Diagonal and vertical routing protocol for underwater wireless sensor network. Procedia-Soc. Behav. Sci. 2014, 129, 372–379. [Google Scholar] [CrossRef]
- Draz, U.; Ali, T.; Yasin, S.; Naseer, N.; Waqas, U. A parametric performance evaluation of SMDBRP and AEDGRP routing protocols in underwater wireless sensor network for data transmission. In Proceedings of the 2018 International Conference on Advancements in Computational Sciences (ICACS), Lahore, Pakistan, 19–21 February 2018; pp. 1–8. [Google Scholar]
- Farooq, W.; Ali, T.; Shaf, A.; UMAR, M.; Yasin, S. Atomic-shaped efficient delay and data gathering routing protocol for underwater wireless sensor networks. Turk. J. Electr. Eng. Comput. Sci. 2019, 27, 3454–3469. [Google Scholar] [CrossRef]
- Ali, T.; Jung, L.T.; Faye, I. Three hops reliability model for underwater wireless sensor network. In Proceedings of the 2014 International Conference on Computer and Information Sciences (ICCOINS), Kuala Lumpur, Malaysia, 3–5 June 2014; pp. 1–6. [Google Scholar]
- Prabha, K.L.; Selvan, S. Energy efficient energy hole repelling (EEEHR) algorithm for delay tolerant wireless sensor network. Wirel. Pers. Commun. 2018, 101, 1395–1409. [Google Scholar] [CrossRef]
- Shaf, A.; Ali, T.; Farooq, W.; Draz, U.; Yasin, S. Comparison of DBR and L2-ABF routing protocols in underwater wireless sensor network. In Proceedings of the 2018 15th International Bhurban Conference on Applied Sciences and Technology (IBCAST), Islamabad, Pakistan, 9–13 January 2018; pp. 746–750. [Google Scholar]
- Draz, U.; Ali, T.; Yasin, S.; Fareed, A.; Shahbaz, M. Watchman-based Data Packet Forwarding Algorithm for Underwater Wireless Sensor and Actor Networks. In Proceedings of the 2019 International Conference on Electrical, Communication, and Computer Engineering (ICECCE), Swat, Pakistan, 24–25 July 2019; pp. 1–7. [Google Scholar]
- Ali, T.; Yasin, S.; Draz, U.; Ayaz, M. Towards formal modeling of subnet based hotspot algorithm in wireless sensor networks. Wireless Pers. Commun. 2019, 107, 1573–1606. [Google Scholar] [CrossRef]
- Draz, U.; Ali, T.; Yasin, S.; Waqas, U.; Rafiq, U. EADSA: Energy-Aware Distributed Sink Algorithm for Hotspot Problem in Wireless Sensor and Actor Networks. In Proceedings of the 2019 International Conference on Engineering and Emerging Technologies (ICEET), Lahore, Pakistan, 21–22 February 2019; pp. 1–6. [Google Scholar]
- Ayaz, M.; Abdullah, A.; Faye, I. Hop-by-hop reliable data deliveries for underwater wireless sensor networks. In Proceedings of the 2010 International Conference on Broadband, Wireless Computing, Communication and Applications, Fukuoka, Japan, 4–6 November 2010; pp. 363–368. [Google Scholar]
- Wang, Z.; Han, G.; Qin, H.; Zhang, S.; Sui, Y. An energy-aware and void-avoidable routing protocol for underwater sensor networks. IEEE Access 2018, 6, 7792–7801. [Google Scholar] [CrossRef]
- Kamaruddin, A.; Ngadi, M.A.; Harun, H. Energy Efficient Opportunistic Routing Protocol (EE-OR) for Underwater Wireless Sensor Network. J. Phys. Conf. Ser. 2019, 1174, 012010. [Google Scholar] [CrossRef]
- Liou, E.C.; Kao, C.C.; Chang, C.H.; Lin, Y.S.; Huang, C.J. Internet of Underwater Things: Challenges and routing protocols. In Proceedings of the 2018 IEEE International Conference on Applied System Invention (ICASI), Chiba, Japan, 13–17 April 2018; pp. 1171–1174. [Google Scholar]
- Arora, P.; Jain, S. Underwater Sensor Network Delay Aware Routing Protocols: A Survey. In Proceedings of the 3rd International Conference on Internet of Things and Connected Technologies (ICIoTCT), Jaipur, India, 26–27 March 2018; pp. 26–27. [Google Scholar]
- Khalid, M.; Cao, Y.; Arshad, M.; Khalid, W.; Ahmad, N. Routing Challenges and Associated protocols in Acoustic Communication. In Magnetic Communications; CRC Press: Boca Raton, FL, USA, 2018; pp. 91–103. [Google Scholar]
- Ahmed, M.; Parveen, S.; Hussain, N.; Naeem, N.; Malookani, R. VNR: Void Node Removal Routing Protocol for Underwater Wireless Sensor Network. IJCSNS 2018, 18, 162–169. [Google Scholar]
- Coutinho, R.W.; Boukerche, A.; Vieira, L.F.; Loureiro, A.A. A novel void node recovery paradigm for long-term underwater sensor networks. Ad Hoc Netw. 2015, 34, 144–156. [Google Scholar] [CrossRef]
- Xie, P.; Zhou, Z.; Peng, Z.; Cui, J.H.; Shi, Z. Void avoidance in three-dimensional mobile underwater sensor networks. In Proceedings of the International Conference on Wireless Algorithms, Systems, and Applications, Boston, MA, USA, 16–18 August 2009; pp. 305–314. [Google Scholar]
- Garcia, M.; Sendra, S.; Atenas, M.; Lloret, J. Underwater wireless ad-hoc networks: A survey. In Mobile Ad Hoc Networks: Current Status and Future Trends; CRC Press: Boca Raton, FL, USA, 2012; pp. 379–411. [Google Scholar]
- Zeng, Z.; Fu, S.; Zhang, H.; Dong, Y.; Cheng, J. A survey of underwater optical wireless communications. IEEE Commun. Surv. Tutor. 2016, 19, 204–238. [Google Scholar] [CrossRef]
- Yang, Y.; Xiao, Y.; Li, T. A Survey of Autonomous Underwater Vehicle Formation: Performance, Formation Control, and Communication Capability. IEEE Commun. Surv. Tutor. 2021. [Google Scholar] [CrossRef]
- Mhemed, R.; Comeau, F.; Phillips, W.; Aslam, N. Void Avoidance Opportunistic Routing Protocol for Underwater Wireless Sensor Networks. Sensors 2021, 21, 1942. [Google Scholar] [CrossRef] [PubMed]
- Ashraf, S.; Gao, M.; Chen, Z.; Naeem, H.; Ahmad, A.; Ahmed, T. Underwater Pragmatic Routing Approach Through Packet Reverberation Mechanism. IEEE Access 2020, 8, 163091–163114. [Google Scholar] [CrossRef]
- Patel, Z.; Rana, K. LAVR: Link failure avoidance and void recovery routing protocol for underwater sensor networks. Int. J. Sens. Netw. 2020, 34, 253–271. [Google Scholar] [CrossRef]
- Luo, J.; Chen, Y.; Wu, M.; Yang, Y. A Survey of Routing Protocols for Underwater Wireless Sensor Networks. IEEE Commun. Surv. Tutor. 2021, 23, 137–160. [Google Scholar] [CrossRef]
- Hao, K.; Ding, Y.; Li, C.; Wang, B.; Liu, Y.; Du, X.; Wang, C. An Energy-Efficient Routing Void Repair Method Based on an Autonomous Underwater Vehicle for UWSNs. IEEE Sens. J. 2020, 21, 5502–5511. [Google Scholar] [CrossRef]
- Zhang, J.; Cai, M.; Han, G.; Qian, Y.; Shu, L. Cellular clustering-based interference-aware data transmission protocol for underwater acoustic sensor networks. IEEE Trans. Veh. Technol. 2020, 69, 3217–3230. [Google Scholar] [CrossRef]
- Ganesh, N. Performance Evaluation of Depth Adjustment and Void Aware Pressure Routing (DA-VAPR) Protocol for Underwater Wireless Sensor Networks. Comput. J. 2020, 63, 193–202. [Google Scholar] [CrossRef]
- Draz, U.; Ali, T.; Asghar, K.; Yasin, S.; Sharif, Z.; Abbas, Q.; Aman, S. A Comprehensive Comparative Analysis of Two Novel Underwater Routing Protocols. IJACSA 2019, 10, 4. [Google Scholar] [CrossRef]
- Draz, U.; Yasin, S.; Ali, A.; Khan, M.A.; Nawaz, A. Traffic Agents-Based Analysis of Hotspot Effect in IoT-Enabled Wireless Sensor Network. In Proceedings of the 2021 International Bhurban Conference on Applied Sciences and Technologies (IBCAST), Islamabad, Pakistan, 12–16 January 2021; pp. 1029–1034. [Google Scholar]
Publisher’s Note: MDPI stays neutral with regard to jurisdictional claims in published maps and institutional affiliations. |
© 2021 by the authors. Licensee MDPI, Basel, Switzerland. This article is an open access article distributed under the terms and conditions of the Creative Commons Attribution (CC BY) license (https://creativecommons.org/licenses/by/4.0/).