A Path-Length Efficient, Low-Overhead, Load-Balanced Routing Protocol for Maximum Network Lifetime in Wireless Sensor Networks with Holes †
Abstract
1. Introduction
2. Related Works
3. Proposed Protocol
3.1. Protocol Overview
3.2. Hole Determination and Hole Information Dissemination
- If the HCI packet contains information of a hole, then the node checks whether it already stored information of the hole in the local memory. If “yes”, it simply drops the HCI packet. Otherwise, it stores information about the hole into the local memory. Moreover, if the node has already stored information on the hole’s core polygon in the memory, then it removes the core polygon’s information because now it already has information on the hole. The node then checks whether it stay inside the hole’s vicinity. If “yes”, it broadcast the HCI packet. If “no”, if replace the information of the hole by the information of the core polygon before broadcast the HCI packet.
- If the HCI packet contains information of a core polygon, then the node checks whether it already stored information of the same core polygon or a hole whose core polygon is the core polygon in the HCI packet. If “yes”, the node simply drops the packet. Otherwise, the node stores information of the core polygon into the local memory and broadcast the HCI packet.
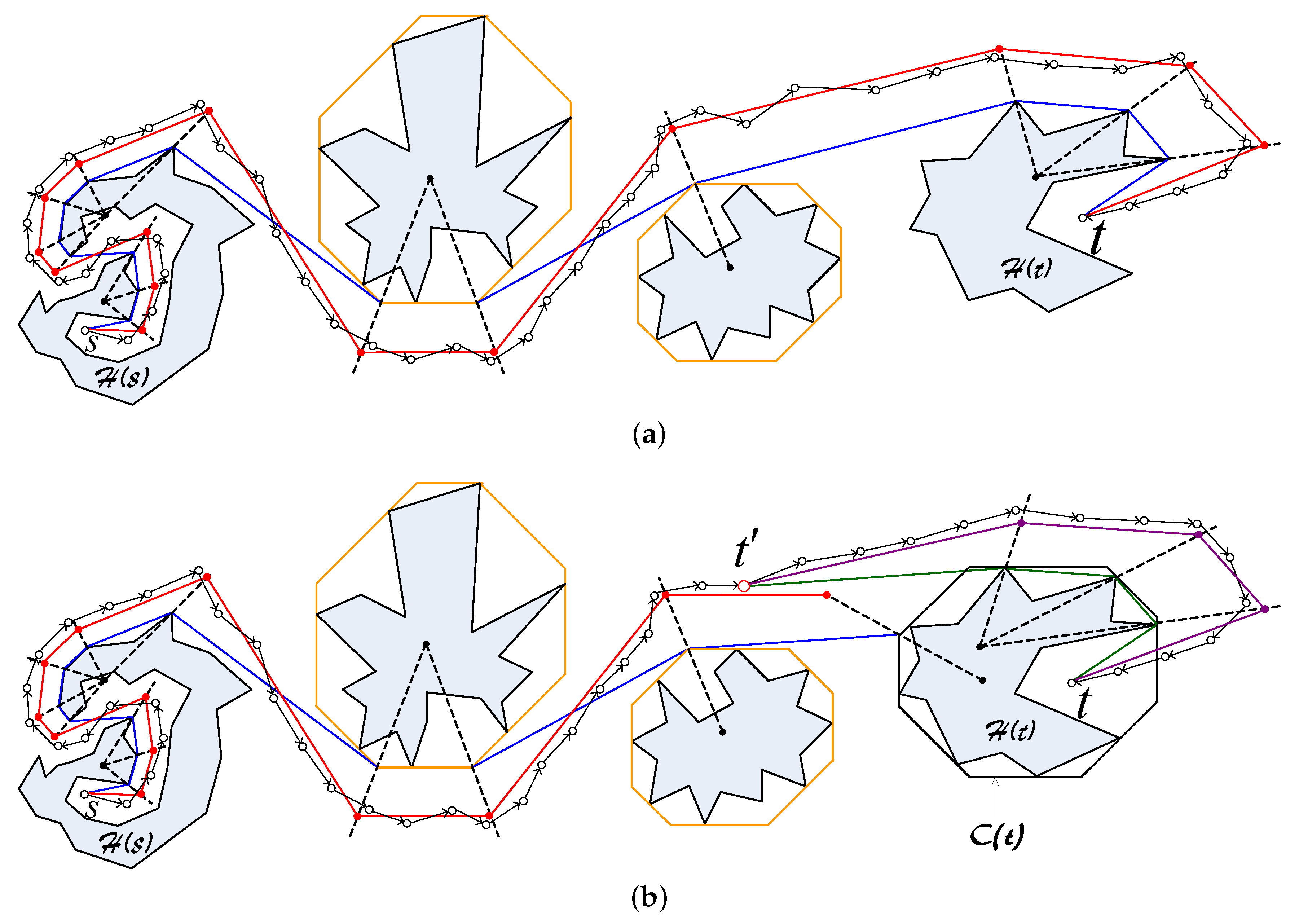
3.3. Data Forwarding Algorithm
3.3.1. Determining the Base Path
- Its length does not exceed Γ.
- The angle between any segment connecting its two consecutive vertices and vector is an obtuse angle.
- If s is a t-aware node, the base path candidates are all paths from s to t that are either the shortest path or -bounded paths, where is the shortest path from s to t, n is the minimum number of vertices of the core polygons.
- If s is a t-blind node, the base path candidates are all paths from s to a vertices on that are -bounded paths, where and denotes the shortest length of the shortest paths from s to a vertex of .
| Algorithm 1: Base path candidate determination algorithm. |
| Input s: source, d: destination, : the stretch factor |
| Output P: base path candidate set P; |
| shortest_len← Shortest_path (s, d); |
| if d_core== null ||d_hole!= null then ; |
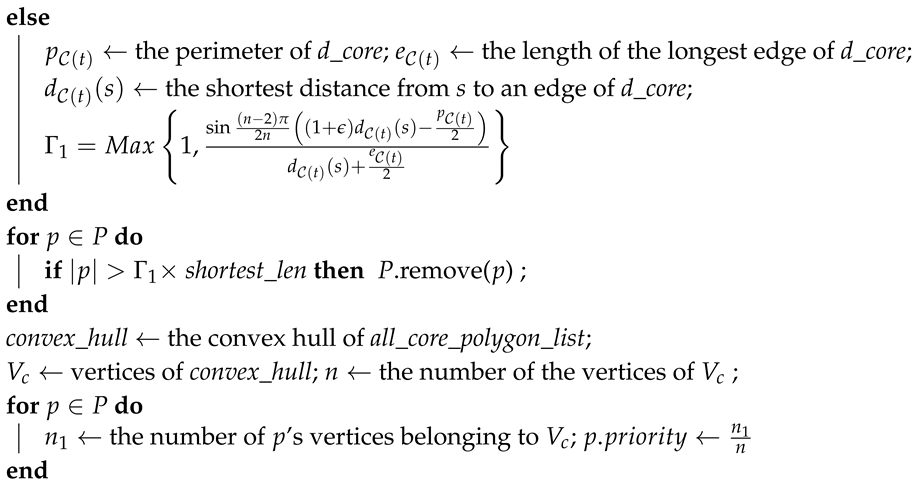 |
| returnP |
3.3.2. Determining the Euclidean Routing Path
3.3.3. Forwarding the Data Packet
- is the shortest path from t to a vertex of .
- is -bounded path, where is the shortest path from to t and .
| Algorithm 2: Euclidean routing path determination algorithm. |
| Input P: the set of base paths, s: source, d: destination, : stretch factor |
| Output r: the Euclidean routing path a base path probabilistically chosen from P; |
| s_core ← the core polygon containing s; |
| s_hole ← the hole whose core polygon is s_core; |
| d_core ← the core polygon containing d; |
| d_hole ← the hole whose core polygon is d_core; |
| all core polygons excepting s_core and d_core; |
| ; |
 |
| ; |
| returnr |
4. Theoretical Analysis
4.1. Computational Complexity
4.1.1. Complexity of the Hole Determination Algorithm
4.1.2. Complexity of the Dissemination Algorithm
- Checking whether the node has already received an HCI packet.
- Constructing the core polygon of the hole contained in the HCI packet.
- Checking whether the node stays inside the vicinity region of the hole contained in the HCI packet.
4.1.3. Complexity of the Data Forwarding Algorithm
- Determining the base path candidate set (i.e., in the case that the node is the source node).
- Determining the Euclidean routing path (i.e., in the case that the node is the source node).
- Determining the next hop by using the greedy forwarding algorithm.
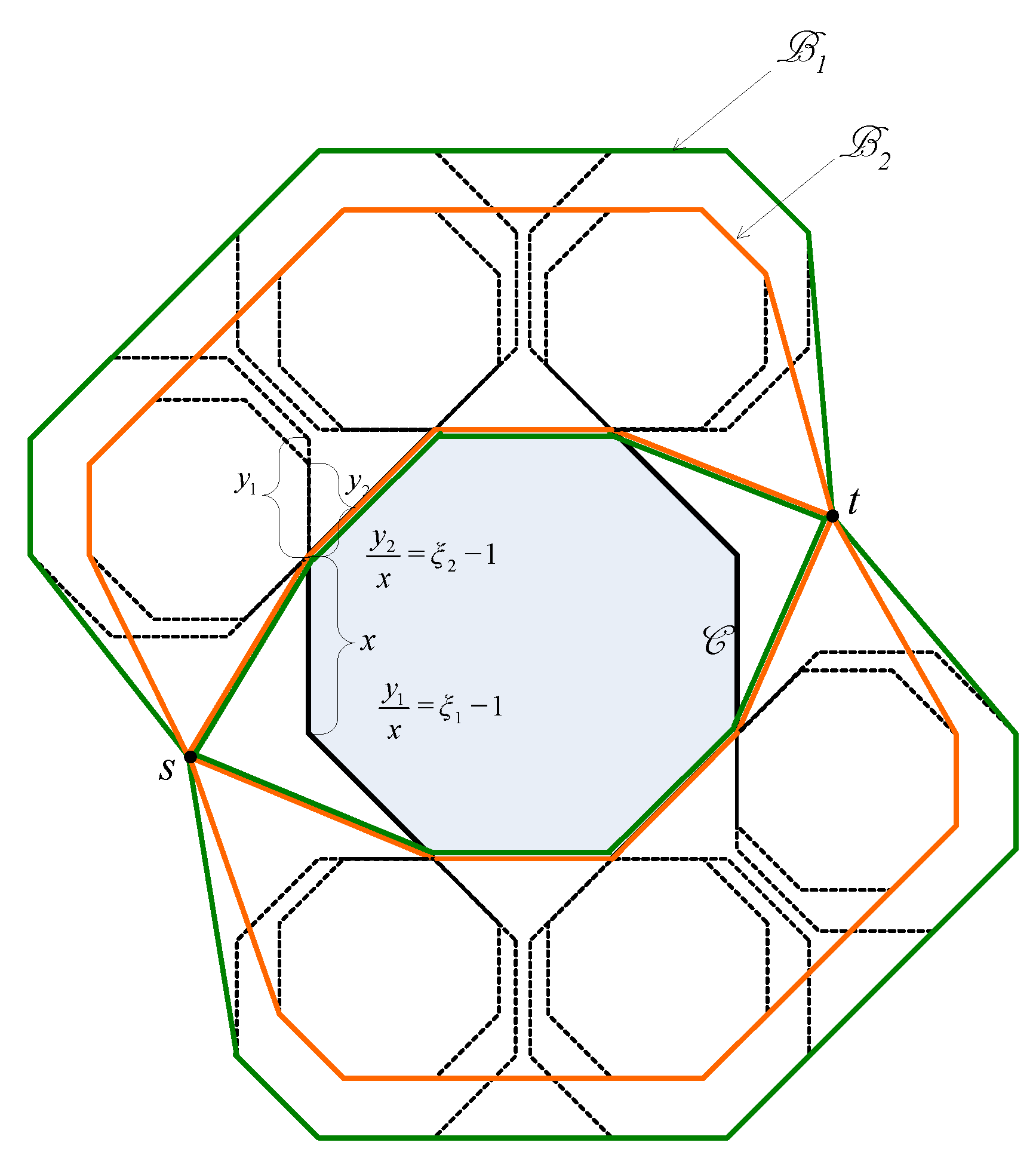
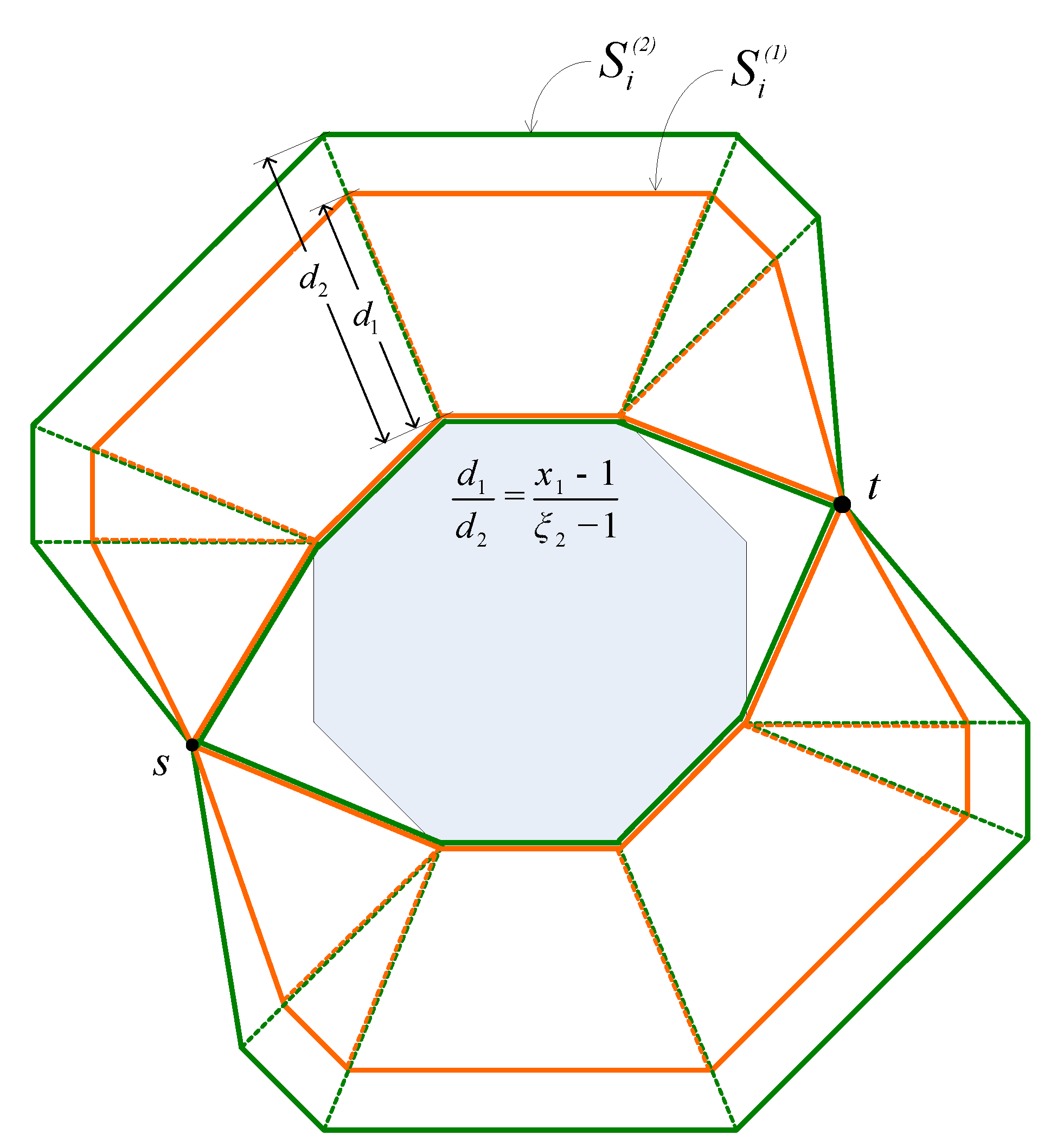
4.2. Impact of the Stretch Factor
4.2.1. Routing Path Stretch
4.2.2. Load Balance
5. Performance Evaluation
5.1. Performance Metrics
- 1.
- Metrics regarding routing path-length minimization
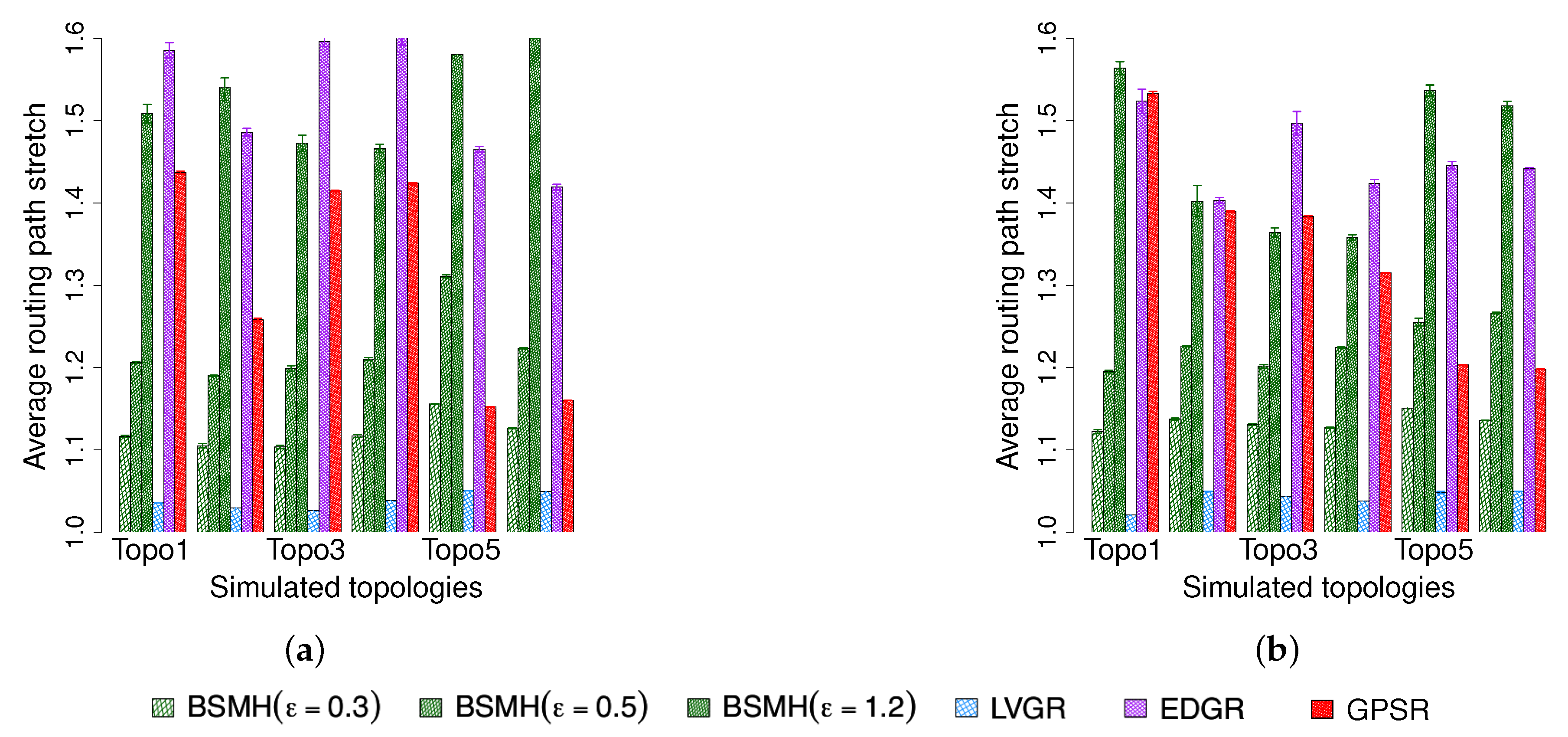
- Average routing path stretch: The routing path stretch of a routing path is defined by the ratio of its hop count to that of the theoretical shortest path. The average routing path stretch of a routing protocol is the average value of routing path stretches of all the routing paths determined by the protocol.
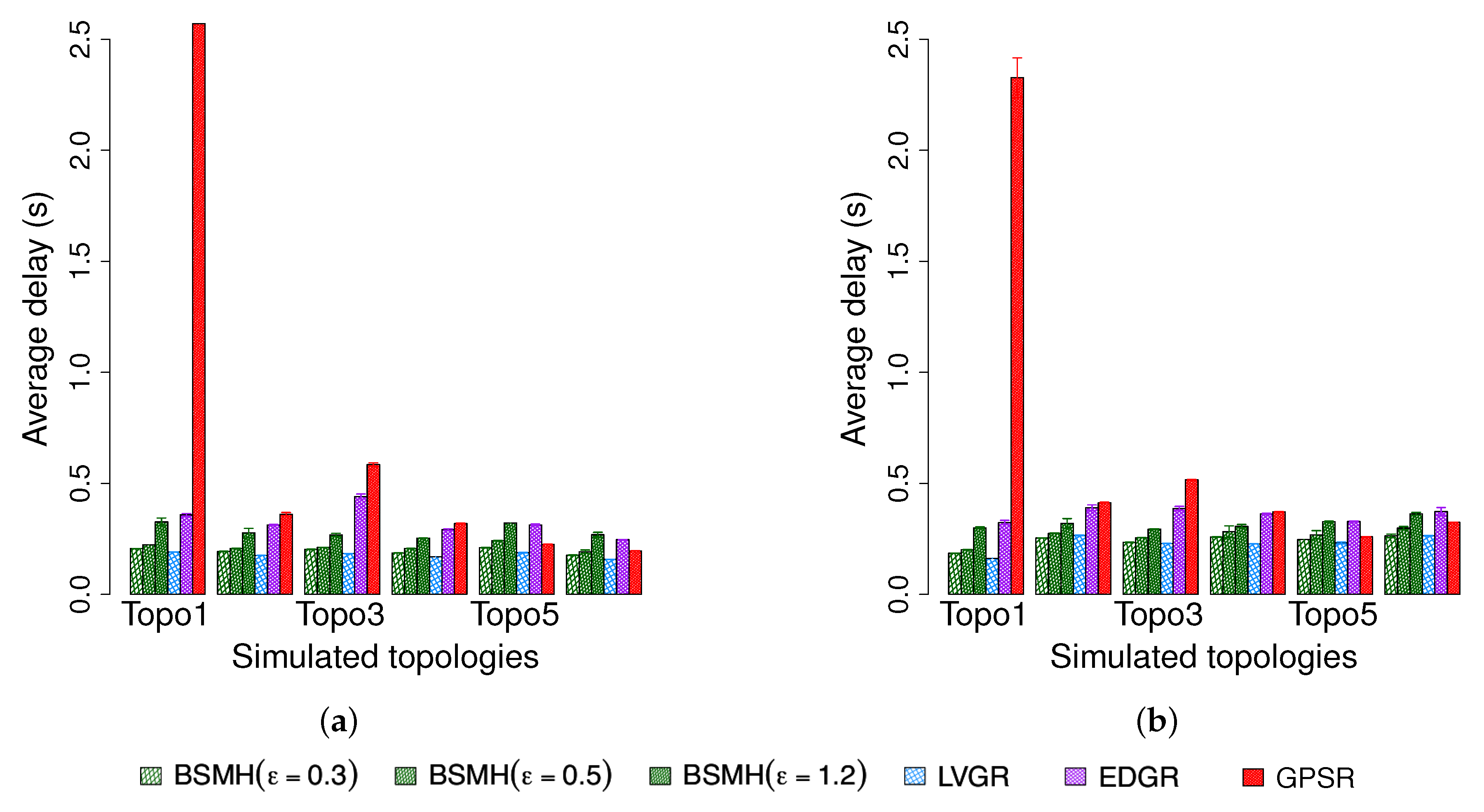
- Average delay: We evaluate the average end-to-end delay of all data packets that successfully arrive at the destinations.
- 2.
- Metrics regarding control overhead minimization
- Total amount of control packets: Control packets are defined as packets that are not data packets. In BSMH and LVGR, control packets consist of packets for exchanging node information (known as HELLO packets), packets for determining hole boundaries (known as HBA packets), and packets for broadcasting hole information (known as HCI packets). In GPSR, the control packet is only HELLO packet. In EDGR, control packets include beacons that periodically broadcast node information (i.e., energy, location, ...), and burst packets that determine the anchors. We measure the total amount (in bytes) of all the control packets which has been transmitted from when the simulation starts till the first node dies.
- 3.
- Metrics regarding load balance maximization
- Maximum packet forwarding ratio: This indicates the maximum ratio of the number of packets forwarded by a node to the total number of packets sent. Specifically, let be the number of packets forwarded by the i-th node, and p be the total number of packet sent by all source nodes, then the maximum forwarding ratio is defined by . In general, the smaller maximum packet forwarding ratio reflects the better load balance.
- Network lifetime: As described in Section 1, in large-scale wireless sensor networks, the death of even only one node may affect the operation of the whole network. Accordingly, the network lifetime should be defined as the time period until the first node dies. In our experiments, all protocols spend the first for the setup phase, and the first data packet is sent after that. Thus, we define the network lifetime as the time period from the first data packet was sent until the first node dies.
- 4.
- Other metrics
- Delivery ratio: This is defined by the ratio of the number of data packets successfully arriving at the destinations to the total number of data packets sent by the sources.
- Energy consumption per packet: This is the ratio of the total energy consumption of all the nodes to the total number of packets successfully delivered.
5.2. Simulation Settings
5.3. Impact of the Stretch Factor
5.4. Comparison of BSMH and Other Benchmarks
5.4.1. Average Routing Path Stretch
5.4.2. Average End-to-End Delay
5.4.3. Control Overhead
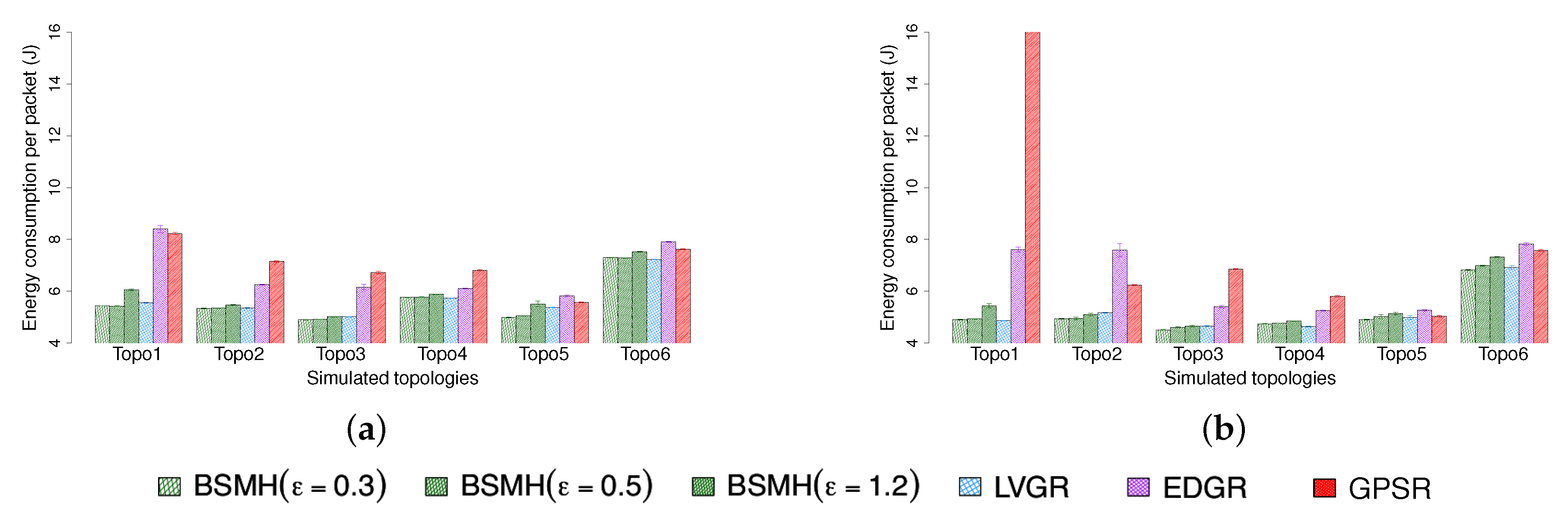
5.4.4. Energy Consumption per Packet
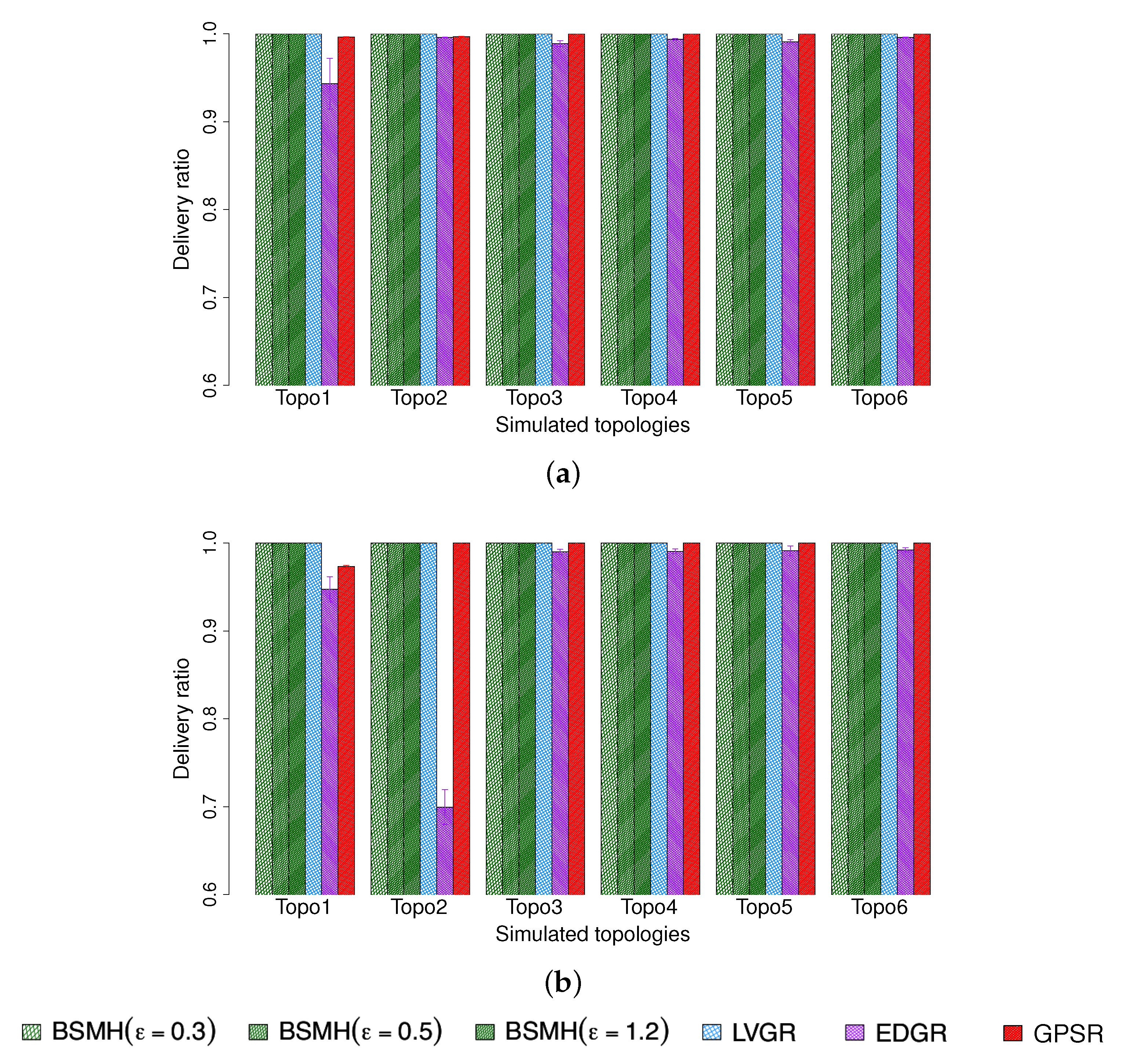
5.4.5. Packet Delivery Ratio
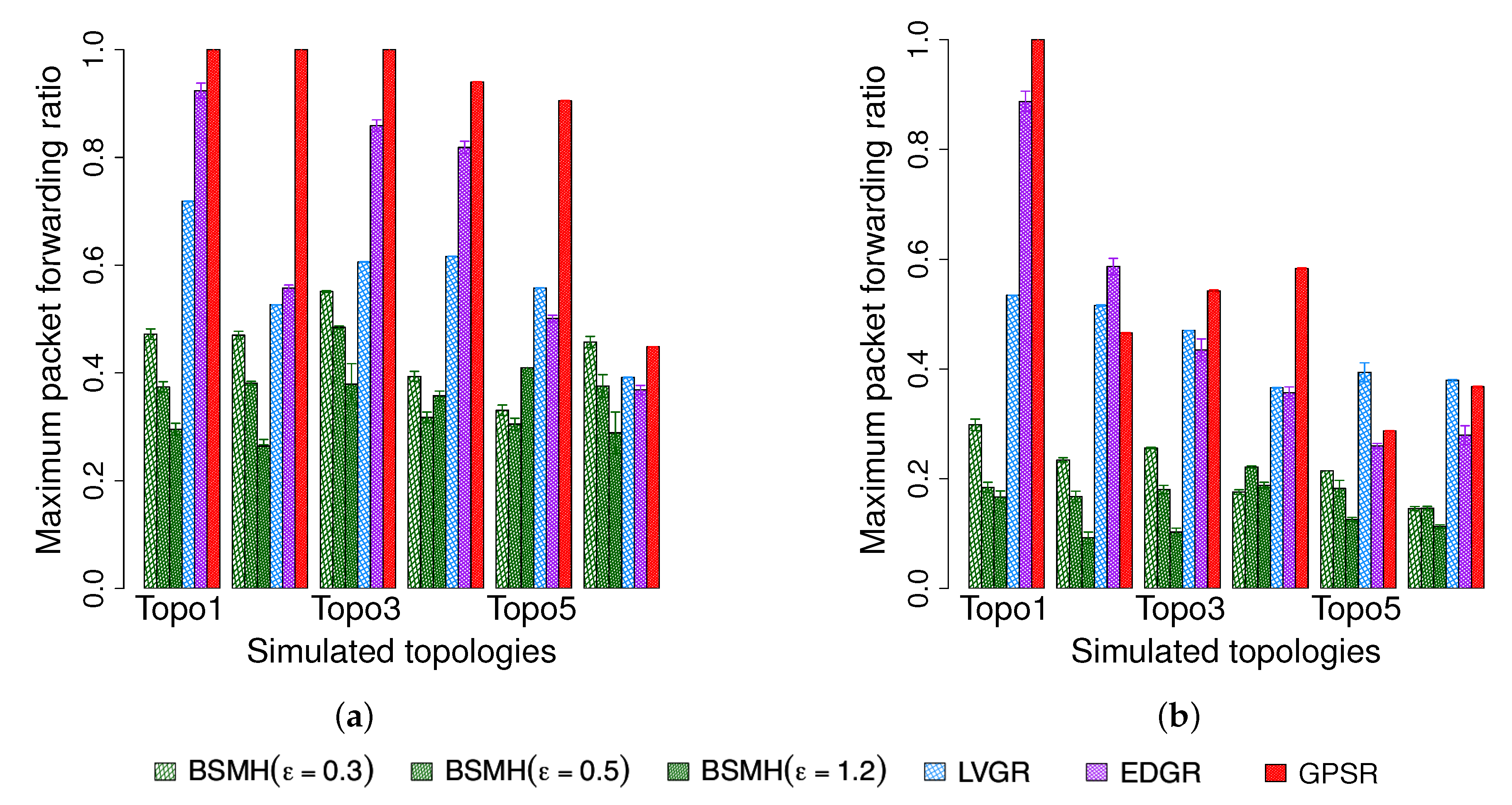
5.4.6. Maximum Packet forwarding Ratio
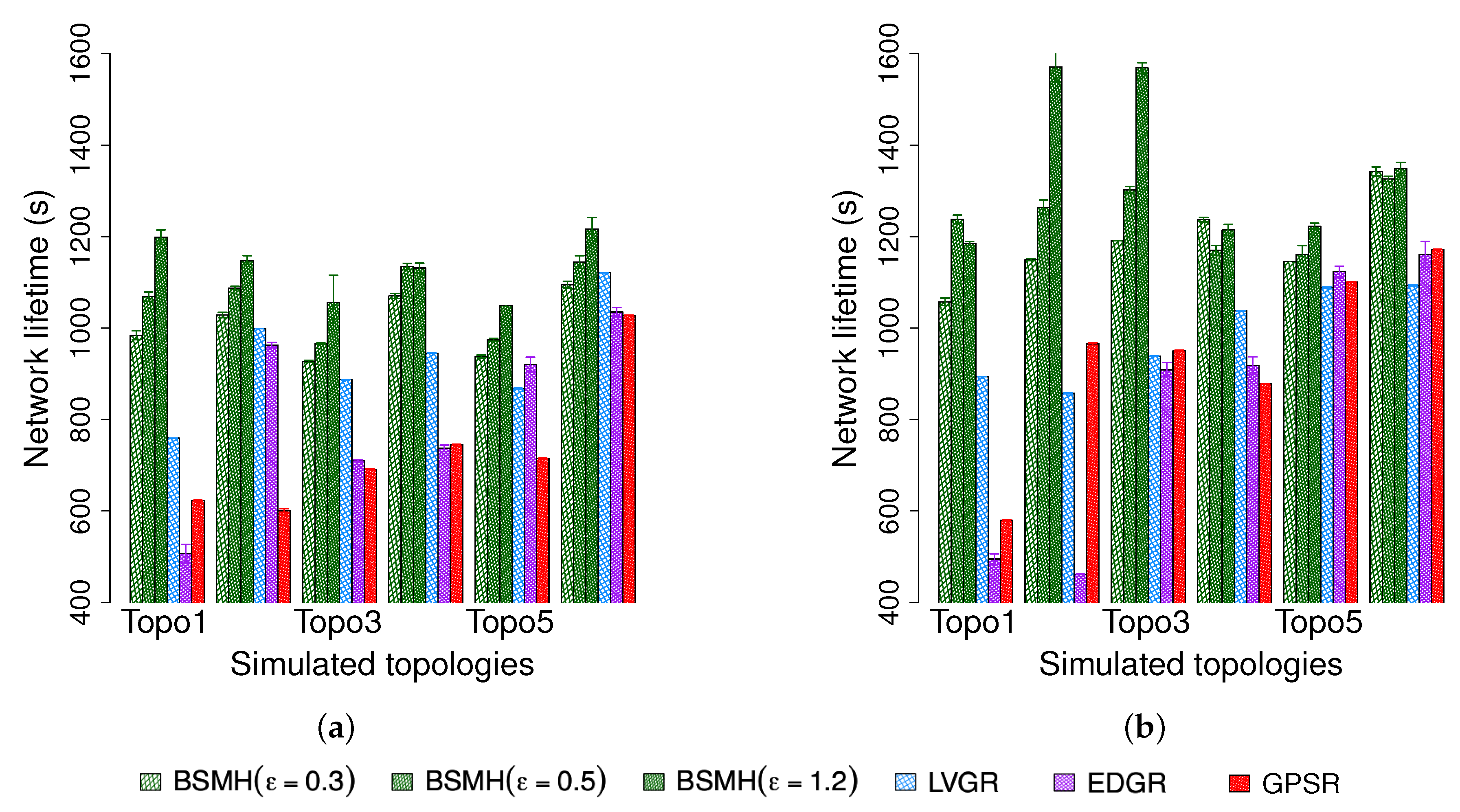
5.4.7. Network Lifetime
6. Conclusions
Author Contributions
Funding
Conflicts of Interest
References
- Gaber, T.; Abdelwahab, S.; Elhoseny, M.; Hassanien, A.E. Trust-based Secure Clustering in WSN-based Intelligent Transportation Systems. Comput. Networks 2018, 146, 151–158. [Google Scholar] [CrossRef]
- Peckens, C.; Porter, C.; Rink, T. Wireless Sensor Networks for Long-Term Monitoring of Urban Noise. Sensors 2018, 18, 3161. [Google Scholar] [CrossRef] [PubMed]
- Miao, Y.; Wu, G.; Liu, C.; Hossain, M.S.; Muhammad, G. Green Cognitive Body Sensor Network: Architecture, Energy Harvesting, and Smart Clothing-Based Applications. IEEE Sens. J. 2019, 19, 8371–8378. [Google Scholar] [CrossRef]
- Rashid, B.; Rehmani, M.H. Applications of wireless sensor networks for urban areas: A survey. J. Netw. Comput. Appl. 2016, 60, 192–219. [Google Scholar] [CrossRef]
- Chen, D.; Liu, Z.; Wang, L.; Dou, M.; Chen, J.; Li, H. Natural Disaster Monitoring with Wireless Sensor Networks: A Case Study of Data-intensive Applications Upon Low-Cost Scalable Systems. Mob. Netw. Appl. 2013, 18, 651–663. [Google Scholar] [CrossRef]
- Erdelj, M.; Król, M.; Natalizio, E. Wireless Sensor Networks and Multi-UAV systems for natural disaster management. Comput. Networks 2017, 124, 72–86. [Google Scholar] [CrossRef]
- Han, G.; Yang, X.; Liu, L.; Zhang, W.; Guizani, M. A Disaster Management-Oriented Path Planning for Mobile Anchor Node-Based Localization in Wireless Sensor Networks. IEEE Trans. Emerg. Top. Comput. 2020, 8, 115–125. [Google Scholar] [CrossRef]
- Bhosle, A.S.; Gavhane, L.M. Forest disaster management with wireless sensor network. In Proceedings of the International Conference on Electrical, Electronics, and Optimization Techniques (ICEEOT), Chennai, India, 3–5 March 2016; pp. 287–289. [Google Scholar]
- Swetha, R.; Santhosh Amarnath, V.A.S. Wireless Sensor Network: A Survey. Int. J. Adv. Res. Comput. Commun. Eng. 2018, 7, 1–4. [Google Scholar]
- Onur, E.; Ersoy, C.; Delic, H.; Akarun, L. Surveillance Wireless Sensor Networks: Deployment Quality Analysis. IEEE Netw. 2007, 21, 48–53. [Google Scholar] [CrossRef]
- Cayirci, E.; Coplu, T. SENDROM: Sensor networks for disaster relief operations management. Wirel. Netw. 2007, 13, 409–423. [Google Scholar] [CrossRef]
- Aqeel-ur-Rehman; Abbasi, A.Z.; Islam, N.; Shaikh, Z.A. A review of wireless sensors and networks’ applications in agriculture. Comput. Stand. Interfaces 2014, 36, 263–270. [Google Scholar] [CrossRef]
- Ojha, T.; Misra, S.; Raghuwanshi, N.S. Wireless sensor networks for agriculture: The state-of-the-art in practice and future challenges. Comput. Electron. Agric. 2015, 118, 66–84. [Google Scholar] [CrossRef]
- Alemdar, H.; Ersoy, C. Wireless sensor networks for healthcare: A survey. Comput. Networks 2010, 54, 2688–2710. [Google Scholar] [CrossRef]
- Sarkar, A.; Murugan, T.S. Routing protocols for wireless sensor networks: What the literature says? Alex. Eng. J. 2016, 55, 3173–3183. [Google Scholar] [CrossRef]
- Le, K.; Nguyen, T.H.; Nguyen, K.; Nguyen, P.L. Exploiting Q-Learning in Extending the Network Lifetime of Wireless Sensor Networks with Holes. In Proceedings of the IEEE 25th International Conference on Parallel and Distributed Systems (ICPADS), Tianjin, China, 4–6 December 2019; pp. 602–609. [Google Scholar]
- Wang, J.; Gao, Y.; Liu, W.; Sangaiah, A.K.; Kim, H.-J. Energy Efficient Routing Algorithm with Mobile Sink Support for Wireless Sensor Networks. Sensors 2019, 19, 1494. [Google Scholar] [CrossRef] [PubMed]
- Thangaramya, K.; Kulothungan, K.; Logambigai, R.; Selvi, M.; Ganapathy, S.; Kannan, A. Energy aware cluster and neuro-fuzzy based routing algorithm for wireless sensor networks in IoT. Comput. Netw. 2019, 151, 211–223. [Google Scholar] [CrossRef]
- Darabkh, K.A.; El-Yabroudi, M.Z.; El-Mousa, A.H. BPA-CRP: A balanced power-aware clustering and routing protocol for wireless sensor networks. Ad Hoc Netw. 2019, 82, 155–171. [Google Scholar] [CrossRef]
- Yuan, Y.; Liu, W.; Wang, T.; Deng, Q.; Liu, A.; Song, H. Compressive Sensing-Based Clustering Joint Annular Routing Data Gathering Scheme for Wireless Sensor Networks. IEEE Access 2019, 7, 114639–114658. [Google Scholar] [CrossRef]
- Hamzah, A.; Shurman, M.; Al-Jarrah, O.; Taqieddin, E. Energy-Efficient Fuzzy-Logic-Based Clustering Technique for Hierarchical Routing Protocols in Wireless Sensor Networks. Sensors 2019, 19, 561. [Google Scholar] [CrossRef]
- Ko, Y.; Vaidya, N.H. Location-Aided Routing (LAR) in mobile ad hoc networks. Wirel. Netw. 2000, 6, 307–321. [Google Scholar] [CrossRef]
- Karp, B.; Kung, H.T. GPSR: Greedy Perimeter Stateless Routing for Wireless Networks. In Proceedings of the 6th Annual International Conference on Mobile Computing and Networking, London, UK, 21–25 September 2000; ACM: New York, NY, USA, 2000; pp. 243–254. [Google Scholar]
- Fang, Q.; Gao, J.; Guibas, L.J. Locating and bypassing routing holes in sensor networks. In Proceedings of the 20th Annual Joint Conference of the IEEE Computer and Communications Societies, Hong Kong, China, 7–11 March 2004; pp. 2458–2468. [Google Scholar]
- Ahmed, N.; Kanhere, S.S.; Jha, S. The Holes Problem in Wireless Sensor Networks: A Survey. Mob. Comput. Commun. Rev. 2005, 9, 4–18. [Google Scholar] [CrossRef]
- Bose, P.; Morin, P.; Stojmenovir, I.; Urrutia, J. Routing with Guaranteed Delivery in Ad Hoc Wireless Networks. In Proceedings of the 5th IEEE International Conference, Chicago, IL, USA, 2–6 June 2008; pp. 347–352. [Google Scholar]
- Kuhn, F.; Wattenhofer, R.; Zollinger, A. Asymptotically Optimal Geometric Mobile Ad-hoc Routing. In Proceedings of the 6th International Workshop on Discrete Algorithms and Methods for Mobile Computing and Communications, Atlanta, GA, USA, 28 September 2002; pp. 24–33. [Google Scholar]
- Kuhn, F.; Wattenhofer, R.; Zollinger, A. Worst-Case Optimal and Average-case Efficient Geometric Ad-hoc Routing. In Proceedings of the 4th ACM International Symposium on Mobile Ad Hoc Networking and Computing, Annapolis, MA, USA, 1–3 June 2003; pp. 267–278. [Google Scholar]
- Yu, F.; Park, S.; Tian, Y.; Jin, M.; Kim, S.-H. Efficient Hole Detour Scheme for Geographic Routing in Wireless Sensor Networks. In Proceedings of the 67th IEEE Vehicular Technology Conference, VTC’08, Singapore, 11–14 May 2008; pp. 153–157. [Google Scholar]
- Kim, S.; Kim, C.; Cho, H.; Yim, Y.; Kim, S. Void Avoidance Scheme for Real-Time Data Dissemination in Irregular Wireless Sensor Networks. In Proceedings of the 30th International Conference on Advanced Information Networking and Applications (AINA), Crans-Montana, Switzerland, 23–25 March 2016; pp. 438–443. [Google Scholar]
- Tian, Y.; Yu, F.; Choi, Y.; Park, S.; Lee, E.; Jin, M.; Kim, S.H. Energy-Efficient Data Dissemination Protocol for Detouring Routing Holes in Wireless Sensor Networks. In Proceedings of the IEEE International Conference on Communications, ICC’08, Beijing, China, 19–23 May 2008; pp. 2322–2326. [Google Scholar]
- Choo, H.; Choi, M.; Shon, M.; Kim, D.S. Efficient hole bypass routing scheme using observer packets for geographic routing in wireless sensor networks. ACM SIGAPP Appl. Comput. Rev. 2011, 11, 7–16. [Google Scholar] [CrossRef]
- Chang, C.; Chang, C.; Chen, Y.; Lee, S. Active Route-Guiding Protocols for Resisting Obstacles in Wireless Sensor Networks. IEEE Trans. Veh. Technol. 2010, 59, 4425–4442. [Google Scholar] [CrossRef]
- Won, M.; Stoleru, R. A Low-Stretch-Guaranteed and Lightweight Geographic Routing Protocol for Large-Scale Wireless Sensor Networks. ACM Trans. Sens. Networks (TOSN) 2014, 11, 18:1–18:22. [Google Scholar] [CrossRef]
- Nguyen, P.L.; Nguyen, D.T.; Nguyen, K.V. Load balanced routing with constant stretch for wireless sensor network with holes. In Proceedings of the IEEE Ninth International Conference on Intelligent Sensors, Sensor Networks and Information Processing (ISSNIP), Singapore, 21–24 April 2014; pp. 1–7. [Google Scholar]
- Nguyen, P.L.; Ji, Y.; Le, K.; Nguyen, T.H. Load balanced and constant stretch routing in the vicinity of holes in WSNs. In Proceedings of the 15th IEEE Annual Consumer Communications Networking Conference (CCNC), Las Vegas, NV, USA, 12–15 January 2018; pp. 1–6. [Google Scholar]
- Nguyen, P.; Ji, Y.; Le, K.; Nguyen, T. Routing in the Vicinity of Multiple Holes in WSNs. In Proceedings of the 5th International Conference on Information and Communication Technologies for Disaster Management (ICT-DM), Sendai, Japan, 4–7 December 2018; pp. 1–8. [Google Scholar]
- Nguyen, P.L.; Nguyen, T.H.; Nguyen, K. A Dynamic Routing Protocol for Maximizing Network Lifetime in WSNs with Holes. In Proceedings of the 10th International Symposium on Information and Communication Technology (SoICT 2019), Hanoi-Halong Bay, Vietnam, 5–6 September 2019. [Google Scholar]
- Kuhn, F.; Wattenhofer, R.; Zhang, Y.; Zollinger, A. Geometric Ad-hoc Routing: Of Theory and Practice. In Proceedings of the 22nd Annual Symposium on Principles of Distributed Computing, Boston, MA, USA, 13–16 July 2003; pp. 63–72. [Google Scholar]
- Subramanian, S.; Shakkottai, S.; Gupta, P. On Optimal Geographic Routing in Wireless Networks with Holes and Non-Uniform Traffic. In Proceedings of the 26th IEEE International Conference on Computer Communications, INFOCOM’07, Barcelona, Spain, 6–12 May 2007; pp. 1019–1027. [Google Scholar]
- Gupta, P.; Kumar, P.R. The capacity of wireless networks. IEEE Trans. Inf. Theory 2000, 46, 388–404. [Google Scholar] [CrossRef]
- Zhou, F.; Trajcevski, G.; Tamassia, R.; Avci, B.; Khokhar, A.; Scheuermann, P. Bypassing holes in sensor networks: Load-balance vs. latency. Ad Hoc Netw. 2017, 61, 16–32. [Google Scholar] [CrossRef]
- Li, F.; Zhang, B.; Zheng, J. Geographic hole-bypassing forwarding protocol for wireless sensor networks. IET Commun. 2011, 5, 737–744. [Google Scholar] [CrossRef]
- Won, M.; Zhang, W.; Stoleru, R. GOAL: A Parsimonious Geographic Routing Protocol for Large Scale Sensor Networks. Ad Hoc Netw. 2013, 11, 453–472. [Google Scholar] [CrossRef]
- Huang, H.; Yin, H.; Min, G.; Zhang, J.; Wu, Y.; Zhang, X. Energy-Aware Dual-Path Geographic Routing to Bypass Routing Holes in Wireless Sensor Networks. IEEE Trans. Mob. Comput. 2018, 17, 1339–1352. [Google Scholar] [CrossRef]
- Fucai Yu, S.P.; Hu, G. Hole plastic scheme for geographic routing in wireless sensor networks. In Proceedings of the 15th IEEE International Conference on Communications, ICC’15, London, UK, 8–12 June 2015; pp. 6444–6449. [Google Scholar]
- Jan, N.; Hameed, A.R.; Ali, B.; Ullah, R.; Ullah, K.; Javaid, N. A Balanced Energy Consuming and Hole Alleviating Algorithm for Wireless Sensor Networks. In Proceedings of the 31st International Conference on Advanced Information Networking and Applications Workshops (WAINA), Taipei, Taiwan, 27–29 March 2017; pp. 231–237. [Google Scholar]
- Lima, M.M.; Oliveira, H.A.B.F.; Guidoni, D.L.; Loureiro, A.A.F. Geographic Routing and Hole Bypass Using Long Range Sinks for Wireless Sensor Networks. Ad Hoc Netw. 2017, 67, 1–10. [Google Scholar] [CrossRef]
- Petrioli, C.; Nati, M.; Casari, P.; Zorzi, M.; Basagni, S. ALBA-R: Load-Balancing Geographic Routing Around Connectivity Holes in Wireless Sensor Networks. IEEE Trans. Parallel Distrib. Syst. 2014, 25, 529–539. [Google Scholar] [CrossRef]
- Yu, F.; Park, S.; Lee, E.; Kim, S. Elastic routing: A novel geographic routing for mobile sinks in wireless sensor networks. IET Commun. 2010, 4, 716–727. [Google Scholar] [CrossRef]
- Ren, F.; Zhang, J.; He, T.; Lin, C.; Ren, S.K.D. EBRP: Energy-Balanced Routing Protocol for Data Gathering in Wireless Sensor Networks. IEEE Trans. Parallel Distrib. Syst. 2011, 22, 2108–2125. [Google Scholar] [CrossRef]
- Djenouri, D.; Balasingham, I. Traffic-Differentiation-Based Modular QoS Localized Routing for Wireless Sensor Networks. IEEE Trans. Mob. Comput. 2011, 10, 797–809. [Google Scholar] [CrossRef]
- Noh, Y.; Lee, U.; Wang, P.; Choi, B.S.C.; Gerla, M. VAPR: Void-Aware Pressure Routing for Underwater Sensor Networks. IEEE Trans. Mob. Comput. 2013, 12, 895–908. [Google Scholar] [CrossRef]
- Lee, U.; Wang, P.; Noh, Y.; Vieira, L.F.M.; Gerla, M.; Cui, J. Pressure Routing for Underwater Sensor Networks. In Proceedings of the IEEE INFOCOM, San Diego, CA, USA, 14–19 March 2010; pp. 1–9. [Google Scholar]
- Shnayder, V.; Hempstead, M.; Rong Chen, B.; Werner-Allen, G.; Welsh, M. Simulating the power consumption of large-scale sensor network applications. In Proceedings of the 2nd ACM Conference on Embedded Networked Sensor Systems, Baltimore, MA, USA, 3–5 November 2004; pp. 188–200. [Google Scholar]









| Factor | Value |
|---|---|
| MAC type | CSMA/CA |
| Interface queue model | DropTail |
| Transmission of radio | TwoRayGround |
| Antenna type | OmniAntenna |
| Queue length | 50 packets |
| Transmission range | 40 m |
| Node initial energy | 30 J |
| Node idle power | 9.6 mW |
| Node receive power | 45 mW |
| Node transmit power | 88.5 mW |
| Packet sending interval | 10 s |
| Data packet size | 50 bytes |
© 2020 by the authors. Licensee MDPI, Basel, Switzerland. This article is an open access article distributed under the terms and conditions of the Creative Commons Attribution (CC BY) license (http://creativecommons.org/licenses/by/4.0/).
Share and Cite
Nguyen, P.L.; Nguyen, T.H.; Nguyen, K. A Path-Length Efficient, Low-Overhead, Load-Balanced Routing Protocol for Maximum Network Lifetime in Wireless Sensor Networks with Holes. Sensors 2020, 20, 2506. https://doi.org/10.3390/s20092506
Nguyen PL, Nguyen TH, Nguyen K. A Path-Length Efficient, Low-Overhead, Load-Balanced Routing Protocol for Maximum Network Lifetime in Wireless Sensor Networks with Holes. Sensors. 2020; 20(9):2506. https://doi.org/10.3390/s20092506
Chicago/Turabian StyleNguyen, Phi Le, Thanh Hung Nguyen, and Kien Nguyen. 2020. "A Path-Length Efficient, Low-Overhead, Load-Balanced Routing Protocol for Maximum Network Lifetime in Wireless Sensor Networks with Holes" Sensors 20, no. 9: 2506. https://doi.org/10.3390/s20092506
APA StyleNguyen, P. L., Nguyen, T. H., & Nguyen, K. (2020). A Path-Length Efficient, Low-Overhead, Load-Balanced Routing Protocol for Maximum Network Lifetime in Wireless Sensor Networks with Holes. Sensors, 20(9), 2506. https://doi.org/10.3390/s20092506






