LBTM: Listen-before-Talk Protocol for Multiclass UHF RFID Networks
Abstract
1. Introduction
2. Related Works
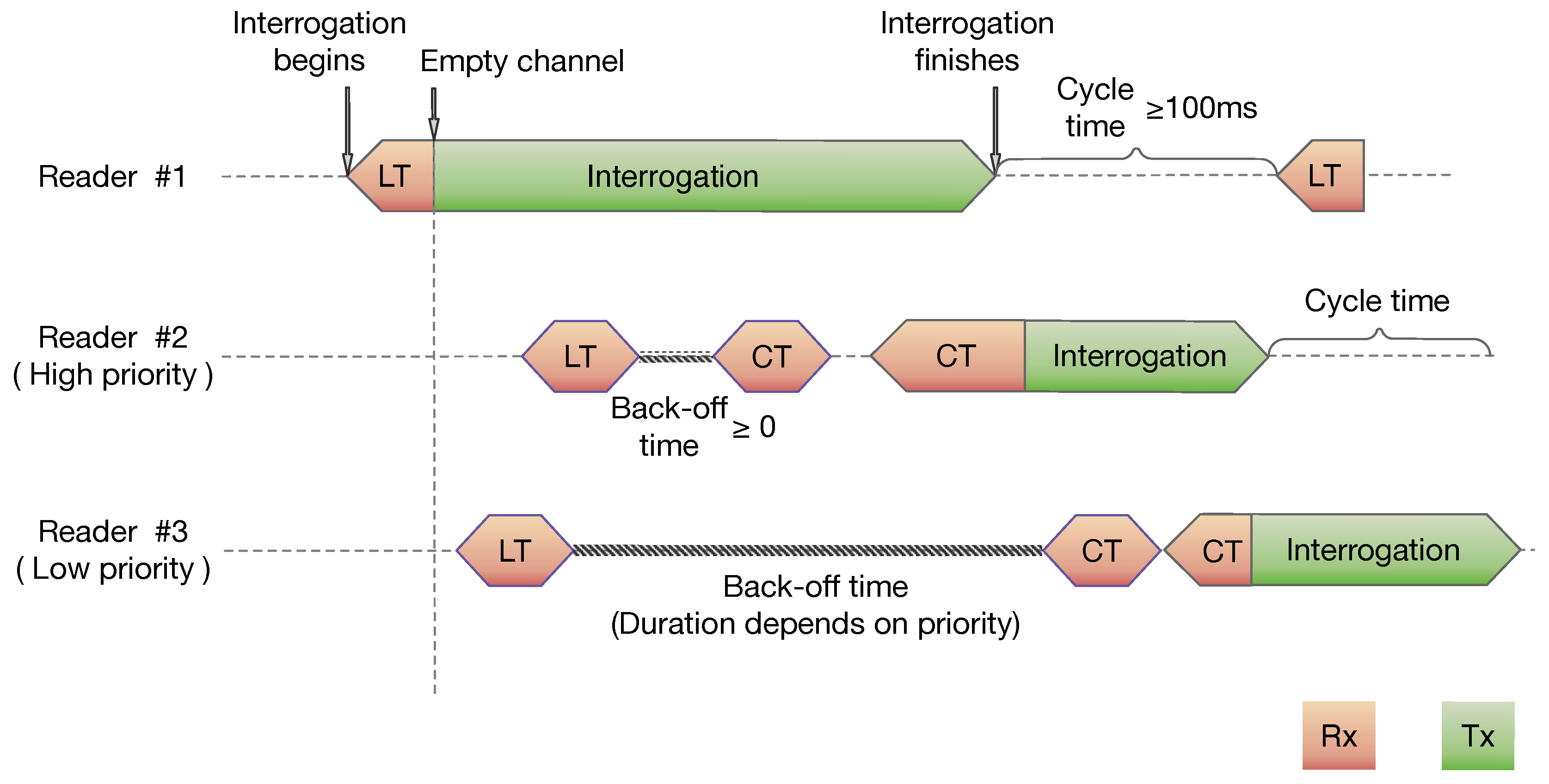
3. LBTM Operation
- Before occupying the channel, a reader probes the channel during a listen period of 5 ms. Henceforth, this period is termed as listening time (LT).
- If the channel is free during this time, the reader can start the interrogation process.
- If the channel is busy, it waits for a contention period between 0 and 5 ms selected at random (in 11 discrete values).
- It repeats the random time until the channel is free, and then it starts the interrogation.
4. Simulation Framework
- It uses a detailed and accurate link budget model, considering distance, antenna aiming, multipath propagation, and shadowing effects. The main physical parameters are summarized in Table 1.
- The location of gates, tags, and all the physical elements can be changed, including dynamic motion.
- It implements several tag anticollision protocols. In particular, in this work, we use the well-known Dynamic Frame Slotted Aloha (DFSA) approach with perfect tag-count estimation. This protocol adapts the interrogation frame length to the number of tags contending to achieve an optimal throughput (e.g., [32] and references therein). Static FSA is also feasible by setting a correct frame size suitable for the incoming traffic.
- It allows multiple traffic patterns, including batch-traffic, continuous-flow traffic, and permanent load. Therefore, it is possible to characterize accurately different real-world situations.
- Finally, it is flexible enough to implement any reader anticollision protocol on top of its stack. By default, it uses LBT/LBTM, but it is possible to update it to include other synchronous or asynchronous schemes.
- The interrogation process lasts until no more tags respond to the readers’ Query packets.
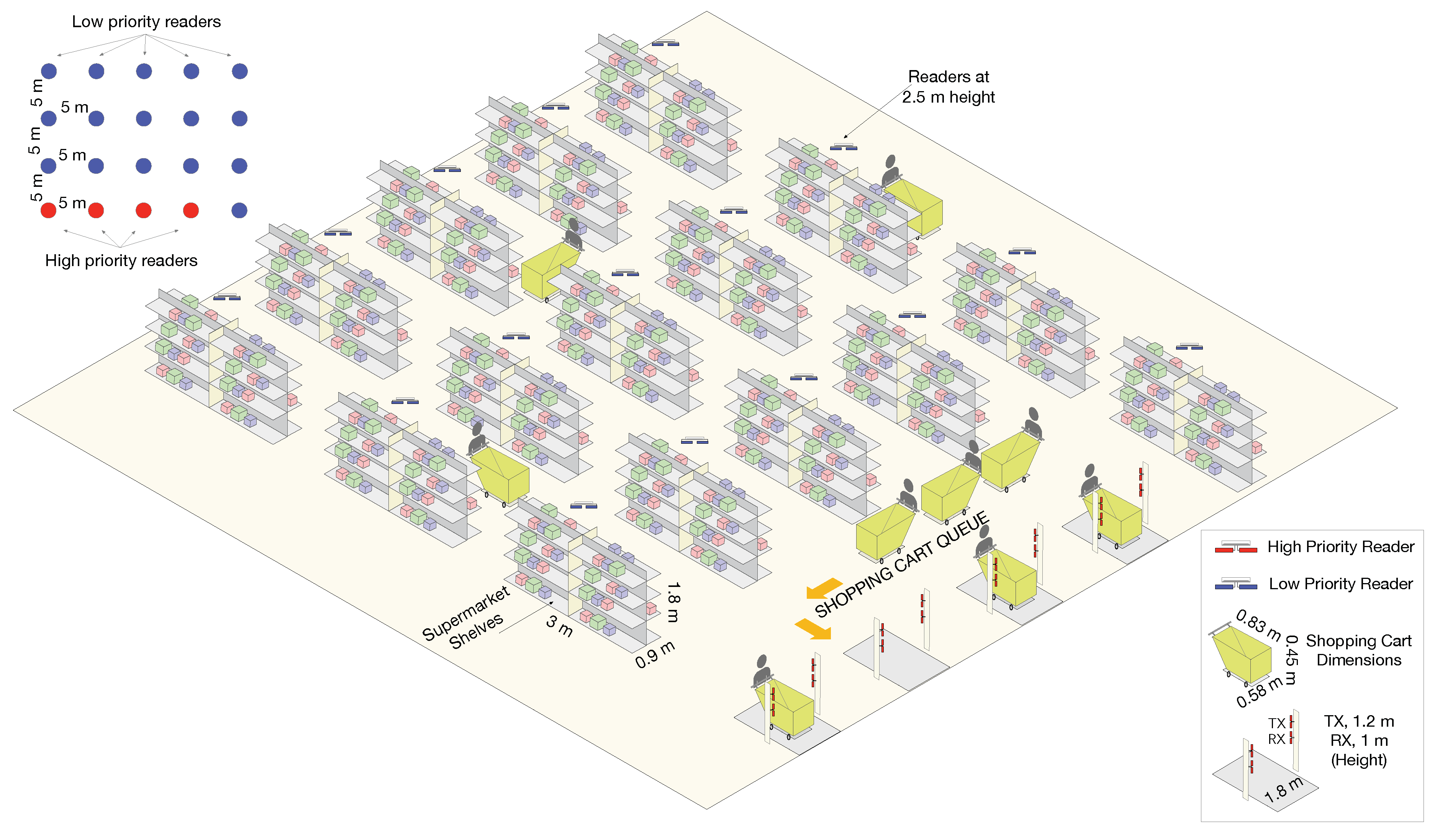
5. Grocery Shop Example
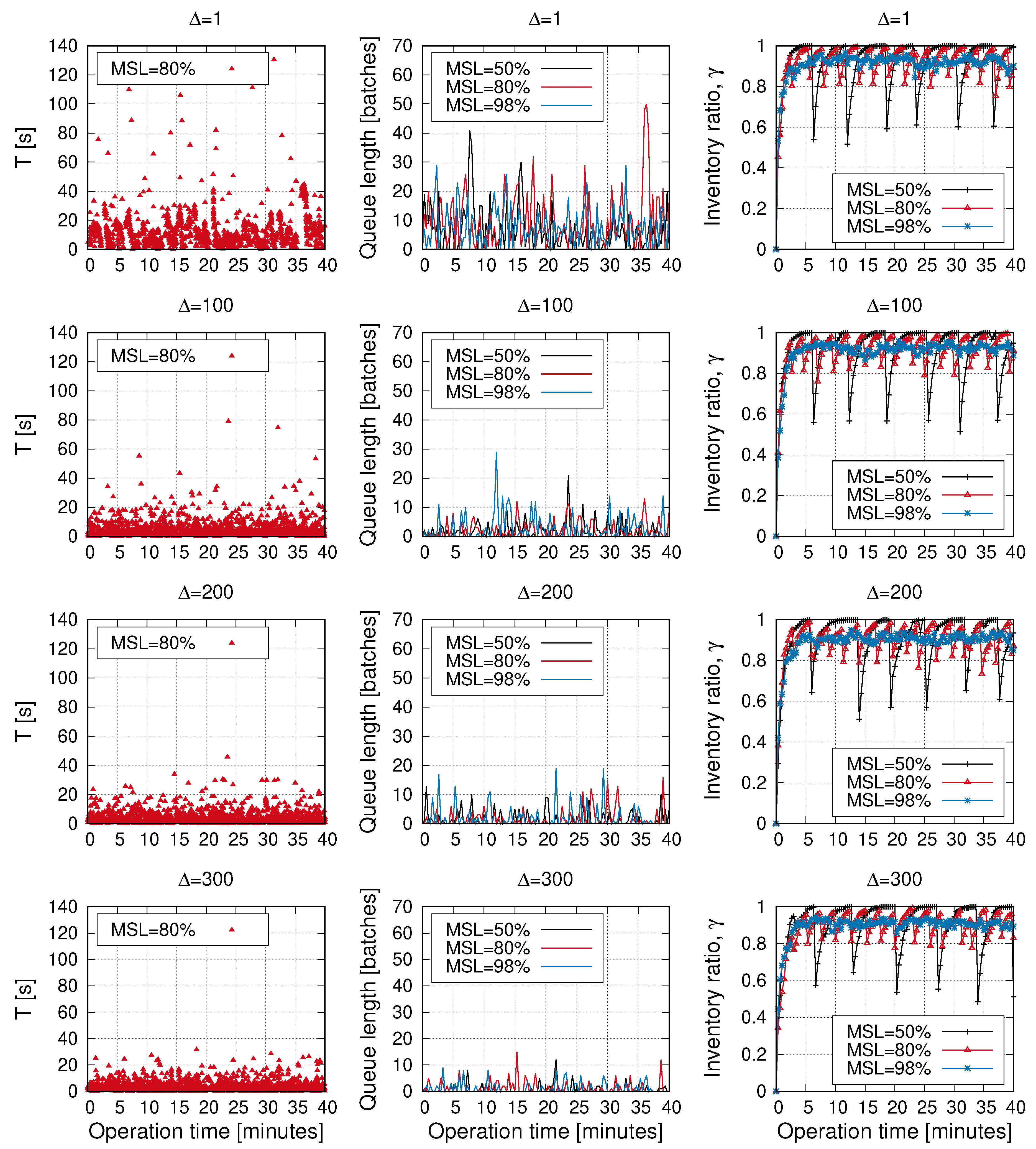
- Inventory traffic. A set of readers realizes a continuous inventory of the items distributed in the store area. The goal of these readers is to maximize the ratio of items correctly inventoried. This metric is called MSL (Minimum Stock Level) [34], and it measures inventory accuracy. MSL is defined as the time-average ratio of time where the percentage of known tags divided by the total number of tags is over a given minimum threshold. For example, an MSL with a threshold of 90% and accuracy of 99% indicates that in at least 99% of the queries (done at randomly chosen time moments) to the inventory database, 90% of the reported data will be exact. Note that items constantly appear, due to replacement tasks; or disappear, if they are picked up by customers. Thus, yielding to frequent changes in the inventory.
- Checking-out traffic. This represents the customers leaving the store. In this case, the customers wait in a shared exit queue until a checking-out gate is available. The number of tags per customer is random, and the batch for each particular buyer is read independently. This traffic has a high priority, and the goal is to minimize the total response (waiting plus interrogation) time of the clients.
- The inventory cycle time for the ceiling readers is 15 s. That is, the time between two consecutive interrogation processes of a ceiling reader.
- The checking-out readers have the minimal cycle time allowed by the ETSI EN 302-208-1 standard [27] of 100 ms.
- Each shelf in the store may contain up to 250 items (tags), and each ceiling reader manages four shelves. Therefore, a total number of up to 1000 tags have to be read at each interrogation process.
- The number of items (tags) picked by each customer is a random variable with a mixed Poisson-lognormal (PLN) distribution [35], which has been found to model this kind of process correctly.
- The clients arrive at the exit queue at a rate of customer (batch) per second.
- Simulation stops after 4000 clients have left the store.
- The replacement task is performed every 15 min in a random number of shelves (between 1 and 4).
- When a customer leaves the store, the same number of items (tags) as those in its batch are selected at random and removed from the shelves.
- All readers cause mutual interferences. In the best case, the minimum interference corresponds to two readers installed in the ceiling at 2.5 m height and which are separated by almost 29 m. The interference signal is reflecting in the ground and is received with a power of slightly below −23 dBm, much higher than the tags’ backscattered signals.
Results
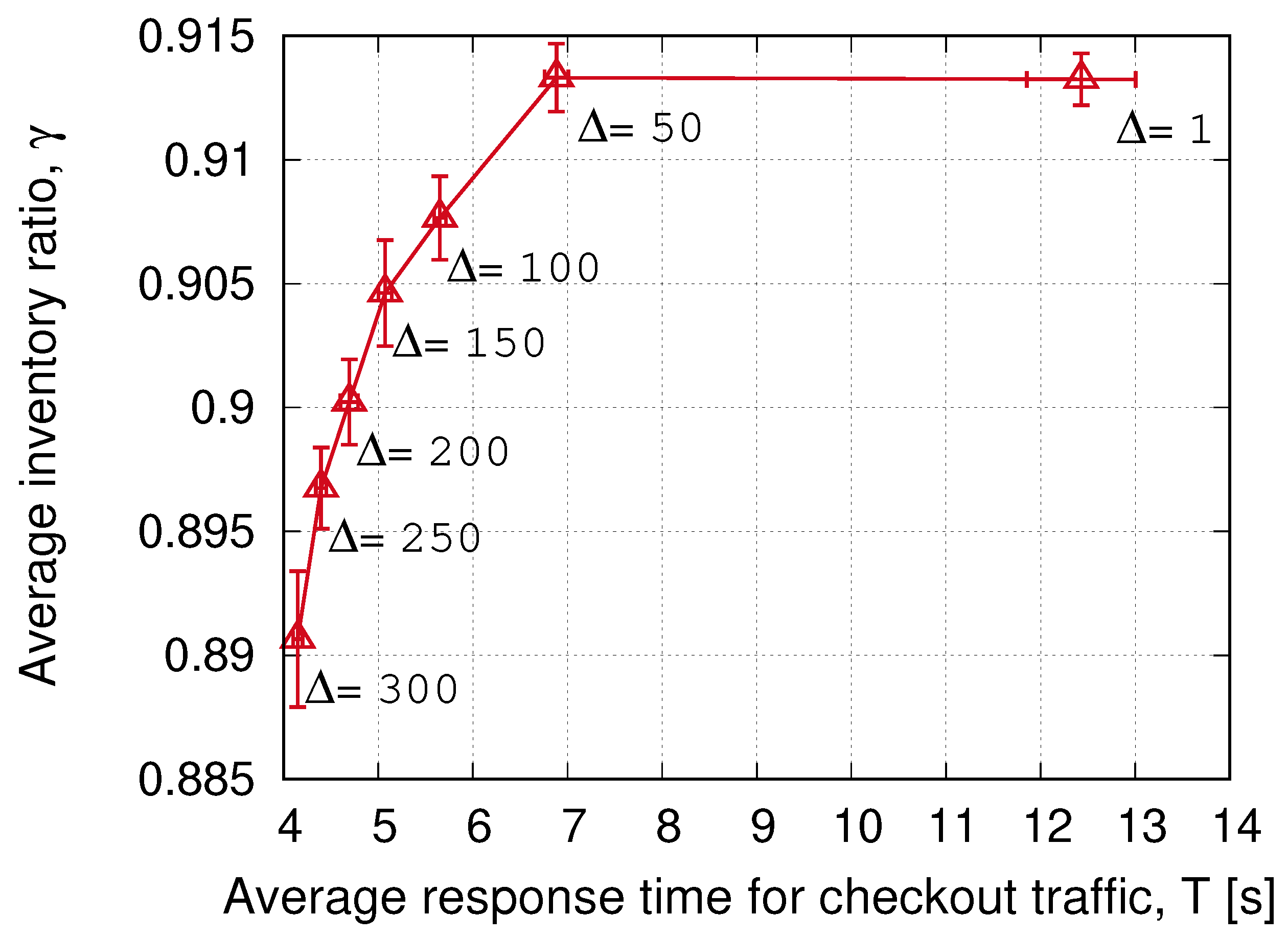
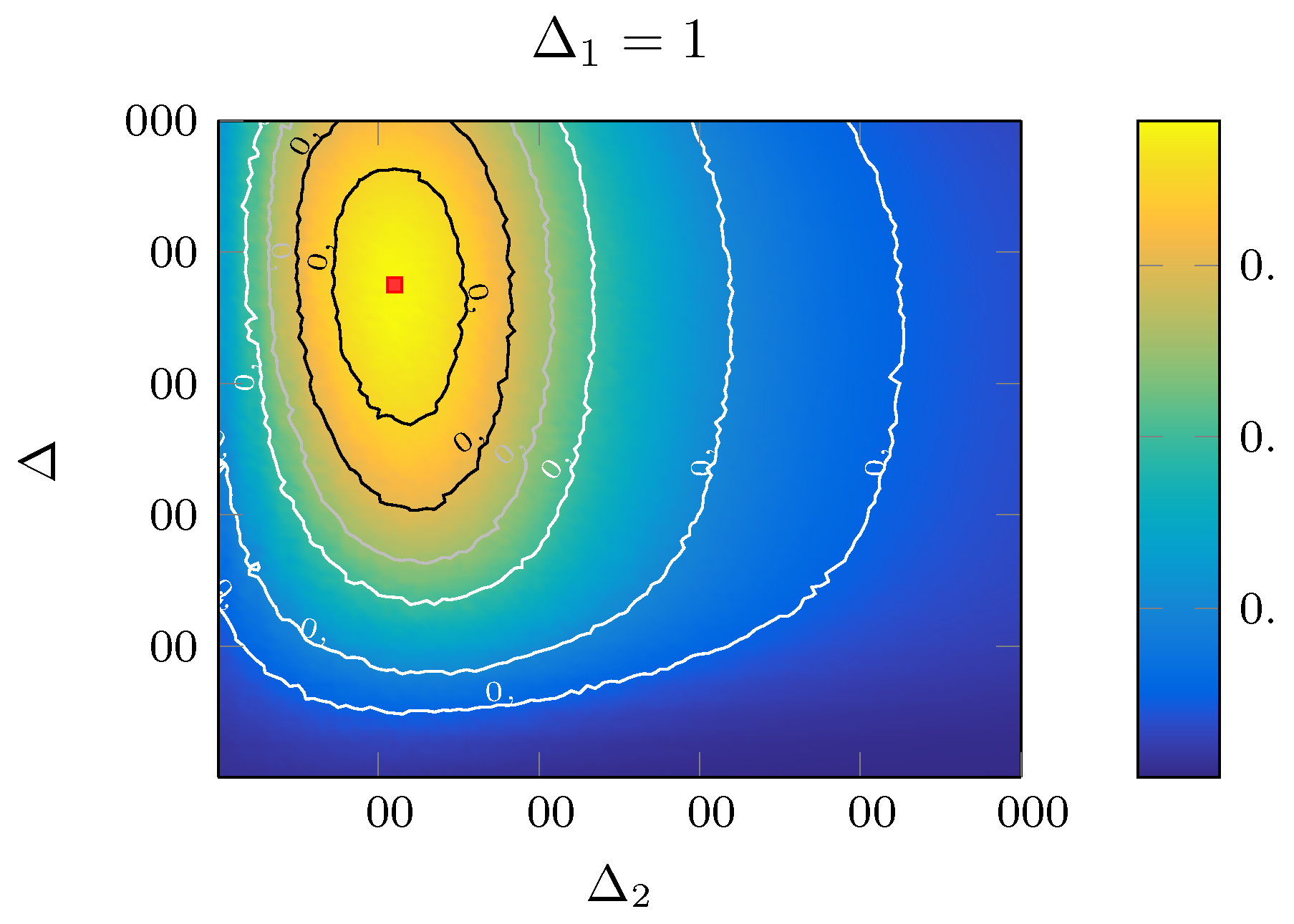
- A very significant reduction of the response time can be achieved with a negligible loss in the inventory accuracy by selecting = 50.
- Higher values can trade-off even less response time for minor losses in the accuracy. The reason for this minimal accuracy loss is that the inventory is a slow-varying process. A significant number of items have to be incorporated or removed to have a noticeable accuracy change, and the readers will be most likely able to correct the dataset, even with low-priority access to the channel.
- Pareto-front shows an exponential shape, and we can effectively select a response-time goal (only limited by the interrogation time, which does not depend on the parameter).
6. Hospital Example
6.1. Background
- Patient identification;
- Blood samples tracking;
- Security on sensitive surgical equipment and pharmacy;
- Tagging meals to ensure patients get the appropriate diet according to their treatment, allergies, and tastes;
- Laundry service can also be greatly optimized;
- Entrance control.
- Pharmaceutical/blood product distribution and tracking;
- Patient/medical staff identification and tracking;
- Medical asset tracking and locating;
- Implantable device RFID use;
- Other areas (including medical documents and patient records) (Kalorama, 2010).
6.2. Scenario Layout
- There are 20 readers installed at 2.5-m height distributed as follows: 8 perform patient monitoring (class 1, highest priority), 8 do continuous inventory of storage rooms (class 3, lowest priority), and the other 4 control items and patients crossing doors (class 2, medium priority).
- Each reader has an initial load of 20 tags.
- Arrival rate at each door is a Poisson of rate 1 group of people every 120 s, with the people in each group also given by a Poisson distribution of rate 3.
- Cycle time is set to the minimum of 100 ms for all reader classes.
- Tagged equipment has a reorganization rate (they change their rooms) every 4 min, involving a random number between 20 to 60 items.
- Simulation stop condition is 1 h of operation.
- As in the grocery shop example, all readers cause mutual interferences; in this case, the minimum level of interference is −26.3 dBm for readers at 42 m.
6.3. Results
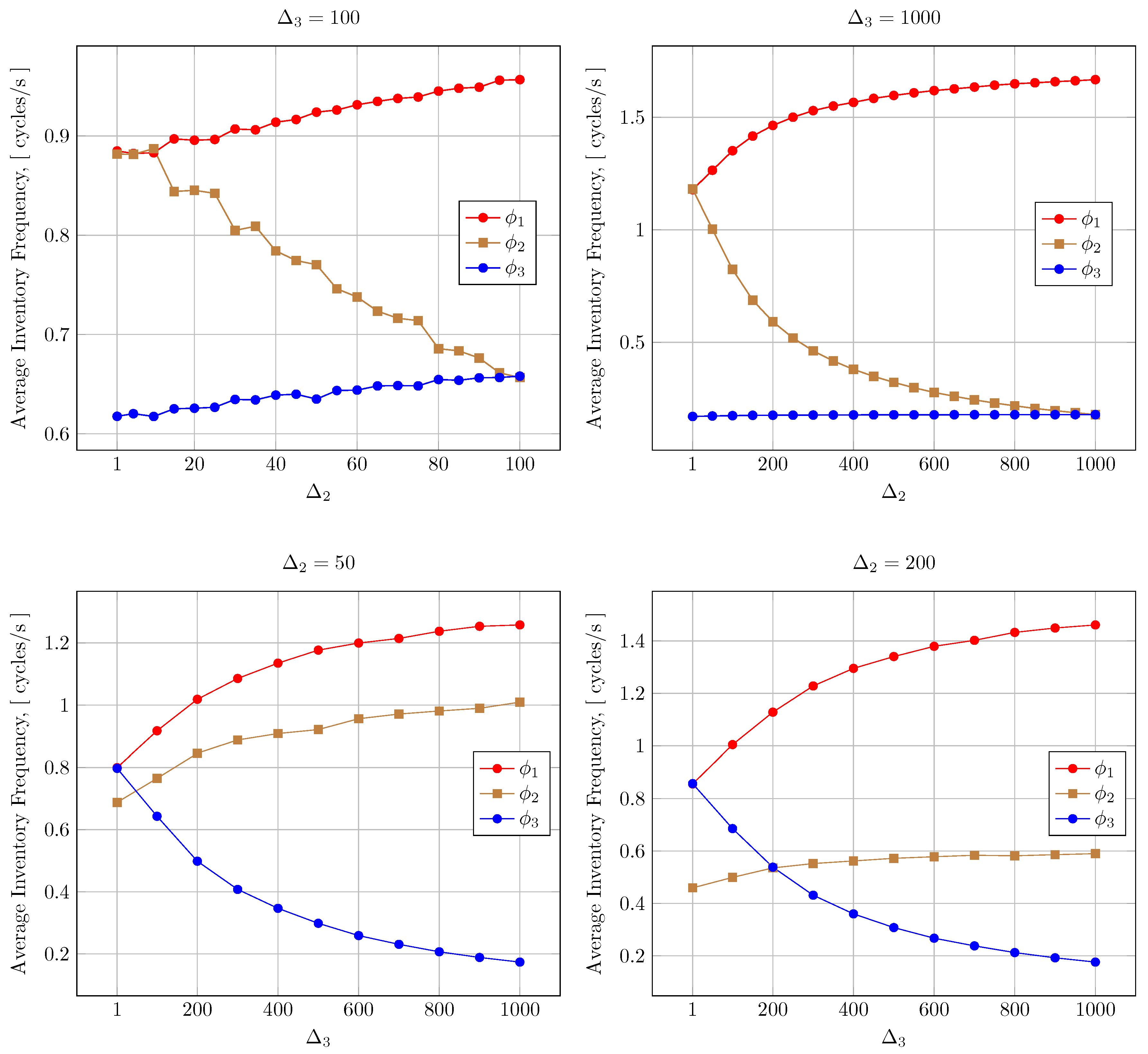
- For patient monitoring readers, the minimum and maximum frequencies are respectively 1 and 1.5 cycles/s;
- For door readers, the minimum and maximum frequencies are respectively 0.2 and 0.5 cycles/s;
- For room-inventorying readers, the minimum and maximum frequencies are respectively 0.1 and 0.2 cycles/s.
7. Greedy Online Scheme
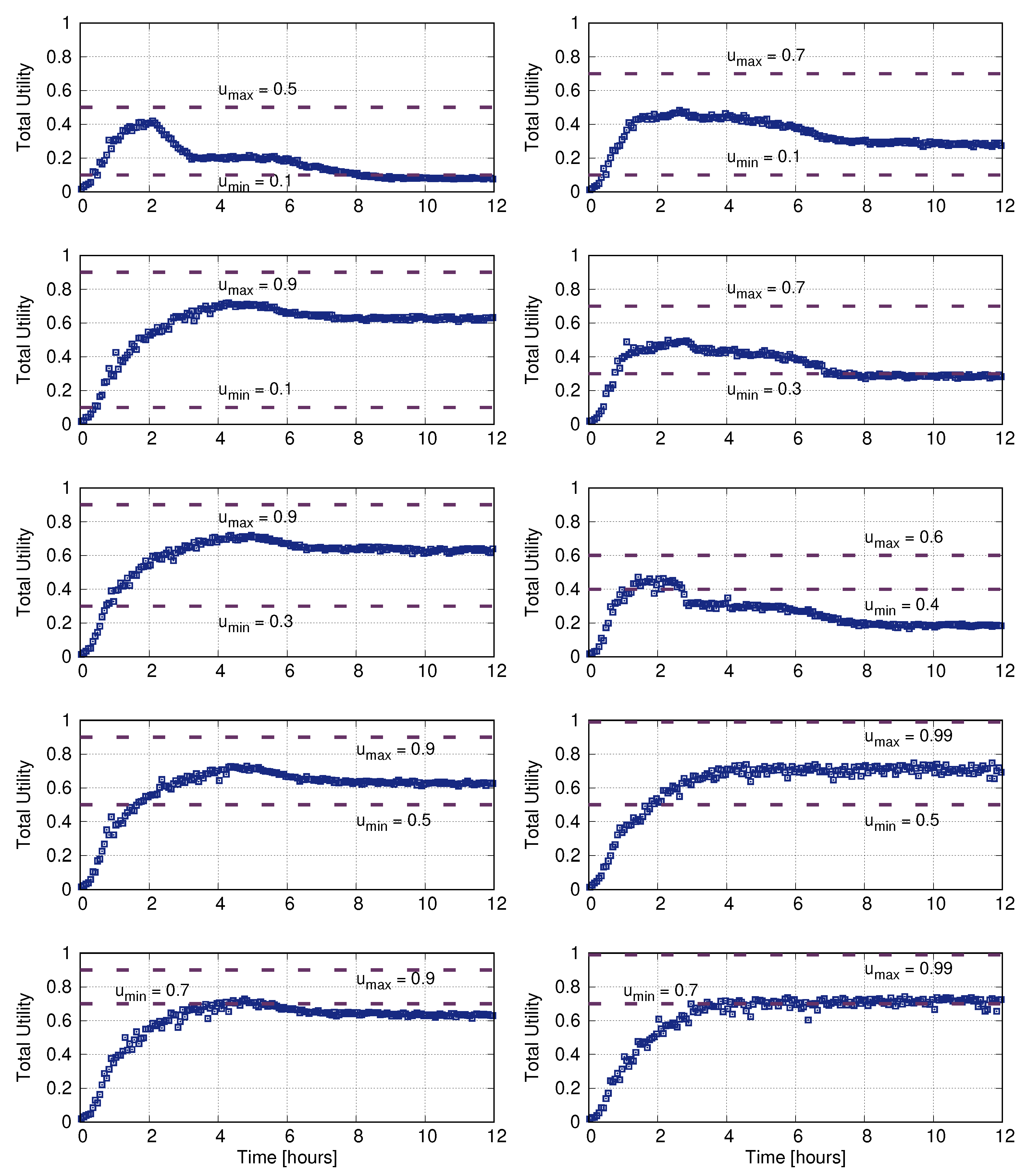
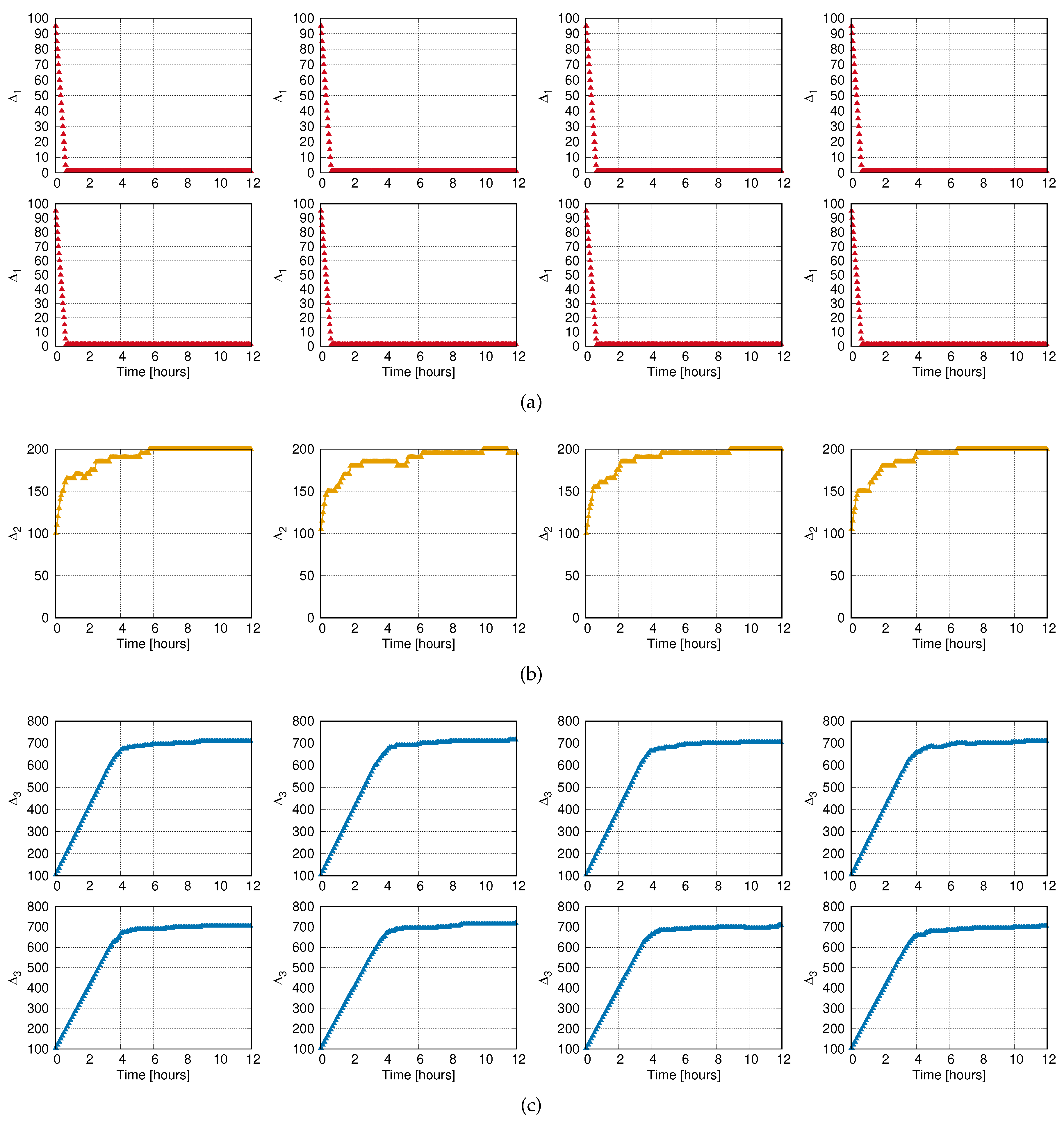
- Each reader operates independently, and for every decision period it estimates its interrogation cycle = Cycles in the last decision period/Decision period duration.
- The utility u is computed from as , a and b being the parameters associated to the particular reader traffic (see Table 2).
- If , then .
- If , then .
- Otherwise, is kept fixed.
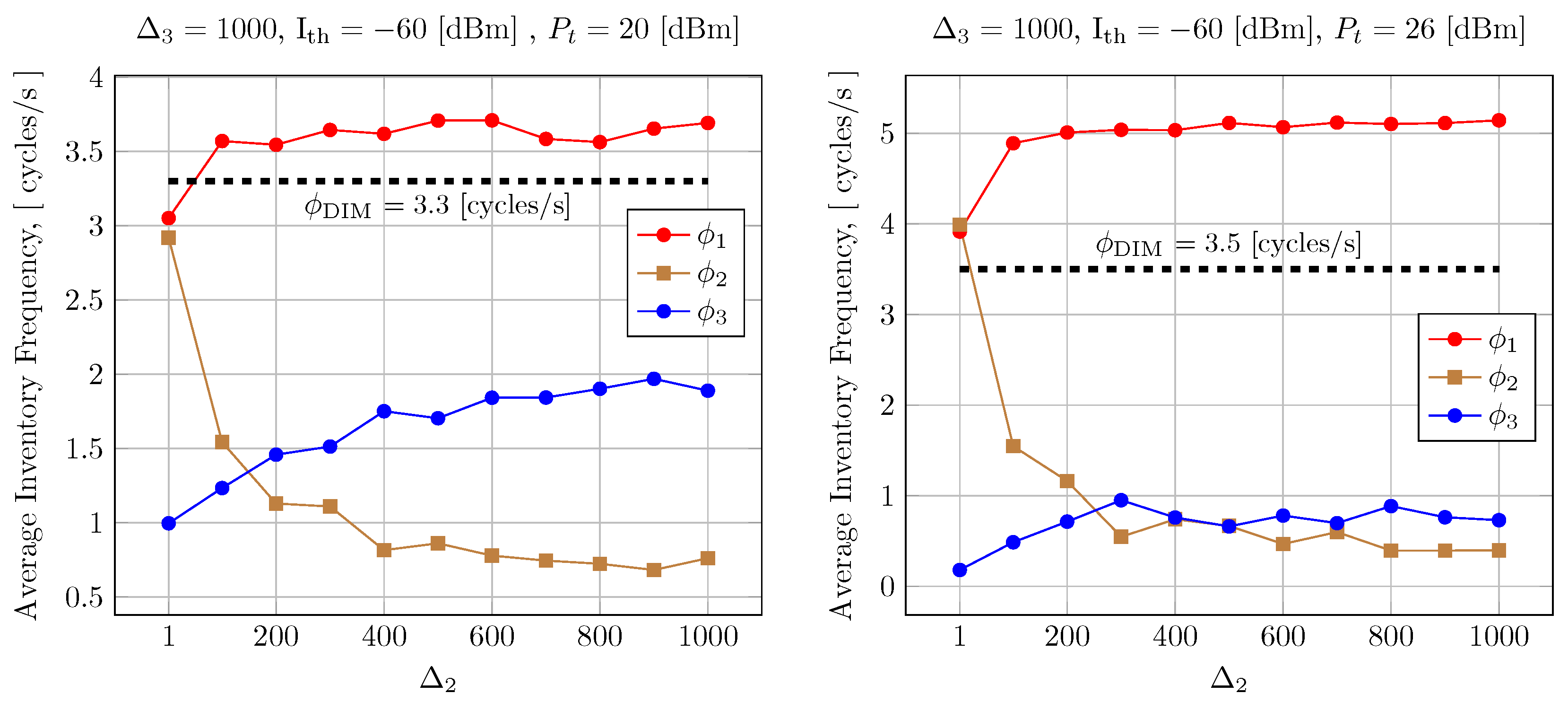
8. LBTM+DIM Mode Analysis
9. Conclusions
Author Contributions
Funding
Conflicts of Interest
References
- EPCglobal. EPC Radio-Frequency Identity Protocols Generation-2 UHF RFID; Specification for RFID Air Interface Protocol for Communications at 860 MHz–960 MHz; EPCglobal, 2015; Available online: https://www.gs1.org/sites/default/files/docs/epc/Gen2_Protocol_Standard.pdf (accessed on 18 April 2020).
- GS1 Barcode and Product Identification Standards. Regulatory Status for Using RFID in the EPC Gen2 (860 to 960 MHz) Band of the UHF Spectrum; Technical Report; EPCglobal, 2020; Available online: https://www.gs1.org/docs/epc/uhf_regulations.pdf (accessed on 18 April 2020).
- Title 47: Telecommunication, Parts 0 to 19. FCC Federal Communications Comission. Rules & Regulations; Technical Report; FCC: Washington, DC, USA, 2013. Available online: https://www.fcc.gov/wireless/bureau-divisions/technologies-systems-and-innovation-division/rules-regulations-title-47 (accessed on 18 April 2020).
- EU Standard. Part 1: Technical characteristics and methods of measurement. In ETSI EN 300 220-1: Short Range Devices (SRD) Operating in the Frequency Range 25 MHz to 1000 MHz; EU: Brussels, Belgium, 2017; Available online: https://www.etsi.org/deliver/etsi_en/300200_300299/30022001/03.01.01_60/en_30022001v030101p.pdf (accessed on 18 April 2020).
- Vales-Alonso, J.; López-Matencio, P.; Alcaraz, J. LBTM: A LBT protocol for Ubiquitous Applications in Multi-class RFID Networks. In Proceedings of the 2019 IEEE International Conference on RFID Technology and Applications (RFID-TA), Pisa, Italy, 25–27 September 2019; pp. 399–403. [Google Scholar]
- Karol, M.; Hluchyj, M.; Morgan, S. Input versus output queueing on a space-division packet switch. IEEE Trans. Commun. 1987, 35, 1347–1356. [Google Scholar] [CrossRef]
- Vis, P. Performance Analysis of Multi-Class Queueing Models. Ph.D. Thesis, Vrije Universiteit Amsterdam, Amsterdam, The Netherlands, 2017. [Google Scholar]
- Wilensky, U. Netlogo; Center for Connected Learning and Computer-Based Modeling, Northwestern University: Evanston, IL, USA, 1999. [Google Scholar]
- Almasi, B.; Bolch, G.; Sztrik, J. Heterogeneous finite-source retrial queues. J. Math. Sci. 2004, 121, 2590–2596. [Google Scholar] [CrossRef]
- Anjum, B.; Uzmi, Z.A. Multi-class Qos in 802.11 networks using gentle decrease of multiple contention windows. In Proceedings of the IEEE GLOBECOM 2007-IEEE Global Telecommunications Conference, Washington, DC, USA, 26–30 November 2007; pp. 5242–5247. [Google Scholar]
- Choi, N.; Seok, Y.; Choi, Y.; Kim, S.; Jung, H. P-DCF: Enhanced backoff scheme for the IEEE 802.11 DCF. In Proceedings of the 2005 IEEE 61st Vehicular Technology Conference, Stockholm, Sweden, 30 May–1 June 2005; Volume 3, pp. 2067–2070. [Google Scholar]
- Nafaa, A.; Ksentini, A.; Mehaoua, A. SCW: Sliding contention window for efficient service differentiation in IEEE 802.11 networks. In Proceedings of the IEEE Wireless Communications and Networking Conference, Wuhan, China, 26 September 2005; Volume 3, pp. 1626–1631. [Google Scholar]
- Wang, C.; Tang, W. A probability-based algorithm to adjust contention window in IEEE 802.11 DCF. In Proceedings of the 2004 International Conference on Communications, Circuits and Systems (IEEE Cat. No. 04EX914), Chengdu, China, 27–29 June 2004; Volume 1, pp. 418–422. [Google Scholar]
- Sun, X.; Dai, L. Backoff design for IEEE 802.11 DCF networks: Fundamental tradeoff and design criterion. IEEE/ACM Trans. Netw. (TON) 2015, 23, 300–316. [Google Scholar] [CrossRef]
- Olanrewaju, B.; Thanni, A.; Deji-Akinpelu, O.; Olanrewaju, O.; Osunade, O. RFID reader collision avoidance CSMA/CA with Fibonacci backoff algorithm. Int. J. Comput. Sci. Inf. Secur. 2018, 167, 204–210. [Google Scholar]
- Dong, Q.; Shukla, A.; Shrivastava, V.; Agrawal, D.; Banerjee, S.; Kar, K. Load balancing in large-scale RFID systems. Comput. Netw. 2008, 52, 1782–1796. [Google Scholar] [CrossRef]
- Ali, K.; Alsalih, W.; Hassanein, H. Set-Cover approximation algorithms for load-aware readers placement in RFID networks. In Proceedings of the 2011 IEEE International Conference on Communications (ICC), Kyoto, Japan, 5–9 June 2011; pp. 1–6. [Google Scholar]
- Chen, T.; Yang, Y.; Yang, B. RFID dense reader network anti-collision PSO model and solving. In Proceedings of the 2011 Third International Conference on Intelligent Human-Machine Systems and Cybernetics, Hangzhou, China, 26–27 August 2011; Volume 1, pp. 92–96. [Google Scholar]
- Zhao, C.; Wu, C.; Chai, J.; Wang, X.; Yang, X.; Lee, J.M.; Kim, M.J. Decomposition-based multi-objective firefly algorithm for RFID network planning with uncertainty. Appl. Soft Comput. 2017, 55, 549–564. [Google Scholar] [CrossRef]
- Ma, L.; Hu, K.; Zhu, Y.; Chen, H. A hybrid artificial bee colony optimizer by combining with life-cycle, Powell’s search and crossover. Appl. Math. Comput. 2015, 252, 133–154. [Google Scholar] [CrossRef]
- Jaballah, A.; Meddeb, A. A new variant of cuckoo search algorithm with self adaptive parameters to solve complex RFID network planning problem. Wirel. Netw. 2019, 25, 1585–1604. [Google Scholar] [CrossRef]
- Li, Z.; Lan, Y.; Yu, Q.; Wang, S. Hierarchical Petri Net Model of Distributed RFID Reader Network. In Proceedings of the 2019 Chinese Control And Decision Conference (CCDC), Nanchang, China, 3–5 June 2019; pp. 4549–4554. [Google Scholar]
- Liu, Y.; Yuen, C.; Cao, X.; Hassan, N.U.; Chen, J. Design of a scalable hybrid MAC protocol for heterogeneous M2M networks. IEEE Internet Things J. 2014, 1, 99–111. [Google Scholar] [CrossRef]
- Toni, L.; Frossard, P. Prioritized random MAC optimization via graph-based analysis. IEEE Trans. Commun. 2015, 63, 5002–5013. [Google Scholar] [CrossRef]
- Noori, M.; Rahimian, S.; Ardakani, M. Capacity Region of Aloha Protocol for Heterogeneous IoT Networks. IEEE Internet Things J. 2019. [Google Scholar] [CrossRef]
- Liva, G. Graph-based analysis and optimization of contention resolution diversity slotted Aloha. IEEE Trans. Commun. 2010, 59, 477–487. [Google Scholar] [CrossRef]
- ETSI EN 302 208 V3. 1.1. Radio Frequency Identification Equipment Operating in the Band 865 MHz to 868 MHz with Power Levels up to 2 W and in the Band 915 MHz to 921 MHz with Power Levels up to 4 W; Harmonised Standard Covering the Essential Requirements of Article 3.2 of the Directive 2014/53/EU; European Telecommunications Standards Institute: Sophia Antipolis, France, 2016. [Google Scholar]
- Bolic, M.; Simplot-Ryl, D.; Stojmenovic, I. RFID Systems: Research Trends and Challenges; John Wiley & Sons: New York, NY, USA, 2010. [Google Scholar]
- RFID4U, RFID Solutions Partner, Software. Dig Deep—RFID Anti-Collision and Dense Reader Mode. Available online: https://rfid4u.com/rfid-basics-resources/dig-deep-dense-reader-mode-and-anti-collision/ (accessed on 18 April 2020).
- López-Matencio, P.; Vales-Alonso, J. A simulation-based comprehensive study of the LBT mechanism in RFID networks. In Proceedings of the 2018 6th International EURASIP Workshop on RFID Technology (EURFID), Brno, Czech Republic, 11–12 September 2018; pp. 1–7. [Google Scholar]
- Pablo López Matencio. LBTM: Multiclass-Traffic-RFID-Simulator for Supermarket and Hospital Plant Scenarios with Different Traffic Classes. 2019. Available online: https://github.com/plopezmp/LBTM (accessed on 18 April 2020).
- Vales-Alonso, J.; Bueno-Delgado, V.; Egea-Lopez, E.; Gonzalez-Castano, F.; Alcaraz, J. Multiframe Maximum-Likelihood Tag Estimation for RFID Anticollision Protocols. Ind. Inform. IEEE Trans. 2011, 7, 487–496. [Google Scholar] [CrossRef]
- Li, R.; Song, T.; Capurso, N.; Yu, J.; Couture, J.; Cheng, X. IoT Applications on Secure Smart Shopping System. IEEE Internet Things J. 2017, 4, 1945–1954. [Google Scholar] [CrossRef]
- Braglia, M.; Zavanella, L. Modelling an industrial strategy for inventory management in supply chains: The ‘Consignment Stock’ case. Int. J. Prod. Res. 2003, 41, 3793–3808. [Google Scholar] [CrossRef]
- Sorensen, H.; Bogomolova, S.; Anderson, K.; Trinh, G.; Sharp, A.; Kennedy, R.; Page, B.; Wright, M. Fundamental patterns of in-store shopper behavior. J. Retail. Consum. Serv. 2017, 37, 182–194. [Google Scholar] [CrossRef]
- Fuhrer, P.; Guinard, D. Building a smart hospital using RFID technologies. ECEH 2006, 91, 131–142. [Google Scholar]
- Haddara, M.; Staaby, A. RFID applications and adoptions in healthcare: A review on patient safety. Procedia Comput. Sci. 2018, 138, 80–88. [Google Scholar] [CrossRef]
- Van Oranje-Nassau, C.; Schindler, H.R.; Valeri, L.; Vilamovska, A.M.; Hatziandreu, E.; Conklin, A. Study on the Requirements and Options for Radio Frequency Identification (RFID) Application in Healthcare; RAND Corporation Publisher: Santa Monica, CA, USA, 2009; Available online: https://www.rand.org/pubs/technical_reports/TR608z1.html (accessed on 18 April 2020).
- Yang, C.; Wang, X.; Mao, S. Unsupervised Detection of Apnea using Commodity RFIDTags with a Recurrent Variational Autoencoder. IEEE Access 2019. [Google Scholar] [CrossRef]
- Hou, Y.; Wang, Y.; Zheng, Y. TagBreathe: Monitor breathing with commodity RFID systems. In Proceedings of the 2017 IEEE 37th International Conference on Distributed Computing Systems (ICDCS), Atlanta, GA, USA, 5–8 June 2017; pp. 404–413. [Google Scholar]
- Del Carmen León-Araujo, M.; Gómez-Inhiesto, E.; Acaiturri-Ayesta, M.T. Implementation and Evaluation of a RFID Smart Cabinet to Improve Traceability and the Efficient Consumption of High Cost Medical Supplies in a Large Hospital. J. Med Syst. 2019, 43, 178. [Google Scholar] [CrossRef]
- Meiller, Y.; Bureau, S.; Zhou, W.; Piramuthu, S. Adaptive knowledge-based system for health care applications with RFID-generated information. Decis. Support Syst. 2011, 51, 198–207. [Google Scholar] [CrossRef]
- Luo, G.; Duan, X.; Sun, Z.; Yin, M.; Jiao, B. Design of a Passive Multi-tag RFID Hospital Entry/Exit Detection System Based on Data Mining Method. In Proceedings of the 2017 International Conference on Sensing, Diagnostics, Prognostics, and Control (SDPC), Shanghai, China, 16–18 August 2017; pp. 438–443. [Google Scholar]
- Montagna, S.; Croatti, A.; Ricci, A.; Agnoletti, V.; Albarello, V. Pervasive Tracking for Time-Dependent Acute Patient Flow: A Case Study in Trauma Management. In Proceedings of the 2019 IEEE 32nd International Symposium on Computer-Based Medical Systems (CBMS), Cordoba, Spain, 5–7 June 2019; pp. 237–240. [Google Scholar]
- IntelliGuard Solutions. IntelliGuard and MEPS Real-Time Inc. 2019. Available online: https://ig.solutions (accessed on 18 April 2020).
- Seidman, S.J.; Brockman, R.; Lewis, B.M.; Guag, J.; Shein, M.J.; Clement, W.J.; Kippola, J.; Digby, D.; Barber, C.; Huntwork, D. In vitro tests reveal sample radiofrequency identification readers inducing clinically significant electromagnetic interference to implantable pacemakers and implantable cardioverter-defibrillators. Heart Rhythm 2010, 7, 99–107. [Google Scholar] [CrossRef] [PubMed]
- Van Der Togt, R.; van Lieshout, E.J.; Hensbroek, R.; Beinat, E.; Binnekade, J.M.; Bakker, P. Electromagnetic interference from radio frequency identification inducing potentially hazardous incidents in critical care medical equipment. JAMA 2008, 299, 2884–2890. [Google Scholar] [CrossRef] [PubMed]
- Al Nahas, H.; Deogun, J.S. Radio frequency identification applications in smart hospitals. In Proceedings of the Twentieth IEEE International Symposium on Computer-Based Medical Systems (CBMS’07), Maribor, Slovenia, 20–22 June 2007; pp. 337–342. [Google Scholar]
- Knels, R.; Ashford, P.; Bidet, F.; Böcker, W.; Briggs, L.; Bruce, P.; Csöre, M.; Distler, P.; Gutierrez, A.; Henderson, I.; et al. Guidelines for the use of RFID technology in transfusion medicine. Vox Sang. 2010, 98, 1–24. [Google Scholar]
- Cairó, J.I.; Bonache, J.; Paredes, F.; Martín, F. Interference Sources in Congested Environments and its Effects in UHF-RFID Systems: A Review. IEEE J. Radio Freq. Identif. 2018, 2, 1–8. [Google Scholar] [CrossRef]





| (mW) | , | (m) | M | Sensitivity (dBm) | ||||
|---|---|---|---|---|---|---|---|---|
| Transmitter Power | Transceiver Gains | Tag Gain | Polarization Mismatch | Wave-length | Modulation Factor | Power Coefficient | On-object Gain Penalty | Receiver Sensitivity |
| 500 | 5 | 1.62 | 0.5 | 0.35 | 0.25 | 1 | 1.2 | −80 |
| Traffic Class | a | b | (cycles) | (cycles) | Notes | ||
|---|---|---|---|---|---|---|---|
| Patient monitoring | 8.78 | 10.98 | 1 | 1.5 | 0.82 | 1 | Reference frequencies are selected to achieved a number of cycles as high as possible and of at least 1 cycle/s |
| Doors | 14.64 | 5.12 | 0.2 | 0.5 | 0.95 | 220 | Reference frequencies aim at getting at least 1 interrogation opportunity for a maximum walking speed of 6 km/h considering a 2-m interrogation radius around door |
| Room inventorying | 43.94 | 6.59 | 0.1 | 0.2 | 0.97 | 750 | Reference frequencies aim at detecting critical equipment transfers in less than 1 min |
© 2020 by the authors. Licensee MDPI, Basel, Switzerland. This article is an open access article distributed under the terms and conditions of the Creative Commons Attribution (CC BY) license (http://creativecommons.org/licenses/by/4.0/).
Share and Cite
López-Matencio, P.; Vales-Alonso, J.; Alcaraz, J.J. LBTM: Listen-before-Talk Protocol for Multiclass UHF RFID Networks. Sensors 2020, 20, 2313. https://doi.org/10.3390/s20082313
López-Matencio P, Vales-Alonso J, Alcaraz JJ. LBTM: Listen-before-Talk Protocol for Multiclass UHF RFID Networks. Sensors. 2020; 20(8):2313. https://doi.org/10.3390/s20082313
Chicago/Turabian StyleLópez-Matencio, Pablo, Javier Vales-Alonso, and Juan J. Alcaraz. 2020. "LBTM: Listen-before-Talk Protocol for Multiclass UHF RFID Networks" Sensors 20, no. 8: 2313. https://doi.org/10.3390/s20082313
APA StyleLópez-Matencio, P., Vales-Alonso, J., & Alcaraz, J. J. (2020). LBTM: Listen-before-Talk Protocol for Multiclass UHF RFID Networks. Sensors, 20(8), 2313. https://doi.org/10.3390/s20082313





