1. Introduction
Advancement in electronics and wireless communication systems leads to the implementation of wireless sensor networks (WSNs). WSN is a collection of wireless nodes, which are deployed in unstructured environment where they can collect and process information according to their assigned task. WSN contains several wireless nodes, which has storage, processing and communication capabilities. Wireless sensors are tiny devices, which are deployed in an infrastructure-free environment to collect information according to their assigned task [
1]. Moreover, these networks have various applications in the real world. In the recent past, wireless sensor network applications have been extended from general to specific uses with the passage of time. The specific application of WSNs includes emergency response systems, weather forecasting, agriculture, body area network and security assessment systems.
The cost of wireless nodes varies according to their size, on board battery charge, processing, computing, receiving and transmitting capabilities. A normal wireless sensor network consists of hundreds to thousands of sensor devices. They work according to their assigned task in the deploying area. The structure (topology) of these networks can be categorized according to their deployment environment [
2]. WSNs are mainly categorized into three types, which includes cluster based, flat based and hierarchical based networks. The deployment of sensor devices in inaccessible, harsh and remote locations increases its importance, because these devices have limited storage, power, bandwidth and communication capabilities. Similarly, open and shared transmission medium of these network increases its susceptibilities to different kind of transmission attacks.
Different types of WSN attacks that affect the integrity, authenticity and availability of information includes denial of service attacks (DoS), jamming attack, black hole attack, eavesdropping attacks, distributed denial of service attacks (DDoS), sybil attack and wormhole attack. Authentication of operational devices in WSNs is one of the challenging task to the research community, because of the self-organizing and dynamic nature of these devices. Moreover, due to the constraint oriented behavior of these nodes, some generalized authentication schemes exists in the literature to develop a secure communication infrastructure for these networks. Likewise, the MAC-AODV scheme is proposed in article [
3] to maintain the physical and network layer security of constraint oriented networks. However, this scheme identifies the malicious nodes in the network by means of MAC address matching in the base station.
There are also some routing, data eavesdropping and Man-in-Middle attacks in WSNs, where the attacker uses the transmission medium to capture network traffic and hijack networks security. Similarly, jamming attack is also a type of transmission attack, where the attacker uses a high range of transmission signals with the same frequency transmissions to disrupt the network security. However, jamming attacks are also happening, due to some unintentionally wireless medium interferences such as noise and collision etc. [
4]. Moreover, jamming attacks in wireless sensor networks constitutes the physical interference of an attacker to disturb the communication process. The objective of DoS attacks in a wireless network is to direct an unwanted transmission signal toward the sensor node to disrupt communication channel, bandwidth, battery resources, storage resources and transmission line of destination node. Furthermore, this not only disturbs the communication process, but also minimizes the network lifespan [
5].
Jamming attack in wireless sensor networks is one of the simplest types of attack that an attacker uses to disrupt network security, because it does not need any special type of hardware or software. To elaborate upon the concept of jamming attacks in a precise way, this attack can be managed by listening to the transmission medium passively to identify the transmission frequency and generate the same frequency signal to disrupt the legitimate communication process. Likewise, a common jamming attack is characterized by a low detection rate, high energy efficiency and anti jamming resistance [
6]. Jamming attack detection has been an ongoing research area in wireless networks over the last decade. The researches community proposed various scheme to address the issue of jamming attacks in WSNs. However, in most of the cases these techniques are specific to operation, software, hardware OR environment.
Moreover, the research community also worked on the prior communication information (behavior of transmission) of the wireless networks to identify jamming attacks. Furthermore, they used indicators and trackers to verify the existence of jamming attacks in WSNs [
7]. The example of these behaviors includes signal strength of transmitting packet at the physical layer and packet lost ratio at the 7th layer of the OSI model (application layer). The cross layer model (CLM) scheme was used to combat the collection of jamming attacks in wireless networks with the help of an indicator [
8]. A multi model scheme for detection of jamming attacks in 802.11b wireless networks is proposed in [
9]. In this model, they used the correlation parameters such as signal strength variation, packet delivery ratio and width of the received signal to identify jamming attacks in deploying WSNs. Zhang et al. [
10] proposed the optimal attack scheduling technique to investigate jamming attacks in WSNs. He used a remote state estimator to check the reliability metrics of data at remote end of deployed WSN. However, this scheme was affective for a specific area of WSNs, where the attacker block individual nodes transmission channels. In case, if the attacker generate a high interference frequency in the transmission channel, then the proposed model is not effective acknowledge the existence of jamming attack in WSNs. Moreover, in the proposed model, the jamming attacks detection rate was based on information such as covariance error of communication, for which is not possible to be consistent every time, due to the dynamic nature of wireless nodes in WSNs. Therefore, the performance reliability metrics for covariance error do not remain constant in a deployed WSN environment.
The optimal jamming attack detection scheme was proposed by Li et al. [
11]. In the proposed scheme, he used monitor nodes to detect estimated jamming attacks in the deployed WSNs. However, wireless sensor networks are deployed in an inaccessible, remote and harsh location, where monitoring of monitor nodes is not possible. Therefore, the proposed model is only effective for small accessible regional based WSNs. Pradhan and Venkitasubramaniam proposed the K-L divergence scheme for detection of dynamic data injection in WSNs [
12]. In dynamic data injection, the attacker gets physical access to the transmission medium and modify the sequence of temporal data in the network. The proposed model uses the K-L divergence mechanism to identify dynamic data injection attacks in WSNs by means of comparing the values of prior and posterior-distribution of arriving data at remote location.
The existing techniques of jamming attacks are mostly based on the single channel and single sensor node transmission channels. However, jamming attacks under multiple channel and sensor nodes are an interesting issue for research community to detect and prevent it accurately in operational networks. By the encouragement of this statement, we considered a wireless network infrastructure (topology) of dynamic number of nodes in this research, whose communication is controlled by three edge nodes and round trip time (RTT). RTT is the amount of time that messages need to travel from source to destination in communication infrastructure. The edge nodes first run the embedded algorithm to calculate the estimated value of RTT at the local side (edge node). likewise, the edge node transmits the message packet, which contain information of estimated RTT of local site to a remote location by means of communication channel. At a remote destination, the estimator calculates the expected value of RTT for the incoming message packet. Similarly, the remote estimator compares both values of RTT (source and destination) to maintain the performance reliability of communication in the network.
Moreover, the three edge nodes used in the deployed area of wireless sensor network have different transmission frequency channels in the same bandwidth. All the three edge nodes calculate the estimated RTT of a packet before transmitting it to the transmission media and the estimated value of RTT is sent in the payload of the packet, where at remote location it is compared to estimator calculated value of RTT to maintain transmission reliability. Similarly, if an adversary wants to disrupt the communication process or degrade the network performance the adversary generates the same frequency signal as that of the edge node transmitting signals to disturb the communication process. In this case, the adversary can only disturb the communication process of only one edge node, because all three edge nodes have different communication channels based on embedded algorithm configuration. Keep in mind the existing schemes of jamming attacks, which verifies that the attacker can jam only one channel at a time to disrupt the communication process. The three edge nodes and channel segregation in our proposed scheme address the aforementioned issue of jamming attacks in WSNs with simple network implementation. Moreover, the proposed model creates a secure infrastructure for deployed WSNs, where they can collect and process information according to their assigned task. Similarly, the secure communication environment maximizes network performance by accurately detecting jamming attack, low latency and high throughput.
1.1. Problem Statement
Detection and prevention of jamming attack in WSNs through an anonymous edge node scheme.
There exists a WSN, which contains a dynamic number of sensor nodes (S), where S = (, , –). The S nodes collects information and transmit it to a remote destination through edge nodes (), where = (, and ). The nodes has different frequency channels (CH), where CH = (, , and ).
1.2. Objective of Research
Design a secure communication infrastructure for deploying wireless nodes (S), where S∈ for designated WSN.
Deploy nodes in designated WSNs.
Categorise the Transmission channels (CH).
Ensure transmission channel security.
Detect jamming attacks
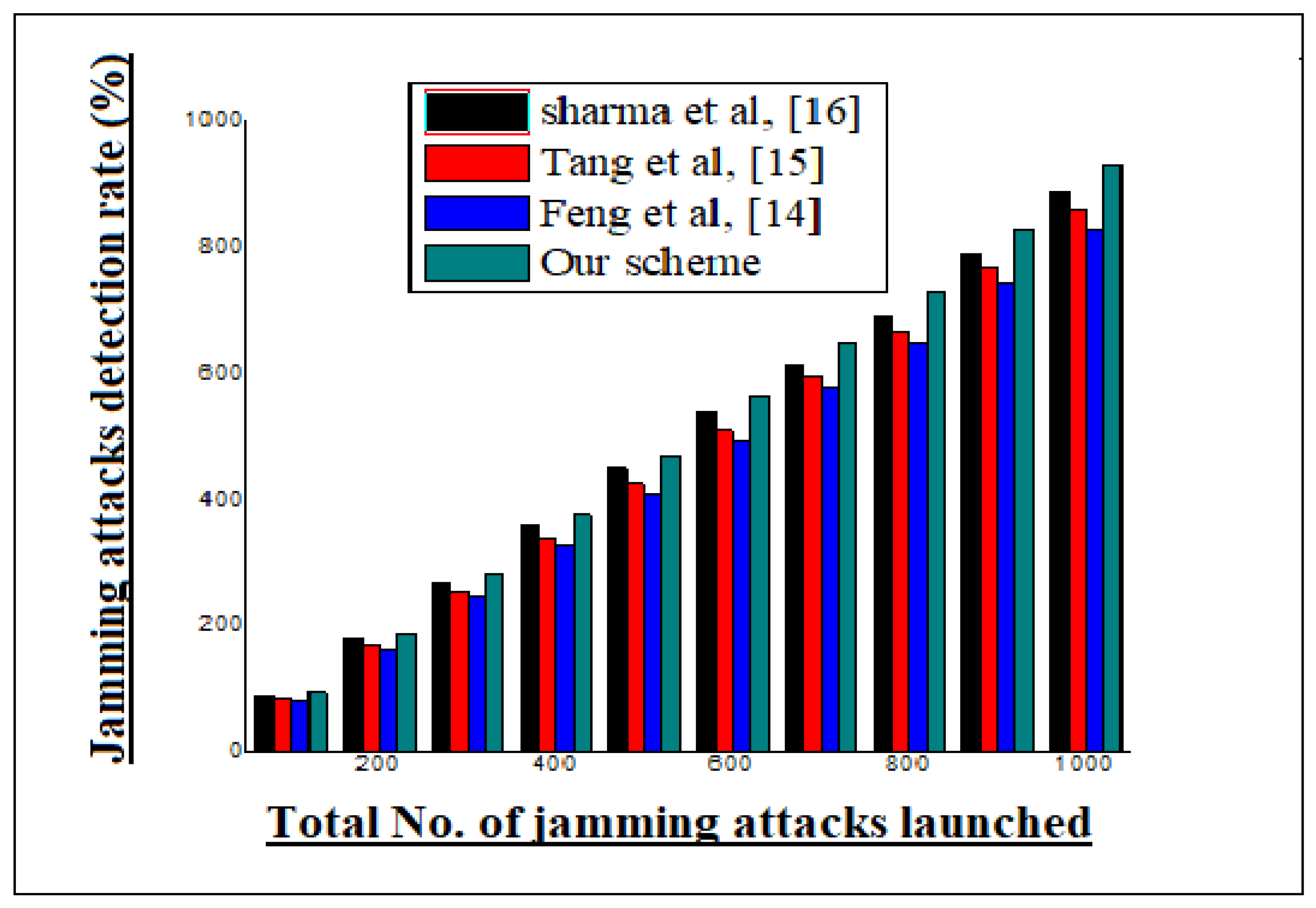
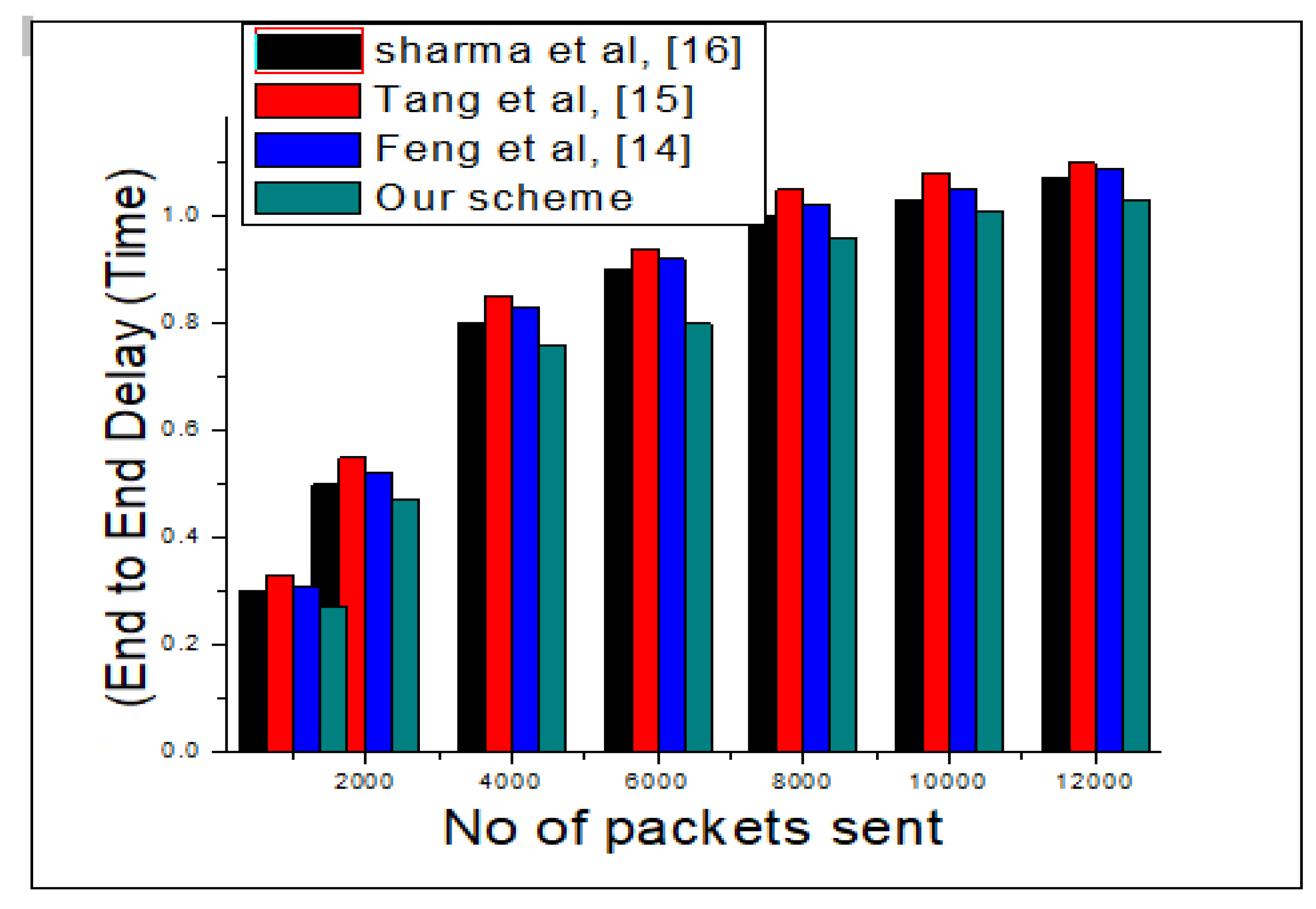
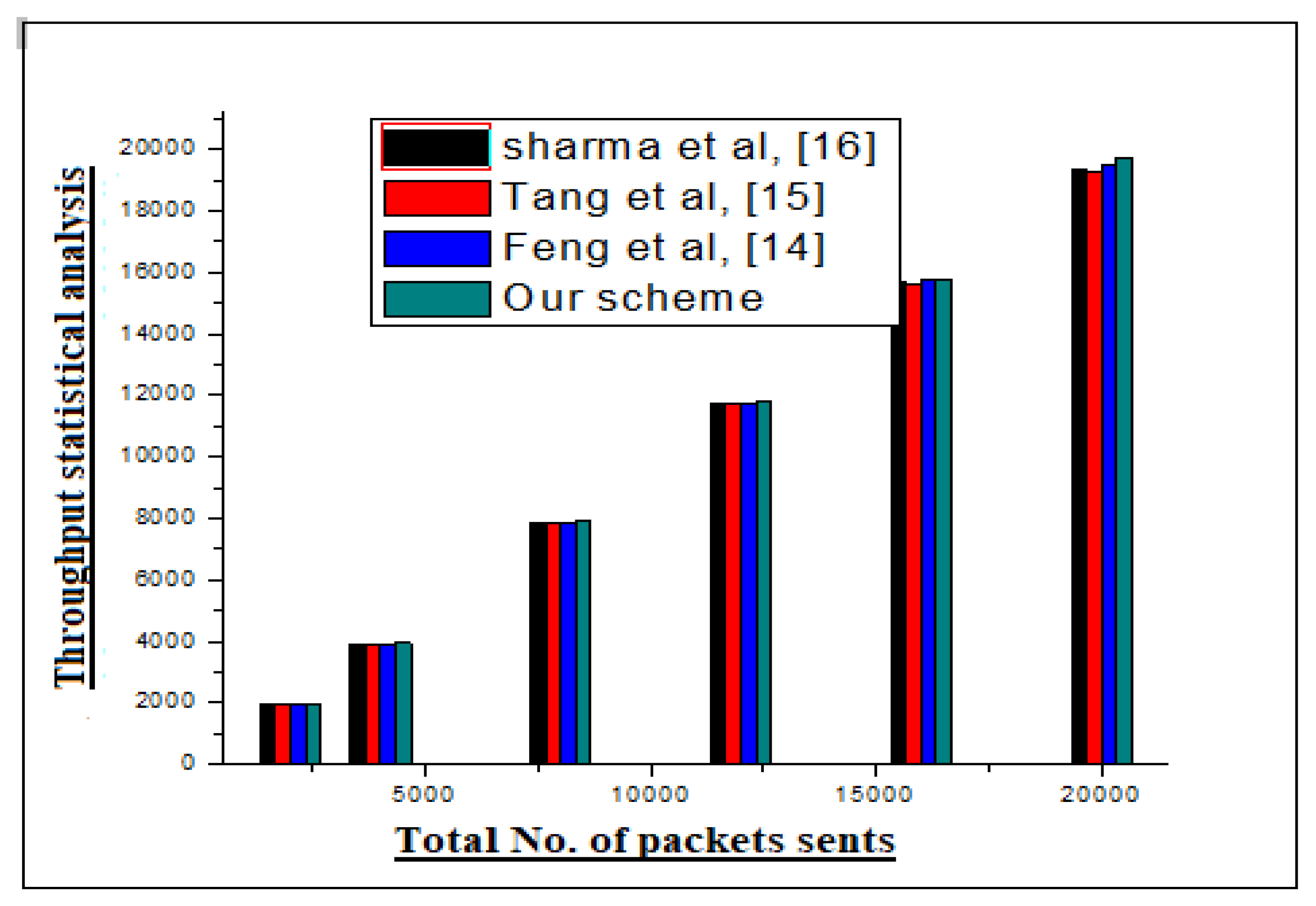
Claim justified results for our scheme in a simulation environment.
The rest of the paper is organized as follows. The subsequent section of the paper overviews the related work of jamming attacks.
Section 3 of the paper contains the proposed methodology with adopted algorithm of our scheme.
Section 4 discusses the simulation experiment and result statistics of our scheme. The subsequent section concludes the paper.
2. Literature Review
In WSNs, the security of wireless devices and communication infrastructure is one of the most challenging issues for researchers, due to its dynamic and unpredictable nature. The literature suggests various schemes to resolve the issues associated with susceptibility and security of the WSNs. Many researchers worked on this issue to develop a secure communication infrastructure. Every network threat has their own aim to hijack the network security by means of monitoring network traffic, damage some wireless nodes, jam network traffic or disrupt the entire network. However, the most destructive attack among all of them is jamming attack, because it disturbs the entire communication of the network. Some of the suggested techniques for prevention of jamming attacks are mentioned below.
The multi joint relay and jammer selection scheme was proposed by Zhang et al. [
13]. They used a secure decoder in their model to assess all incoming signal before and after transmission. Additionally, they used an artificial broadcast signal in their scheme to misguide the adversary/attacker, before launching attack on the communication channel. Feng et al. [
14] used the random Markov chain process in their research to develop a multi agent system infrastructure for prevention of strategic cyber attacks in wireless networks. In this scheme, a hybrid stochastic secure control framework was used to investigate and identify jamming attack. However, after each and every investigation check, the connectivity restoration mechanism was mandatory, which increase the complexity and network overhead in designated WSNs. Tang et al. [
15], suggested the triggering strategy model for detection of jamming attacks such as denial of service (DoS) in mobile robots. They check the proposed model in the operational environment of tracking control mobile robots to detect and identify jamming attacks in the form of DoS attacks.
Sharma et al. [
16], proposed the lightweight behavior rule specification method to identify cyber physical attacks in WSNs. The proposed technique uses the communication behavior information of deployed sensor nodes to identify region based jamming attacks in the networks. The key concept of the proposed model was to identify the malicious sensor node in the network based on transmission behavior. Moreover, in the proposed model, an automatic verification process was enabled to continuously check the operational network for jamming attacks. Intrusion detection system (IDS) has been used for a couple of decades to protect networks from external attacks. However, applying traditional and ordinary IDS to WSNs is very difficult, due to its limited resources and dynamic nature. Zarpelao et al. [
17], overviews in their survey the utilization of IDS in WSNs and IoT. Furthermore, he specifically highlight the attacks, where IDS can play an important role in WSNs environment. The attacks that were highlighted in this paper include routing base attacks, IP spoofing attack, DoS attack and DDoS attacks.
The fault detection scheme for an unmanned surface vehicle system (USVS) was proposed by Ma et al. [
18]. The USVS model is based on three phases, which includes event triggering, event base switching and piecewise function to verify the legitimacy of the network traffic and transmission medium. The event based triggering schemes had great importance to detect and prevent jamming attacks in WSNs. Additionally, the USVS scheme uses information such as communication delay and disturbance in communication process to detect jamming attacks. Ge et al. [
19], in their article briefly provided an overview of the existing techniques adopted for prevention of jamming attacks in WSNs. The new resilient based security (NRBS) scheme for prevention of jamming attacks was proposed by Shammari et al. [
20]. In NRBS scheme, the authors used information such as data delivery and power consumption of participating ordinary nodes to detect estimated jamming attack in WSNs.
Lu et al. [
21] proposed the channel training method to identify covert pilot spoofing attacks in WSNs. The channel training scheme was very effective at detecting eavesdropping and routing attacks in WSNs. However, the attack categorization were made on the basis of transmission channel threshold value, which can not be effective in the worst condition of transmission. Therefore, the channel training model was effective in a normal WSNs communication environment, but during external interferences such as weather, fidelity and attenuation, the effectiveness ratio of the proposed model was found to be degraded. Saeed et al. [
22] suggest an intelligent security scheme, which is known as random neural networks (RNNs) to detect jamming attacks in WSNs. The RNN scheme uses an application source instruction to detect malicious activity in the network. Moreover, the tags of application are broadcasted in the proposed model to verify the authenticity and legitimacy of the network traffic.
The non-orthogonal multiple access (NOMA) and Hybrid automatic repeat request (HARQ) scheme was proposed by Xiang et al. [
23]. The combination of NOMA and HARQ were used in the proposed model to enhance the security of deployed WSNs. Jing et al. [
24] briefly provided an overview of the security issues associated with three layers of IoT such as perception, transport and application layer. Moreover, they also suggest possible solutions to address the aforementioned issues in the IoT communication infrastructure. The LAM-CIoT lightweight authentication scheme was proposed by Wazid et al. [
25]. The proposed model was used in a cloud-based IoT infrastructure to ensure the security of a collected date from a sensor at a remote location by means of a one-way cryptographic hash function authentication process. Wazid et al. [
26] proposed the secure key management and user authentication model, which was known as SAKA-FC for fog computing environment to develop a secure communication infrastructure. They used a one-way cryptographic hash function with addition of bitwise-OR (XOR) operation to verify the legitimacy of participating devices in the network. The limitations of the existing literature are briefly summarised in
Table 1.
Limitation of the Literature
WSNs are very sensitive, due to their limited resources and dynamic behavior. Therefore, efficient utilization of these networks increases their productivity and reliability. WSNs consists of hundreds and thousands of wireless nodes, which are susceptible to different kind of attacks, due to their unattended or inaccessible environment. Jamming attack is one of the most damaging attacks to these networks, because it disrupts the communication process of deployed WSNs. The literature suggest various techniques to mitigate jamming attacks on WSNs environment, but most of them are specific to environment, system and software. Some limitations of existing techniques are described below:
Some of the existing schemes in the literature are specific to the system or operation [
15].
Most of the mentioned schemes are complex in their implementation [
13,
14].
Some of the mentioned schemes have a complex authentication process, which generates network overhead [
13,
16].
Some of the mentioned schemes are effective against network attacks, but they are degrading network performance by means packet lost ratio, throughput and latency, etc., [
13,
14].
The solution proposed in this paper is not only efficient in network performance and reliability, but it is also accurate in jamming attack detection and has simple operational deployment.
3. Proposed Methodology: Three Edge Node Scheme
WSNs are deployed in different environment such as sea, forest, agriculture, mountain and health-care etc., where in most of the cases human access is not possible. These networks consist of sensor nodes, which collects information from their surrounding according to their directed tasks. However, these networks are susceptible to various security threats, which can affect their performance. Therefore, the design of a secure communication infrastructure can maximize its effectiveness and performance. WSNs are vulnerable to different security threats such as wormhole attacks, black hole attacks, DoS attacks, DDoS attacks, Sybil attacks and Jamming attacks etc,. Jamming attack is one of the most lurid types of attack for these networks, because it disrupts the communication process of WSNs.
The literature has suggested various schemes to combat jamming attacks in WSNs, but most of them are specific to operation or system, which minimizes their effectiveness in real world deployment. In the presence of existing literature limitations, an efficient three edge nodes scheme is proposed in this research to address the aforementioned issue of jamming attacks in WSNs. The three edge nodes are deployed in designated WSNs infrastructure, where they share the collected information of ordinary nodes with remote destination. Moreover, each edge node has different transmission channels in the same bandwidth, which enables the detection of jamming attacks in the transmission media. Therefore, our proposed model is very effective at detecting jamming attacks in WNS with a great accuracy. Moreover, it also maintains high throughput, minimum end to end delay and least packet lost ratio in the operational network.
To elaborate upon the concept of the proposed model, in this research, three edge nodes are used in the deployed WSN to transmit the collected information of ordinary nodes deployed in WSN topology. All the edge nodes have different transmission channels in our scheme, which they are using to communicate with remote destination. Moreover, all edge nodes (in our case three) have embedded built-in configuration to calculate the estimated RTT of a message packet and transmit the calculated value of RTT in message payload to remote destination. At remote destination, once the message packet is received, the estimator again calculate the value of RTT. After calculation of RTT at a remote location, the source message estimated time and remote location RTT is compared to maintain the reliability of the network and high quality detection of malicious activity.
To elaborate upon the concept of proposed model, the step by step process is shown in a flowchart diagram.
Figure 1 of the paper shows the step by step implementation process of this research.
The above flowchart diagram of
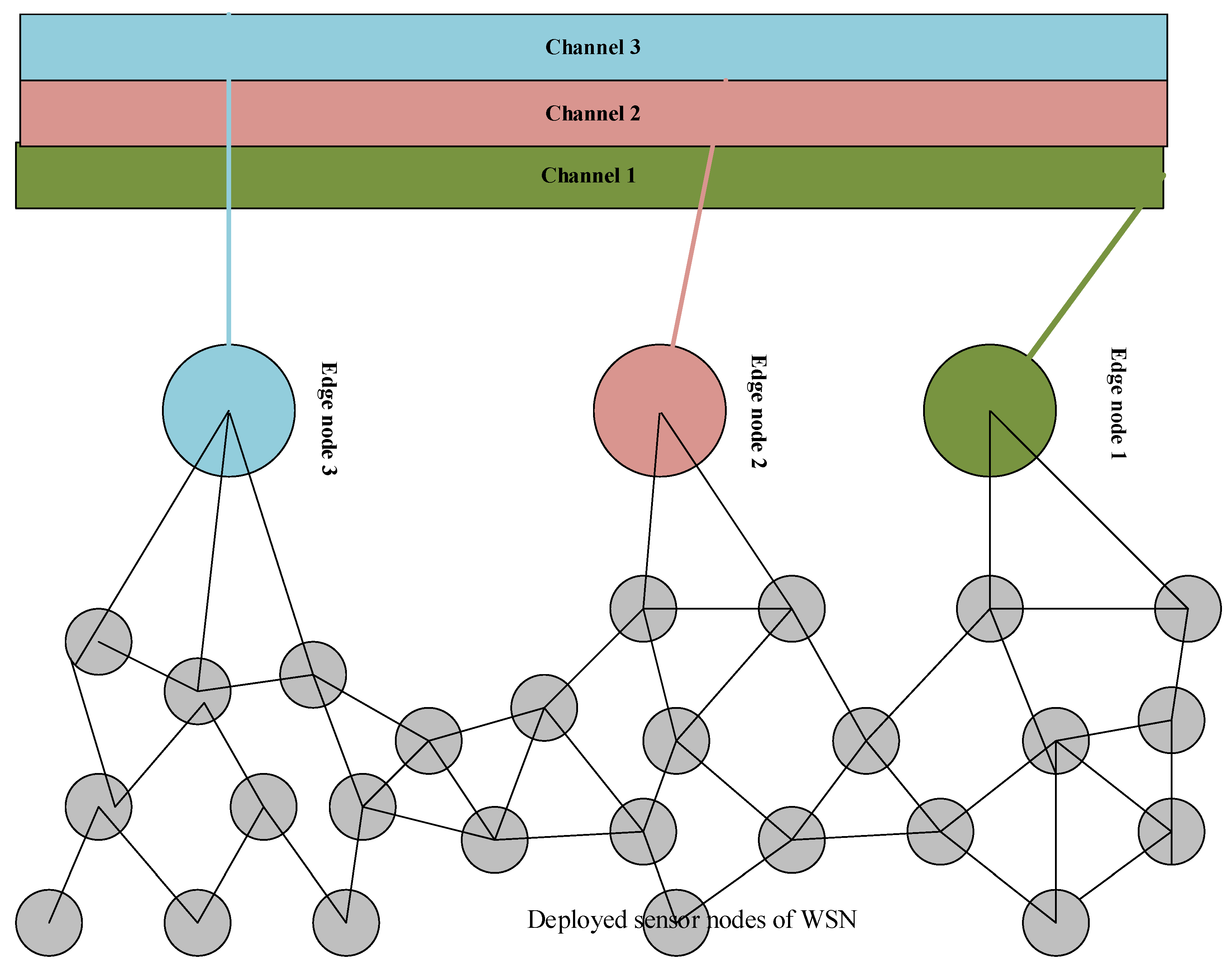
Figure 1 represents the complete overview of our proposed model. An ordinary network of a dynamic number of wireless nodes had been chosen with three edge nodes. Each edge node (
) with unique ID has a different frequency channel in the same frequency band. Likewise, the edge node transmits the collected information of deployed sensor network over the transmission media to a remote destination. However, each edge node has different transmission channel to transmit information from source to the destination location.
Additionally, each edge node at a time of transmission calculates the estimated RTT of every packet. Similarly, after reception of packets at a remote location, the estimated RTT is again calculated for each incoming packet. After calculation, the estimated RTTs are compared to verify the legitimacy of network traffic. However, the traffic legitimacy parameter is set for RTT with a threshold value of 15 s. In the normal environment of WSNs, all incoming packet have less than 15 s time RTT after comparison at a remote location. In case of interference in the communication channel, which we call malicious activity in the network, the value of RTT is increased from defined threshold value, which indicates the existence of external interference in the network. Similarly, if any incoming packet cross the threshold value of RTT, which is 15 s, then this is the indication of a malicious activity in the network.
To elaborate upon the concept of RTT, in the ordinary communication condition, the RTT delay is less than 15 s in our scheme. If, after comparison the RTT delay is more than 15 s, then there is something wrong in the transmission media. Therefore, at remote locations, the same incoming frequency channel is kept under observation for 3 consecutive incoming packets. If all the incoming packets (3 consecutive packets) do not satisfy the estimated RTT condition of comparison (for source and destination RTT), an alarm message is broadcast, which is the indication of estimated jamming in the network. Moreover, every transmitted packet payload contain information such as ID, RTT, source and destination address, which make the communication process transparent in our scheme. Similarly, this is very helpful to identify the under attacks channel or edge node during operational network. Consequently, the communication of the channel under attack is completely unavailable at remote locations. In this case, the RTT importance is increased, because the channels adjacent to the channel under attack are also disturbed, due to high frequency interference, which disturbs the consistency of RTT during comparison. So the estimated RTT also ensures the existence of an estimated jamming attack in the adjacent channel. This is because the adjacent channels’ frequency is also effected with the attacking channel by means of high frequency interference. The RTT of the adjacent channels is calculated at the destination. The consistency of RTT will be found to be effected, which we have discussed in this paper.
Figure 2 of the paper represents the channel categorization of our scheme. The figure shows how the edge nodes collect information from deployed wireless nodes in the WSN infrastructure. Furthermore, the channel categorization is shown with different colors, according to edge node color, which explains the concept of our scheme. The edge nodes collects information form from deployed wireless nodes and forwards it to the specified transmission channel. Likewise, the specified channel transmits this information to remote locations. Moreover, the edge node (
) first calculates the estimated RTT.
In communication, RTT is very important to determine the accomplishment of connection. Moreover, in wireless networks RTT is profitable and efficient to measure retransmission time, window size and available bandwidth in transmission medium [
27].
The RTT of a message packet can be calculated by the following Equations (
1) and (
2).
The above mentioned formula is used to calculate the RTT at edge node (
).
In the equation, is the constant weight factor.
In Equation (
1), the current RTT represents destination node, while the new RTT represents the new incoming packets. This is used for RTT comparison at remote sites. Moreover, to elaborate upon the concept of Equation (
1), after reception of the message packet at remote destinations, the value of RTT is again calculated by following the same formula for each incoming packet. After calculation, the value of RTT is compared with source RTT value for each edge node. If they match, the communication process is continued in a smooth manner. However, if they did not match then the RTT value for an incoming packet is checked with time parameter, which is less than 15
s for a legitimate incoming packet. If it exceeds the defined limit of 15
s, then the incoming packets are consecutively seen for 3 RTT comparison. If the still do not match with the defined interval of time, then an alarm message is broadcast in the network to acknowledge the existence of tampering with the channel.
The RTT mainly depends on the sensor nodes’ presence in their round trip path and distance. The accuracy of RTT can be improved by reducing the number of sensor nodes present in the path of RTT. Our scheme is quite accurate by means of RTT calculation, because we have only two nodes involved in the communication process.
So the RTT for two sensor nodes is given by:
In Equation (
2),
represents the delay from source node (
) and destination node (
). where
= (
,
,
).
The edge nodes are almost at the same distance from the node.
As a result of equal distance, , and are all equal.
So = = =
All the
have uniform RTT delay. Therefore, for the paired sensor nodes (
&
), RTT delay is obtained by Equation (
3). Referring to Equation (
2)
This is the minimum RTT for a pair of sensors to exchange message packets in the operational WSNs. When under attack, the edge node () or channel can be identified by comparing the specific RTT values.
Let us assume that the communication channel is established among ((
) and
)), which is represented by (
M) in the given Equation.
In Equation (
4), C represents the number of channels used for communication. The analysis time required to calculate all
nodes with RTT in the WSNs needs to be obtained. Therefore, the equation for analysis time of channel (C) is obtained and given by Equation (
5).
Referring to Equation (
3), the optimal value of RTT for channel (C) is obtained by considering only two nodes (
&
).
So, the obtained equation verifies the legitimacy, while calculating RTT for & .
Theorem 1. An edge node exchange data with remote destination (). If node is <15 s at . Accept, else, observe and broadcast alarm.
Proof of Theorem 1. Let us suppose that the edge node calculates the estimated RTT time for the packet at the source end in the network. After calculating the RTT time, the node transmits the packet in the network through the specified frequency channel. After reception of the packet at destination (), the estimator again calculates the estimated value of RTT for incoming packet. If the calculated value of RTT for the incoming packet matches the () RTT value, both the values are matched. □
Hence, the communication of is legitimate and the estimator at the destination allows the packet to be further processed.
Conversely, the RTT might not match the RTT time. Then, the estimator will deny the incoming packet and look for three packets to verify the legitimacy of the traffic.
Therefore, the afore-stated theorem verifies that only and matched estimated RTT values packets are allowed to communicate in the network.
Algorithm 1 of the paper comprehensively overviews the step by step process of the RRT time calculation of our proposed scheme, which is adopted for the calculation of legitimate traffic in the network. Let us assume that an Edge node
initiates the communication process with a destination location/node. The
calculates the RRT time of the packet before its transmission (
). Once the packet is transmitted through a communication channel, it contains all the necessary information such as source address, destination address and RRT time. Then the said packet is received at the destination location (
). The RRT time is again calculated and its value is matched with source packet RRT, if the time interval is <15
s. Then the incoming packet allows for further communication in the network. If the incoming packet time interval is >15
s, then 3 packets of the same source node are seen. If all three consecutive packets do not satisfy the defined interval of time (RRT) then an alarm message is broadcast on the network to acknowledge the existence of malicious activity.
| Algorithm 1 Legitimate traffic identification through RTT estimation |
| Require: Allow only legitimate traffic, they have matched values of and RTT. |
| Ensure: and RTT time matching. |
- 1:
initiate the process - 2:
Calculates ⟼ Estimated at source side - 3:
compile ← - 4:
transmit ← through their frequency - 5:
Estimator ← at remote location (recalculate RTT of ) - 6:
matches RTT values of ← - 7:
If - 8:
& RTT values matches ← Accept - 9:
- 10:
Checks for 3 consecutive packets - 11:
Deny after verification - 12:
← allow network traffic of - 13:
end if - 14:
return Current information of specific node, traffic and channel.
|
3.1. Packets Lost Ratio in the Channel: Based on RTT
In the proposed model, the communication among sensor nodes and remote location (estimator) is through a wireless channel. We know that the unreliability of wireless medium means that there is more packet loss in the transmission process. Moreover, the packet loss process in this research process is defined through a random binary process , where “A” is the RTT time. Likewise, in the proposed model, if the value of i = 1 at a remote destination (estimator), then the estimator or remote destination allows the traffic to be further processed. Conversely, if the value of i = 0, then the packets are lost in the communication process (channel) and the estimator looks for more incoming packets (at least 3 packets). Hence, the remote state estimator or destination fails to forward the incoming packets.
3.2. Jamming Attack: Based on RTT
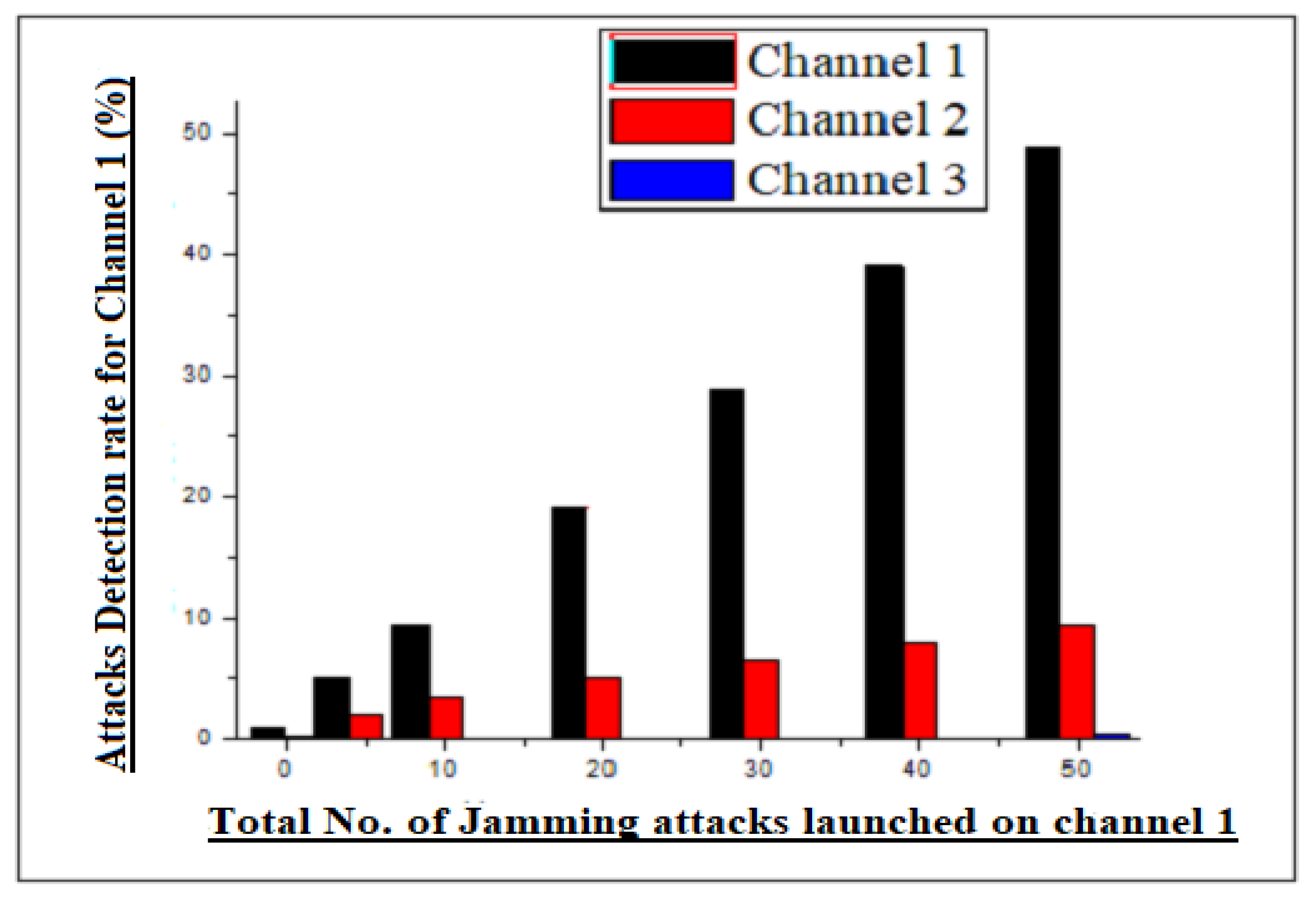
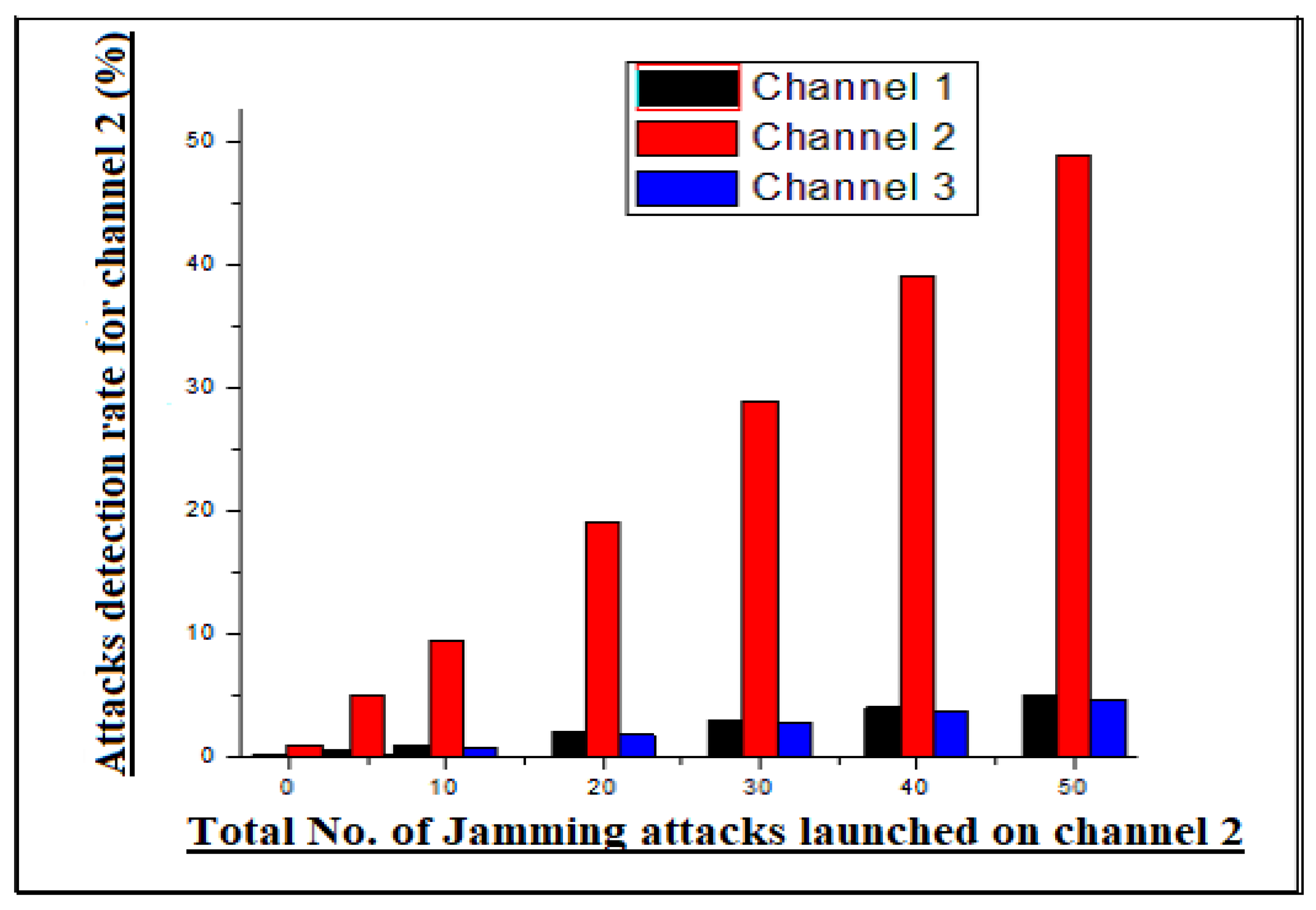
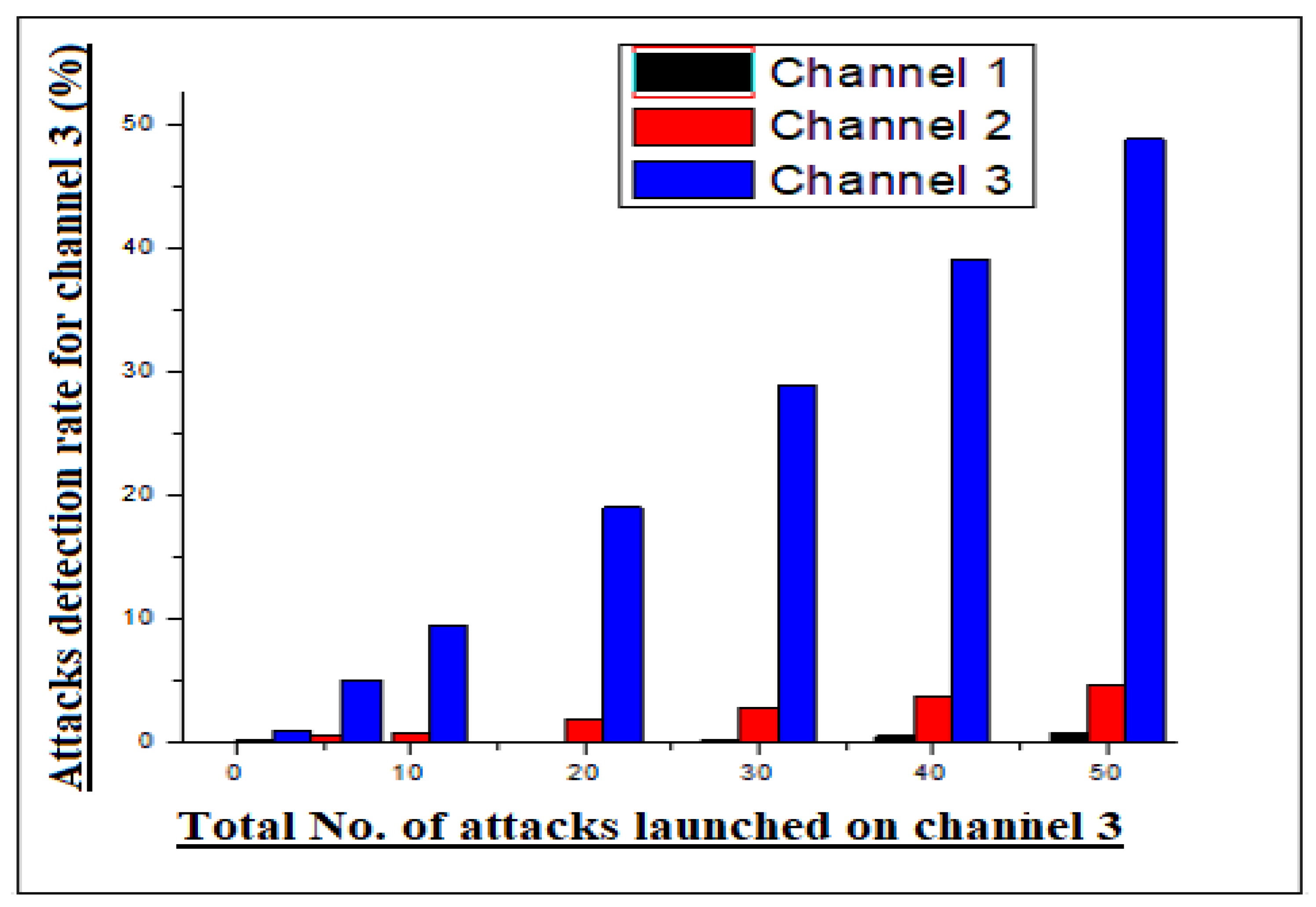
Let us assume that an attacker wants to launch a jamming attack on the deployed network. The attacker has the capabilities to conduct the jamming attacks on the transmission media (transmission channel) and jam network traffic. However, the jamming of channel disrupts the communication process of edge node and remote destination/estimator, which causes dropout data packets in the process. The 3 edge nodes of the network send their data on different frequency channels when the attacker jams one frequency channel, because the other two channels are working. Likewise, the attacker is not blocking all channels at the same time in the network, so the other two channels help to identify the estimated jamming attack on the network. Moreover, the detection of jamming attacks is identified through the model shown below. A variable
was chosen, variable
i is the number of channels and t is the time. The channels are furthermore represented by the given statement as
i = 1, 2, 3 and
t = 0. As we discussed, only one channel, and in extreme cases two channels, can be blocked by an attacker at a given time. Keeping this in mind, when the attacker jams one or two channels in time
t, then
where
i = 1, 2, 3. likewise, when the attacker blocks two channels, then
= 2, etc.