P4UIoT: Pay-Per-Piece Patch Update Delivery for IoT Using Gradual Release
Abstract
1. Introduction
2. Related Work
2.1. General Architectures for IoT Patching
2.2. Decentralized Storage Networks
3. Security Model
3.1. Threat Model
3.2. Adversarial Model
3.3. Security Goals
4. Preliminary
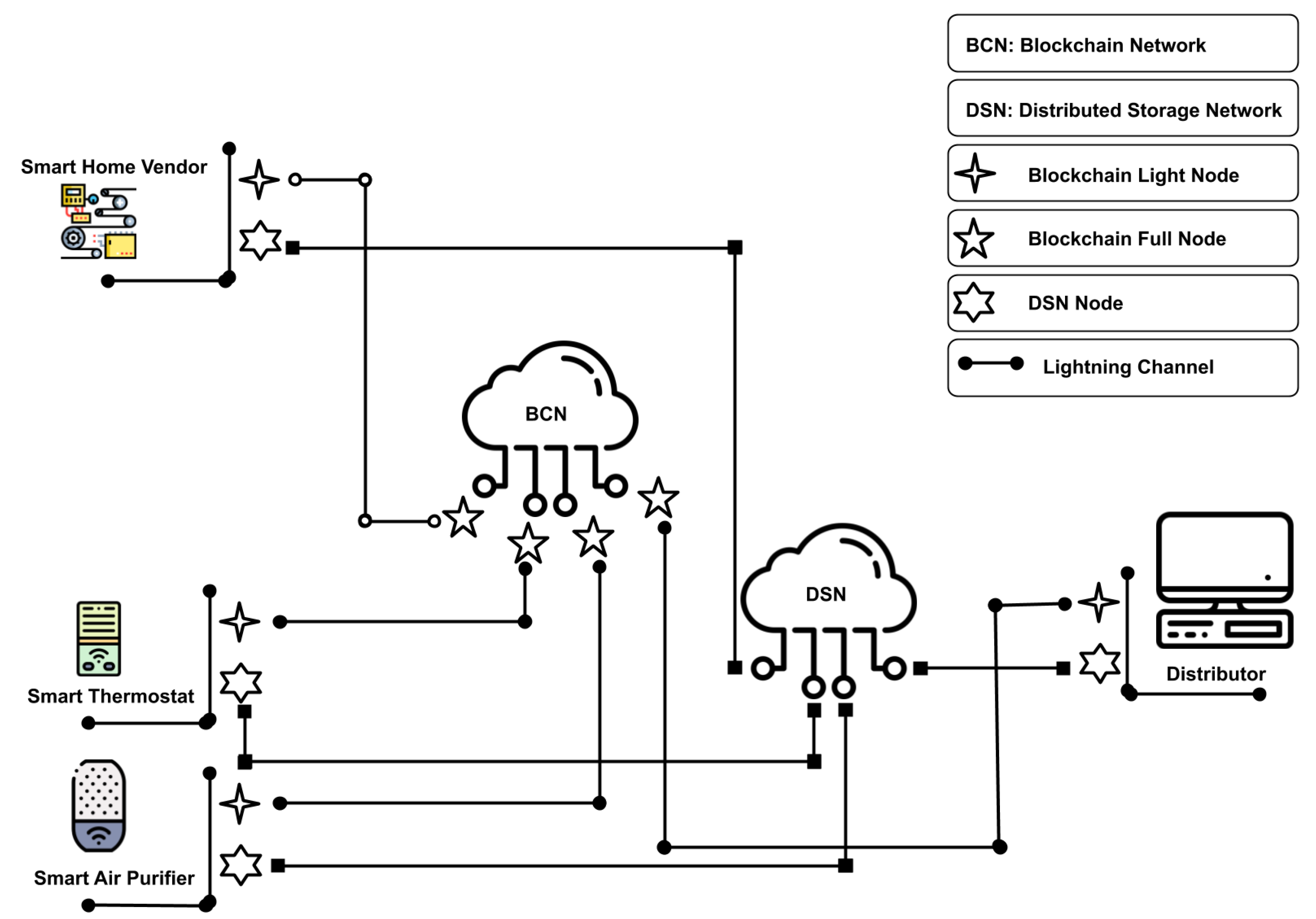
4.1. Decentralized Storage Network (DSN)
4.2. Blockchain Network
4.3. Vendor Nodes
- a pair of public and private keys .
- a collection of IoT device identities. This can be achieved by configuring a private key to each device and accumulating the corresponding public keys.
4.4. IoT Nodes
- a pair of public and private keys ;
- public key of its vendor node, .
4.5. Distributor Nodes
5. Pay-Per-Piece Patch Update
- Patch size limitations: the IoTPatchPool [30] framework relies on the ZKCP protocol, which is limited in its current implementation for 55 kB.
- Network overhead: in addition to the patch update itself, the former framework requires the sending of additional data in the form of ZKsnarks proving and verification keys; in some cases, it is a hundred folds bigger than the patch file itself.
- Demands for IoT devices: in the ZCKP protocol, the IoT devices need to verify the ZKsnarks statement, and also, there is a need to decrypt the patch binaries once the decryption key is revealed. These two operations are having additional demands on the device storage memory and processing power.
- Costs: the former network is a first layer solution on the blockchain network. To reduce costs, new methods of offering payment to the distributors should be used.
- Schnorr Signatures were introduced to the Bitcoin network in [52]. Given n signatures on n distinct messages from n distinct users, it is possible to aggregate all these signatures into a single short signature. The tests conducted show a significant speedup. The ratio between the time it takes to verify n signatures individually and to verify a batch of n signatures goes up logarithmically with the number of signatures or, in other words: the total time to verify n signatures grows with .
- ECDSA Elliptic Curve Digital Signature Algorithm [53] is one of the main building blocks of the Bitcoin network, and it is used for verifying all the transactions. Reviewing all the possibilities, the ECDSA alternative was chosen for its low costs and lack of demand for preliminary online setup between signers. It is important to notice that choosing ECDSA will allow this framework to be scalable as the blockchain ledger itself is making additional improvements in scalability to be applied to this framework.
5.1 Protocol
5.1.1. Initial Setup
5.1.2. Bid Commitment
5.1.3. Initiating Patch Update Seeding
- Computes the hash of patch file
- Sets N as the total count of IoTs
- Sets M as the total count of pieces
- Prepares the payload as: , where is represented as an ordered list of the IoT devices public keys
- Computes the hash of the payload
- Sets as sufficient time for vendor V to seed the patch
- Emits an event announcing the availability of patch update.
- Corresponding to the hash , the distributor requests vendor V for the payload via the DSN network.
- The vendor V begins the seeding of the payload P using the DSN network. The vendor seeds the payload P for a reasonable time within which some distributor can receive the update.
- After completely downloading the package P, verifies that:
- the patch is published by the vendor.
- the integrity of the patch is maintained throughout the communication.
- then announces via DHT to its peers as a possible source of the patch update.
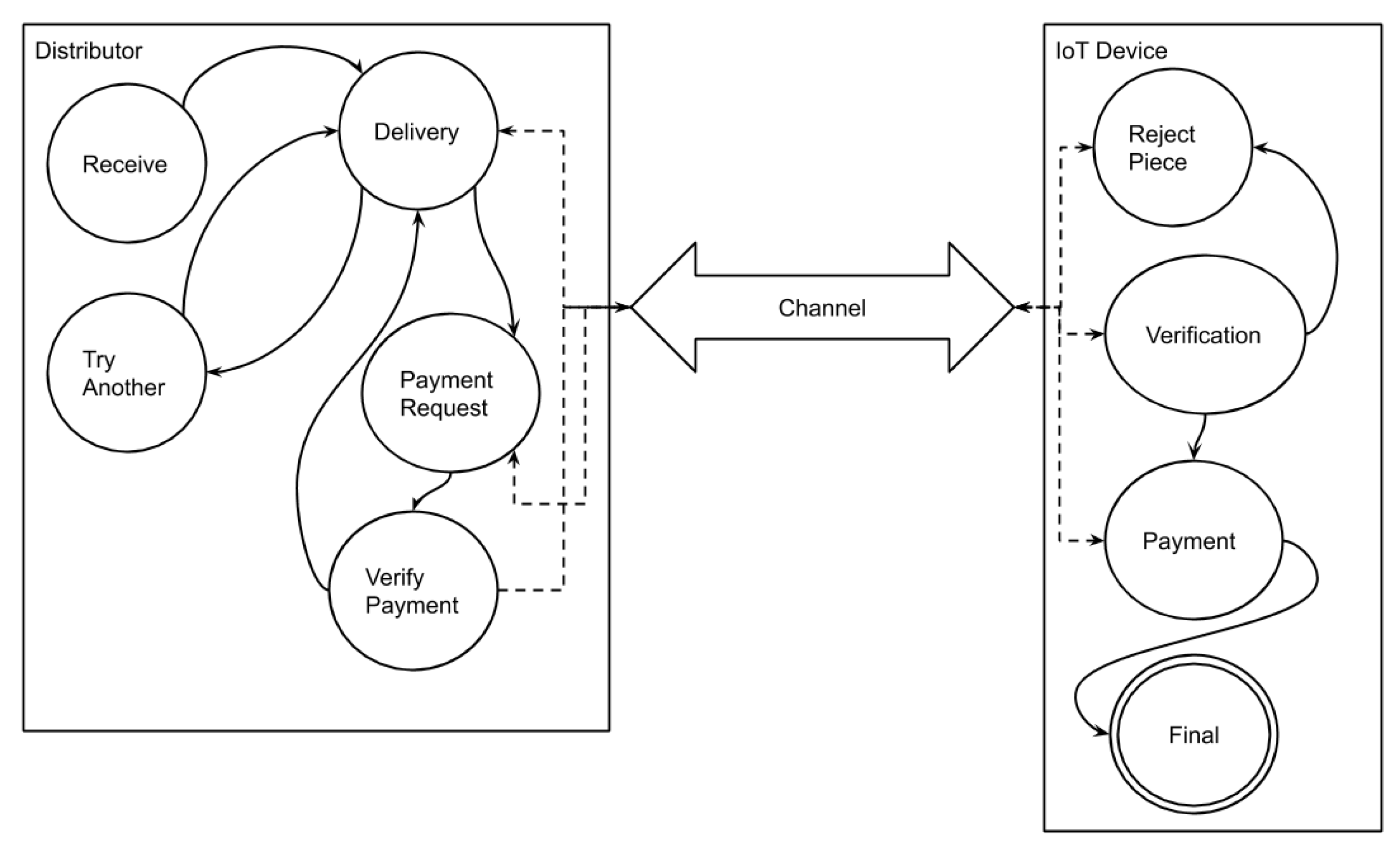
5.1.4. Exchange
- The patch update available event is received by the IoT device , and the device verifies the sender of the event.
- The device searches for distributor possessing of the patch update via the DHT peer discovery. Once found, the device sends the download request to the distributor .
- sends a random nonce c, a challenge, to to sign on.
- :
- Computes .
- Sends the tuple to k.
- In this stage, the IoT device can start downloading pieces from any free providing distributors (i.e., the vendor node).
- :
- Verifies that
- Verifies that
- Piece by piece exchange:
- sends the requested j part of the patch file
- concats = and sends to
- sends part to
- chokes further transfer till the payment for the part is received.
5.1.5. Reward Claiming
- :
- once the piece is received, sends the payment of the piece to .
- once received the payment, it sends the next piece and waits for payment.
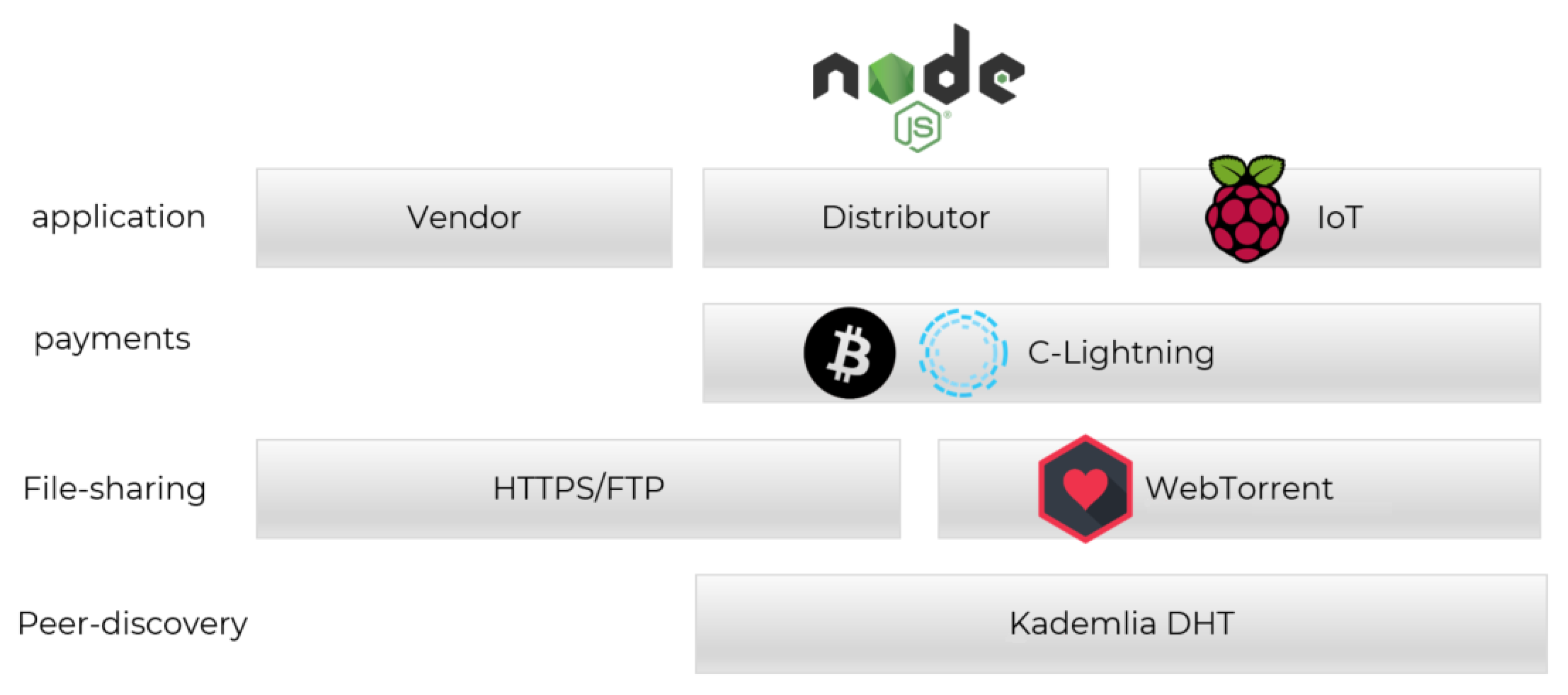
6. Implementation
7. Formal Specification
7.1. State Transitions
- the entry condition, and
- the variable changes
7.2. Vendors
7.3. Distributors
7.4. IoT Devices
7.5. Terminating
8. Evaluation
8.1. Model Checking with Correctness Properties
8.2. Threat Analysis
8.3. Properties
- Fair exchange: The protocol construction is based on first delivering the piece from the distributor to the IoT device and, in return, receiving the signature assuring the reward claim via the lightning network. In the protocol, the distributor can be listed on the DSN by first downloading the patch and hashing the file into an address, meaning that the distributor holds the patch binaries ready to deliver. Each piece in the torrent protocol is hashed and can be verified by the receiver. In the case of delivering false pieces from the distributor to the IoT device, the IoT will validate the piece against the hash and confirm its validity.The second phase is IoT signing the requested message. In this construction, the distributor can validate the signature only after receiving the signature, thus, putting himself in risk and will be compromising a fraction of the reward once per IoT lifetime. Since this phase starts only after validating the IoT public address in the handshake phase, the distributor can hold a blacklist of IoT, making it protected the next time the IoT requests a piece. In the transitional construction of the gradual release, both parties should have the same computational power to eliminate the ability of one party to abort between rounds and brute force the remaining information In this protocol, the availability of the piece is from multiple sources, eliminating the incentive of one party to redraw from the transfer.
- Patch integrity: The patch update file hash is listed in the BitTorrent protocol header. This, along with the use of a collision-free hash function patch, will lose its integrity with insignificant probability.
- Patch availability: In PUIoT, the initial seed of the vendor is used throughout the process. The decentralized storage and Bitcoin network with the seed mentioned above ensures that at least one distributor can complete the file download, and thus, further ensures the availability of the patch update.
8.4. Execution Results
9. Conclusions
Author Contributions
Funding
Conflicts of Interest
References
- Laurence, G. Gartner Says 5.8 Billion Enterprise and Automotive IoT Endpoints Will Be in Use in 2020. Available online: https://www.gartner.com/en/newsroom/press-releases/2019-08-29-gartner-says-5-8-billion-enterprise-and-automotive-io (accessed on 24 January 2020).
- Christo, P. Internet Of Things Statistics 2020 [The Rise Of IoT]. Available online: https://techjury.net/stats-about/internet-of-things-statistics/#gref (accessed on 24 January 2020).
- Darina, L. IoT Statistics and Trends to Know in 2020. Available online: https://leftronic.com/internet-of-things-statistics/ (accessed on 24 January 2020).
- Statista Research Department. Internet of Things—Number of Connected Devices Worldwide 2015–2025. Available online: https://www.statista.com/statistics/471264/iot-number-of-connected-devices-worldwide/ (accessed on 24 January 2020).
- Antonakakis, M.; April, T.; Bailey, M.; Bernhard, M.; Bursztein, E.; Cochran, J.; Durumeric, Z.; Halderman, J.A.; Invernizzi, L.; Kallitsis, M.; et al. Understanding the mirai botnet. In Proceedings of the 26th {USENIX} Security Symposium ({USENIX} Security 17), Vancouver, BC, Canada, 16–18 August 2017; pp. 1093–1110. [Google Scholar]
- Ronen, E.; Shamir, A.; Weingarten, A.O.; O’Flynn, C. IoT goes nuclear: Creating a ZigBee chain reaction. In Proceedings of the 2017 IEEE Symposium on Security and Privacy (SP), San Jose, CA, USA, 22–26 May 2017; pp. 195–212. [Google Scholar]
- Fernandes, E.; Jung, J.; Prakash, A. Security analysis of emerging smart home applications. In Proceedings of the 2016 IEEE Symposium on Security and Privacy (SP), San Jose, CA, USA, 22–26 May 2016; pp. 636–654. [Google Scholar]
- Andrey, M.; Vladimir, D.; Roland, S. IoT Hack: How to Break a Smart Home… Again. Available online: https://securelist.com/iot-hack-how-to-break-a-smart-home-again/84092/ (accessed on 26 January 2020).
- Lily, N. An eLaborate Hack Shows How Much Damage Iot Bugs Can Do. Available online: https://www.wired.com/story/elaborate-hack-shows-damage-iot-bugs-can-do/ (accessed on 26 January 2020).
- Williams-Grut, O. Hackers Once Stole a Casino’S High-Roller Database Through a Thermometer in the Lobby Fish Tank; Business Insider: New York, NY, USA, 2018. [Google Scholar]
- Check Point. The Dark Side of Smart Lighting: Check Point Research Shows How Business and Home Networks Can Be Hacked from a Lightbulb. Available online: https://blog.checkpoint.com/2020/02/05/the-dark-side-of-smart-lighting-check-point-research-shows-how-business-and-home-networks-can-be-hacked-from-a-lightbulb/ (accessed on 28 January 2020).
- Wang, Q.; Hassan, W.U.; Bates, A.; Gunter, C. Fear and Logging in the Internet of Things. In Proceedings of the Network and Distributed Systems Symposium, San Diego, CA, USA, 18–21 February 2018. [Google Scholar]
- Fernandes, E.; Paupore, J.; Rahmati, A.; Simionato, D.; Conti, M.; Prakash, A. Flowfence: Practical data protection for emerging iot application frameworks. In Proceedings of the 25th {USENIX} Security Symposium ({USENIX} Security 16), Austin, TX, USA, 10–12 August 2016; pp. 531–548. [Google Scholar]
- He, W.; Golla, M.; Padhi, R.; Ofek, J.; Dürmuth, M.; Fernandes, E.; Ur, B. Rethinking access control and authentication for the home internet of things (IoT). In Proceedings of the 27th {USENIX} Security Symposium ({USENIX} Security 18), Baltimore, MD, USA, 15–17 August 2018; pp. 255–272. [Google Scholar]
- Jia, Y.J.; Chen, Q.A.; Wang, S.; Rahmati, A.; Fernandes, E.; Mao, Z.M.; Prakash, A.; Unviersity, S.J. ContexloT: Towards Providing Contextual Integrity to Appified IoT Platforms. In Proceedings of the NDSS, San Diego, CA, USA, 26 February–1 March 2017. [Google Scholar]
- Bruce, S. E-Mail Vulnerabilities and Disclosure. Available online: https://www.schneier.com/blog/archives/2018/06/e-mail_vulnerab.html (accessed on 26 January 2020).
- Schooler, E.M.; Zage, D.; Sedayao, J.; Moustafa, H.; Brown, A.; Ambrosin, M. An architectural vision for a data-centric iot: Rethinking things, trust and clouds. In Proceedings of the 2017 IEEE 37th International Conference on Distributed Computing Systems (ICDCS), Atlanta, GA, USA, 5–8 June 2017; pp. 1717–1728. [Google Scholar]
- Abbas, N.; Zhang, Y.; Taherkordi, A.; Skeie, T. Mobile edge computing: A survey. IEEE Internet Things J. 2017, 5, 450–465. [Google Scholar] [CrossRef]
- David, R. Hundreds of Enterprise Services Reportedly Hit by AWS Outage. Available online: https://virtualizationreview.com/articles/2018/03/05/aws-outage.aspx (accessed on 28 January 2020).
- Gnutella. Gnutella Protocol Specification 0.4. Available online: http://rfc-gnutella.sourceforge.net/developer/stable/ (accessed on 28 January 2020).
- Benet, J. Ipfs-content addressed, versioned, p2p file system. arXiv 2014, arXiv:1407.3561. [Google Scholar]
- Cohen, B. Incentives build robustness in BitTorrent. In Proceedings of the Workshop on Economics of Peer-to-Peer systems, Berkeley, CA, USA, 17–19 June 2003; pp. 1–5. [Google Scholar]
- Tom, W. Microsoft to Deliver Windows 10 Updates Using Peer-to-Peer Technology. Available online: https://www.theverge.com/2015/3/15/8218215/microsoft-windows-10-updates-p2p (accessed on 28 January 2020).
- Ernesto, V. Bittorrent Makes Twitter’S Server Deployment 75x Faster. Available online: https://torrentfreak.com/bittorrent-makes-twitters-server-deployment-75-faster-100716/ (accessed on 28 January 2020).
- Kreitz, G.; Niemela, F. Spotify–large scale, low latency, P2P music-on-demand streaming. In Proceedings of the 2010 IEEE Tenth International Conference on Peer-to-Peer Computing (P2P), Delft, The Netherlands, 25–27 August 2010; pp. 1–10. [Google Scholar]
- Amazon. Using BitTorrent with Amazon S3. Available online: https://docs.aws.amazon.com/AmazonS3/latest/dev/S3Torrent.html (accessed on 28 January 2020).
- Lee, B.; Lee, J.H. Blockchain-based secure firmware update for embedded devices in an Internet of Things environment. J. Supercomput. 2017, 73, 1152–1167. [Google Scholar] [CrossRef]
- Boudguiga, A.; Bouzerna, N.; Granboulan, L.; Olivereau, A.; Quesnel, F.; Roger, A.; Sirdey, R. Towards better availability and accountability for iot updates by means of a blockchain. In Proceedings of the 2017 IEEE European Symposium on Security and Privacy Workshops (EuroS&PW), Paris, France, 26–28 April 2017; pp. 50–58. [Google Scholar]
- Lee, J. Patch transporter: Incentivized, decentralized software patch system for WSN and IoT environments. Sensors 2018, 18, 574. [Google Scholar] [CrossRef] [PubMed]
- Leiba, O.; Bitton, R.; Yitzchak, Y.; Nadler, A.; Kashi, D.; Shabtai, A. IoTPatchPool: Incentivized delivery network of IoT software updates based on proofs-of-distribution. Pervasive Mob. Comput. 2019, 58, 101019. [Google Scholar] [CrossRef]
- Poon, J.; Dryja, T. The Bitcoin Lightning Network: Scalable Off-Chain Instant Payments. 2016. Available online: https://lightning.network/lightning-network-paper.pdf (accessed on 28 January 2020).
- Lamport, L. Specifying Systems: The TLA+ Language and Tools for Hardware And Software Engineers; Addison-Wesley Longman Publishing Co., Inc.: Boston, MA, USA, 2002. [Google Scholar]
- Liu, K.; Zou, D.; Jin, H. Uaas: Software update as a service for the iaas cloud. In Proceedings of the 2015 IEEE International Conference on Services Computing, New York, NY, USA, 27 June–2 July 2015; pp. 483–490. [Google Scholar]
- Xiong, Z.H.; Yang, Y.Z. Automatic updating method based on Maven. In Proceedings of the 2014 9th International Conference on Computer Science & Education, Vancouver, BC, Canada, 22–24 August 2014; pp. 1074–1077. [Google Scholar]
- Yu, T.; Sekar, V.; Seshan, S.; Agarwal, Y.; Xu, C. Handling a trillion (unfixable) flaws on a billion devices: Rethinking network security for the internet-of-things. In Proceedings of the 14th ACM Workshop on Hot Topics in Networks, Philadelphia, PA, USA, 16–17 November 2015; pp. 1–7. [Google Scholar]
- Onuma, Y.; Terashima, Y.; Kiyohara, R. ECU software updating in future vehicle networks. In Proceedings of the 2017 31st International Conference on Advanced Information Networking and Applications Workshops (WAINA), Taipei, Taiwan, 27–29 March 2017; pp. 35–40. [Google Scholar]
- Huth, C.; Duplys, P.; Güneysu, T. Secure software update and IP protection for untrusted devices in the Internet of Things via physically unclonable functions. In Proceedings of the 2016 IEEE International Conference on Pervasive Computing and Communication Workshops (PerCom Workshops), Sydney, NSW, Australia, 14–18 March 2016; pp. 1–6. [Google Scholar]
- Kim, D.Y.; Kim, S.; Park, J.H. Remote software update in trusted connection of long range IoT networking integrated with mobile edge cloud. IEEE Access 2017, 6, 66831–66840. [Google Scholar] [CrossRef]
- Popov, S. The Tangle. White Paper. 2017. Available online: https://iota.org/IOTA_Whitepaper.pdf (accessed on 26 January 2020).
- Adar, E.; Huberman, B.A. Free riding on Gnutella. Available online: https://www.hpl.hp.com/research/idl/papers/gnutella/gnutella.pdf (accessed on 26 January 2020).
- Hughes, D.; Coulson, G.; Walkerdine, J. Free riding on Gnutella revisited: The bell tolls? IEEE Distrib. Syst. Online 2005, 6, 8655317. [Google Scholar] [CrossRef]
- Kaune, S.; Rumin, R.C.; Tyson, G.; Mauthe, A.; Guerrero, C.; Steinmetz, R. Unraveling bittorrent’s file unavailability: Measurements and analysis. In Proceedings of the 2010 IEEE Tenth International Conference on Peer-to-Peer Computing (P2P), Delft, The Netherlands, 25–27 August 2010; pp. 1–9. [Google Scholar]
- Vorick, D.; Champine, L. Sia: Simple Decentralized Storage. Available online: https://sia.tech/sia.pdf (accessed on 26 January 2020).
- Wilkinson, S.; Boshevski, T.; Brandoff, J.; Buterin, V. Storj a Peer-to-Peer Cloud Storage Network. Available online: https://storj.io/storj2014.pdf (accessed on 26 January 2020).
- Viktor, T. Swarm Alpha Public Pilot and the Basics of Swarm. Available online: https://blog.ethereum.org/2016/12/15/swarm-alpha-public-pilot-basics-swarm/ (accessed on 28 January 2020).
- Protocol Labs. Filecoin: A Decentralized Storage Network. Available online: https://filecoin.io/filecoin.pdf (accessed on 28 January 2020).
- Miller, A.; Bentov, I.; Bakshi, S.; Kumaresan, R.; McCorry, P. Sprites and state channels: Payment networks that go faster than lightning. In Proceedings of the International Conference on Financial Cryptography and Data Security, Frigate Bay, St. Kitts and Nevis, 18–22 February 2019; pp. 508–526. [Google Scholar]
- Phillip, J.W. An Overview of Self-Sovereign Identity: The Use Case at the Core of Hyperledger Indy. Available online: https://www.hyperledger.org/blog/2019/05/01/an-overview-of-self-sovereign-identity-the-use-case-at-the-core-of-hyperledger-indy (accessed on 28 January 2020).
- Dolev, D.; Yao, A. On the security of public key protocols. IEEE Trans. Inf. Theory 1983, 29, 198–208. [Google Scholar] [CrossRef]
- Baumgart, I.; Mies, S. S/kademlia: A practicable approach towards secure key-based routing. In Proceedings of the 2007 International Conference on Parallel and Distributed Systems, Hsinchu, Taiwan, 5–7 December 2007; pp. 1–8. [Google Scholar]
- Nakamoto, S.; Bitcoin, A. A Peer-to-Peer Electronic Cash System. Available online: https://bitcoin.org/bitcoin.pdf (accessed on 26 January 2020).
- Wuill, P.; Nick, J.; Ruffing, T. Schnorr Signatures for secp256k1. Available online: https://github.com/sipa/bips/blob/bip-schnorr/bip-schnorr.mediawiki (accessed on 28 January 2020).
- Johnson, D.; Menezes, A.; Vanstone, S. The elliptic curve digital signature algorithm (ECDSA). Int. J. Inf. Secur. 2001, 1, 36–63. [Google Scholar] [CrossRef]
- Imem, A.A. Comparison and evaluation of digital signature schemes employed in NDN network. arXiv 2015, arXiv:1508.00184. [Google Scholar]
- Lu, T.; Merz, S.; Weidenbach, C. Towards verification of the pastry protocol using TLA+. In Formal Techniques for Distributed Systems; Springer: Berlin, Germany, 2011; pp. 244–258. [Google Scholar]


| Reference | Type | Distributed/Centralized | Incentives | Trust (Fair Exchange) | Scaling | Solution D, I, or S | Comment |
|---|---|---|---|---|---|---|---|
| Yu et al. (2015) [35] | IoT Patching | Centralized | – | – | – | D + I | Centralized IoT security via antivirus and patching. |
| Onuma et al. (2017) [36] | General | Centralized | – | – | – | D + I + S | Reduction in update latency using divide and distribute. |
| Huth et al. (2016) [37] | IoT Patching | Centralized | – | – | – | D + I + S | Secure software patch update in IoT using Physically Unclonable Functions. |
| Kim et al. (2017) [38] | IoT Patching | Centralized | – | – | – | D + I + S | Secure software patch delivery using Cloud. |
| Lee et al. (2017) [27] | IoT Patching | Distributed (Bitcoin Network) | – | – | – | D | distributed storage network and blockchain-based patch delivery framework. |
| Boudguiga et al. (2017) [28] | IoT Patching | Distributed (Multichain Network) | – | – | – | D + I | distributed storage network and blockchain-based patch delivery framework with trusted verifier. |
| Lee et al. (2018) [29] | IoT Patching | Distributed (Ethereum Network) | Eth | – | – | D + I + S | distributed storage network and blockchain-based incentivized patch delivery framework. |
| Popov (2017) [39] | General | Distributed (DAG Tangle) | IOTA | – | X | D + I + S | Incentivized distributed storage network. |
| Cohen (2003) [22] | General | Distributed (BitTorrent Network) | – | – | X | D + I + S | Incentivized distributed storage network with fair exchange. |
| Siacoin (2014) [43] | General | Distributed (Sia Network) | Siacoin | X | X | D + I + S | Incentivized distributed storage network. |
| Storj (2014) [44] | General | Distributed (Storj Network) | STORJ | – | X | D + I + S | Incentivized distributed storage network. |
| Swarm (2016) [45] | General | Distributed (Ethereum Network) | Eth | – | X | D | Incentivized distributed storage network. |
| Filecoin (2017) [46] | General | Distributed (Filecoin Network) | Filecoin | – | X | D + I | Incentivized distributed storage network. |
| Leiba et al. (2019) [30] | IoT Patching | Distributed (Ethereum Network & BitTorrent Network) | Eth | X | – | D + I + S | Blockchain-based incentivized distributed storage network with fair exchange. |
| PUIoT | IoT Patching | Distributed (Bitcoin Network & BitTorrent Network) BitTorrent Network) | Bitcoin | X | X | D + I + S | Blockchain-based incentivized distributed storage network with fair exchange and scalability. |
| Time | Depth | States Found | Distinct States | Errors |
|---|---|---|---|---|
| 780’ | 71 | 17,315,287 | 3,302,038 | 0 |
| Number of IoT Devices | Patch Size | ||
|---|---|---|---|
| 10 kb | 100 kb | 1 mb | |
| 1 | 0.532 | 13.027 | 128.513 |
| 10 | 1.41 | 13.56 | 133.75 |
| 25 | 2.8 | 18.77 | 177.12 |
| 50 | 5.81 | 34.88 | 336.94 |
| Number of IoT Devices | Patch Size | ||
|---|---|---|---|
| 10 kb | 100 kb | 1 mb | |
| 1 | 1 | 7 | 64 |
| 10 | 10 | 70 | 640 |
| 25 | 25 | 175 | 1600 |
| 50 | 50 | 350 | 3200 |
| Transaction Type | Usage Frequency | Proposed Solution ($) | IoTPatchPool ($) |
|---|---|---|---|
| Create factory | per framework setup | – | 0.36 |
| Create contract | per update file | – | 0.29 |
| Create channel | per IoT device | 0.017 | – |
| Commit | per delivery | – | 0.08 |
| Reveal | per delivery | – | 0.02 |
| Delivery cost | per piece | 0.000097 + 1% of transaction amount | – |
© 2020 by the authors. Licensee MDPI, Basel, Switzerland. This article is an open access article distributed under the terms and conditions of the Creative Commons Attribution (CC BY) license (http://creativecommons.org/licenses/by/4.0/).
Share and Cite
Tapas, N.; Yitzchak, Y.; Longo, F.; Puliafito, A.; Shabtai, A. P4UIoT: Pay-Per-Piece Patch Update Delivery for IoT Using Gradual Release. Sensors 2020, 20, 2156. https://doi.org/10.3390/s20072156
Tapas N, Yitzchak Y, Longo F, Puliafito A, Shabtai A. P4UIoT: Pay-Per-Piece Patch Update Delivery for IoT Using Gradual Release. Sensors. 2020; 20(7):2156. https://doi.org/10.3390/s20072156
Chicago/Turabian StyleTapas, Nachiket, Yechiav Yitzchak, Francesco Longo, Antonio Puliafito, and Asaf Shabtai. 2020. "P4UIoT: Pay-Per-Piece Patch Update Delivery for IoT Using Gradual Release" Sensors 20, no. 7: 2156. https://doi.org/10.3390/s20072156
APA StyleTapas, N., Yitzchak, Y., Longo, F., Puliafito, A., & Shabtai, A. (2020). P4UIoT: Pay-Per-Piece Patch Update Delivery for IoT Using Gradual Release. Sensors, 20(7), 2156. https://doi.org/10.3390/s20072156







