2.1. Features of the Reception of Broadband Signals by Antenna Arrays
An antenna array with
receiving elements is a multi-channel receiving device with output signals
, whose vector
is represented in the time and frequency domains by the relations
The matrix function characterizes the effects of the propagation of the signal generated by the source, as well as the effects of possible distortions introduced by the receiving elements. The front of the wave received in the far zone is considered flat, and then the signal becomes a scalar function of time. The wave front does not reach the receiving elements simultaneously, but with delays , where is the unit direction vector of the wave front, is the coordinate vector of the i-th antenna element and c is the signal propagation speed. In a non-dispersive medium the matrix becomes a vector with components , that reflect only the time delay.
In the two-dimensional problem, the vectors
are located in the same plane and it is assumed that the reception is carried out on a linear equidistant lattice with an inter-element distance
d located along the axis
, and the angle between
and the axis
is equal
. The signals from various array elements are weighed, generally speaking, with complex weights
,
and summed. The frequency response of such an antenna array has the form
If the array is tuned to the frequency
of the received signal then the function
depends on the angle
. Moreover, it determines the normalized radiation pattern of the antenna array
(in terms of power). In a dispersive medium, the signal
in Equation (
1) is a vector with a component
at the input of the
i-th element of antenna.
If the signal has a carrier frequency , then it is impossible, generally speaking, to tune the array simultaneously to each of these signal frequencies. This fact determines the difference in the methods of receiving narrow-band and wide-band signals on the antenna arrays. During broadband reception, the signal received by the i-th antenna element is fed to a transverse filter with amplitude and phase frequency characteristics that are adjustable for it, wherein each channel has its own transverse filter. If the latter is synthesized on the basis of a multi-tap delay line (with a delay between adjacent taps), the choice of value depends on the frequency sub-band of the signal that this filter processes.
Consider some channel of the array that processes a frequency-limited portion of the input signal spectrum. The Fourier transform of the output signal of such a filter has a limited support. By Kotelnikov’s sampling theorem, a discrete set of points , defined by the formula the time interval between adjacent sample points), is enough to restore the function from these points. Namely, just put . Similarly, the function can be reconstructed from a discrete sequence according to the same theorem. In particular, if , we have . At intermediate points, the use of an expression of the type serves as an interpolation scheme which restores by values .
For digital computers, the use of the Kotelnikov’s theorem is not entirely convenient. It would be desirable to have a slightly different form of the Fourier transform, in which they are also specified discretely, but the limits of summation are finite both in the direct and inverse Fourier transforms. This form is used in the theory of the fast Fourier transform (FFT), where the time sequence
and its frequency FFT sequence
are set by formulas
where
.
The FFT algorithm can be given in a matrix notation [
20]
where
is a vector representation of the sequence
,
is a vector representation of the sequence
and
is a unitary matrix with elements
From this fact, the equivalence of the results obtained using the time and frequency representations of the data follows. In particular, if
is a random vector of Gaussian time samples, then the vector
in Equation (
2) of frequency samples of its Fourier image will also be Gaussian. Recalculation of covariance matrices from one representation to another is simplified due to the unitarity of the transition matrix. In this paper, both representations are used equally. In particular, such an important parameter in the problems of detecting and evaluating signals as the signal-to-noise ratio is easily recalculated.
Finally, the last remark concerns the inclusion of scattering indicatrix (in power) for an object emitting a signal. The indicatrix depends on the course angle of the object. Multiplying the scattering indicatrix and the radiation pattern of the receiving antenna, we obtain a function depending on the frequency and two angular variables, which determines the strength of the target at the receiving point. It can be shown that for the case of a spatial (and not just flat) problem, the function can be represented by the Chebyshev polynomials with coefficients depending on the frequency. The coefficients are downloaded in the form of tables from the database for the entire set of operating frequencies of the monitoring station.
The selection of weighting coefficients of antenna arrays and frequency channel parameters for a broadband signal processing is not considered in the work. As noted in the introduction, the purpose of the work is not to optimize the detection procedure, but to optimize the trajectory of the object in order to evade detection.
2.2. Non-Detection Probability of UUV under Passive Surveillance
The covertness of the UUV on the selected trajectory with a given velocity law can be characterized by the probability that during the passage of the whole route it will not be detected at any tact. Such probability is denoted by
and will be called the non-detection probability of UUV on the trajectory. Let us denote as
the UUV transit time of the whole trajectory, and the duration of the tact will be
. Then the entire trajectory can be divided into
segments, on each of which a decision is made about the absence of an object and the corresponding probabilities
are calculated. Then, assuming statistical independence of the signals on each segment, one of the simplest variants of the probability measure on the trajectory is defined as the product of the probabilistic measures on the segments of the trajectory
In the case of several SSS, the product of expressions of the form Equation (
3) over all available SSS is taken [
2]. Thus, the criterion in the formalization problem of the stealth concept of UUV is the Formula (
3). Now the task is to construct the optimal trajectory and the optimal UUV velocity law, maximizing the UUV non-detection probability
.
In passive mode, the signal on the elements of the antenna array is described by the formula
where
,
,
are Gaussian input signal, object signal and noise, respectively, and
– number of discrete time samples. Here
in the case of hypothesis
(a signal from UUV is absent) and
in the case of alternative
(a signal from UUV is present).
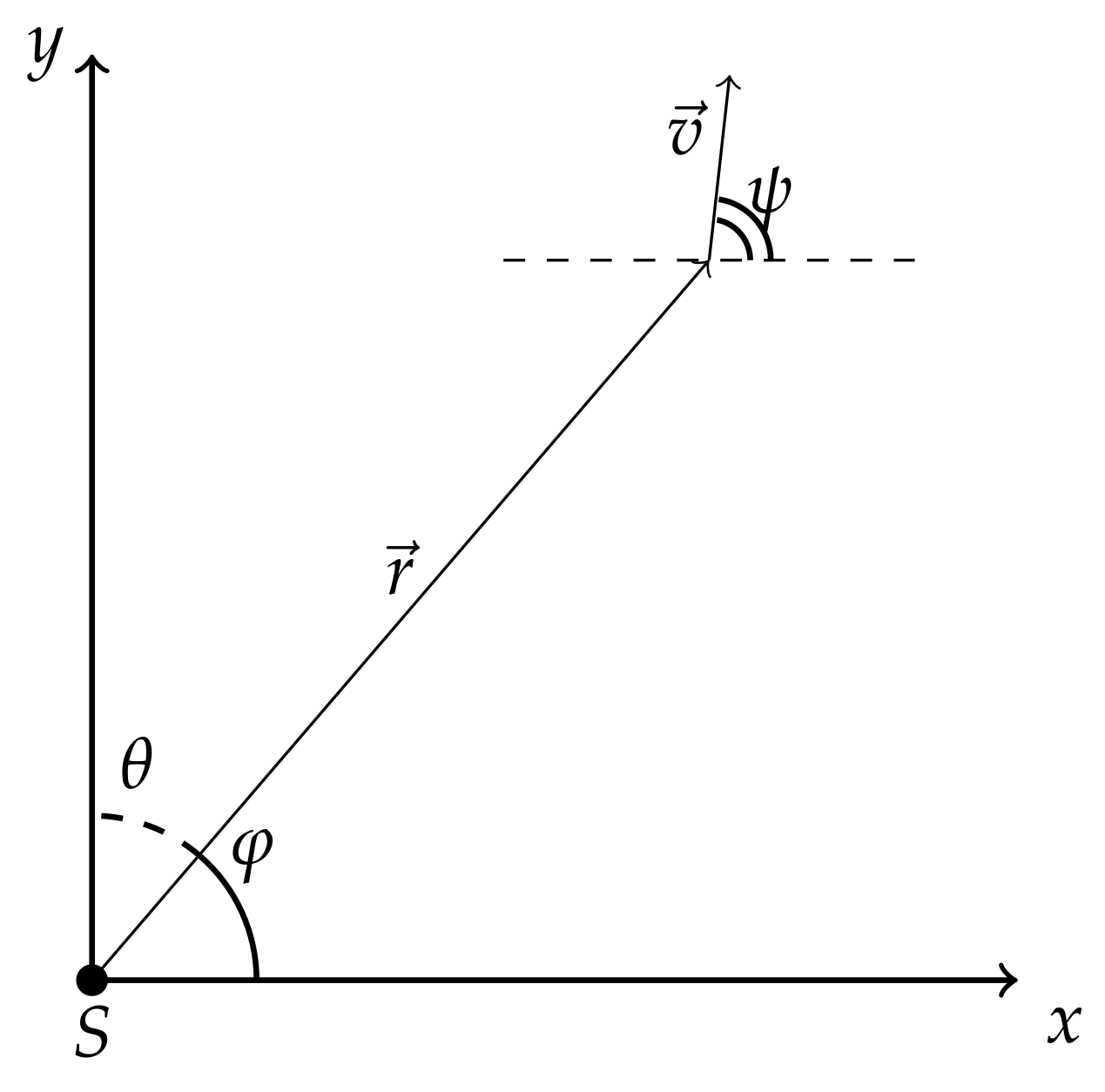
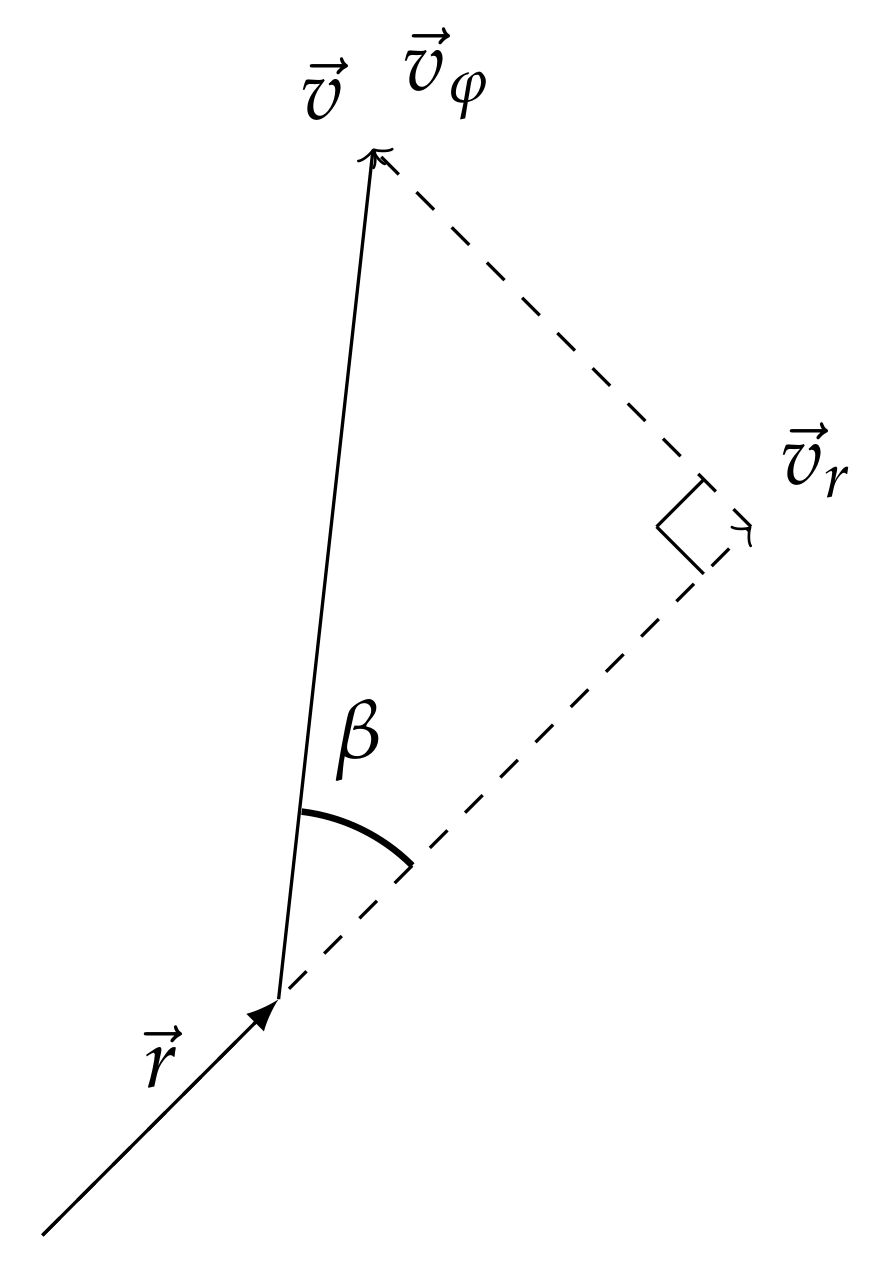
If the bearing (with the angle
) to the UUV does not coincide with the normal to the antenna line and it is known, then the hydrophone input signal is
where
d is the distance between antenna elements,
c is a speed of sound in water and
is the number of hydrophones. This signal at the
k-th hydrophone is a function of time and after sampling in time it turns into a vector
of size
. The covariance matrix of this vector is equal to the sum of the covariance matrices
of the signal and noise respectively, where, due to the independence of time samples of noise, the matrix becomes diagonal, and the matrix of the signal from the object, due to the assumed stationarity, is a Toeplitz matrix with elements
where a pair of indices
fixes the numbers of hydrophones, and
corresponds to the time shift of the signals during sampling by time in step
. Similarly,
means the inter-element delay in the equidistant linear array when the wave is incident at an angle
. The time sequence of
vectors in the number of
pieces can be represented as a single column vector
with
elements. In modern SSS with linear antenna array the incoming signal is often preprocessed in the receiving path using FFT. Consider the detector, which performs FFT of time-sampled signals coming from the hydrophones of the linear antenna. As a result, we get a sample of Gaussian centered complex random vectors
of dimension equal to the number of hydrophones
in antenna. Further processing of the received signal is assumed not in the time but in the frequency domain, since in the case of broadband reception, it is possible to select the frequency ranges most informative for the received useful signal. Therefore, the FFT is applied to the temporal components of the vector
.
After the FFT conversion, the observation signal is described as
The detector works according to the threshold principle, according to which the observations obtained at one tact are converted into decisive statistics compared with the threshold. If the threshold is exceeded, a decision is made about the presence of the object. A false alarm is when the threshold is exceeded in the absence of an object. Such an event is random, and the threshold is selected from the condition that the probability of false alarm is equal to a given small number .
After pre-processing at each hydrophone (band-pass filtering, time-shift of the input signal, sampling by time of the continuous signal and FFT of them), the input signal to be decided is a set of random vector-columns
with a dimension equal to the number of hydrophones
. Moreover,
in the case of a hypothesis and
in the case of an alternative. A
-vector
is compiled from complex vectors
. Then the likelihood ratio for Gaussian vector
can be determined as [
21]
where
is the covariance matrix of a random vector
of the frequency components of the signal in the case of a hypothesis
, and
is the covariance matrix of the vector in the case of an alternative
. Assuming noise independence at various hydrophones, covariance matrices can be represented in a block form
where
is the covariance matrix of a noise which is the same on each of the frequency channels of the antenna array processor, and
is the Toeplitz covariance matrix of the vector signal
from an object with elements
where
and
O is the square zero matrix. For simplicity we assume that signal
is stationary. Then the covariance matrix of signal
can be represented as
, where
is the normalized covariance matrix, and
is the variance of the signal from the object.
2.3. Non-Detection Probability of UUV under Passive Surveillance at a Small Signal/Noise Ratio
The Hermitian form in the likelihood ratio Equation (
4) is reduced to
which allows in the case of a small signal/noise ratio to significantly simplify this expression, bringing it to the form
Then in the far detection zone the likelihood ratio is approximated as a function of the statistics [
22]
where
.
In this case, the likelihood ratio is a monotonically non-decreasing function of statistics
Q and there is a uniformly the most powerful criterion for testing the hypothesis
against
. This criterion is to compare the statistics
Q from Equation (
5) with the threshold
h chosen from the condition that the probability of false alarm equals to a given number
:
.
By virtue of the central limit theorem the probability distribution of the statistics in Equation (
5) is approximately normal with expectation
and variance
in the case of the hypothesis
(there is no useful signal) and with expectation
and variance
in the case of the alternative
. When calculating the UUV probability of detection it is assumed that the bearing on the UUV is known. In this case, the probability of UUV being undetected in the next cycle is obtained as
where
is a function of the standard normal distribution
.
Due to Equation (
5) the next expressions for distribution of statistics
Q moments are valid
Taking into account Equations (
7) – (
9) the Formula (
6) is representable in the form
In the absence of information about covariances between hydrophones we accept
(
I is identity matrix), and then
Finally, the UUV non-detection probability on the trajectory is equal (with a small ratio signal/noise)
The next lemma is valid.
Lemma 1. On the i-th cycle of observation non-detection probability of UUV under passive surveillance at a small signal/noise ratio can be approximately formulated as Proof. Choose the non-detection probability of the form Equation (
10) and consider it at a small signal/noise ratio
Taylor series expansion with respect to a small signal/noise parameter leads Equation (
12) to the form
which is simplified to an expression
□
The total probability of UUV detection formally corresponds to the probability of occurrence of a detection event at least once in a series of
N observations and for independent events (observations) is calculated by the formula
or, if you introduce the concept of “risk”,
where
is the risk for the
i-th observation segment. Given Equation (
12), for enough small
Formula (
13) takes the form
Multiplying and dividing the last expression by
(tact duration) and assuming that
(UUV time on the route), we obtain
The last sum is represented as an integral, which we call the threat functional [
4,
5] in the problem of UUV route planning for the case of passive sonar
This conclusion coincides with the result given in Reference [
3] in the case of one sonar for
with the non-detection probability in the form
where
– probability distribution with
n degrees of freedom,
is a false alarm probability,
– attenuation coefficient,
is the distance from UUV to sonar at
j tact, starting from the moment of appearance of UUV on the trajectory, and
is a constant speed of UUV at this tact,
,
,
,
,
are some model parameters. The number of factors in the product is equal to the number
N of tacts when moving UUV along the trajectory.
To use the Formula (
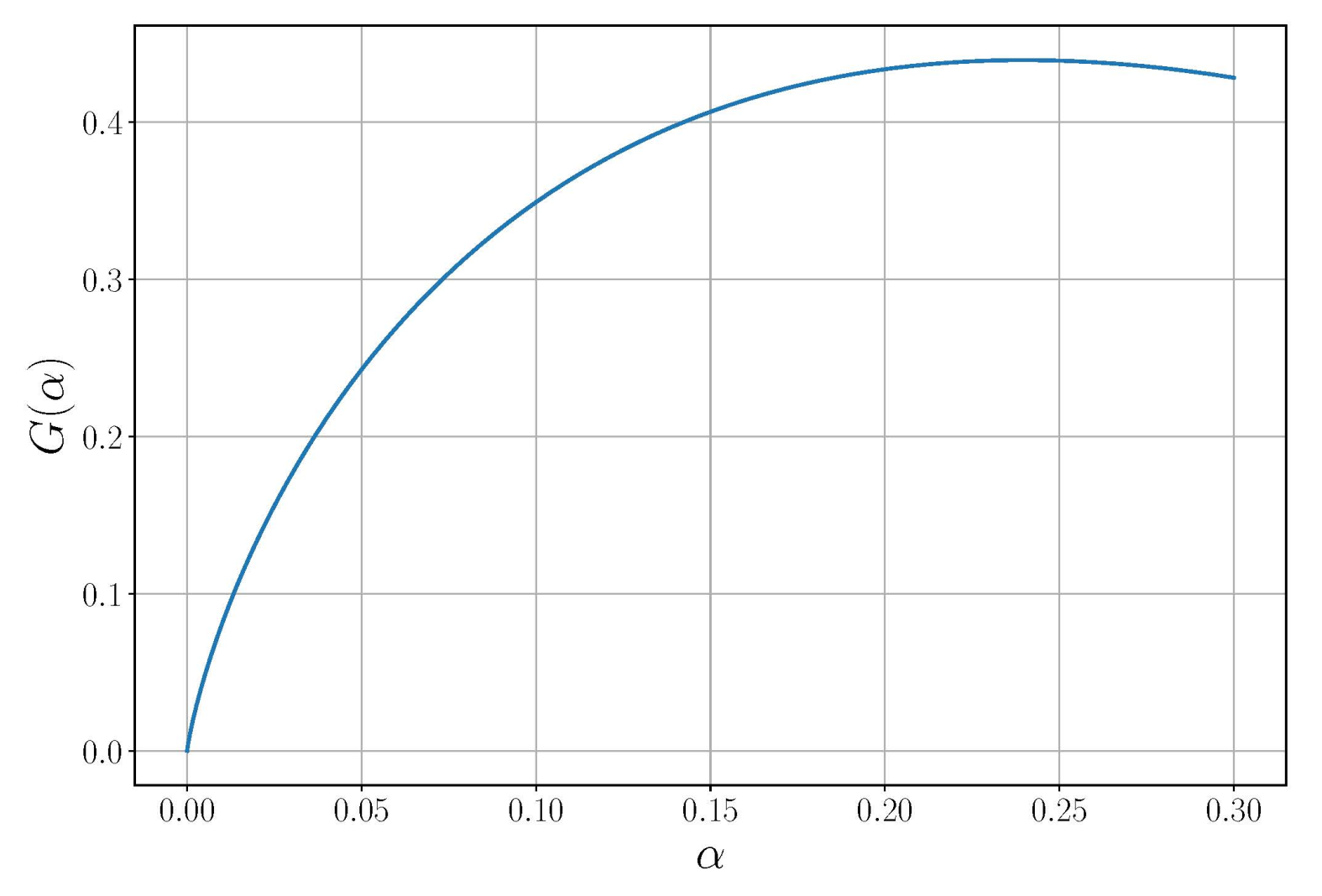
14) for calculations, it is necessary to ensure the smallness of the first term and to estimate the value of the multiplier standing before the sign of the sum in the second term. The dependence
of this multiplier on the probability of a false alarm is shown in
Figure 1. Moreover, for the path planning task, it is not required to know the exact values of the information processing parameters included in expression Equation (
14) because they are not included in Equation (
15).
2.4. Non-Detection Probability of UUV under Active Surveillance
Consider the case of an active location, when the observation model has the form
where
,
,
are Gaussian complex input signal, useful signal and noise, respectively, after FFT conversion. The meaning of
is the same. In this case, the statistics for comparing with the threshold is as follows
where
is the covariance matrix of noise vector. Statistics Equation (
18) is linear in observations,
has a normal distribution and the non-detection probability on the observation cycle after sending the probing signal is written in the form of Equation (
8), but here
and hence
In the absence of information about covariances between hydrophones the probability of non-detection at one sending of the probing signal is equal to
The number of factors in the product is equal to the number of cycles during the passage of the entire trajectory of UV. As in Equation (
11), the non-detection probability on the trajectory in active mode is the product of all observation cycles on the trajectory
It should be noted that in Formulas (
11) and (
20), the variance of the useful signal is a function not only of the distance
r to the object, but also of the attenuation coefficient
when the acoustic wave propagates in a stratified medium.
Choose the non-detection probability of the form Equation (
20) and consider it at a small signal/noise ratio with the aid of Taylor series. Then next formula is valid. Like Formula (
15), summing up all the cycles of observation, we obtain the treat functional part of active mode equal to
The treat functional Equation (
15) or (
21) on a segment of the trajectory has as input parameters the data of sonar systems, including their location (coordinates and parameters of detection active or passive mode, orientation of antenna, etc.) and calculated for these values of the ratio signal/noise reference source (its speed and the direction of sonar), the values of latitude and longitude start and end points of the segment, the speed of the UUV.