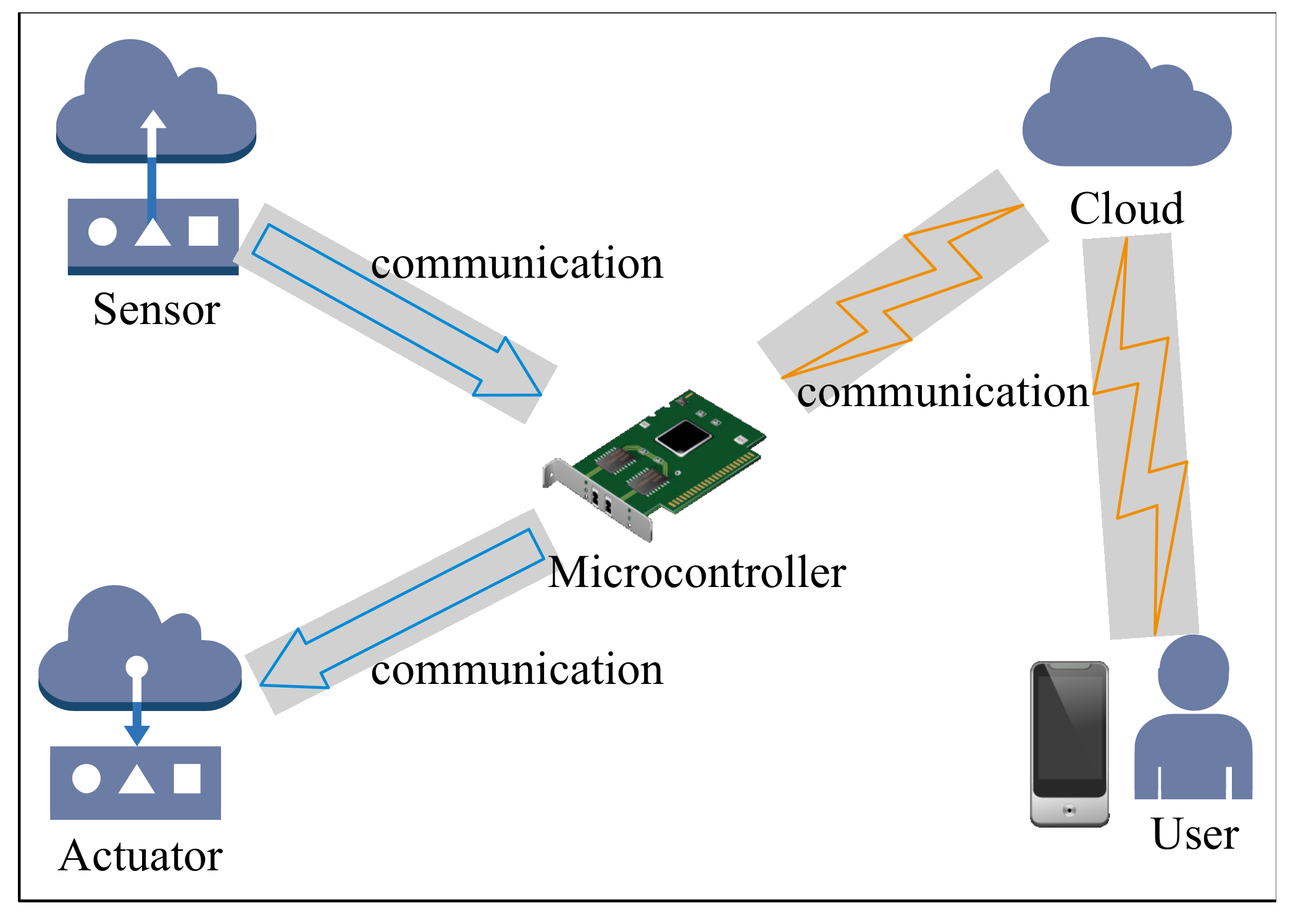
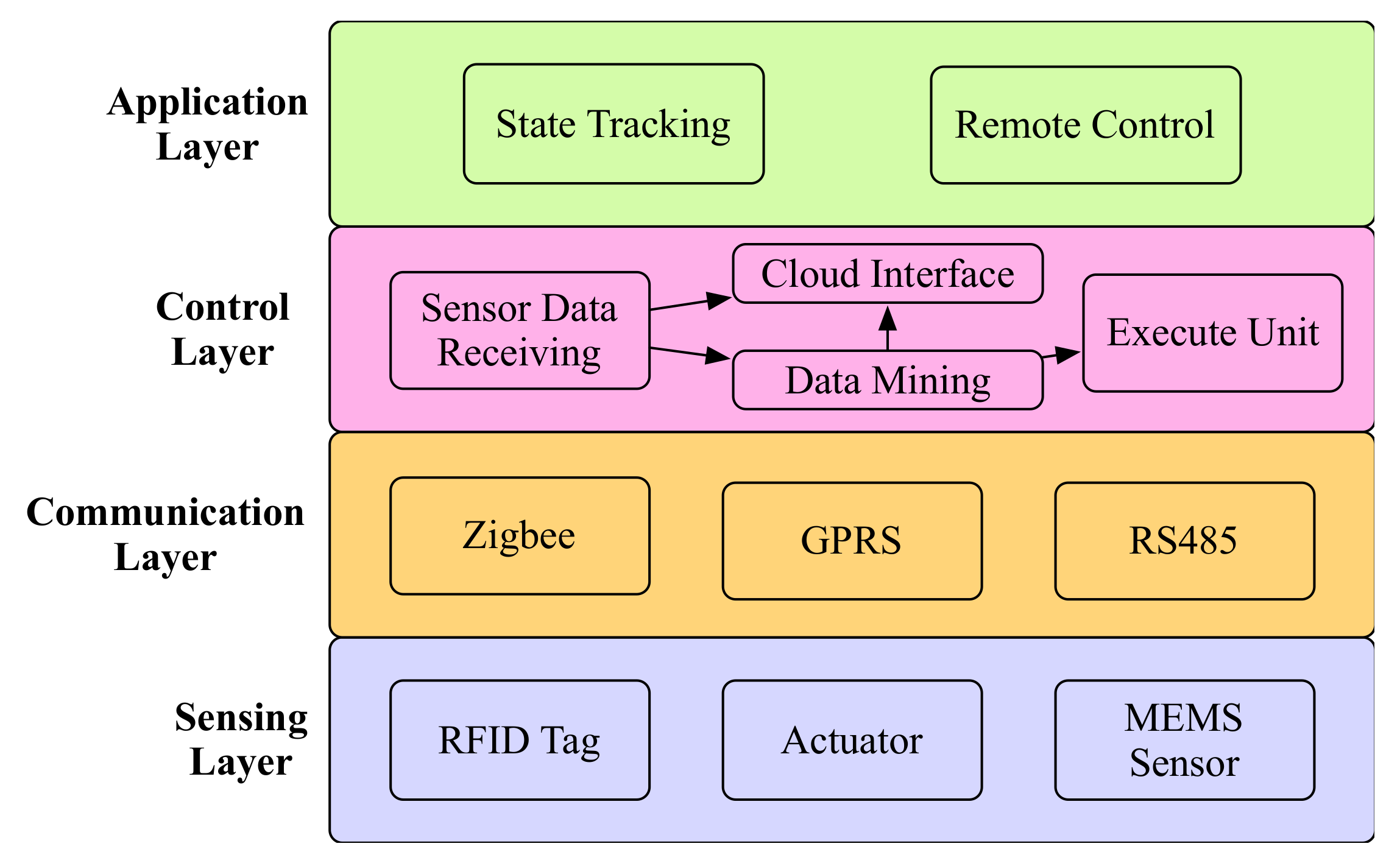
In this section, two industrial implementations of the proposed architecture are introduced. Both of these two implementations are coming from the real requirements of the companies, and they have been successfully deployed for daily uses.
3.1. A RFID-Based Microcomputer Lock System Using One Microcontroller
The first implementation has been successfully applied in an electricity company in Jiangsu province of China. In fact, the maintenance of electricity equipment is difficult because of the special characteristics of electricity. Accidents frequently occur when the maintenance workers wrongly operate the equipment. Meanwhile, the amount of electricity equipment has rapidly increased with the development of the power grid, which increases the operation difficulties. Generally, a duplicate naming mechanism could be used to help maintenance workers identify different equipment. However, entering the wrong equipment room or operating the wrong electricity equipment always occurs during the process of their daily maintenance works. In general, a lock system is applied to reliably avoid the occurrence of these accidents. The five anti microcomputer lock is such a solution to effectively avoid accidents involving wrong operations.
However, the five anti microcomputer lock has only 10 bits address space for encoding identification number. That is, it only has 1024 permutations, which will result in the following two drawbacks: first, if the number of pieces of equipment exceeds 1024, the identification numbers assigned to the locks would be duplicated. This would cause the risk of wrong operations. Second, the identification number could only be used at one substation. It could also have the chance to be duplicated at different substations. If the maintenance workers try to sequentially maintain the substations, the digital keys should be repeatedly configured on site to guarantee the uniqueness of the lock identification number. This will waste the time and energy of maintenance workers.
RFID technology is a major breakthrough in the embedded communication paradigm which enables design of microchips for wireless data communication. They help in automatic identification of anything they are attached to acting as an electronic barcode [
25]. Therefore, the RFID technology incorporating the proposed microcontroller architecture is applied to effectively solve the above problem. This greatly facilitates the operation and maintenance of the electricity equipment.
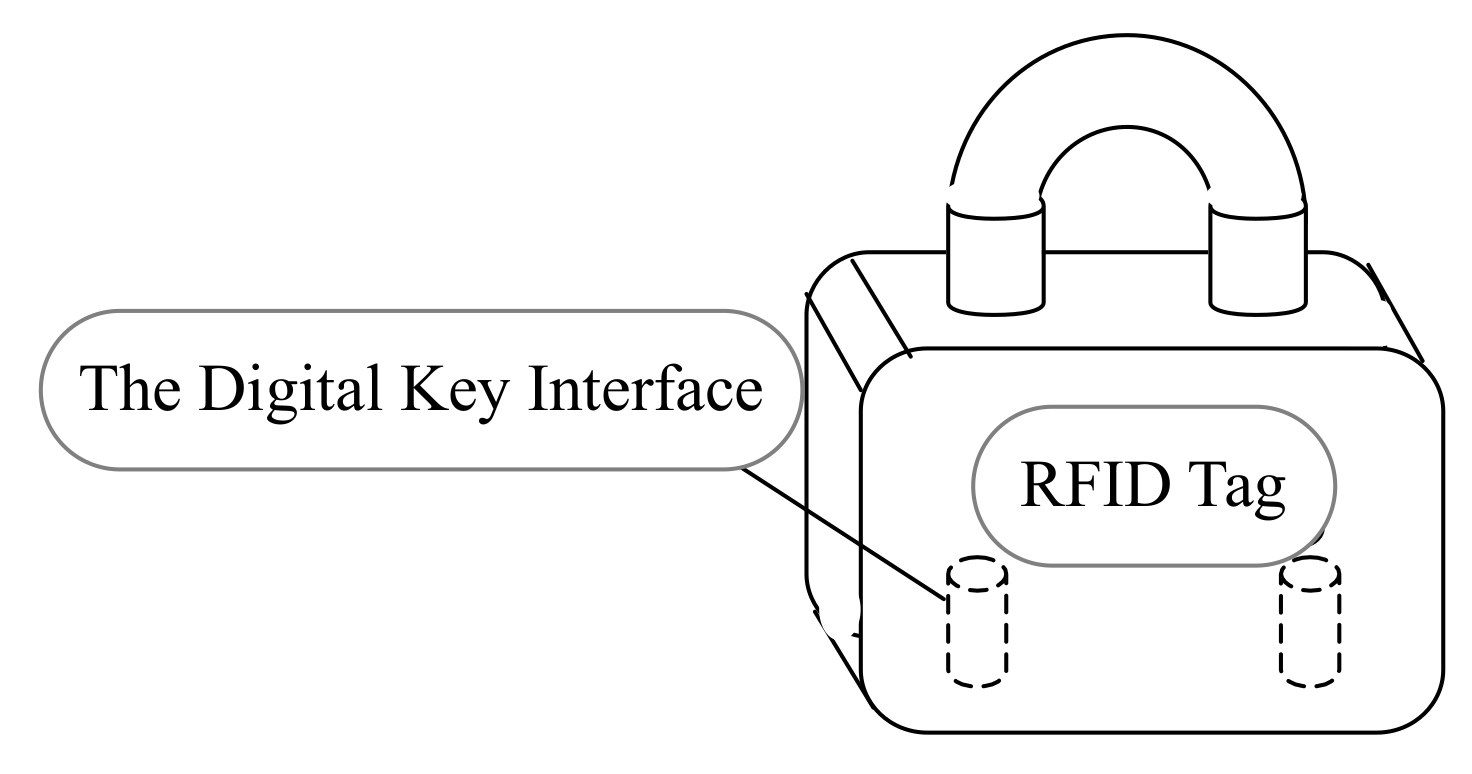
To deploy the product in a more effective way, the original five anti microcomputer lock is improved in the following two steps: first, a RFID tag with a unique identification number is attached to the lock; second, the digital key incorporated the proposed microcontroller architecture is implemented. A RFID reader is implemented in the digital key to decode the identification number from RFID tag. Therefore, the lock could be controlled by RFID tag together with its original machinery. The logical rules are used to determine whether the lock will be unlocked or not. With this solution, the uniqueness of the equipment identification number could be ensured. Generally, 64 bits or 96 bits identification number is enough. Moreover, the remote authentication of the digital key to any equipment could be achieved. The unlock time and the operator of the lock could also be recorded. Therefore the solution could greatly improve the efficiency of maintenance workers and ensure the normal work of the equipment. The system structure is shown in
Figure 4. A RFID tag is attached to the lock, and two interfaces are left to the digital key.
To develop a robust system, there are several requirements. First, the system should properly work in the strong electromagnetic environment. Meanwhile, the RFID tag should be safely attached to the surface of the lock. Second, the RFID tag reader could communicate with the RFID tag that is located more than 2 meters away. Third, the digital key should be powered by low power battery. Moreover, it could store data, such as unlock time. Fourth, the digital key could communicate with remote computers by RS232 or USB. Finally, the digital key should automatically shut down in case there are no operations within a specific time, such as 10 min.
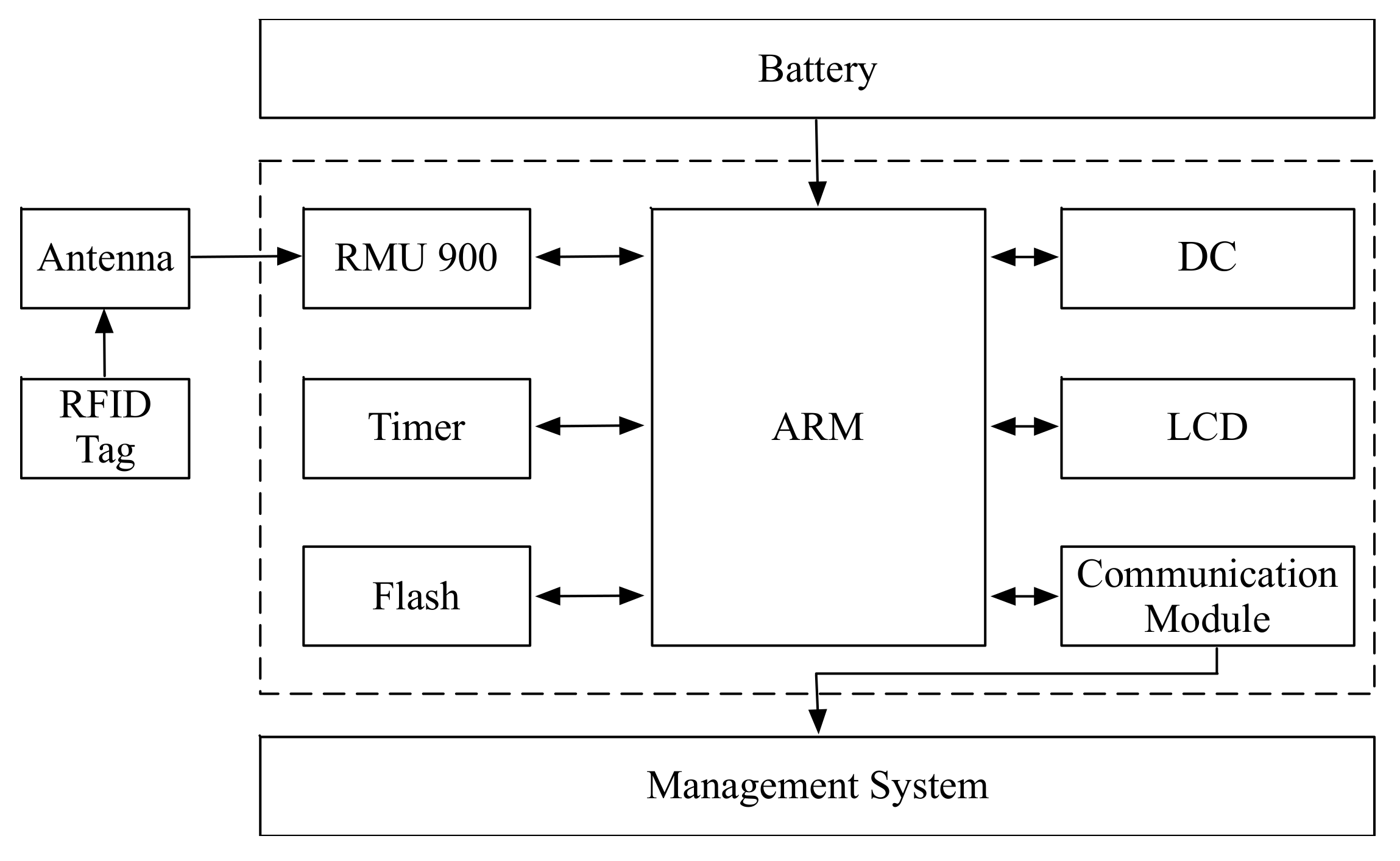
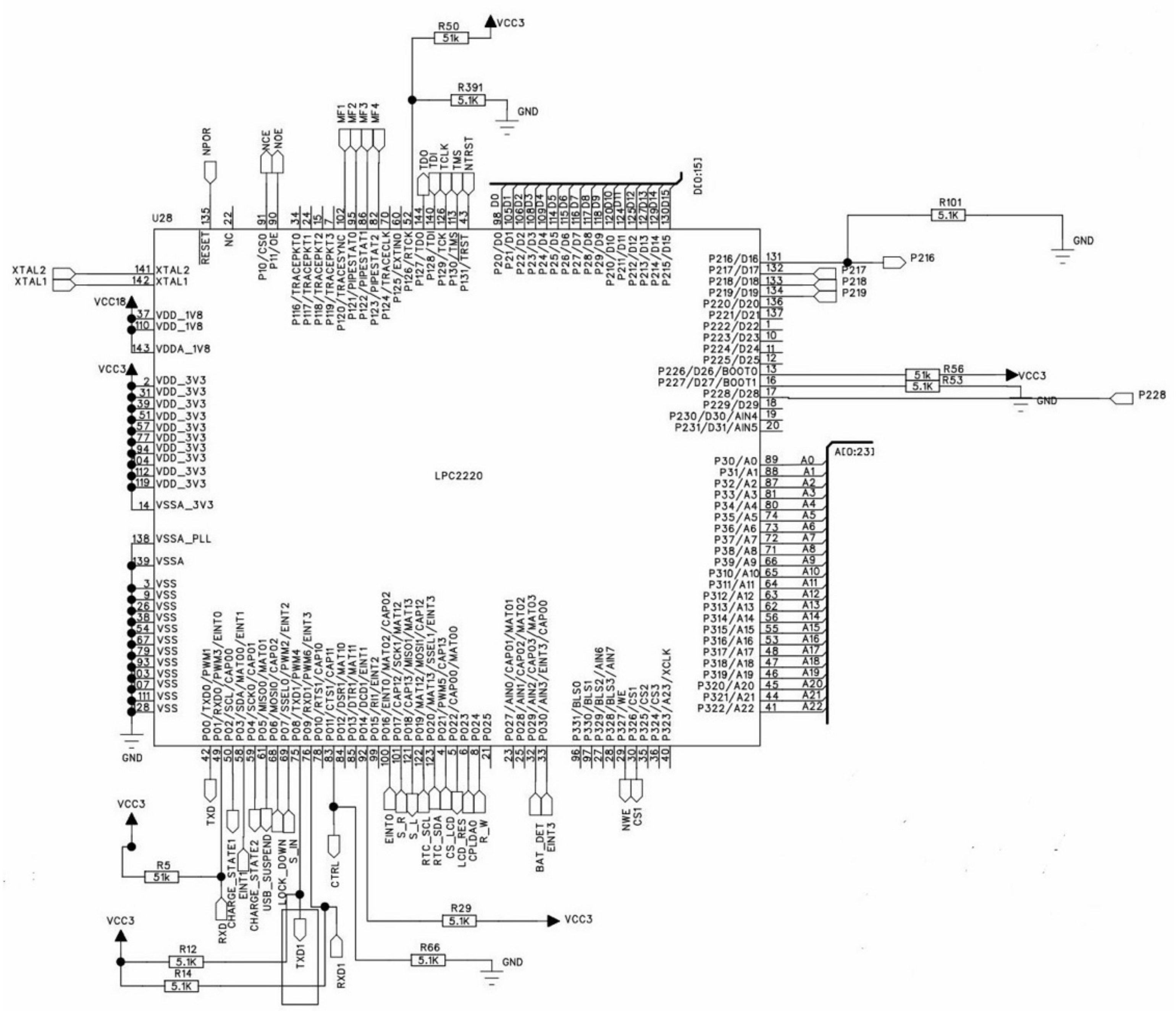
Therefore, the detailed design of the digital key in RFID-based microcomputer lock system is shown in
Figure 5. All components have their own functionalities to meet the requirements mentioned above.
3.1.1. RFID Tag Component
A RFID system is composed of tag, reader, and the application software. The tag could also be called transponder. The working flow is as follows: first, the reader emits a radio wave with a specific frequency to the transponder; second, the transponder sends out the data stored in its memory; third, the reader sequentially read the data and send them to the application software.
There are two types of RFID tags. The one is the passive tag, and the other is the active tag. For the passive tag, after the RFID tag enters the magnetic field, it receives the radio frequency signal sent by the reader. The data stored in the tag chip is sent out with the energy obtained by the induced current. For the active tag, it could send out a signal with a certain frequency. After reading and decoding the data, the reader will send the data to the central information system for further processing.
In order to reduce the maintenance cost, the passive tag with compact size is selected in this system. Moreover, the working frequency of RFID tag is another key point of the whole proposed hardware system because it determines not only the operational principle of the radio frequency identification system, but also the difficulty and cost of the implementation of the RFID reader. In the proposed system, an ultra-high frequency RFID tag with the frequency of 915 MHz is used. Based on this frequency, the RFID tag reader is developed.
3.1.2. RFID Tag Reader Component
In this system, there are two kinds of RFID tag readers. The first one is used to maintain the unique identification number of RFID tag attached to the lock. It could write the encoded identification number to a RFID tag, and it could also correctly read that number. The other one is embedded in the digital key. It could read the encoded identification number from a RFID tag and compare this number with the one stored in the digital lock flash to determine whether the target lock should be unlocked or not.
There are large amounts of adjacent locks in the same equipment room. Therefore, the working distance should be properly set to prevent misreads.
In our implementation, the RMU900 module is used to work as the key component of the RFID reader. The components such as emission, receiver, radio frequency coupling, and MCU are all integrated in the RMU900. Moreover, it has several advantages. First, an application programming interface (API) is provided to conveniently control the module. Second, it works at low voltage, which is suitable for handheld devices. Based on this module, we implemented the following two functionalities: one is configuring the working frequency and reading distance of the module, the other is reading data from RFID tag and sending it to other circuit for processing and storing.
3.1.3. Central Control Module
The central control module is the core component of the microcontroller. It can read data from flash and perform logical controls. In the digital key, the central control module uses the Acorn RISC Machine (ARM7) processor with advantages of low power consumption and high operation speed.
3.1.4. Battery Component
The digital key is powered by a battery. Therefore, a robust battery is needed to ensure its normal work. Lithium batteries have the advantages of high energy density and long service life (more than 6 years). Moreover, the working voltage of a single battery is 3.7 V or 3.2 V, which shows that it has high power endurance. Furthermore, its self-discharge rate is very low. These advantages show that lithium batteries are one of the best battery solutions for the proposed digital key.
3.1.5. Flash Component
Flash memory is used to store two types of data in the digital key. First, the identification number of the target lock should be stored. Second, other important data such as unlock time, unlock worker should also be stored for future tracking.
The SST39VF1601 NOR flash memory unit is used in our implemented digital key. It could meet the storage requirements because it can store 2 M of data. The flash address space is shown in
Table 1. In this table, not all of the storage contents are listed. Three major contents including working ID, unlock start time, and unlock end time are used to indicate the address space.
3.1.6. Communication Module
The digital key should communicate with the management software so that its status could be tracked. Therefore, the communication module in the digital key has two functionalities. First, setting the configurations of the digital key. Second, showing the running status of the digital key.
In our implementation, the communication interface is RS232. The format of the communication data is shown in
Table 2. The 2-bytes “Start” means the begging of the data frame. The 1-byte “Length” means the length of the whole data frame. The 1-byte “Command” means the control commands sent between the digital key and the management software. The “Data” means real data transferred between the digital key and the management software. The “Checksum” is used to check the correctness of the transferred data.
3.1.7. Management System
The management system includes two software systems. The one is the lock management system, and the other is the remote authentication system.
The lock management system is used to maintain the identification numbers of all the electric equipment. That is, it can assign a unique identification number to electric equipment. Moreover, the unlock time and unlock operator could also be recorded by the management system.
The remote authentication system allows the administrator to remotely authenticate the digital keys. Therefore, one or more locks in different locations could be unlocked. The maintenance workers collect all the equipment needed to be unlocked and send a request to the administrator who will audit the request. If this is a legal request, the identification number will be sent to the digital key. Meanwhile, every operation will be recorded by the system.
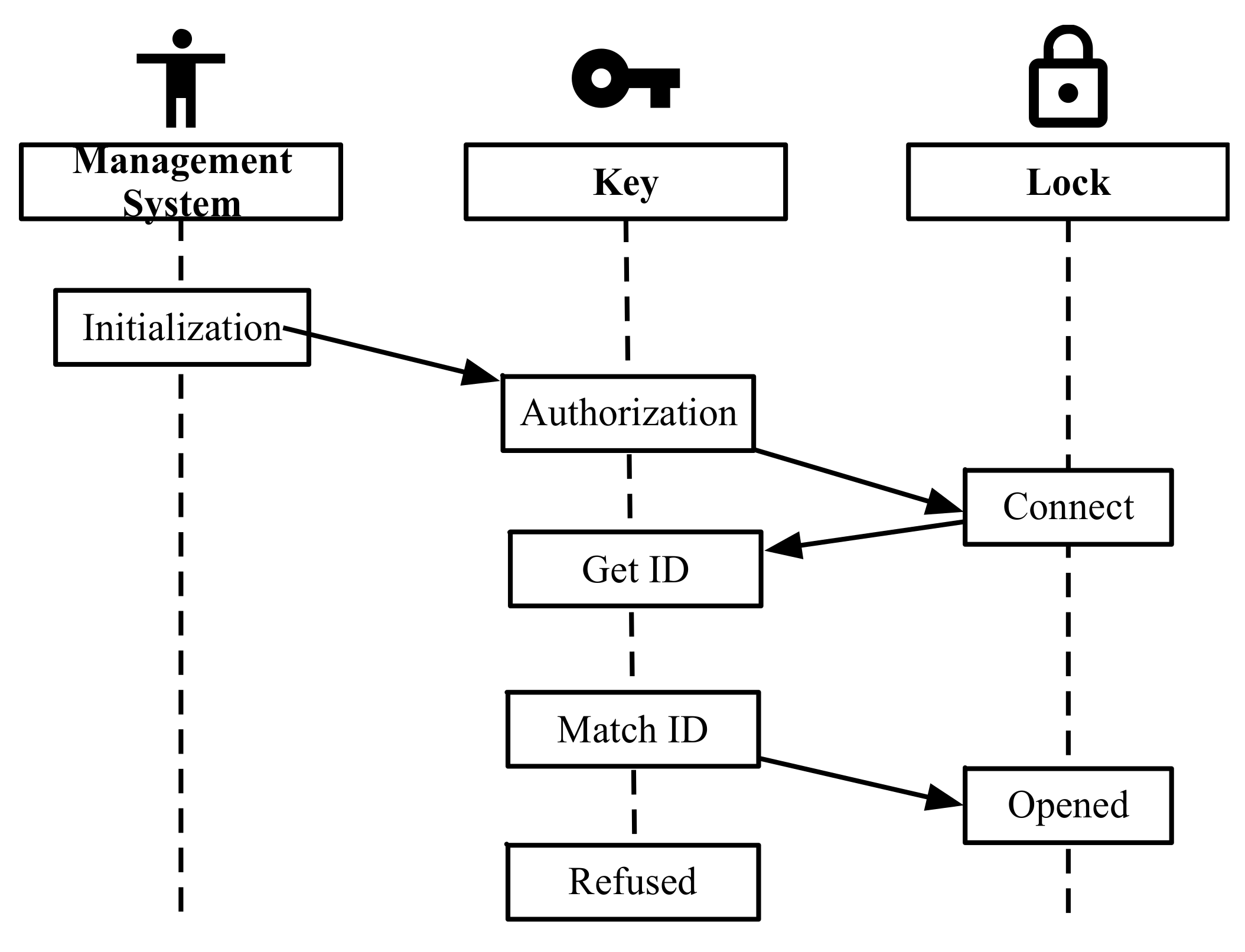
The working flow of the RFID-based microcomputer lock system is shown in
Figure 6. The first step is “initialization”. A unique identification number generated by management system is assigned to RFID tag which will be attached to the lock. The second step is “authorization”. The maintenance worker submits an unlock request to the administrator according to his working content. The administrator sends the audited identification number to the digital key. The third step is “unlock”. The maintenance worker inserts the digital key into the lock. The digital lock will connect to the lock system and read the identification number. The final step is “match”. If the read identification number is matched with the number stored in the digital key, the lock will be unlocked. Otherwise, the lock cannot be unlocked. The logic control circuits are shown in
Figure 7.
The usage data is collected after applying the RFID based microcomputer lock system in the electricity company. The results are shown in
Figure 8. In this figure, the horizontal axis stands for the days in one month, and the vertical axis stands for the average maintenance time used in that day. Obviously, the average time is reduced from 7.4 to 4.8 hours when the RFID-based lock is deployed. This result demonstrates that the working efficiency has been improved.
3.2. A Distributed Game System Using Multiple Microcontrollers
It is hard to deal with complex problems using a single microcontroller. Therefore, the distributed microcontroller architecture could be used to achieve this goal. In this section, we will show an IoT-based game system with distributed microcontrollers. The real room escape game is originated from a computer game. Players in the room can walk out of the room by answering questions to find the clues.
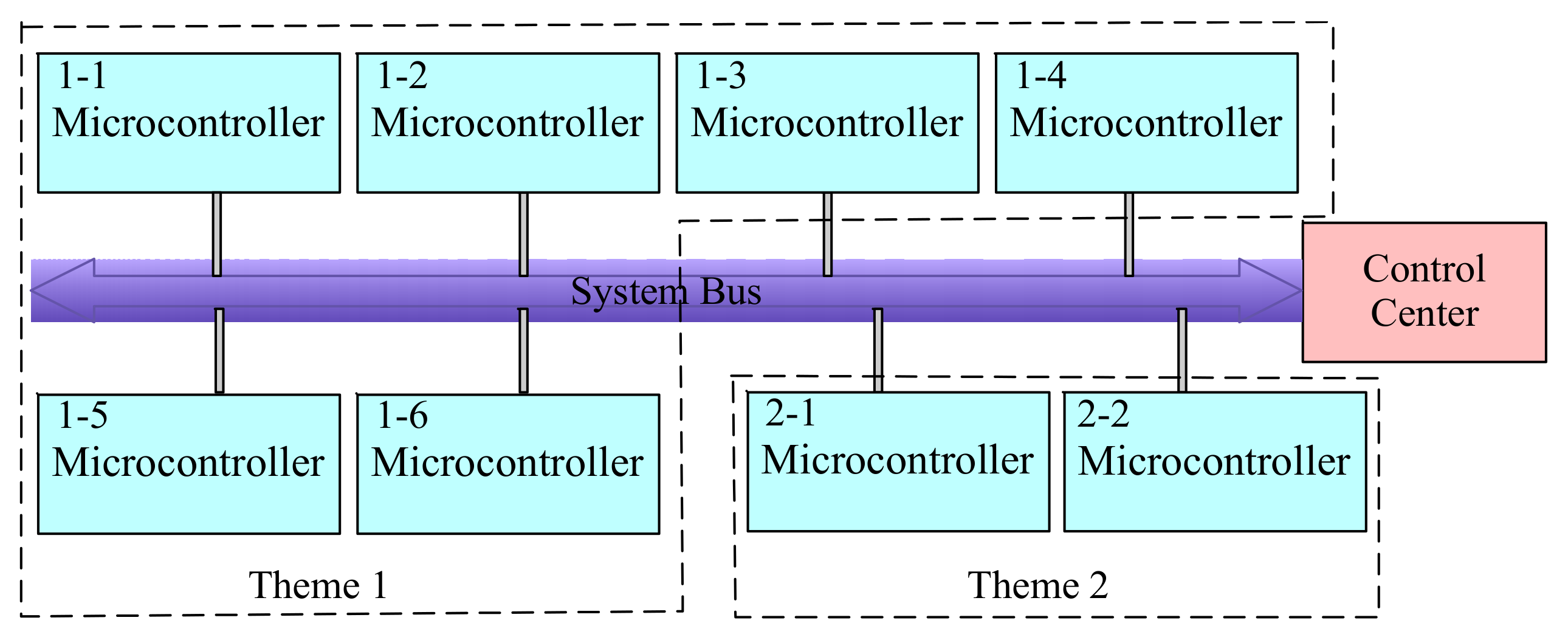
There are plenty of themes and scenarios in this game. This requires the system to be scalable. When adding a new scenario, the original system architecture should not be modified. Furthermore, the microcontroller should be reusable. Therefore, the hardware could be reused in each scenario, and the software should be modified for different scenarios. Finally, all microcontrollers should be uniformly controlled for the convenient administration. In order to meet the above requirements, the distributed architecture is designed, as shown in
Figure 9. The game has two themes, and every game has different scenarios. Each scenario is assigned to a single room. Therefore, every scenario has a microcontroller called the local controller. All local controllers are connected to a control center by the system bus.
The local controller collects data from different sensors such as light sensor, steering sensor, magnetic induction sensor, RFID tags, and so on. Furthermore, the control signal is generated according to the logical rules embedded in the microcontroller. The control signal will drive other devices including electromagnetic lock, motor, alarm, and audio equipment to finish the control process. In our implementation, the local controller is powered by a 5 V battery. Moreover, it communicates with the control center with a RS485 system bus. With this architecture, the system functionalities could be conveniently extended by connecting a new microcontroller to the RS485 system bus.
The control center is also a microcontroller, which has the same platform with the local controller. Because the control center connects all local controllers, it can remotely control microcontroller of each scenario. For example, the control center could reset every local controller located in the game rooms. Moreover, the control center has management software which could be used by the administrator to remotely control the equipment located in the game room.
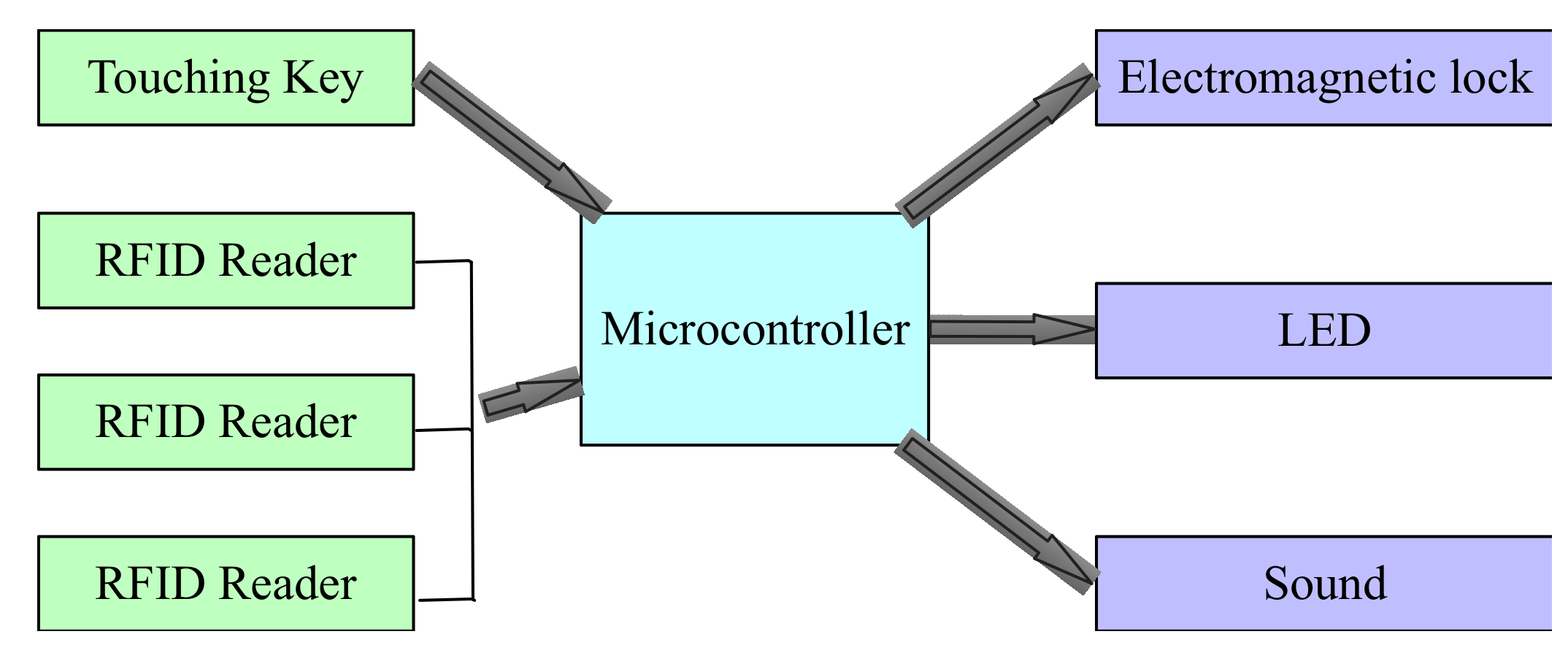
Because there are lots of local controllers in our implemented distributed game system, but only one local controller is picked up to demonstrate the working flow. The local controller system is shown in
Figure 10. In the figure, the left four components are sensors. The touching key is used to capture the touching actions of players. RFID readers are used to receive signals from RFID tags attached in the body of players. The logical computation is executed in the microcontroller, which will generate the control signals. In this example, there are three control signals. One is used to unlock an electromagnetic lock, one is used to control LED light, and one is used to control the sound device.
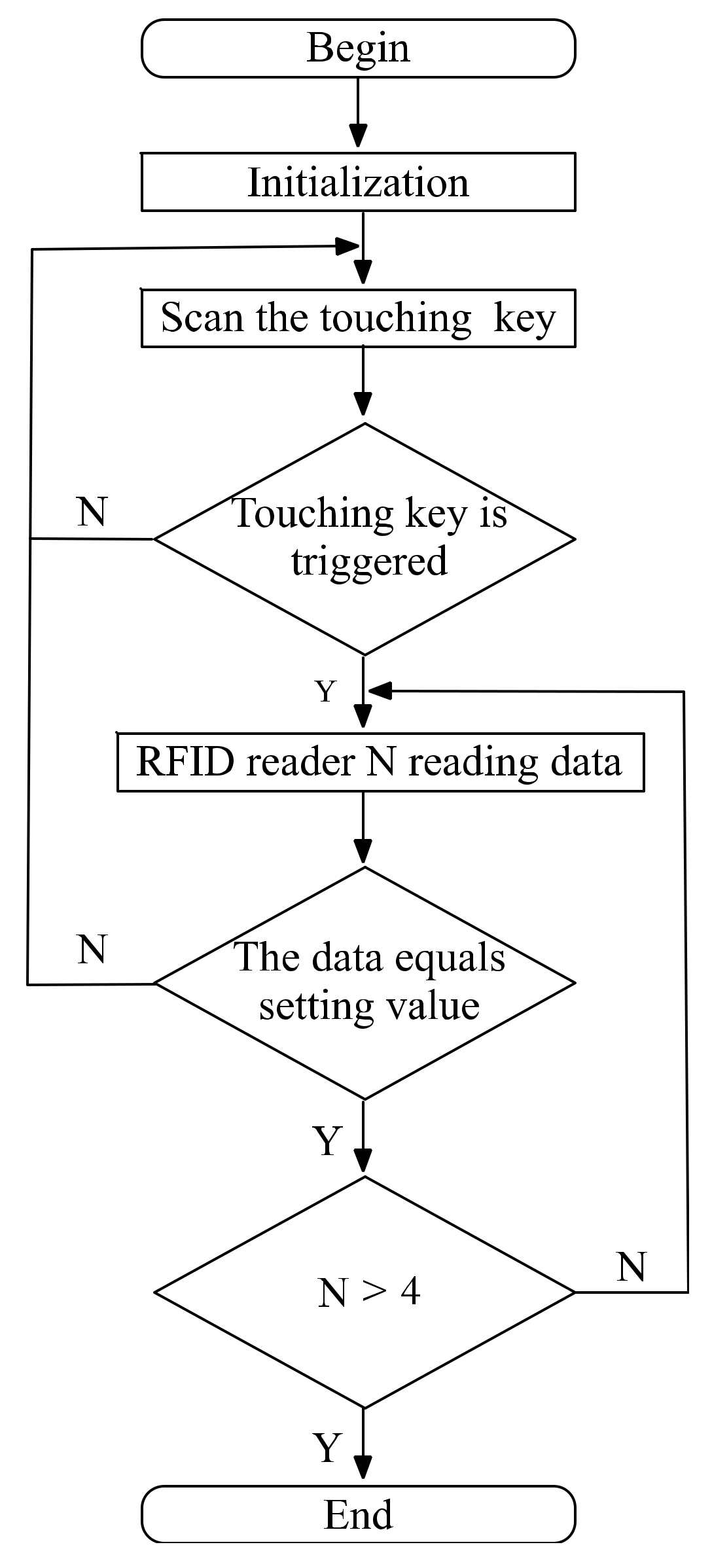
The program flow chart of the logical control is shown in
Figure 11. In initialization step, the configurations of microcontroller are reset. The microcontroller begins to scan the status of the touching key. If the touching key is triggered, it begins to read data from one RFID reader. Otherwise, it will wait for the players to trigger the touching key. The read data is compared with the setting value, and if they are equal, this challenge for the players is passed. When all of the challenges are passed, the program ends.
In summary, a total of eight scenarios are designed in this system. There are 62 buttons, 15 RFID readers and 12 laser sensors are used in the implementation.
3.3. Simulation Experiments
To quantitatively evaluate the proposed architecture, a simulation experiment is setup. Assuming that there is a control center C,
M local centers
LC = {
S1, S2, …, SM}. The communication time between the
i-th local center and C is
tsci (1 ≤
i ≤
M). The working time between two local centers is
tssi (1 ≤
i ≤
M − 1). The processing time of the
i-th communication request for C is
tci ~
f(M) (1 ≤
i ≤
M), that is, the time is proportional to
M. The processing time between the action of a player and the local center is
thsi (1 ≤
i ≤
M), and there is
Ni actions for the
i-th local center. The total time
T used by the system could be defined as follows:
where, the former part is used to measure the time costs of communications, and the latter part is used to measure the time costs of a player moving between two local centers. The uncertainties of the simulation experiments are as follows: first, the communication time
tsci is uncertain because different local centers have different communication conditions with the control center. Second, the time
tssi is uncertain because the time intervals between a player leaving a local center and entering the next local center are different. Finally, the time
thsi is uncertain because different players have different capabilities to escape from a local center. To simulate the process of the game, the cloud model is applied to handle above uncertainties. The cloud model is a model of the uncertainty transition between a linguistic term of a qualitative concept and its numerical representation, which could deal with fuzziness and uncertainties in a unified way. It can be explained by means of the traditional probability and statistics theory and fuzzy set theory [
12]. The cloud model has been widely used in data mining, nonlinear systems control, knowledge discovery, subjective trust management systems and evolutionary computing etc.
Normal distribution is one of the most important distributions in probability theory. It is usually represented by two numeric characteristics: mean and variance. The normal cloud model is proposed based on the normal distribution. It has three numeric characteristics: Expected value (
Ex), Entropy (
En) and Hyper-Entropy (
He).
Ex is the position corresponding to the center of the cloud gravity, whose elements are fully compatible with the linguistic concept,
En is a measure of the concept coverage,
He is a measure of the dispersion on the data samples, which can also be considered as the entropy of
En. Vector
v = (
Ex, En, He) is called the eigenvector of a cloud. With the given algorithms of forward and backward cloud generators, it is easy to build the mapping between qualitative concept and quantitative data. The forward cloud generator algorithm generates the data samples by inputting (
Ex, En, He). On the contrary, the backward cloud generator algorithm calculates three numeric characteristics (
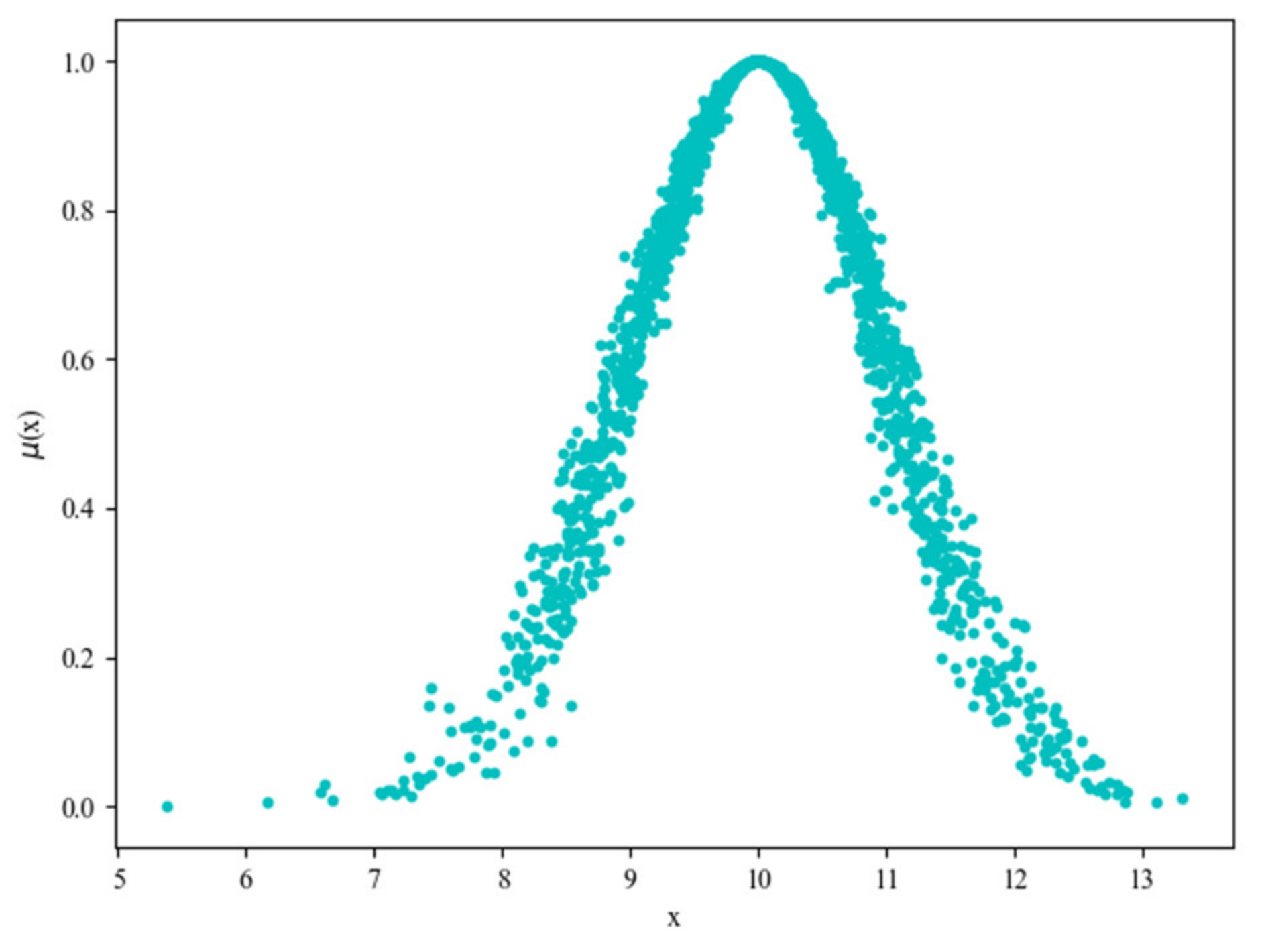
Ex, En, He) by processing data samples. A normal cloud model is shown in
Figure 12, the data is generated using a forward cloud generator with three input parameter
Ex = 10,
En = 1,
He = 0.1.
The normal cloud model is used to handle the uncertainties in simulations by using the normal cloud (0.9, 0.2, 0.02) to measure
tsc, using the normal cloud (0.3, 0.05, 0.01) to measure
ths, using the normal cloud (3, 1, 0.1) to measure
tss and using the normal cloud (0.5, 0.05, 0.01) to measure
tc. The parameters are listed in
Table 3.
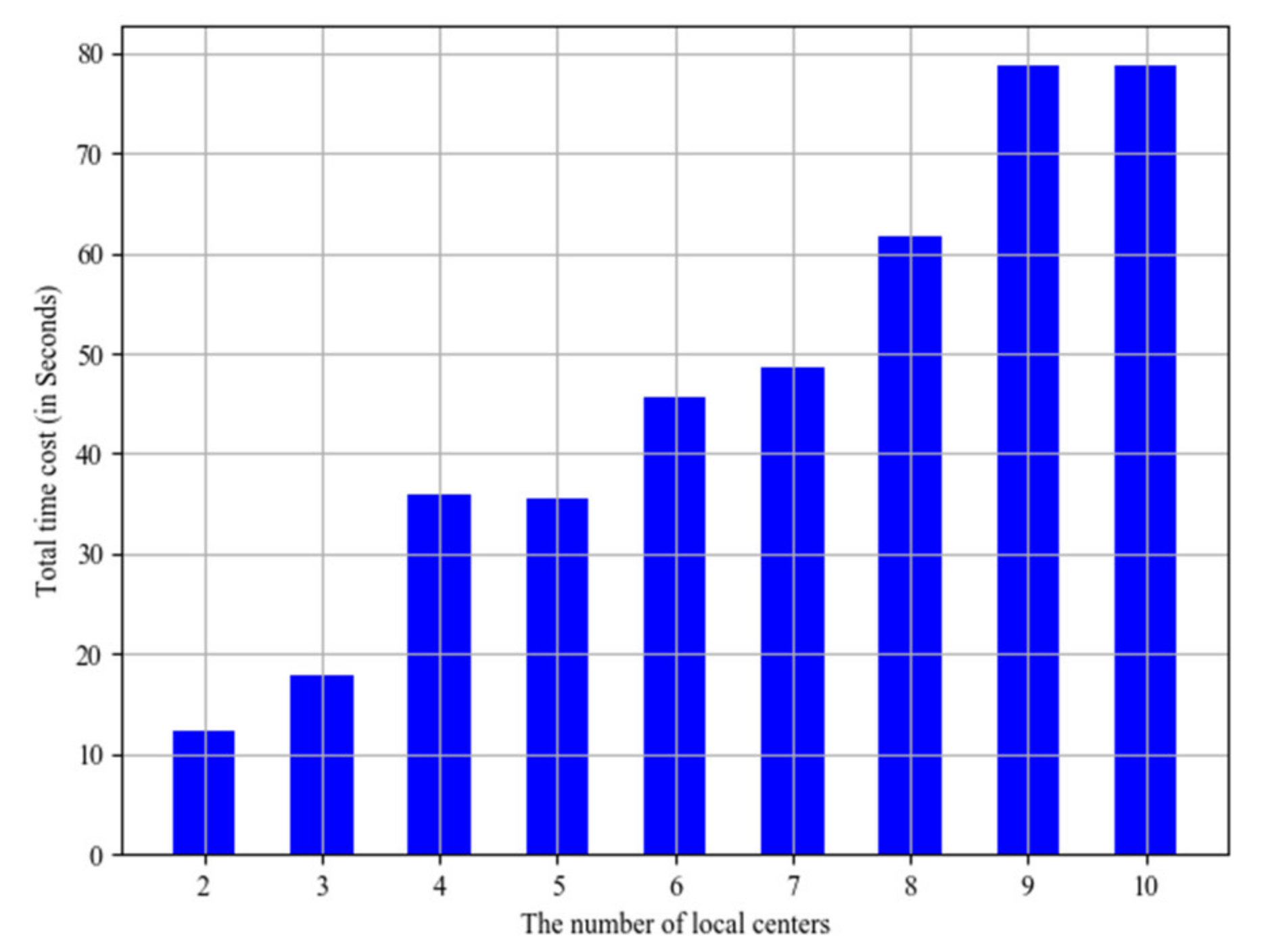
The number of local centers is increasing to evaluate the scalability of the system. The total time costs with different local center number are shown in
Figure 13, where the horizontal axis stands for the number of local centers, and the vertical axis stands for the corresponding total time cost. Obviously, the total time costs are increasing with the growth of the local center number. This shows that the player has spent much more time because of the increase of local center number. Moreover, the system is extendable.
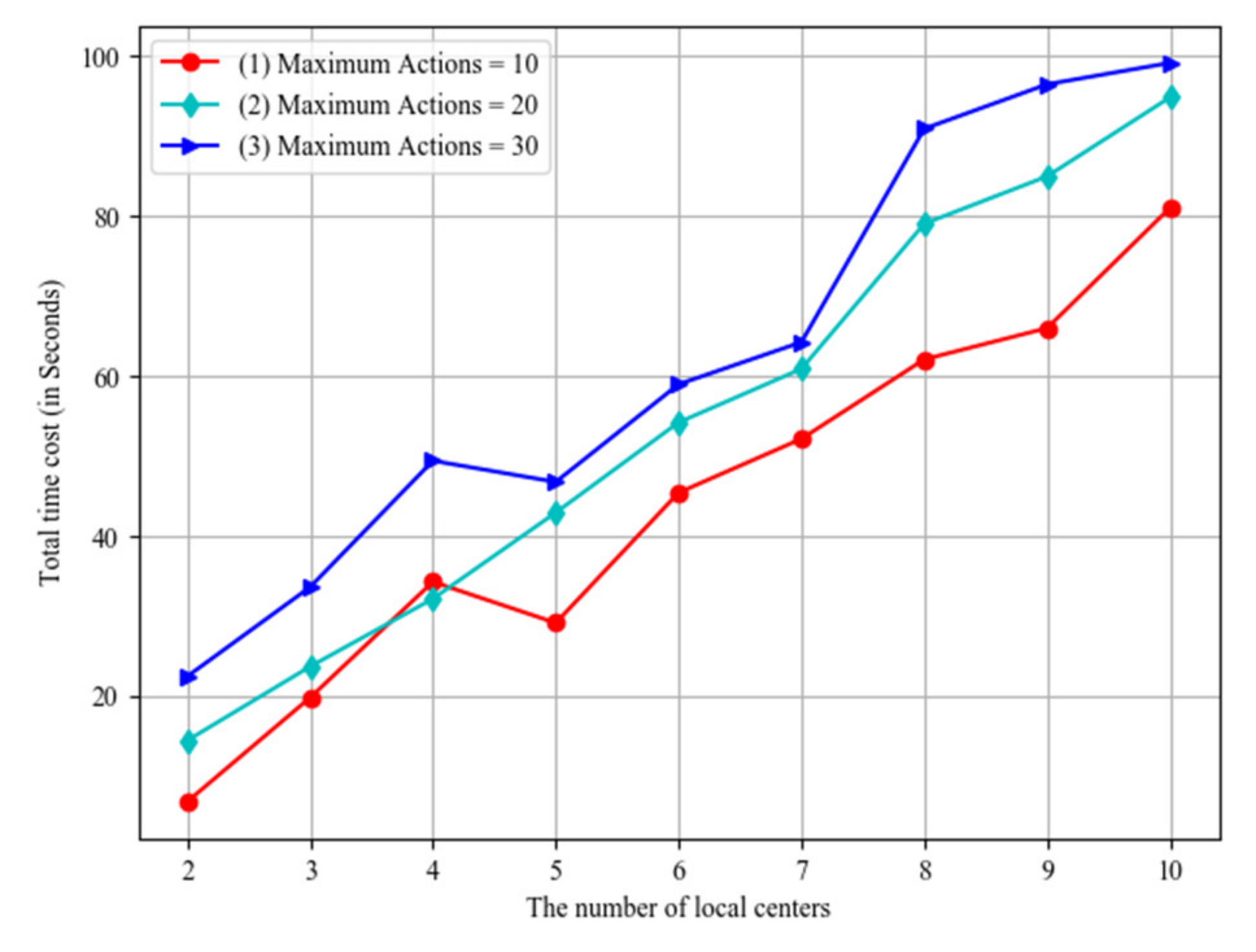
During the process of the game, a player would have interactions with the control system. The action number shows the capability of the player. That is, the level of the player is not high if he has used too many actions. The impact of the player actions is shown in
Figure 14, where the horizontal axis stands for the number of local centers, and the vertical axis stands for the total time costs. Line (1), line (2) and line (3) respectively show the results with maximum actions equaling 10, 20 and 30. The results demonstrate that the higher level of the player, the less time he would use.
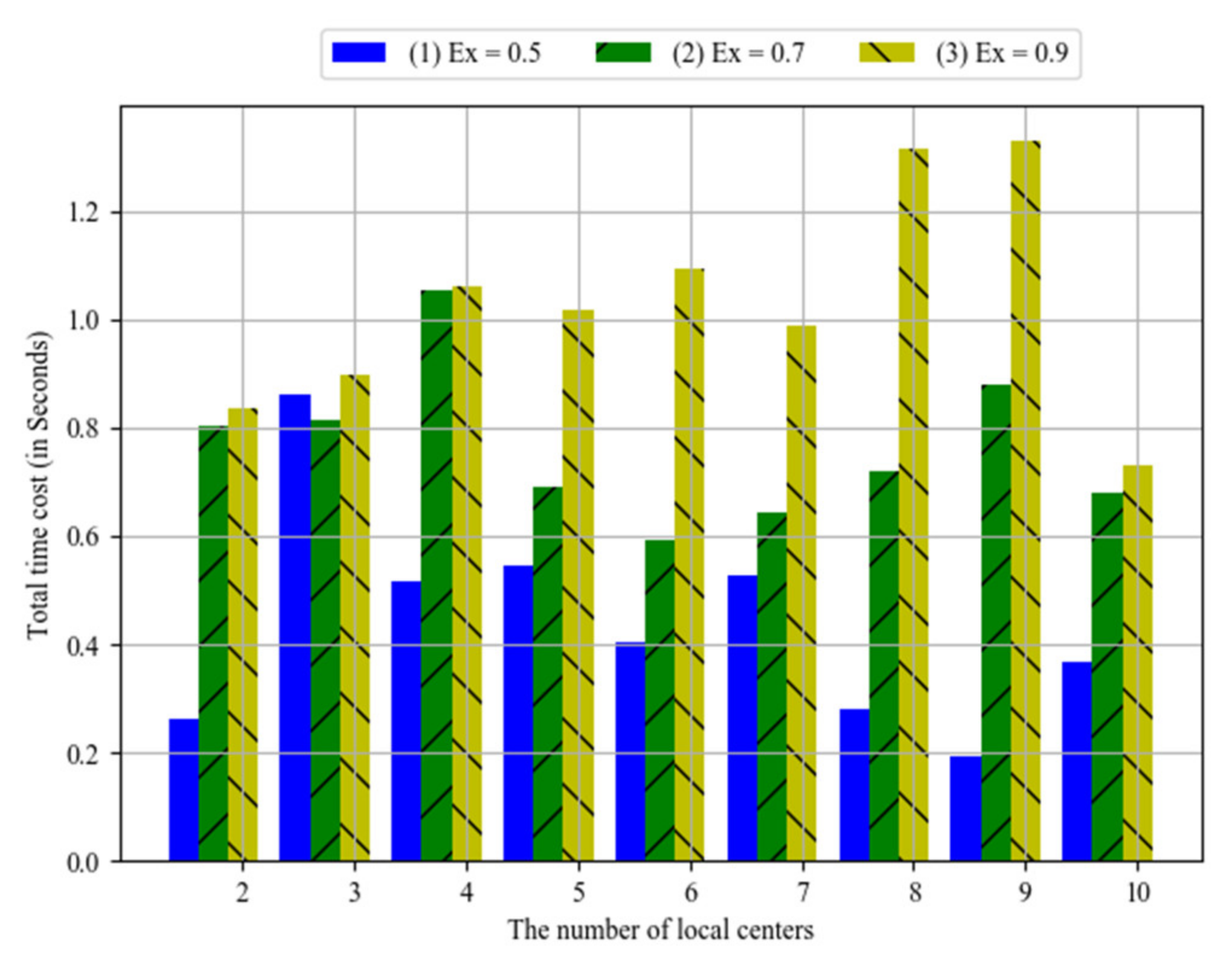
The system bus is very important for the communication between local centers and the control center. Its communication time might be affected by network conditions. Parameter
Ex could reflect different network conditions. For example, it would be a higher value for more congested network. The simulation results are shown in
Figure 15, where the horizontal axis stands for the number of local centers, and the vertical axis stands for the total time costs. Bar (1), bar (2) and bar (3) respectively show the results when
Ex equals 0.5, 0.7 and 0.9. Obviously, the total time costs increase with the values of
Ex. That is, the communication time of system bus is greater, the total time costs would be greater.
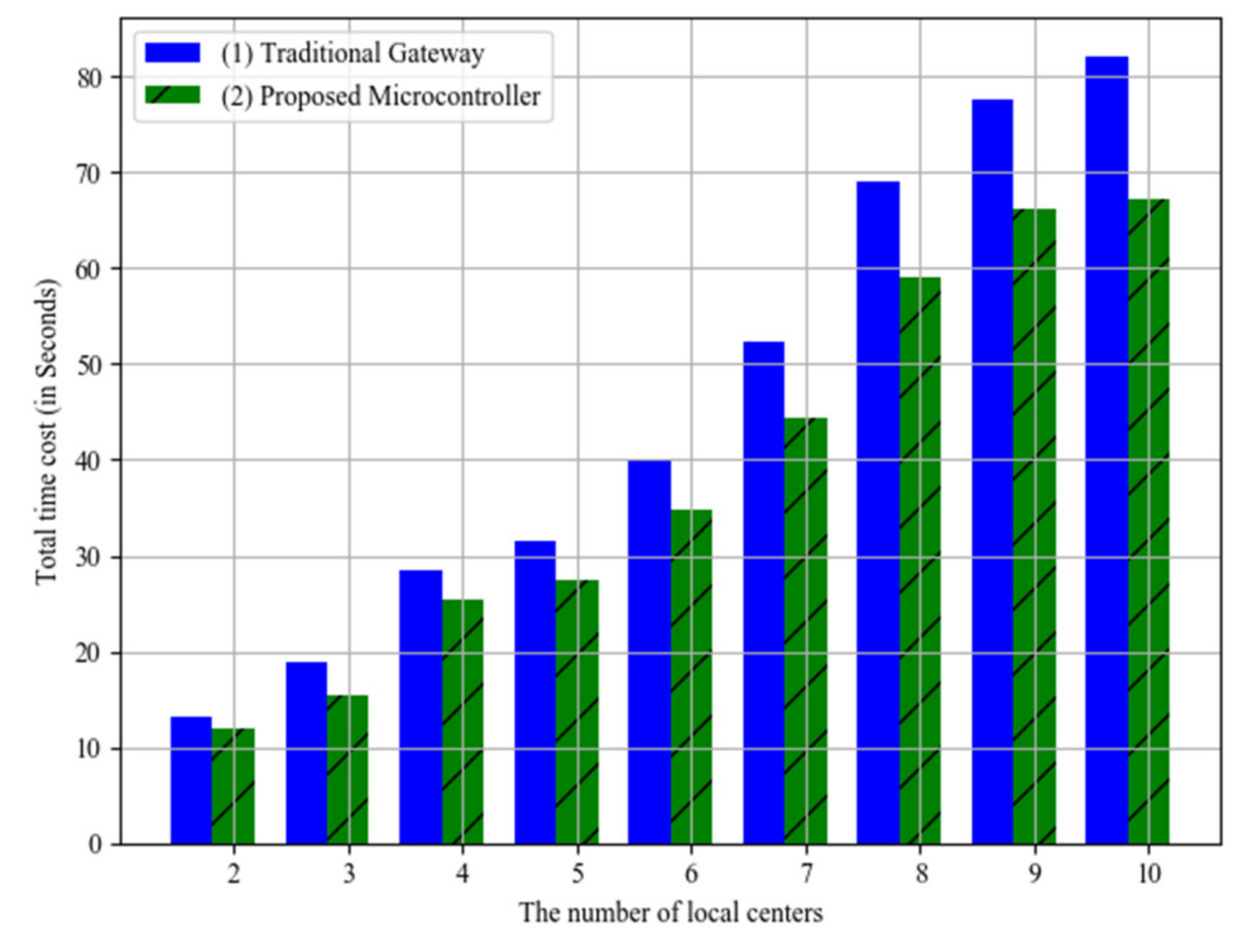
The efficiency comparations between the proposed microcontroller and the traditional gateway are shown in
Figure 16, where the horizontal axis stands for the number of local centers, and the vertical axis stands for the total time costs. In this simulation experiments, we assume that the traditional gateway only has network functions instead of intelligent data processing functions. The time costs of the proposed microcontroller are lower than those of the traditional gateway. The maximum difference value is 14.89 seconds when the local center number is 10, and the maximum difference value is 1.32 seconds when the local center number is 2. Moreover, the average difference value is 6.84 seconds. The average time saving rate is about 17.5%. This is because of the parallel working of the microcontrollers in the proposed architecture. Instead, the traditional gateway would send the data to control center for further processing.