A Survey of Using Swarm Intelligence Algorithms in IoT
Abstract
1. Introduction
- This paper introduces and summarizes more than 40 applications of SI in IoT—such as the WSN and UAV network, especially in the last three years;
- This paper compares 11 SI-based CH selection algorithms and 13 SI-based routing protocols in WSN applications;
- We summarize the validation platform and parameter selection of each method used in WSNs as well as their merits and demerits;
- We survey the state-of-art SI algorithms in IoT applications and discuss potential future development directions.
2. Swarm Intelligence Algorithms
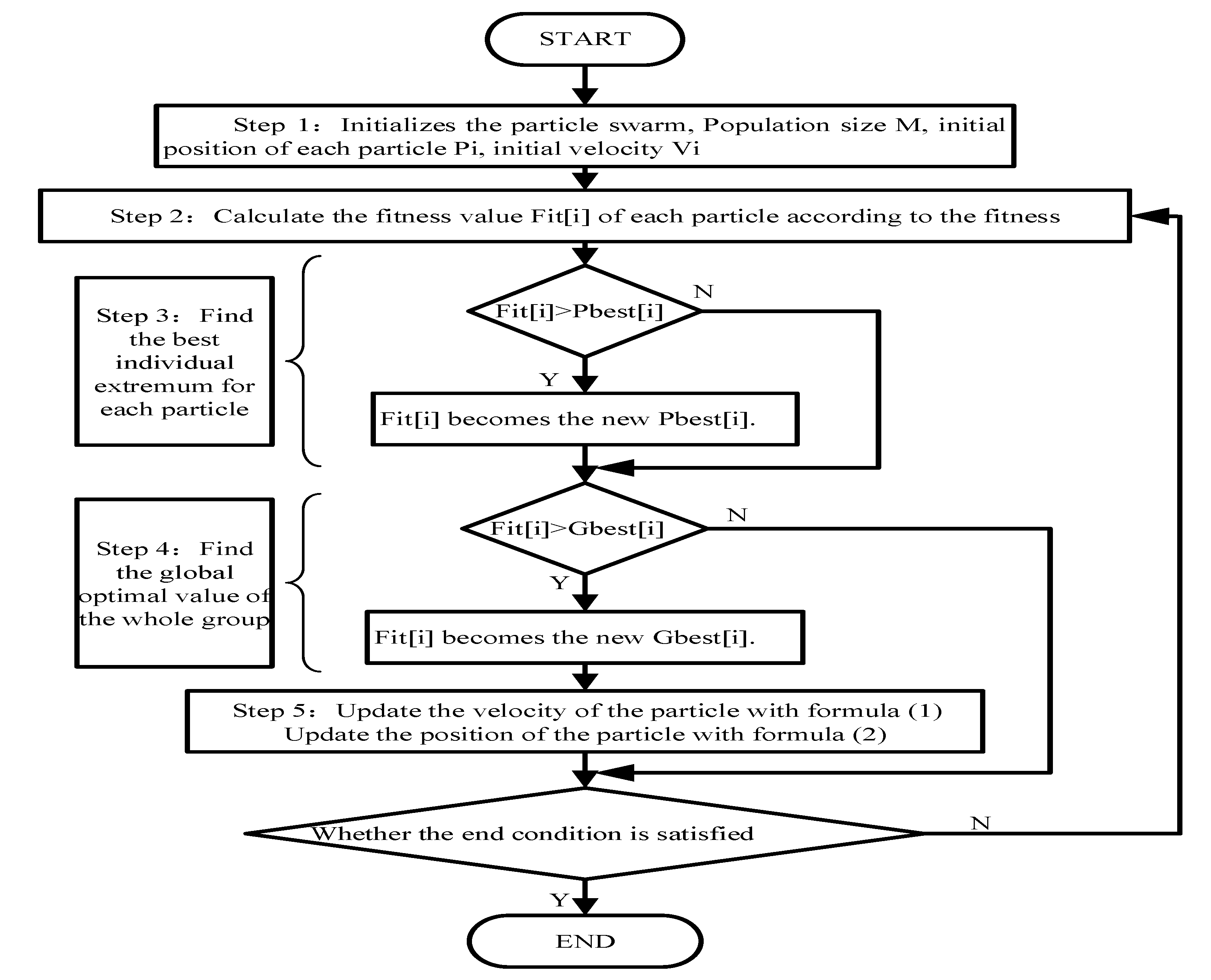
2.1. Particle Swarm Optimization (PSO)
2.2. Ant Colony Optimization (ACO)
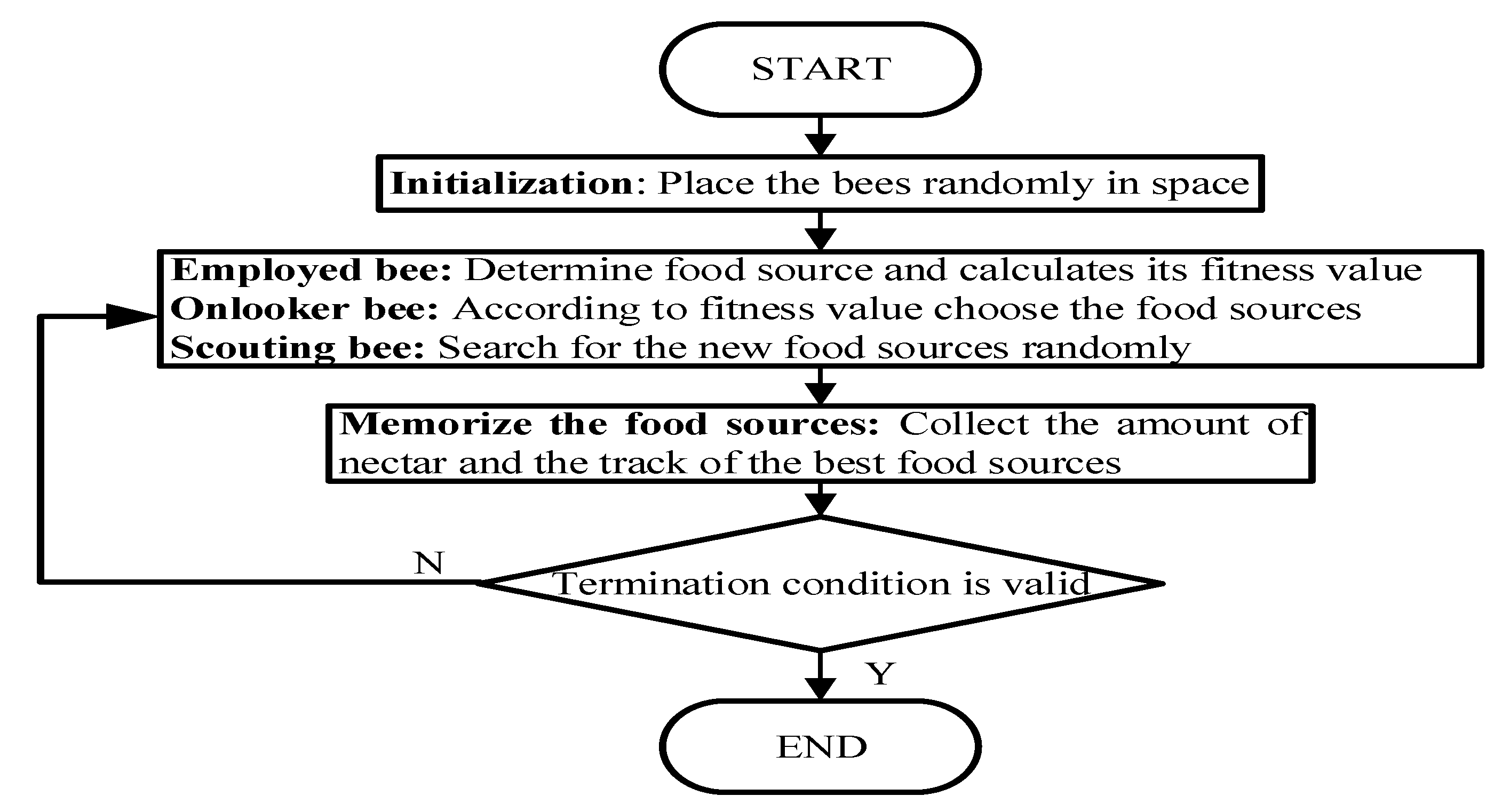
2.3. Artificial Bee Colony (ABC)
3. Applications of Swarm Intelligence Algorithms in WSN
3.1. CH Selection Algorithms Based on SI
3.1.1. Cluster Classification Properties
- Sensor coverage mode
- Clustering method
- The number of clusters
- The size of the cluster
- Intra-cluster communication method
- CH selection factors
3.1.2. CH Selection Algorithms Based on PSO
3.1.3. Cluster Head Selection Algorithm Based on ACO and ABC
3.2. WSN Routing Protocols Based on SI
3.2.1. Routing Protocol Classification Properties
- Distributed (D)/Centralized (C)
- Besteffort (B)/QoS (Q)
- Single path (S)/Multipath (M) routing
- Event-driven/Query-based routing
- Fault tolerant
- Energy aware
- Loop free
3.2.2. Wireless Sensor Routing Protocols Based on PSO
3.2.3. WSN Routing Protocols Based on ACO
3.3. SI Applications in Sensor Deployment
3.4. SI Applications in Node Localization
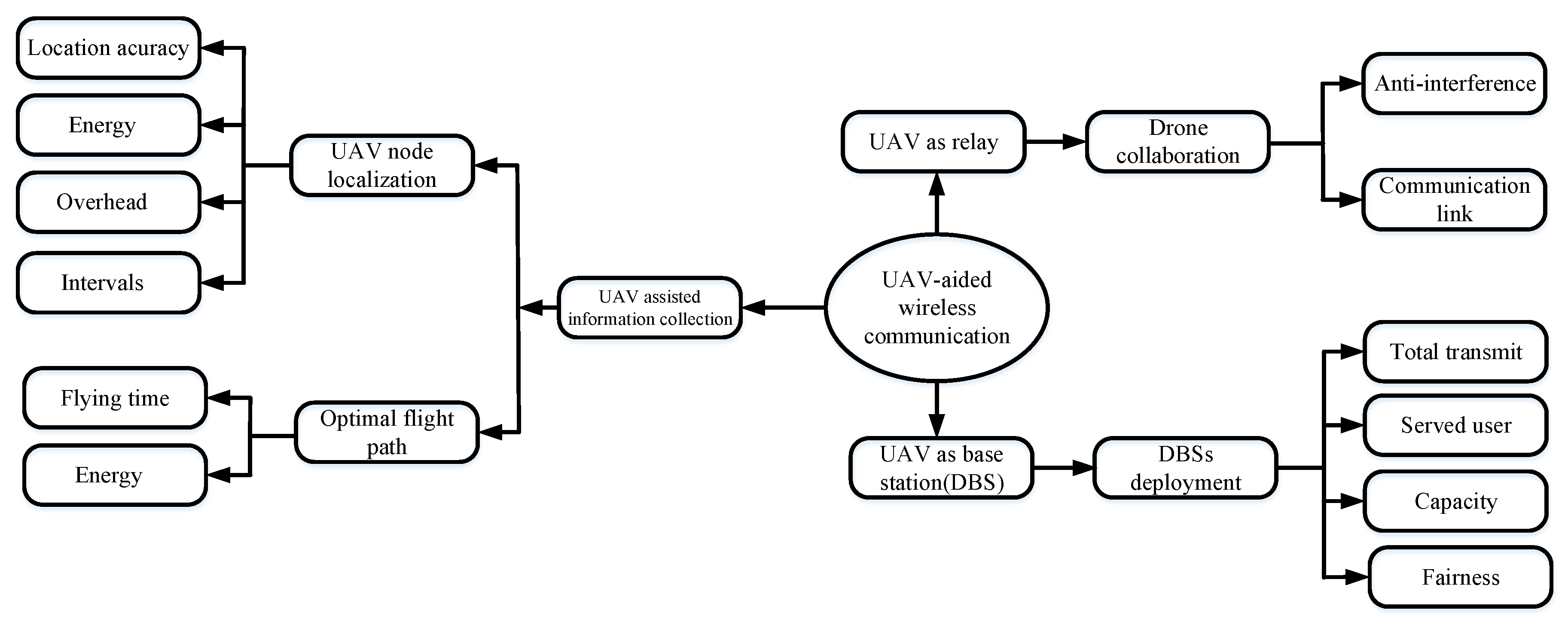
3.5. SI Applications in UAV-Aided WSNs
3.6. Parameters to Be Considered in the Validation of SI Applications in the WSN
4. Application of Swarm Intelligence Algorithms in UAV-Aided Wireless Networks
5. Application of Swarm Intelligence Algorithms in Other IoTs
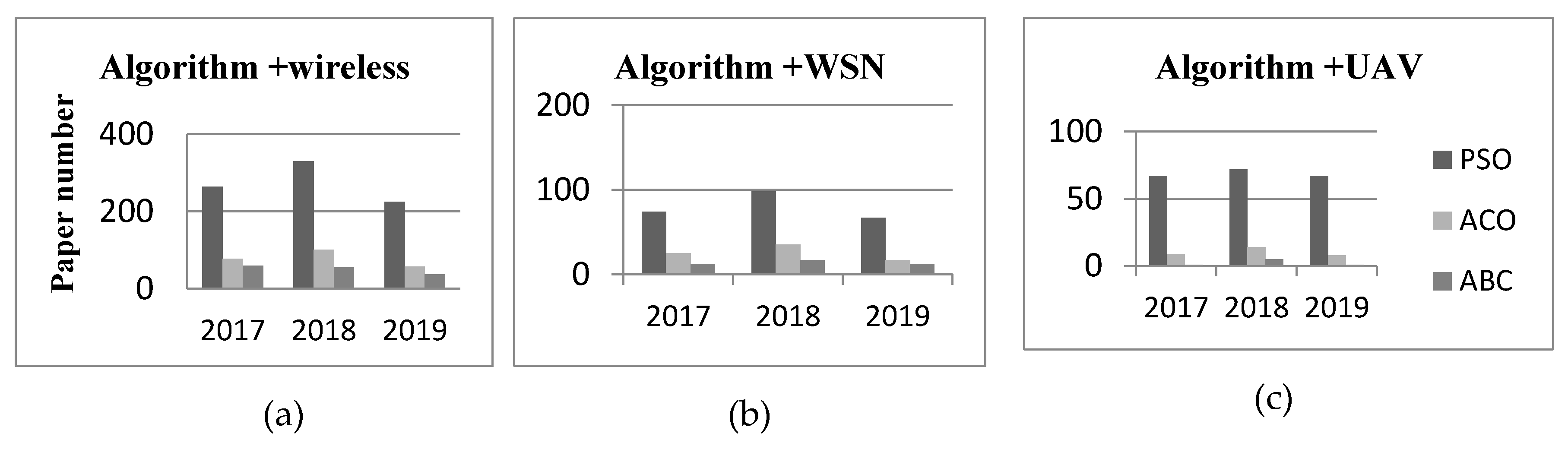
6. Analysis of the Verification Methods Adopted by SI in WSN and Problems
7. Current Situation and Development Trend
7.1. Current Statuses
7.2. Development Trend
7.2.1. SI Applications in More WSNs
7.2.2. Wireless Network Based on UAV
7.2.3. QoS Assuring on WSN
7.2.4. Intelligent Mobile Edge Computing
7.2.5. 5G Networks
7.2.6. Wireless Security Assured by SI Algorithms
8. Conclusions
Author Contributions
Funding
Acknowledgments
Conflicts of Interest
References
- Kennedy, J.Y. Swarm Intelligence; Morgan Kaufmann Publishers Inc.: San Francisco, CA, USA, 2001. [Google Scholar]
- Eberhart, R.; Kennedy, J. Particle swarm optimization. In Proceedings of the ICNN’95-International Conference on Neural Networks, Perth, WA, Australia, 27 November–1 December 1995; Volume 4, pp. 1942–1948. [Google Scholar]
- Dorigo, M.; di Caro, G.A. Ant colony optimization: A new meta-heuristic. In Proceedings of the 1999 congress on evolutionary computation-CEC99 (Cat. No. 99TH8406), Washington, DC, USA, 6–9 July 1999; Volume 2, pp. 1470–1477. [Google Scholar]
- Karaboga, D. An Idea Based on Honey Bee Swarm for Numerical Optimization; Technical report-tr06; Computer Engineering Department, Engineering Faculty, Erciyes University: Kayseri, Turkey, 2005; Volume 200, pp. 1–10. [Google Scholar]
- Passino, K.M. Biomimicry of bacterial foraging for distributed optimization and control. IEEE Control Syst. Mag. 2002, 22, 52–67. [Google Scholar]
- Arora, S.; Singh, S. Butterfly algorithm with Lèvy Flights for global optimization. In Proceedings of the 2015 International Conference on Signal Processing, Computing and Control (ISPCC), Waknaghat, India, 24–26 September 2015; pp. 220–224. [Google Scholar]
- Gubbi, J.; Buyya, R.; Marusic, S.; Palaniswami, M. Internet of Things (IoT): A vision, architectural elements, and future directions. Future Gener. Comput. Syst. 2013, 29, 1645–1660. [Google Scholar] [CrossRef]
- Mann, P.S.; Singh, S. wireless sensor networks. Soft Comput. 2017, 21, 6699–6712. [Google Scholar] [CrossRef]
- Saleem, M.; di Caro, G.A.; Farooq, M. Swarm intelligence based routing protocol for wireless sensor networks: Survey and future directions. Inf. Sci. 2011, 181, 4597–4624. [Google Scholar] [CrossRef]
- Sendra, S.; Parra, L.; Lloret, J.; Khan, S. Systems and algorithms for wireless sensor networks based on animal and natural behavior. Int. J. Distrib. Sens. Netw. 2015, 11, 625972. [Google Scholar] [CrossRef]
- Zedadra, O.; Guerrieri, A.; Jouandeau, N.; Spezzano, G.; Seridi, H.; Fortino, G. Swarm intelligence-based algorithms within IoT-based systems: A review. J. Parallel Distrib. Comput. 2018, 122, 173–187. [Google Scholar] [CrossRef]
- Kolias, C.; Kambourakis, G.; Maragoudakis, M. Swarm intelligence in intrusion detection: A survey. Comput. Secur. 2011, 30, 625–642. [Google Scholar] [CrossRef]
- Li, X.-L. An optimizing method based on autonomous animats: Fish-swarm algorithm. Syst. Eng. Theory Pract. 2002, 22, 32–38. [Google Scholar]
- Yang, X.S. Firefly algorithm. Nat. Inspired Metaheuristic Algorithms 2008, 20, 79–90. [Google Scholar]
- Duan, H.; Qiao, P. Pigeon-inspired optimization: A new swarm intelligence optimizer for air robot path planning. Int. J. Intell. Comput. Cybern. 2014, 7, 24–37. [Google Scholar] [CrossRef]
- Aravinth, S.S.; Senthilkumar, J.; Mohanraj, V.; Suresh, Y. A hybrid swarm intelligence based optimization approach for solving minimum exposure problem in wireless sensor networks. Concurr. Comput. Pract. Exp. 2019, 4, 819–827. [Google Scholar] [CrossRef]
- Karaboga, D.; Akay, B. A comparative study of artificial bee colony algorithm. Appl. Math. Comput. 2009, 214, 108–132. [Google Scholar] [CrossRef]
- Mann, P.S.; Singh, S. Energy-efficient hierarchical routing for wireless sensor networks: A swarm intelligence approach. Wirel. Pers. Commun. 2017, 92, 785–805. [Google Scholar] [CrossRef]
- Vijayalakshmi, K.; Anandan, P. A multi objective Tabu particle swarm optimization for effective cluster head selection in WSN. Clust. Comput. 2019, 22, 12275–12282. [Google Scholar] [CrossRef]
- Wang, J.; Cao, Y.; Kim, H.; Lee, S. Particle swarm optimization based clustering algorithm with mobile sink for WSNs. Future Gener. Comput. Syst. 2017, 76, 452–457. [Google Scholar] [CrossRef]
- Rao, P.C.S.; Jana, P.K.; Banka, H. A particle swarm optimization based energy efficient cluster head selection algorithm for wireless sensor networks. Wirel. Netw. 2017, 23, 2005–2020. [Google Scholar] [CrossRef]
- Tam, N.T.; Hai, D.T.; Son, l.; Vinh, l. Improving lifetime and network connections of 3D wireless sensor networks based on fuzzy clustering and particle swarm optimization. Wirel. Netw. 2018, 24, 1477–1490. [Google Scholar] [CrossRef]
- ME, A.T.; ME, J.J.S.; Priya, A.K.; Maarlin, R.; Harinetha, M. Energy aware heuristic approach for cluster head selection in wireless sensor networks. Bull. Electr. Eng. Inform. 2017, 6, 70–75. [Google Scholar]
- Wang, J.; Gao, Y.; Liu, W.; Sangaiah, A.K.; Kim, H.Y. An improved routing schema with special clustering using PSO algorithm for heterogeneous wireless sensor network. Sensors 2019, 19, 671. [Google Scholar] [CrossRef]
- Wang, J.; Cao, J.; Sherratt, R.S.; Park, J.H. An improved ant colony optimization-based approach with mobile sink for wireless sensor networks. J. Supercomput. 2018, 74, 6633–6645. [Google Scholar] [CrossRef]
- Gajjar, S.; Sarkar, M.; Dasgupta, K. FAMACROW: Fuzzy and ant colony optimization based combined mac, routing, and unequal clustering cross-layer protocol for wireless sensor networks. Appl. Soft Comput. J. 2016, 43, 235–247. [Google Scholar] [CrossRef]
- Kumar, R.; Kumar, D.; Kumar, D. EACO and FABC to multi-path data transmission in wireless sensor networks. IET Commun. 2017, 11, 522–530. [Google Scholar] [CrossRef]
- Shokouhifar, M.; Jalali, A. Optimized sugeno fuzzy clustering algorithm for wireless sensor networks. Eng. Appl. Artif. Intell. 2017, 60, 16–25. [Google Scholar] [CrossRef]
- Mann, P.S.; Singh, S. Improved metaheuristic-based energy-efficient clustering protocol with optimal base station location in wireless sensor networks. Soft Comput. 2019, 23, 1021–1037. [Google Scholar] [CrossRef]
- Zhou, Y.; Wang, N.; Xiang, W. Clustering hierarchy protocol in wireless sensor networks using an improved PSO algorithm. IEEE Access 2016, 5, 2241–2253. [Google Scholar] [CrossRef]
- Hasan, M.Z.; Al-Turjman, F. Optimizing multipath routing with guaranteed fault tolerance in Internet of Things. IEEE Sens. J. 2017, 17, 6463–6473. [Google Scholar] [CrossRef]
- Sun, Y.; Dong, W.; Chen, Y. An improved routing algorithm based on ant colony optimization in wireless sensor networks. IEEE Commun. Lett. 2017, 21, 1317–1320. [Google Scholar] [CrossRef]
- Sun, Z.; Wei, M.; Zhang, Z.; Qu, G. Secure Routing Protocol based on Multi-objective Ant-colony-optimization for wireless sensor networks. Appl. Soft Comput. 2019, 77, 366–375. [Google Scholar] [CrossRef]
- Li, C.; Zhang, H.; Hao, B.; Li, J. A survey on routing protocols for large-scale wireless sensor networks. Sensors 2011, 11, 3498–3526. [Google Scholar] [CrossRef]
- Rosset, V.; Paulo, M.A.; Cespedes, J.G.; Nascimento, M.C.V. Enhancing the reliability on data delivery and energy efficiency by combining swarm intelligence and community detection in large-scale WSNs. Expert Syst. Appl. 2017, 78, 89–102. [Google Scholar] [CrossRef]
- Wang, J.; Ju, C.; Gao, Y.; Sangaiah, A.K.; Kim, G.-J. A PSO based energy efficient coverage control algorithm for wireless sensor networks. Comput. Mater. Contin. 2018, 56, 433–446. [Google Scholar]
- Ke, W.-C.; Liu, B.-H.; Tsai, M.-J. Constructing a wireless sensor network to fully cover critical grids by deploying minimum sensors on grid points is NP-complete. IEEE Trans. Comput. 2007, 56, 710–715. [Google Scholar] [CrossRef]
- Deif, D.S.; Gadallah, Y. An ant colony optimization approach for the deployment of reliable wireless sensor networks. IEEE Access 2017, 5, 10744–10756. [Google Scholar] [CrossRef]
- Kaur, R.; Arora, S. Nature Inspired Range Based Wireless Sensor Node Localization Algorithms. Int. J. Interact. Multimed. Artif. Intell. 2017, 4, 7–17. [Google Scholar] [CrossRef]
- Raguraman, P.; Ramasundaram, M.; Balakrishnan, V. Localization in wireless sensor networks: A dimension based pruning approach in 3D environments. Appl. Soft Comput. 2018, 68, 219–232. [Google Scholar] [CrossRef]
- Arora, S.; Singh, S. Node localization in wireless sensor networks using butterfly optimization algorithm. Arab. J. Sci. Eng. 2017, 42, 3325–3335. [Google Scholar] [CrossRef]
- Yang, Q.; Yoo, S.-J. Optimal UAV path planning: Sensing data acquisition over IoT sensor networks using multi-objective bio-inspired algorithms. IEEE Access 2018, 6, 13671–13684. [Google Scholar] [CrossRef]
- Ari, A.A.A.; Damakoa, I.; Gueroui, A.; Titouna, C.; Labraoui, N.; Kaladzavi, G.; Yenké, B.O. Bacterial foraging optimization scheme for mobile sensing in wireless sensor networks. Int. J. Wirel. Inf. Netw. 2017, 24, 254–267. [Google Scholar] [CrossRef]
- Zhou, Z.; Zhao, D.; Liu, L.; Hung, P.C.K. Energy-aware composition for wireless sensor networks as a service. Future Gener. Comput. Syst. 2018, 80, 299–310. [Google Scholar] [CrossRef]
- Yun, X.; Bachmann, E.R.; Moore, H.; Calusdian, J. Self-contained position tracking of human movement using small inertial/magnetic sensor modules. In Proceedings of the IEEE International Conference on Robotics and Automation, Rome, Italy, 10–14 April 2007; pp. 2526–2533. [Google Scholar]
- Zeng, Y.; Zhang, R.; Lim, T.J. Wireless communications with unmanned aerial vehicles: Opportunities and challenges. IEEE Commun. Mag. 2016, 54, 36–42. [Google Scholar] [CrossRef]
- Kalantari, E.; Bor-Yaliniz, I.; Yongacoglu, A.; Yanikomeroglu, H. User association and bandwidth allocation for terrestrial and aerial base stations with backhaul considerations. In Proceedings of the 28th IEEE Annual International Symposium on Personal, Indoor and Mobile Radio Communications (PIMRC), Montreal, QC, Canada, 8–13 October 2017; pp. 1–6. [Google Scholar]
- Akarsu, A.; Girici, T. Fairness aware multiple drone base station deployment. IET Commun. 2017, 12, 425–431. [Google Scholar] [CrossRef]
- Shakhatreh, H.; Khreishah, A.; Alsarhan, A.; Khalil, I.; Sawalmeh, A.; Othman, N.S. Efficient 3D placement of a UAV using particle swarm optimization. In Proceedings of the 2017 8th International Conference on Information and Communication Systems (ICICS), Irbid, Jordan, 4–6 April 2017; pp. 258–263. [Google Scholar]
- Arafat, M.Y.; Moh, S. Localization and clustering based on swarm intelligence in UAV networks for emergency communications. IEEE IoTJ. 2019, 6, 8958–8976. [Google Scholar] [CrossRef]
- Zhang, X.; Zhang, X.; Gu, C. A micro-artificial bee colony based multicast routing in vehicular ad hoc networks. Ad Hoc Netw. 2017, 58, 213–221. [Google Scholar] [CrossRef]
- Hamrioui, S.; Lorenz, P. Bio inspired routing algorithm and efficient communications within IoT. IEEE Netw. 2017, 31, 74–79. [Google Scholar] [CrossRef]
- Kumrai, T.; Ota, K.; Dong, M.; Kishigami, J.; Sung, D.K. Multiobjective optimization in cloud brokering systems for connected Internet of Things. IEEE IoTJ. 2016, 4, 404–413. [Google Scholar] [CrossRef]
- Elhoseny, M.; Abdelaziz, A.; Salama, A.S.; Riad, A.M.; Muhammad, K.; Sangaiah, A.K. A hybrid model of internet of things and cloud computing to manage big data in health services applications. Future Gener. Comput. Syst. 2018, 86, 1383–1394. [Google Scholar] [CrossRef]
- Lin, J.C.; Wu, J.M.; Fournier-Viger, P.; Djenouri, Y.; Chen, C.; Zhang, Y. A Sanitization Approach to Secure Shared Data in an IoT Environment. IEEE Access 2019, 7, 25359–25368. [Google Scholar] [CrossRef]
- Lin, Y.H.; Hu, Y.C. Residential Consumer-Centric Demand-Side Management Based on Energy Disaggregation-Piloting Constrained Swarm Intelligence: Towards Edge Computing. Sensors 2018, 18, 1365. [Google Scholar] [CrossRef]
- Qiu, T.; Li, B.; Zhou, X.; Song, H.; Lee, I.; Ioret, J.L. A Novel Shortcut Addition Algorithm with Particle Swarm for Multi-sink Internet of Things. IEEE Trans. Ind. Inform. 2020, 16, 3566–3577. [Google Scholar] [CrossRef]
- Pan, Q.; Ni, Q.; Du, H.; Yao, Y.; Lv, Q. An improved energy-aware cluster heads selection method for wireless sensor networks based on k-means and binary particle swarm optimization. In International Conference in Swarm Intelligence; Springer: Cham, Switzerland, October 2014; pp. 125–134. [Google Scholar]
- Collotta, M.; Pau, G.; Maniscalco, V. A fuzzy logic approach by using particle swarm optimization for effective energy management in IWSNs. IEEE Trans. Ind. Electron. 2017, 64, 9496–9506. [Google Scholar] [CrossRef]
- Kim, S.S.; McLoone, S.; Byeon, J.-H.; Lee, S.; Liu, H. Cognitively inspired artificial bee colony clustering for cognitive wireless sensor networks. Cogn. Comput. 2017, 9, 207–224. [Google Scholar] [CrossRef]
- Lewandowski, M.; Płaczek, B. An Event-Aware Cluster-Head Rotation Algorithm for Extending Lifetime of Wireless Sensor Network with Smart Nodes. Sensors 2019, 19, 4060. [Google Scholar] [CrossRef] [PubMed]
- Hamdi, M.; Zaied, M. Resource allocation based on hybrid genetic algorithm and particle swarm optimization for D2D multicast communications. Appl. Soft Comput. 2019, 83, 105605. [Google Scholar] [CrossRef]




| Abbreviations | Instructions | Abbreviations | Instructions |
|---|---|---|---|
| WSN | Wireless sensor network | UAV | Unmanned aerial vehicle |
| PSO | Particle swarm optimization | CH | Cluster head |
| ABC | Artificial bee colony | MS | Master station |
| BOA | Butterfly optimization algorithm | LP | Label propagation algorithm |
| FCM | Fuzzy c-means algorithm | BS | Base station |
| LS | Local search | DBS | Drone base station |
| GA | Genetic algorithm | VANET | Vehicular ad-hoc network |
| IoT | Internet of Things | ACO | Ant colony algorithm |
| GWO | Grey wolf optimization | DBS | UAV as a base station |
| LEACH | Low energy adaptive Clustering hierarchy | BFO | Bacterial foraging algorithm |
| Parameter | Meaning |
|---|---|
| relative importance of the heuristic factor | |
| collection of cities that ant k allows selecting in the next step | |
| times | |
| pheromone on the edge | |
| visibility of pheromones on edge (i,j) | |
| distance between cities | |
| number of ants | |
| ant number | |
| number of cities | |
| pheromone increment on edge of this iteration | |
| pheromone quantity on edge left by the ant k in this iteration | |
| pheromone evaporation (volatilization) coefficient 1- is the persistence (residual) coefficient where 0 < < 1 | |
| probability of ant k moving from city i to city j at time t (transition probability) | |
| tabu list for ant k |
| Method | Year | Key Technology | Uniform (U)/ Random (R) | Static(S)/ Dynamic (D) | Number of Clusters | Size of the Cluster | Multi-hop(M)/Single-hop(S) | CH Selection Factor |
|---|---|---|---|---|---|---|---|---|
| LEACH | 2000 | — | R | S | V | V | S | Cyclic random |
| [19] | 2018 | PSO Tabu | R | S | V | V | M | E |
| [20] | 2016 | PSO | R | S | F | F | S | E,C |
| [21] | 2016 | PSO | R | D | F | V | S | E,D2S,C average intra-cluster distance |
| [22] | 2016 | PSO FCM | R | S | F | F | S | - |
| [23] | 2017 | PSO BFO | R | S | V | V | S | E |
| [24] | 2019 | PSO | R | S | F | V | M | E |
| [25] | 2017 | ACO | U | S | F | F | M | Initial: E Below threshold: E,C |
| [26] | 2016 | ACO | R | D | F | F | M | E,D2N, LQI |
| [27] | 2017 | EACO FABC | U | D | F | F | M | E,C,delay |
| [28] | 2017 | ABC FCM | R | D | F | F | S | E,D2S,C |
| [29] | 2017 | ABC | R | D | F | V | S | E,D2B |
| Method | Year | Key Technology | Distributed (D)/ Centralized (C) | BestEffort (B)/QoS (Q) | Single Path (S)/Multipath (M) Routing | Event-Driven (E)/Query-Based (Q) | Fault Tolerant | Energy Aware | Loop Free |
|---|---|---|---|---|---|---|---|---|---|
| [19] | 2018 | PSO Tabu | D | B | S | E | N | N | N |
| [20] | 2016 | PSO | D | B | S | Q | N | Y | N |
| [24] | 2019 | PSO | D | B | S | Q | N | Y | N |
| [30] | 2016 | PSO | D | B | S | QE | N | Y | N |
| [31] | 2017 | PSO | D | Q | M | E | Y | N | N |
| [25] | 2017 | ACO | D | B | S | E | Y | Y | N |
| [26] | 2016 | ACO | D | B | S | QE | N | Y | N |
| [27] | 2017 | EACO FABC | D | B | M | E | Y | Y | N |
| [32] | 2017 | ACO | D | B | S | E | N | Y | N |
| [33] | 2019 | ACO | D | Q | S | E | Y | Y | N |
| [35] | 2017 | ACO LP | D | B | S/M | E | N | Y | N |
| [28] | 2017 | ABC FCM | C | B | S | Q | N | N | N |
| [29] | 2017 | ABC | D | Q | S | E | N | Y | N |
| Method | Package Loss | Delay | Packets Received | Run Time | Energy Consumption | Life Time | Active Node Ratio | Other |
|---|---|---|---|---|---|---|---|---|
| [19] | Y | Y | N | N | N | N | Y | - |
| [20] | N | Y | N | N | Y | Y | N | - |
| [21] | N | N | Y | N | Y | Y | Y | - |
| [22] | N | N | N | N | Y | N | N | Connection rate |
| [23] | N | N | N | N | Y | N | N | - |
| [24] | N | N | N | N | Y | Y | N | Number of hops |
| [25] | N | N | Y | N | Y | Y | N | - |
| [26] | N | Y | Y | N | Y | Y | Y | Throughput |
| [27] | N | N | N | N | Y | N | N | - |
| [28] | N | N | Y | Y | N | Y | N | Throughput |
| [29] | N | Y | Y | N | Y | Y | N | - |
| [30] | N | N | N | N | Y | Y | Y | Throughput |
| [31] | N | Y | N | N | Y | N | N | - |
| [32] | N | N | N | N | Y | Y | N | Path length, Packet deliver |
| [33] | Y | N | N | N | Y | N | N | Routing load, Throughput |
| [35] | N | Y | N | N | Y | N | N | - |
| [36] | N | N | N | N | Y | N | N | Coverage rate, Sensing radius of nodes |
| [38] | N | N | N | N | N | N | N | Deployment cost |
| [40] | N | N | N | N | N | N | N | Target nodes, Convergence behavior, Location |
| [41] | N | N | N | N | N | N | N | Node localization |
| Simulation Platform | Percentage |
|---|---|
| Did not mention | 32.4 |
| MATLAB | 38.3 |
| Java | 5.9 |
| Ns2 | 5.9 |
| OMNeT++/Castalia | 8.8 |
| jMetal | 2.9 |
| CloudSim package | 2.9 |
| QT Creator 2.4.0 | 2.9 |
| Number of Scenarios | Percentage |
|---|---|
| One or two | 61.8 |
| Three or four | 17.6 |
| At least five | 20.6 |
© 2020 by the authors. Licensee MDPI, Basel, Switzerland. This article is an open access article distributed under the terms and conditions of the Creative Commons Attribution (CC BY) license (http://creativecommons.org/licenses/by/4.0/).
Share and Cite
Sun, W.; Tang, M.; Zhang, L.; Huo, Z.; Shu, L. A Survey of Using Swarm Intelligence Algorithms in IoT. Sensors 2020, 20, 1420. https://doi.org/10.3390/s20051420
Sun W, Tang M, Zhang L, Huo Z, Shu L. A Survey of Using Swarm Intelligence Algorithms in IoT. Sensors. 2020; 20(5):1420. https://doi.org/10.3390/s20051420
Chicago/Turabian StyleSun, Weifeng, Min Tang, Lijun Zhang, Zhiqiang Huo, and Lei Shu. 2020. "A Survey of Using Swarm Intelligence Algorithms in IoT" Sensors 20, no. 5: 1420. https://doi.org/10.3390/s20051420
APA StyleSun, W., Tang, M., Zhang, L., Huo, Z., & Shu, L. (2020). A Survey of Using Swarm Intelligence Algorithms in IoT. Sensors, 20(5), 1420. https://doi.org/10.3390/s20051420






