Data Security and Trading Framework for Smart Grids in Neighborhood Area Networks
Abstract
1. Introduction
2. SG-Trading Systems and Data Security—State-of-the-Art
2.1. Trading Systems for SG Prosumers
2.2. Auctions in the Electricity Systems and the Preston McAfee
- Individual Rationality (IR)—A trading user should have positive utility. The IR is a necessary property for a price mechanism.
- Incentive Compatibility (IC)—Reporting the true value is a dominant strategy.
- Balanced Budget (BB)—The auctioneer should not lose or gain from the trade. For real-world applications, if the auctioneer does not have to subsidize the trade (called weakly BB property), then it is acceptable.
- Economic Efficiency (EE)—The social welfare should be maximized.
2.3. Data Security and Privacy in the Smart Grid
2.4. Cryptographic Solutions for the SG
2.5. Blockchain in the Smart Grid
3. Requirements for the NAN Architecture and Security Framework
4. Proposed Framework for the NAN Electricity Trading System
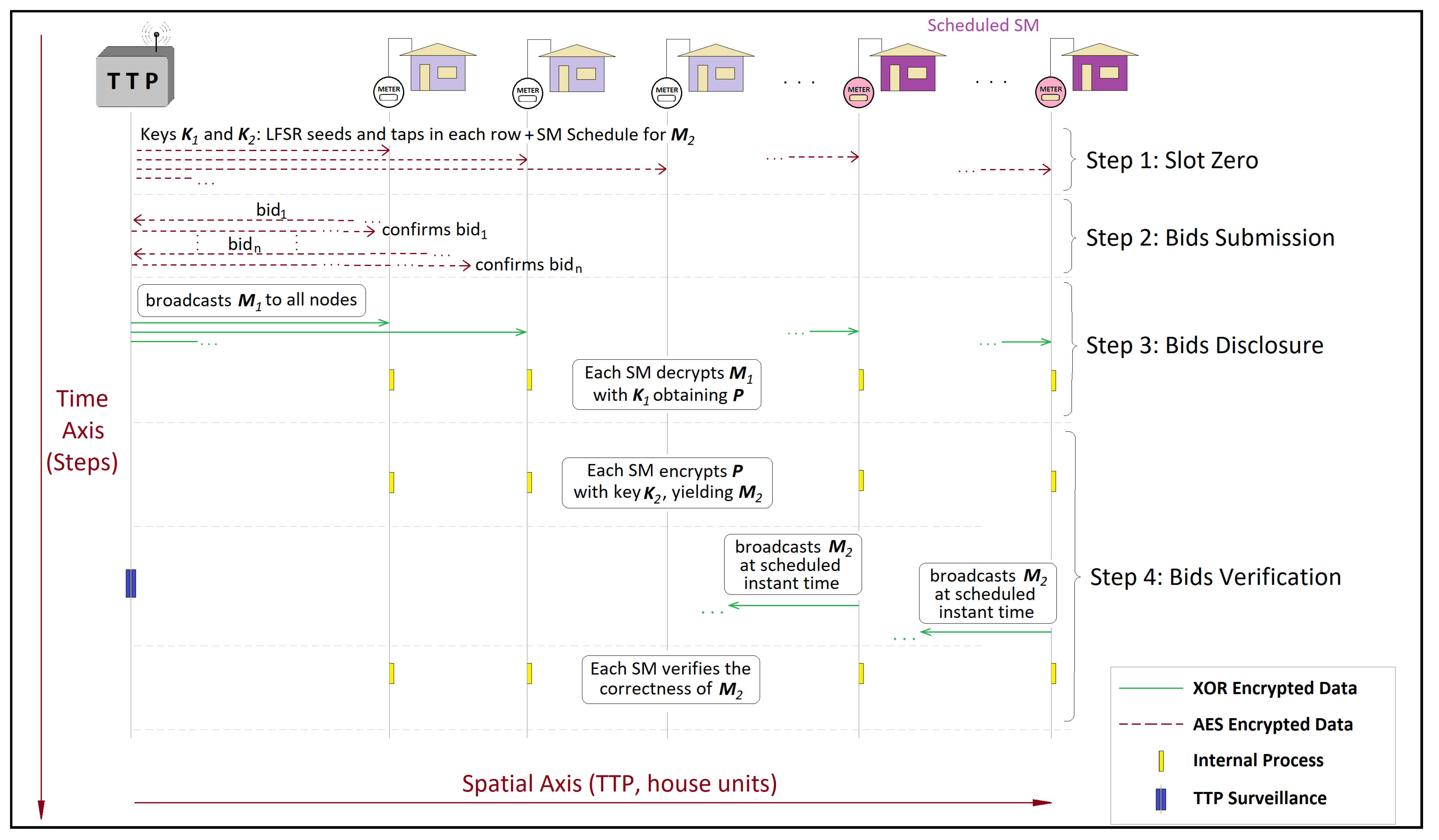
4.1. Privacy-Oriented Data-Security System
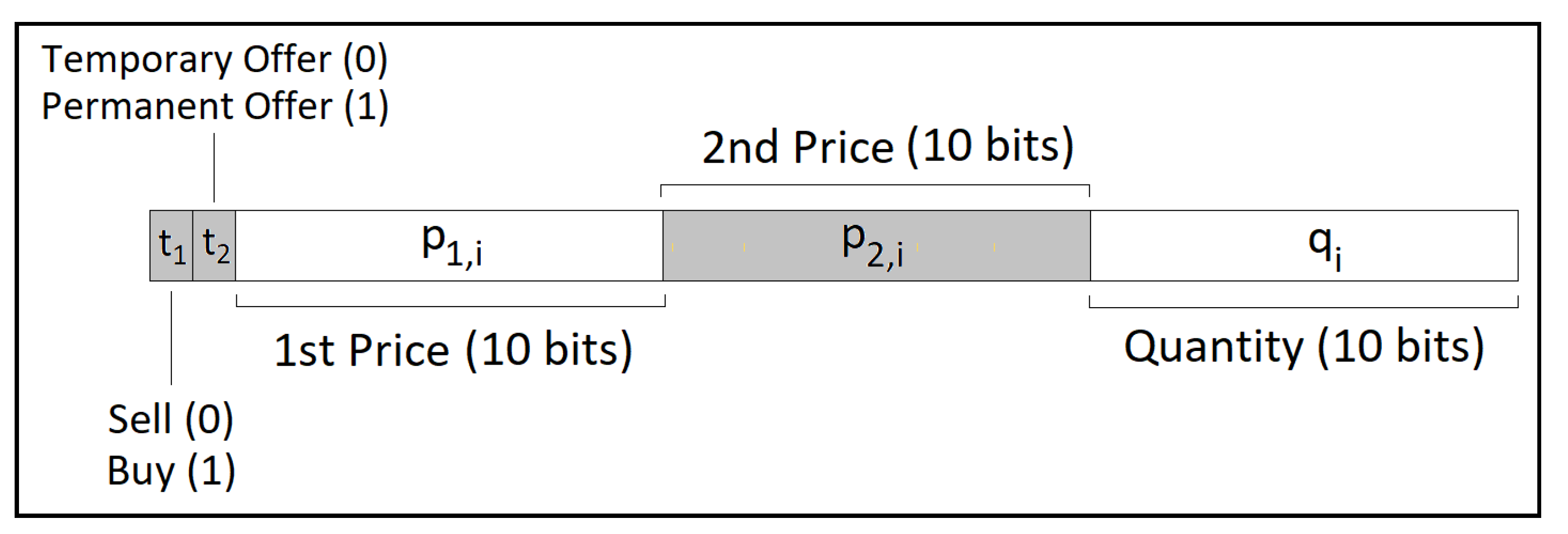
4.2. Trading System Framework
| Algorithm 1 Adapted Trade Reduction Mechanism (TRM) algorithm |
|
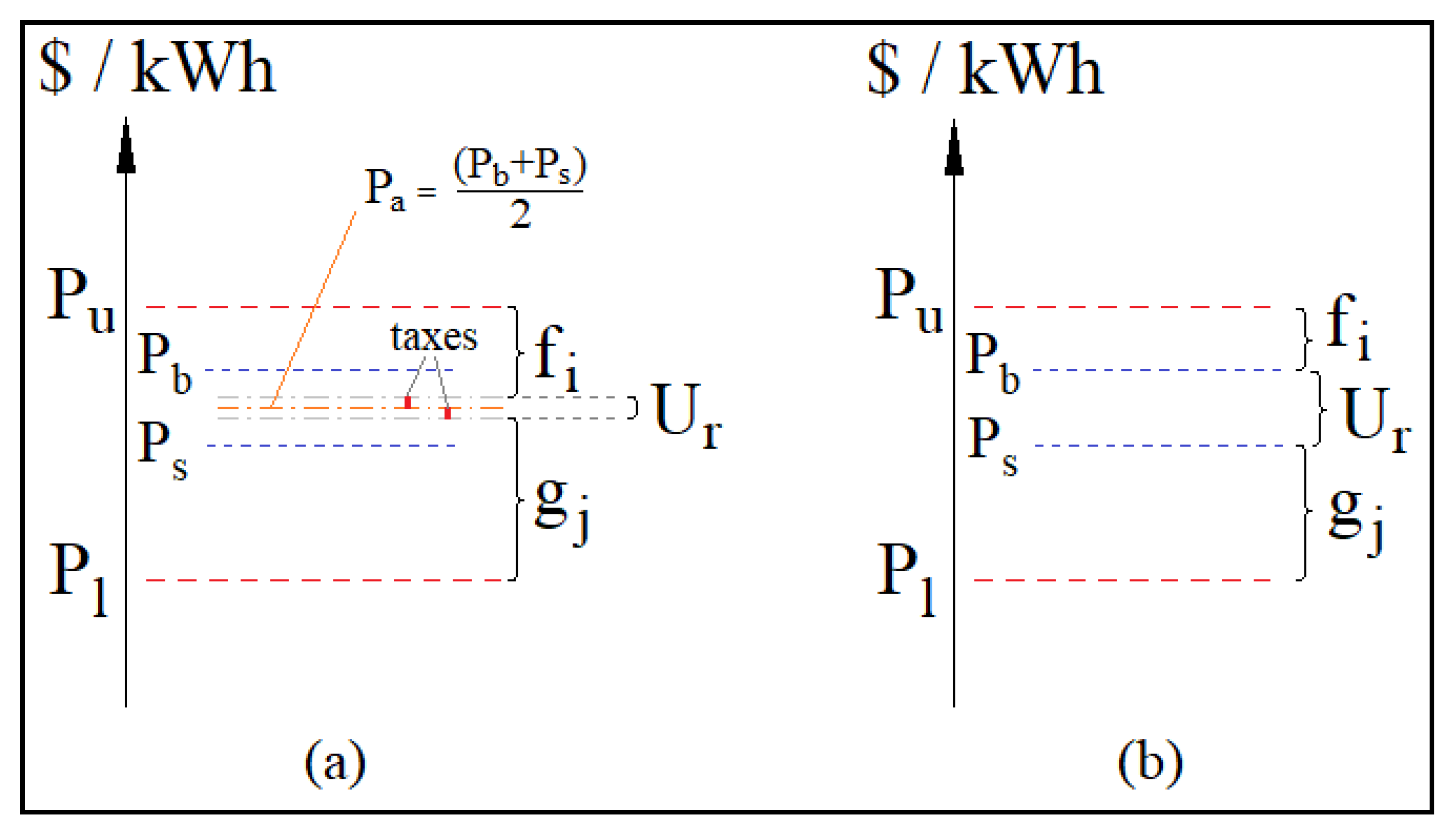
4.3. Social Welfare of the Proposed System
5. Results
5.1. Security and Computational Cost Analysis
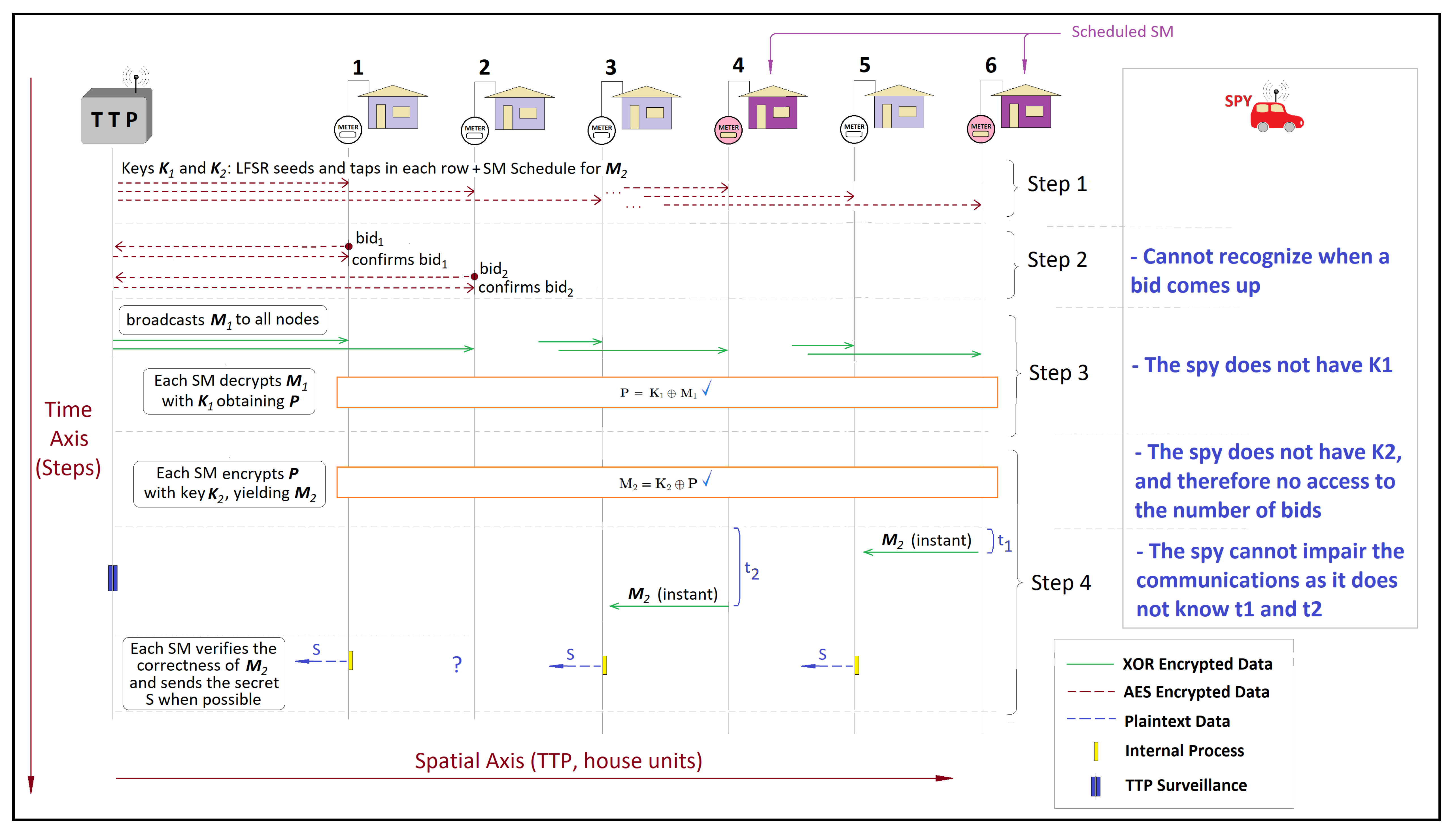
5.1.1. Privacy Threats Along Stages of the Proposed Framework
5.1.2. Security and Privacy Features
5.2. Comparison with the State-of-the-Art Privacy and Trading Systems
6. Conclusions
Author Contributions
Funding
Acknowledgments
Conflicts of Interest
Abbreviations
| NAN | Neighborhood Area Network |
| AES | Advanced Encryption Standard |
| XOR | Exclusive-OR |
| SGs | Smart Grids |
| SM | Smart Meters |
| HAN | Home Area Network |
| DER | Distributed Energy Resources |
| NEM | Net Energy Metering |
| KWh | kilowatt-hours |
| AMS | Advanced Metering Structure |
| IP | Internet Protocol |
| WAN | Wide Area Network |
| DLP | Discrete Logarithm Problem |
| DSO | Distribution System Operator |
| TTP | Trusted Third Party |
| LFSR | Linear-Feedback Shift Register |
| SNIR | Signal-to-Noise-plus-Interference Ratio |
| PSK | Phase Shift Keying |
| QPSK | Quadrature Phase Shift Keying |
| CSS | Chirp Spread Spectrum |
| BER | Bit Error Rate |
| TRM | Trade Reduction Mechanism |
| PMSC | Power Market Scheduling Center |
Appendix A
| Purchasers | Sellers | ||||||||
|---|---|---|---|---|---|---|---|---|---|
| H | H | ||||||||
| 80 | 11 | 1555 | 1556 | 80 | 31 | 00 | 1800 | 1790 | 140 |
| 3 | 10 | 1820 | 1830 | 90 | 142 | 00 | 1900 | 1870 | 200 |
| 115 | 10 | 1501 | 1877 | 100 | 99 | 00 | 1910 | 1920 | 65 |
| 77 | 10 | 1845 | 1846 | 30 | 10 | 00 | 1960 | 1580 | 70 |
References
- Liang, G.; Weller, S.R.; Luo, F.; Zhao, J.; Dong, Z.Y. Distributed Blockchain-Based Data Protection Framework for Modern Power Systems against Cyber Attacks. IEEE Trans. Smart Grid 2018. [Google Scholar] [CrossRef]
- Wu, J.; Ota, K.; Dong, M.; Li, J.; Wang, H. Big Data Analysis-Based Security Situational Awareness for Smart Grid. IEEE Trans. Big Data 2018, 4, 408–417. [Google Scholar] [CrossRef]
- Chen, T.; Su, W. Indirect Customer-to-Customer Energy Trading with Reinforcement Learning. IEEE Trans. Smart Grid 2018. [Google Scholar] [CrossRef]
- Chen, T.; Alsafasfeh, Q.; Pourbabak, H.; Su, W. The Next-Generation U.S. Retail Electricity Market with Customers and Prosumers—A Bibliographical Survey. Energies 2018, 11, 8. [Google Scholar] [CrossRef]
- Knirsch, F.; Eibl, G.; Engel, D. Error-Resilient Masking Approaches for Privacy Preserving Data Aggregation. IEEE Trans. Smart Grid 2018, 9, 3351–3361. [Google Scholar] [CrossRef]
- Chun, H.; Ren, K.; Jiang, W. Privacy-Preserving Power Usage and Supply Control in Smart Grid. Comput. Secur. 2018, 77, 709–719. [Google Scholar] [CrossRef]
- Jia, W.; Zhu, H.; Cao, Z.; Dong, X.; Xiao, C. Human-Factor-Aware Privacy-Preserving Aggregation in Smart Grid. IEEE Syst. J. 2014, 8, 598–607. [Google Scholar] [CrossRef]
- Eibl, G.; Engel, D. Influence of Data Granularity on Smart Meter Privacy. IEEE Trans. Smart Grid 2015, 6, 930–939. [Google Scholar] [CrossRef]
- Paverd, A.J.; Martin, A.P.; Brown, I. Security and Privacy in Smart Grid Demand Response Systems. In Proceedings of the Smart Grid Security—Second International Workshop, SmartGridSec 2014, Munich, Germany, 26 February 2014; Revised Selected Papers. pp. 1–15. [Google Scholar] [CrossRef]
- Kessler, S.; Flath, C.M.; Böhm, K. Allocative and Strategic Effects of Privacy Enhancement in Smart Grids. Inf. Syst. 2015, 53, 170–181. [Google Scholar] [CrossRef]
- Kvaternik, K.; Laszka, A.; Walker, M.; Schmidt, D.; Sturm, M.; Lehofer, M.; Dubey, A. Privacy-Preserving Platform for Transactive Energy Systems. arXiv 2018, arXiv:1709.09597v2. [Google Scholar]
- Mohammadi, R.; Mashhadi, H.R.; Shahidehpour, M. Market-based Customer Reliability Provision in Distribution Systems Based on Game Theory: A Bi-level Optimization Approach. IEEE Trans. Smart Grid 2018, 10, 3840–3848. [Google Scholar] [CrossRef]
- Da Costa, J.P.C.L.; Weichenberger, L. Reliable Intra-System Communication for Wireless Battery Management Systems; Deutsches Patent- und Markenamt (DPMA): München, Germany.
- Gope, P.; Sikdar, B. An Efficient Privacy-Preserving Dynamic Pricing-based Billing Scheme for Smart Grids. In Proceedings of the 2018 IEEE Conference on Communications and Network Security (CNS), Beijing, China, 30 May–1 June; pp. 1–2.
- Zinaman, O.; Aznar, A.; Linvill, C.; Darghouth, N.; Dubbeling, T.; Bianco, E. Grid-Connected Distributed Generation: Compensation Mechanism Basics; National Renewable Energy Laboratory: Golden, CO, USA, 2017.
- Tushar, W.; Yuen, C.; Smith, D.B.; Poor, H.V. Price Discrimination for Energy Trading in Smart Grid: A Game Theoretic Approach. IEEE Trans. Smart Grid 2017, 8, 1790–1801. [Google Scholar] [CrossRef]
- Liu, N.; Yu, X.; Wang, C.; Li, C.; Ma, L.; Lei, J. Energy-Sharing Model With Price-Based Demand Response for Microgrids of Peer-to-Peer Prosumers. IEEE Trans. Power Syst. 2017, 32, 3569–3583. [Google Scholar] [CrossRef]
- Jacquot, P.; Beaude, O.; Gaubert, S.; Oudjane, N. Analysis and Implementation of an Hourly Billing Mechanism for Demand Response Management. IEEE Trans. Smart Grid 2018, 10, 4265–4278. [Google Scholar] [CrossRef]
- Lee, J.; Guo, J.; Choi, J.K.; Zukerman, M. Distributed Energy Trading in Microgrids: A Game-Theoretic Model and Its Equilibrium Analysis. IEEE Trans. Ind. Electron. 2015, 62, 3524–3533. [Google Scholar] [CrossRef]
- Mediwaththe, C.P.; Stephens, E.R.; Smith, D.B.; Mahanti, A. A Dynamic Game for Electricity Load Management in Neighborhood Area Networks. IEEE Trans. Smart Grid 2016, 7, 1329–1336. [Google Scholar] [CrossRef]
- Ma, K.; Hu, G.; Spanos, C.J. Distributed Energy Consumption Control via Real-Time Pricing Feedback in Smart Grid. IEEE Trans. Control Syst. Technol. 2014, 22, 1907–1914. [Google Scholar] [CrossRef]
- Zhu, J.; Chen, M.Z.Q.; Zuo, Z.; Du, B. A New Pricing Scheme for Controlling Energy Storage Devices in Smart Grid. In Proceedings of the 2014 American Control Conference, Portland, OR, USA, 4–6 June 2014; pp. 2912–2917. [Google Scholar]
- Verschae, R.; Kato, T.; Matsuyama, T. Energy Management in Prosumer Communities: A Coordinated Approach. Energies 2016, 9, 562. [Google Scholar] [CrossRef]
- Guo, F.; Wen, C.; Li, Z. Distributed Optimal Energy Scheduling Based on a Novel PD Pricing Feedback Strategy in Smart Grid. In Proceedings of the 2015 IEEE 10th Conference on Industrial Electronics and Applications (ICIEA), Auckland, New Zealand, 15–17 June 2015; pp. 208–213. [Google Scholar] [CrossRef]
- Wu, Y.; Tan, X.; Qian, L.; Tsang, D.H.K.; Song, W.-Z.; Yu, L. Optimal Pricing and Energy Scheduling for Hybrid Energy Trading Market in Future Smart Grid. IEEE Trans. Ind. Inform. 2015, 11, 1585–1596. [Google Scholar] [CrossRef]
- Samadi, P.; Mohsenian-Rad, H.; Schober, R.; Wong, V.; Jatskevich, J. Optimal Real-Time Pricing Algorithm Based on Utility Maximization for Smart Grid. In Proceedings of the Conference on Smart Grid Communications, Gaithersburg, MD, USA, 4–6 October 2010. [Google Scholar]
- Qian, L.P.; Wu, Y.; Zhang, Y.J.; Huang, J. Demand Response Management via Real-time Electricity Price Control in Smart Grids. In Smart Grid—Networking, Data Management, and Business Models; CRC Press: Boca Raton, FL, USA; Taylor & Francis Group: New York, NY, USA, 2016. [Google Scholar]
- Voice, T.; Vytelingum, P.; Ramchurn, S.; Rogers, A.; Jennings, N. Decentralised Control of Micro-Storage in the Smart Grid. In Proceedings of the AAAI Conference on Artificial Intelligence, San Francisco, CA, USA, 7–11 August 2011. [Google Scholar]
- Ye, M.; Hu, G.; Spanos, C.J. Decentralized Optimal Load Scheduling Using Extremum Seeking-Based Optimization; Center for Research in Energy Systems Transformation (CREST): Berkeley, CA, USA, 2014. [Google Scholar]
- Eddy, Y.S.F.; Gooi, H.B.; Chen, S.X. Multi-Agent System for Distributed Management of Microgrids. IEEE Trans. Power Syst. 2015, 30, 24–34. [Google Scholar] [CrossRef]
- Mohsenian-Rad, A.-H.; Wong, V.W.S.; Jatskevich, J.; Schober, R.; Leon-Garcia, A. Autonomous Demand-Side Management Based on Game-Theoretic Energy Consumption Scheduling for the Future Smart Grid. IEEE Trans. Smart Grids 2010, 1, 320–331. [Google Scholar] [CrossRef]
- Chakraborty, P.; Baeyens, E.; Khargonekar, P.P.; Poolla, K.; Varaiya, P. Analysis of Solar Energy Aggregation under Various Billing Mechanisms. IEEE Trans. Smart Grid 2018, 10, 4175–4187. [Google Scholar] [CrossRef]
- Wei, W.; Liu, F.; Mei, S. Energy Pricing and Dispatch for Smart Grid Retailers Under Demand Response and Market Price Uncertainty. IEEE Trans. Smart Grid 2015, 6, 1364–1374. [Google Scholar] [CrossRef]
- Yaagoubi, N.; Mouftah, H.T. A Distributed Game Theoretic Approach to Energy Trading in the Smart Grid. In Proceedings of the 2015 IEEE Electrical Power and Energy Conference (EPEC), London, ON, Canada, 26–28 October 2015; pp. 203–208. [Google Scholar] [CrossRef]
- Sikdar, S.; Rudie, K. Microgrid Level Competitive Market Using Dynamic Matching. In Proceedings of the Electrical Power & Energy Conference (EPEC), Halifax, NS, Canada, 21–23 August 2013; pp. 1–6. [Google Scholar]
- Wang, Y.; Saad, W.; Han, Z.; Poor, H.V.; Başar, T. A Game-Theoretic Approach to Energy Trading in the Smart Grid. arXiv 2013, arXiv:1310.1814. [Google Scholar] [CrossRef]
- Vytelingum, P.; Voice, T.D.; Ramchurn, S.D.; Rogers, A.; Jennings, N.R. Agent-Based Micro-Storage Management for the Smart Grid. In Proceedings of the Ninth International Conference on Autonomous Agents and Multiagent Systems, Toronto, ON, Canada, 10–14 May 2010; pp. 39–46. [Google Scholar]
- Kim, M.; Parkt, S.; Choi, J.K.; Lee, J. Energy Independence of Energy Trading System in Microgrid. In Proceedings of the 2017 IEEE Innovative Smart Grid Technologies—Asia (ISGT-Asia), Auckland, New Zealand, 4–7 December 2017. [Google Scholar] [CrossRef]
- Ilic, D.; da Silva, P.G.; Karnouskos, S.; Griesemer, M. An Energy Market for Trading Electricity in Smart Grid Neighbourhoods. In Proceedings of the IEEE International Conference on Digital Ecosystems and Technologies, Campione d’Italia, Italy, 18–20 June 2012; pp. 1–6. [Google Scholar]
- Bayram, I.S.; Shakir, M.Z.; Abdallah, M.; Qaraqe, K. A Survey on Energy Trading in Smart Grid. In Proceedings of the 2014 IEEE Global Conference on Signal and Information Processing, Atlanta, GA, USA, 3–5 December 2014; pp. 258–262. [Google Scholar]
- Gkatzikis, L.; Koutsopoulos, I.; Salonidis, T. The Role of Aggregators in Smart Grid Demand Response Markets. IEEE J. Sel. Areas Commun. 2013, 31, 1247–1257. [Google Scholar] [CrossRef]
- Ghorani, R.; Fotuhi-Firuzabad, M.; Moeini-Aghtaie, M. Optimal Bidding Strategy of Transactive Agents in Local Energy Markets. IEEE Trans. Smart Grid 2018, 10, 5152–5162. [Google Scholar] [CrossRef]
- McKenna, E.; Thomson, M. Photovoltaic Metering Configurations, Feed-in Tariffs and the Variable Effective Electricity Prices that Result. IET Renew. Power Gener. 2013, 7, 235–245. [Google Scholar] [CrossRef]
- Parkes, D.C.; Rabin, M.O.; Shieber, S.M.; Thorpe, C. Practical Secrecy-Preserving, Verifiably Correct and Trustworthy Auctions. Electron. Commer. Res. Appl. 2008, 7, 294–312. [Google Scholar] [CrossRef]
- Zhu, L.Y. Dominant Strategy Double Auction Mechanisms: Design and Implementation. Master’s Thesis, University of Florida, Gainesville, FL, USA, 2005. [Google Scholar]
- Parsons, S.; Rodriguez-Aguilar, J.A.; Klein, M. Auctions and Bidding: A Guide for Computer Scientists. ACM Comput. Surv. 2011, 43, 10. [Google Scholar] [CrossRef]
- Zhang, J.; Wen, D.; Zeng, S. A Discounted Trade Reduction Mechanism for Dynamic Ridesharing Pricing. IEEE Trans. Intell. Transp. Syst. 2016, 17, 1586–1595. [Google Scholar] [CrossRef]
- Myerson, R.B.; Satterthwaite, M.A. Efficient Mechanisms for Bilateral Trading. J. Econ. Theory 1983, 29, 265–281. [Google Scholar] [CrossRef]
- McAfee, R.P. A Dominant Strategy Double Auction. J. Econ. Theory 1992, 56, 434–450. [Google Scholar] [CrossRef]
- Segal-Halevi, E.; Hassidim, A.; Aumann, Y. SBBA: A Strongly-Budget-Balanced Double-Auction Mechanism. arXiv 2016, arXiv:1607.05139v1. [Google Scholar]
- Chu, L.Y.; Shen, Z.-J.M. Agent Competition Double-Auction Mechanism. Manag. Sci. 2006, 52, 1215–1222. [Google Scholar] [CrossRef]
- Vardakas, J.S.; Zorba, N.; Verikoukis, C.V. A Survey on Demand Response Programs in Smart Grids: Pricing Methods and Optimization Algorithms. IEEE Commun. Surv. Tuts. 2014, 17, 152–178. [Google Scholar] [CrossRef]
- Tang, Q.; Yang, K.; Zhou, D.; Luo, Y.; Yu, F. A Real-Time Dynamic Pricing Algorithm for Smart Grid With Unstable Energy Providers and Malicious Users. IEEE Internet Things J. 2016, 3, 554–562. [Google Scholar] [CrossRef]
- Jiang, T.; Cao, Y.; Yu, L.; Wang, Z. Load Shaping Strategy Based on Energy Storage and Dynamic Pricing in Smart Grid. IEEE Trans. Smart Grid 2014, 5, 2868–2876. [Google Scholar] [CrossRef]
- Takahashi, S.; Tokuro, M. A Formalization of Quantity Based Double Auction Mechanism. In Proceedings of the 19th International Conference on Systems Engineering, Las Vegas, NV, USA, 3–5 February 2008. [Google Scholar] [CrossRef]
- Wang, W.; Lu, Z. Cyber security in the Smart Grid: Survey and Challenges. Comput. Netw. 2013, 57, 1344–1371. [Google Scholar] [CrossRef]
- Buchmann, E.; Böhm, K.; Burghardt, T.; Kessler, S. Re-identification of Smart Meter Data. Pers. Ubiquitous Comput. 2013, 17, 653–662. [Google Scholar] [CrossRef]
- Shiobara, T.; Palensky, P.; Nishi, H. Effective Metering Data Aggregation for Smart Grid Communication Infrastructure. In Proceedings of the 41st Annual Conference of the IEEE Industrial Electronics Society (IECON 2015), Yokohama, Japan, 9–12 November 2015; pp. 2136–2140. [Google Scholar] [CrossRef]
- Gong, Y.; Cai, Y.; Guo, Y.; Fang, Y. A Privacy-Preserving Scheme for Incentive-Based Demand Response in the Smart Grid. IEEE Trans. Smart Grid 2016, 7, 1304–1313. [Google Scholar] [CrossRef]
- Tudor, V.; Almgren, M.; Papatriantafilou, M. The Influence of Dataset Characteristics on Privacy Preserving Methods in the Advanced Metering Infrastructure. Comput. Secur. 2018, 76, 178–196. [Google Scholar] [CrossRef]
- Metke, A.R.; Ekl, R.L. Security Technology for Smart Grid Networks. IEEE Trans. Smart Grid 2010, 1, 99–107. [Google Scholar] [CrossRef]
- Iyer, S. Cyber Security for Smart Grid, Cryptography, and Privacy. Int. J. Digit. Multimed. Broadcast. 2011, 2011, 372020. [Google Scholar] [CrossRef]
- Yadav, S.A.; Kumar, S.R.; Sharma, S.; Singh, A. A Review of Possibilities and Solutions of Cyber Attacks in Smart Grids. In Proceedings of the 1st International Conference on Innovation and Challenges in Cyber Security (ICICCS 2016), Noida, India, 3–5 February 2016; pp. 60–63. [Google Scholar]
- Abidin, A.; Aly, A.; Cleemput, S.; Mustafa, M.A. Secure and Privacy-Friendly Local Electricity Trading and Billing in Smart Grid. arXiv 2018, arXiv:1801.08354. [Google Scholar]
- Shapsough, S.; Qatan, F.; Aburukba, R.; Aloul, F.; al Ali, A.R. Smart Grid Cyber Security: Challenges and Solutions. In Proceedings of the International Conference on Smart Grid and Clean Energy Technologies (ICSGCE), Offenburg, Germany, 20–23 October 2015; pp. 170–175. [Google Scholar]
- Richardson, C.; Race, N.; Smith, P. A Privacy Preserving Approach to Energy Theft Detection in Smart Grids. In Proceedings of the 2016 IEEE International Smart Cities Conference (ISC2), Trento, Italy, 3 October 2016; pp. 1–4. [Google Scholar]
- He, D.; Kumar, N.; Zeadally, S.; Vinel, A.; Yang, L.T. Efficient and Privacy-Preserving Data Aggregation Scheme for Smart Grid Against Internal Adversaries. IEEE Trans. Smart Grid 2017, 8, 2411–2419. [Google Scholar] [CrossRef]
- Iwamura, K.; Tokita, K. Fast Secure Computation Based on a Secret Sharing Scheme for n < 2k − 1. In Proceedings of the 4th International Conference on Mobile and Secure Services (MobiSecServ), Miami Beach, FL, USA, 24–25 February 2018; pp. 1–5. [Google Scholar]
- Abood, O.G.; Elsadd, M.A.; Guirguis, S.K. Investigation of Cryptography Algorithms Used for Security and Privacy Protection in Smart Grid. In Proceedings of the 2017 Nineteenth International Middle East Power Systems Conference (MEPCON), Cairo, Egypt, 19–21 December 2017; pp. 644–649. [Google Scholar]
- Barletta, A.; Callegari, C.; Giordano, S.; Pagano, M.; Procissi, G. Privacy Preserving Smart Grid Communications by Verifiable Secret Key Sharing. In Proceedings of the 2015 Intl. Conference on Computing and Network Communications (CoCoNet’15), Trivandrum, India, 16–19 December 2015; pp. 199–204. [Google Scholar]
- Mihaylov, M.; Jurado, S.; Avellana, N.; van Moffaert, K.; de Abril, I.M.; Nowé, A. NRGcoin: Virtual Currency for Trading of Renewable Energy in Smart Grids. In Proceedings of the 11th International Conference on the European Energy Market (EEM14), Krakow, Poland, 28–30 May 2014; pp. 1–5. [Google Scholar] [CrossRef]
- Hu, C.; Liao, X.; Cheng, X. Verifiable Multi-Secret Sharing Based on LFSR Sequences. Theor. Comput. Sci. 2012, 445, 52–62. [Google Scholar] [CrossRef]
- George, M.; Alfke, P. Linear Feedback Shift Registers in Virtex Devices; Xilinx XAPP210 (v1.3); Xilinx Inc.: San Jose, CA, USA, 2007; pp. 1–5. [Google Scholar]
- Paar, C.; Pelzl, J. Understanding Cryptography. A Textbook for Students and Practitioners; Springer: Berlin/Heidelberg, Germany, 2010. [Google Scholar] [CrossRef]
- Hao, J.; Piechocki, R.J.; Kaleshi, D.; Chin, W.H.; Fan, Z. Optimal Malicious Attack Construction and Robust Detection in Smart Grid Cyber Security Analysis. In Proceedings of the 2014 IEEE International Conference on Smart Grid Communications (SmartGridComm), Venice, Italy, 3–6 November 2015. [Google Scholar] [CrossRef]
- Rahman, M.S.; Basu, A.; Kiyomoto, S.; Bhuiyan, M.Z.A. Privacy-Friendly Secure Bidding for Smart Grid Demand-Response. Inf. Sci. 2017, 379, 229–240. [Google Scholar] [CrossRef]
- Duan, J.; Chow, M.-Y. A Resilient Consensus-Based Distributed Energy Management Algorithm against Data Integrity Attacks. IEEE Trans. Smart Grid 2018. [Google Scholar] [CrossRef]
- Hung, Y.; Michailidis, G. Modeling and Optimization of Time-Of-Use Electricity Pricing Systems. IEEE Trans. Smart Grid 2018. [Google Scholar] [CrossRef]
| Criterion | Cooperative Games | Competitive Games |
|---|---|---|
| How energy is predominantly seen | as a public good | as a commodity |
| Main goals | social fairness, market control | decentralization, market efficiency |
| Main references | [17,18,22,23,24,25,26,27,28,29,30,31,32,33] | [3,4,19,20,21,34,35,36,37,38,39,40,41,42] |
| Reference | [1] | [67] | [76] | [77] | [11] | Proposed |
|---|---|---|---|---|---|---|
| Privacy enhancement method | DLP-based public key + secure hash algorithm | DLP-based public key (Boneh- Goh-Nissim) | DLP-based public key (ElGamal) | None | Anonymous Addresses + cryptographic signature | AES keys + XOR matrix of fixed length |
| Cost of cryptography | High | High | High | None | Medium | Low |
| Disclosure of SM address | 1 | 1 | 1 | 1 | 0 | 1 |
| Dismissal of secure communication channel | 1 | 1 | 0 | 0 | 1 | 1 |
| ID de-anonymization proof | 0 | 0 | 1 | 0 | 0 | 1 |
| Absence of need for connection between each pair of nodes | 0 | 1 | 1 | 1 | 0 | 1 |
| Impossibility of interested parties identification | 0 | 0 | 0 | 0 | 0 | 1 |
| Reference | [53] | [33] | [41] | [78] | [18] | [22] | [20] | [23] | [24] | [3] | [16] | [34] | Proposed |
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| Dismissal of consumption profile assumptions | 0 | 0 | 0 | 0 | 0 | 1 | 0 | 0 | 1 | 1 | 1 | 1 | 1 |
| Possibility of storage elements inclusion | 0 | 1 | 0 | 1 | 0 | 1 | 0 | 1 | 0 | 0 | 1 | 1 | 1 |
| Pricing freedom | 0 | 0 | 0 | 0 | 0 | 0 | 0 | 0 | 0 | 1 | 0 | 1 | 1 |
| Inclusion of a TTP | 1 | 1 | 1 | 0 | 1 | 1 | 0 | 1 | 1 | 1 | 1 | 0 | 1 |
| Competitive market | 0 | 0 | 1 | 1 | 1 | 0 | 1 | 0 | 0 | 1 | 0 | 1 | 1 |
© 2020 by the authors. Licensee MDPI, Basel, Switzerland. This article is an open access article distributed under the terms and conditions of the Creative Commons Attribution (CC BY) license (http://creativecommons.org/licenses/by/4.0/).
Share and Cite
Junior, J.M.; da Costa, J.P.C.L.; Garcez, C.C.R.; de Oliveira Albuquerque, R.; Arancibia, A.; Weichenberger, L.; de Mendonça, F.L.L.; Galdo, G.d.; de Sousa Jr., R.T. Data Security and Trading Framework for Smart Grids in Neighborhood Area Networks. Sensors 2020, 20, 1337. https://doi.org/10.3390/s20051337
Junior JM, da Costa JPCL, Garcez CCR, de Oliveira Albuquerque R, Arancibia A, Weichenberger L, de Mendonça FLL, Galdo Gd, de Sousa Jr. RT. Data Security and Trading Framework for Smart Grids in Neighborhood Area Networks. Sensors. 2020; 20(5):1337. https://doi.org/10.3390/s20051337
Chicago/Turabian StyleJunior, Jayme Milanezi, João Paulo C. L. da Costa, Caio C. R. Garcez, Robson de Oliveira Albuquerque, Arnaldo Arancibia, Lothar Weichenberger, Fábio Lucio Lopes de Mendonça, Giovanni del Galdo, and Rafael T. de Sousa Jr. 2020. "Data Security and Trading Framework for Smart Grids in Neighborhood Area Networks" Sensors 20, no. 5: 1337. https://doi.org/10.3390/s20051337
APA StyleJunior, J. M., da Costa, J. P. C. L., Garcez, C. C. R., de Oliveira Albuquerque, R., Arancibia, A., Weichenberger, L., de Mendonça, F. L. L., Galdo, G. d., & de Sousa Jr., R. T. (2020). Data Security and Trading Framework for Smart Grids in Neighborhood Area Networks. Sensors, 20(5), 1337. https://doi.org/10.3390/s20051337






