Enhancing Security on Touch-Screen Sensors with Augmented Handwritten Signatures
Abstract
1. Introduction
2. Related Works
3. Materials and Methods
3.1. Signature Data Acquisition
3.2. Signature Types
- the usual signature with initials (SI);
- the usual signature with name-surname (SN);
- the usual signature with date (SD);
- the usual signature with place (SP);
- the usual signature with date and place (SDP);
- the usual signature with initials, date and place (SIDP);
- the name-surname with date and place (NDP).
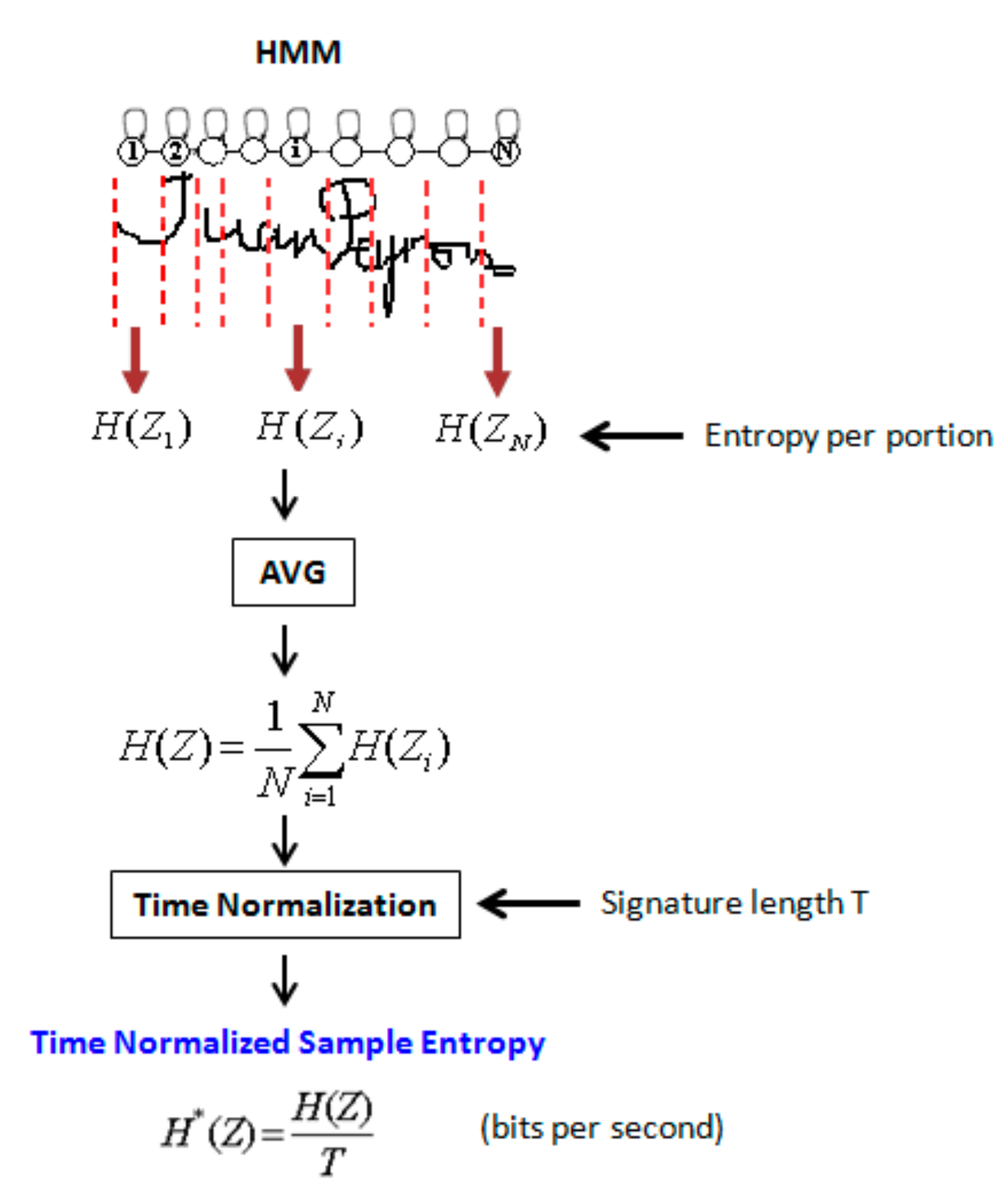
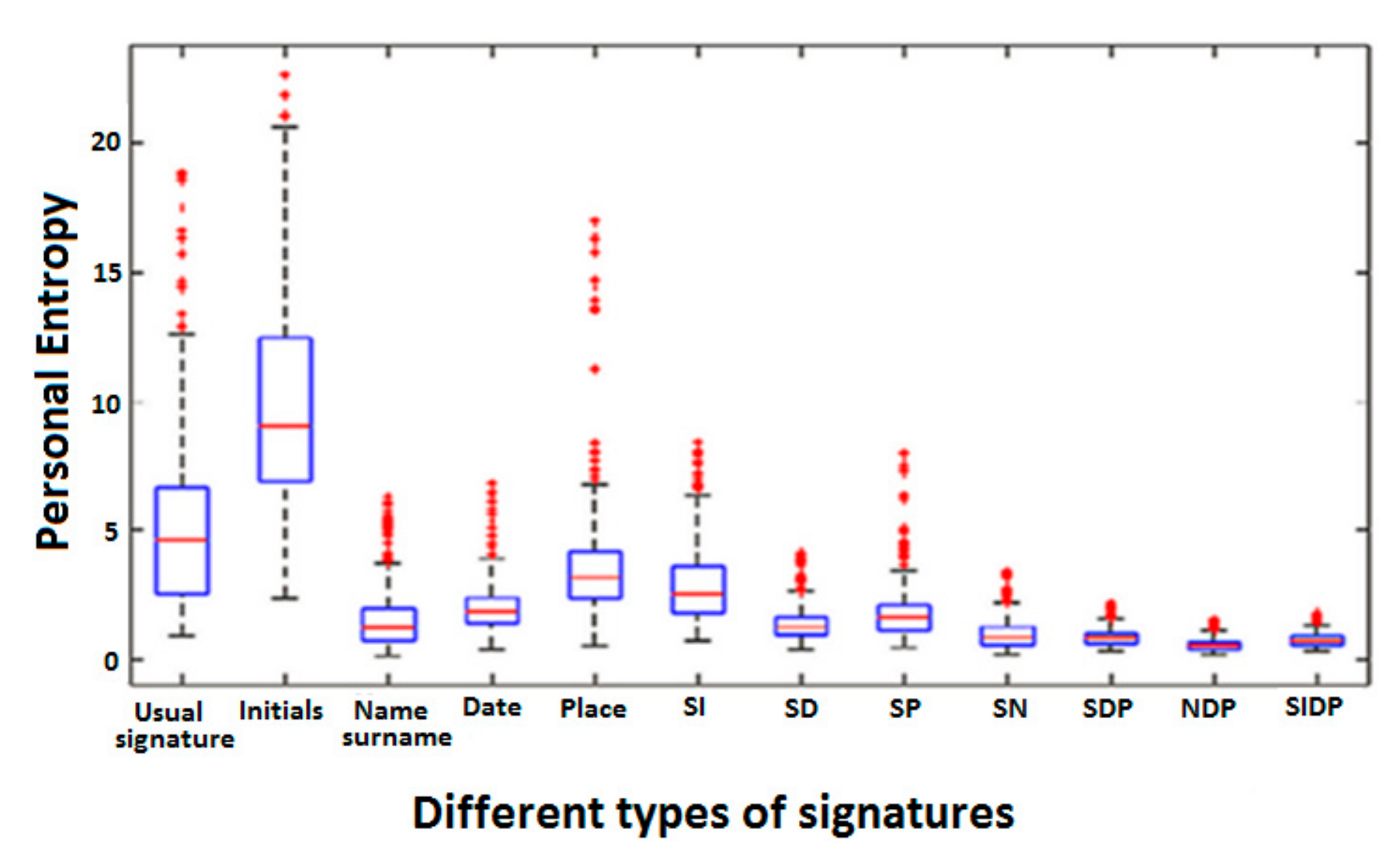
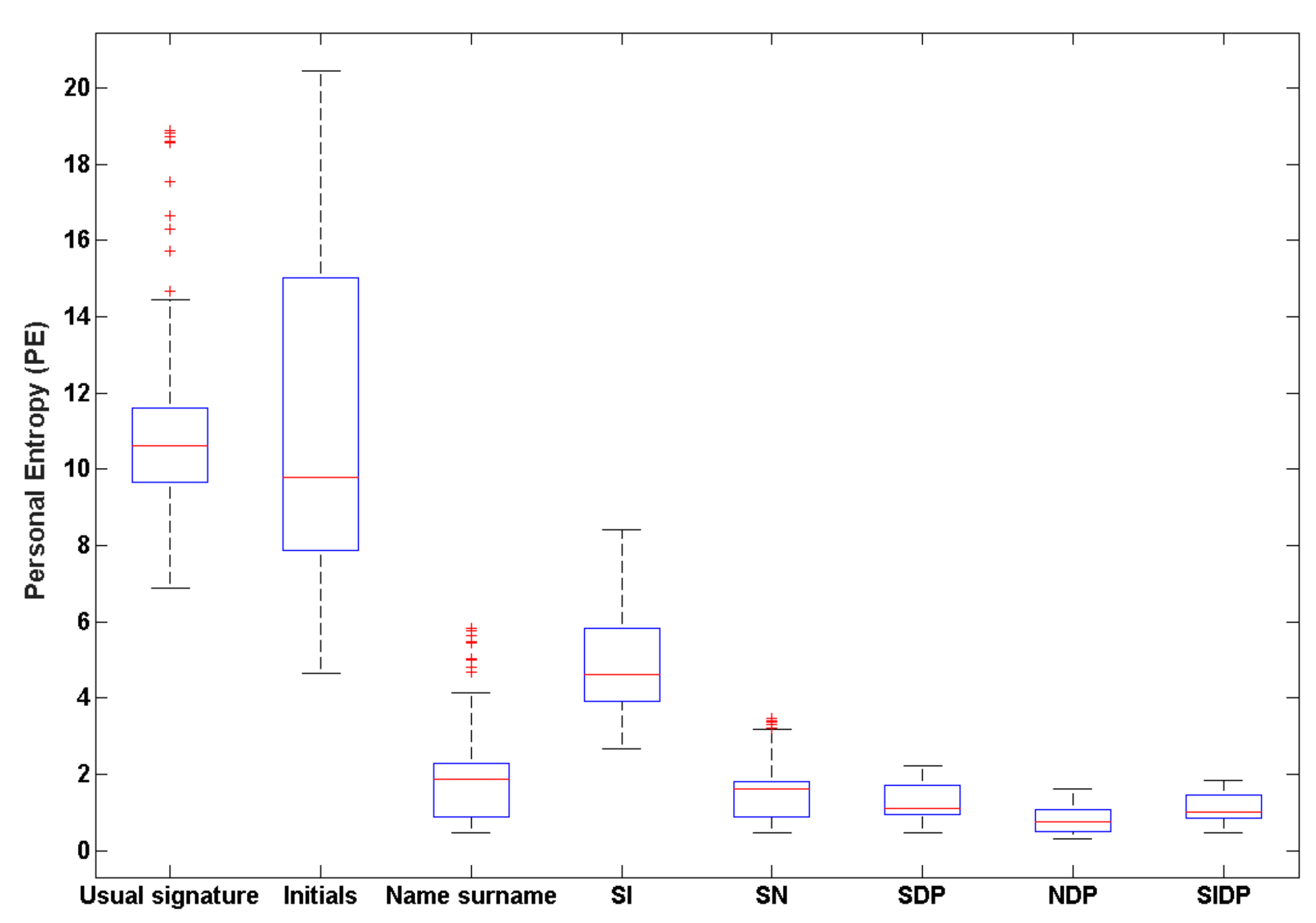
3.3. Quantifying Quality of Signature Types
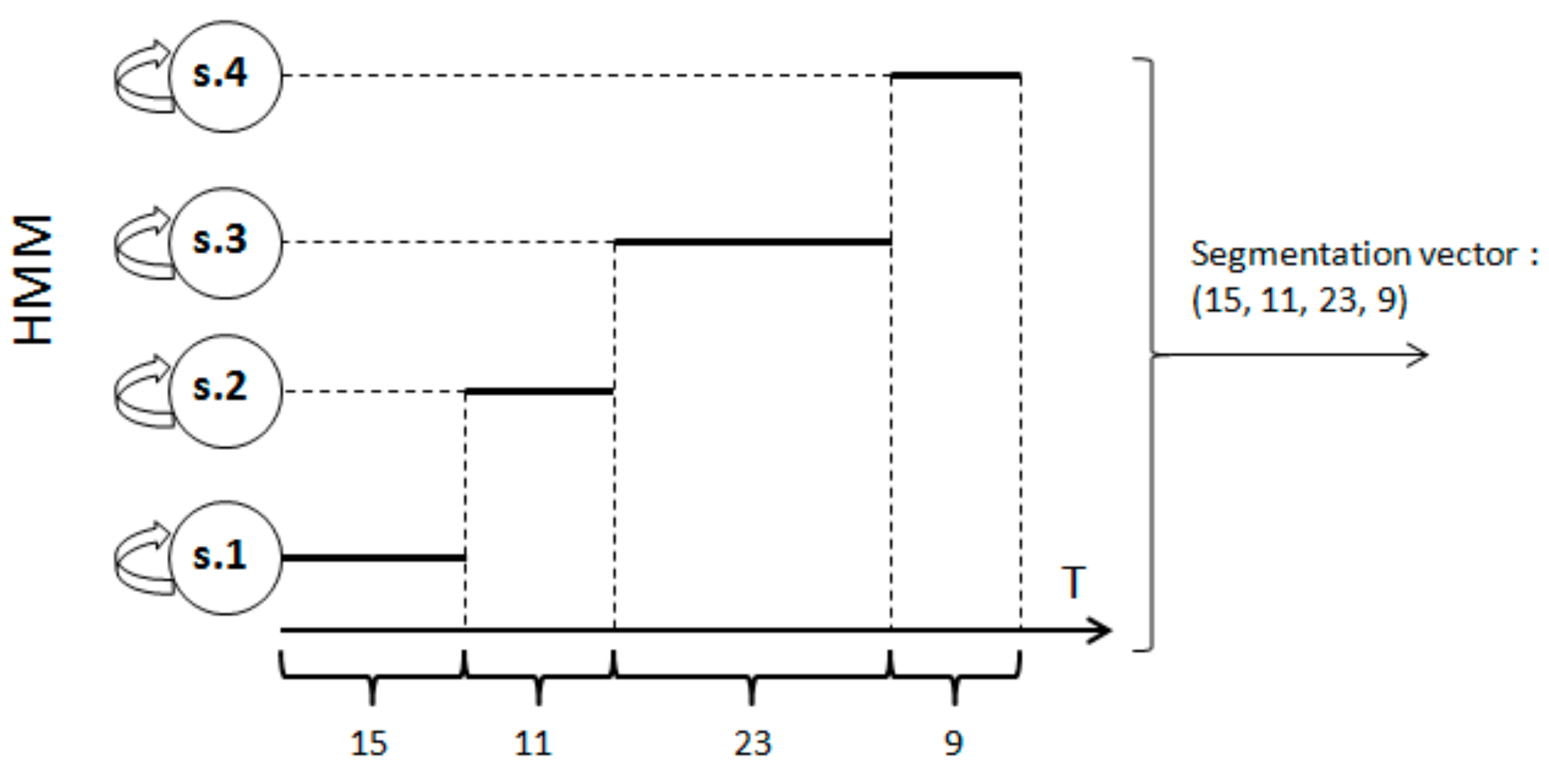
3.4. Signature Verification System
4. Results
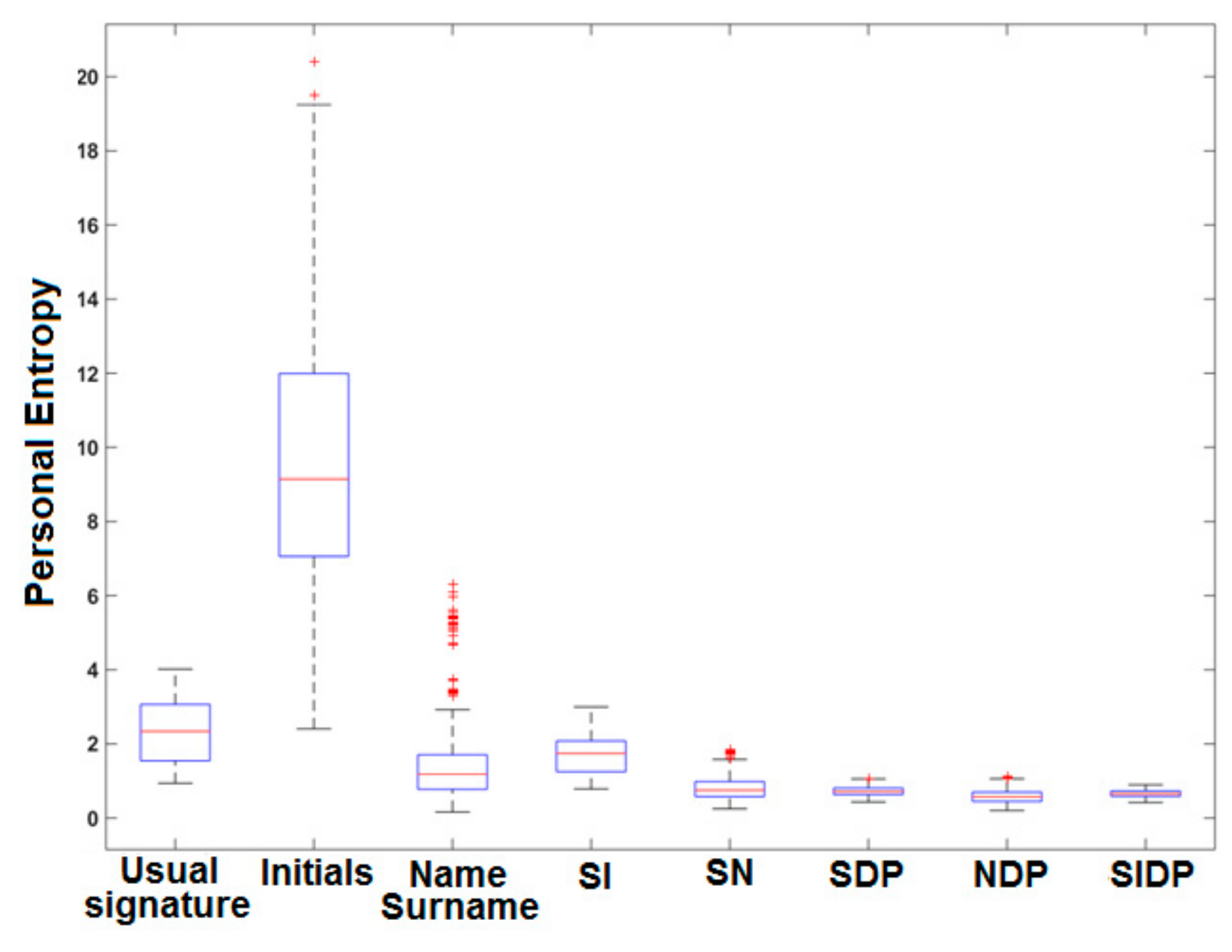
4.1. Quality Measure of Usual Signatures
4.2. Quality Measure of All Signature Types
4.3. Evaluation of the Proposed Scheme
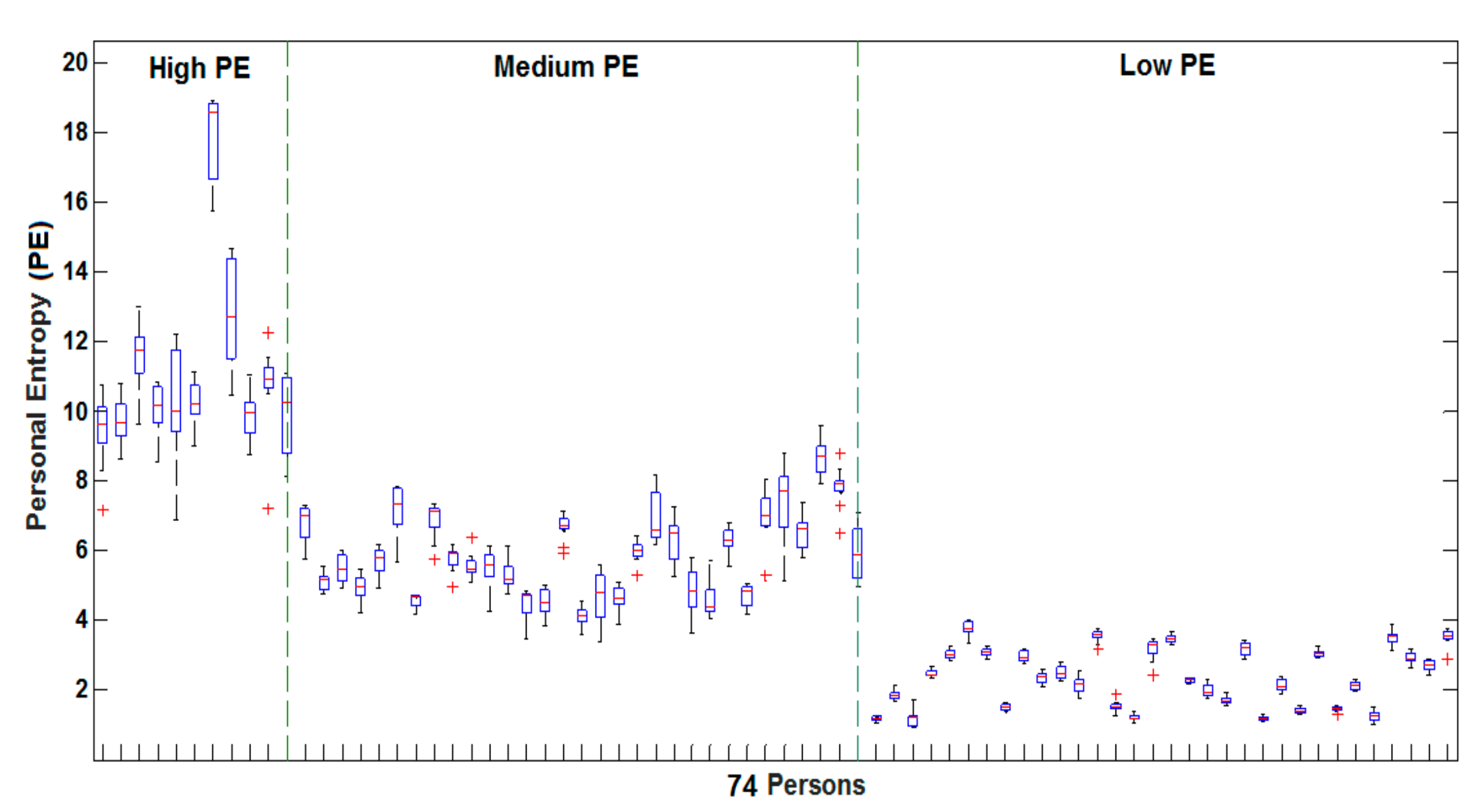
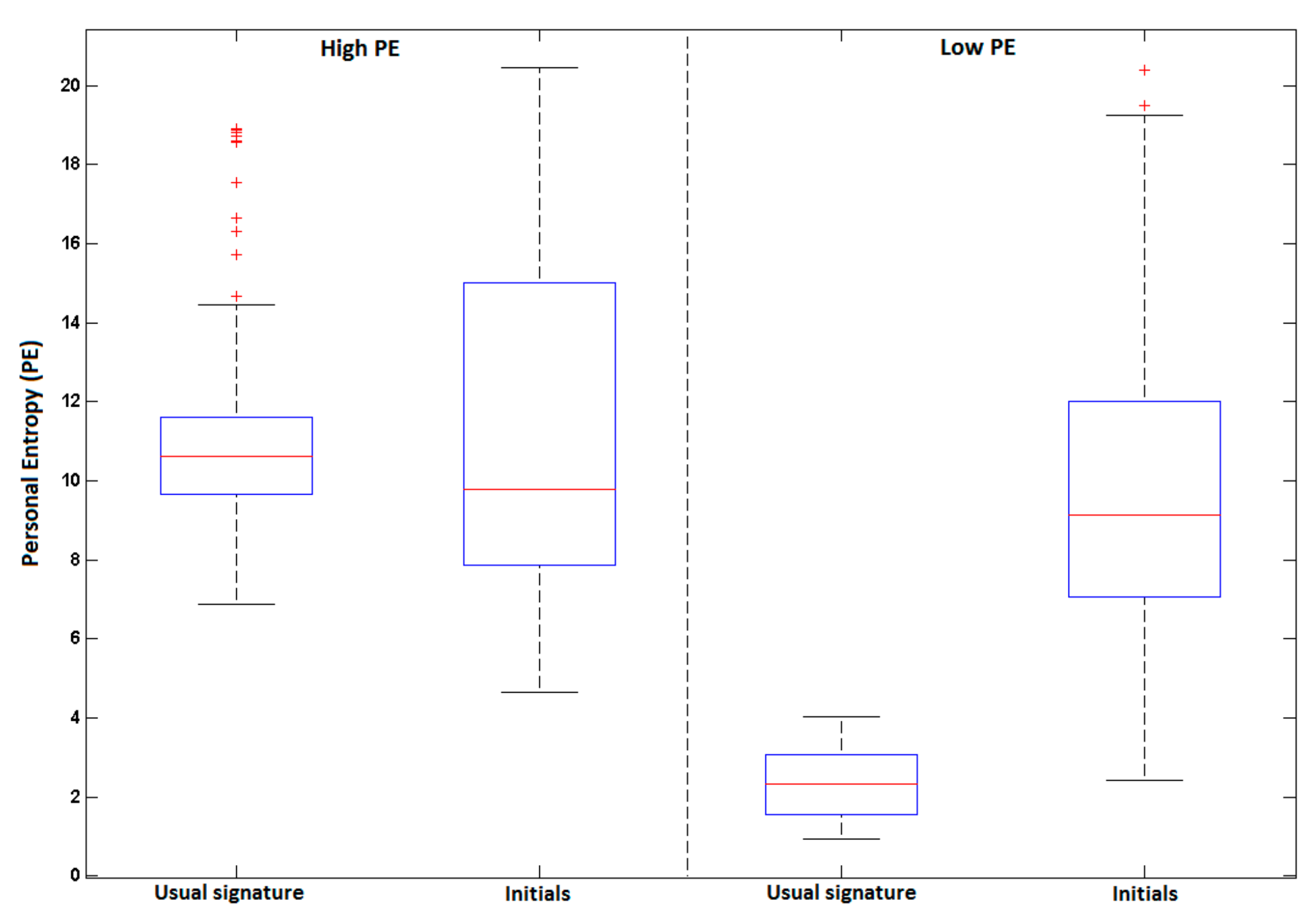
4.3.1. Results on High PE Category
4.3.2. Results on Low PE Category
4.3.3. Results on Medium PE Category
5. Discussion
6. Conclusions and Future Work
Author Contributions
Funding
Conflicts of Interest
Appendix A
| N° | Feature Name | |
|---|---|---|
| Gesture related features | 1–2 | Normalized coordinates (x(t)−xg, y(t)−yg) relative to the gravity center (xg, yg) of the signature |
| 3–4 | Speed in x and y | |
| 5 | Absolute speed | |
| 6 | Ratio of the minimum over the maximum speed on a window of 5 points | |
| 7–8 | Acceleration in x and y | |
| 9 | Absolute acceleration | |
| 10 | Tangential acceleration | |
| Local shape related features | 11 | Angle α between the absolute speed vector and the x axis |
| 12–13 | Sine(α) and Cosine(α) | |
| 14 | Variation of the α angle: | |
| 15–16 | Sine() and Cosine() | |
| 17 | Log(1 + r) where r is the curvature radius of the signature at the present point | |
| 18 | Length to width ratio on windows of size of 5 points | |
| 19 | Length to width ratio on windows of size of 7 points |
- The absolute speed (N° 5 in Table A1):
- Acceleration in x and y (N° 7–8 in Table A1):
- The absolute acceleration (N° 9 in Table A1):
- The tangential acceleration (N° 10 in Table A1):
- Variation of the angle α angle (N° 14 in Table A1):
- Sine and cosine of angle (N° 15–16 in Table A1):
- Length to width ratio on windows of size of 5 points centered on the current point t (N° 18 in Table A1).
- Length to width ratio on windows of size of 7 points centered on the current point t (N° 19 in Table A1).
References
- Impedovo, D.; Pirlo, G. Automatic Signature Verification: The State of the Art. IEEE Trans. Syst. Man Cybern. Part C Appl. Rev. 2008, 38, 609–635. [Google Scholar] [CrossRef]
- Diaz, M.; Ferrer, M.A.; Impedovo, D.; Malik, M.I.; Pirlo, G.; Plamondon, R. A Perspective Analysis of Handwritten Signature Technology. ACM Comput. Surv. 2019, 51, 1–39. [Google Scholar] [CrossRef]
- Dolfing, J.; Aarts, E.; Van Oosterhout, J. On-line signature verification with hidden Markov models. In Proceedings of the Fourteenth International Conference on Pattern Recognition, Brisbane, Australia, 20 August 1998; pp. 1309–1312. [Google Scholar]
- Garcia-Salicetti, S.; Beumier, C.; Chollet, G.; Dorizzi, B.; Jardins, J.L.L.; Lunter, J.; Ni, Y.; Petrovska-Delacrétaz, D. BIOMET: A Multimodal Person Authentication Database Including Face, Voice, Fingerprint, Hand and Signature Modalities. In Proceedings of the Computer Vision, Guildford, UK, 9–11 June 2003; Springer Science and Business Media LLC: Berlin, Germany; pp. 845–853. [Google Scholar]
- Ortega-Garcia, J.; Fierrez-Aguilar, J.; Simon, D.; González, J.; Faundez-Zanuy, M.; Espinosa, V.; Satue, A.; Hernaez, I.; Igarza, J.J.; Vivaracho, C.; et al. MCYT baseline corpus: A bimodal biometric database. IEE Proc. Vision Image Signal Process. 2003, 150, 395–401. [Google Scholar] [CrossRef]
- Yeung, D.Y.; Chang, H.; Xiong, Y.; George, S.; Kashi, R.; Matsumoto, T.; Rigoll, G. SVC2004: First International Signature Verification Competition. In Proceedings of the Biometric Authentication, First International Conference ICBA, Hong Kong, China, 15–17 July 2004; pp. 16–22. [Google Scholar]
- Kholmatov, A.; Yanikoglu, B. SUSIG: An on-line signature database, associated protocols and benchmark results. Pattern Anal. Appl. 2009, 12, 227–236. [Google Scholar] [CrossRef]
- SUSIG On-Line Signature Database. Available online: https://biometrics.sabanciuniv.edu/susig.html (accessed on 16 December 2011).
- Ortega-Garcia, J.; Fierrez, J.; Alonso-Fernandez, F.; Galbally, J.; Freire, M.R.; Gonzalez-Rodriguez, J.; Garcia-Mateo, C.; Alba-Castro, J.L.; Gonzalez-Agulla, E.; Otero-Muras, E.; et al. The Multiscenario Multienvironment BioSecure Multimodal Database (BMDB). IEEE Trans. Pattern Anal. Mach. Intell. 2010, 32, 1097–1111. [Google Scholar] [CrossRef] [PubMed]
- Biometrics in Identity Management: Concepts to Applications. Available online: http://biosecure.itsudparis.eu/AB/ (accessed on 4 October 2017).
- Fierrez, J.; Galbally, J.; Ortega-Garcia, J.; Freire, M.R.; Alonso-Fernandez, F.; Ramos, D.; Toledano, D.T.; Gonzalez-Rodriguez, J.; Siguenza, J.A.; Garrido-Salas, J.; et al. BiosecurID: A multimodal biometric database. Pattern Anal. Appl. 2010, 13, 235–246. [Google Scholar] [CrossRef]
- Mayoue, A.; Dorizzi, B.; Allano, L.; Chollet, G.; Hennebert, J.; Petrovska-Delacr, D.; Verdet, F. Biosecure multimodal evaluation campaign 2007 (BMEC’2007). In Guide to Biometric Reference Systems and Performance Evaluation; Springer: London, UK, 2009; pp. 327–369. [Google Scholar]
- Encyclopedia of Biometrics: I–Z. Available online: http://biometrics.itsudparis.eu/BMEC2007/ (accessed on 12 June 2008).
- Blankers, V.L.; Heuvel, C.E.V.D.; Franke, K.Y.; Vuurpijl, L.G. ICDAR 2009 Signature Verification Competition. In Proceedings of the 10th International Conference on Document Analysis and Recognition, Barcelona, Spain, 26–29 July 2009; pp. 1403–1407. [Google Scholar]
- Houmani, N.; Mayoue, A.; Garcia-Salicetti, S.; Dorizzi, B.; Khalil, M.I.; Moustafa, M.N.; Abbas, H.; Muramatsu, D.; Yanikoglu, B.; Kholmatov, A.; et al. Biosecure Signature Evaluation Campaign (BSEC’2009): Evaluating Online Signature Verification Systems’ Performance. Pattern Recogn. 2012, 45, 993–1003. [Google Scholar] [CrossRef]
- Houmani, N.; Garcia-Salicetti, S.; Dorizzi, B.; Montalvão, J.; Canuto, J.C.; Andrade, M.V.; Qiao, Y.; Wang, X.; Scheidat, T.; Makrushin, A.; et al. BioSecure Signature Evaluation Campaign (ESRA’2011): Evaluating systems on quality-based categories of skilled forgeries. In Proceedings of the 2011 International Joint Conference on Biometrics (IJCB), Washington, DC, USA, 11–13 October 2011; pp. 1–10. [Google Scholar]
- Impedovo, D.; Pirlo, G. Automatic signature verification in the mobile cloud scenario: Survey and way ahead. IEEE Trans. Emerg. Top. Comput. 2018, 1. [Google Scholar] [CrossRef]
- Houmani, N.; Garcia-Salicetti, S. Digitizing Tablet. In Encyclopedia of Biometrics, 2nd ed.; Springer: Boston, MA, USA, 2015; pp. 351–356. [Google Scholar]
- Di Lecce, V.; DiMauro, G.; Guerriero, A.; Impedovo, S.; Pirlo, G.; Salzo, A.; Sarcinella, L. Selection of Reference Signatures for Automatic Signature Verification. In Proceedings of the Fifth International Conference on Document Analysis and Recognition, ICDAR ’99 (Cat. No.PR00318), Bangalore, India, 22 September 1999; pp. 597–600. [Google Scholar]
- Guest, R.; Fairhurst, M. Sample selection for optimising signature enrolment. In Proceedings of the 10th International Workshop on Frontiers in Handwriting Recognition, La Baule, France, 23–26 October 2006. [Google Scholar]
- Kahindo, C.; Garcia-Salicetti, S.; Houmani, N. A Signature Complexity Measure to Select Reference Signatures for Online Signature Verification. In Proceedings of the 2015 International Conference of the Biometrics Special Interest Group (BIOSIG), Darmstadt, Germany, 9–11 September 2015; pp. 1–8. [Google Scholar]
- Tolosana, R.; Vera-Rodriguez, R.; Fierrez, J.; Ortega-Garcia, J. Exploring Recurrent Neural Networks for On-Line Handwritten Signature Biometrics. IEEE Access 2018, 6, 5128–5138. [Google Scholar] [CrossRef]
- Lai, S.; Jin, L.; Yang, W. Online Signature Verification Using Recurrent Neural Network and Length-Normalized Path Signature Descriptor. In Proceedings of the 2017 14th IAPR International Conference on Document Analysis and Recognition (ICDAR), Kyoto, Japan, 9–15 November 2017; pp. 400–405. [Google Scholar]
- Sekhar, C.; Mukherjee, P.; Guru, D.S.; Pulabaigari, V. OSVNet: Convolutional Siamese Network for Writer Independent Online Signature Verification. arXiv 2019, arXiv:1904.00240. Available online: https://arxiv.org/abs/1904.00240 (accessed on 7 February 2020).
- Wu, X.; Kimura, A.; Uchida, S.; Kashino, K. Prewarping Siamese Network: Learning Local Representations for Online Signature Verification. In Proceedings of the ICASSP 2019–2019 IEEE International Conference on Acoustics, Speech and Signal Processing (ICASSP), Brighton, UK, 12–17 May 2019; pp. 2467–2471. [Google Scholar]
- Martinez-Diaz, M.; Fierrez, J.; Galbally, J.; Ortega-Garcia, J. Towards mobile authentication using dynamic signature verification: Useful features and performance evaluation. In Proceedings of the 19th International Conference on Pattern Recognition, Tampa, FL, USA, 8–11 December 2008; pp. 1–5. [Google Scholar]
- Houmani, N.; Garcia-Salicetti, S.; Dorizzi, B.; El-Yacoubi, M. On-line signature verification on a mobile platform. In Proceedings of the International Conference on Mobile Computing Applications, and Services, Santa Clara, CA, USA, 25–28 October 2010; pp. 396–400. [Google Scholar]
- Houmani, N.; Garcia-Salicetti, S. Quality criteria for on-line handwritten signature. In Signal and Image Processing for Biometrics, ser. Lecture Notes in Electrical Engineering; Scharcanski, J., Proença, H., Du, E., Eds.; Springer: Berlin/Heidelberg, Germany, 2014; pp. 255–283. [Google Scholar]
- Blanco-Gonzalo, R.; Miguel-Hurtado, O.; Mendaza-Ormaza, A.; Sanchez-Reillo, R. Handwritten signature recognition in mobile scenarios: Performance evaluation. In Proceedings of the IEEE International Carnahan Conference on Security Technology (ICCST), Boston, MA, USA, 15–18 October 2012; pp. 174–179. [Google Scholar]
- Blanco-Gonzalo, R.; Sanchez-Reillo, R.; Hurtado, O.M.; Liu-Jimenez, J. Usability analysis of dynamic signature verification in mobile environments. In Proceedings of the International Conference of the BIOSIG Special Interest Group (BIOSIG), Darmstadt, Germany, 5–6 September 2013; pp. 1–9. [Google Scholar]
- Blanco-Gonzalo, R.; Sanchez-Reillo, R.; Liu-Jimenez, J.; Miguel-Hurtado, O. Performance evaluation of handwritten signature recognition in mobile environments. IET Biom. 2014, 3, 139–146. [Google Scholar] [CrossRef]
- Martinez-Diaz, M.; Fierrez, J.; Galbally, J. The DooDB Graphical Password Database: Data Analysis and Benchmark Results. IEEE Access 2013, 1, 596–605. [Google Scholar] [CrossRef]
- Martinez-Diaz, M.; Galbally, J.; Krish, R.P.; Fierrez, J. Mobile signature verification: Feature robustness and performance comparison. IET Biom. 2014, 3, 267–277. [Google Scholar] [CrossRef]
- Sae-Bae, N.; Memon, N. Online Signature Verification on Mobile Devices. IEEE Trans. Inf. Forensics Secur. 2014, 9, 933–947. [Google Scholar] [CrossRef]
- Antal, M.; Bandi, A. Finger or stylus: Their impact on the performance of on-line signature verification systems. MACRo 2015, 2, 11–22. [Google Scholar] [CrossRef]
- Antal, M.; Zsolt Szabó, L.; Tordai, T. Online Signature Verification on MOBISIG Finger-Drawn Signature Corpus. Mob. Inf. Syst. 2018, 2018, 3127042. [Google Scholar] [CrossRef]
- Tolosana, R.; Vera-Rodriguez, R.; Fierrez, J.; Morales, A.; Ortega-Garcia, J. Benchmarking desktop and mobile handwriting across COTS devices: The e-BioSign biometric database. PLOS ONE 2017, 12, e0176792. [Google Scholar] [CrossRef]
- Zareen, F.J.; Jabin, S. Authentic mobile-biometric signature verification system. IET Biom. 2016, 5, 13–19. [Google Scholar] [CrossRef]
- Nam, S.; Park, H.; Seo, C.; Choi, D. Forged Signature Distinction Using Convolutional Neural Network for Feature Extraction. Appl. Sci. 2018, 8, 153. [Google Scholar] [CrossRef]
- Garcia-Salicetti, S.; Houmani, N.; Dorizzi, B. A Novel Criterion for Writer Enrolment Based on a Time-Normalized Signature Sample Entropy Measure. EURASIP J. Adv. Signal Process. 2009, 2009, 964746. [Google Scholar] [CrossRef][Green Version]
- Salicetti, S.G.; Houmani, N.; Dorizzi, B. A client-entropy measure for On-line Signatures. In Proceedings of the Biometrics Symposium, Tampa, FL, USA, 23–25 September 2008; pp. 83–88. [Google Scholar]
- Houmani, N.; Garcia-Salicetti, S.; Dorizzi, B. A Novel Personal Entropy Measure confronted with Online Signature Verification Systems’ Performance. In Proceedings of the IEEE 2nd International Conference on Biometrics: Theory, Applications and Systems, Arlington, VA, USA, 29 September–1 October 2008; pp. 1–6. [Google Scholar]
- Houmani, N.; Garcia-Salicetti, S. On Hunting Animals of the Biometric Menagerie for Online Signature. PLoS ONE 2016, 11, e0151691. [Google Scholar] [CrossRef] [PubMed]
- Houmani, N.; Garcia-Salicetti, S.; Dorizzi, B. On measuring forgery quality in online signatures. Pattern Recognit. 2012, 45, 1004–1018. [Google Scholar] [CrossRef]
- Brault, J.J.; Plamondon, R. How to detect problematic signers for automatic signature verification. In Proceedings of the International Canadian Conference on Security Technology (ICCST), Zurich, Switzerland, 3–5 October 1989; pp. 127–132. [Google Scholar]
- Abazid, M.; Houmani, N.; Garcia-Salicetti, S. Impact of Spatial Constraints when Signing in Uncontrolled Mobile Conditions. In Proceedings of the ACM Workshop on Information Hiding and Multimedia Security, Paris, France, 3–5 July 2019; pp. 89–94. [Google Scholar]
- Ly Van, B.; Garcia-Salicetti, S.; Dorizzi, B. On using the Viterbi Path along with HMM Likelihood Information for On-line Signature Verification. IEEE Trans. Syst. Man Cybern. Part B Cybern. 2007, 37, 1237–1247. [Google Scholar] [CrossRef] [PubMed]
- Garcia-Salicetti, S.; Houmani, N.; Ly Van, B.; Dorizzi, B.; Alonso-Fernandez, F.; Fierrez, J.; Ortega-GarciaClaus, J.; Vielhauer, C.; Scheidat, T. On-line Handwritten Signature Verification. In Guide to Biometric Reference Systems and Performance Evaluation; Petrovska-Delacrétaz, D., Chollet, G., Dorizzi, B., Eds.; Springer: London, UK, 2009; pp. 125–164. [Google Scholar]
- Garcia-Salicetti, S.; Fierrez-Aguilar, J.; Alonso-Fernandez, F.; Vielhauer, C.; Guest, R.; Allano, L.; Trung, T.D.; Scheidat, T.; Ly Van, B.; Dittmann, J.; et al. Biosecure Reference Systems for On-Line Signature Verification: A Study of Complementarity. Ann. Telecommun. 2007, 62, 36–61. [Google Scholar]
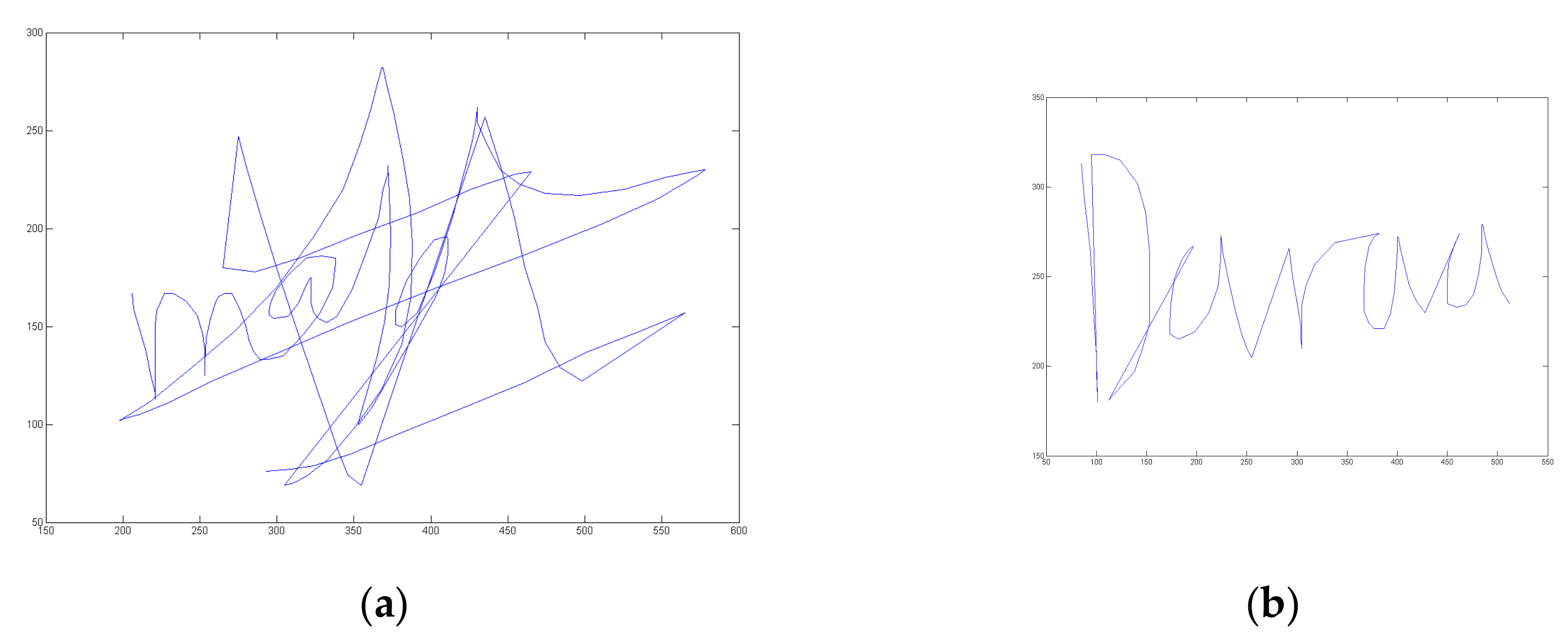

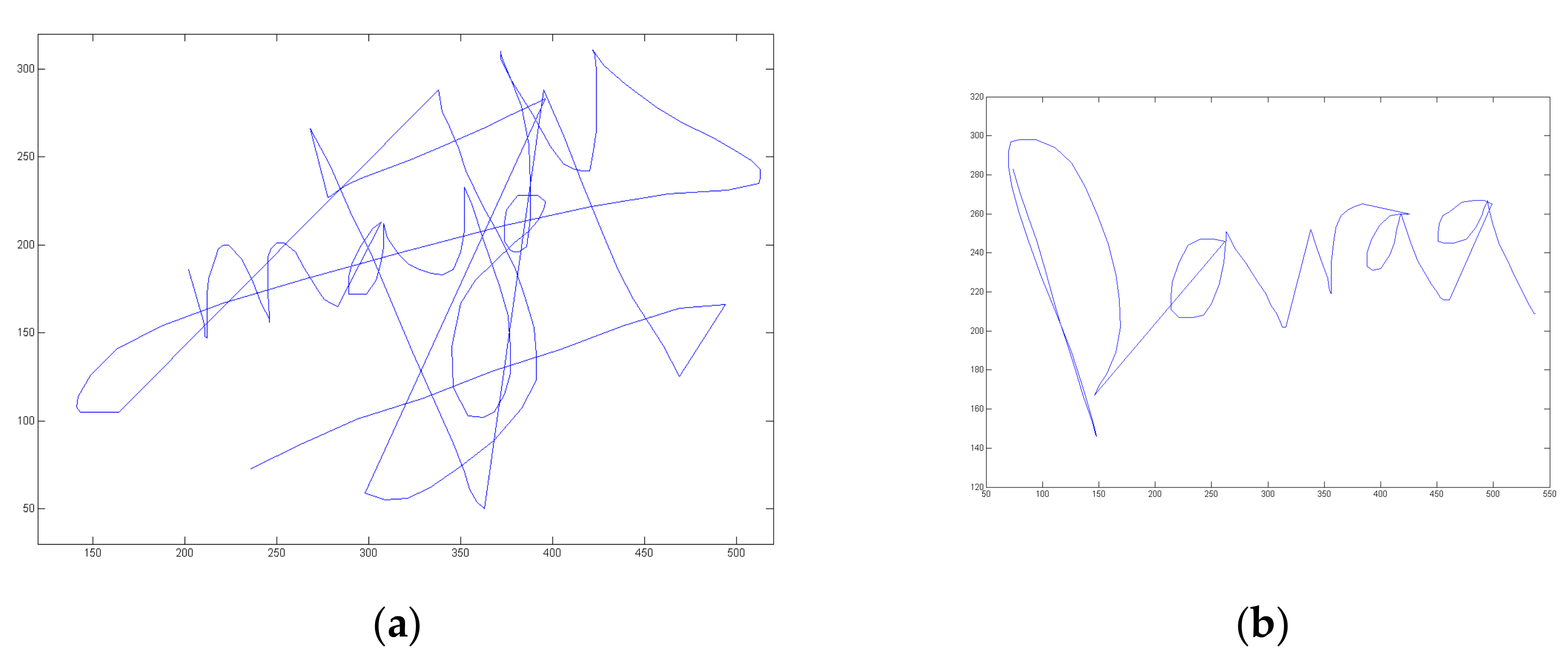




| Databases | Evaluation Campaigns | Year | Devices | Users | EER (in %) |
|---|---|---|---|---|---|
| DS2-382 [15] | BSEC’2009 | 2012 | Wacom tablet | 382 | 4.47 |
| DS3-382 [15] | BSEC’2009 | 2012 | PDA (stylus) | 382 | 11.27 |
| DS2-382 [16] | ESRA’2011 | 2011 | Wacom tablet | 382 | 2.73–4.04 |
| DS3-382 [16] | ESRA’2011 | 2011 | PDA (stylus) | 382 | 8.13–10.92 |
| DS3-210 [27] | - | 2010 | PDA (stylus) | 210 | 9.95 |
| PDA-64 [27] | - | 2010 | PDA (stylus) | 64 | 16.02 |
| iPad-74 [46] | - | 2019 | iPad (stylus) | 74 | 7.04 |
| iPhone-74 [46] | - | 2019 | iPhone (stylus) | 74 | 4.95 |
| BIOMET [47] | - | 2007 | Wacom tablet | 84 | 2.33 |
| PHILIPS [47] | - | 2007 | Digitizing tablet | 51 | 3.25 |
| SVC2004 [47] | - | 2007 | Digitizing tablet | 40 | 4.83 |
| MCYT-100 [47] | - | 2007 | Wacom tablet | 100 | 3.37 |
| MCYT-330 [48] | - | 2009 | Wacom tablet | 330 | 3.91 |
| Databases | Year | Users | Sensor | EER (in %) |
|---|---|---|---|---|
| ATVS-DooDB [32] | 2013 | 100 | HTC Touch HD (Pseudo-signatures) | Finger: 26.9 |
| Blanco-Gonzalo et al. [31] | 2013 | 43 | Asus Eee PC Touch (stylus) Samsung Gal. Note (stylus/finger) BlackBerry Playbook (finger) Apple Ipad2 (finger) Samsung Gal. Tab (finger) | - |
| e-Biosign [37] | 2016 | 65 | Samsung ATIV7 Samsung Gal. Note | Stylus: 7.9 Finger: 22.1 Stylus: 10.7 Finger: 26.4 |
| Zareen and Jabin [38] | 2016 | 25 | Samsung Gal. Note | - |
| MOBISIG [36] | 2018 | 83 | Nexus 9 tablet capacitive (Finger-drawn pseudo-signatures) | Personalized vs. global threshold: 8.56% vs. 25.45% |
| Nam et al. [39] | 2018 | 20 | Samsung Gal. S3 | Finger: 4.4% |
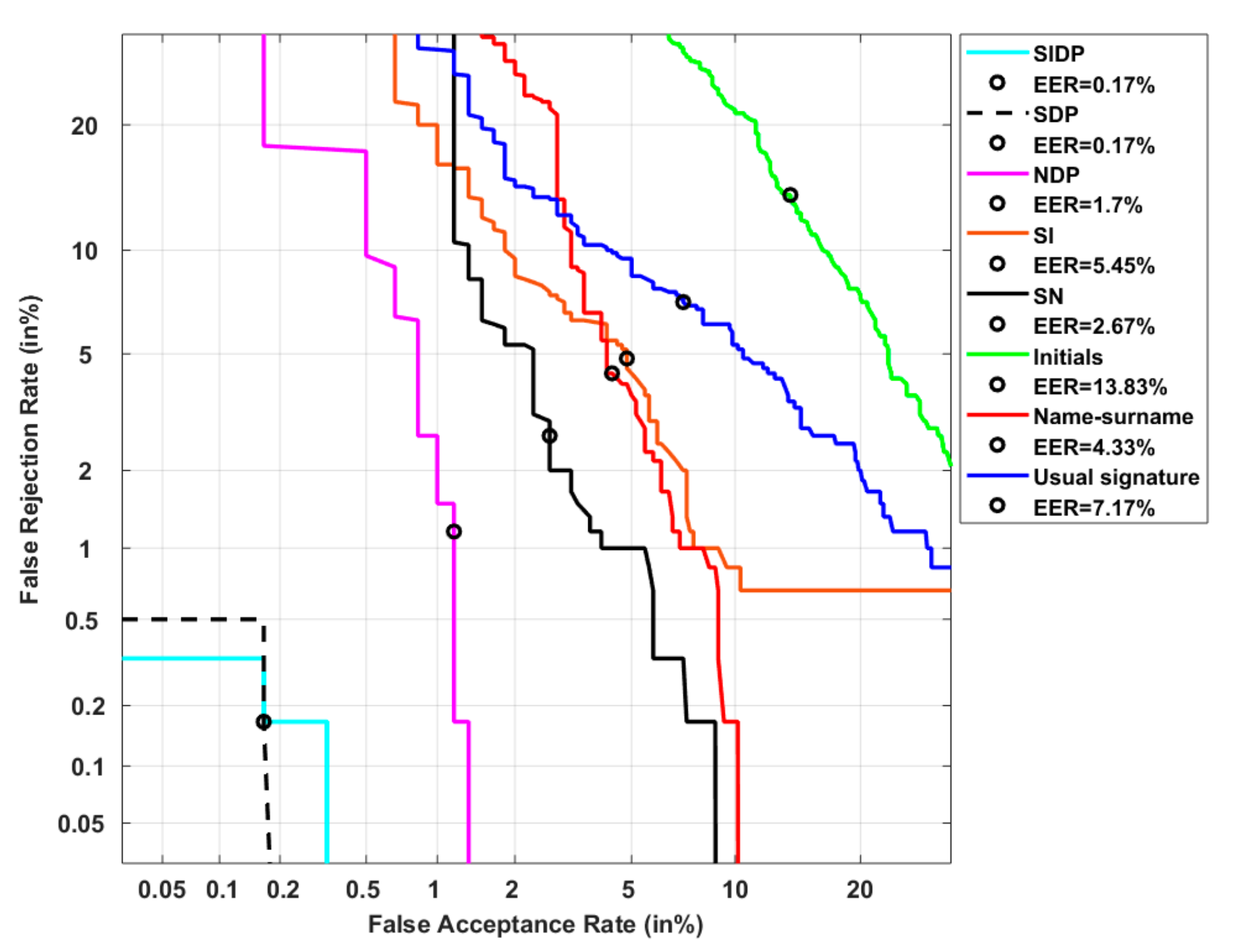
| Type of Signatures | EER |
|---|---|
| Usual signature | 7.17% |
| Initials | 13.83% |
| Name-surname | 4.33% |
| SN | 2.67% |
| SI | 5.45% |
| NDP | 1.7% |
| SDP | 0.17% |
| SIDP | 0.17% |
| Type of Signatures | EER |
|---|---|
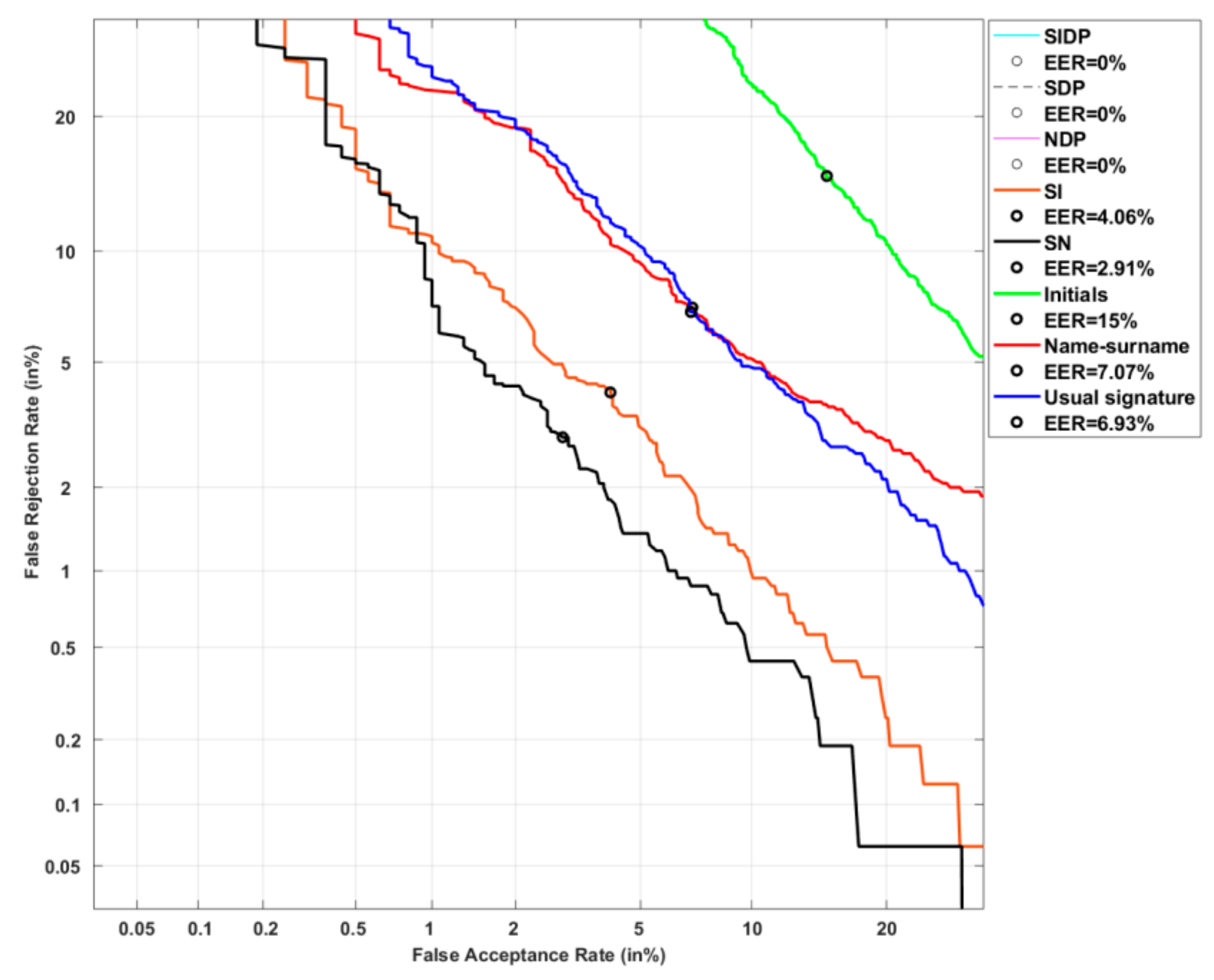
| Usual signature | 6.93% |
| Initials | 15% |
| Name-surname | 7.07% |
| SN | 2.91% |
| SI | 4.06% |
| NDP | 0% |
| SDP | 0% |
| SIDP | 0% |
| Type of Signatures | EER |
|---|---|
| Usual signature | 5.93% |
| Initials | 16.07% |
| Name-surname | 5.97% |
| SN | 2.3% |
| SI | 3.33% |
| NDP | 0.47% |
| SDP | 0.4% |
| SIDP | 0.5% |
© 2020 by the authors. Licensee MDPI, Basel, Switzerland. This article is an open access article distributed under the terms and conditions of the Creative Commons Attribution (CC BY) license (http://creativecommons.org/licenses/by/4.0/).
Share and Cite
Abazid, M.; Houmani, N.; Garcia-Salicetti, S. Enhancing Security on Touch-Screen Sensors with Augmented Handwritten Signatures. Sensors 2020, 20, 933. https://doi.org/10.3390/s20030933
Abazid M, Houmani N, Garcia-Salicetti S. Enhancing Security on Touch-Screen Sensors with Augmented Handwritten Signatures. Sensors. 2020; 20(3):933. https://doi.org/10.3390/s20030933
Chicago/Turabian StyleAbazid, Majd, Nesma Houmani, and Sonia Garcia-Salicetti. 2020. "Enhancing Security on Touch-Screen Sensors with Augmented Handwritten Signatures" Sensors 20, no. 3: 933. https://doi.org/10.3390/s20030933
APA StyleAbazid, M., Houmani, N., & Garcia-Salicetti, S. (2020). Enhancing Security on Touch-Screen Sensors with Augmented Handwritten Signatures. Sensors, 20(3), 933. https://doi.org/10.3390/s20030933





