Dynamic Adaptive Cross-Chain Trading Mode for Multi-Microgrid Joint Operation
Abstract
1. Introduction
- The existing cross-chain technology mainly guarantees the atomicity of asset interaction by means of electronic cryptocurrency deployment. Due to the complex logic of upstream routing and asset interaction in general digital assets [15], it cannot be applied to the lightweight cross-chain dynamic adaptive interaction scenario of energy blockchains directly.
- The underlying architecture and consensus mechanism of each energy blockchain network may be different [18]. Therefore, it is necessary to establish a universal and reliable dynamic adaptive cross-chain consensus mechanism without changing the original operation mechanism of each system.
- The power system data is so huge and changes so instantaneously that it requires higher operation efficiency for multi-microgrid. The existing cross-chain key management pays little attention to data throughput and system operational efficiency.
- We propose a proof of credit threshold consensus mechanism for cross-chain communication to achieve effective information verification. This consensus mechanism can ensure the adaptive consistency of cross-chain information without changing the existing blockchain architecture of each system.
- We design a corresponding key management interoperability protocol though an optimized RSA algorithm based on Chinese remainder theorem, and this communication protocol can realize effective data transfer and information consensus for cross-chain transactions.
- To analyze the feasibility of the cross-chain trading mode used in multiple energy systems, we verify the effectiveness, security and operational efficiency through theoretical and experimental results.
2. Background and Related Work
2.1. Energy Blockchain
2.2. Cross-Chain Interoperability
2.3. Cross-Chain Technology in the Energy Field
3. Cross-Chain Transaction for Multi-Microgrid
3.1. Multi-Microgrid Joint Operation Architecture
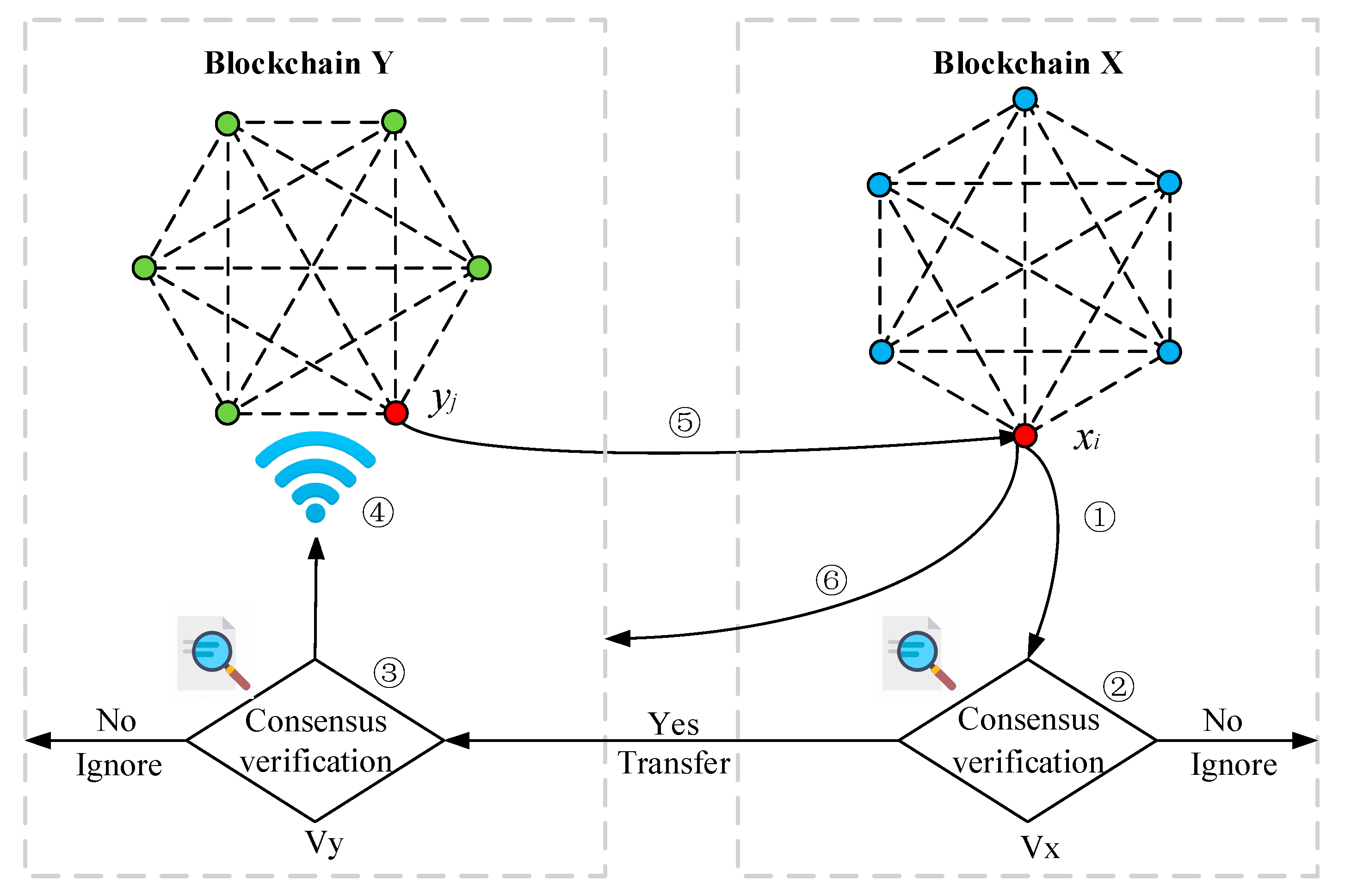
3.2. Cross-Chain Communication Process
- constructs a figure identity certificate and a data transfer key , and then writes the description of the cross-chain trading requirements . The details of the power transaction and the deadline are written into a smart contract , and this smart contract is deployed.
- verifies the trading requirement by the consensus mechanism presented in Section 4. If the verification is successful, the key is updated and a new smart contract is built. Then the cross-chain transaction requirements are sent to . If the verification is not passed, the trading requirement is ignored.
- verifies the trading requirement . If the verification is successful, the key is updated and a new smart contract is built. The smart contract broadcasts to all nodes in blockchain Y. If the verification is not passed, is ignored.
- The node in blockchain Y is expected to conclude a deal with based on the trading requirement . If Equations (3)–(5) are true, updates the key and writes the blind response result Reply(). Then deploy the corresponding power transaction replay to . If Equations (3)–(5) are false, the power transaction is ignored.where indicates the upper limit of the time to deploy or execute a smart contract, or indicates the upper limit of single-hop response time. is the proof of information traceability and trustworthiness. and respectively indicate the key and corresponding digital signature of to .
- verifies the smart contract from . If it passes, writes the hash function of power trading information into the smart contract and extracts the response result Reply(). returns the power transaction key to when the smart contract executes. Other cross-chain transactions are executed in turn similarly to the above stages.
- After the power transaction protocol is executed, and broadcast the cross-chain certificate to the multi-microgrid system respectively.
4. Proof of Credit Threshold Consensus Mechanism
4.1. Threshold Signature for Cross-Blockchain Communication
4.2. Credit Evaluation of Microgrid Power Transactions
5. Key Management Interoperability Protocol in Cross-Chain
5.1. Optimized RSA Algorithm based on Chinese Remainder Theorem
5.2. Key Management Interoperability Protocol
6. Theoretical Analysis
6.1. Effectiveness Analysis
6.2. Security Analysis
7. Case Study
7.1. Experimental Deployment
7.2. Experimental Results and Discussions
8. Conclusions
Author Contributions
Funding
Conflicts of Interest
References
- Barros, E.B.C.; Batista, B.G.; Kuehne, B.T.; Peixoto, M.L.M. Fog Computing Model to Orchestrate the Consumption and Production of Energy in Microgrids. Sensors 2019, 19, 2642. [Google Scholar] [CrossRef]
- Du, Y.; Wang, Z.; Liu, G.; Chen, X.; Yuan, H.; Wei, Y.; Li, F. A cooperative game approach for coordinating multi-microgrid operation within distribution systems. Appl. Energy 2018, 222, 383–395. [Google Scholar] [CrossRef]
- Xia, S.; Chan, K.W.; Luo, X.; Bu, S.; Ding, Z.; Zhou, B. Optimal sizing of energy storage system and its cost-benefit analysis for power grid planning with intermittent wind generation. Renew. Energy 2018, 122, 472–486. [Google Scholar] [CrossRef]
- Lin, C.; Wu, W.; Zhang, B.; Sun, Y. Decentralized solution for combined heat and power dispatch through benders decomposition. IEEE Trans. Sustain. Energy 2017, 8, 1361–1372. [Google Scholar] [CrossRef]
- Wang, J.; Wang, Q.; Zhou, N.; Chi, Y. A novel electricity transaction mode of microgrids based on blockchain and continuous double auction. Energies 2017, 10, 1971. [Google Scholar] [CrossRef]
- Croce, D.; Giuliano, F.; Tinnirello, I.; Giarré, L. Privacy-Preserving Overgrid: Secure Data Collection for the Smart Grid. Sensors 2020, 20, 2249. [Google Scholar] [CrossRef]
- Afrakhte, H.; Bayat, P. A self-evolving type-2 fuzzy energy management strategy for multi-microgrid systems. Comput. Electr. Eng. 2020, 85, 106702. [Google Scholar] [CrossRef]
- Xia, S.; Bu, S.; Wan, C.; Lu, X.; Chan, K.W.; Zhou, B. A fully distributed hierarchical control framework for coordinated operation of DERs in active distribution power networks. IEEE Trans. Power Syst. 2019, 34, 5184–5197. [Google Scholar] [CrossRef]
- Miglani, A.; Kumar, N.; Chamola, V.; Zeadally, S. Blockchain for Internet of Energy management: Review, solutions, and challenges. Comput. Commun. 2020, 151, 395–418. [Google Scholar] [CrossRef]
- Ali, O.; Ally, M.; Dwivedi, Y. The state of play of blockchain technology in the financial services sector: A systematic literature review. Int. J. Inf. Manag. 2020, 54, 102199. [Google Scholar] [CrossRef]
- Noor, S.; Yang, W.; Guo, M.; Dama, K.; Wang, X. Energy Demand Side Management within micro-grid networks enhanced by blockchain. Appl. Energy 2018, 228, 1385–1398. [Google Scholar] [CrossRef]
- Ahl, A.; Yarime, M.; Tanaka, K.; Sagawa, D. Review of blockchain-based distributed energy: Implications for institutional development. Renew. Sustain. Energy Rev. 2019, 107, 200–211. [Google Scholar] [CrossRef]
- Alladi, T.; Chamola, V.; Rodrigues, J.J.; Kozlov, S.A. Blockchain in smart grids: A review on different use cases. Sensors 2019, 19, 4862. [Google Scholar] [CrossRef]
- Deng, L.; Chen, H.; Zeng, J.; Zhang, L.-J. Research on cross-chain technology based on sidechain and hash-locking. In Proceedings of the International Conference on Edge Computing, Seattle, WA, USA, 25–30 June 2018; pp. 144–151. [Google Scholar]
- Qiao, R.; Luo, X.-Y.; Zhu, S.-F.; Liu, A.-D.; Yan, X.-Q.; Wang, Q.-X. Dynamic Autonomous Cross Consortium Chain Mechanism in e-Healthcare. IEEE J. Biomed. Health Inform. 2020, 24, 2157–2168. [Google Scholar] [CrossRef] [PubMed]
- Zeng, Z.; Li, Y.; Cao, Y.; Zhao, Y.; Zhong, J.; Sidorov, D.; Zeng, X. Blockchain Technology for Information Security of the Energy Internet: Fundamentals, Features, Strategy and Application. Energies 2020, 13, 881. [Google Scholar] [CrossRef]
- Xu, X.; Zeng, Z.; Yang, S.; Shao, H. A Novel Blockchain Framework for Industrial IoT Edge Computing. Sensors 2020, 20, 2061. [Google Scholar] [CrossRef]
- Wang, N.; Zhou, X.; Lu, X.; Guan, Z.; Wu, L.; Du, X.; Guizani, M. When energy trading meets blockchain in electrical power system: The state of the art. Appl. Sci. 2019, 9, 1561. [Google Scholar] [CrossRef]
- Andoni, M.; Robu, V.; Flynn, D.; Abram, S.; Geach, D.; Jenkins, D.; McCallum, P.; Peacock, A. Blockchain technology in the energy sector: A systematic review of challenges and opportunities. Renew. Sustain. Energy Rev. 2019, 100, 143–174. [Google Scholar] [CrossRef]
- Reid, F.; Harrigan, M. An analysis of anonymity in the bitcoin system. In Security and Privacy in Social Networks; Springer: New York, NY, USA, 2013; pp. 197–223. [Google Scholar]
- Wu, J.; Tran, N.K. Application of blockchain technology in sustainable energy systems: An overview. Sustainability 2018, 10, 3067. [Google Scholar] [CrossRef]
- Mengelkamp, E.; Gärttner, J.; Rock, K.; Kessler, S.; Orsini, L.; Weinhardt, C. Designing microgrid energy markets: A case study: The Brooklyn Microgrid. Appl. Energy 2018, 210, 870–880. [Google Scholar] [CrossRef]
- Sikorski, J.; Haughton, J.; Kraft, M. Blockchain technology in the chemical industry: Machine-to-machine electricity market. Appl. Energy 2017, 195, 234–246. [Google Scholar] [CrossRef]
- Kim, S.K.; Huh, J.H. Blockchain of Carbon Trading for UN Sustainable Development Goals. Sustainability 2020, 12, 4021. [Google Scholar] [CrossRef]
- Su, Z.; Wang, Y.; Xu, Q.; Fei, M.; Tian, Y. A secure charging scheme for electric vehicles with smart communities in energy blockchain. IEEE Internet Things J. 2018, 6, 4601–4613. [Google Scholar] [CrossRef]
- Schulte, S.; Sigwart, M.; Frauenthaler, P.; Borkowski, M. Towards blockchain interoperability. In Proceedings of the International Conference on Business Process Management, Vienna, Austria, 1–6 September 2019; pp. 3–10. [Google Scholar]
- Scheid, E.J.; Hegnauer, T.; Rodrigues, B.; Stiller, B. Bifröst: A Modular Blockchain Interoperability API. In Proceedings of the 2019 IEEE 44th Conference on Local Computer Networks, Osnabruck, Germany, 14–17 October 2019; pp. 332–339. [Google Scholar]
- Kannengießer, N.; Pfister, M.; Greulich, M.; Lins, S.; Sunyaev, A. Bridges between islands: Cross-chain technology for distributed ledger technology. In Proceedings of the 53rd Hawaii International Conference on System Sciences, Maui, HI, USA, 7–10 January 2020. [Google Scholar]
- Lunardi, R.C.; Michelin, R.A.; Neu, C.V.; Zorzo, A.F. Distributed access control on iot ledger-based architecture. In Proceedings of the NOMS 2018–2018 IEEE/IFIP Network Operations and Management Symposium, Taipei, Taiwan, 23–27 April 2018; pp. 1–7. [Google Scholar]
- Deshpande, A.; Herlihy, M. Privacy-Preserving Cross-Chain Atomic Swaps. In Proceedings of the International Conference on Financial Cryptography and Data Security, Istanbul, Turkey, 6–7 May 2020; pp. 540–549. [Google Scholar]
- Pop, C.; Antal, M.; Cioara, T.; Anghel, I.; Sera, D.; Salomie, I.; Raveduto, G.; Ziu, D.; Croce, V.; Bertoncini, M. Blockchain-based scalable and tamper-evident solution for registering energy data. Sensors 2019, 19, 3033. [Google Scholar] [CrossRef] [PubMed]
- She, W.; Gu, Z.; Yang, X.; Tian, Z.; Chen, J.; Liu, W. Multi-energy complementary secure transaction model of heterogeneous energy blockchain. Power Grid Technol. 2019, 16. [Google Scholar] [CrossRef]
- Sestrem Ochôa, I.; Augusto Silva, L.; de Mello, G.; Garcia, N.M.; de Paz Santana, J.F.; Quietinho Leithardt, V.R. A Cost Analysis of Implementing a Blockchain Architecture in a Smart Grid Scenario Using Sidechains. Sensors 2020, 20, 843. [Google Scholar] [CrossRef]
- Daghmehchi Firoozjaei, M.; Ghorbani, A.; Kim, H.; Song, J. Hy-Bridge: A hybrid blockchain for privacy-preserving and trustful energy transactions in Internet-of-Things platforms. Sensors 2020, 20, 928. [Google Scholar] [CrossRef] [PubMed]
- He, H.; Luo, Z.; Wang, Q.; Chen, M.; He, H.; Gao, L.; Zhang, H. Joint Operation Mechanism of Distributed Photovoltaic Power Generation Market and Carbon Market Based on Cross-Chain Trading Technology. IEEE Access 2020, 8, 66116–66130. [Google Scholar] [CrossRef]
- Singh, N.; Elamvazuthi, I.; Nallagownden, P.; Ramasamy, G.; Jangra, A. Routing Based Multi-Agent System for Network Reliability in the Smart Microgrid. Sensors 2020, 20, 2992. [Google Scholar] [CrossRef] [PubMed]
- Lyu, Z.; Yang, X.; Zhang, Y.; Zhao, J. Bi-level Optimal Strategy of Islanded Multi-microgrid Systems Based on Optimal Power Flow and Consensus Algorithm. Energies 2020, 13, 1537. [Google Scholar] [CrossRef]
- Yang, H.; Xiong, S.; Frimpong, S.A.; Zhang, M. A Consortium Blockchain-Based Agricultural Machinery Scheduling System. Sensors 2020, 20, 2643. [Google Scholar] [CrossRef] [PubMed]
- Helal, S.A.; Hanna, M.O.; Najee, R.J.; Shaaban, M.F.; Osman, A.H.; Hassan, M.S. Energy Management System for Smart Hybrid AC/DC Microgrids in Remote Communities. Electr. Power Compon. Syst. 2019, 47, 1012–1024. [Google Scholar] [CrossRef]
- Wan, S.; Li, M.; Liu, G.; Wang, C. Recent advances in consensus protocols for blockchain: A survey. Wirel. Netw. 2019, 26, 5579–5593. [Google Scholar] [CrossRef]
- Banubakode, A.; Patil, P.; Bhandare, S.; Wattamwar, S.; Muchrikar, A. Key Management Interoperability Protocol-Based Library for Android Devices. In Artificial Intelligence and Evolutionary Computations in Engineering Systems; Springer: Berlin/Heidelberg, Germany, 2018; pp. 315–323. [Google Scholar]
- Yang, L.T.; Huang, G.; Feng, J.; Xu, L. Parallel GNFS algorithm integrated with parallel block Wiedemann algorithm for RSA security in cloud computing. Inf. Sci. 2017, 387, 254–265. [Google Scholar] [CrossRef]
- Jiang, Y.; Shen, Y.; Zhu, Q. A Lightweight Key Agreement Protocol Based on Chinese Remainder Theorem and ECDH for Smart Homes. Sensors 2020, 20, 1357. [Google Scholar] [CrossRef]
- Yang, B. Modern Cryptography, 4th ed.; Tsinghua University Press: Beijing, China, 2017; pp. 84–134. [Google Scholar]






| Work | Year | Technical Type | Technical Contribution | Application Scenarios |
|---|---|---|---|---|
| Pop et al. [31] | 2019 | Hash-locking | Response time and data throughput | Smart energy grid |
| She et al. [32] | 2019 | Relays method | Trust transaction | Multiple energy transaction |
| Ochôa et al. [33] | 2020 | Sidechain | Solving privacy and security problems | Smart grid |
| Firoozjaei et al. [34] | 2020 | Hybrid blockchain | Privacy-preserving and trustful | Energy transaction in IOT platforms |
| He et al. [35] | 2020 | Sidechain | Cross-system trading | Joint operation of PV and carbon markets |
Publisher’s Note: MDPI stays neutral with regard to jurisdictional claims in published maps and institutional affiliations. |
© 2020 by the authors. Licensee MDPI, Basel, Switzerland. This article is an open access article distributed under the terms and conditions of the Creative Commons Attribution (CC BY) license (http://creativecommons.org/licenses/by/4.0/).
Share and Cite
Wang, L.; Wu, J.; Yuan, R.; Zhang, D.; Liu, J.; Jiang, S.; Zhang, Y.; Li, M. Dynamic Adaptive Cross-Chain Trading Mode for Multi-Microgrid Joint Operation. Sensors 2020, 20, 6096. https://doi.org/10.3390/s20216096
Wang L, Wu J, Yuan R, Zhang D, Liu J, Jiang S, Zhang Y, Li M. Dynamic Adaptive Cross-Chain Trading Mode for Multi-Microgrid Joint Operation. Sensors. 2020; 20(21):6096. https://doi.org/10.3390/s20216096
Chicago/Turabian StyleWang, Longze, Jing Wu, Rongfang Yuan, Delong Zhang, Jinxin Liu, Siyu Jiang, Yan Zhang, and Meicheng Li. 2020. "Dynamic Adaptive Cross-Chain Trading Mode for Multi-Microgrid Joint Operation" Sensors 20, no. 21: 6096. https://doi.org/10.3390/s20216096
APA StyleWang, L., Wu, J., Yuan, R., Zhang, D., Liu, J., Jiang, S., Zhang, Y., & Li, M. (2020). Dynamic Adaptive Cross-Chain Trading Mode for Multi-Microgrid Joint Operation. Sensors, 20(21), 6096. https://doi.org/10.3390/s20216096





