1. Introduction
Multihop Sensor Networks are a collection of sensors equipped with a wireless interface, each of which uses other nodes as relays. This type of network presents various advantages over traditional wired networks, mainly the ease of deployment. In sensor networks, it becomes necessary to measure variables over a vast region. Multihop Sensor Networks can also be found in the IoT networks by seeking to interconnect all things surrounding people with their environment to gather data from those things [
1,
2]. However, the one aspect that makes these networks both attractive and challenging is the nodes’ ability to communicate over long distances using other nodes as relays. In this sense, it is common that nodes seek a specific resource (such as a sensor with specific capabilities, a sink to transmit it or even finding a route to a specific node) before exchanging data [
3].
Resource discovery can be achieved by using a traditional flooding technique where the resource is searched over all the possible nodes in the network. Although more complex route discovery protocols exist, traditional flooding remains the most widely used protocol in practice. In this protocol, a source node broadcasts a search packet looking for a specific target node. This packet is received only by nodes located within the source node’s transmission range. Upon receiving a search packet, a node adds its node ID to the packet header and retransmits it as soon as possible. This process continues until every node in the network has retransmitted the search packet. Once a search packet reaches the target node, it can respond to the source node, using unicast packets, through the reverse route stored in the packet header. Traditional flooding represents a robust and straightforward solution for route discovery, but it generates many packets, consuming much bandwidth [
4]. Even though nodes in traditional flooding retransmit search packets once, many collisions may occur in densely populated networks due to a large number of nodes transmitting search packets simultaneously [
5,
6]. These collisions generate unnecessary retransmissions, increasing contention, and channel access delays for both control and data packets. This problem is known as the broadcast storm problem [
4,
7].
Various authors have proposed alternative methods to route discovery in ad hoc and sensor networks to address traditional flooding drawbacks. Although these protocols were originally designed for routing, these can also be applied to a resource discovery flooding. The following section presents a discussion of this issue in detail. However, most approaches attempt to repeal the propagation of flooded packets with chase flooding once either the source or target nodes reach each other. In general, protocols where the chase initiates at the destination are more efficient at stopping earlier the propagation of flooded packets. Repeal-based schemes can also be classified as bounded or unbounded, depending on the area nodes are allowed to chase and stop the propagation of the original flooding. Unbounded protocols allow any target node at any distance from the source node to chase the original flooding. On the other hand, bounded protocols allow a target node to chase ongoing flooding only if located within a given hop count from the source node. If the target node is not found, the maximum hop count is increased until, at a given hop count distance, the target node is finally found.
However, repeal-based protocols source or destination initiated, bounded or unbounded might end up transmitting even more signaling packets than the original flooding protocol they try to outperform.
Figure 1 illustrates, in general terms, the behavior of most repeal-based flooding protocols vs. Flood and Contain (F&C). This figure is not the result of any simulation experiment, but a trending behavior observed in other works and the simulations performed at the end of this work (refer to Figure 13). In this figure, the number of signaling packets considering both the original flooding and chase packets is plotted against the hop-count separating source and destination nodes. As a reference, the number of packets generated by traditional flooding is shown as a constant number, indicating all nodes in the network always participated in the flooding process. As
Figure 1 shows, repeal-based protocols are efficient only when the source and destination nodes are somewhat near to each other; otherwise, they can generate even more signaling packets than the original flooding. The main idea behind F&C is to have a mechanism that generates an overhead similar to repeal-based flooding schemes for near destinations, and behaves like traditional flooding for distant destinations. The critical point to achieve such a behavior is to allow each node to establish its optimized repeal-flooding boundary beyond which there is no attempt to chase and stop propagating the original flooding. Establishing and finding such an optimized repeal-flooding boundary is the key contribution of F&C and what sets this protocol apart from other repeal-based schemes.
The main features of the F&C algorithm are as follows:
F&C reduces the number of control messages over the whole network, thus saving energy and making the network more resistant to some Vampire Energy Depletion Attacks [
8].
F&C protocol establishes a repeal-flooding boundary that delimits if the flooding is worth attempting to stop, allowing each node to decide whether it should initiate a chase flooding independently.
Experiments demonstrate that F&C achieves an optimized performance with as few as just one previous chase flooding, and its performance is relatively immune to variations in the network shape, node density, and mobility patterns.
F&C’s signaling overhead is proportional to the distance separating source and target nodes before the repeal-flooding boundary. This behavior makes F&C appeal to applications where the target node is located close to the source node, as in some IoT applications [
1,
2].
Considering all possible locations of the source and target nodes within the network, F&C generates up to 35 percent fewer signaling packets on average, compared with traditional flooding. Other repeal-based schemes might transmit even more signaling packets on average than traditional flooding.
F&C maintains a lower than or equal delay, compared with other repeal-based schemes. That is, it behaves at least as good as them while reducing the delay when the target node is far from the source node in terms of hops.
The rest of this paper is organized as follows.
Section 2 presents relevant research related to reducing the overhead of flooding, particularly protocols based on chasing the original flooding.
Section 3 presents a detailed description of the F&C algorithm.
Section 4 describes how F&C allows each node to estimate its optimized repeal-flooding boundary.
Section 5 describes the experiments conducted on the F&C algorithm as well as on other repeal-based schemes, and
Section 6 presents the conclusions.
2. Related Work
Table 1 summarises the previous works made for trying to contain the overhead that traditional flooding generates. All protocols listed share a standard behavior; they chase the original flooding once the target node is found, attempting to stop further propagation of flooded packets in the rest of the network. Repeal-based protocols can be divided according to the entity that initiates the chase flooding into Broadcast-Repealing-Initiated in Source (BRIS) or Broadcast-Repealing-Initiated in the Destination (BRID). These protocols can also be divided into bounded, if the chase packet is bounded to an area (usually defined by a TTL), and unbounded if the chase packet can go along the whole network. Also, the protocols use different broadcasting speeds to allow the chase of the flooding messages. Such speed usually depends on the time required to transmit a packet
, and the number of hops between the source and the retransmitting node
d. Another distinctive feature of these protocols is the propagation strategy used during the initial and chase floodings. For example, protocols can use different propagation speeds for the initial and chase floodings, delay packets during the initial flooding so they can be reached by chasing packets, or might use one speed inside a ring and a different one outside the ring.
In L-B [
9], the authors introduced the first attempt to contain the propagation of flooded packets by chasing the Resource Request (RQ) packets after the source node received a Resource Reply (RP) packet. The L-B protocol relies on different speeds for transmitting the RQ and the chase packet, with the chase packet speed being faster. In LHBA [
11], they improved the chasing time by starting the chase in the destination rather than in the source. BERS [
12] proposed a ring-search mechanism to reduce the energy consumption of TTL-Expanding Ring Search widely used by some reactive routing protocols. This mechanism was improved by BERS+ [
13], where the ring expands without the need of retransmitting the original RQ from the source, but it resumes the expansion from the last ring. An update was performed in BERS* [
15] by halving the waiting time in each ring, thus speeding up the route discovery. In [
17], the chase stage occurs in the receiver rather than in the source node as performed earlier. In [
14], the authors used the ring as a boundary to retransmit the RQ at two different speeds. Inside the ring, the RQ travels at speed
while out of it, it travels at speed
where
. AODV-PC [
16] improved [
14] by starting the chasing in the receiver. ABC [
20] retransmits the RQ only to areas where it is more probable to find the destination node to prevent arbitrary flooding. This scheme has the disadvantage that it needs some previous information about routes, as well as topological information. A clustered version that combines BERS+ and MPR is presented in [
21], where the authors reduced the number of broadcasts by selecting appropriate cluster heads.
Unbounded protocols (L-R, BERS+, TLRDA-C, AODV-PCABC, CMBERS+) do not establish a limit or boundary for the chase packets to contain the original flooding. As a result, these protocols can easily transmit more packets than traditional flooding alone. This behavior occurs when the distance between the source and destination is equal to or greater than the network radius, which is a frequent event. Bounded protocols (ERS, LHBA, BERS, BERS*, tBERS, BCIR, I-BERS) try to avoid the previous drawback by placing a ring-boundary defined by the source-destination hop count beyond which no chase packets can cross.
However, the performance of bounded and unbounded protocols might not always be what their authors expected. As
Section 5 shows, bounded and unbounded protocols perform well only when the source and destination nodes are close to each other; otherwise, the added signaling of the original and chase flooding might easily become higher than the signaling of traditional flooding alone. As
Section 4 shows, there exists an optimized repeal-flooding boundary, for any source-destination pair beyond it is counterproductive to chase the original flooding. Finding such boundary for chase packets is not a trivial task. Placing the boundary too close to the source makes chasing the original flooding unlikely as most destinations are usually located outside such boundary. Remember that only destinations found inside the repeal-flooding boundary contain the original flooding by using chase packets. On the other hand, placing the boundary farther away from the source increases the number of destinations allowed to chase the original flooding; however, adding up the overhead of the original flooding and chase packets may end up being higher than the overhead of traditional flooding.
This paper introduces Flood and Contain (F&C), a repeal-based flooding algorithm that can quickly establish the optimized repeal-flooding boundary for each node without making any assumptions on the underlying network. F&C falls into the BRID category that uses two separate flooding processes as most repeal-based schemes; however, opposite to other proposals, F&C does not attempt to chase the original flooding beyond the optimized repeal-flooding boundary. The evaluation section presents the conducted overhead and delays comparisons among the most significant repeal-based protocols listed in
Table 1 and F&C to emphasize the improved qualities of the proposed algorithm.
There are other strategies proposed in the literature to reduce the signaling overhead of route discovery that do not consider the use of chase packets at any phase of their operation [
22,
23] and therefore are not directly comparable to F&C. For example, in [
24,
25], the authors proposed a probabilistic scheme for broadcasting search packets. Within such a scheme, upon receiving a search packet, a node rebroadcasts it with a specific probability (
p). Probabilistic flooding reduces transmission redundancy, but it does not guarantee that all nodes receive the search packet, due to the fact that
p is set to a fixed value [
26]. In [
27], the authors proposed a dynamic probabilistic scheme, in which each node uses a parameter for counting the number of times a packet was received, using it as a node density estimator. Other methods use neighbor-knowledge to form clusters and minimize the broadcast messages produced by flooding. One example is MPR (MultiPoint Relay) [
28], in which each node periodically broadcasts hello messages to obtain a list of all its two-hop neighbors. Every node selects some symmetric nodes in its neighborhood called MultiPoint Relays, and only those nodes are selected to retransmit route search packets. In MPR, the number of retransmissions depends on the number of multipoint relays selected. MPR, used by OLSR (Optimized Link State Routing) [
29], reduces duplicated retransmissions locally. However, maintaining this physical organization of the multipoint relays involves the use of a significant amount of signaling. The area-based method [
22] is a different strategy for flooding packets in search of a destination, in which nodes use location information to decide whether or not to rebroadcast search packets. This method’s main disadvantage is that it relies on location hardware.
3. Flood and Contain (F&C)
The main goal of F&C is to stop further propagation of a flooding search once the target node is found, guaranteeing that the generated overhead is always less than or equal to the one generated by the original flooding. To achieve this, F&C uses two flooding events with different propagation speeds. During the initial flooding, a source node seeking a route to a node having a particular resource or feature floods the network with RQ packets. Upon receiving a RQ packet, a target node initiates a fast chase flooding to eat up the initial slow flooding packets to avoid unnecessary resource consumption in the rest of the network. For this operation to occur, it is necessary for the initial flooding to propagate more slowly than the chase flooding. To slow down the propagation of search packets during the initial flooding, nodes receiving an RQ packet do not retransmit it immediately, but keep it in their buffer for a short predetermined period (
) before forwarding it. What sets F&C apart from any other repeal-based protocol is that nodes only launch a chase flooding if the reported hop-count to the source node is smaller than the node’s estimated repeal-flooding boundary. This condition guarantees that the aggregate overheard, considering the initial and chase flooding, never surpasses traditional flooding overhead. In case the reported hop-count to the source node is within the repeal-flooding boundary, the target node launches the chase flooding of RP packets. In this case, nodes attempt to retransmit RP packets as soon as they receive them. In case a node receives an RP packet before it has forwarded the previously received RQ packet, further propagation of both RQ and RP packets stops. This operation contains the area flooded with control packets during the resource discovery phase to a portion of the network only, as opposed to traditional flooding in which typically the entire network is flooded with signaling packets. Algorithm 1 defines the operation of the F&C protocol.
| Algorithm 1 F&C (S, N, D) |
|
/*S: source node*/ |
| /*D: Resource node set*/ |
| /*N: node*/ |
- 1:
S initiates a slow flooding of RQ packets - 2:
receives an RQ - 3:
ifthen - 4:
reads delay flooding parameter - 5:
waits seconds - 6:
forwards the RQ packet - 7:
else ifthen - 8:
if is reached after ’s repeal-flooding boundary then - 9:
replies to S (unicast) using the reverse route - 10:
else if is located before ’s repeal-flooding boundary then - 11:
initiates a chase flooding of RP packets - 12:
end if - 13:
end if - 14:
receives an RP packet - 15:
if has previously received an RP then - 16:
does not forward the RP packet - 17:
end if - 18:
if has already received and forwarded the RQ packet then - 19:
forwards the RP packet - 20:
else if has the RQ packet in its buffer then - 21:
does not forward the RQ and RP packets - 22:
end if
|
Figure 2 graphically illustrates the behavior of the F&C protocol.
Figure 2a shows source node
S initiating flooding of RQ packets in search of a target node in
D; blue diamonds illustrate nodes propagating RQ packets. Every time a node receives an RQ packet, it keeps the packet in its buffer for a predefined time interval (
) before forwarding the packet again.
Figure 2b,c show further propagation of RQ packets over time. Upon receiving the first RQ packet (see
Figure 2c), a target node replies immediately with an RP packet (see
Figure 2d) (this example assumed that the source node is within the target node’s maximum repeal-flooding boundary). The RP originates a chase flooding that propagates faster since nodes receiving an RP packet attempt to retransmit it as soon as possible.
Figure 2d–f illustrate further propagation of RP packets, represented by red stars. Because the chase flooding moves faster, its propagation reaches and contains further propagation of the initial flooding process before it floods the entire network.
Figure 2f shows how the chase flooding encompasses all the nodes covered so far by the original flooding. This operation allows F&C to reduce the area covered with route signaling packets, reducing the signaling overhead of the search process, compared with traditional flooding and other repeal-based protocols.
To gain some initial understanding of the problems found while attempting to repeal the initial flooding, we conducted a basic simulation of a standard repeal-flooding protocol where target nodes always attempt to contain the initial flooding, regardless of the distance. A detailed experimental study of repeal-flooding protocols versus F&C is presented later in
Section 5. We implemented the repeal-flooding protocol in the ns-3 network simulator [
30] and conducted a series of experiments to observe its behavior and present some areas of opportunity to improve its performance. Simulations used the standard IEEE 802.11g and randomly placed 300 nodes in a 3500 × 3500 m
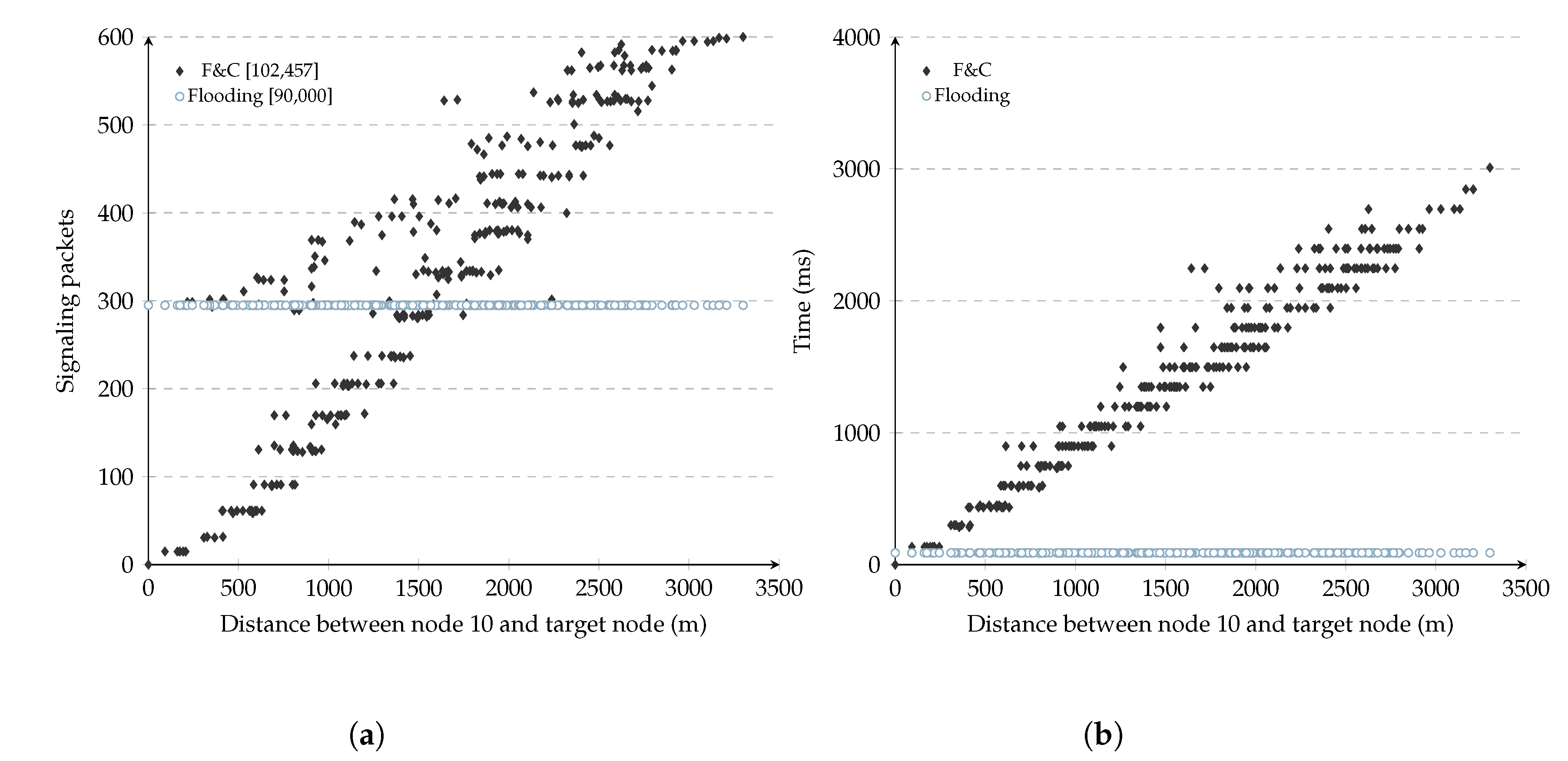
network. The transmission range is 250 m. The simulations consisted of allowing one node to find a route to each of the remaining 299 nodes. Similar to traditional flooding, there was no previous knowledge about the network’s state for any of the 299 simulations. For each simulation, the number of signaling packets needed to discover the target node was added, including RQ (i.e., original flooding) and RP packets (i.e., chase packets). There was no chase boundary in these experiments, so the target node always initiated a chase flooding after receiving an RQ packet to illustrate the need for such a boundary.
Figure 3a shows the number of signaling packets generated by this repeal-flooding protocol versus the distance separating source and target nodes for each of the 299 experiments (each point in the figure represents one such experiment). In these experiments, each node used a fixed 150 ms delay before attempting to forward RQ packets during the initial flooding. As a reference, the figure also shows the number of packets generated by traditional flooding, which remained constant at 299 packets per experiment. The number inside the square brackets in this figure shows the aggregate signaling overhead for the 299 experiments for either the repeal-flooding protocol and traditional flooding. On the other hand,
Figure 3b shows the delay it took the repeal-flooding protocol to reach each of the 299 nodes versus the distance between the source and target nodes. We refer to the three key observations resulting from these figures as
distance,
escape, and
delay issues, and explain them below.
3.1. Distance
Referring to
Figure 3a, it shows that the number of signaling packets generated by the repeal-flooding protocol increased linearly as the distance separating source and target nodes increased. This increment is the expected behavior since longer distances involve more hops and more signaling packets while attempting to find the target node (e.g., slow flooding) and contain its propagation with a chase flooding (e.g., fast flooding). This figure shows how particularly effective at containing the number of nodes involved in the route search process a repeal-flooding protocol is whenever source and target nodes are somewhere near each other. Unfortunately, the same figure shows that in some experiments, the repeal-flooding protocol can generate even more signaling packets compared with traditional flooding when longer distances are present. This problem is referred to as the distance problem and is addressed by the F&C protocol in
Section 4. Finally, please note that the distance between the source node and the furthest node in
Figure 3a depends on the source node’s position (node 10). In this figure, node ten was located in mid-position between the center and boundary of the network.
3.2. Escape
The escape issue is related to the points found above the 300 packet level in the 0–1200 m range in
Figure 3a. At first, these points seemed odd since they were supposed to follow the trend of other points at that distance range. Looking deeper at the experiments leading to these points, we found that a collision of packets belonging to the chase flooding had caused an incorrect reception of an RP packet by one node, which caused it to transmit a queued RQ packet. This escaped RQ packet eventually flooded the entire network with packets belonging to the original flooding. This problem is not exclusive to repeal-flooding protocols; in fact, it appears in most route discovery protocols using the IEEE 802.11 MAC standard, even affecting traditional flooding as well since collisions of RQ packets may prevent the target node from being reached.
A simple solution to the collision problem is to change the added delay during the initial flooding to be a random variable with mean . Also, the chase flooding phase might add a random delay, which might be chosen to be as small as possible, in order to avoid delaying the chase of the original flooding. This random delay will reduce the probability that two nodes transmit RQ or RP packets simultaneously, thus avoiding a collision.
3.3. Delay
Figure 3b shows the delay it took the repeal-flooding protocol to reach each of the 299 nodes versus the distance between the source and target nodes. As the figure shows, the resource discovery delay increases monotonically as the distance between the source and target nodes increases. In most repeal-flooding protocols, each node delays retransmissions of RQ packets during the initial flooding by
seconds, but how long should that delay take? If the delay is too short, the chase flooding might not stop propagating the initial flooding before it covers the entire network. If the delay is too long, then the overall time it takes for the source node to reach the target node can get to the point that it becomes unbearable for the application. The value of
should last longer than the accumulated delay of the resource discovery by the time it reaches the target node, which depends on the number of hops in the route and the MAC layer technology used. Simulations used to evaluate F&C use the IEEE 802.11g standard, and in [
31], they found forwarding delays in the range of 2–10 ms for one hop only (including channel contention and packet transmission). Simulations in
Figure 3b used a value of
set to 150 m, so the chase flooding was able to contain the propagation of the initial flooding, even in routes having 10–15 intermediate hops. The value of
can also be easily adjusted depending on whether or not the chase flooding contained the propagation of the first flooding before it propagated in the entire network. A detailed analysis of
is presented in
Section 5.1.