A Secure and Portable Multi-Sensor Module for Distributed Air Pollution Monitoring
Abstract
1. Introduction and Motivation
1.1. Related Work
2. System Architecture and Protocol Design
2.1. System and Components
2.2. Protocol Design Goals
- Developing a protocol stack that is computationally affordable for mid-range embedded devices, e.g., 32-bit Cortex M3 at 80 Mhz in our implementation.
- Assuring authenticity and non-repudiation for values that are broadcasted by the sensor modules.
- Assuring confidentiality of the traffic from the sensor modules to protect users from eavesdroppers.
- Assuring privacy for users such that the reporting sensor module remains anonymous for the rest of the network.
- Immutability, by which data cannot be changed later (this is to be assured by a blockchain-like structure).
- Proof-of-concept implementation on ARM-based microcontrollers and data servers.
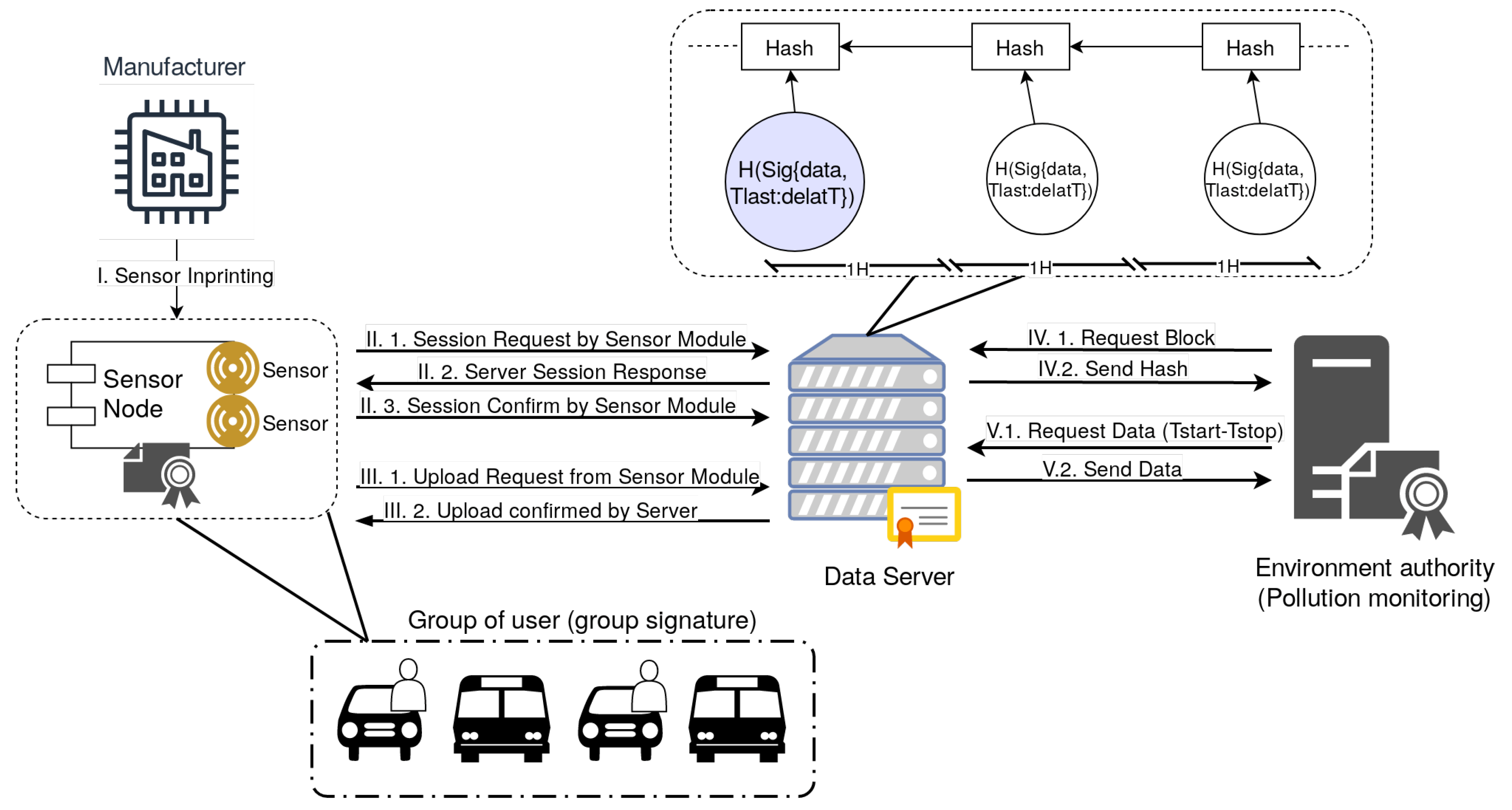
- Manufacturers are responsible for releasing the multi-sensor modules (also referred as sensor nodes in our work) and imprinting them with the corresponding keys.
- Users that are the physical entities to which the sensors belong. A user may posses one or multiple sensor modules, our assumption is that these are installed in mobile devices, e.g., cars or buses, but we do not exclude the possibility that they may be carried by persons as the modules are quite lightweight.
- Sensor modules are the devices used for monitoring air quality parameters, e.g., VOC, , etc., their architecure was already presented in the previous section.
- Data servers are used for storing data from the sensors and mediates data visualization. We assume that these data servers are not necessarily trustworthy, a reason for which we store data in a blockchain-like structure and add the next entity for assuring immutability of the information.
- The environment authority has the role of storing the blockchain-like structure and to verify the correctness of the data from the data servers at any later point.
2.3. Proposed Protocol
3. Experimental Results
3.1. Implementation Details
3.1.1. AQSensorNode
3.1.2. AQConnector
3.1.3. AQMonitor, AQServer, and the Database
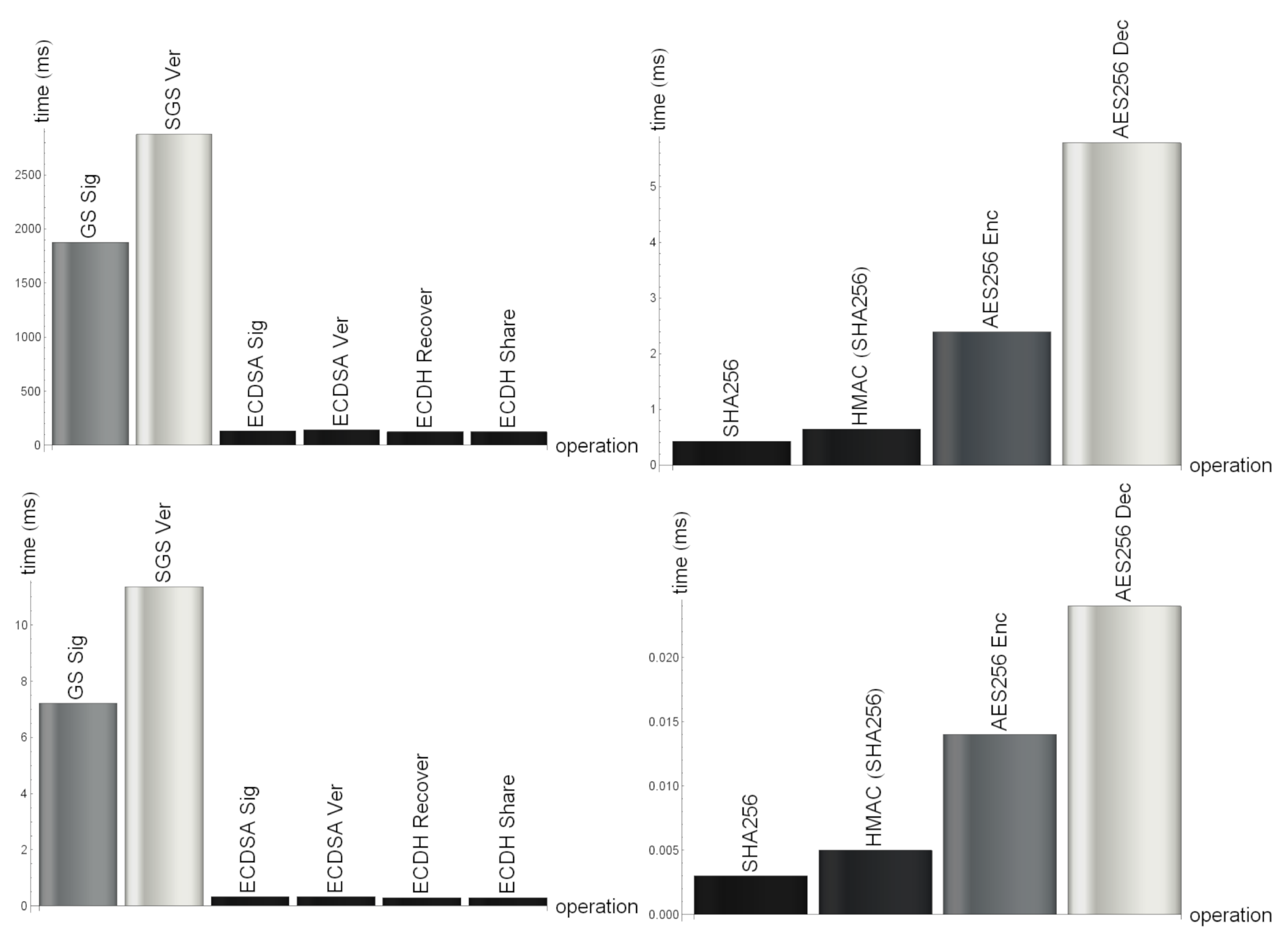
3.2. Computational Results
3.3. Power Consumption
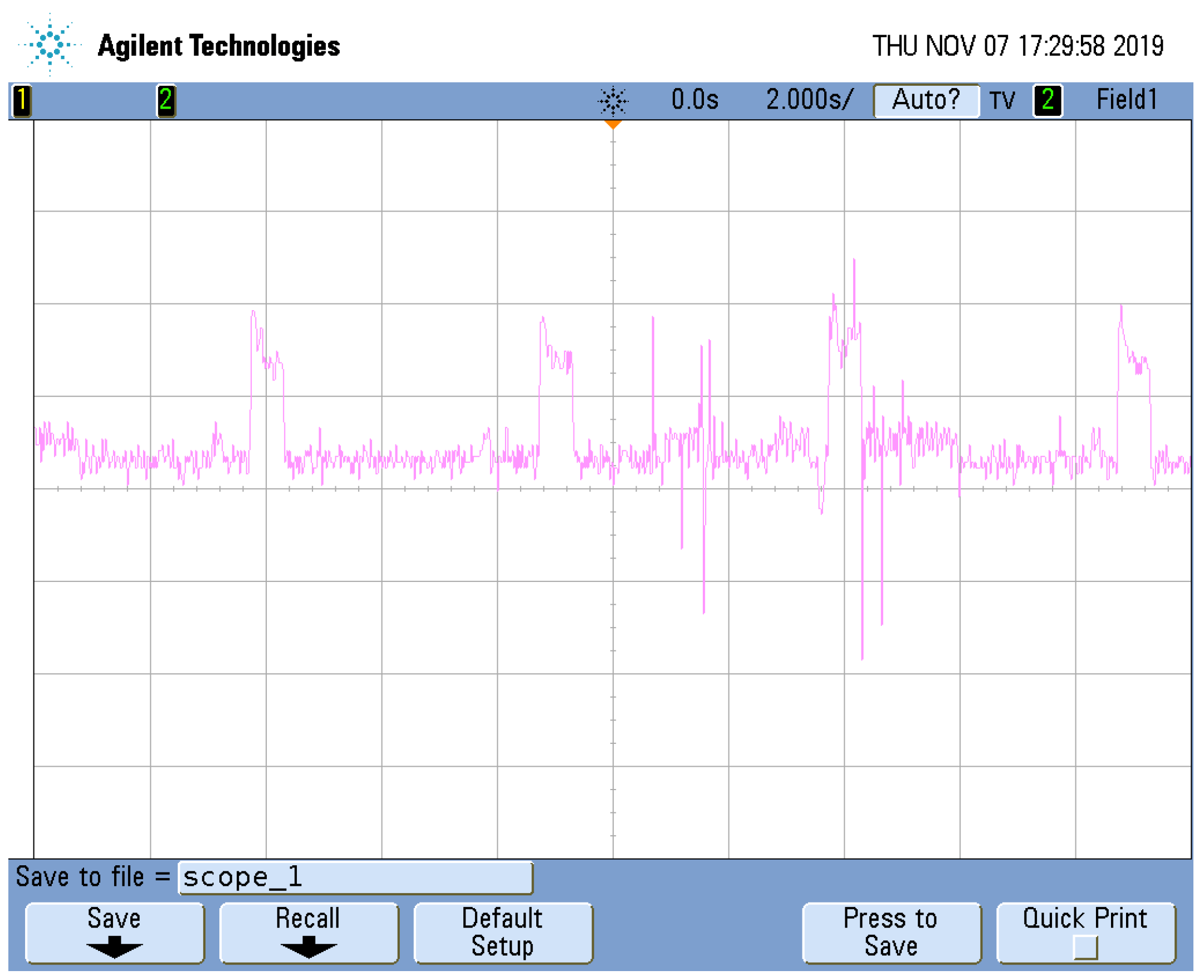
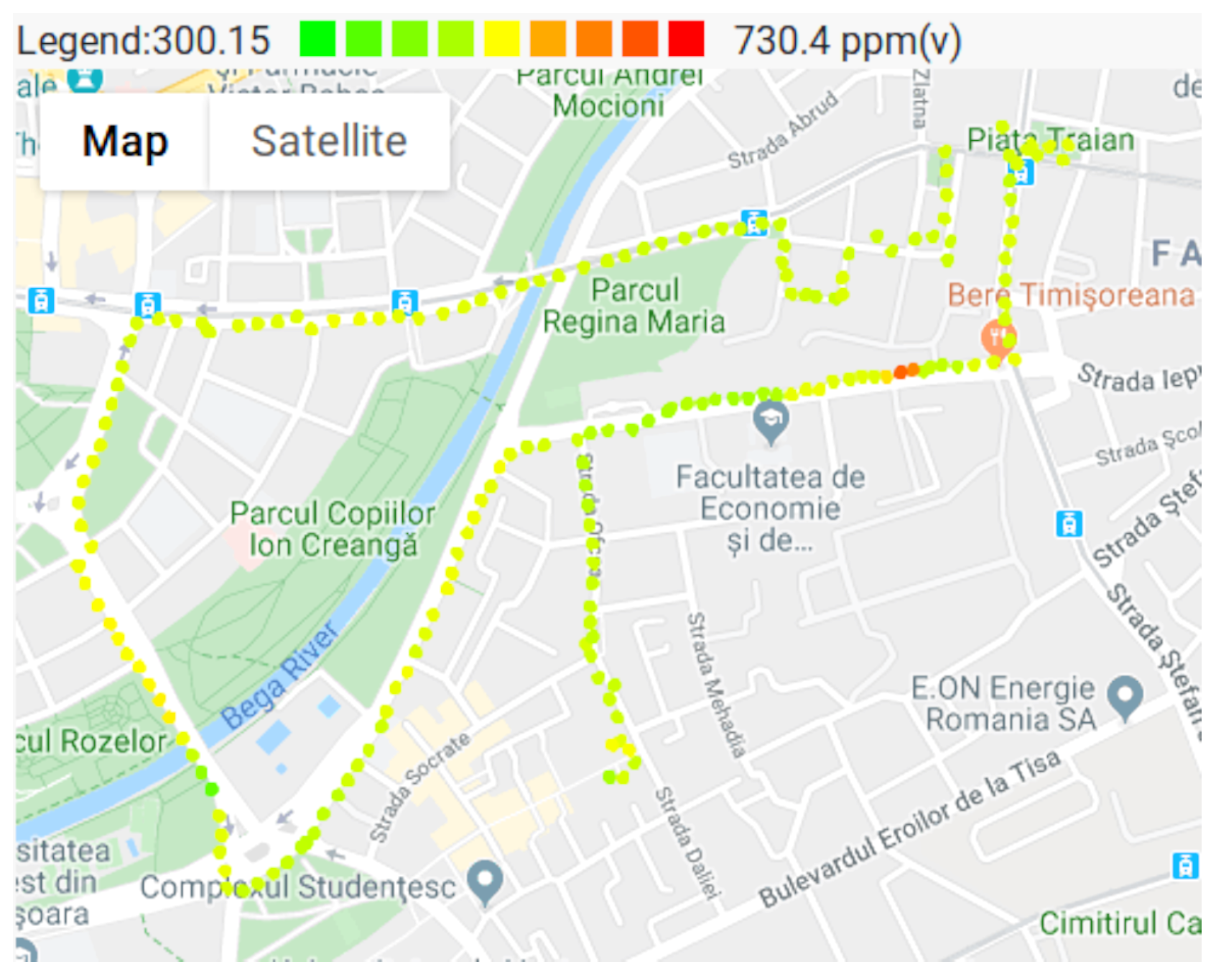
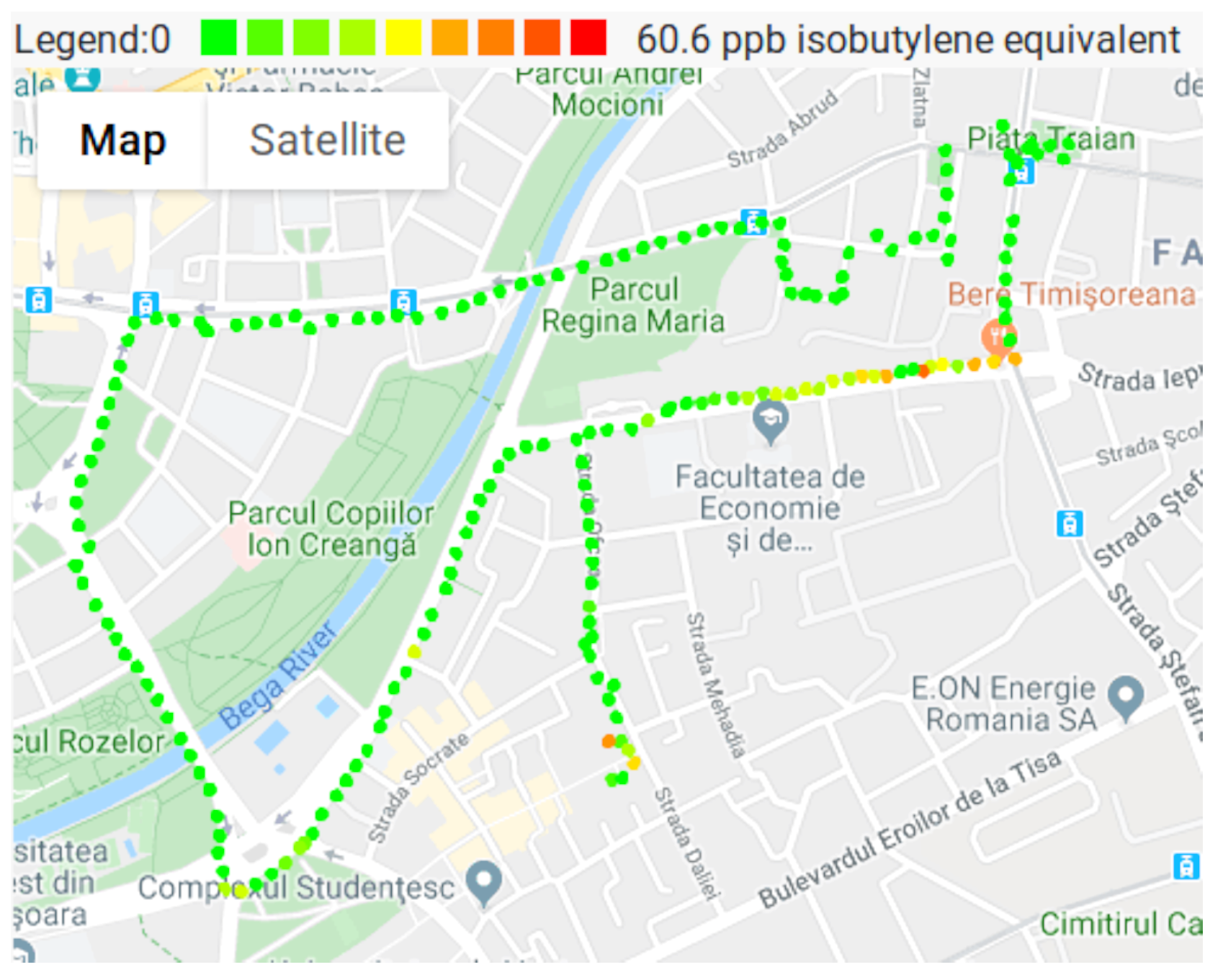
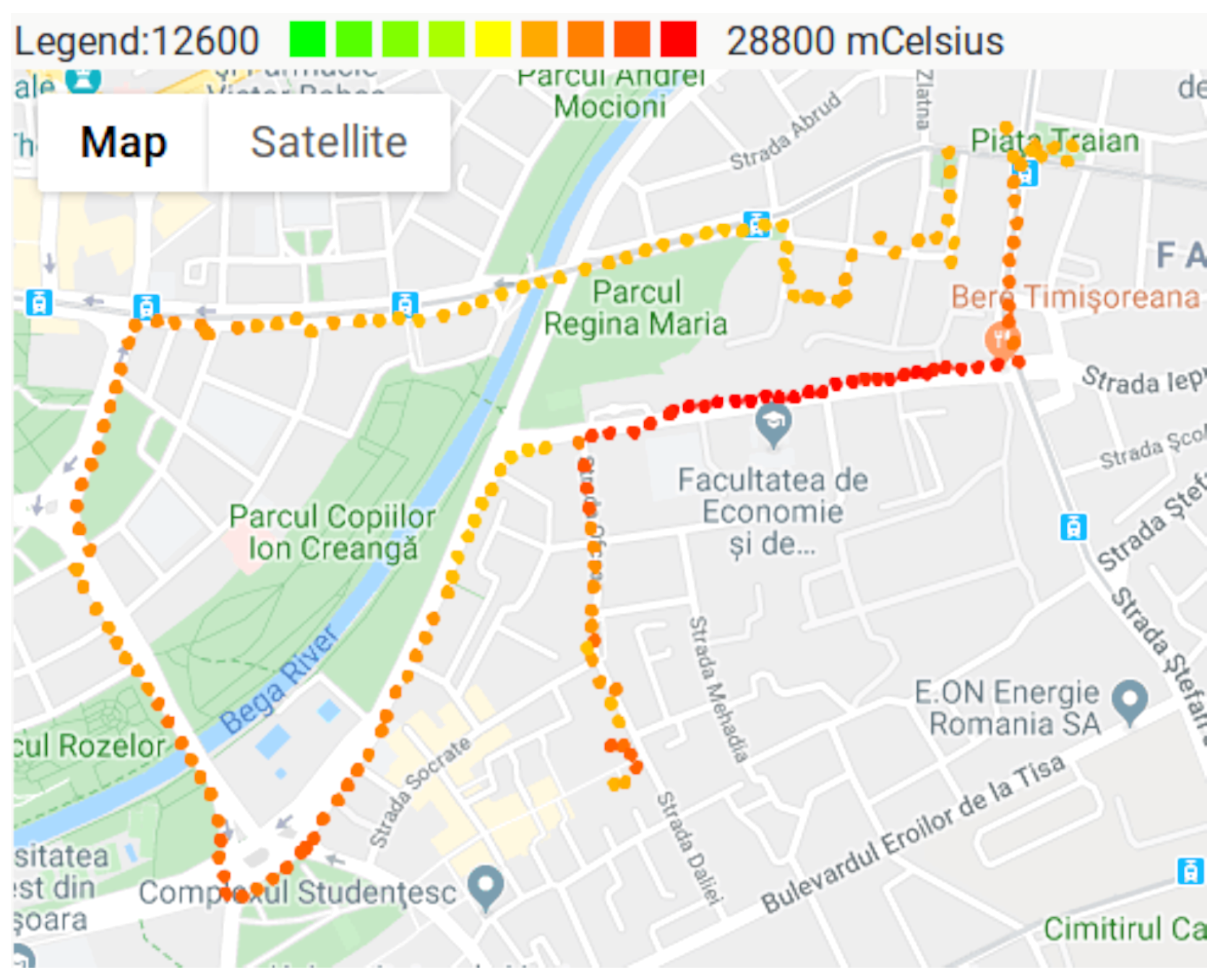
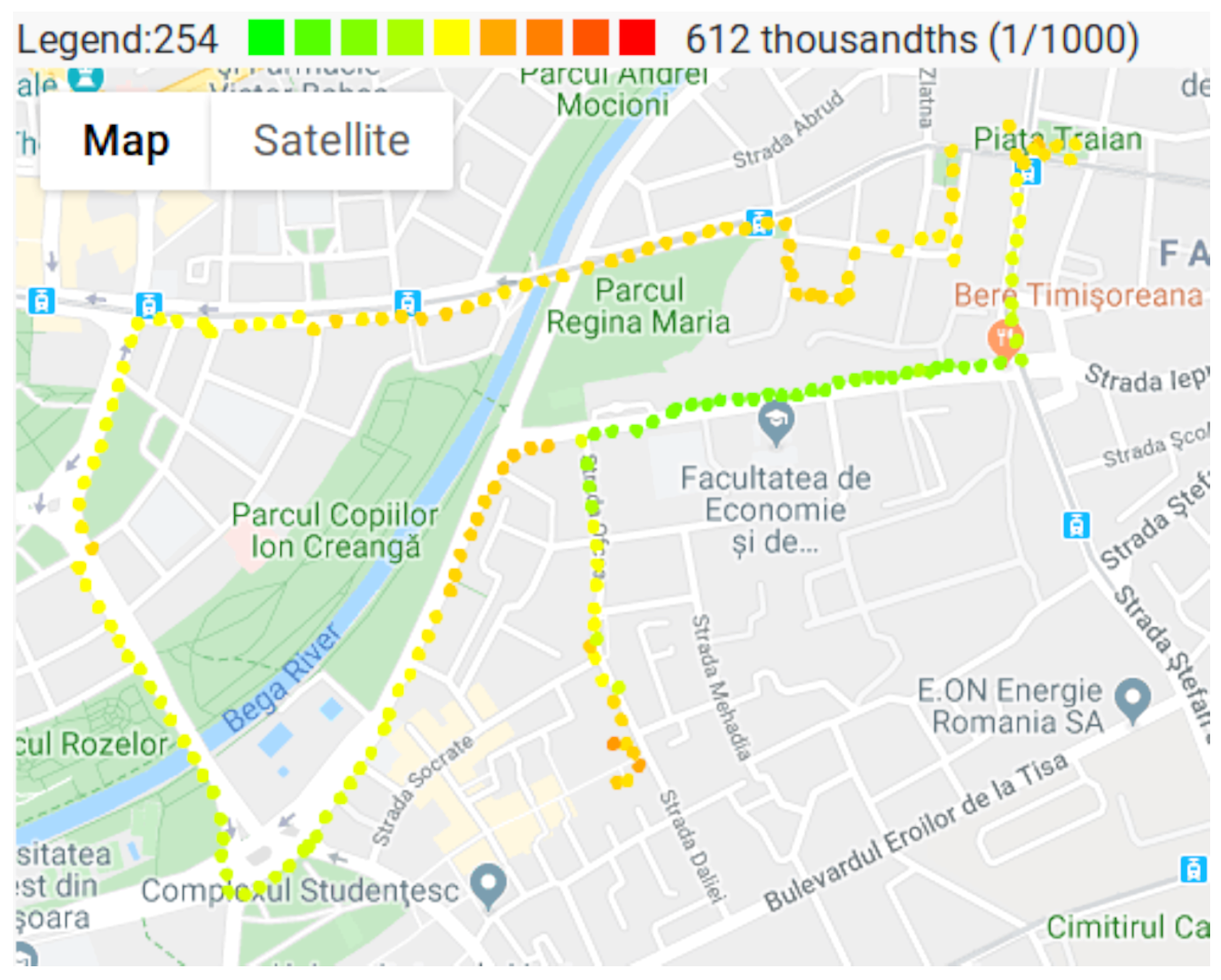
3.4. Air Pollution Monitoring
4. Conclusions
Author Contributions
Funding
Acknowledgments
Conflicts of Interest
References
- Salvi, C.; Brickman, S. Air Pollution Costs European Economies US$ 1.6 Trillion a Year in Diseases and Deaths. Available online: http://www.euro.who.int/en/media-centre/sections/press-releases/2015/04/air-pollution-costs-european-economies-us$-1.6-trillion-a-year-in-diseases-and-deaths,-new-who-study-says (accessed on 14 December 2019).
- Hien, V.T.D.; Lin, C.; Thanh, V.C.; Oanh, N.T.K.; Thanh, B.X.; Weng, C.E.; Yuan, C.S.; Rene, E.R. An overview of the development of vertical sampling technologies for ambient volatile organic compounds (VOCs). J. Environ. Manag. 2019, 247, 401–412. [Google Scholar] [CrossRef]
- Re, G.L.; Peri, D.; Vassallo, S.D. Urban air quality monitoring using vehicular sensor networks. In Advances onto the Internet of Things; Springer: Berlin/Heidelberg, Germany, 2014; pp. 311–323. [Google Scholar]
- Kumar, P.; Morawska, L.; Martani, C.; Biskos, G.; Neophytou, M.; Sabatino, S.D.; Bell, M.; Norford, L.; Britter, R. The rise of low-cost sensing for managing air pollution in cities. Environ. Int. 2015, 75, 199–205. [Google Scholar] [CrossRef]
- Postolache, O.; Pereira, J.; Girao, P. Smart Sensors Network for Air Quality Monitoring Applications. IEEE Trans. Instrum. Meas. 2009, 58, 3253–3262. [Google Scholar] [CrossRef]
- Lungu, M.; Stefu, N. Study on particulate matter dispersion by correlating direct measurements with numerical simulations: Case study—Timisoara urban area. Int. J. Environ. Sci. Technol. 2018, 15, 1441–1452. [Google Scholar] [CrossRef]
- Xiang, Y. Mobile Sensor Network Design and Optimization for Air Quality Monitoring. Ph.D. Thesis, University of Michigan, Ann Arbor, MI, USA, 2014. [Google Scholar]
- Xiang, Y.; Piedrahita, R.; Dick, R.P.; Hannigan, M.; Lv, Q.; Shang, L. A Hybrid Sensor System for Indoor Air Quality Monitoring. In Proceedings of the 2013 IEEE International Conference on Distributed Computing in Sensor Systems, Cambridge, MA, USA, 21–23 May 2013; pp. 96–104. [Google Scholar] [CrossRef]
- Huang, Q.; Mao, C.; Chen, Y. A Compact and Versatile Wireless Sensor Prototype for Affordable Intelligent Sensing and Monitoring in Smart Buildings. In Proceedings of the ASCE International Workshop on Computing in Civil Engineering 2017, Seattle, WA, USA, 25–27 June 2017; pp. 155–161. [Google Scholar] [CrossRef]
- Lee, U.; Magistretti, E.; Gerla, M.; Bellavista, P.; Corradi, A. Dissemination and Harvesting of Urban Data Using Vehicular Sensing Platforms. IEEE Trans. Veh. Technol. 2009, 58, 882–901. [Google Scholar] [CrossRef]
- Hu, S.C.; Wang, Y.C.; Huang, C.Y.; Tseng, Y.C. Measuring air quality in city areas by vehicular wireless sensor networks. J. Syst. Softw. 2011, 84, 2005–2012. [Google Scholar] [CrossRef]
- Kim, R.; Lim, H.; Krishnamachari, B. Prefetching-Based Data Dissemination in Vehicular Cloud Systems. IEEE Trans. Veh. Technol. 2016, 65, 292–306. [Google Scholar] [CrossRef]
- Boubrima, A.; Bechkit, W.; Rivano, H. Optimal WSN Deployment Models for Air Pollution Monitoring. IEEE Trans. Wirel. Commun. 2017, 16, 2723–2735. [Google Scholar] [CrossRef]
- Wang, Y.C.; Chen, G.W. Efficient Data Gathering and Estimation for Metropolitan Air Quality Monitoring by Using Vehicular Sensor Networks. IEEE Trans. Veh. Technol. 2017, 66, 7234–7248. [Google Scholar] [CrossRef]
- Lai, Y.; Yang, F.; Su, J.; Zhou, Q.; Wang, T.; Zhang, L.; Xu, Y. Fog-Based Two-Phase Event Monitoring and Data Gathering in Vehicular Sensor Networks. Sensors 2018, 18, 82. [Google Scholar] [CrossRef]
- Yim, Y.; Cho, H.; Kim, S.H.; Lee, E.; Gerla, M. Vehicle location service scheme based on road map in Vehicular Sensor Networks. Comput. Netw. 2017, 127, 138–150. [Google Scholar] [CrossRef]
- Nie, W.; Lee, V.C.S.; Niyato, D.; Duan, Y.; Liu, K.; Nutanong, S. A Quality-Oriented Data Collection Scheme in Vehicular Sensor Networks. IEEE Trans. Veh. Technol. 2018, 67, 5570–5584. [Google Scholar] [CrossRef]
- Devarakonda, S.; Sevusu, P.; Liu, H.; Liu, R.; Iftode, L.; Nath, B. Real-time air quality monitoring through mobile sensing in metropolitan areas. In Proceedings of the 2nd ACM SIGKDD International Workshop on Urban Computing; ACM: New York, NY, USA, 2013; p. 15. [Google Scholar]
- Liu, D.; Ning, P.; Li, R. Establishing pairwise keys in distributed sensor networks. ACM Trans. Inf. Syst. Secur. (TISSEC) 2005, 8, 41–77. [Google Scholar] [CrossRef]
- Liu, A.; Ning, P. TinyECC: A configurable library for elliptic curve cryptography in wireless sensor networks. In Proceedings of the 7th International Conference on Information Processing in SENSOR Networks, St. Louis, MO, USA, 22–24 April 2008; IEEE Computer Society: Washington, DC, USA, 2008; pp. 245–256. [Google Scholar]
- Koblitz, N.; Menezes, A. Pairing-based cryptography at high security levels. In Proceedings of the IMA International Conference on Cryptography and Coding, Cirencester, UK, 19–21 December 2005; Springer: Berlin/Heidelberg, Germany, 2005; pp. 13–36. [Google Scholar]
- Zhang, L.; Wu, Q.; Solanas, A.; Domingo-Ferrer, J. A scalable robust authentication protocol for secure vehicular communications. IEEE Trans. Veh. Technol. 2009, 59, 1606–1617. [Google Scholar] [CrossRef]
- Wasef, A.; Shen, X. Efficient group signature scheme supporting batch verification for securing vehicular networks. In Proceedings of the 2010 IEEE International Conference on Communications, Cape Town, South Africa, 23–27 May 2010; IEEE: Piscataway, NJ, USA, 2010; pp. 1–5. [Google Scholar]
- Zhu, X.; Jiang, S.; Wang, L.; Li, H. Efficient privacy-preserving authentication for vehicular ad hoc networks. IEEE Trans. Veh. Technol. 2013, 63, 907–919. [Google Scholar] [CrossRef]
- Wu, L.; Fan, J.; Xie, Y.; Wang, J.; Liu, Q. Efficient location-based conditional privacy-preserving authentication scheme for vehicle ad hoc networks. Int. J. Distrib. Sens. Netw. 2017, 13. [Google Scholar] [CrossRef]
- Tangade, S.; Manvi, S.S.; Lorenz, P. Decentralized and scalable privacy-preserving authentication scheme in VANETs. IEEE Trans. Veh. Technol. 2018, 67, 8647–8655. [Google Scholar] [CrossRef]
- Boneh, D.; Boyen, X.; Shacham, H. Short group signatures. In Proceedings of the Annual International Cryptology Conference, Santa Barbara, CA, USA, 15–19 August 2004; Springer: Berlin/Heidelberg, Germany, 2004; pp. 41–55. [Google Scholar]
- Lo, N.W.; Tsai, J.L. An Efficient Conditional Privacy-Preserving Authentication Scheme for Vehicular Sensor Networks Without Pairings. IEEE Trans. Intell. Transp. Syst. 2016, 17, 1319–1328. [Google Scholar] [CrossRef]
- Asaar, M.R.; Salmasizadeh, M.; Susilo, W.; Majidi, A. A Secure and Efficient Authentication Technique for Vehicular Ad-hoc Networks. IEEE Trans. Veh. Technol. 2018, 67, 5409–5423. [Google Scholar] [CrossRef]
- Li, C.; Zhang, X.; Wang, H.; Li, D. An Enhanced Secure Identity-Based Certificateless Public Key Authentication Scheme for Vehicular Sensor Networks. Sensors 2018, 18, 194. [Google Scholar] [CrossRef]
- Cui, J.; Xu, W.; Zhong, H.; Zhang, J.; Xu, Y.; Liu, L. Privacy-Preserving Authentication Using a Double Pseudonym for Internet of Vehicles. Sensors 2018, 18, 1453. [Google Scholar] [CrossRef] [PubMed]
- Javed, M.A.; Zeadally, S.; Hamid, Z. Trust-based security adaptation mechanism for Vehicular Sensor Networks. Comput. Netw. 2018, 137, 27–36. [Google Scholar] [CrossRef]
- Manvi, S.S.; Tangade, S. A survey on authentication schemes in VANETs for secured communication. Veh. Commun. 2017, 9, 19–30. [Google Scholar] [CrossRef]
- Gayathri, N.B.; Thumbur, G.; Reddy, P.V.; Muhammad, Z.U.R. Efficient Pairing-Free Certificateless Authentication Scheme With Batch Verification for Vehicular Ad-Hoc Networks. IEEE Access 2018, 6, 31808–31819. [Google Scholar] [CrossRef]
- Dai, F.; Luo, M.; ZHANG, Y. A Fault-Tolerant Batch Verification Scheme for Cloud Assisted VANETs. DEStech Trans. Eng. Technol. Res. 2017. [Google Scholar] [CrossRef][Green Version]
- Islam, S.H.; Obaidat, M.S.; Vijayakumar, P.; Abdulhay, E.; Li, F.; Reddy, M.K.C. A robust and efficient password-based conditional privacy preserving authentication and group-key agreement protocol for VANETs. Future Gener. Comput. Syst. 2018, 84, 216–227. [Google Scholar] [CrossRef]
- Liu, Z.; Xiong, L.; Peng, T.; Peng, D.Y.; Liang, H.B. A Realistic Distributed Conditional Privacy- Preserving Authentication Scheme for Vehicular Ad Hoc Networks. IEEE Access 2018, 6, 26307–26317. [Google Scholar] [CrossRef]
- Ming, Y.; Shen, X. PCPA: A Practical Certificateless Conditional Privacy Preserving Authentication Scheme for Vehicular Ad Hoc Networks. Sensors 2018, 18, 1573. [Google Scholar] [CrossRef]
- Wan, C.; Zhang, J. Efficient identity-based data transmission for VANET. J. Ambient. Intell. Humaniz. Comput. 2017, 9, 1861–1871. [Google Scholar] [CrossRef]
- Ying, B.; Nayak, A. Anonymous and Lightweight Authentication for Secure Vehicular Networks. IEEE Trans. Veh. Technol. 2017, 66, 10626–10636. [Google Scholar] [CrossRef]
- CO2 Earth. Available online: https://www.co2.earth/ (accessed on 24 July 2019).
- Törnqvist, M.; Ehrenberg, L. On cancer risk estimation of urban air pollution. Environ. Health Perspect. 1994, 102, 173–182. [Google Scholar] [CrossRef] [PubMed][Green Version]
- Tsai, W.T. Toxic Volatile Organic Compounds (VOCs) in the Atmospheric Environment: Regulatory Aspects and Monitoring in Japan and Korea. Environments 2016, 3, 23. [Google Scholar] [CrossRef]
- Kolumban-Antal, G.; Lasak, V.; Bogdan, R.; Groza, B. Air pollution monitoring with secure low-cost Vehicular Sensor Networks. In Proceedings of the 1st International Conference on Computational Methods and Applications in Engineering, Timisoara, Romania, 23–26 May 2018. [Google Scholar]
- Diffie, W.; Van Oorschot, P.C.; Wiener, M.J. Authentication and authenticated key exchanges. Des. Codes Cryptogr. 1992, 2, 107–125. [Google Scholar] [CrossRef]
- Unterluggauer, T.; Wenger, E. Efficient pairings and ECC for embedded systems. In Proceedings of the International Workshop on Cryptographic Hardware and Embedded Systems, Busan, Korea, 23–26 September 2014; Springer: Berlin/Heidelberg, Germany, 2014; pp. 298–315. [Google Scholar]
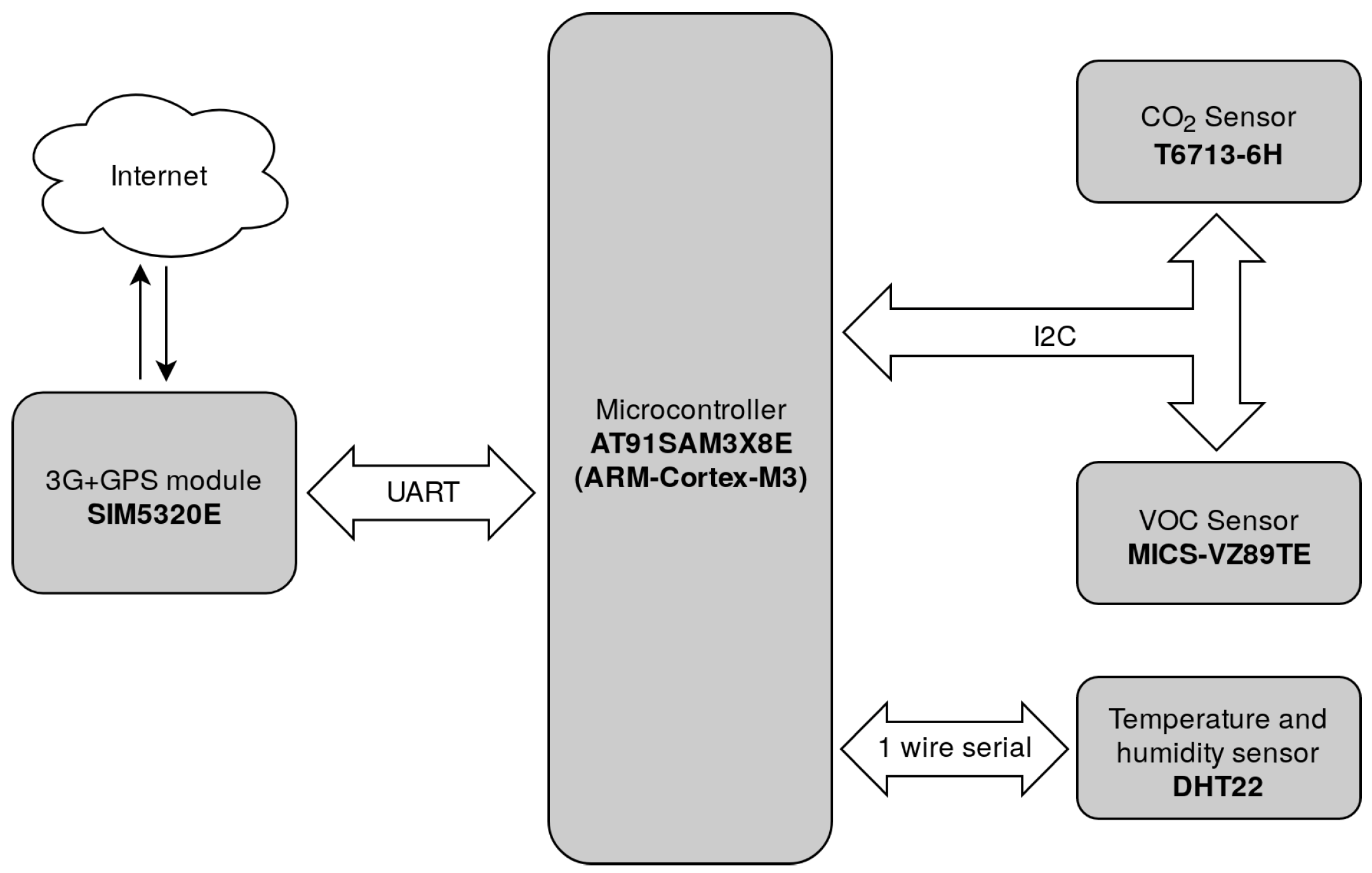

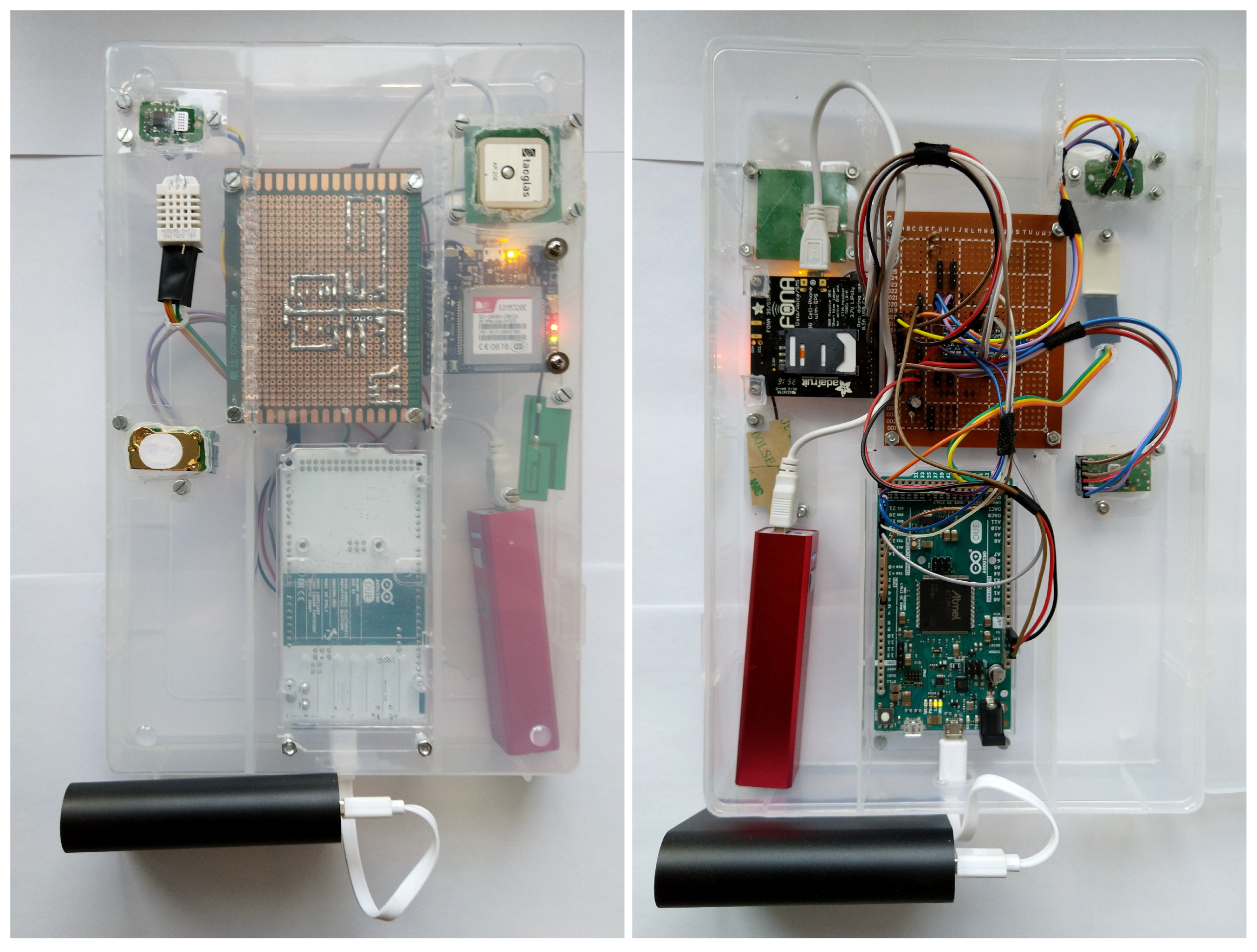

| Component | Role | Resources | Interfaces |
|---|---|---|---|
| Arduino Due | processing | AT91SAM3X8E microcontroller, 84 MHz, 96 Kb RAM | UART |
| Adafruit Fona 3G | network + GPS | SIM5320E chip | UART |
| Taoglas AP 25.E | GPS antenna | N/A | U.FL |
| ZL-PB350B2-PEX35B | GSM antenna | N/A | U.FL |
| External batteries | power source | N/A | N/A |
| Sensor | Role | Interfaces | Measurement Range | Precision | Price Range |
|---|---|---|---|---|---|
| T6713-6H | Sensor | I2C | 400–5000 ppm | of the reading | 50–100 USD |
| MICS-VZ- 89TE | VOC Sensor | I2C | 0–1000 ppb isobutylene equivalent | not specified | 10–50 USD |
| DHT22 | temperature and humidity sensor | I2C | −40–80 °C temperature 0–100 humidity | °C temperature humidity | 1–10 USD |
| Algorithm | Input Size [byte] | Key Size [bit] | Runtime on AT91SAM3X8E [ms] | Runtime on Xeon E5-2676 v3 [ms] |
|---|---|---|---|---|
| SGS Signature | 74 | 158 | 1877.39 | 7.22 |
| SGS Verification | 74 | 158 | 2873.67 | 11.36 |
| ECDSA Signature | 74 | 256 | 132.55 | 0.33 |
| ECDSA Verification | 74 | 256 | 141.08 | 0.33 |
| ECDH Recover | - | 256 | 126.24 | 0.30 |
| ECDH Share | - | 256 | 126.24 | 0.30 |
| SHA256 | 320 | - | 0.43 | 0.003 |
| HMAC (SHA256) | 320 | 256 | 0.65 | 0.005 |
| AES256 Encrypt | 320 | 256 | 2.39 | 0.014 |
| AES256 Decrypt | 320 | 256 | 5.79 | 0.024 |
| Operation | Phase | Client Side Processing Time (ms) | Server Side Processing Time (ms) |
|---|---|---|---|
| Session key establishment | message 1 | 1.32 | 0.34 |
| message 2 | 470.39 | 0.33 | |
| message 3 | 2263.69 | 12.43 | |
| Data upload | message 1 | 2.02 | 0.02 |
| message 2 | 0.95 | 0.07 | |
| Hash chain computation | not signed | 0.25 | 0.003 |
| signed | 2268.90 | 12.60 |
| Operation | Measured on | Processing Time (ms) | Transmission Delay (ms) | Total Time (ms) |
|---|---|---|---|---|
| Session key establishment | client side | 2735.88 | 5717.54 | 8453.42 |
| Session key establishment | server side | 2747.18 | 5581.43 | 8328.62 |
| Data upload with hash chain (not signed) | client side | 3.31 | 5595.10 | 5598.41 |
| Data upload with hash chain (signed) | client side | 2271.97 | 5461.45 | 7733.41 |
© 2020 by the authors. Licensee MDPI, Basel, Switzerland. This article is an open access article distributed under the terms and conditions of the Creative Commons Attribution (CC BY) license (http://creativecommons.org/licenses/by/4.0/).
Share and Cite
Kolumban-Antal, G.; Lasak, V.; Bogdan, R.; Groza, B. A Secure and Portable Multi-Sensor Module for Distributed Air Pollution Monitoring. Sensors 2020, 20, 403. https://doi.org/10.3390/s20020403
Kolumban-Antal G, Lasak V, Bogdan R, Groza B. A Secure and Portable Multi-Sensor Module for Distributed Air Pollution Monitoring. Sensors. 2020; 20(2):403. https://doi.org/10.3390/s20020403
Chicago/Turabian StyleKolumban-Antal, Gyorgy, Vladko Lasak, Razvan Bogdan, and Bogdan Groza. 2020. "A Secure and Portable Multi-Sensor Module for Distributed Air Pollution Monitoring" Sensors 20, no. 2: 403. https://doi.org/10.3390/s20020403
APA StyleKolumban-Antal, G., Lasak, V., Bogdan, R., & Groza, B. (2020). A Secure and Portable Multi-Sensor Module for Distributed Air Pollution Monitoring. Sensors, 20(2), 403. https://doi.org/10.3390/s20020403





