Medium Access Control Protocols for the Internet of Things Based on Unmanned Aerial Vehicles: A Comparative Survey
Abstract
1. Introduction
- We present and discuss the communication architecture of UIoT, along with common application scenarios and their associated challenges. In addition, we preview the MAC protocols for IoT and UAV networks separately, because the heterogeneous architecture of UIoT consists of both IoT and UAV networks.
- By exploiting the important design considerations of MAC protocols for UIoT, we present a new taxonomy of existing MAC protocols tailored to UIoT based on MAC strategies used to access the channel for data transmission. Hence, the existing MAC protocols for UIoT are classified into three categories. Subsequently, they are reviewed and discussed with regard to the main ideas, operational principles, advantages, limitations, application domains, and future improvements.
- The major features, operational characteristics, and performance metrics of the reviewed MAC protocols are qualitatively compared.
- Finally, important open research issues and challenges that must be overcome for developing a better MAC protocol for UIoT are summarized and discussed. Recommended solutions for each of the open research issues are also provided.
2. UIoT Communication Architecture and Application Scenarios
2.1. Communication Architecture of UIoT
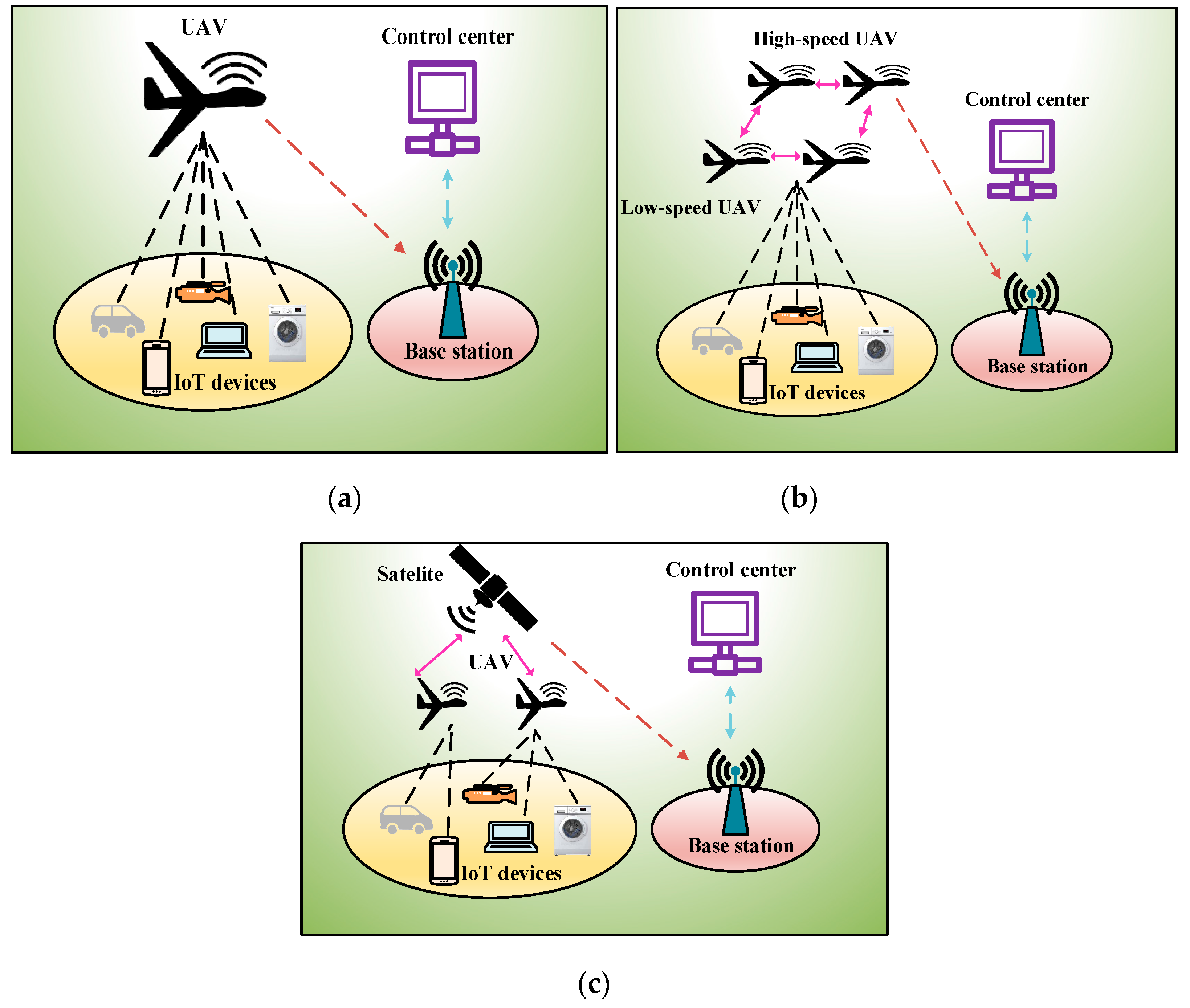
2.1.1. Single-UIoT Architecture
2.1.2. Multi-UIoT Architecture
2.1.3. SAGIN
2.1.4. UAV Equipped with IoT Devices
2.2. Application Scenarios
2.2.1. UAV-Based Wireless Networks for IoT Devices
2.2.2. UAVs as Relays for Data Collection from IoT Devices
2.2.3. UAVs in 5G Communication for IoT Devices
2.2.4. UAVs as Energy Harvester for IoT Devices
2.2.5. UAVs in Mobile Edge Computing (MEC) for IoT Devices
2.2.6. UAV-IoT in Crowd Surveillance Using IoT Devices
3. Preliminaries
3.1. MAC Protocols for IoT
3.2. MAC Protocols for UAV Networks
4. Design Considerations for MAC Protocols of UIoT
4.1. Throughput
4.2. Energy Efficiency
4.3. Low Latency
4.4. Scalability
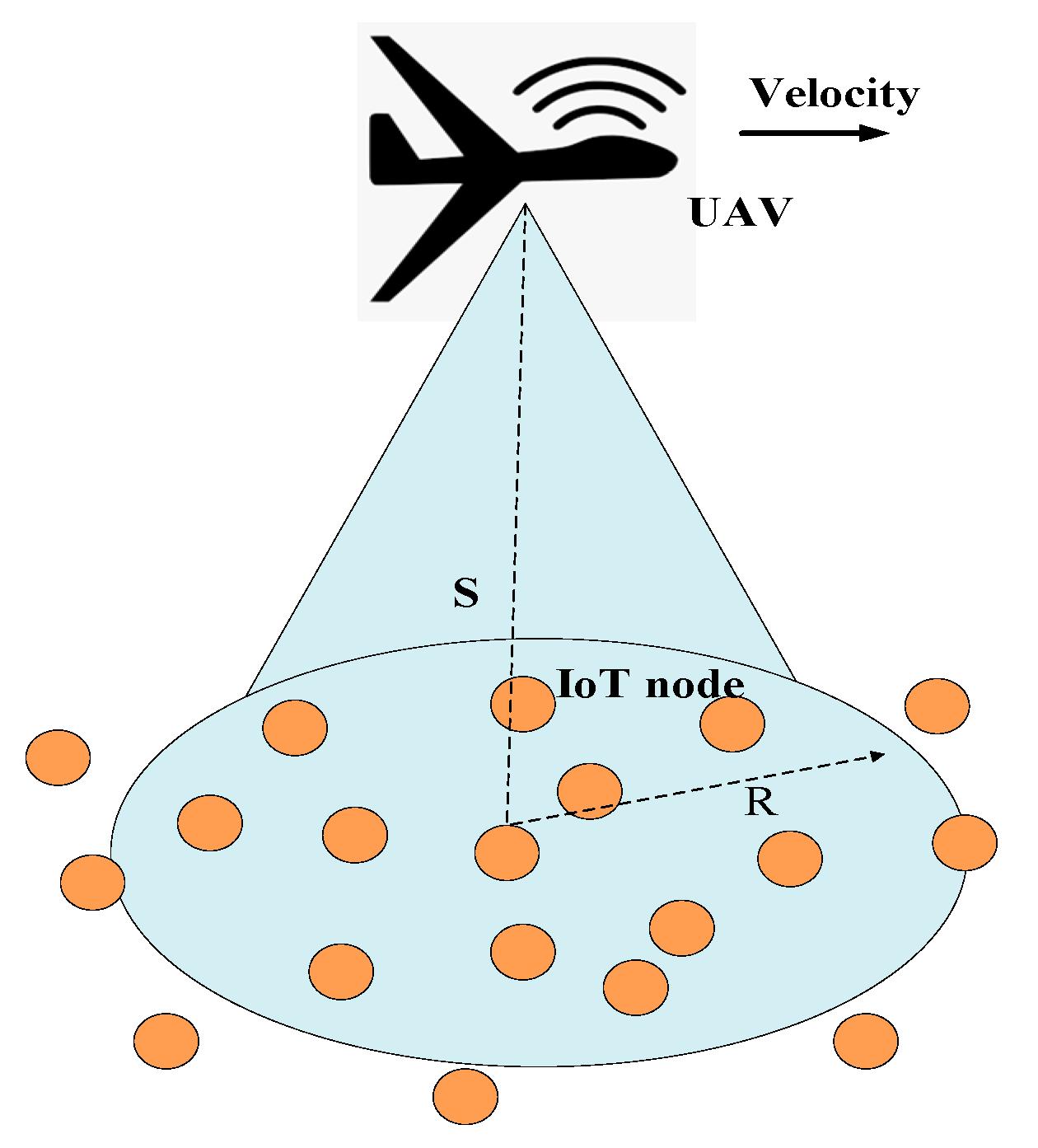
4.5. UAV Speed
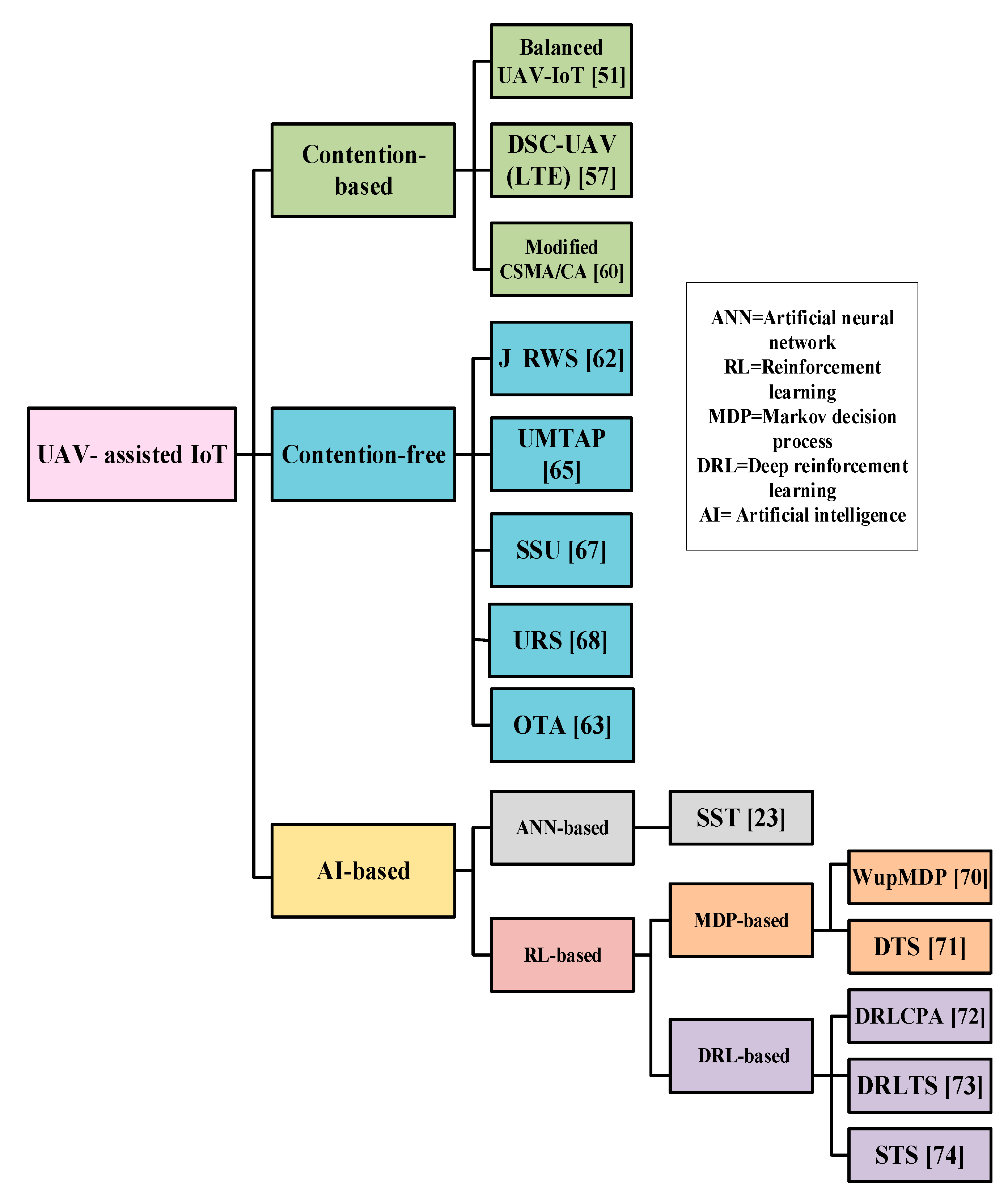
5. MAC Protocols for UIoT
5.1. Contention-Based Protocols for UIoT
5.1.1. Balanced UAV-IoT
- Advantages: The Balanced UAV-IoT system has a high throughput in the system-efficiency mode, but its energy consumption is significantly lower in the energy-efficiency mode. Moreover, a cross-layer architecture is applied that helps to optimize different system parameters.
- Limitations: The system performance is significantly affected by the empty slots, collided slots [59], and overhearing.
- Application domains: The sensor nodes follow a line model, making the system suitable for railway lines, power lines, country borders, and human-inaccessible or hostile areas.
- Future improvements: The system efficiency can be enhanced by applying suitable path planning and a suitable UAV flight time.
5.1.2. Dynamic Speed Control and Data Collection Framework of UAV (DSC-UAV)
- Advantages: DSC-UAV performs well with regard to the probability of successful access, access delay, and data-collection efficiency. Moreover, the optimal velocity of the UAV is measured for different densities of IoT devices.
- Limitations: DSC-UAV requires a four-step handshaking technique to establish a connection between the UAV and the IoT devices. However, owing to the dynamic and mobile nature of the UAV, a long connection process is undesirable. Many IoT devices can miss the opportunity for data transmission because of the long connection process.
- Application domains: This protocol may be suitable for a smart city where sensor nodes on roadsides (roads with sensors and smart vehicles) are higher than nearby smart buildings.
- Future improvements: The multi-UAV mechanism should be investigated for different densities of IoT devices. The multi-UAV systems can be compared with the DSC-UAV in terms of the system performance.
5.1.3. Modified CSMA/CA
- Advantages: The Modified CSMA/CA protocol outperforms the original CSMA/CA with regard to throughput for different densities of IoT devices owing to the use of transmission priorities.
- Limitations: The CW size must be calculated and updated frequently, leading to energy and time consumption for the system.
- Application domains: Wide, remote areas with randomly distributed IoT devices are suitable candidates for this protocol.
- Future improvements: Hidden and exposed nodes must be addressed to reduce collisions and energy wastage.
5.2. Contention-Free MAC Protocols for UIoT
5.2.1. Joint Resources and Workflow Scheduling (JRWS)
- Advantages: The proposed workflow model provides a multitasking mechanism during the UAV flight. This helps to reduce the UAV hovering time and energy consumption.
- Limitations: Large synchronization overhead is suspected for the communication between the UAV and the IoT devices due to the use of the TDMA structure for multi-workflow modeling.
- Application domains: This algorithm can be used in industrial IoT applications where a multiple-workflow system is necessary to reduce the time consumption. Furthermore, it may be suitable for emergency cases where multiple-workflow algorithms can reduce the time and energy consumption.
- Future improvements: The multichannel mechanism can be applied for improving the channel utilization.
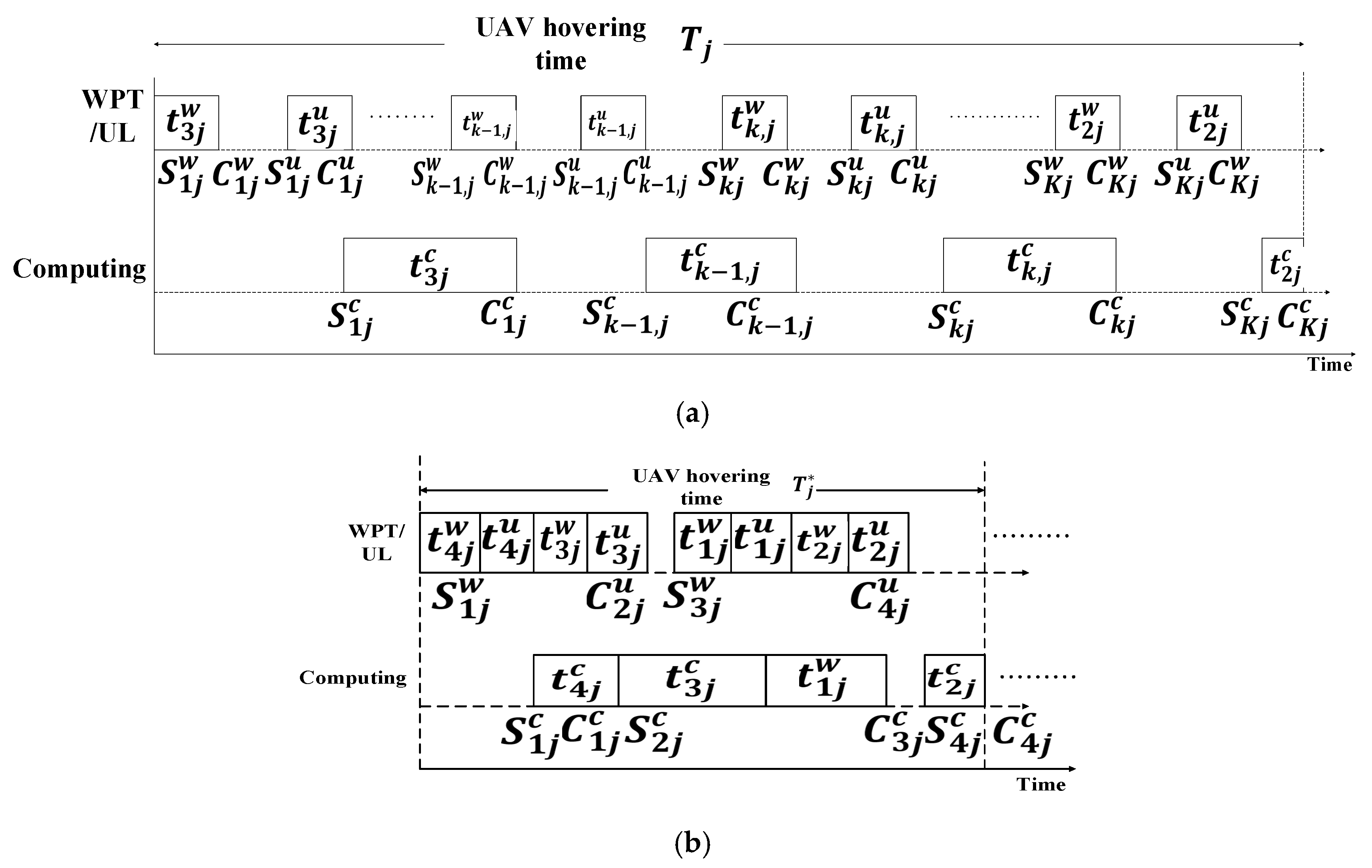
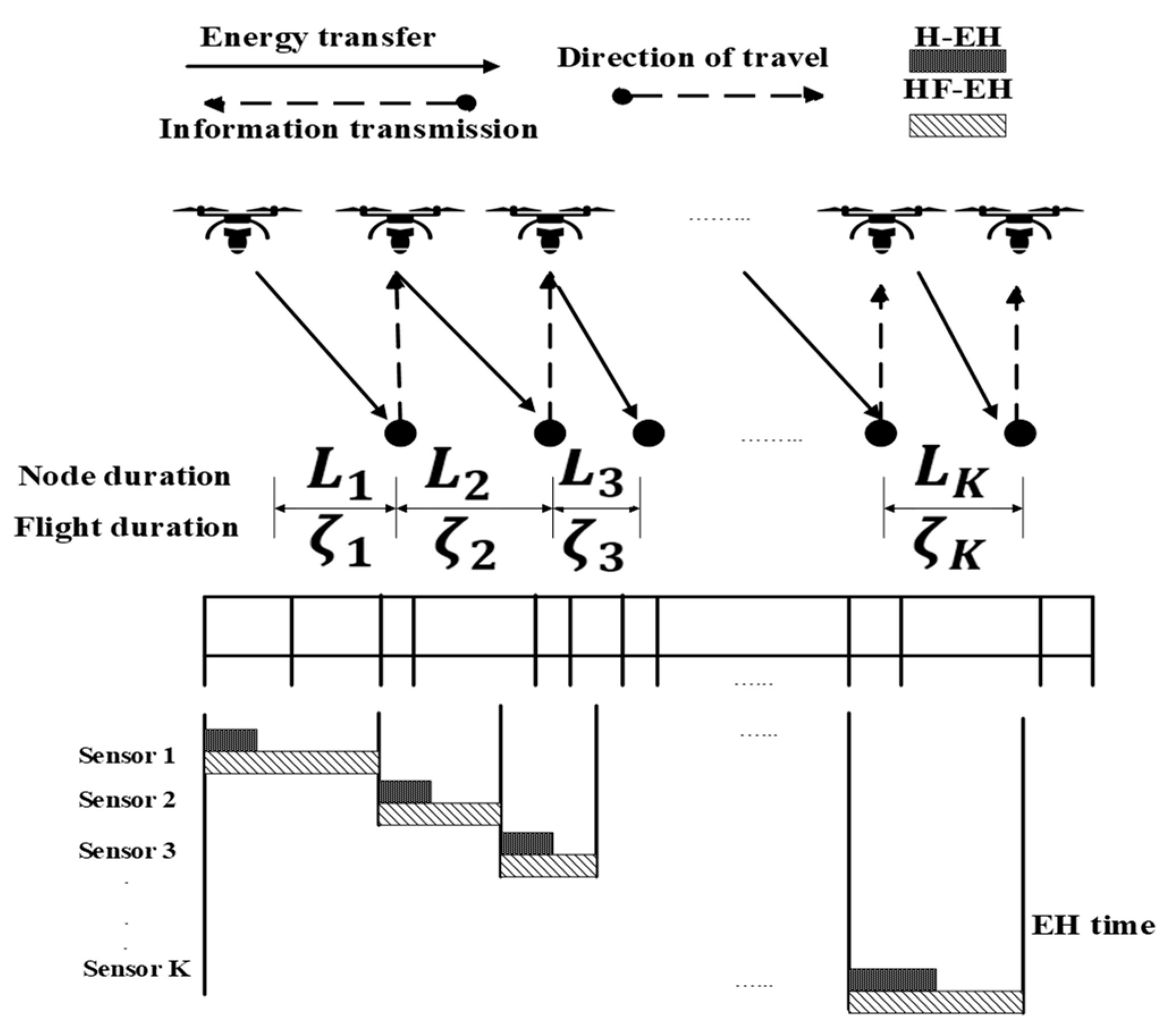
5.2.2. Optimal Time Allocation (OTA)
- Advantages: OTA can achieve the maximum throughput within an optimized allocated time. Additionally, the UAV wirelessly transfers energy to sensors while hovering and flying.
- Limitations: IoT networks tend to be dense [64]. However, the system was not simulated in a dense IoT network. The system performance highly depends on the density of IoT devices in the network.
- Application domains: This model is suitable for IoT systems that are located in remote and rural areas and deployed in a line. The UAV can facilitate the sensors by acting as a charging source.
- Future improvements: The UAV altitude, packet size, and number of nodes should be optimized for improving timeslot access.
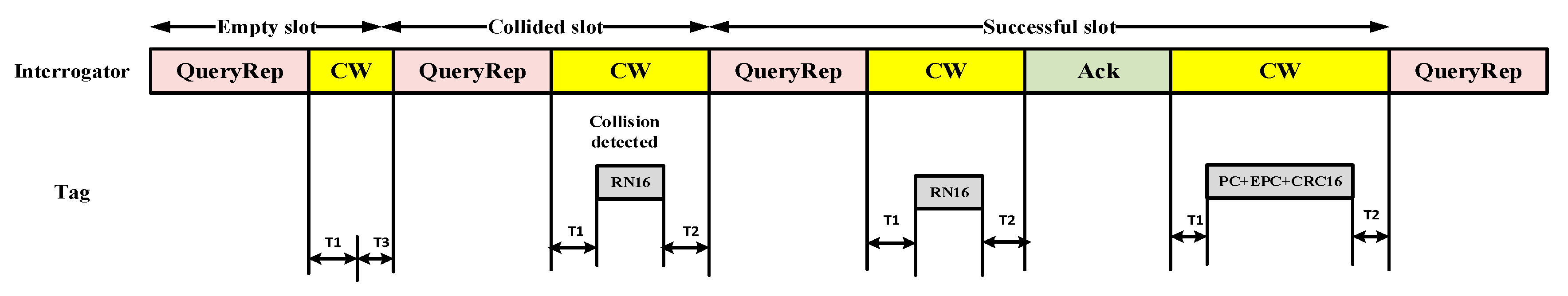
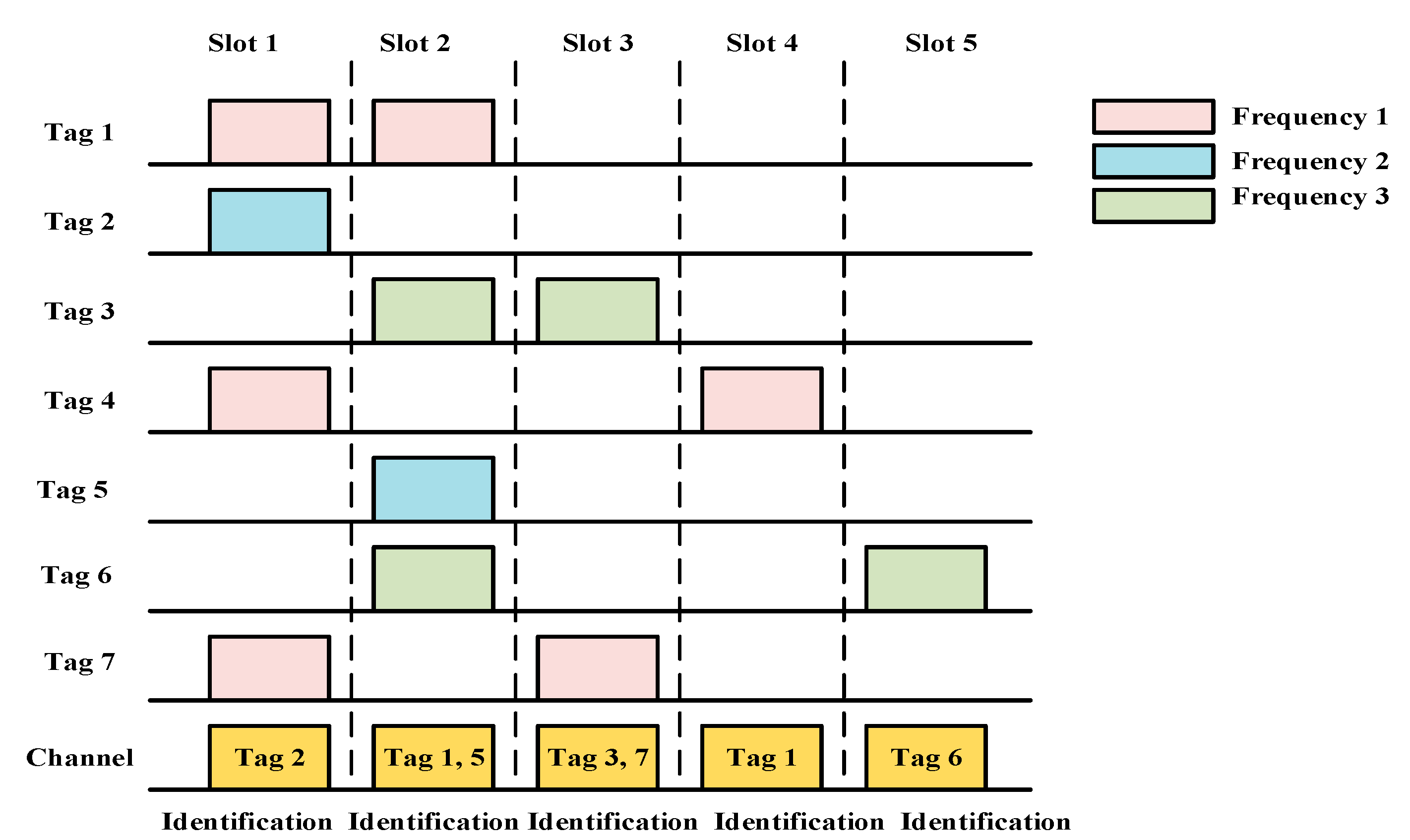
5.2.3. UAV-Based Multiple Tags Anti-Collision Protocol (UMTAP)
- Advantages: The anti-collision mechanism of the UMTAP yields a high system efficiency. Additionally, the tag identification time is shorter than that of similar protocols.
- Limitations: Channel and energy wastage occurs owing to the empty slots [66]. The numbers of successful slots, empty slots, and collision slots must be calculated after every one-slot duration, leading to significant energy and time consumption. Moreover, the speed and mobility of the UAV are not considered.
- Application domains: This protocol is useful for dense RFID-based environments in a 3D communication scenario.
- Future improvements: The multi-UAV architecture should be applied to increase the coverage area, and a mechanism of acquiring data from the IoT nodes should be developed.
5.2.4. Spectrum Sensing Using UAV (SSU)
- Advantages: The proposed mechanism performs well in terms of system throughput and avoids collisions due to the use of the cognitive UAV to detect idle channels.
- Limitations: The UAV continuously senses the channel while moving, leading to significant energy consumption.
- Application domains: Remote areas with multiple mobile users are promising candidates for this protocol.
- Future improvements: An optimized and efficient trajectory should be designed for the UAV to locate the IoT devices efficiently without significant energy wastage.
5.2.5. UAV-Based Relaying and Scheduling (URS)
- Advantages: By performing simulations, the UAV trajectory has been optimized for different scenarios. The optimization algorithm can yield stable performance in a dynamic environment.
- Limitations: Latency-critical tasks are not prioritized over normal tasks in the computation process. Hence, the completion of latency-critical tasks may be delayed if the number of normal tasks is large.
- Application domains: Remotely deployed IoT devices with blocked surroundings are suitable for this protocol.
- Future improvements: The multi-UAV scenario should be adopted for better coverage and interference avoidance between UAVs.
5.3. AI-Based MAC for UIoT
5.3.1. Sustainable and Secure Trajectory (SST)-Based MAC for UIoT
- Advantages: The protocol provides high performance, along with the optimal division of resources and link durations.
- Limitations: Owing to the complex system model, real-life implementation is difficult. Moreover, the model does not consider the energy consumption.
- Application domains: This protocol may be suitable for military and governmental applications, which requires secure path trajectories and sustainable links, because the system is secure from third-party attacks.
- Future improvements: The interference affecting the UAV-UAV communication should be considered by introducing a synchronization process between the UAVs.
5.3.2. Wake Up-Based on MDP (WupMDP) for UIoT
- Advantages: WupMDP MAC is effective for successful packet delivery. Moreover, an efficient collision-avoidance mechanism is applied in the device wake-up period, helping to prevent collisions during data transmission.
- Limitations: The localization of the IoT devices, which is crucial for the UIoT network, is omitted. Moreover, the UAV speed, height, and path planning are not considered.
- Application domains: This protocol may be appropriate for IoT monitoring applications where sensors must send data occasionally, e.g., soil monitoring, crop-field monitoring, and flood monitoring.
- Future improvements: The proposed model and algorithm should be extended to the multi-UAV application scenario, and the interference among the UAVs should be addressed.
5.3.3. Delay-Aware IoT Task Scheduling (DTS) with Constrained MDP (CMDP) for UIoT
- Advantages: The proposed scheme performs well with regard to the system delay for tasks with different arrival rates, owing to the use of the CMDP.
- Limitations: The interference between the UAV and the satellite is not considered.
- Application domains: Smart cities and smart oceans are good candidates for this scheme.
- Future improvements: Multi-UAV and multi-satellite scenarios should be considered to enhance the applicability.
5.3.4. DRL-Based Channel and Power Allocation Framework (DRLCPA)
- Advantages: The protocol is energy-efficient owing to the use of DRL by properly allocating the channel and power.
- Limitations: In the simulation, a dense IoT network was not considered. Additionally, the UAV speed and the localization of the IoT devices were ignored.
- Application domains: Remote hilly and mountainous areas are candidates for this protocol.
- Future improvements: The UAV trajectory should be optimized for efficient data collection within a short time.
5.3.5. DRL-Based Task Scheduling (DRLTS)
- Advantages: Load balancing for task offloading is effective owing to the use of the multi-UAV mechanism. DRLTS is effective for minimizing the slowdown of the task-execution process.
- Limitations: In a multi-UAV scenario, communication between UAVs is important for avoiding collisions and achieving proper synchronization. In [63], the communication between the UAVs was not considered.
- Application domains: Remotely deployed MEC-based applications are suitable for this protocol.
- Future improvements: DRL can be used for proper channel selection to minimize the collisions in data transmission.
5.3.6. Space/Aerial-Based Task Scheduling (STS)
- Advantages: The scheme performs well with regard to the average total delay and the total cost of UAV server usage. The UAV server usage is reduced through the DRL-based approach. Moreover, the prioritization of tasks is maintained, enhancing the QoS of the application.
- Limitations: The SAGIN system is expensive and complex to deploy in real application scenarios due to the use of UAVs, a satellite network, and the DRL-based approach [75].
- Application domains: Remote infrastructure-less areas with mobile IoT devices have good application prospects for this protocol.
- Future improvements: Communication between the UAVs and the satellite with proper synchronization should be investigated.
6. Comparison of MAC Protocols for UIoT
6.1. Discussion of Performance and Special Features
6.2. Discussion of Operational Characteristics
6.3. Lessons Learned
7. Open Issues and Research Challenges of MAC Protocols for UIoT
7.1. Energy Consumption and Network Lifetime
7.2. Privacy and Security
7.3. Interoperability
7.4. Integration of Machine Learning
7.5. Scalability and Large Network Size
7.6. Congestion Control
7.7. Cross-Layer Architecture
7.8. Performance Evaluation Tools
8. Conclusions
Author Contributions
Funding
Acknowledgments
Conflicts of Interest
References
- Mavrogiorgou, A.; Kiourtis, A.; Perakis, K.; Pitsios, S.; Kyriazis, D. IoT in healthcare: Achieving interoperability of high-quality data acquired by IoT medical devices. Sensors 2019, 19, 1978. [Google Scholar] [CrossRef]
- Alvarez-Campana, M.; López, G.; Vázquez, E.; Villagrá, V.A.; Berrocal, J. Smart CEI moncloa: An iot-based platform for people flow and environmental monitoring on a Smart University Campus. Sensors 2017, 17, 2856. [Google Scholar] [CrossRef]
- Mohammed, J.; Lung, C.-H.; Ocneanu, A.; Thakral, A.; Jones, C.; Adler, A. Internet of Things: Remote patient monitoring using web services and cloud computing. In Proceedings of the 2014 IEEE International Conference on Internet of Things (iThings), and IEEE Green Computing and Communications (GreenCom) and IEEE Cyber, Physical and Social Computing (CPSCom), Taipei, Taiwan, 1–3 September 2014; pp. 256–263. [Google Scholar]
- Haseeb, K.; Ud Din, I.; Almogren, A.; Islam, N. An Energy Efficient and Secure IoT-Based WSN Framework: An Application to Smart Agriculture. Sensors 2020, 20, 2081. [Google Scholar] [CrossRef]
- Chooruang, K.; Meekul, K. Design of an IoT energy monitoring system. In Proceedings of the 2018 16th International Conference on ICT and Knowledge Engineering (ICT&KE), Bangkok, Thailand, 21–23 November 2018; pp. 1–4. [Google Scholar]
- Benammar, M.; Abdaoui, A.; Ahmad, S.H.; Touati, F.; Kadri, A. A modular IoT platform for real-time indoor air quality monitoring. Sensors 2018, 18, 581. [Google Scholar] [CrossRef] [PubMed]
- Siddula, S.S.; Babu, P.; Jain, P. Water level monitoring and management of dams using IoT. In Proceedings of the 2018 3rd International Conference on Internet of Things: Smart Innovation and Usages (IoT-SIU), Bhimtal, India, 23–24 February 2018; pp. 1–5. [Google Scholar]
- Barthélemy, J.; Verstaevel, N.; Forehead, H.; Perez, P. Edge-computing video analytics for real-time traffic monitoring in a smart city. Sensors 2019, 19, 2048. [Google Scholar] [CrossRef]
- Gonzalez, L.F.; Montes, G.A.; Puig, E.; Johnson, S.; Mengersen, K.; Gaston, K.J. Unmanned aerial vehicles (UAVs) and artificial intelligence revolutionizing wildlife monitoring and conservation. Sensors 2016, 16, 97. [Google Scholar] [CrossRef]
- Primicerio, J.; Di Gennaro, S.F.; Fiorillo, E.; Genesio, L.; Lugato, E.; Matese, A.; Vaccari, F.P. A flexible unmanned aerial vehicle for precision agriculture. Precis. Agric. 2012, 13, 517–523. [Google Scholar] [CrossRef]
- Sun, J.; Li, B.; Jiang, Y.; Wen, C.-Y. A camera-based target detection and positioning UAV system for search and rescue (SAR) purposes. Sensors 2016, 16, 1778. [Google Scholar] [CrossRef]
- Elloumi, M.; Dhaou, R.; Escrig, B.; Idoudi, H.; Saidane, L.A. Monitoring road traffic with a UAV-based system. In Proceedings of the 2018 IEEE Wireless Communications and Networking Conference (WCNC), Barcelona, Spain, 15–18 April 2018; pp. 1–6. [Google Scholar]
- Katikala, S. Google project loon. Insight Rivier Acad. J. 2014, 10, 1–6. [Google Scholar]
- Gomez, M.L.; Cox, A. Flying Aquila: Early Lessons from the First Full-Scale Test Flight and the Path Ahead. Available online: https://engineering.fb.com/connectivity/flying-aquila-early-lessons-from-the-first-full-scale-test-flight-and-the-path-ahead/ (accessed on 21 October 2019).
- Shen, L.; Wang, N.; Ji, X.; Mu, X.; Cai, L. Iterative trajectory optimization for physical-layer secure buffer-aided UAV mobile relaying. Sensors 2019, 19, 3442. [Google Scholar] [CrossRef]
- Cao, H.; Liu, Y.; Yue, X.; Zhu, W. Cloud-assisted UAV data collection for multiple emerging events in distributed WSNs. Sensors 2017, 17, 1818. [Google Scholar] [CrossRef]
- Yu, T.; Wang, X.; Shami, A. UAV-enabled spatial data sampling in large-scale IoT systems using denoising autoencoder neural network. IEEE Internet Things J. 2018, 6, 1856–1865. [Google Scholar] [CrossRef]
- Sharma, V.; Song, F.; You, I.; Atiquzzaman, M. Energy efficient device discovery for reliable communication in 5G-based IoT and BSNs using unmanned aerial vehicles. J. Netw. Comput. Appl. 2017, 97, 79–95. [Google Scholar] [CrossRef]
- Liu, M.; Yang, J.; Gui, G. DSF-NOMA: UAV-assisted emergency communication technology in a heterogeneous Internet of Things. IEEE Internet Things J. 2019, 6, 5508–5519. [Google Scholar] [CrossRef]
- Zhan, C.; Lai, H. Energy minimization in Internet-of-Things system based on rotary-wing UAV. IEEE Wirel. Commun. Lett. 2019, 8, 1341–1344. [Google Scholar] [CrossRef]
- Say, S.; Inata, H.; Shimamoto, S. A hybrid collision coordination-based multiple access scheme for super dense aerial sensor networks. In Proceedings of the 2016 IEEE Wireless Communications and Networking Conference, Doha, Qatar, 3–6 April 2016; pp. 1–6. [Google Scholar]
- Liu, J.; Shi, Y.; Fadlullah, Z.M.; Kato, N. Space-air-ground integrated network: A survey. IEEE Commun. Surv. Tutor. 2018, 20, 2714–2741. [Google Scholar] [CrossRef]
- Choudhary, G.; Sharma, V.; You, I. Sustainable and secure trajectories for the military Internet of Drones (IoD) through an efficient Medium Access Control (MAC) protocol. Comput. Electr. Eng. 2019, 74, 59–73. [Google Scholar] [CrossRef]
- Alzenad, M.; El-Keyi, A.; Yanikomeroglu, H. 3-D placement of an unmanned aerial vehicle base station for maximum coverage of users with different QoS requirements. IEEE Wirel. Commun. Lett. 2017, 7, 38–41. [Google Scholar] [CrossRef]
- Mozaffari, M.; Saad, W.; Bennis, M.; Debbah, M. Mobile unmanned aerial vehicles (UAVs) for energy-efficient Internet of Things communications. IEEE Trans. Wirel. Commun. 2017, 16, 7574–7589. [Google Scholar] [CrossRef]
- Savkin, A.V.; Huang, H. Deployment of unmanned aerial vehicle base stations for optimal quality of coverage. IEEE Wirel. Commun. Lett. 2018, 8, 321–324. [Google Scholar] [CrossRef]
- Sun, X.; Ansari, N.; Fierro, R. Jointly Optimized 3D Drone Mounted Base Station Deployment and User Association in Drone Assisted Mobile Access Networks. IEEE Trans. Veh. Technol. 2019, 69, 2195–2203. [Google Scholar] [CrossRef]
- Schellenberg, B.; Richardson, T.; Richards, A.; Clarke, R.; Watson, M. On-board real-time trajectory planning for fixed wing unmanned aerial vehicles in extreme environments. Sensors 2019, 19, 4085. [Google Scholar] [CrossRef] [PubMed]
- Hu, H.; Xiong, K.; Qu, G.; Ni, Q.; Fan, P.; Letaief, K.B. AoI-Minimal Trajectory Planning and Data Collection in UAV-Assisted Wireless Powered IoT Networks. IEEE Internet Things J. 2020. Early Access, 1. [Google Scholar] [CrossRef]
- Mozaffari, M.; Saad, W.; Bennis, M.; Debbah, M. Mobile Internet of Things: Can UAVs provide an energy-efficient mobile architecture? In Proceedings of the 2016 IEEE global communications conference (GLOBECOM), Washington, DC, USA, 4–8 December 2016; pp. 1–6. [Google Scholar]
- Zhan, C.; Zeng, Y.; Zhang, R. Energy-efficient data collection in UAV enabled wireless sensor network. IEEE Wirel. Commun. Lett. 2017, 7, 328–331. [Google Scholar] [CrossRef]
- Marchese, M.; Moheddine, A.; Patrone, F. IoT and UAV integration in 5G hybrid terrestrial-satellite networks. Sensors 2019, 19, 3704. [Google Scholar] [CrossRef]
- Wang, H.; Zhao, H.; Wu, W.; Xiong, J.; Ma, D.; Wei, J. Deployment algorithms of flying base stations: 5G and beyond with UAVs. IEEE Internet Things J. 2019, 6, 10009–10027. [Google Scholar] [CrossRef]
- Arabi, S.; Sabir, E.; Elbiaze, H.; Sadik, M. Data gathering and energy transfer dilemma in UAV-assisted flying access network for IoT. Sensors 2018, 18, 1519. [Google Scholar] [CrossRef]
- Li, L.; Wen, X.; Lu, Z.; Pan, Q.; Jing, W.; Hu, Z. Energy-Efficient UAV-Enabled MEC System: Bits Allocation Optimization and Trajectory Design. Sensors 2019, 19, 4521. [Google Scholar] [CrossRef]
- De Moraes, R.S.; de Freitas, E.P. Multi-UAV based crowd monitoring system. IEEE Trans. Aerosp. Electron. Syst. 2019, 56, 1332–1345. [Google Scholar] [CrossRef]
- Kim, D.; Jung, J.; Koo, Y.; Yi, Y. Bird-MAC: Energy-Efficient MAC for Quasi-Periodic IoT Applications by Avoiding Early Wake-up. IEEE Trans. Mob. Comput. 2019, 19, 788–802. [Google Scholar] [CrossRef]
- Al-Janabi, T.A.; Al-Raweshidy, H.S. An energy efficient hybrid MAC protocol with dynamic sleep-based scheduling for high density IoT networks. IEEE Internet Things J. 2019, 6, 2273–2287. [Google Scholar] [CrossRef]
- Wymore, M.L.; Qiao, D. RIVER-MAC: A Receiver-Initiated Asynchronously Duty-Cycled MAC Protocol for the Internet of Things. In Proceedings of the 2019 IEEE 43rd Annual Computer Software and Applications Conference (COMPSAC), Milwaukee, WI, USA, 15–19 July 2019; pp. 860–869. [Google Scholar]
- Hassan, G.; Hassanein, H.S. MoT: A deterministic latency MAC protocol for mission-critical IoT applications. In Proceedings of the 2018 14th International Wireless Communications & Mobile Computing Conference (IWCMC), Limassol, Cyprus, 25–29 June 2018; pp. 588–593. [Google Scholar]
- Farag, H.; Mahmood, A.; Gidlund, M.; Oesterberg, P. PR-CCA MAC: A prioritized random CCA MAC protocol for mission-critical IoT applications. In Proceedings of the 2018 IEEE International Conference on Communications (ICC), Kansas City, KS, USA, 20–24 May 2018; pp. 1–6. [Google Scholar]
- Zhuo, S.; Song, Y.-Q. GoMacH: A traffic adaptive multi-channel MAC protocol for IoT. In Proceedings of the 2017 IEEE 42nd Conference on Local Computer Networks (LCN), Singapore, 9–12 October 2017; pp. 489–497. [Google Scholar]
- Ye, Q.; Zhuang, W. Token-based adaptive MAC for a two-hop Internet-of-Things enabled MANET. IEEE Internet Things J. 2017, 4, 1739–1753. [Google Scholar] [CrossRef]
- Kim, K.T.; Kim, H.; Park, H.; Kim, S.-T. An industrial iot mac protocol based on ieee 802.15. 4e tsch for a large-scale network. In Proceedings of the 2017 19th International Conference on Advanced Communication Technology (ICACT), PyeongChang, Korea, 19–22 February 2017; pp. 721–724. [Google Scholar]
- Balevi, E.; Gitlin, R.D. A random access scheme for large scale 5G/IoT applications. In Proceedings of the 2018 IEEE 5G World Forum (5GWF), Santa Clara, CA, USA, 9–11 July 2018; pp. 452–456. [Google Scholar]
- Zhang, M.; Dong, C.; Huang, Y. FS-MAC: An adaptive MAC protocol with fault-tolerant synchronous switching for FANETs. IEEE Access 2019, 7, 80602–80613. [Google Scholar] [CrossRef]
- Wang, W.; Dong, C.; Wang, H.; Jiang, A. Design and implementation of adaptive MAC framework for UAV ad hoc networks. In Proceedings of the 2016 12th International Conference on Mobile Ad-Hoc and Sensor Networks (MSN), Hefei, China, 16–18 December 2016; pp. 195–201. [Google Scholar]
- Feng, P.; Bai, Y.; Huang, J.; Wang, W.; Gu, Y.; Liu, S. CogMOR-MAC: A cognitive multi-channel opportunistic reservation MAC for multi-UAVs ad hoc networks. Comput. Commun. 2019, 136, 30–42. [Google Scholar] [CrossRef]
- Wang, W.; Dong, C.; Zhu, S.; Wang, H. DFRA: Demodulation-free random access for UAV ad hoc networks. In Proceedings of the 2017 IEEE International Conference on Communications (ICC), Paris, France, 21–25 May 2017; pp. 1–6. [Google Scholar]
- Vashisht, S.; Jain, S. An energy-efficient and location-aware medium access control for quality of service enhancement in unmanned aerial vehicular networks. Comput. Electr. Eng. 2019, 75, 202–217. [Google Scholar] [CrossRef]
- Lin, X.; Su, G.; Chen, B.; Wang, H.; Dai, M. Striking a balance between system throughput and energy efficiency for UAV-IoT systems. IEEE Internet Things J. 2019, 6, 10519–10533. [Google Scholar] [CrossRef]
- Kozłowski, A.; Sosnowski, J. Energy efficiency trade-off between duty-cycling and wake-up radio techniques in IoT networks. Wirel. Pers. Commun. 2019, 107, 1951–1971. [Google Scholar] [CrossRef]
- Shi, B.; Wei, W.; Wang, Y.; Shu, W. A novel energy efficient topology control scheme based on a coverage-preserving and sleep scheduling model for sensor networks. Sensors 2016, 16, 1702. [Google Scholar] [CrossRef]
- Agrawal, P.; Chen, J.-C.; Kishore, S.; Sivalingam, K.M. CDMA Mobile Station Wireless Transmission Power Management with Adaptive Scheduling Priorities Based On Battery Power Level. U.S. Patent 6,072,784, 6 June 2000. [Google Scholar]
- Yang, X.; Wang, L.; Xie, J.; Wang, Y. Medium Access control for unmanned aerial vehicle based mission critical wireless sensor networks in 3D monitoring networks. IEEE Access 2019, 7, 102274–102283. [Google Scholar] [CrossRef]
- Liu, Y.; Yuen, C.; Chen, J.; Cao, X. A scalable hybrid MAC protocol for massive M2M networks. In Proceedings of the 2013 IEEE wireless communications and networking conference (WCNC), Shanghai, China, 7–10 April 2013; pp. 250–255. [Google Scholar]
- Pan, Q.; Wen, X.; Lu, Z.; Li, L.; Jing, W. Dynamic speed control of unmanned aerial vehicles for data collection under internet of things. Sensors 2018, 18, 3951. [Google Scholar] [CrossRef]
- Oliveira, L.; Rodrigues, J.J.; Kozlov, S.A.; Rabêlo, R.A.; de Albuquerque, V.H.C. MAC layer protocols for Internet of Things: A survey. Future Internet 2019, 11, 16. [Google Scholar] [CrossRef]
- Abbasian, A.; Safkhani, M. CNCAA: A new anti-collision algorithm using both collided and non-collided parts of information. Comput. Netw. 2020, 172, 107159. [Google Scholar] [CrossRef]
- Li, B.; Guo, X.; Zhang, R.; Du, X.; Guizani, M. Performance Analysis and Optimization for the MAC Protocol in UAV-based IoT network. IEEE Trans. Veh. Technol. 2020. [Google Scholar] [CrossRef]
- Cionca, V.; Newe, T.; Dadârlat, V. TDMA protocol requirements for wireless sensor networks. In Proceedings of the 2008 Second International Conference on Sensor Technologies and Applications (sensorcomm 2008), Cap Esterel, France, 25–31 August 2008; pp. 30–35. [Google Scholar]
- Du, Y.; Yang, K.; Wang, K.; Zhang, G.; Zhao, Y.; Chen, D. Joint resources and workflow scheduling in uav-enabled wirelessly-powered mec for iot systems. IEEE Trans. Veh. Technol. 2019, 68, 10187–10200. [Google Scholar] [CrossRef]
- Ye, H.-T.; Kang, X.; Joung, J.; Liang, Y.-C. Optimal time allocation for full-duplex wireless-powered IoT networks with unmanned aerial vehicle. In Proceedings of the ICC 2019-2019 IEEE International Conference on Communications (ICC), Shanghai, China, 20–24 May 2019; pp. 1–6. [Google Scholar]
- Chen, S.; Ma, R.; Chen, H.-H.; Zhang, H.; Meng, W.; Liu, J. Machine-to-machine communications in ultra-dense networks—A survey. IEEE Commun. Surv. Tutor. 2017, 19, 1478–1503. [Google Scholar] [CrossRef]
- He, Y.; Zhang, R.; Jiang, Y.; Li, B.; Wang, D. An Anti-Collision Protocol Based on UAV for Internet of Things. In Proceedings of the 2019 11th International Conference on Wireless Communications and Signal Processing (WCSP), Xi’an, China, 23–25 October 2019; pp. 1–6. [Google Scholar]
- Pushpan, S.; Velusamy, B. Fuzzy-based dynamic time slot allocation for wireless body area networks. Sensors 2019, 19, 2112. [Google Scholar] [CrossRef]
- Almasoud, A.M.; Kamal, A.E. Data dissemination in IoT using a cognitive UAV. IEEE Trans. Cogn. Commun. Netw. 2019, 5, 849–862. [Google Scholar] [CrossRef]
- Hu, X.; Wong, K.-K.; Yang, K.; Zheng, Z. UAV-assisted relaying and edge computing: Scheduling and trajectory optimization. IEEE Trans. Wirel. Commun. 2019, 18, 4738–4752. [Google Scholar] [CrossRef]
- Long, F.; Li, N.; Wang, Y. Autonomic mobile networks: The use of artificial intelligence in wireless communications. In Proceedings of the 2017 2nd International Conference on Advanced Robotics and Mechatronics (ICARM), Hefei/Tai’an, China, 27–31 August 2017; pp. 582–586. [Google Scholar]
- Djiroun, F.Z.; Bagaa, M.; Taleb, T. A Markov decision process-based collision avoidance in IoT applications. In Proceedings of the GLOBECOM 2017-2017 IEEE Global Communications Conference, Singapore, 4–8 December 2017; pp. 1–6. [Google Scholar]
- Zhou, C.; Wu, W.; He, H.; Yang, P.; Lyu, F.; Cheng, N.; Shen, X. Delay-aware IoT task scheduling in space-air-ground integrated network. In Proceedings of the 2019 IEEE Global Communications Conference (GLOBECOM), Waikoloa, HI, USA, 9–13 December 2019; pp. 1–6. [Google Scholar]
- Cao, Y.; Zhang, L.; Liang, Y.-C. Deep Reinforcement Learning for Channel and Power Allocation in UAV-enabled IoT Systems. In Proceedings of the 2019 IEEE Global Communications Conference (GLOBECOM), Waikoloa, HI, USA, 9–13 December 2019; pp. 1–6. [Google Scholar]
- Yang, L.; Yao, H.; Wang, J.; Jiang, C.; Benslimane, A.; Liu, Y. Multi-UAV-Enabled Load-Balance Mobile-Edge Computing for IoT Networks. IEEE Internet Things J. 2020, 7, 6898–6908. [Google Scholar] [CrossRef]
- Cheng, N.; Lyu, F.; Quan, W.; Zhou, C.; He, H.; Shi, W.; Shen, X. Space/aerial-assisted computing offloading for IoT applications: A learning-based approach. IEEE J. Sel. Areas Commun. 2019, 37, 1117–1129. [Google Scholar] [CrossRef]
- Cheng, N.; Quan, W.; Shi, W.; Wu, H.; Ye, Q.; Zhou, H.; Zhuang, W.; Shen, X.S.; Bai, B. A comprehensive simulation platform for space-air-ground integrated network. IEEE Wirel. Commun. 2020, 27, 178–185. [Google Scholar] [CrossRef]
- Orsino, A.; Araniti, G.; Militano, L.; Alonso-Zarate, J.; Molinaro, A.; Iera, A. Energy efficient IoT data collection in smart cities exploiting D2D communications. Sensors 2016, 16, 836. [Google Scholar] [CrossRef] [PubMed]
- Rani, S.; Talwar, R.; Malhotra, J.; Ahmed, S.H.; Sarkar, M.; Song, H. A novel scheme for an energy efficient Internet of Things based on wireless sensor networks. Sensors 2015, 15, 28603–28626. [Google Scholar] [CrossRef] [PubMed]
- Nakamoto, S. Bitcoin: A Peer-to-Peer Electronic Cash System. Available online: www.bitcoin.org (accessed on 31 October 2019).
- Islam, A.; Shin, S.Y. Bus: A blockchain-enabled data acquisition scheme with the assistance of UAV swarm in internet of things. IEEE Access 2019, 7, 103231–103249. [Google Scholar] [CrossRef]
- Azmoodeh, A.; Dehghantanha, A.; Choo, K.-K.R. Robust malware detection for internet of (battlefield) things devices using deep eigenspace learning. IEEE Trans. Sustain. Comput. 2018, 4, 88–95. [Google Scholar] [CrossRef]
- Motlagh, N.H.; Taleb, T.; Arouk, O. Low-altitude unmanned aerial vehicles-based internet of things services: Comprehensive survey and future perspectives. IEEE Internet Things J. 2016, 3, 899–922. [Google Scholar] [CrossRef]
- Xie, P.; Xing, L.; Wu, H.; Seo, J.T.; You, I. Cooperative Jammer Selection for Secrecy Improvement in Cognitive Internet of Things. Sensors 2018, 18, 4257. [Google Scholar] [CrossRef]
- Ghosh, A.; Chatterjee, T.; Samanta, S.; Aich, J.; Roy, S. Distracted driving: A novel approach towards accident prevention. Adv. Comput. Sci. Technol 2017, 10, 2693–2705. [Google Scholar]
- Liu, Y.; Yuen, C.; Cao, X.; Hassan, N.U.; Chen, J. Design of a scalable hybrid MAC protocol for heterogeneous M2M networks. IEEE Internet Things J. 2014, 1, 99–111. [Google Scholar] [CrossRef]
- Ancillotti, E.; Bruno, R.; Vallati, C.; Mingozzi, E. Design and evaluation of a rate-based congestion control mechanism in CoAP for IoT applications. In Proceedings of the 2018 IEEE 19th International Symposium on “A World of Wireless, Mobile and Multimedia Networks” (WoWMoM), Chania, Greece, 12–15 June 2018; pp. 14–15. [Google Scholar]
- Beulah Jayakumari, R.; Jawahar Senthilkumar, V. Priority based congestion control dynamic clustering protocol in mobile wireless sensor networks. Sci. World J. 2015, 2015, 596138. [Google Scholar] [CrossRef]
- Fallah, Y.P.; Huang, C.; Sengupta, R.; Krishnan, H. Congestion control based on channel occupancy in vehicular broadcast networks. In Proceedings of the 2010 IEEE 72nd Vehicular Technology Conference-Fall, Ottawa, ON, Canada, 6–9 September 2010; pp. 1–5. [Google Scholar]
- Resner, D.; de Araujo, G.M.; Fröhlich, A.A. Design and implementation of a cross-layer IoT protocol. Sci. Comput. Program. 2018, 165, 24–37. [Google Scholar] [CrossRef]

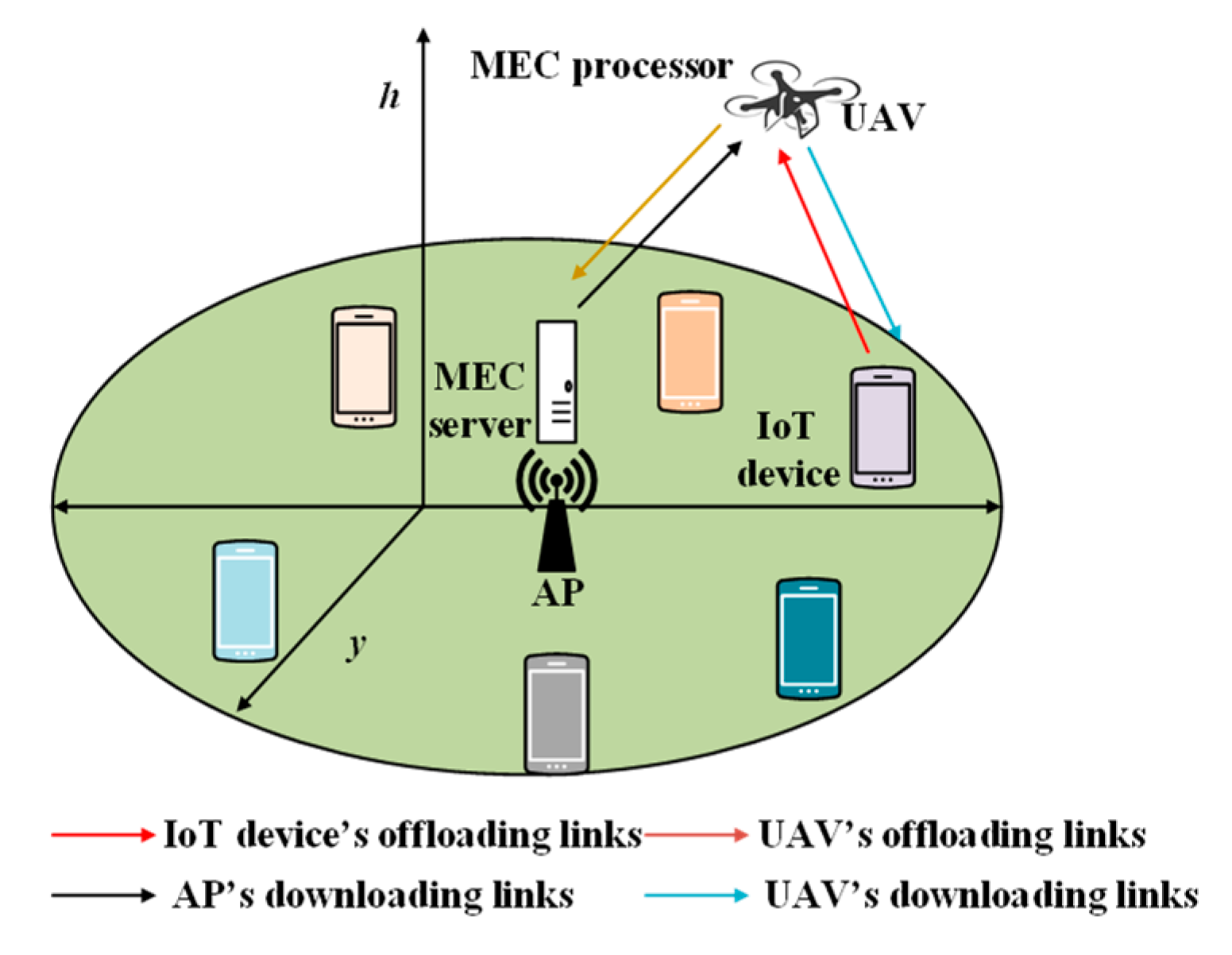
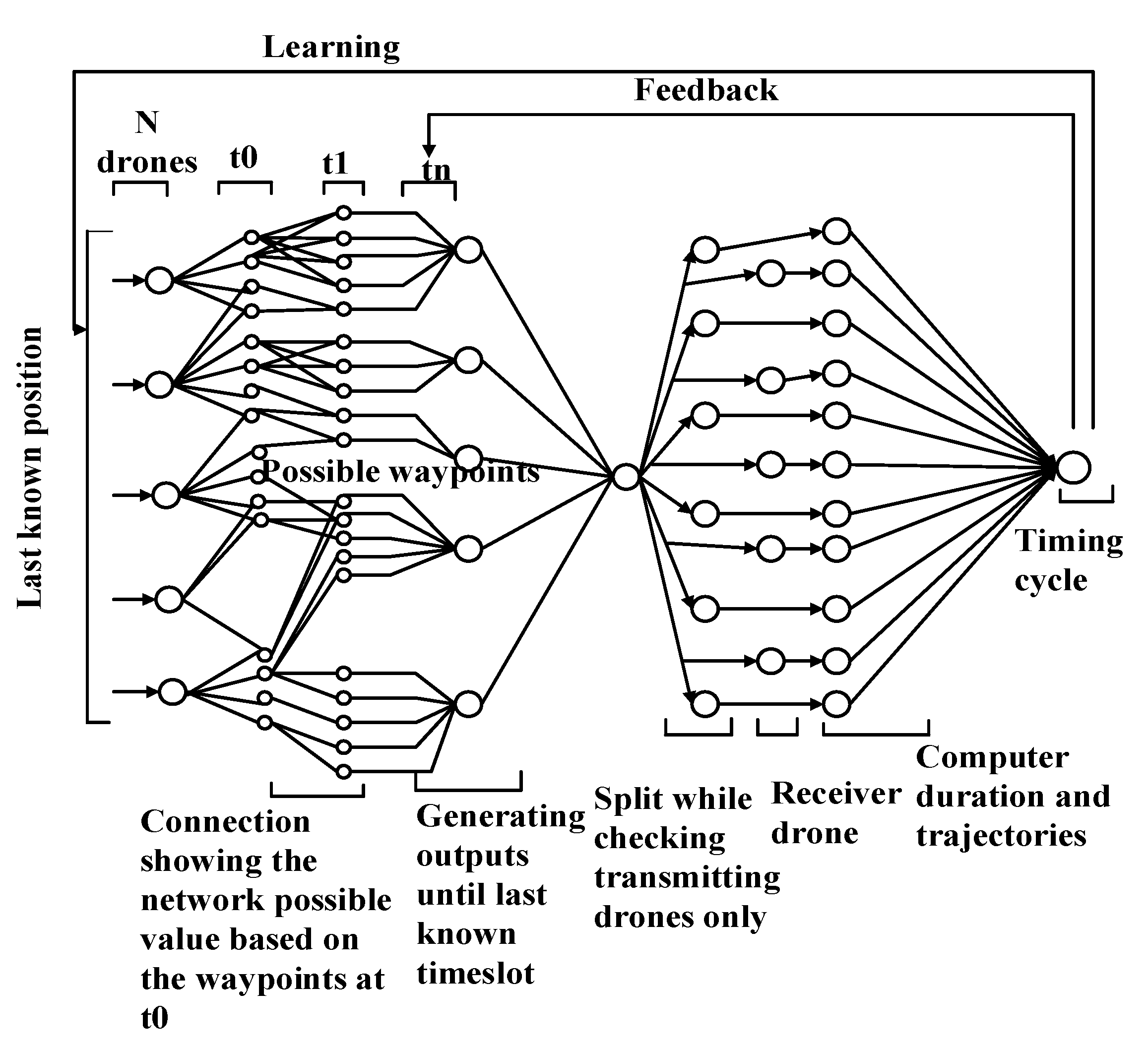
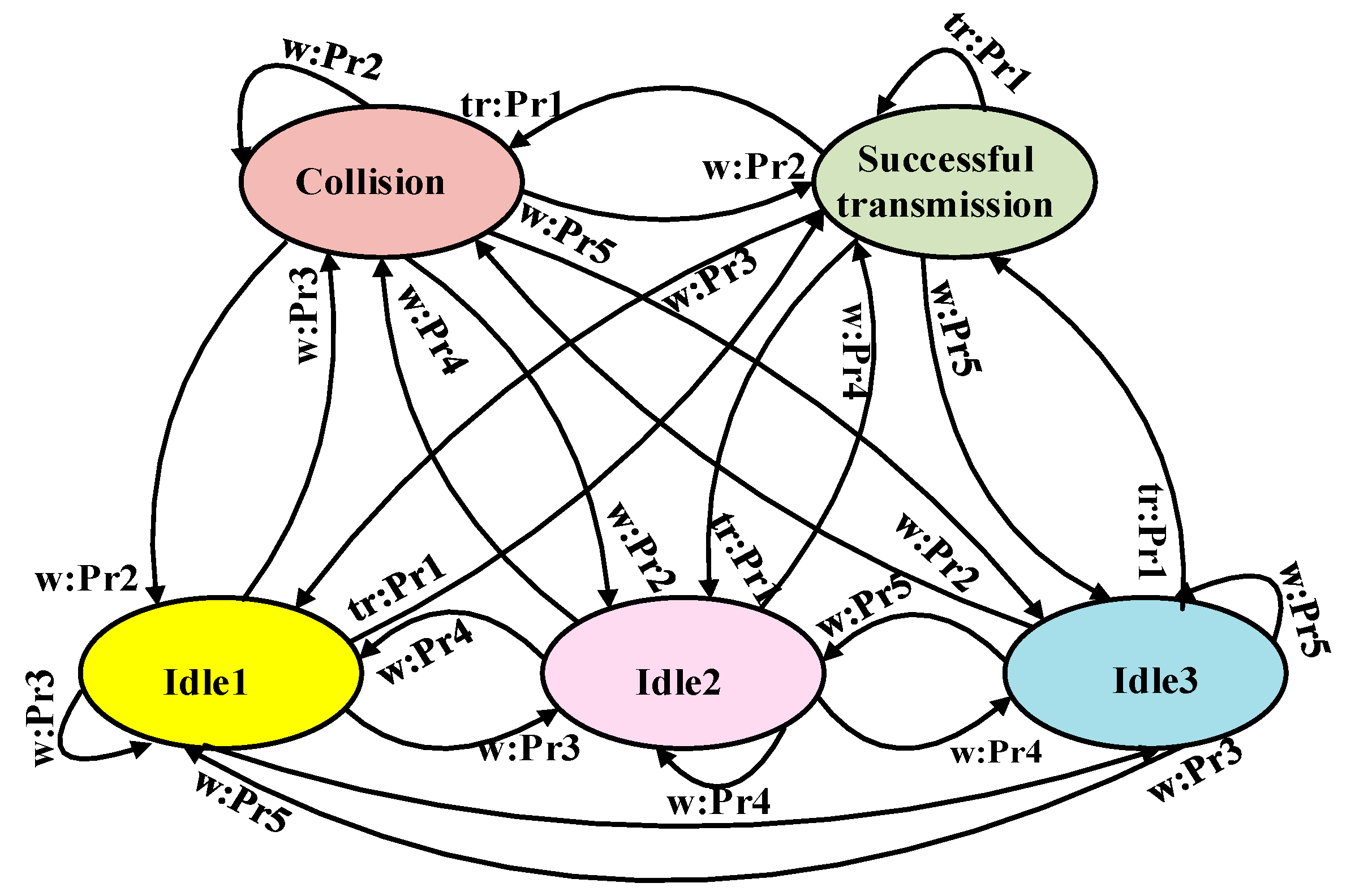
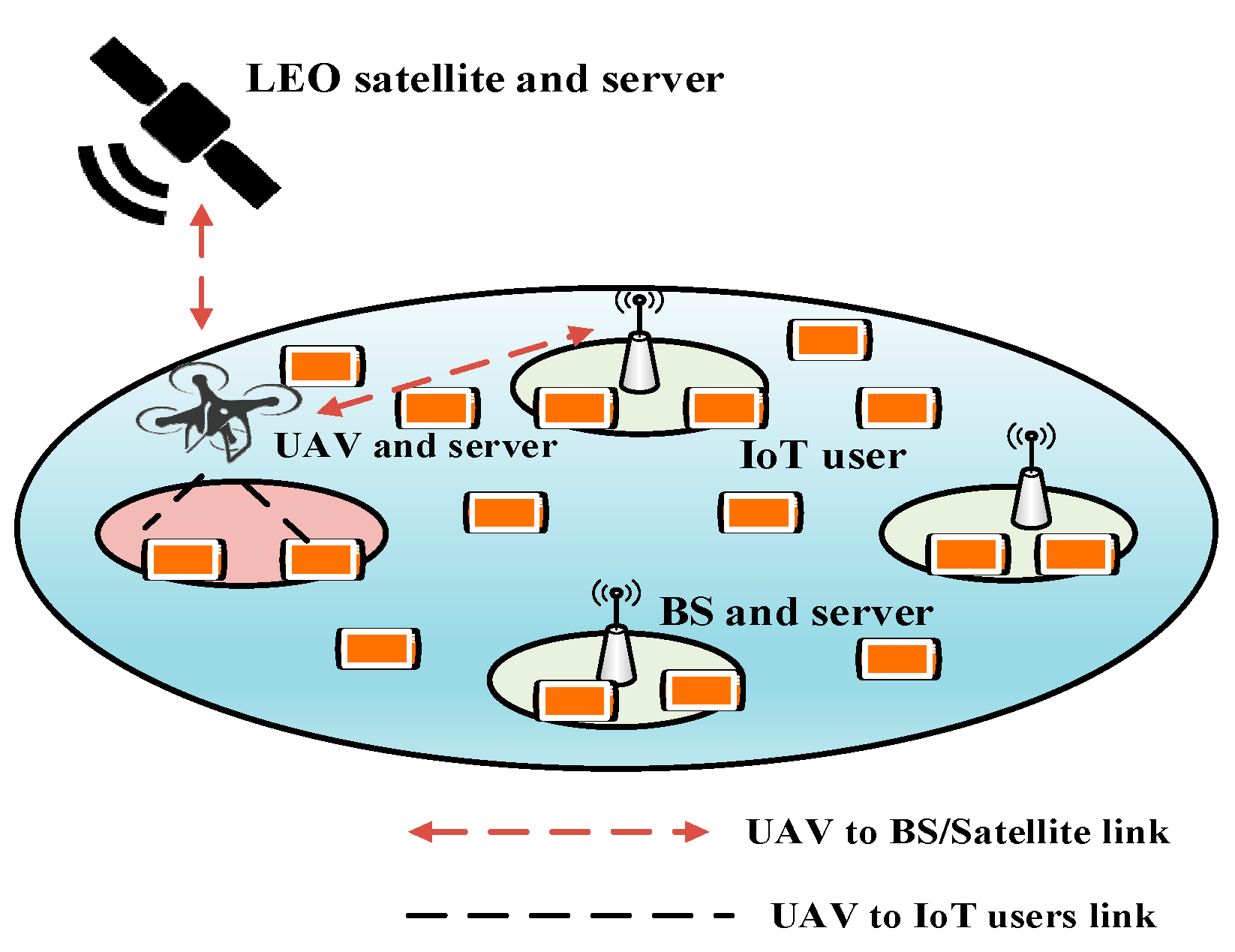


| Protocol | Year | Main Ideas | Innovative Features | Optimization Techniques |
|---|---|---|---|---|
| Balanced UAV-IoT [51] | 2019 | Slotted ALOHA-based approach is adopted. | Two modes are adopted: energy-efficient mode and system efficiency mode. | Locating optimal parameters utilizing the particle swarm optimization algorithm. |
| DSC-UAV [57] | 2018 | Physical RAP is adopted under LTE/LTE-A network. | UAVs can adaptively adjust their speed to maximize data-collection efficiency. | – |
| Modified CSMA/CA [60] | 2020 | CSMA/CA-based approach is adopted. | CW size is adjusted according to the contact duration between UAV and IoT device. | – |
| JRWS [62] | 2019 | TDMA-based workflow model is adopted for data transmission and computation. | Different optimization techniques are used. | UAV energy minimization problem is solved by the block coordinate descent method. The resource allocation problem is solved by the Lagrange dual method. The optimal IoTD sequence is obtained using flow shop scheduling techniques. |
| OTA [63] | 2019 | Dynamic TDMA-based frame structure is adopted. | UAV is equipped with a full-duplex HAP. | Optimal time allocation strategy is solved by Karush–Kuhn–Tucker conditions. |
| UMTAP [65] | 2019 | TDMA-based approach is adopted. | Multi frequency tag collision is resolved. | Optimal frame length is calculated using Limit theorems and Taylor’s formula. |
| SSU [67] | 2019 | TDMA-based approach is adopted. | Optimal transmission strategy is used, with the number of transmission slots below a threshold level. | Successive convex approximation algorithm is used to optimize imperfect spectrum sensing. |
| URS [68] | 2019 | TDMA-based approach is adopted. | Each IoT device can simultaneously perform offloading and local computation. | Computation resource scheduling, bandwidth allocation, and UAV’s trajectory are optimized using successive convex approximation methods. |
| SST [23] | 2019 | ANN-based security framework is adopted. | Three types of communication links are used: UAV-to-UAV, UAV-to-device, and virtual. | – |
| WupMDP [70] | 2017 | MDP-based approach is adopted. | MDP comprises five stages: successful transmission, collision, Idle1, Idle2, and Idle3. | – |
| DTS [71] | 2019 | MDP-based approach is adopted. | UAV is equipped with two communication interfaces. | Energy consumption is optimized using constrained MDP. |
| DRLCPA [72] | 2019 | Deep learning-based approach is adopted. | UAV-BS uses a trajectory buffer to store learned experiences in a first-in-last-out manner. | The DRL-based actor-critic network is used to optimize energy consumption and enhance system performance. |
| DRLTS [73] | 2020 | Deep learning-based approach is adopted. | Reward function directs the agent to minimize the average slowdown for UAVs. | An approximation algorithm is used to determine all the connections between UAV and IoT devices. |
| STS [74] | 2019 | Deep learning-based approach is adopted. | UAV employs different VMs for different tasks. | DRL is used to find the optimal offloading policy. |
| Protocol | Reference | Evaluated Performance Metrics | Performance Objective |
|---|---|---|---|
| Balanced UAV-IoT | [51] | Number of competing tags in each reading cycle, maximal allowable flying speed, energy-efficiency gain | Maximize throughput with minimum energy consumption |
| DSC-UAV | [57] | Successful access probability, average access delay, block probability, data-collection efficiency, collision probability | Maximize data-collection efficiency |
| Modified CSMA/CA | [60] | Saturation throughput for different device densities, retry limit, CW size, radius | Increase saturation throughput |
| JRWS | [62] | Energy consumption, weighted energy consumption, total hovering time | Minimize total energy consumption |
| OTA | [63] | Total throughput | Maximize total throughput |
| UMTAP | [65] | System efficiency, tag identification time | Increase system efficiency |
| SSU | [67] | Average data rate, average number of bits | Maximize number of bits received by IoT devices |
| URS | [68] | Total task completion time, weight for energy consumption of UAV, uniform size ratio of task-output data to task-input data, separate energy consumption for IoT devices and UAV, weighted sum of energy consumption for UAV and IoT devices | Minimize weighted sum of energy consumption of UAV and IoT devices |
| SST | [23] | Macaulay duration for network resources, link depletion at different values of variables, link duration based on Macaulay-duration conditions, network learning rate | Secure link connectivity |
| WupMDP | [70] | Number of successfully transmitted packets, gain between successfully transmitted and collided packets | Increase number of successfully transmitted packets |
| DTS | [71] | System delay vs. energy consumption, system drop rate, and task arrival rate | Reduce delay |
| DRLCPA | [72] | Moving-average max–min energy efficiency of IoT nodes with varying number of nodes, moving-average max–min energy efficiency of IoT nodes with different algorithms | Maximize minimum energy efficiency among all IoT nodes |
| DRLTS | [73] | Reward, average slowdown, fitness | Improve task-execution efficiency for each UAV |
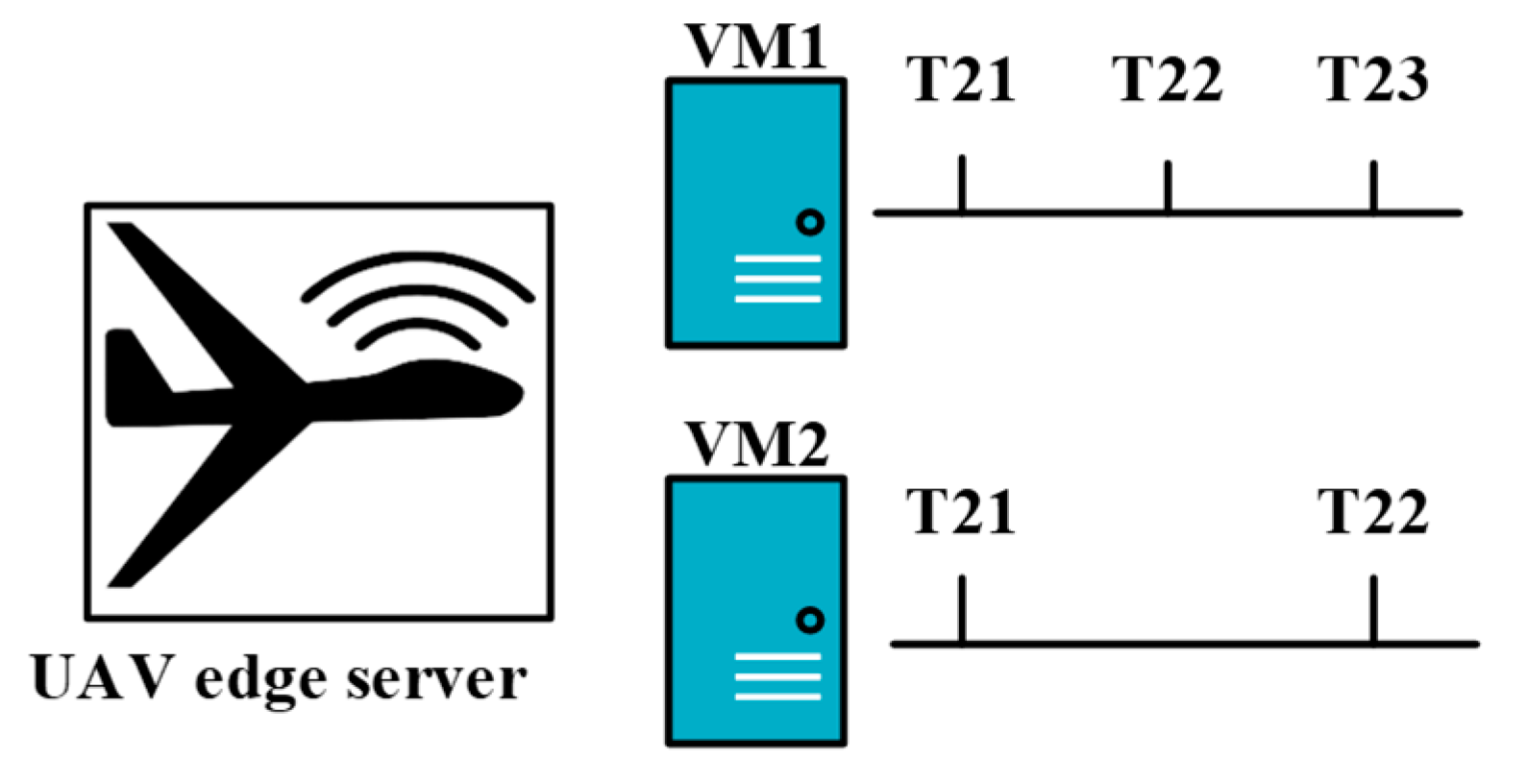
| STS | [74] | Average total delay vs. UAV edge server computational resources, total number of tasks, total cost | Reduce total cost |
| Reference | MAC Type | Protocol Overhead | UAV Transmission Range | Scalability | Fairness | Energy Efficiency | Load Balancing | UAV Speed (m/s) | UAV Altitude (m) | Number of UAVs | Data Rate | Bandwidth |
|---|---|---|---|---|---|---|---|---|---|---|---|---|
| [51] | C | Y | 150–550 | H | Me | Y | N | 0–120 | 0–300 | S | 40 kbps | - |
| [57] | C | Y | 30 | L | Me | N | N | 0–100 | - | S | - | - |
| [60] | C | Y | 1000 | L | Me | N | N | 10–20 | - | S | 1 Mbits | - |
| [62] | CF | N | - | H | H | Y | N | - | 5 | S | - | 10 MHz |
| [63] | CF | N | - | L | H | N | N | 10 | 5, 10 | S | - | - |
| [68] | CF | N | - | L | H | Y | N | - | 10 | S | - | 30 MHz |
| [65] | CF | Y | 200 | H | H | N | Y | - | - | Mu | 2 Mbps | - |
| [67] | CF | N | L | L | H | N | N | 15 | 50, 80 | S | - | 2 MHz |
| [23] | NN | Y | - | L | H | N | Y | 11.11 | - | Mu | - | - |
| [70] | MDP | Y | - | L | H | N | Y | - | - | Mu | - | - |
| [71] | MDP | Y | 500 | H | H | N | N | - | 100 | S | - | 10 MHz |
| [72] | DRL | Y | 40 | H | H | Y | N | - | 100 | S | - | 1 kHz |
| [73] | DRL | Y | 100 | H | H | N | Y | - | 100 | Mu | - | 1 MHz |
| [74] | DRL | Y | - | H | H | Y | Y | - | 90 | Mu | 10 Mbps | 20 MHz |
© 2020 by the authors. Licensee MDPI, Basel, Switzerland. This article is an open access article distributed under the terms and conditions of the Creative Commons Attribution (CC BY) license (http://creativecommons.org/licenses/by/4.0/).
Share and Cite
Khisa, S.; Moh, S. Medium Access Control Protocols for the Internet of Things Based on Unmanned Aerial Vehicles: A Comparative Survey. Sensors 2020, 20, 5586. https://doi.org/10.3390/s20195586
Khisa S, Moh S. Medium Access Control Protocols for the Internet of Things Based on Unmanned Aerial Vehicles: A Comparative Survey. Sensors. 2020; 20(19):5586. https://doi.org/10.3390/s20195586
Chicago/Turabian StyleKhisa, Shreya, and Sangman Moh. 2020. "Medium Access Control Protocols for the Internet of Things Based on Unmanned Aerial Vehicles: A Comparative Survey" Sensors 20, no. 19: 5586. https://doi.org/10.3390/s20195586
APA StyleKhisa, S., & Moh, S. (2020). Medium Access Control Protocols for the Internet of Things Based on Unmanned Aerial Vehicles: A Comparative Survey. Sensors, 20(19), 5586. https://doi.org/10.3390/s20195586






