Security in IoMT Communications: A Survey
Abstract
1. Introduction
1.1. Research Motivation
1.2. Contribution—Paper Structure
- We provide an exhaustive list of IoMT-specific communication protocols. In Section 3 we present a detailed classification of IoT communication protocols based on the three-layered approach (Section 3.1) and also based on the specific categories of IoMT devices (Section 3.2).
- Based on the above taxonomy, we present, for all the IoMT-specific communication protocols identified, their inherent security characteristics (Section 4.1), as well as their security weaknesses and relevant attacks, as derived by the literature (Section 4.2). In addition, based on the IoMT protocol taxonomy, we discuss mitigation controls for IoMT-specific communication protocols that take into consideration the limitations of the medical ecosystem (Section 4.3).
- Having in mind the current security status of the IoMT communication protocols described above, we discuss real case attack scenarios against medical devices (Section 5.1). In addition, we provide a comparative assessment of the various characteristics of the IoMT-specific communication protocols. Based on various use case scenarios, in Section 5.2 we provide a suitability assessment of the aforementioned protocols (whose protocol would be more suitable for the various types of medical devises, the underlying infrastructure and technologies used).
- Finally, in Section 6 we discuss open issues and challenges for IoMT protocol security.
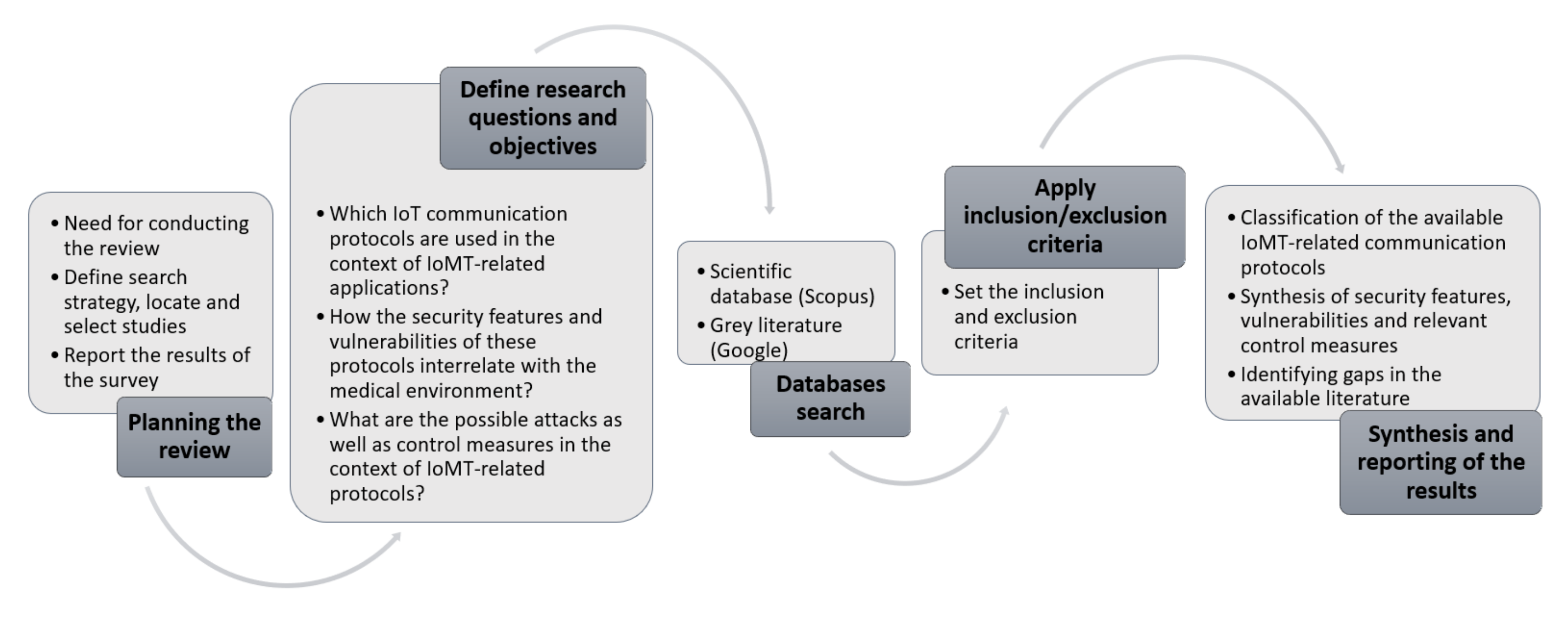
2. Research Methodology
- RQ1:
- Which IoT communication protocols are used in the context of IoMT?
- RQ2:
- What are the security features and possible vulnerabilities of these protocols and how do they interrelate with the medical environment?
- RQ3:
- What are the possible attacks as well as the likely available control measures in the context of IoMT-related communication protocols?
3. Classification of IoT Protocols Used in Medical Devices
3.1. Medical-Specific IoT Communication Protocols
3.1.1. Perception Layer
Infrared
RFID
NFC
Bluetooth/BLE
Z-Wave
UWB
3.1.2. Network Layer
WiFi
ZigBee
WIA-PA
ISA 100.11a
6LoWPAN
LoRaWAN
3.1.3. Application Layer
HL7
COAP
MQTT
HTTP
3.2. IoMT Communication Protocols in Medical Devices
3.2.1. Physiologic Monitoring Devices
Wearable Monitoring Medical Devices
Ingestible Monitoring Medical Devices
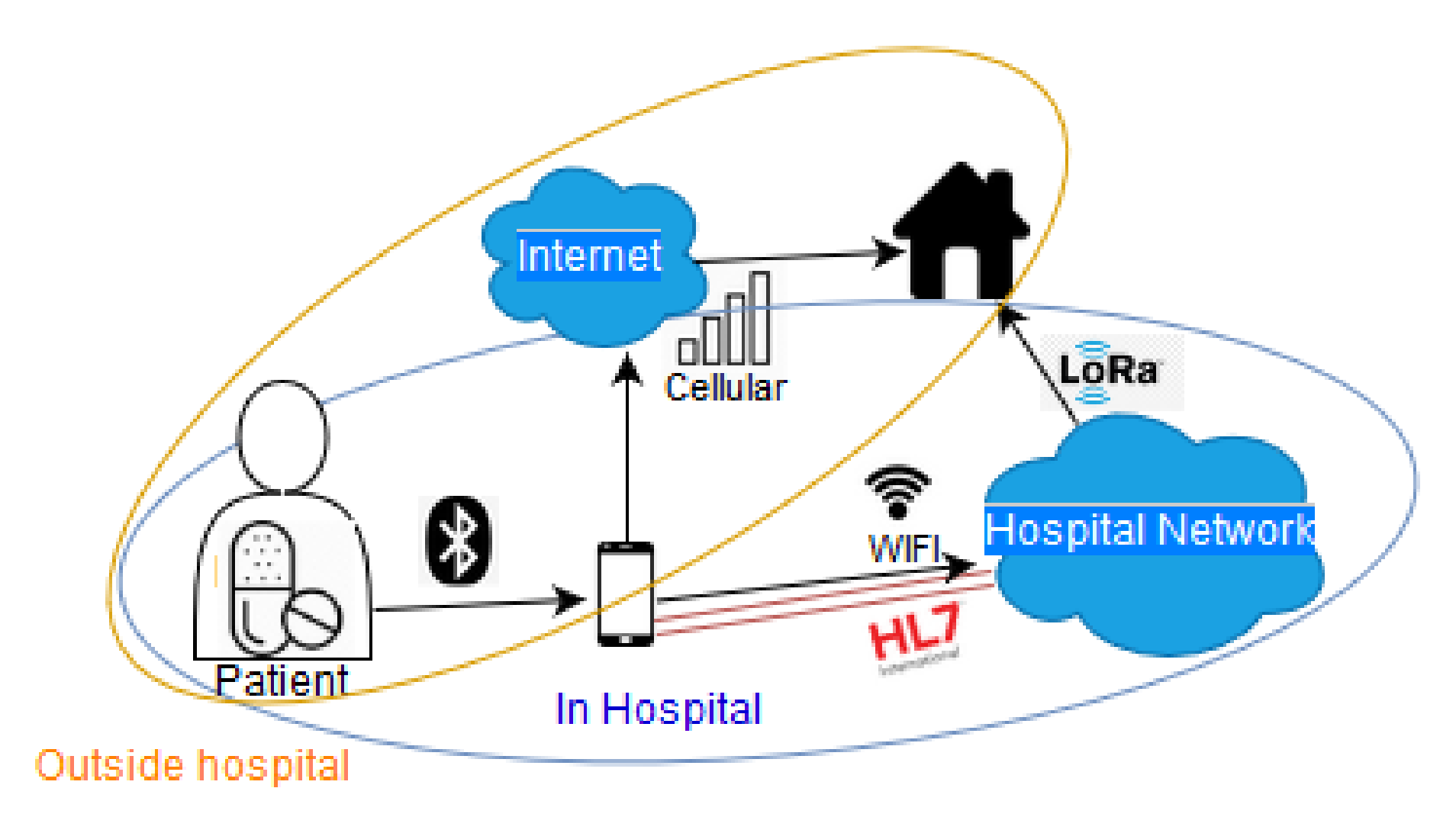
3.2.2. Medical Treatment Devices
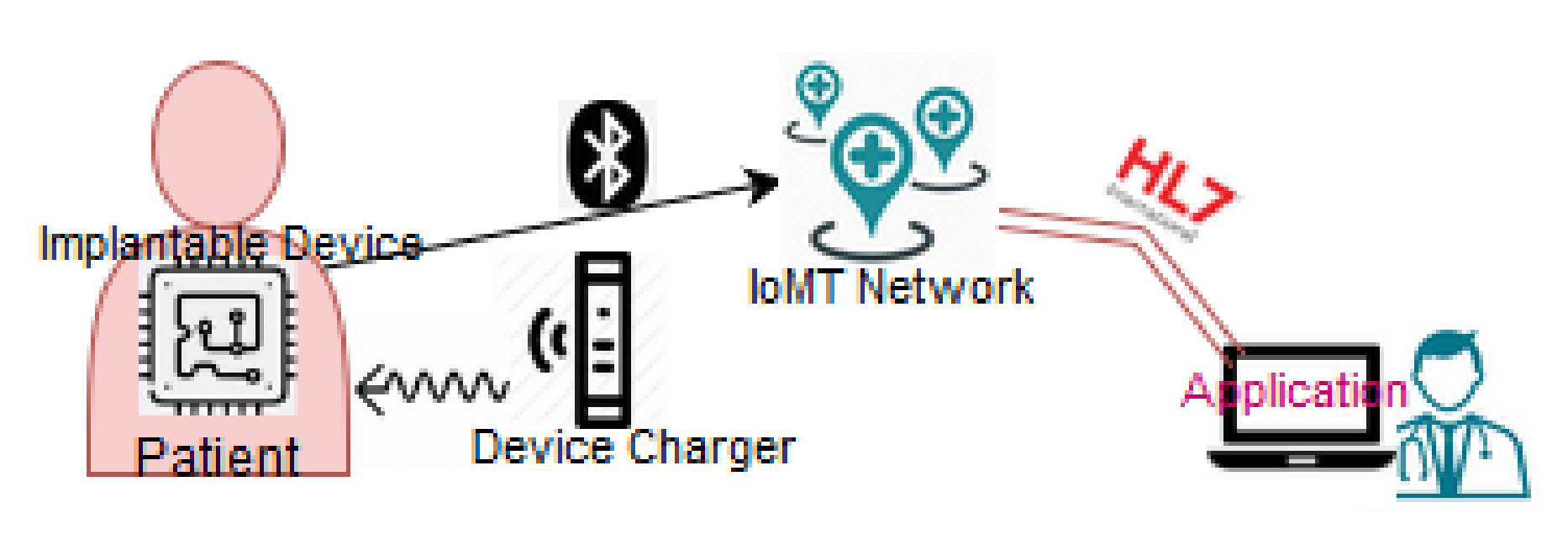
Implantable Medical Devices
Infusion Pumps
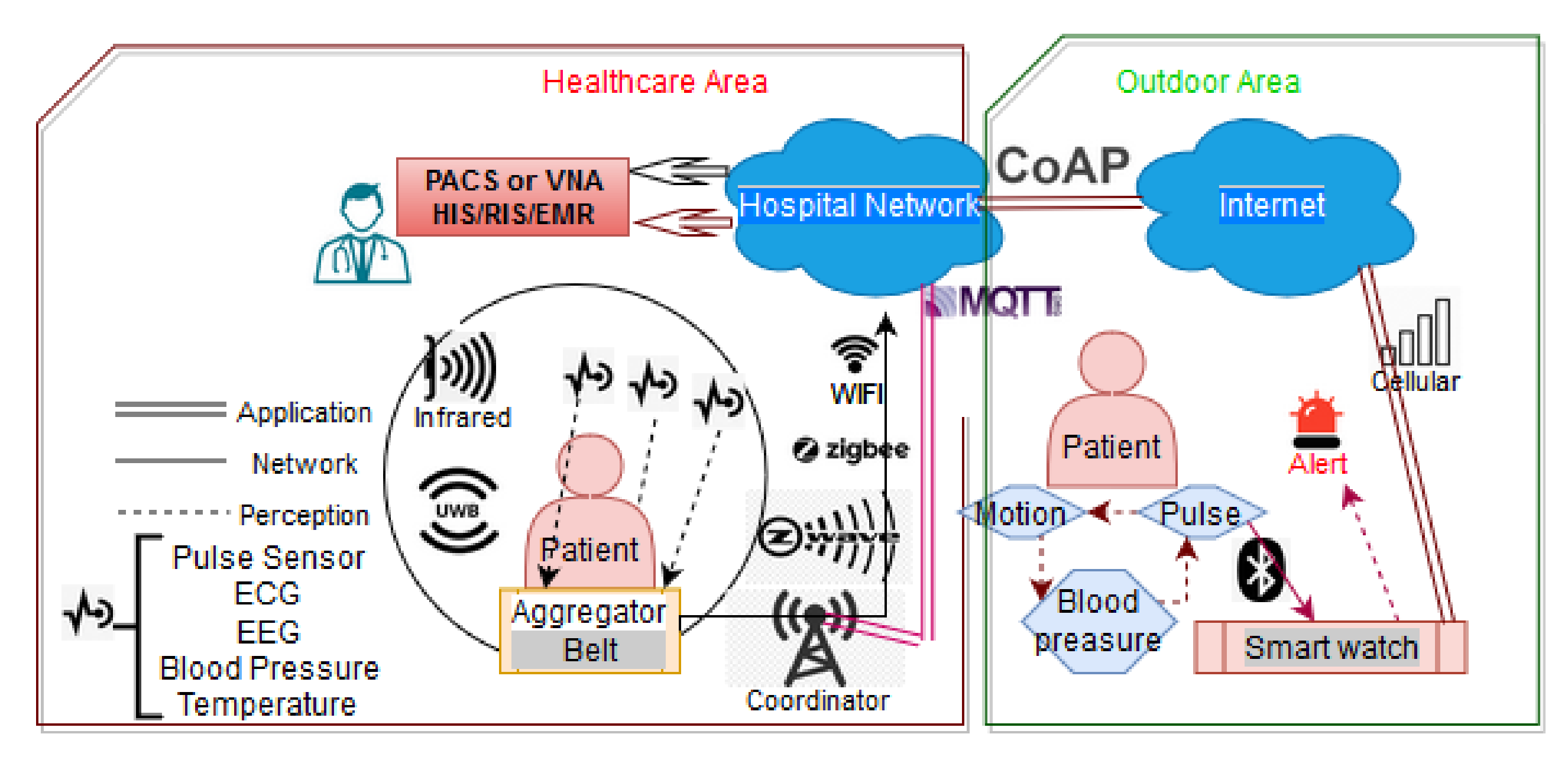
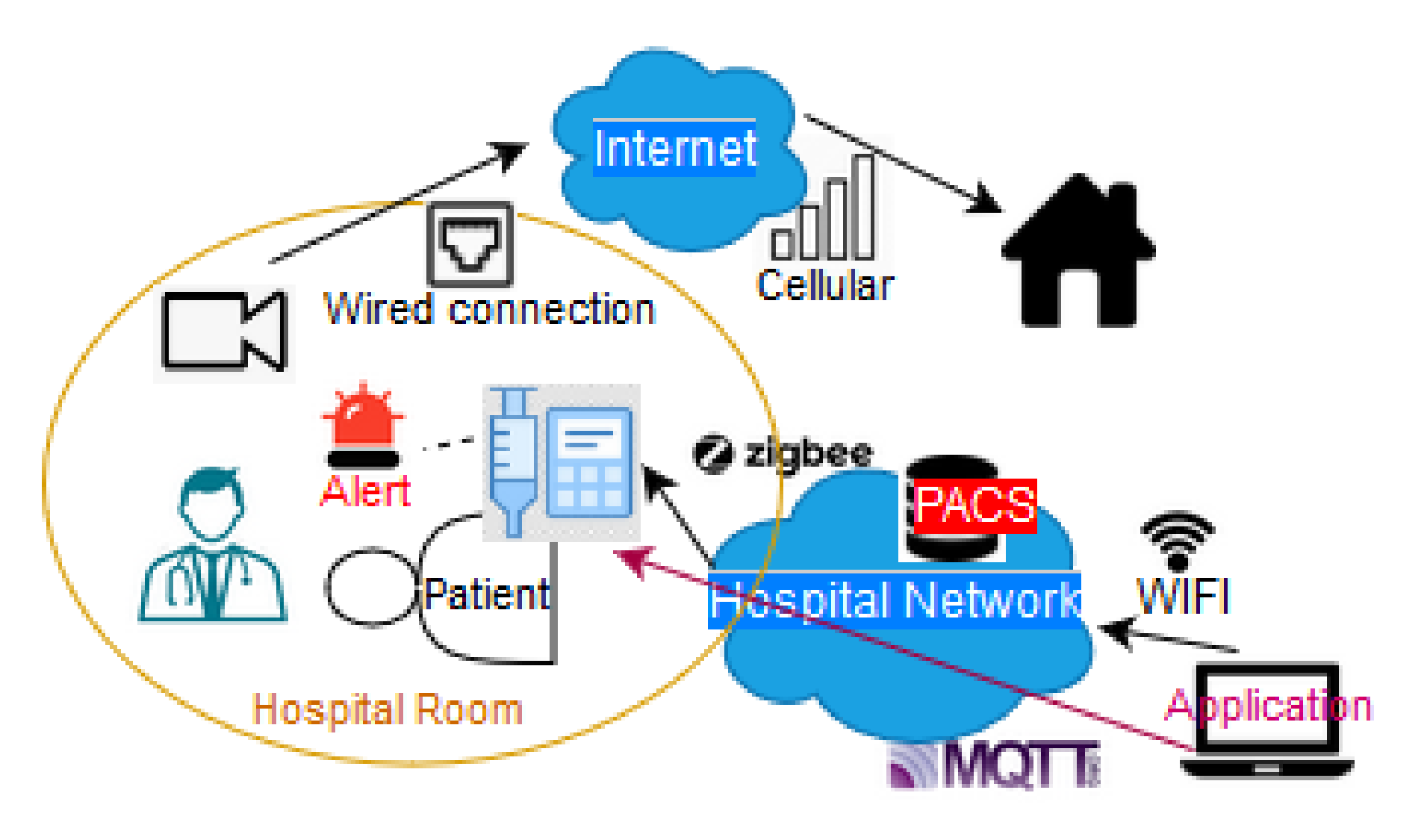
3.2.3. In-Hospital Connected Medical Devices
Institutional Medical Devices
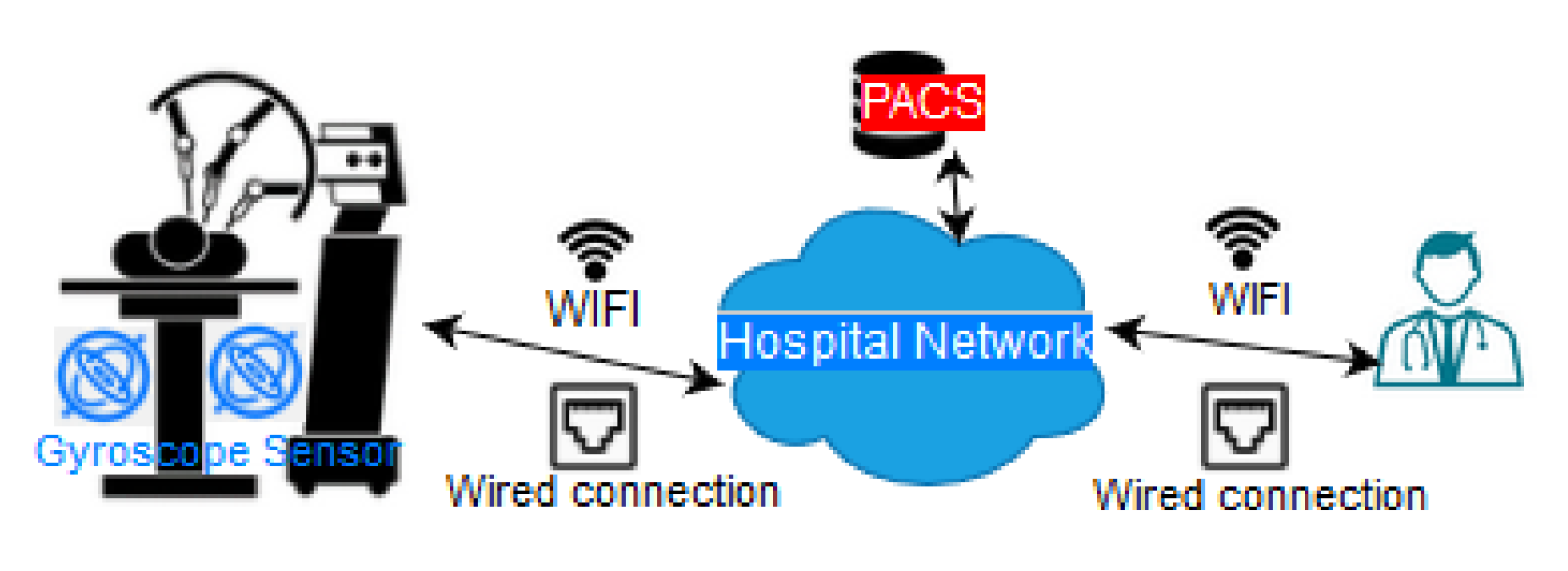
In-hospital Medical Robotics
3.2.4. Ambient Devices
3.2.5. Other ICT Devices
3.2.6. Monitoring and Handling
3.2.7. Coordinators
4. Security in IoMT Communication Protocols
4.1. IoMT Protocol Embedded Security Features
4.1.1. Perception Layer Security Issues
Infrared
RFID
NFC
Bluetooth/BLE
Z-Wave
UWB
4.1.2. Network Layer Security Issues
WiFi
ZigBee
WIA-PA
ISA 100.11a
6LowPAN
LoRaWAN
4.1.3. Application Layer Security Issues
HL7
HTTP
COAP
MQTT
4.2. IoMT Protocols Security Weaknesses and Attacks
4.2.1. Perception Layer Weaknesses and Attacks
Infrared
RFID
NFC
Bluetooth/BLE
Z-Wave
UWB
4.2.2. Network Layer Weaknesses and Attacks
WiFi
ZigBee
WIA-PA
- It does not provide any nonrepudiation security service as it lacks a public key encryption algorithm.
- WIA-PA can defend against most Sybil attacks. However, attackers can disguise as a proxy node and send join responses to devices trying to join the network during the nonencrypted join request phase. This makes the network vulnerable to Sybil-type attacks [153].
- Since the primary stage of secure authentication, the request is not encrypted. This security flaw can make the WIA-PA network vulnerable to DOS and Sybil attacks.
- The security management framework and its interface are not determined in detail.
ISA 100.11a
- Devices have limited storage space, computing capability, bandwidth and communication capability that may be exploited for attackers to launch DoS attacks.
- Devices have limited power supply that can be a target of power depletion attacks.
- The dynamic nature of its network environment can affect the network performance.
6LowPAN
LoRaWAN
4.2.3. Application Layer Weaknesses and Attacks
HL7
HTTP
- Waste Flood: An attacker tries to open a connection to a known HTTP port like 80 or 443 to send excessive binary data using the the http protocol.
- GET Flood: The attacker uses the HTTP GET request method on a large scale to overload servers and cause DoS on provided services.
- HTTP methods flood: Attacks use the HEAD and POST methods in conjunction with a GET flood attack to overload the server code.
- HTTP fuzzer and faulty fields: The main purpose of these attacks is to break code execution at the server by sending junk data or bad values inside specific HTTP protocol fields. For example the attacker can send a G(3)T request (instead of a GET request), or the attacker can send traffic to version HTTP 1(,)1 (instead of HTTP 1.1).
- Low and slow rate attack: In this case an attacker sends illegitimate HTTP traffic at a very low rate, in an effort to avoid being perceived by intrusion detection mechanisms [161]. In IoT, such attacks often try to deplete the energy of devices.
COAP
- Parsing attacks, where a node could execute malicious code.
- Cache attacks, where a proxy server can gain control of a part of the network.
- Amplification attacks, where an attacker can use end devices to convert a small packet into a larger packet and launch DoS attacks. COAP Servers can mitigate amplification attacks by using Blocking/Slicing modes.
- Cross-Protocol attacks, where packet translation from TCP to UDP is liable to attacks.
- Spoofing attacks.
MQTT
- Data Privacy: By default, MQTT does not provide any embedded data encryption mechanism. Whether the broker device (the master device that handles the traffic in the MQTT protocol) uses authentication mechanism or not, the intruder can still sniff the data when transmitted between the broker and a simple IoT device node.
- Authentication: If the attacker is in the same network with the publisher, he can sniff traffic and wait for a “Connect” packet from the publisher. Such packets can contain the username and password used to connect to the broker. Additionally, attackers can monitor for the “Keep Alive” packet. During the authentication process, there is a header in this packet which indicates how long the IoT device will remain connected to the broker. Therefore, when time expires, the device will resend the “Connect” packet to restart the connection.
- Data integrity: Intruders can modify data during transport between IoT nodes. They can use a compiled filter to modify the packages after the successful execution of ARP poisoning to reroute network connections to pass through the intruder’s computer (Man-In-the-Middle attack).
- Botnet Over MQTT: In this case, the attacker uses the Shodan search engine to find a device with the role of a broker. Then, he tries to transform it to a free broker server that connects himself to the victim’s device. In this scenario, the intruder uses the “unsecured” broker as an arbiter to create an IoT botnet.
4.3. Proposed Mitigations to Common Protocol Weaknesses
4.3.1. Perception Layer Mitigations
Infrared
RFID
NFC
- Denial of Service and phishing attacks.
- Issues due to the fixed unique ID and in-device security.
- Transactions over the peer link and during the relay of data transferred over the RF.
- Create a button to turn on the NFC device, with a user able to operate this device consciously.
- Only random NFC ID should be used for anti-conflict (without the use of ID-based systems).
- Allow the NFC admin to use the security features of a secure peer-to-peer NFC connection.
- Create a whitelist with authenticated and signed applications.
- Use of signed tags against phishing attacks.
Bluetooth/BLE
- Device settings and BLE version should be constantly kept updated.
- Update authentication credentials.
- Pair only with authenticated devices and avoid auto-pairing.
- Turn off Bluetooth modules when not necessary and set device to undiscoverable mode.
- Utilise strict pairing policies.
- Use of combination keys instead of link or unit keys to prevent MITM attacks.
- Use link encryption to prevent eavesdropping.
- Do not use multihope communication when encryption is not supported.
- Use of encrypting broadcast interceptions and use of security mode three implemented at the link layer with a 128 bit encryption key.
Z-Wave
- Hide the WLAN SSID: Since an attacker should be able to use a passive network scan tool to locate the WLAN, the administrator can hide the Service Set Identifier (SSID).
- WPA2 should be used instead of WEP. A WEP 128-bit key can be cracked in just few minutes with free available tools.
- MAC address filtering allows the WLAN administrator to choose a number of devices that are authentic and should be acceptable in the network. This procedure must be combined with WPA2 or AES-128 bit encryption. Otherwise, a spoofing attack can take place.
- Use a Reverse Proxy Server.
- Inspect log files mostly for prevention or direct intervention.
UWB
4.3.2. Network Layer Mitigations
WiFi
- WiFi AP access points and wireless routers support WPA/2 and WEP authentication and encryption to ensure data confidentiality on the wireless link.
- Access points implement MAC addresses filtering.
- Wireless network protocol filtering.
- Shield SSID broadcast information.
- Rational allocation of IP addresses.
ZigBee
WIA-PA
- For the selective forwarding attack, the WIA-PA network manager is responsible for observing the network device status reports.
- For the Interference attack, WIA-PA uses adaptive frequency hopping to effectively suppress sudden interference and eliminate the frequency selective fading. Some hopping mechanisms for the mitigation of the interference are the Adaptive frequency switch (AFS), Adaptive Frequency Hopping (AFH) and Timeslot hopping (TH).
- For the jamming attack WIA-PA uses AFH, but still there are node energy issues to be solved.
- For the tampering, WIA-PA application layer and the Data link sublayer use message integrity (MIC) to achieve data integrity.
ISA 100.11a
6LowPAN
LoRa
4.3.3. Application Layer Mitigations
HL7
HTTP
COAP
MQTT
5. Secure IoMT Communications: Threat Landscape and Protocol Comparison
5.1. IoMT Current Threat Landscape
- Attacks on wearable devices: Wearable devices usually collaborate with various devices such as mobile phones through a communication protocol (for example BLE) or with an aggregator (e.g., to collect medical data from various sensors). In this scenario, a smart watch works as a pulse oximeter connected directly with a mobile phone using BLE. The attacker could be in range to pair forcibly with the wearable device. When the user’s mobile phone collects data, the collected data may be accessed by the attacker’s smartphone. This particular attack exploits the vulnerability that the wearable device and smartphone do not authenticate each other at every connection instance. Consequently, the wearable device does not differentiate the real user’s smartphone from the attacker’s. In addition, as we previously presented (see Section 4.3.1), securely updating the authentication credentials, pairing only with authenticated devices and avoiding auto pairing [188,189], are very important measures for avoiding such threats.
- Attacks on infusion pumps: The infusion pump belongs to the treatment devices. It is operated by the patient either remotely or with physical access, thus a doctor or a nurse can handle the device in both ways. Below we present some real case scenarios of proven vulnerable infusion pumps that are used in healthcare areas and a threat that can easily happen. In 2015, the US Federal Drugs Administration (FDA) ceased the use of a specific infusion pump due to a safety breach. Security researchers (Billy Rios in 2014 and Jeremy Richards in 2015) discovered several vulnerabilities for a specific model of Hospira infusion pumps. These vulnerabilities allowed a hacker to tap into the pumps and change the original amount of medication set to dispense. FDA recommended that all hospitals in California and across the country should stop using the vulnerable medical devices [190,191,192]. As infusion pumps can also be handled with physical access, human mistake and physical tampering are also applicable threats. Strong identification and authentication are required to repulse the attacker from accessing the device. In Section 4.3, an RFID identification system and authorisation mechanisms are discussed.
- Attacks on Surgical Robotics: Realistic attack scenarios involve direct attacks against connected surgical robots, or indirect attacks against ambient devices, such as gyroscope sensors, that may affect a surgical operation. The nature of the surgery makes micrometre accuracy highly important. A direct attack to the surgical robot or an indirect attack against the sensors is possible. Perception layer attacks are the main threat for gyroscope sensors. An attacker can make replay attacks, by producing signals to confuse the original gyroscope signals. This attack can cause problems to the mapping of the human body. It may change the coordinates or produce error signals [193]. An attack like this requires close proximity of the attacker with the sensor. So the doctor has to operate from outside the surgery room and the room has to have a lack of monitoring and identification systems. In the case of a direct attack against the surgery robot, the following attacks are possible:
- -
- Modification of robot’s intent. During the transportation of the packets, the attacker may modify them. This action may cause minor malfunctions in the device like unusual robot movements or delays.
- -
- Manipulation of the robot’s intent. The intruder in this case cannot handle the medical device but may affect the feedback of the device like the images and coordinates.
- -
- Hijacking. The intruder takes over the surgical robot.
In the above scenarios the attackers may act in several ways. First, as network eavesdroppers who collect information. Then as active attackers who also inject small packets. In addition, attackers may act as network mediators (MITM attack) when the in-hospital device stops to communicate directly with the IoMT network. The Address Resolution Protocol (ARP) poisoning attack could be a method to alleviate direct attacks against surgical robotics [194]. - Attacks on monitoring devices: In this case the malicious actor may try to hack a camera or to affect an alarm system. Of course, if someone affects the alarm system of a treatment device and the alarm is switched off for some minutes (even and for seconds), a patient might receive a medicine overdose, resulting in severe consequences. Example of attack patterns involve DoS attacks and SQL injections. Securing from such attacks may require the implementation of advanced Intrusion Detection Systems (IDS) and strong authentication systems [195]. The protocols involved here are mainly from the application layer (COAP, MQTT). The need of early detection is considered highly important [196].
5.2. Network Protocol Comparison in IoMT Use Cases
5.2.1. Short-Range Low-Power Protocols
5.2.2. Long-Range Low-Power Protocols
5.3. Comparing IoMT Protocols in Medical Use Cases
5.3.1. Use-Case 1: Remote Monitoring and Portable Medical Devices (Ambient, Wearables, Ingestibles, Implantables)
5.3.2. Use-Case 2: Drug Delivery Devices—Infusion Pumps
5.3.3. Use-Case 3: Large Institutional Medical Devices
6. Challenges and Open Issues
6.1. Organisational Challenges
6.2. Data Privacy and Technical Issues
- Key management remains an open issue for medical networks, especially when it comes to wearable devices or ad-hoc connections. Current solutions may partially mitigate most issues but, still, there exists no unified approach able to tackle security concerns both for Wireless Sensor Network (WSN) and ad-hoc networks to the extent required by medical services.
- The technical heterogeneity of IoMT networks paves the way for numerous attacks. Currently, there exists no unified standardisation process or protocol able to mitigate the security issues introduced by such heterogeneous technologies. This is true for all the IoT networks, not only those implemented for the medical sector [207]. Even worse, medical networks have even more stringent rules and require stronger security than common IoT networks.
- Out of all the documented attacks and exploits, DoS remains the most frequent type of attack applicable in IoT networks. Since medical devices and services rely heavily on their availability, such attacks can be considered extremely dangerous for patients. Unavailability of medical devices (either through lack of connectivity or lack of power) can lead to elevated risks or even patient death, if certain circumstances are met.
- The existing protocols mostly inherit the pros and cons of current WSN standards like IEEE 802.15.x. Currently it is difficult to balance secure authentication mechanisms with power consumption. This is extremely important for the medical sector, since computation and communication overhead in the IoMT can result in power depletion; a state that can be proven fatal when it comes to medical services. Trust management and node management are also important when it comes to protecting the confidentiality of medical data. Numerous attacks on IoMT either use a man-in-the-middle node or exploit the trust relations to leak sensitive data.
- Data confidentiality is of utmost importance when it comes to protecting medical services. As such, the use of a horizontal rule when it comes to encrypting data in the IoMT is mandatory. This is something that should also be addressed at a legal level, where possible extensions or an explanatory circular on the General Data Protection Regulation (GDPR) can specifically be used to address encryption schemes for modern medical networks.
7. Conclusions
Author Contributions
Funding
Conflicts of Interest
References
- Gubbi, J.; Buyya, R.; Marusic, S.; Palaniswami, M. Internet of Things (IoT): A vision, architectural elements, and future directions. Future Gener. Comput. Syst. 2013, 29, 1645–1660. [Google Scholar] [CrossRef]
- Sundmaeker, H.; Guillemin, P.; Friess, P.; Woelfflé, S. Vision and challenges for realising the Internet of Things. In Cluster of European Research Projects on the Internet of Things; European Commission: Brussels, Belgium, 2010; Volume 3, pp. 34–36. [Google Scholar]
- Stellios, I.; Kotzanikolaou, P.; Psarakis, M.; Alcaraz, C.; Lopez, J. A survey of iot-enabled cyberattacks: Assessing attack paths to critical infrastructures and services. IEEE Commun. Surv. Tutor. 2018, 20, 3453–3495. [Google Scholar] [CrossRef]
- ENISA. Smart Hospitals. Security and Resilience for Smart Health Service and Infrastructures; Technical Report; ENISA: Heraklion, Greece, 2016; Available online: https://www.enisa.europa.eu/publications/cyber-security-and-resilience-for-smart-hospitals/at_download/fullReport (accessed on 25 August 2020).
- Ren, Z.; Liu, X.; Ye, R.; Zhang, T. Security and privacy on internet of things. In Proceedings of the 2017 7th IEEE International Conference on Electronics Information and Emergency Communication (ICEIEC), Shenzhen, China, 21–23 July 2017; pp. 140–144. [Google Scholar]
- Mosenia, A. Addressing Security and Privacy Challenges in Internet of Things. arXiv 2018, arXiv:cs.CR/1807.06724. [Google Scholar]
- Dang, L.M.; Piran, M.J.; Han, D.; Min, K.; Moon, H. A Survey on Internet of Things and Cloud Computing for Healthcare. Electronics 2019, 8, 768. [Google Scholar] [CrossRef]
- Al-Sarawi, S.; Anbar, M.; Alieyan, K.; Alzubaidi, M. Internet of Things (IoT) communication protocols: Review. In Proceedings of the 2017 8th International Conference on Information Technology (ICIT), Amman, Jordan, 17–18 May 2017; pp. 685–690. [Google Scholar] [CrossRef]
- Verma, A.; Prakash, S.; Srivastava, V.; Kumar, A.; Mukhopadhyay, S.C. Sensing, Controlling, and IoT Infrastructure in Smart Building: A Review. IEEE Sens. J. 2019, 19, 9036–9046. [Google Scholar] [CrossRef]
- Sain, M.; Kang, Y.J.; Lee, H.J. Survey on security in Internet of Things: State of the art and challenges. In Proceedings of the International Conference on Advanced Communication Technology, ICACT, Bongpyeong, Korea, 19–22 February 2017; pp. 699–704. [Google Scholar] [CrossRef]
- Santos, M.A.; Munoz, R.; Olivares, R.; Filho, P.P.; Ser, J.D.; de Albuquerque, V.H.C. Online heart monitoring systems on the internet of health things environments: A survey, a reference model and an outlook. Inf. Fusion 2020, 53, 222–239. [Google Scholar] [CrossRef]
- Javdani, H.; Kashanian, H. Internet of things in medical applications with a service-oriented and security approach: A survey. Health Technol. 2018, 8, 39–50. [Google Scholar] [CrossRef]
- Fotouhi, H.; Čaušević, A.; Vahabi, M.; Björkman, M. Interoperability in heterogeneous Low-Power Wireless Networks for Health Monitoring Systems. In Proceedings of the 2016 IEEE International Conference on Communications Workshops (ICC), Kuala Lumpur, Malaysia, 23–27 May 2016; pp. 393–398. [Google Scholar] [CrossRef]
- Denyer, D.; Tranfield, D. Producing a systematic review. In The Sage Handbook of Organizational Research Methods; Sage Publications Ltd.: Thousand Oaks, CA, USA, 2009; pp. 671–689. [Google Scholar]
- Altawy, R.; Youssef, A.M. Security Tradeoffs in Cyber Physical Systems: A Case Study Survey on Implantable Medical Devices. IEEE Access 2016, 4, 959–979. [Google Scholar] [CrossRef]
- Al-Fuqaha, A.; Guizani, M.; Mohammadi, M.; Aledhari, M.; Ayyash, M. Internet of Things: A Survey on Enabling Technologies, Protocols, and Applications. IEEE Commun. Surv. Tutor. 2015, 17, 2347–2376. [Google Scholar] [CrossRef]
- Deshmukh, S.; Sonavane, S.S. Security protocols for Internet of Things: A survey. In Proceedings of the 2017 International Conference on Nextgen Electronic Technologies: Silicon to Software (ICNETS2), Chennai, India, 23–25 March 2017; pp. 71–74. [Google Scholar] [CrossRef]
- Bagga, M.; Thakral, P.; Bagga, T. A study on IoT: Model, communication protocols, security hazards countermeasures. In Proceedings of the PDGC 2018—2018 5th International Conference on Parallel, Distributed and Grid Computing, Solan Himachal Pradesh, India, 20–22 December 2018; pp. 591–598. [Google Scholar] [CrossRef]
- IEEE 802 Working Group. IEEE Standard for Local and Metropolitan Area Networks–Part 15.4: Low-Rate Wireless Personal Area Networks (LR-WPANs). IEEE Std 802(2011):4-2011. Available online: https://doi.org/10.1109/ieeestd.2011.6012487 (accessed on 25 August 2020).
- Devadiga, K. IEEE 802.15.4 and the Internet of Things; Technical Report; Aalto University of Science: Espoo, Finland, 2011; Available online: https://wiki.aalto.fi/download/attachments/59704179/devadiga-802-15-4-and-the-iot.pdf?version=1 (accessed on 25 August 2020).
- Jain, R. Wireless Protocols for IoT Part I : Bluetooth and Bluetooth Smart; Washington University in Saint Louis: Saint Louis, MO, USA, 2016; Available online: https://www.cse.wustl.edu/~jain/cse574-16/ftp/j_11ble.pdf (accessed on 25 August 2020).
- Asadallahi, S.; Refai, H.H.; LoPresti, P.G. Performance comparison of CSMA/CA Advanced Infrared (AIr) and a new point-to-multipoint optical MAC protocol. In Proceedings of the 2012 8th International Wireless Communications and Mobile Computing Conference (IWCMC), Limassol, Cyprus, 27–31 August 2012; pp. 1149–1153. [Google Scholar]
- ISO/IEC 4335. Information Technology—Telecommunications and Information Exchange between Systems—High-Level Data Link Control (HDLC) Procedures—Elements of Procedures; ISO: Geneva, Switzerland, 1979; Available online: https://www.iso.org/standard/53459.html (accessed on 25 August 2020).
- Millar, I.; Beale, M.; Donoghue, B.J.; Lindstrom, K.W.; Williams, S. The IrDA standards for high-speed infrared communications. Hewlett-Packard J. 1998, 49, 1–20. [Google Scholar]
- Baker, B.C. Wireless Communication Using the IrDA Standard Protocol; Technical Report; Microchip Technology Inc.: Chandler, AZ, USA, 2003; Available online: https://ww1.microchip.com/downloads/en/DeviceDoc/adn006.pdf (accessed on 25 August 2020).
- Rozlosnik, A. Potential contribution of the Infrared Industry in the future of IoT/IIoT. In Proceedings of the 14th Quantitative InfraRed Thermography Conference, Berlin, Germany, 25–29 June 2018. [Google Scholar] [CrossRef]
- Amendola, S.; Lodato, R.; Manzari, S.; Occhiuzzi, C.; Marrocco, G. RFID Technology for IoT-Based Personal Healthcare in Smart Spaces. IEEE Internet Things J. 2014, 1, 144–152. [Google Scholar] [CrossRef]
- Pandian, A.; Senjyu, T.; Islam, S.; Wang, H. Proceeding of the International Conference on Computer Networks, Big Data and IoT (ICCBI-2018); Lecture Notes on Data Engineering and Communications Technologies; Springer International Publishing: Berlin/Heidelberg, Germany, 2019. [Google Scholar]
- GS1. EPC™ Radio-Frequency Identity Protocols Generation-2 UHF RFID Specification for RFID Air Interface; GS1: Brussels, Belgium, 2013; pp. 1–152. Available online: https://www.gs1.org/sites/default/files/docs/epc/Gen2_Protocol_Standard.pdf (accessed on 25 August 2020).
- Freudenthal, E.; Herrera, D.; Kautz, F.; Natividad, C.; Ogrey, A.; Sipla, J.; Sosa, A.; Betancourt, C.; Estevez, L. Suitability of NFC for Medical Device Communication and Power Delivery. In Proceedings of the 2007 IEEE Dallas Engineering in Medicine and Biology Workshop, Dallas, TX, USA, 11–12 November 2007; pp. 51–54. [Google Scholar] [CrossRef]
- ECMA International. Near Field Communication—Interface and Protocol (NFCIP-1); ECMA International: Geneva, Switzerland, 2013; p. 52. Available online: https://www.ecma-international.org/publications/files/ECMA-ST/ECMA-340.pdf (accessed on 25 August 2020).
- Choudhary, G.; Jain, A.K. Internet of Things: A survey on architecture, technologies, protocols and challenges. In Proceedings of the 2016 International Conference on Recent Advances and Innovations in Engineering (ICRAIE), Jaipur, India, 23–25 December 2016; pp. 1–8. [Google Scholar] [CrossRef]
- Cypress. PSoC® Creator Component Datasheet— Bluetooth Low Energy (BLE) 3.10 Description SIG adopted Profiles and Services Comprehensive APIs. 2015, pp. 408–943. Available online: https://www.cypress.com/file/232821/download (accessed on 25 August 2020).
- Renesas Electronics Corporation. Bluetooth® Low Energy Protocol Stack Introduction. 2017, pp. 1–722. Available online: https://www.renesas.com/kr/en/doc/products/mpumcu/doc/rl78/r01qs0014ej0100-bleintro.pdf (accessed on 25 August 2020).
- Silicon Labs. Software Design Specification. Z-Wave Transport-Encapsulation Command Class Specification. 2020. Available online: https://www.silabs.com/documents/login/miscellaneous/SDS13783-Z-Wave-Transport-Encapsulation-Command-Class-Specification.pdf (accessed on 25 August 2020).
- Ahmadi, H.; Arji, G.; Shahmoradi, L.; Safdari, R.; Nilashi, M.; Alizadeh, M. The application of internet of things in healthcare: A systematic literature review and classification. Univ. Access Inf. Soc. 2019, 18, 837–869. [Google Scholar] [CrossRef]
- Fotouhi, H.; Čaušević, A.; Lundqvist, K.; Björkman, M. Communication and Security in Health Monitoring Systems—A Review. In Proceedings of the I2016 IEEE 40th Annual Computer Software and Applications Conference (COMPSAC), Atlanta, GA, USA, 10–14 June 2016; pp. 545–554. [Google Scholar] [CrossRef]
- Committee-Electronic-Communications. Electronic Communications Committee (ECC) within the European Conference of Postal and Telecommunications Administrations (CEPT); Committee-Electronic-Communications: Brussels, Belgium, 2007; pp. 1–98. Available online: https://www.ecodocdb.dk/download/7185a0fb-48a8/ECCREP160.PDF (accessed on 25 August 2020).
- Fuentes, M.R.; Huq, N. Securing Connected Hospitals by Trend Micro. 2018. Available online: https://documents.trendmicro.com/assets/rpt/rpt-securing-connected-hospitals.pdf (accessed on 25 August 2020).
- Poongodi, T.; Rathee, A.; Indrakumari, R.; Suresh, P. IoT Sensing Capabilities: Sensor Deployment and Node Discovery, Wearable Sensors, Wireless Body Area Network (WBAN), Data Acquisition. In Principles of Internet of Things (IoT) Ecosystem: Insight Paradigm; Peng, S.L., Pal, S., Huang, L., Eds.; Springer International Publishing: Cham, Switzerland, 2020; pp. 127–151. [Google Scholar] [CrossRef]
- Salman, T.; Jain, R. A Survey of Protocols and Standards for Internet of Things. arXiv 2019, arXiv:1903.11549. [Google Scholar]
- Calcagnini, G.; Mattei, E.; Censi, F.; Triventi, M.; Lo Sterzo, R.; Marchetta, E.; Bartolini, P. Electromagnetic Compatibility of WiFi Technology with Life-Supporting Medical Devices. In Proceedings of the World Congress on Medical Physics and Biomedical Engineering, Munich, Germany, 7–12 September 2009; Springer: Berlin/Heidelberg, Germany, 2009; pp. 616–619. [Google Scholar]
- Feng, Z. Introduction of Wi-Fi Standardization and Interoperability Certification Test; CAICT: Beijing, China, 2017; Available online: https://www.itu.int/en/ITU-D/Regional-Presence/AsiaPacific/SiteAssets/Pages/Events/2017/Oct2017CIIOT/CIIOT/7.Session3-2%20Introduction%20of%20Wi-Fi%20Interoperability%20Certification%20Test-%E5%86%AF%E5%BF%97%E8%8A%B3V3.pdf (accessed on 25 August 2020).
- Tektronix Inc. Wi-Fi: Overview of the 802.11 Physical Layer and Transmitter Measurements; Tektronix Inc.: Beaverton, OR, USA, 2013; p. 44. Available online: https://www.cnrood.com/en/media/solutions/Wi-Fi_Overview_of_the_802.11_Physical_Layer.pdf (accessed on 25 August 2020).
- Hossain, M.; Islam, S.M.; Ali, F.; Kwak, K.S.; Hasan, R. An Internet of Things-based health prescription assistant and its security system design. Future Gener. Comput. Syst. 2018, 82, 422–439. [Google Scholar] [CrossRef]
- Uddin, M.A.; Stranieri, A.; Gondal, I.; Balasubramanian, V. Continuous Patient Monitoring with a Patient Centric Agent: A Block Architecture. IEEE Access 2018, 6, 32700–32726. [Google Scholar] [CrossRef]
- Yacchirema, D.C.; Palau, C.E.; Esteve, M. Enable IoT interoperability in ambient assisted living: Active and healthy aging scenarios. In Proceedings of the 2017 14th IEEE Annual Consumer Communications & Networking Conference (CCNC), Las Vegas, NV, USA, 8–11 January 2017; pp. 53–58. [Google Scholar] [CrossRef]
- Zigbee-Alliance. ZigBee wireless sensor applications for health, wellness and fitness. White Paper. 2009. Available online: https://www.science.smith.edu/~jcardell/Courses/EGR328/Readings/Zigbee&HealthCare.pdf (accessed on 25 August 2020).
- Zigbee Alliance Inc. ZigBee Specification; Zigbee Alliance Inc.: Davis, CA, USA, 2014; pp. 1–378. Available online: https://zigbeealliance.org/wp-content/uploads/2019/11/docs-05-3474-21-0csg-zigbee-specification.pdf (accessed on 25 August 2020).
- Tang, Z.; Cheng, M.; Zeng, P.; Wang, H. Real-time communication in WIA-PA industrial wireless networks. In Proceedings of the 2010 3rd International Conference on Computer Science and Information Technology, Chengdu, China, 9–11 July 2010; Volume 2, pp. 600–605. [Google Scholar]
- Zheng, M.; Liang, W.; Yu, H.; Xiao, Y. Performance Analysis of the Industrial Wireless Networks Standard: WIA-PA. Mob. Netw. Appl. 2017, 22, 139–150. [Google Scholar] [CrossRef]
- Su, C.R.; Hajiyev, J.; Fu, C.J.; Kao, K.C.; Chang, C.H.; Chang, C.T. A novel framework for a remote patient monitoring (RPM) system with abnormality detection. Health Policy Technol. 2019, 8, 157–170. [Google Scholar] [CrossRef]
- Ristaino, A. ISA100. 11a Approved as IEC 62734 by ISA Wireless Compliance Intitute October 2014. Available online: https://isa100wci.org/en-US/Documents/Presentations/2014-Oct-15-ISA100-Wireless-IEC62734-Approval.aspx (accessed on 25 August 2020).
- Nixon, M. A Comparison of WirelessHART™ and ISA100.11a. In Emerson White Paper; Emerson Process Management: St. Louis, MO, USA, 2012; pp. 1–36. Available online: https://www.emerson.com/documents/automation/white-paper-a-comparison-of-wirelesshart-isa100-11a-en-42598.pdf (accessed on 25 August 2020).
- Yeole, A.; Kalbande, D.; Sharma, A. Security of 6LoWPAN IoT Networks in Hospitals for Medical Data Exchange. Procedia Comput. Sci. 2019, 152, 212–221. [Google Scholar] [CrossRef]
- Verma, A.; Ranga, V. Security of RPL Based 6LoWPAN Networks in the Internet of Things: A Review. IEEE Sens. J. 2020, 20, 5666–5690. [Google Scholar] [CrossRef]
- Olsson, J. 6LoWPAN Demystified; Texas Instruments: Dallas, TX, USA, 2014; Volume 13, Available online: https://www.ti.com/lit/wp/swry013/swry013.pdf?ts=1598291385949&ref_url=https%253A%252F%252Fwww.google.com%252F (accessed on 25 August 2020).
- i-Scoop. LoRa and LoRaWAN: The Technologies, Ecosystems, Use Cases and Market by i-Scoop. Available online: https://www.i-scoop.eu/internet-of-things-guide/lpwan/iot-network-lora-lorawan/ (accessed on 25 August 2020).
- N.SORNIN (Semtech). LoRaWAN 1.1 Specification; LoRa Alliance Technical Committee: Beaverton, OR, USA, 2017; p. 101. Available online: https://lora-alliance.org/sites/default/files/2018-04/lorawantm_specification_-v1.1.pdf (accessed on 25 August 2020).
- Mdhaffar, A.; Chaari, T.; Larbi, K.; Jmaiel, M.; Freisleben, B. IoT-based health monitoring via LoRaWAN. In Proceedings of the IEEE EUROCON 2017—17th International Conference on Smart Technologies, Ohrid, North Macedonia, 6–8 July 2017; pp. 519–524. [Google Scholar]
- Catherwood, P.A.; Steele, D.; Little, M.; Mccomb, S.; Mclaughlin, J. A Community-Based IoT Personalized Wireless Healthcare Solution Trial. IEEE J. Transl. Eng. Health Med. 2018, 6, 1–13. [Google Scholar] [CrossRef]
- Ring, E.; Ammer, K. Infrared thermal imaging in medicine. Physiol. Meas. 2012, 33, R33–R46. [Google Scholar] [CrossRef] [PubMed]
- Alsubaei, F.; Abuhussein, A.; Shiva, S. Security and Privacy in the Internet of Medical Things: Taxonomy and Risk Assessment. In Proceedings of the 2017 IEEE 42nd Conference on Local Computer Networks Workshops LCN Workshops, Singapore, 9 October 2017; pp. 112–120. [Google Scholar] [CrossRef]
- Rathnayake, R.M.; Karunarathne, M.S.; Nafi, N.S.; Gregory, M.A. Cloud Enabled Solution for Privacy Concerns in Internet of Medical Things. In Proceedings of the 2018 28th International Telecommunication Networks and Applications Conference ITNAC, Sydney, NSW, Australia, 21–23 November 2018; pp. 1–4. [Google Scholar] [CrossRef]
- Zanjal, S.V.; Talmale, G.R. Medicine Reminder and Monitoring System for Secure Health Using IOT. Phys. Procedia 2016, 78, 471–476. [Google Scholar] [CrossRef]
- Pérez, M.M.; Dafonte, C.; Gómez, Á. Traceability in patient healthcare through the integration of RFID technology in an ICU in a hospital. Sensors 2018, 18, 1627. [Google Scholar] [CrossRef] [PubMed]
- Bansal, M.; Gandhi, B. IoT & Big Data in Smart Healthcare (ECG Monitoring). In Proceedings of the 2019 International Conference on Machine Learning, Big Data, Cloud and Parallel Computing (COMITCon), Faridabad, India, 14–16 February 2019; pp. 390–396. [Google Scholar] [CrossRef]
- Santamaria, A.F.; De Rango, F.; Serianni, A.; Raimondo, P. A real IoT device deployment for e-Health applications under lightweight communication protocols, activity classifier and edge data filtering. Comput. Commun. 2018, 128, 60–73. [Google Scholar] [CrossRef]
- Gia, T.N.; Jiang, M.; Rahmani, A.M.; Westerlund, T.; Liljeberg, P.; Tenhunen, H. Fog computing in healthcare Internet of Things: A case study on ECG feature extraction. In Proceedings of the 2015 IEEE International Conference on Computer and Information Technology, Ubiquitous Computing and Communications, Dependable, Autonomic and Secure Computing, Pervasive Intelligence and Computing, Liverpool, UK, 26–28 October 2015; pp. 356–363. [Google Scholar] [CrossRef]
- Pasha, M.; Shah, S.M.W. Framework for E-Health Systems in IoT-Based Environments. Wirel. Commun. Mob. Comput. 2018, 2018. [Google Scholar] [CrossRef]
- Pattnaik, P.; Kumar, R.; Pal, S. Internet of Things and Analytics for Agriculture; Springer: Berlin/Heidelberg, Germany, 2020; Volume 2. [Google Scholar] [CrossRef]
- Taştan, M. IoT Based Wearable Smart Health Monitoring System. Celal Bayar Üniversitesi Fen Bilim. Derg. 2018, 343–350. [Google Scholar] [CrossRef]
- Suciu, G.; Suciu, V.; Martian, A.; Craciunescu, R.; Vulpe, A.; Marcu, I.; Halunga, S.; Fratu, O. Big Data, Internet of Things and Cloud Convergence – An Architecture for Secure E-Health Applications. J. Med. Syst. 2015, 39. [Google Scholar] [CrossRef]
- Nguyen, T.M.C.; Hoang, D.B.; Dat Dang, T. A software-defined model for IoT clusters: Enabling applications on demand. In Proceedings of the 2018 International Conference on Information Networking (ICOIN), Chiang Mai, Thailand, 10–12 January 2018; pp. 776–781. [Google Scholar] [CrossRef]
- Islam, S.M.; Kwak, D.; Kabir, M.H.; Hossain, M.; Kwak, K.S. The internet of things for health care: A comprehensive survey. IEEE Access 2015, 3, 678–708. [Google Scholar] [CrossRef]
- Arrieta, S.S.; Parra, O.J.S.; Chaves, R.M.P. Design of PHD Solution Based on HL7 and IoT. In Future Data and Security Engineering; Dang, T.K., Küng, J., Wagner, R., Thoai, N., Takizawa, M., Eds.; Springer International Publishing: Cham, Switzerland, 2018; pp. 405–409. [Google Scholar]
- Hong, J.; Morris, P.; Seo, J. Interconnected Personal Health Record Ecosystem Using IoT Cloud Platform and HL7 FHIR. In Proceedings of the 2017 IEEE International Conference on Healthcare Informatics (ICHI), Park City, UT, USA, 23–26 August 2017; pp. 362–367. [Google Scholar]
- Lubamba, C.; Bagula, A. Cyber-healthcare cloud computing interoperability using the HL7-CDA standard. In Proceedings of the 2017 IEEE Symposium on Computers and Communications (ISCC), Heraklion, Greece, 3–6 July 2017; pp. 105–110. [Google Scholar]
- Dolin, R.H.; Alschuler, L.; Boyer, S.; Beebe, C.; Behlen, F.M.; Biron, P.V.; Shabo, A. HL7 clinical document architecture, release 2. J. Am. Med. Inform. Assoc. 2006, 13, 30–39. [Google Scholar] [CrossRef]
- Gündoğan, C.; Kietzmann, P.; Lenders, M.; Petersen, H.; Schmidt, T.C.; Wählisch, M. NDN, COAP, and MQTT: A comparative measurement study in the IoT. In Proceedings of the 5th ACM Conference on Information-Centric Networking, Boston, MA, USA, September 2018; pp. 159–171. [Google Scholar] [CrossRef]
- Nastase, L. Security in the Internet of Things: A Survey on Application Layer Protocols. In Proceedings of the 2017 21st International Conference on Control Systems and Computer, CSCS 2017, Bucharest, Romania, 29–31 May 2017; pp. 659–666. [Google Scholar] [CrossRef]
- Karagiannis, V.; Chatzimisios, P.; Vazquez-gallego, F.; Alonso-zarate, J. Sensus: Smart Water Network. Trans. IoT Cloud Comput. 2016, 3, 1–10. [Google Scholar] [CrossRef]
- Swamy, S.N.; Jadhav, D.; Kulkarni, N. Security threats in the application layer in IOT applications. In Proceedings of the 2017 International Conference on I-SMAC (IoT in Social, Mobile, Analytics and Cloud) (I-SMAC), Palladam, India, 10–11 February 2017; pp. 477–480. [Google Scholar] [CrossRef]
- Dey, T.; Jaiswal, S.; Sunderkrishnan, S.; Katre, N. HealthSense: A medical use case of Internet of Things and blockchain. In Proceedings of the 2017 International Conference on Intelligent Sustainable Systems (ICISS), Palladam, India, 7–8 December 2017; pp. 486–491. [Google Scholar]
- Sicari, S.; Rizzardi, A.; Coen-Porisini, A. How to evaluate an Internet of Things system: Models, case studies, and real developments. Software Pract. Exp. 2019, 49, 1663–1685. [Google Scholar] [CrossRef]
- Mendez, F.; Jabba, D. IoT Connected Health Architecture for Heart Rate Monitoring based on Interoperability Standards. In Proceedings of the 2018 IEEE 2nd Colombian Conference on Robotics and Automation, CCRA 2018, Barranquilla, Colombia, 1–3 November 2018; pp. 1–6. [Google Scholar] [CrossRef]
- Li, W.E.; Jung, C.; Park, J. IoT healthcare communication system for IEEE 11073 PHD and IHE PCD-01 integration using CoAP. KSII Trans. Internet Inf. Syst. 2018, 12, 1396–1414. [Google Scholar] [CrossRef]
- Catarinucci, L.; de Donno, D.; Mainetti, L.; Palano, L.; Patrono, L.; Stefanizzi, M.L.; Tarricone, L. An IoT-Aware Architecture for Smart Healthcare Systems. IEEE Internet Things J. 2015, 2, 515–526. [Google Scholar] [CrossRef]
- Petrellis, N.; Birbas, M.; Gioulekas, F. On the design of low-cost IoT sensor node for e-health environment. Electronics 2019, 8, 178. [Google Scholar] [CrossRef]
- Rodgers, M.M.; Pai, V.M.; Conroy, R.S. Recent Advances in Wearable Sensors for Health Monitoring. IEEE Sens. J. 2015, 15, 3119–3126. [Google Scholar] [CrossRef]
- Haghi, M.; Thurow, K.; Stoll, R. Wearable devices in medical internet of things: Scientific research and commercially available devices. Healthc. Inform. Res. 2017, 23, 4–15. [Google Scholar] [CrossRef]
- Nguyen, K.T.; Laurent, M.; Oualha, N. Survey on secure communication protocols for the Internet of Things. Ad Hoc Netw. 2015, 32, 17–31. [Google Scholar] [CrossRef]
- Scarpato, N.; Pieroni, A.; Di Nunzio, L.; Fallucchi, F. E-health-IoT universe: A review. Int. J. Adv. Sci. Eng. Inf. Technol. 2017, 7, 2328–2336. [Google Scholar] [CrossRef]
- Myroniv, B.; Wu, C.W.; Ren, Y.; Christian, A.; Bajo, E.; Tseng, Y.C. Analyzing User Emotions via Physiology Signals. Ubiquitous Int. 2017, 1, 11–25. [Google Scholar]
- Neethirajan, S. Recent advances in wearable sensors for animal health management. Sens. Bio-Sens. Res. 2017, 12, 15–29. [Google Scholar] [CrossRef]
- Rotariu, C.; Manta, V. Wireless system for remote monitoring of oxygen saturation and heart rate. In Proceedings of the 2012 Federated Conference on Computer Science and Information Systems (FedCSIS), Wroclaw, Poland, 9–12 September 2012; IEEE: Piscataway, NJ, USA, 2012; pp. 193–196. [Google Scholar]
- Adiputra, R.; Hadiyoso, S.; Hariyani, Y. Internet of Things: Low Cost and Wearable SpO2 Device for Health Monitoring. Int. J. Electr. Comput. Eng. (IJECE) 2018, 8, 939. [Google Scholar] [CrossRef]
- Hussain, S.R.; Mehnaz, S.; Nirjon, S.; Bertino, E. Secure Seamless Bluetooth Low Energy Connection Migration for Unmodified IoT Devices. IEEE Trans. Mob. Comput. 2018, 17, 927–944. [Google Scholar] [CrossRef]
- Stachel, J.R.; Sejdić, E.; Ogirala, A.; Mickle, M.H. The impact of the internet of Things on implanted medical devices including pacemakers, and ICDs. In Proceedings of the 2013 IEEE International Instrumentation and Measurement Technology Conference (I2MTC), Minneapolis, MN, USA, 6–9 May 2013; pp. 839–844. [Google Scholar]
- De Lima, J.A. A compact and power-efficient CMOS battery charger for implantable devices. In Proceedings of the 2014 27th Symposium on Integrated Circuits and Systems Design (SBCCI), Aracaju, Brazil, 1–5 September 2014; pp. 1–6. [Google Scholar]
- Hached, S.; Trigui, A.; El Khalloufi, I.; Sawan, M.; Loutochin, O.; Corcos, J. A Bluetooth-based Low-Energy Qi-compliant battery charger for implantable medical devices. In Proceedings of the 2014 IEEE International Symposium on Bioelectronics and Bioinformatics (IEEE ISBB 2014), Chung Li, Taiwan, 11–14 April 2014; pp. 1–4. [Google Scholar]
- Larson, B.R.; Zhang, Y.; Barrett, S.C.; Hatcliff, J.; Jones, P.L. Enabling Safe Interoperation by Medical Device Virtual Integration. IEEE Des. Test 2015, 32, 74–88. [Google Scholar] [CrossRef]
- Fiaidhi, J.; Fiaidhi, J.; Mohammed, S. Security and Vulnerability of Extreme Automation Systems: The IoMT and IoA Case Studies. IT Prof. 2019, 21, 48–55. [Google Scholar] [CrossRef]
- Belkhouja, T.; Du, X.; Mohamed, A.; Al-Ali, A.K.; Guizani, M. New plain-text authentication secure scheme for implantable medical devices with remote control. In Proceedings of the GLOBECOM 2017 IEEE Global Communications Conference, Singapore, 4–8 December 2017; pp. 1–5. [Google Scholar] [CrossRef]
- Gatouillat, A.; Badr, Y.; Massot, B.; Sejdic, E. Internet of Medical Things: A Review of Recent Contributions Dealing with Cyber-Physical Systems in Medicine. IEEE Internet Things J. 2018, 5, 3810–3822. [Google Scholar] [CrossRef]
- Limaye, A.; Adegbija, T. A Workload Characterization for the Internet of Medical Things (IoMT). In Proceedings of the 2017 IEEE Computer Society Annual Symposium on VLSI (ISVLSI), Bochum, Germany, 3–5 July 2017; pp. 302–307. [Google Scholar]
- Vossberg, M.; Tolxdorff, T.; Krefting, D. DICOM Image Communication in Globus-Based Medical Grids. IEEE Trans. Inf. Technol. Biomed. 2008, 12, 145–153. [Google Scholar] [CrossRef]
- Nabha, R.A.; Sbeyti, H. Exploiting Vulnerabilities Of MRI Scanner Machine: Lebanon Case Study. In Proceedings of the 2020 8th International Symposium on Digital Forensics and Security (ISDFS), Beirut, Lebanon, 1–2 June 2020; pp. 1–7. [Google Scholar]
- Anwer, H.; Azam, F.; Anwar, M.W.; Rashid, M. A Model-Driven Approach for Load-Balanced MQTT Protocol in Internet of Things (IoT). In Complex, Intelligent, and Software Intensive Systems; Barolli, L., Hussain, F.K., Ikeda, M., Eds.; Springer: Berlin/Heidelberg, Germany, 2020; pp. 368–378. [Google Scholar]
- Patel, A.R.; Patel, R.S.; Singh, N.M.; Kazi, F.S. Vitality of Robotics in Healthcare Industry: An Internet of Things (IoT) Perspective. In Internet of Things and Big Data Technologies for Next Generation Healthcare; Bhatt, C., Dey, N., Ashour, A.S., Eds.; Springer: Berlin/Heidelberg, Germany, 2017; pp. 91–109. [Google Scholar] [CrossRef]
- Patel, A.R.; Azadi, S.; Babaee, M.H.; Mollaei, N.; Patel, K.L.; Mehta, D.R. Significance of Robotics in Manufacturing, Energy, Goods and Transport Sector in Internet of Things (IoT) Paradigm. In Proceedings of the 2018 Fourth International Conference on Computing Communication Control and Automation (ICCUBEA), Pune, India, 16–18 August 2018; pp. 1–4. [Google Scholar]
- Lee, J.H.; Seo, D.W. Development of ECG Monitoring System and Implantable Device with Wireless Charging. Micromachines 2019, 10, 38. [Google Scholar] [CrossRef]
- Sonune, S.; Kalbande, D.; Yeole, A.; Oak, S. Issues in IoT healthcare platforms: A critical study and review. In Proceedings of the 2017 International Conference on Intelligent Computing and Control (I2C2), Coimbatore, India, 23–24 June 2017; pp. 1–5. [Google Scholar] [CrossRef]
- Rathore, M.M.; Paul, A.; Ahmad, A.; Anisetti, M.; Jeon, G. Hadoop-Based Intelligent Care System (HICS). ACM Trans. Internet Technol. 2017, 18, 1–24. [Google Scholar] [CrossRef]
- Borgohain, T.; Kumar, U.; Sanyal, S. Survey of security and privacy issues of internet of things. arXiv 2015, arXiv:1501.02211. [Google Scholar]
- Mendez, D.M.; Papapanagiotou, I.; Yang, B. Internet of things: Survey on security and privacy. arXiv 2017, arXiv:1707.01879. [Google Scholar]
- Fan, X.; Gong, G. Securing NFC with Elliptic Curve Cryptography-Challenges and Solutions. RFIDSec Asia 2013, 11, 97–106. [Google Scholar]
- SIG, J.B. Bluetooth Specification, v. 3.0. IEEE Spectr. 2009. Available online: file:///C:/Users/dkout/AppData/Local/Temp/WhitePaper_Bluetooth_V01_0910_low.pdf (accessed on 25 August 2020).
- Badenhop, C.W.; Graham, S.R.; Ramsey, B.W.; Mullins, B.E.; Mailloux, L.O. The Z-Wave routing protocol and its security implications. Comput. Secur. 2017, 68, 112–129. [Google Scholar] [CrossRef]
- Flury, M.; Poturalski, M.; Papadimitratos, P.; Hubaux, J.P.; Le Boudec, J.Y. Effectiveness of Distance-Decreasing Attacks Against Impulse Radio Ranging. In Proceedings of the 3rd ACM Conference on Wireless Network Security, WiSec’10, Hoboken, NJ, USA, 22–24 March 2010. [Google Scholar] [CrossRef]
- Zillner, T. ZigBee Exploited. The Good, the Bad and the Ugly; Technical Report; Cognosec©2015: Vienna, Austria, August 2015; Available online: https://media.kasperskycontenthub.com/wp-content/uploads/sites/43/2015/11/20081735/us-15-Zillner-ZigBee-Exploited-The-Good-The-Bad-And-The-Ugly-wp.pdf (accessed on 25 August 2020).
- Zigbee Alliance Inc. ZigBee 3.0 Stack User Guide JN-UG-3113; Technical Report; Zigbee Alliance Inc.: Davis, CA, USA, 11 September 2018; Available online: https://www.nxp.com/docs/en/user-guide/JN-UG-3113.pdf (accessed on 25 August 2020).
- Fan, X.; Susan, F.; Long, W.; Li, S.; Specification, Z.; Gislason, D.; Hillman, M.; Fan, X.; Susan, F.; Long, W.; et al. Security Analysis of ZigBee. MWR InfoSecurity 2017, 1–18. [Google Scholar] [CrossRef]
- Fan, X.; Susan, F.; Long, W.; Li, S. Security Analysis of Zigbee; Computer Network Security Class, Massachusetts Institute Technological: Cambridge, MA, USA, 2017; Available online: https://courses.csail.mit.edu/6.857/2017/project/17.pdf (accessed on 25 August 2020).
- Wang, X.; Cui, L.; Guo, Z. Advanced Technologies in Ad Hoc and Sensor Networks, Proceedings of the 7th China Conference on Wireless Sensor Networks; Springer: Berlin/Heidelberg, Germany, 2014; Volume 295. [Google Scholar] [CrossRef]
- Kitano, K.; Yamamoto, S. Strong Security Measures Implemented in ISA100.11a Wireless System. Yokogawa Technical Report English Edition. 2014, Volume 57, pp. 47–50. Available online: https://web-material3.yokogawa.com/rd-te-r05702-005.pdf (accessed on 25 August 2020).
- Hennebert, C.; Santos, J.D. Security protocols and privacy issues into 6LoWPAN stack: A synthesis. IEEE Internet Things J. 2014, 1, 384–398. [Google Scholar] [CrossRef]
- Kaufman, C.; Hoffman, P.; Nir, Y.; Eronen, P.; Kivinen, T. Internet Key Exchange Protocol Version 2 (IKEv2); Technical Report; RFC 5996; Internet Engineering Task Force (IETF); October 2014. by the Internet Engineering Steering Group (IESG). Available online: https://tools.ietf.org/html/rfc7296 (accessed on 25 August 2020).
- Gemalto, A.; Semtech. LoRaWAN™ Security A White Paper Prepared for the LoRa Alliance. Available online: https://lora-alliance.org/sites/default/files/2019-05/lorawan_security_whitepaper.pdf (accessed on 25 August 2020).
- Yegin, A.; Kramp, T.; Dufour, P.; Gupta, R.; Soss, R.; Hersent, O.; Hunt, D.; Sornin, N. 3—LoRaWAN protocol: Specifications, security, and capabilities. In LPWAN Technologies for IoT and M2M Applications; Chaudhari, B.S., Zennaro, M., Eds.; Academic Press: Cambridge, MA, USA, 2020; pp. 37–63. [Google Scholar] [CrossRef]
- Reschke, J. The ’basic’ http authentication scheme. In Internet Engineering Task Force (IETF); Engineering Steering Group (IESG): Fremont, CA, USA, 2015; Available online: https://httpwg.org/specs/rfc7617.html (accessed on 25 August 2020).
- Brachmann, M.; Garcia-Morchon, O.; Kirsche, M. Security for practical coap applications: Issues and solution approaches. In GI/ITG KuVS Fachgesprch Sensornetze (FGSN), Paderborn, Germany; University Stuttgart: Stuttgart, Germany, 2011. [Google Scholar]
- Antonakakis, M.; April, T.; Bailey, M.; Bernhard, M.; Bursztein, E.; Cochran, J.; Durumeric, Z.; Halderman, J.A.; Invernizzi, L.; Kallitsis, M.; et al. Understanding the mirai botnet. In Proceedings of the 26th USENIX Security Symposium, Vancouver, BC, Canada, 16–18 August 2017; pp. 1093–1110. [Google Scholar]
- Hallman, R.; Bryan, J.; Palavicini, G.; Divita, J.; Romero-Mariona, J. IoDDoS-the internet of distributed denial of sevice attacks. In Proceedings of the 2nd International Conference on Internet of Things, Big Data and Security, Porto, Portugal, 24–26 April 2017; SCITEPRESS: Setúbal, Portugal, 2017; pp. 47–58. [Google Scholar]
- Haataja, K.M.J.; Box, P.O.; Kuopio, F. Security in Bluetooth, WLAN and IrDA: A comparison Department of Computer Science Security; University of Kuopio: Kuopio, Finland, 2006; pp. 1–14. Available online: http://www.cs.uku.fi/research/publications/reports/A-2006-1.pdf (accessed on 25 August 2020).
- Sundaresan, S.; Doss, R.; Zhou, W. RFID in Healthcare–Current Trends and the Future. In Mobile Health; Springer: Berlin/Heidelberg, Germany, 2015; pp. 839–870. [Google Scholar]
- Weis, S.A.; Sarma, S.E.; Rivest, R.L.; Engels, D.W. Security and privacy aspects of low-cost radio frequency identification systems. In Security in Pervasive Computing; Springer: Berlin/Heidelberg, Germany, 2004; pp. 201–212. [Google Scholar]
- Upson, S. RFID Systems May Disrupt the Function of Medical Devices. IEEE Spectr. 2008. Available online: https://spectrum.ieee.org/computing/embedded-systems/rfid-systems-may-disrupt-the-function-of-medical-devices (accessed on 25 August 2020).
- Roland, M.; Langer, J.; Scharinger, J. Applying relay attacks to Google Wallet. In Proceedings of the 2013 5th International Workshop on Near Field Communication (NFC), Zurich, Switzerland, 5 February 2013; pp. 1–6. [Google Scholar]
- Haselsteiner, E.; Breitfuß, K. Security in Near Field Communication ( NFC ) Strengths and Weaknesses. Semiconductors 2006, 11, 71. [Google Scholar] [CrossRef]
- Dunning, J. Taming the blue beast: A survey of bluetooth based threats. IEEE Secur. Priv. 2010, 8, 20–27. [Google Scholar] [CrossRef]
- LeCroy. CATC Merlin II—Bluetooth V1.2 Protocol Analyzer; LeCroy: Santa Clara, CA, USA, 2003; Available online: http://cdn.teledynelecroy.com/files/pdf/lecroy_merlinii_datasheet.pdf (accessed on 25 August 2020).
- Haataja, K.M.; Hypponen, K. Man-in-the-middle attacks on bluetooth: A comparative analysis, a novel attack, and countermeasures. In Proceedings of the 2008 3rd International Symposium on Communications, Control and Signal Processing, St Julians, Malta, 12–14 March 2008; pp. 1096–1102. [Google Scholar]
- Minar, N.B.N.I.; Tarique, M. Bluetooth security threats and solutions: A survey. Int. J. Distrib. Parallel Syst. 2012, 3, 127. [Google Scholar] [CrossRef]
- Fouladi, B.; Ghanoun, S. SensePost UK Honey, i’m home!!, hacking zwave home automation systems. Black Hat USA, Las Vegas, Nevada. 2013. Available online: https://code.google.com/archive/p/z-force/ (accessed on 25 August 2020).
- Singh, M.; Leu, P.; Capkun, S. UWB with Pulse Reordering: Securing Ranging against Relay and Physical-Layer Attacks. In Proceedings of the 26th Annual Network and Distributed System Security Symposium (NDSS 2019), San Diego, CA, USA, 24–27 February 2019. [Google Scholar] [CrossRef]
- Olawumi, O.; Haataja, K.; Asikainen, M.; Vidgren, N.; Toivanen, P. Three practical attacks against ZigBee security: Attack scenario definitions, practical experiments, countermeasures, and lessons learned. In Proceedings of the 2014 14th International Conference on Hybrid Intelligent Systems, Hawally, Kuwait, 14–16 December 2014; pp. 199–206. [Google Scholar]
- Vidgren, N.; Haataja, K.; Patiño-Andres, J.L.; Ramírez-Sanchis, J.J.; Toivanen, P. Security threats in ZigBee-enabled systems: Vulnerability evaluation, practical experiments, countermeasures, and lessons learned. In Proceedings of the Annual Hawaii International Conference on System Sciences, Maui, HI, USA, 7–10 January 2013; pp. 5132–5138. [Google Scholar] [CrossRef]
- Rudresh, V. Zigbee Security : Basics (Part 3); Technical Report; Zigbee: Davis, CA, USA, 2017; Available online: https://research.kudelskisecurity.com/2017/11/21/zigbee-security-basics-part-3/ (accessed on 25 August 2020).
- Whitehurst, L.N.; Andel, T.R.; McDonald, J.T. Exploring security in ZigBee networks. In Proceedings of the 9th Annual Cyber and Information Security Research Conference, Oak Ridge, TN, USA, 8–10 April 2014; pp. 25–28. [Google Scholar]
- Ronen, E.; Shamir, A.; Weingarten, A.O.; O’Flynn, C. IoT goes nuclear: Creating a ZigBee chain reaction. In Proceedings of the 2017 IEEE Symposium on Security and Privacy (SP), Jose, CA, USA, 22–26 May 2017; pp. 195–212. [Google Scholar]
- Cao, X.; Shila, D.M.; Cheng, Y.; Yang, Z.; Zhou, Y.; Chen, J. Ghost-in-zigbee: Energy depletion attack on zigbee-based wireless networks. IEEE Internet Things J. 2016, 3, 816–829. [Google Scholar] [CrossRef]
- Qi, Y.; Li, W.; Luo, X.; Wang, Q. Security analysis of WIA-PA protocol. In Advanced Technologies in Ad Hoc and Sensor Networks; Springer: Berlin/Heidelberg, Germany, 2014; pp. 287–298. [Google Scholar]
- Chen, P.; Yokogawa Electric Corporation. Using ISA100.11a Wireless Technology to Monitor Pressure and Temperature in a Refinery; Chen, P., Ed.; Yokogawa Electric Corporation: Tokyo, Japan, 2011. [Google Scholar]
- Zhang, X.; Wei, M.; Wang, P.; Kim, Y. Research and implementation of security mechanism in ISA100.11a networks. In Proceedings of the 2009 9th International Conference on Electronic Measurement Instruments, Beijing, China, 16–19 August 2009; pp. 4-716–4-721. [Google Scholar]
- Glissa, G.; Meddeb, A. 6LoWPAN multi-layered security protocol based on IEEE 802.15. 4 security features. In Proceedings of the 2017 13th International Wireless Communications and Mobile Computing Conference (IWCMC), Valencia, Spain, 26–30 June 2017; pp. 264–269. [Google Scholar]
- Wang, X.; Mu, Y. Addressing and privacy support for 6LoWPAN. IEEE Sens. J. 2015, 15, 5193–5201. [Google Scholar] [CrossRef]
- Hummen, R.; Hiller, J.; Wirtz, H.; Henze, M.; Shafagh, H.; Wehrle, K. 6LoWPAN fragmentation attacks and mitigation mechanisms. In Proceedings of the 6th ACM Conference on S: Ecurity and Privacy in Wireless and Mobile Networks, WiSec April 2013, Budapest, Hungary; 2013; pp. 55–66. [Google Scholar] [CrossRef]
- Yang, X.; Karampatzakis, E.; Doerr, C.; Kuipers, F. Security vulnerabilities in LoRaWAN. In Proceedings of the 2018 IEEE/ACM Third International Conference on Internet-of-Things Design and Implementation (IoTDI), Orlando, FL, USA, 17–20 April 2018; IEEE, 2018; pp. 129–140. [Google Scholar]
- Duggal, A. HL7 2. x security. In Proceedings of the The 8th Annual HITB Security Conference, Amsterdam, The Nertherlands, 10–14 April 2017. [Google Scholar]
- Moustis, D.; Kotzanikolaou, P. Evaluating security controls against HTTP-based DDoS attacks. In Proceedings of the IISA, Piraeus, Greece, 10–12 July 2013; IEEE, 2013; pp. 1–6. [Google Scholar]
- Rahman, R.A.; Shah, B. Security analysis of IoT protocols: A focus in CoAP. In Proceedings of the 2016 3rd MEC International Conference on Big Data and Smart City, ICBDSC 2016, Muscat, Oman, 15–16 March 2016; pp. 172–178. [Google Scholar] [CrossRef]
- Arvind, S.; Narayanan, V.A. An Overview of Security in CoAP: Attack and Analysis. In Proceedings of the 2019 5th International Conference on Advanced Computing Communication Systems (ICACCS), Coimbatore, India, 15–16 March 2019; pp. 655–660. [Google Scholar]
- Dinculeană, D. Vulnerabilities and Limitations of MQTT Protocol Used between IoT Devices. Appl. Sci. 2019, 9, 848. [Google Scholar] [CrossRef]
- Andy, S.; Rahardjo, B.; Hanindhito, B. Attack scenarios and security analysis of MQTT communication protocol in IoT system. In Proceedings of the 2017 4th International Conference on Electrical Engineering, Computer Science and Informatics (EECSI), Yogyakarta, Indonesia, 19–21 September 2017; pp. 1–6. [Google Scholar]
- Song, B.; Mitchell, C.J. RFID Authentication Protocol for Low-Cost Tags. In Proceedings of the First ACM Conference on Wireless Network Security, WiSec ’08, Alexandria, VA, USA, 31 March–2 April 2008; Association for Computing Machinery: New York, NY, USA, 2008; pp. 140–147. [Google Scholar] [CrossRef]
- Sun, D.; Zhong, J. A hash-based RFID security protocol for strong privacy protection. IEEE Trans. Consum. Electron. 2012, 58, 1246–1252. [Google Scholar] [CrossRef]
- Cvitić, I.; Vujić, M.; Husnjak, S. Classification of security risks in the IoT environment. In Proceedings of the Annals of DAAAM and Proceedings of the International DAAAM Symposium, Vienna, Austria, 21–24 October 2015; Volume 2015, pp. 731–740. [Google Scholar] [CrossRef]
- Eun, H.; Lee, H.; Oh, H. Conditional privacy preserving security protocol for NFC applications. IEEE Trans. Consum. Electron. 2013, 59, 153–160. [Google Scholar] [CrossRef]
- Madlmayr, G.; Langer, J.; Kantner, C.; Scharinger, J. NFC Devices: Security and Privacy. In Proceedings of the 2008 Third International Conference on Availability, Reliability and Security, Barcelona, Spain, 4–7 March 2008; pp. 642–647. [Google Scholar]
- Tabet, N.E.; Ayu, M.A. Analysing the security of NFC based payment systems. In Proceedings of the 2016 International Conference on Informatics and Computing (ICIC), Mataram, Indonesia, 28–29 October ; 2016; pp. 169–174. [Google Scholar] [CrossRef]
- Frustaci, M.; Pace, P.; Aloi, G.; Fortino, G. Evaluating critical security issues of the IoT world: Present and future challenges. IEEE Internet Things J. 2018, 5, 2483–2495. [Google Scholar] [CrossRef]
- Chakrabarty, S.; Engels, D.W. Black networks for Bluetooth Low Energy. In Proceedings of the 2016 IEEE International Conference on Consumer Electronics, ICCE 2016, Las Vegas, NV, USA, 7–11 January 2016; pp. 11–14. [Google Scholar] [CrossRef]
- Meneghello, F.; Calore, M.; Zucchetto, D.; Polese, M.; Zanella, A. IoT: Internet of Threats? A survey of practical security vulnerabilities in real IoT devices. IEEE Internet Things J. 2019, 6, 1. [Google Scholar] [CrossRef]
- Lonzetta, A.M.; Cope, P.; Campbell, J.; Mohd, B.J.; Hayajneh, T. Security vulnerabilities in bluetooth technology as used in IoT. J. Sens. Actuator Netw. 2018, 7, 28. [Google Scholar] [CrossRef]
- Yassein, M.B.; Mardini, W.; Almasri, T. Evaluation of Security Regarding Z-Wave Wireless Protocol. In Proceedings of the Fourth International Conference on Engineering & MIS, ICEMIS ’18, Istanbul, Turkey, 9–11 April 2018; Association for Computing Machinery: New York, NY, USA, 2018. [Google Scholar] [CrossRef]
- Zeng, Y.; Cao, J.; Hong, J.; Zhang, S.; Xie, L. Secure localization and location verification in wireless sensor networks: A survey. J. Supercomput. 2013, 64, 685–701. [Google Scholar] [CrossRef]
- Tippenhauer, N.O.; Capkun, S. ID-Based Secure Distance Bounding and Localization. In Lecture Notes in Computer Science; Springer: Berlin/Heidelberg, Germany, 2009; pp. 621–636. [Google Scholar] [CrossRef]
- Wang, Y.; Ma, X.; Leus, G. An UWB ranging-based localization strategy with internal attack immunity. In Proceedings of the 2010 IEEE International Conference on Ultra-Wideband, Nanjing, China, 20–23 September 2010; Volume 2, pp. 1–4. [Google Scholar]
- Peng, H. WIFI network information security analysis research. In Proceedings of the 2012 2nd International Conference on Consumer Electronics, Communications and Networks (CECNet), Yichang, China, 21–23 April 2012; pp. 2243–2245. [Google Scholar] [CrossRef]
- Plosz, S.; Farshad, A.; Tauber, M.; Lesjak, C.; Ruprechter, T.; Pereira, N. Security vulnerabilities and risks in industrial usage of wireless communication. In Proceedings of the 2014 IEEE Emerging Technology and Factory Automation (ETFA), Barcelona, Spain, 16–19 September 2014. [Google Scholar] [CrossRef]
- Khanji, S.; Iqbal, F.; Hung, P. ZigBee Security Vulnerabilities: Exploration and Evaluating. In Proceedings of the 2019 10th International Conference on Information and Communication Systems, ICICS, Irbid, Jordan, 11–13 June 2019; pp. 52–57. [Google Scholar] [CrossRef]
- Kim, H.; Chung, J.; Kim, C. Secured communication protocol for internetworking ZigBee cluster networks. Comput. Commun. 2009, 32, 1531–1540. [Google Scholar] [CrossRef]
- Min, W.; Zhang, X.; Ping, W.; Kim, K.; Kim, Y. Research and Implementation of the Security Method Based on WIA-PA Standard. In Proceedings of the 2010 International Conference on Electrical and Control Engineering, Wuhan, China, 25–27 June 2010; pp. 1580–1585. [Google Scholar]
- Petersen, S.; Carlsen, S. WirelessHART Versus ISA100.11a: The Format War Hits the Factory Floor. IEEE Ind. Electron. Mag. 2011, 5, 23–34. [Google Scholar] [CrossRef]
- Glissa, G.; Meddeb, A. 6LowPSec: An end-to-end security protocol for 6LoWPAN. Ad Hoc Netw. 2019, 82, 100–112. [Google Scholar] [CrossRef]
- Benslimane, Y.; Benahmed, K.; Benslimane, H. Security Mechanisms for 6LoWPAN Network in Context of Internet of Things: A Survey. In Renewable Energy for Smart and Sustainable Cities; Hatti, M., Ed.; Springer International Publishing: Cham, Switzerland, 2019; pp. 49–69. [Google Scholar]
- Lee, M.; Lee, K.; Shim, J.; Cho, S.; Choi, J. Security threat on wearable services: Empirical study using a commercial smartband. In Proceedings of the 2016 IEEE International Conference on Consumer Electronics-Asia (ICCE-Asia), Seoul, Korea, 26–28 October 2016; pp. 1–5. [Google Scholar]
- Zubair, M.; Unal, D.; Al-Ali, A.; Shikfa, A. Exploiting Bluetooth Vulnerabilities in e-Health IoT Devices. In Proceedings of the 3rd International Conference on Future Networks and Distributed Systems (ICFNDS ’19), Paris, France, 1–2 July 2019; pp. 1–7. [Google Scholar] [CrossRef]
- Yang, Y.; Wu, L.; Yin, G.; Li, L.; Zhao, H. A Survey on Security and Privacy Issues in Internet-of-Things. IEEE Internet Things J. 2017, 4, 1250–1258. [Google Scholar] [CrossRef]
- Asplund, M.; Nadjm-Tehrani, S. Attitudes and Perceptions of IoT Security in Critical Societal Services. IEEE Access 2016, 4, 2130–2138. [Google Scholar] [CrossRef]
- Chacko, A.; Hayajneh, T. Security and privacy issues with IoT in healthcare. EAI Endorsed Trans. Pervasive Health Technol. 2018, 4, 155079. [Google Scholar] [CrossRef]
- Huang, C.; Chen, H.; Yang, L.; Zhang, Q. BreathLive: Liveness Detection for Heart Sound Authentication with Deep Breathing. Proc. ACM Interact. Mob. Wearable Ubiquitous Technol. 2018, 2. [Google Scholar] [CrossRef]
- Bonaci, T.; Herron, J.; Yusuf, T.; Yan, J.; Kohno, T.; Chizeck, H.J. To Make a Robot Secure: An Experimental Analysis of Cyber Security Threats Against Teleoperated Surgical Robots. arXiv 2015, arXiv:1504.04339. [Google Scholar]
- Casola, V.; De Benedictis, A.; Riccio, A.; Rivera, D.; Mallouli, W.; Montes de Oca, E. A security monitoring system for Internet of Things. Internet Things 2019, 7, 100080. [Google Scholar] [CrossRef]
- Butt, S.; Diaz, J.; Jamal, T.; Ali, A.; De la Hoz, E.; Shoaib, M. IoT Smart Health Security Threats. In Proceedings of the 2019 19th International Conference on Computational Science and Its Applications (ICCSA), Saint Petersburg, Russia, 1–4 July 2019. [Google Scholar] [CrossRef]
- Culler, D.E. Berkeley CWSN Keynote, University of California. Available online: http://web.archive.org/web/20080207010024/http://www.808multimedia.com/winnt/kernel.htm (accessed on 25 August 2020).
- Toscano, E.; Bello, L.L. Comparative assessments of IEEE 802.15. 4/ZigBee and 6LoWPAN for low-power industrial WSNs in realistic scenarios. In Proceedings of the 2012 9th IEEE International Workshop on Factory Communication Systems, Lemgo/Detmold, Germany, 21–24 May 2012; pp. 115–124. [Google Scholar]
- Tabish, R.; Mnaouer, A.B.; Touati, F.; Ghaleb, A.M. A comparative analysis of BLE and 6LoWPAN for U-HealthCare applications. In Proceedings of the 2013 7th IEEE GCC Conference and Exhibition (GCC), Doha, Qatar, 17–20 November 2013; pp. 286–291. [Google Scholar]
- Clarke, M.; de Folter, J.; Verma, V.; Gokalp, H. Interoperable end-to-end remote patient monitoring platform based on IEEE 11073 PHD and ZigBee health care profile. IEEE Trans. Biomed. Eng. 2017, 65, 1014–1025. [Google Scholar] [CrossRef]
- Fontana, R.J. Recent system applications of short-pulse ultra-wideband (UWB) technology. IEEE Trans. Microw. Theory Tech. 2004, 52, 2087–2104. [Google Scholar] [CrossRef]
- Shelby, Z.; Bormann, C. 6LoWPAN: The Wireless Embedded Internet; John Wiley & Sons: Hoboken, NJ, USA, 2011; Volume 43. [Google Scholar]
- NXP. Medical Applications User Guide—Home Portable Medical Diagnostic and Therapy Devices Medical Imaging Wearables. Available online: https://www.nxp.com/docs/en/user-guide/MDAPPUSGDRM118.pdf (accessed on 25 August 2020).
- O’Brien, G. Securing Wireless Infusion Pumps; Technical Report; National Institute of Standards and Technology: Montgomery County, MD, USA, 2018. Available online: https://nvlpubs.nist.gov/nistpubs/SpecialPublications/NIST.SP.1800-8.pdf (accessed on 25 August 2020).
- HL7 FHIR Specification (v4.0.1: R4). Resource DiagnosticReport—Content. Available online: https://www.hl7.org/fhir/diagnosticreport.html (accessed on 25 August 2020).
- Pant, R. Computer networks in radiology: An introduction. Indian J. Radiol. Imaging 2009, 19, 318. [Google Scholar] [CrossRef]
- Da Xu, L.; He, W.; Li, S. Internet of things in industries: A survey. IEEE Trans. Ind. Inform. 2014, 10, 2233–2243. [Google Scholar]
| Scientific Literature | Grey Literature |
|---|---|
| Keywords for the first stream: TITLE (IoMT OR “Internet of Medical Things” OR “medical” OR “healthcare” OR implantable OR implanted AND protocol OR “communication protocol”) Keywords for the second stream: TITLE (IoT OR “Internet of Things” AND security OR vulnerability OR threat OR attack OR control) | Medical, healthcare, communication protocols |
| Layer | Relevant Literature | Frequency | Data Rate | Range | Power Cons/Ion | Definition | |
|---|---|---|---|---|---|---|---|
| IoT Protocols | |||||||
| IrDA(Infrared) | Perception-Network | [12,15,26,62] | 850–900 nm | 14.4 Kbps | 1 m | na | Protocol |
| RFID | Perception | [12,15,45,52,63,64,65] | 13.56 MHz | 106–424 Kbps | 20 cm | Very Low | Technology |
| NFC | Perception-Network | [7,15,36,66,67] | 13.56 MHz | 106–424 Kbps | 20 cm | Very Low | Technology |
| Bluetooth/BLE | Perception-Network | [7,12,13,15,37,68,69,70] | 2.4 GHz | 1, 2, 3 Mbps | 80–90 m | Low | Technology |
| ZWave | Perception-Network | [18,71] | sub GHz | 40 kbps | 30 m | low | Protocol |
| UWB | Perception | [7,12,15,37] | 3.1–10.6 GHz | 53–480 Mbps | 10 m | Very Low | Technology |
| WiFi | Network | [7,37,47,63,72] | 2.4 GHz, 5 GHz | 0.1–54 Mbps | 80 m | Medium | Protocol-Standard (ISO) |
| ZigBee | Perception-Network | [7,13,36,37,47,64,69,70,73] | 2.4 GHz | 250 kbps | 100 m | Low | Protocol |
| WIA-PA | Network | [52] | na | na | na | na | Standard |
| ISA100.11a | Network | [52] | na | na | na | na | Technology |
| 6LoWPAN | Network | [7,13,36,37,45,47,52,63] | 2.4 GHz | na | na | na | Technology-Set of standards |
| LoRa WAN | Network | [7,60,61] | sub GHz | 50 kbps | 3–4 km | Low | Protocol |
| Layer | Relevant Literature | Standards | Encoding Format | Architecture | Header/Message | |
|---|---|---|---|---|---|---|
| IoT Protocols | ||||||
| COAP | App | [36,47,70,86,87,88] | IETF, Eclipse foundations | Binary | Client-Server, Broker | 4 Byte/Small |
| MQTT | App | [47,65,68,85,86,89] | OASIS, Eclipse foundations | Binary | Client-Broker | 2 Byte/Small |
| HTTP | App | [7,47,70,73,85,89] | IETF, W3C | Text | Client-Server | Undefined, Large |
| HL7 | App | [87] | ANSI/ISO/HITSP/CDA/EHR/FHIR/CCOW | UTF-8/16/32, ISO 8859-1 | Client-Server | 402/1039 bytes |
| Physiologic Monitoring | Medical Treatment | In-Hospital Connected | Ambient | Additional Devices |
|---|---|---|---|---|
| Motion sensors | Infusion pumps | MRI | Identification devices | Coordinators |
| Blood glucose device | ICPs | X-rays | Gyroscope sensors | Network devices |
| Blood pressure device | Cardiac rhythmic management | Surgical Robotics | Motion sensors | End user devices |
| Temperature sensor | Smart medical capsules | Prosthetic using Surgical Robotics | Vibration sensors | Databases |
| Pulse oximetry | Monitoring devices | Servers | ||
| Pacemakers | Alarm devices | |||
| EEG sensors | Implantable device Charger | |||
| ECG sensors | ||||
| Respiratory rate sensors | ||||
| Muscle activity sensors | ||||
| Implantable devices | ||||
| Pill-line sensors | ||||
| Aggregators |
| Protocol | Security Features | Vulnerabilities | Attacks | Controls | |
|---|---|---|---|---|---|
| IrDA(Infrared) | No embedded security controls. | Detect reflected infrared-light and filtering out the surrounding ambient noise. | Eavesdrop attack. | Physical security controls. | |
| RFID | Embedded data are unprotected and read only. | Active (continuously transmitting) and passive (electromagnetic field) RFID systems suffer from weaknesses. | Side channel attack. | Authentication-hash based protocols, encryption functions. | |
| NFC | SSE, SCH, 3 modes of operation: Read/Write, Peer-to-Peer and Card Emulation Mode. | Data exchange in close proximity, PICC emulations in protocol challenge-response requests. | Near proximity, MITM, DoS, Modification attacks. | Architecture and the distance limitations, secure channel with a standard key agreement protocol. | |
| Bluetooth/BLE | Secure simple pairing (SSP), Connectivity issues over obstacles | Encryption of the payload and not of all the entire packet, matching the connection’s frequency hops and then capturing data in that frequency range, address verification, PINs. | Sniffinig, DoS, MITM, Brute-Force, device duplication attacks. | AES-CCM, 4-byte MIC module, AES-128 | |
| ZWave | AES encryption with three shared keys. | Does not enforce a standard key exchange protocol, Z-Wave devices implicitly trust the source and destination fields of794the MPDU frame.a malicious node can assigned by the controller. | Key Reset, impersonation, node spoofing, BlackHole attacks. | AES-128 with three shared keys. | |
| UWB | LRP/HRP secure ranging schemes, size of the UWB symbol. | Long symbols length, wrong access control configuration or power failure. | ED/LC, Same-Nonce attack. | Localization and distancing protocols secure the range between nodes. | |
| WiFi | WPA2, SSID hiding, MAC filtering and static IP addressing, Connectivity issues over obstacles | Lack of granular device authentication, weakness against denial of service, limited protection of service integrity. | DoS, Replay, Channel collision, Spoofing attacks. | WPA, WPA2 capability, 128-bit WEP authentication. | |
| ZigBee | 128-bit AES with pre-share keys, frame-protection mechanisms, essential key(encryption in network layer), global link key and unique link key(App layer), Connectivity issues over obstacles | Utilizing insecure key transportation for pre-shared keys, ACKs have no integrity checks, insufficient registration of network keys, the lack of verification in PAN IDs. | Installing default link keys or sending security headers in clear text on auxiliary frames, looding that causes DoS, euses of Initiation Vectors which may lead to key compromise, energy-consuming attacks. | AES for symmetric key, AES-CTR, AES-CBC-MAC, AES-CCM, Use the Non Volatile Memory of the node to store the nonce states, Key management algorithm. | |
| WIA-PA | Join-key shared between device and security manager. | Lack of public key encryption algorithm, no intrusion prevention, no broadcast key, The first request is not encrypted. | Sybil, DoS, wormhole, Jaming , traffic analysis attack. | AFS, AFH, TH, MIC. | |
| ISA100.11a | Linchpin, AES-128, time limitations | Requires some special conditions to be implemented in a secure path. | Sniffing, Spoofing, Replay attacks and Data falsification. | AES-128 on TL header. | |
| 6LoWPAN | AES cipher suit, ESP, IKEv2, DTLS, Connectivity issues over obstacles | IP network, radio signal of implementations, Unchanged nodes address, fragmentation mechanism. | Use of malicious intermediary network nodes, Signal jamming, traffic analysis, attackers selectively prevent correct packet reassembly. | DTLS, HIP, IKE, cryptographic techniques. | |
| LoRa WAN | 128-bit application session key (AppSKey), AES. | Resetting frame counters without re-keying, caching and replay of ACK packets, transmit falsified gateway beacons to repeatedly wake up sensors, utilize a dictionary of pastmessage. | Replay attacks, recovery of passwords, malicious message modification, battery exhaustion and DoS. | AES-CMAC, AAES-CTR, MIC. | |
| HL7 | No built-in security. | Message sources are often not validated by default, ize of HL7 messages is often not validated. | Spoofing or integrity attacks, Flooding attacks. | SSL, VPN. | |
| HTTP | Basic-Digest authentication. | Data transfer is not encrypted, Get request. | Evasedropping- theft- breach and manipulation, flooding attacks | SSL/TLS(HTTPS) | |
| COAP | NoSec- SharedKey -MultiKey- Certificate mode. | Proxies having to decide if DTLS implementation will be multi-cast or uni-cast message. | Parsing, Cache, amplification, spoofing. Cross-protocol attacks. | DTLS, Strong authentication technique. | |
| MQTT | Four-way handshake mechanism. | No embedded data encryption mechanism, IP broker (sometimes is unsecure). | Traffic analysis, Port Obscurity, Botnet Over MQTT. | SSL/TLS |
© 2020 by the authors. Licensee MDPI, Basel, Switzerland. This article is an open access article distributed under the terms and conditions of the Creative Commons Attribution (CC BY) license (http://creativecommons.org/licenses/by/4.0/).
Share and Cite
Koutras, D.; Stergiopoulos, G.; Dasaklis, T.; Kotzanikolaou, P.; Glynos, D.; Douligeris, C. Security in IoMT Communications: A Survey. Sensors 2020, 20, 4828. https://doi.org/10.3390/s20174828
Koutras D, Stergiopoulos G, Dasaklis T, Kotzanikolaou P, Glynos D, Douligeris C. Security in IoMT Communications: A Survey. Sensors. 2020; 20(17):4828. https://doi.org/10.3390/s20174828
Chicago/Turabian StyleKoutras, Dimitris, George Stergiopoulos, Thomas Dasaklis, Panayiotis Kotzanikolaou, Dimitris Glynos, and Christos Douligeris. 2020. "Security in IoMT Communications: A Survey" Sensors 20, no. 17: 4828. https://doi.org/10.3390/s20174828
APA StyleKoutras, D., Stergiopoulos, G., Dasaklis, T., Kotzanikolaou, P., Glynos, D., & Douligeris, C. (2020). Security in IoMT Communications: A Survey. Sensors, 20(17), 4828. https://doi.org/10.3390/s20174828









