Protecting Physical Communications in 5G C-RAN Architectures through Resonant Mechanisms in Optical Media
Abstract
1. Introduction
- Enhanced Mobile Broadband Communications (eMBC) [4]: Mobile nodes and devices must be provided with very high-speed communication links. Typically, experts indicate that effective bitrate should be above 50 Mbps.
- Ultra-Reliable Low Latency Communications (URLLC) [5]: Communication links supported by 5G networks must guarantee a very low delay and jitter in transmissions with remote nodes. According to most authors, jitter must be null and communication delays be below 10 (ten) milliseconds.
- Massive Machine-Type Communications (MMTC) [6]: In future 5G networks thousands of nodes and devices in pervasive infrastructures and dense deployments must communicate concurrently. All of them must be provided with eMBC and URLLC, and mobile networks must be able to handle these scenarios.
2. State of the Art on 5G Security Solutions and C-RAN Solutions
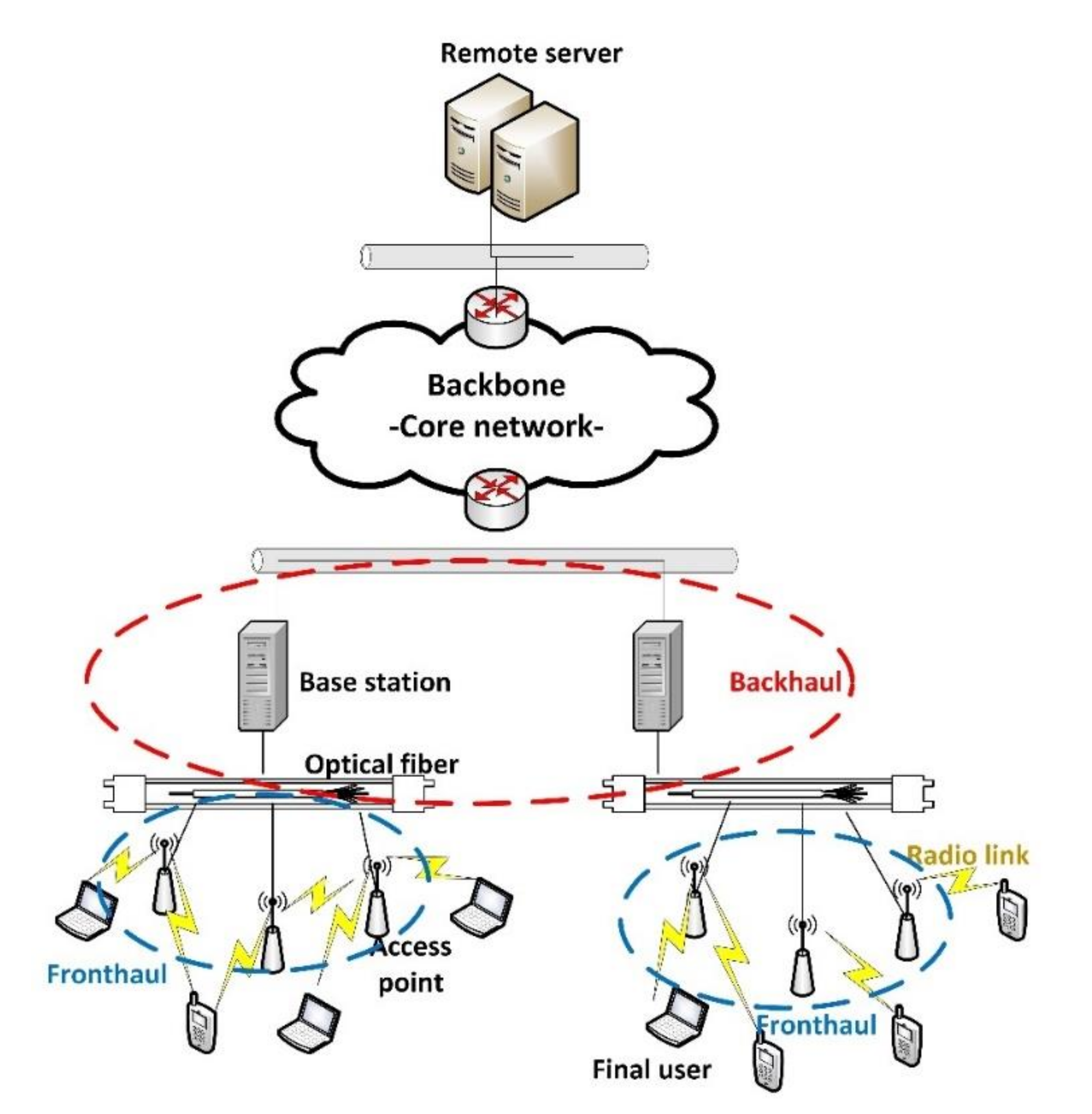
2.1. C-RAN Architectures, Solutions, and Characteristics
2.2. Security Technologies for C-RAN Architectures
3. A New Protection Solution for Communications at Physical Layer in C-RAN Architectures
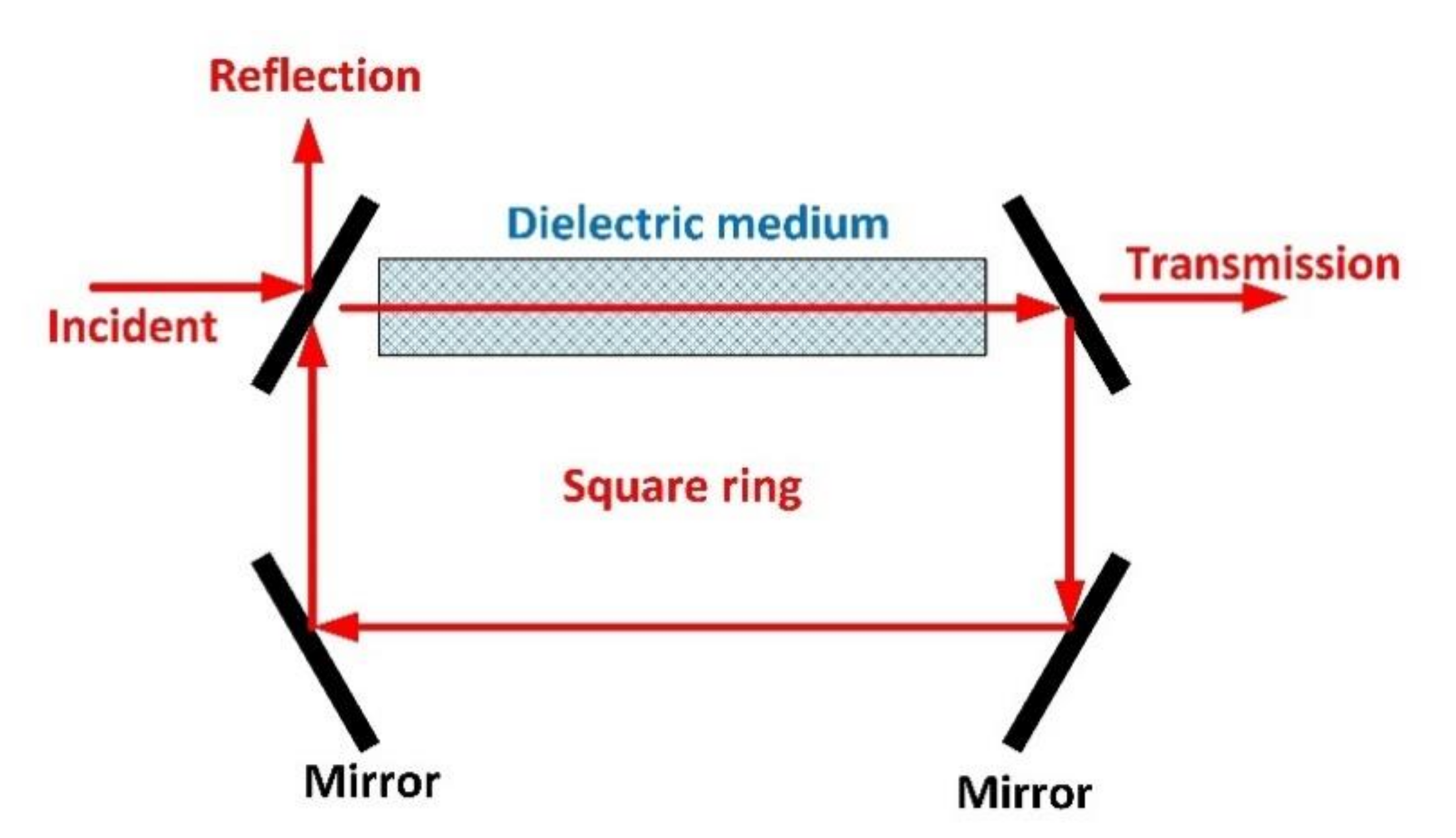
3.1. Non-Linear and Unclonable Effects in Optical Fibers
3.2. Resonant Structures in Optical Fibers
3.3. Generating Chaotic Resonant Phenomena in Optical Links
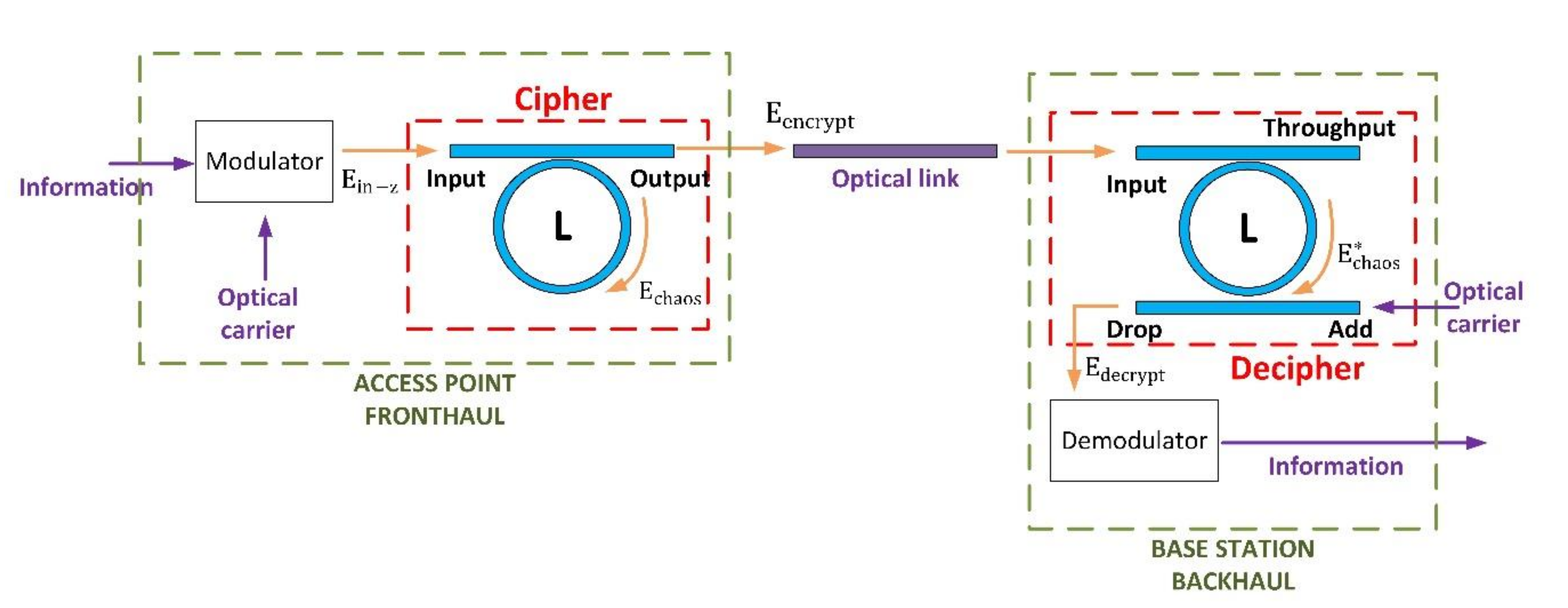
3.4. Information Protection Infrastructure
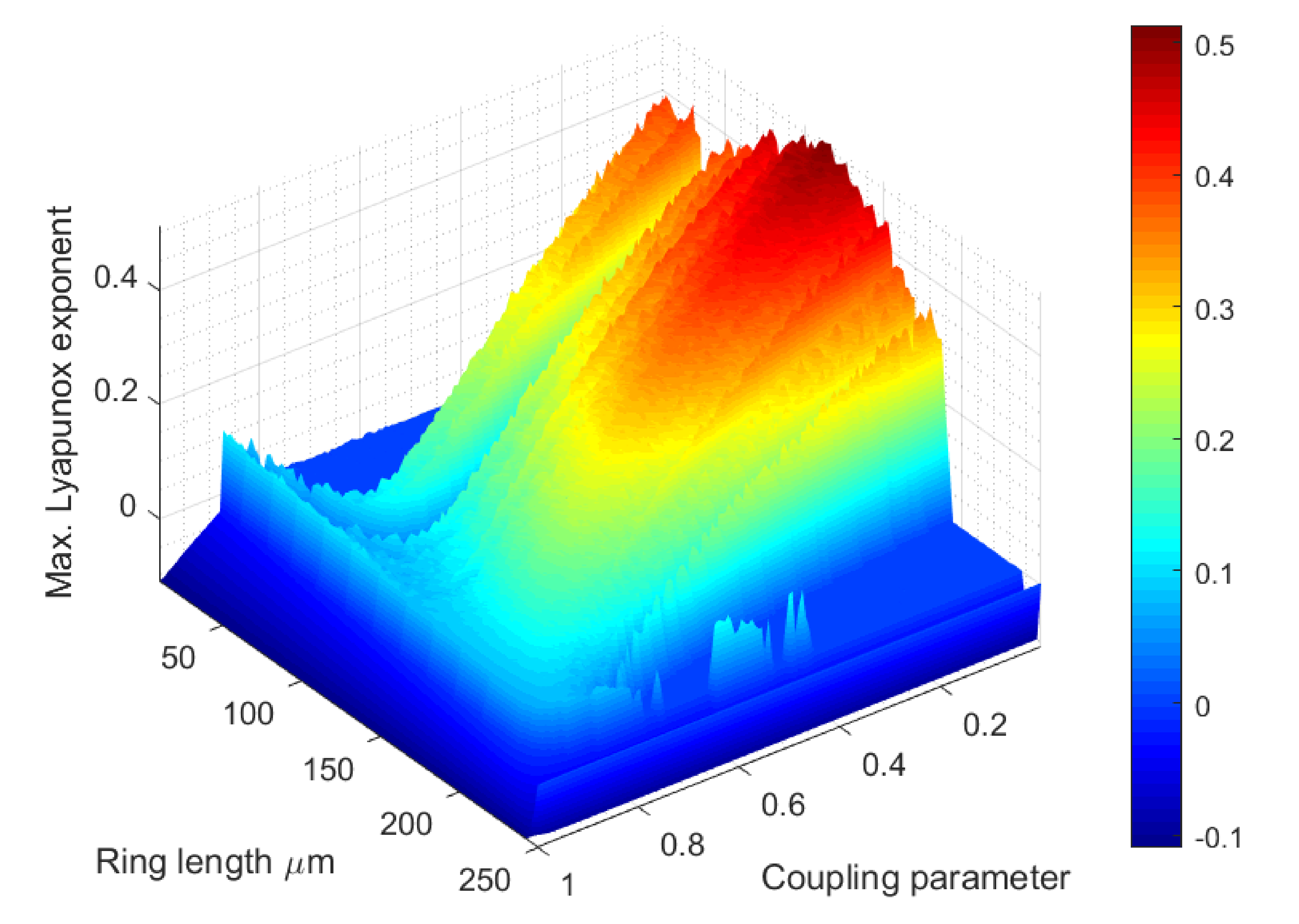
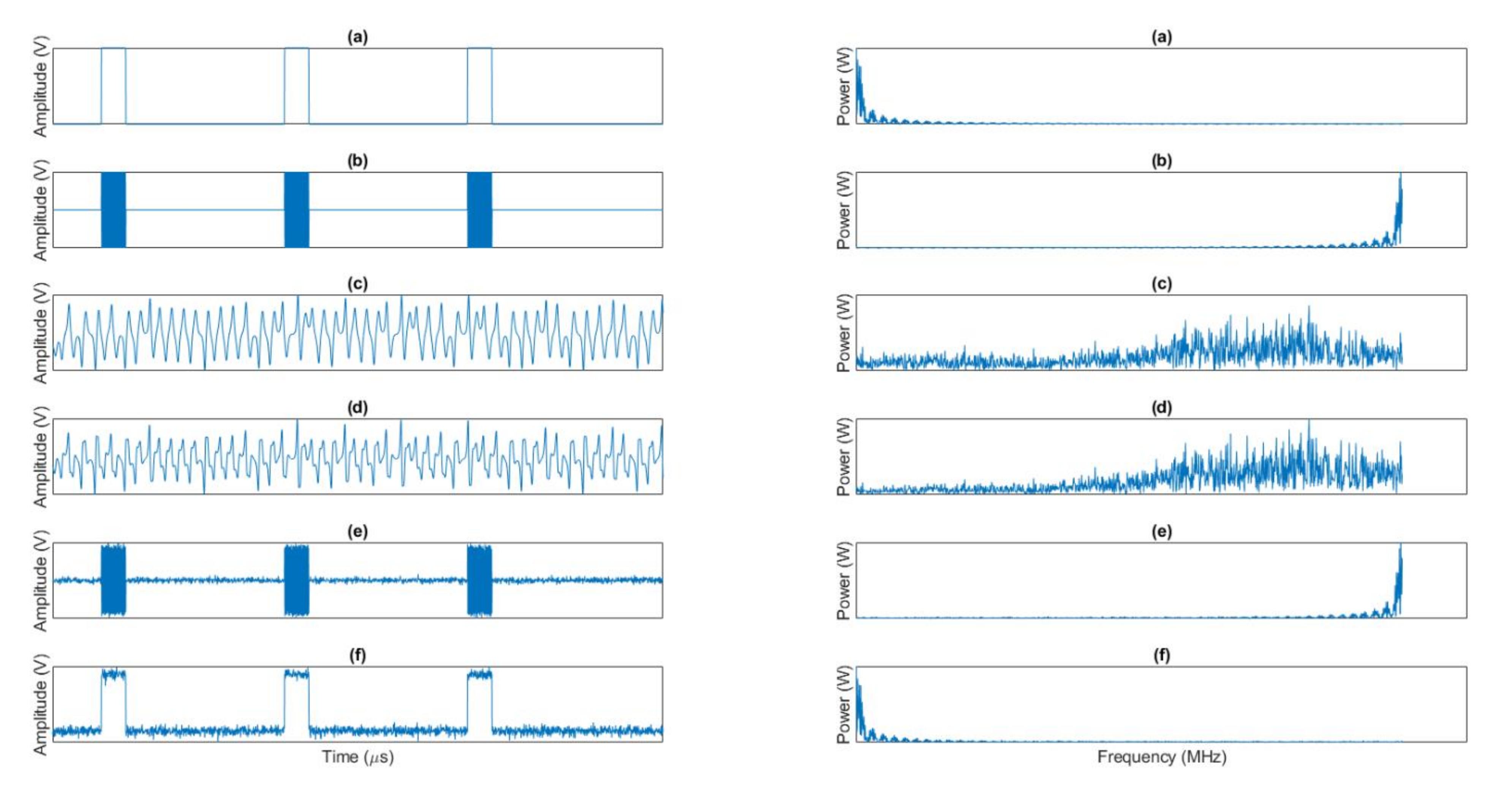
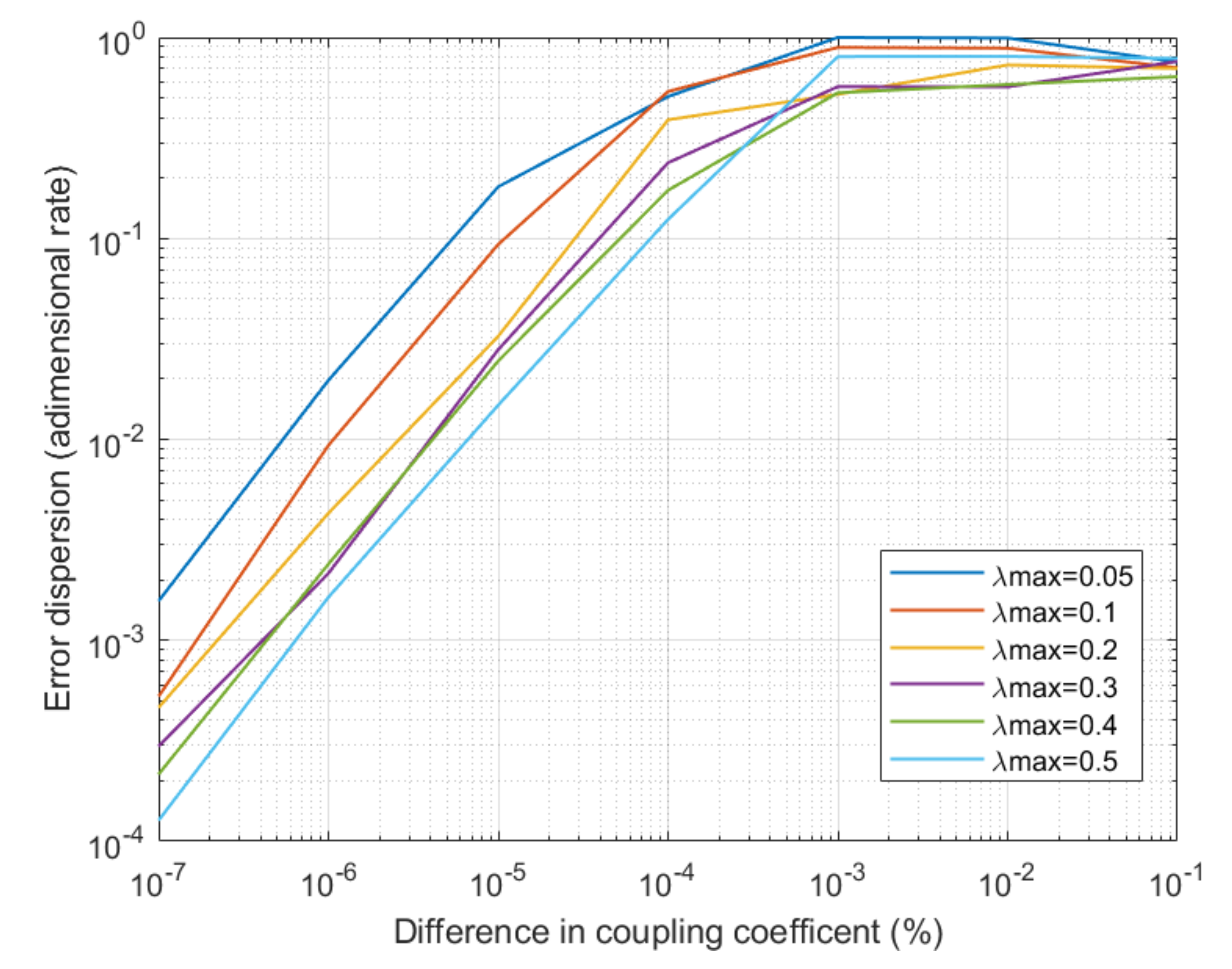
4. Experimental Validation and Results
5. Conclusions and Future Works
Author Contributions
Funding
Conflicts of Interest
References
- Panwar, N.; Sharma, S.; Singh, A.K. A survey on 5G: The next generation of mobile communication. Phys. Commun. 2016, 18, 64–84. [Google Scholar] [CrossRef]
- Sánchez, B.B.; Sanchez-Picot, A.; De Rivera, D.S. Using 5G Technologies in the Internet of Things Handovers, Problems and Challenges. In Proceedings of the 2015 9th International Conference on Innovative Mobile and Internet Services in Ubiquitous Computing, Blumenau, Brazil, 8–10 July 2015; pp. 364–369. [Google Scholar]
- Bordel, B.; Alcarria, R.; Robles, T.; Sánchez-De-Rivera, D. Service management in virtualization-based architectures for 5G systems with network slicing. Integr. Comput. Eng. 2019, 27, 77–99. [Google Scholar] [CrossRef]
- Gamage, H.; Rajatheva, N.; Latva-Aho, M. Channel coding for enhanced mobile broadband communication in 5G Systems. In Proceedings of the 2017 European Conference on Networks and Communications (EuCNC), Oulu, Finland, 12–15 June 2017; pp. 1–6. [Google Scholar]
- Pocovi, G.; Shariatmadari, H.; Berardinelli, G.; Pedersen, K.; Steiner, J.; Li, Z. Achieving Ultra-Reliable Low-Latency Communications: Challenges and Envisioned System Enhancements. IEEE Netw. 2018, 32, 8–15. [Google Scholar] [CrossRef]
- Bockelmann, C.; Pratas, N.K.; Nikopour, H.; Au, K.; Svensson, T.; Stefanovic, C.; Popovski, P.; Dekorsy, A. Massive machine-type communications in 5g: Physical and MAC-layer solutions. IEEE Commun. Mag. 2016, 54, 59–65. [Google Scholar] [CrossRef]
- Kowalski, J.M.; Nogami, T.; Yin, Z.; Sheng, J.; Ying, K. Coexistence of enhanced mobile broadband communications and ultra reliable low latency communications in mobile front-haul. In Proceedings of the Broadband Access Communication Technologies XII, Washington, DC, USA, 23 May 2018; Volume 10559, p. 105590C. [Google Scholar] [CrossRef]
- Ge, X.; Cheng, H.; Guizani, M.; Han, T. 5G wireless backhaul networks: Challenges and research advances. IEEE Netw. 2014, 28, 6–11. [Google Scholar] [CrossRef]
- Ranaweera, C.; Wong, E.; Nirmalathas, A.; Jayasundara, C.; Lim, C. 5G C-RAN With Optical Fronthaul: An Analysis From a Deployment Perspective. J. Lightwave Technol. 2018, 36, 2059–2068. [Google Scholar] [CrossRef]
- Wu, J.; Zhang, Z.; Hong, Y.; Wen, Y. Cloud radio access network (C-RAN): A primer. IEEE Netw. 2015, 29, 35–41. [Google Scholar] [CrossRef]
- Mareca, P.; Bordel, B. An intra-slice chaotic-based security solution for privacy preservation in future 5G systems. In World Conference on Information Systems and Technologies; Springer: Cham, Switzerland, 2018; pp. 144–154. [Google Scholar]
- Bordel, B.; Orue, A.B.; Alcarria, R.; Sánchez-De-Rivera, D. An Intra-Slice Security Solution for Emerging 5G Networks Based on Pseudo-Random Number Generators. IEEE Access 2018, 6, 16149–16164. [Google Scholar] [CrossRef]
- Bordel, B.; Alcarria, R.; Robles, T.; Sánchez, B.B. Stochastic and Information Theory Techniques to Reduce Large Datasets and Detect Cyberattacks in Ambient Intelligence Environments. IEEE Access 2018, 6, 34896–34910. [Google Scholar] [CrossRef]
- Kardaras, G.; Lanzani, C. Advanced multimode radio for wireless & mobile broadband communication. In Proceedings of the 2009 European Wireless Technology Conference, Rome, Italy, 28–29 September 2009; pp. 132–135. [Google Scholar]
- Quek, T.Q.; Peng, M.; Simeone, O.; Yu, W. Cloud Radio Access Networks: Principles, Technologies, and Applications; Cambridge University Press: Cambridge, UK, 2017. [Google Scholar]
- Lin, Y.; Shao, L.; Zhu, Z.; Wang, Q.; Sabhikhi, R.K. Wireless network cloud: Architecture and system requirements. IBM J. Res. Dev. 2010, 54, 4:1–4:12. [Google Scholar] [CrossRef]
- Checko, A.; Christiansen, H.L.; Yan, Y.; Scolari, L.; Kardaras, G.; Berger, M.S.; Dittmann, L. Cloud RAN for Mobile Networks—A Technology Overview. IEEE Commun. Surv. Tutor. 2014, 17, 405–426. [Google Scholar] [CrossRef]
- Bordel, B.; De Rivera, D.S.; Alcarria, R. Virtualization-based techniques for the design, management and implementation of future 5G systems with network slicing. In World Conference on Information Systems and Technologies; Springer: Cham, Switzerland, 2018; pp. 133–143. [Google Scholar]
- Venkatarman, H.; Trestian, R. 5G Radio Access Networks: Centralized RAN, Cloud-RAN and Virtualization of Small Cells; CRC Press: Boca Raton, FL, USA, 2007. [Google Scholar]
- Simeone, O.; Gambini, J.; Bar-Ness, Y.; Spagnolini, U. Cooperation and cognitive radio. In Proceedings of the 2007 IEEE International Conference on Communications, Glasgow, UK, 24–28 June 2007; pp. 6511–6515. [Google Scholar]
- Lien, S.-Y.; Hung, S.-C.; Hsu, H.; Chen, K.-C. Collaborative radio access of heterogeneous cloud radio access networks and edge computing networks. In Proceedings of the 2016 IEEE International Conference on Communications Workshops (ICC), Kuala Lumpur, Malaysia, 23–27 May 2016; pp. 193–199. [Google Scholar]
- Marsch, P.; Da Silva, I.; Bulakci, O.; Tesanovic, M.; El Ayoubi, S.E.; Rosowski, T.; Kaloxylos, A.; Boldi, M. 5G Radio Access Network Architecture: Design Guidelines and Key Considerations. IEEE Commun. Mag. 2016, 54, 24–32. [Google Scholar] [CrossRef]
- Agrawal, R.; Bedekar, A.; Kolding, T.; Ram, V. Cloud RAN challenges and solutions. Ann. Telecommun. 2017, 72, 387–400. [Google Scholar] [CrossRef]
- Holma, H.; Toskala, A. LTE Advanced: 3GPP Solution for IMT-Advanced; John Wiley & Sons: Hoboken, NJ, USA, 2012. [Google Scholar]
- Liu, C.; Sundaresan, K.; Jiang, M.; Rangarajan, S.; Chang, G.-K. The case for re-configurable backhaul in cloud-RAN based small cell networks. In Proceedings of the 2013 Proceedings IEEE INFOCOM, Turin, Italy, 14–19 April 2013; pp. 1124–1132. [Google Scholar]
- Werthmann, T.; Grob-Lipski, H.; Proebster, M. Multiplexing gains achieved in pools of baseband computation units in 4G cellular networks. In Proceedings of the 2013 IEEE 24th Annual International Symposium on Personal, Indoor, and Mobile Radio Communications (PIMRC), London, UK, 8–11 September 2013; pp. 3328–3333. [Google Scholar]
- Checko, A.; Holm, H.; Christiansen, H. Optimizing small cell deployment by the use of C-RANs. In Proceedings of the European Wireless 2014; 20th European Wireless Conference, Barcelona, Spain, 14–16 May 2014; pp. 1–6. [Google Scholar]
- Jinling, H. TD-SCDMA/TD-LTE evolution Go Green. In Proceedings of the 2010 IEEE International Conference on Communication Systems, Singapore, 17–19 November 2010; pp. 301–305. [Google Scholar]
- Bansal, M.; Mehlman, J.; Katti, S.; Levis, P. Openradio: A programmable wireless dataplane. In Proceedings of the First Workshop on Hot Topics in Software Defined Networks; ACM: New York, NY, USA, 2012; pp. 109–114. [Google Scholar]
- Yang, K. Interference management in LTE wireless networks [Industry Perspectives]. IEEE Wirel. Commun. 2012, 19, 8–9. [Google Scholar] [CrossRef]
- Beyene, Y.D.; Jantti, R.; Tirkkonen, O.; Ruttik, K.; Iraji, S.; Larmo, A.; Tirronen, T.; Torsner, A.J. NB-IoT Technology Overview and Experience from Cloud-RAN Implementation. IEEE Wirel. Commun. 2017, 24, 26–32. [Google Scholar] [CrossRef]
- Darsena, D.; Gelli, G.; Verde, F. Cloud-Aided Cognitive Ambient Backscatter Wireless Sensor Networks. IEEE Access 2019, 7, 57399–57414. [Google Scholar] [CrossRef]
- Arfaoui, G.; Bisson, P.; Blom, R.; Borgaonkar, R.; Englund, H.; Felix, E.; Klaedtke, F.; Nakarmi, P.K.; Naslund, M.; O’Hanlon, P.; et al. A Security Architecture for 5G Networks. IEEE Access 2018, 6, 22466–22479. [Google Scholar] [CrossRef]
- Ahmad, I.; Kumar, T.; Liyanage, M.; Okwuibe, J.; Ylianttila, M.; Gurtov, A. Overview of 5G Security Challenges and Solutions. IEEE Commun. Stand. Mag. 2018, 2, 36–43. [Google Scholar] [CrossRef]
- Ahmad, I.; Kumar, T.; Liyanage, M.; Okwuibe, J.; Ylianttila, M.; Gurtov, A. 5G security: Analysis of threats and solutions. In Proceedings of the 2017 IEEE Conference on Standards for Communications and Networking (CSCN), Helsinki, Finland, 18–20 September 2017; pp. 193–199. [Google Scholar]
- Namal, S.; Ahmad, I.; Gurtov, A.; Ylianttila, M.; Ahmad, I. SDN Based Inter-Technology Load Balancing Leveraged by Flow Admission Control. In Proceedings of the 2013 IEEE SDN for Future Networks and Services (SDN4FNS), Trento, Italy, 11–13 November 2013; pp. 1–5. [Google Scholar]
- Khan, A.N.; Kiah, M.M.; Khan, S.U.; Madani, S.A. Towards secure mobile cloud computing: A survey. Future Gener. Comput. Syst. 2013, 29, 1278–1299. [Google Scholar] [CrossRef]
- Chonka, A.; Abawajy, J. Detecting and Mitigating HX-DoS Attacks against Cloud Web Services. In Proceedings of the 2012 15th International Conference on Network-Based Information Systems, Melbourne, VIC, Australia, 26–28 September 2012; pp. 429–434. [Google Scholar]
- Namal, S.; Ahmad, I.; Gurtov, A.; Ylianttila, M.; Ahmad, I. Enabling Secure Mobility with OpenFlow. In Proceedings of the 2013 IEEE SDN for Future Networks and Services (SDN4FNS), Trento, Italy, 11–13 November 2013; pp. 1–5. [Google Scholar]
- Zhang, X.; Kunz, A.; Schroder, S. Overview of 5G security in 3GPP. In Proceedings of the 2017 IEEE Conference on Standards for Communications and Networking (CSCN), Helsinki, Finland, 18–20 September 2017; pp. 181–186. [Google Scholar]
- Pan, F.; Wen, H.; Song, H.; Jie, T.; Wang, L. 5G security architecture and light weight security authentication. In Proceedings of the 2015 IEEE/CIC International Conference on Communications in China—Workshops (CIC/ICCC), Shenzhen, China, 2–4 November 2015; pp. 94–98. [Google Scholar]
- Fang, D.; Qian, Y.; Hu, R.Q. Security for 5G Mobile Wireless Networks. IEEE Access 2018, 6, 4850–4874. [Google Scholar] [CrossRef]
- Ahmad, I.; Liyanage, M.; Shahabuddin, S.; Ylianttila, M.; Gurtov, A. Design Principles for 5G Security. In A Comprehensive Guide to 5G Security; Wiley: Hoboken, NJ, USA, 2018; pp. 75–98. [Google Scholar]
- Gao, Y.; Hu, S.; Tang, W.; Li, Y.; Sun, Y.; Huang, D.; Cheng, S.; Li, X. Physical Layer Security in 5G Based Large Scale Social Networks: Opportunities and Challenges. IEEE Access 2018, 6, 26350–26357. [Google Scholar] [CrossRef]
- Wang, N.; Wang, P.; Alipour-Fanid, A.; Jiao, L.; Zeng, K. Physical-Layer Security of 5G Wireless Networks for IoT: Challenges and Opportunities. IEEE Internet Things J. 2019, 6, 8169–8181. [Google Scholar] [CrossRef]
- Wu, Y.; Khisti, A.; Xiao, C.; Caire, G.; Wong, K.-K.; Gao, X. A Survey of Physical Layer Security Techniques for 5G Wireless Networks and Challenges Ahead. IEEE J. Sel. Areas Commun. 2018, 36, 679–695. [Google Scholar] [CrossRef]
- Darsena, D.; Gelli, G.; Iudice, I.; Verde, F. Design and Performance Analysis of Channel Estimators Under Pilot Spoofing Attacks in Multiple-Antenna Systems. IEEE Trans. Inf. Forensics Secur. 2020, 15, 3255–3269. [Google Scholar] [CrossRef]
- Tian, F.; Zhang, P.; Yan, Z. A Survey on C-RAN Security. IEEE Access 2017, 5, 13372–13386. [Google Scholar] [CrossRef]
- Ran, C.; Guo, G. Security XACML access control model based on SOAP encapsulate. In Proceedings of the 2011 International Conference on Computer Science and Service System (CSSS), Nanjing, China, 27–29 June 2011; pp. 2543–2546. [Google Scholar]
- Duan, X.; Wang, X. Authentication handover and privacy protection in 5G hetnets using software-defined networking. IEEE Commun. Mag. 2015, 53, 28–35. [Google Scholar] [CrossRef]
- Yan, S.; Wang, W.-B. Physical layer security strategies for downlink heterogeneous cloud radio access networks. J. China Univ. Posts Telecommun. 2014, 21, 47–54. [Google Scholar] [CrossRef]
- Park, S.-H.; Simeone, O.; Shitz, S.S. Fronthaul quantization as artificial noise for enhanced secret communication in C-RAN. In Proceedings of the 2017 IEEE 18th International Workshop on Signal Processing Advances in Wireless Communications (SPAWC), Sapporo, Japan, 3–6 July 2017; pp. 1–5. [Google Scholar] [CrossRef]
- Xiao, K.; Gong, L.; Kadoch, M. Opportunistic Multicast NOMA with Security Concerns in a 5G Massive MIMO System. IEEE Commun. Mag. 2018, 56, 91–95. [Google Scholar] [CrossRef]
- Wang, L.; Wong, K.-K.; Elkashlan, M.; Nallanathan, A.; Lambotharan, S. Secrecy and Energy Efficiency in Massive MIMO Aided Heterogeneous C-RAN: A New Look at Interference. IEEE J. Sel. Top. Signal Process. 2016, 10, 1375–1389. [Google Scholar] [CrossRef]
- Yupapin, P.; Suwancharoen, W. Chaotic signal generation and cancellation using a micro ring resonator incorporating an optical add/drop multiplexer. Opt. Commun. 2007, 280, 343–350. [Google Scholar] [CrossRef]
- Ikeda, K.; Daido, H.; Akimoto, O. Optical Turbulence: Chaotic Behavior of Transmitted Light from a Ring Cavity. Phys. Rev. Lett. 1980, 45, 709–712. [Google Scholar] [CrossRef]
- Pérez-Jiménez, M.; Sánchez, B.B.; Migliorini, A.; Alcarria, R. Protecting Private Communications in Cyber-Physical Systems through Physical Unclonable Functions. Electronics 2019, 8, 390. [Google Scholar] [CrossRef]
- VanWiggeren, G.D.; Roy, R. Optical Communication with Chaotic Waveforms. Phys. Rev. Lett. 1998, 81, 3547–3550. [Google Scholar] [CrossRef]
- Sciamanna, M.; Shore, K.A. Physics and applications of laser diode chaos. Nat. Photonics 2015, 9, 151–162. [Google Scholar] [CrossRef]
- Virte, M.; Panajotov, K.; Thienpont, H.; Sciamanna, M. Deterministic polarization chaos from a laser diode. Nat. Photonics 2012, 7, 60–65. [Google Scholar] [CrossRef]
- Willner, A. Optical Fiber Telecommunications; Academic Press: London, UK, 2019; Volume 11. [Google Scholar]
- Moussu, R.; Pelletier, F. Sur le théorème de Poincaré-Bendixson. Ann. l’Institut Fourier 1974, 24, 131–148. [Google Scholar] [CrossRef][Green Version]
- Mareca, M.P.; Bordel, B.; Lopez, M.P.M.; Pilar, A. Improving the Complexity of the Lorenz Dynamics. Complexity 2017, 2017. [Google Scholar] [CrossRef]
- Bordel, B.; Alcarria, R. Physical Unclonable Functions based on silicon micro-ring resonators for secure signature delegation in Wireless Sensor Networks. J. Internet Serv. Inf. Secur. 2018, 8, 40–53. [Google Scholar]




| Parameter | Value | Comments |
|---|---|---|
| 0.1 dB | Common commercial value | |
| 1500 nm | Common value | |
| Elemental harmonic signal | ||
| 5 | Common commercial value |
| Parameter | Value | Comments |
|---|---|---|
| 0.1 dB | Common commercial value | |
| 1310 nm | Second optical window | |
| - | Random sequences of bits | |
| 5 | Common commercial value |
© 2020 by the authors. Licensee MDPI, Basel, Switzerland. This article is an open access article distributed under the terms and conditions of the Creative Commons Attribution (CC BY) license (http://creativecommons.org/licenses/by/4.0/).
Share and Cite
Bordel Sánchez, B.; Alcarria, R.; Robles, T.; Jara, A. Protecting Physical Communications in 5G C-RAN Architectures through Resonant Mechanisms in Optical Media. Sensors 2020, 20, 4104. https://doi.org/10.3390/s20154104
Bordel Sánchez B, Alcarria R, Robles T, Jara A. Protecting Physical Communications in 5G C-RAN Architectures through Resonant Mechanisms in Optical Media. Sensors. 2020; 20(15):4104. https://doi.org/10.3390/s20154104
Chicago/Turabian StyleBordel Sánchez, Borja, Ramón Alcarria, Tomás Robles, and Antonio Jara. 2020. "Protecting Physical Communications in 5G C-RAN Architectures through Resonant Mechanisms in Optical Media" Sensors 20, no. 15: 4104. https://doi.org/10.3390/s20154104
APA StyleBordel Sánchez, B., Alcarria, R., Robles, T., & Jara, A. (2020). Protecting Physical Communications in 5G C-RAN Architectures through Resonant Mechanisms in Optical Media. Sensors, 20(15), 4104. https://doi.org/10.3390/s20154104








