DYNASTI—Dynamic Multiple RPL Instances for Multiple IoT Applications in Smart City
Abstract
1. Introduction
- Limiting a single instance per application and no flexibility of instances management. As a result of this, the instances are statics. In other words, it means that each application is associated with a single routing metric and a single interval between application messages throughout the application lifetime on the network, since the applications are associated with a single instance. If the applications could associate to multiple instances, this flexibility would improve the service differentiation for each kind of applications, since each application could be adapted its traffic class.
- Sporadic applications that eventually send messages are not supported. It is important to emphasise that the RPL control and applications messages are currently generated and sent at regular intervals throughout the lifetime of the network. The related work implementations do not reflect a network with different traffic patterns.
- Multiple instances performing occurs alternately: one single instance each time. When one instance is communicating, the remainder instances are in wait mode in a First In First Out (FIFO) queue. Thus, there is no way to prioritize instances. This aspect makes very difficult to support applications with different levels of critical requirements such as delay.
- Support to sporadic applications.
- Implementation of concurrency between multiple instances.
- Providing more dynamic and flexible applications, allowing each application to have different instances over time.
- Adapting to more critical and sporadic applications that eventually can run on the network (service differentiation between applications with critical requirements).
- Interruption and adjustment of control and application message transmissions.
2. RPL Background
3. Related Work
- Metric: Which metrics were used to generate the results.
- Number of instances per application: Number of instances per application.
- Service differentiation for applications: Modified instance settings, for instance routing metric, to prioritize applications.
- Traffic Pattern: Existence of sending messages in different patterns.
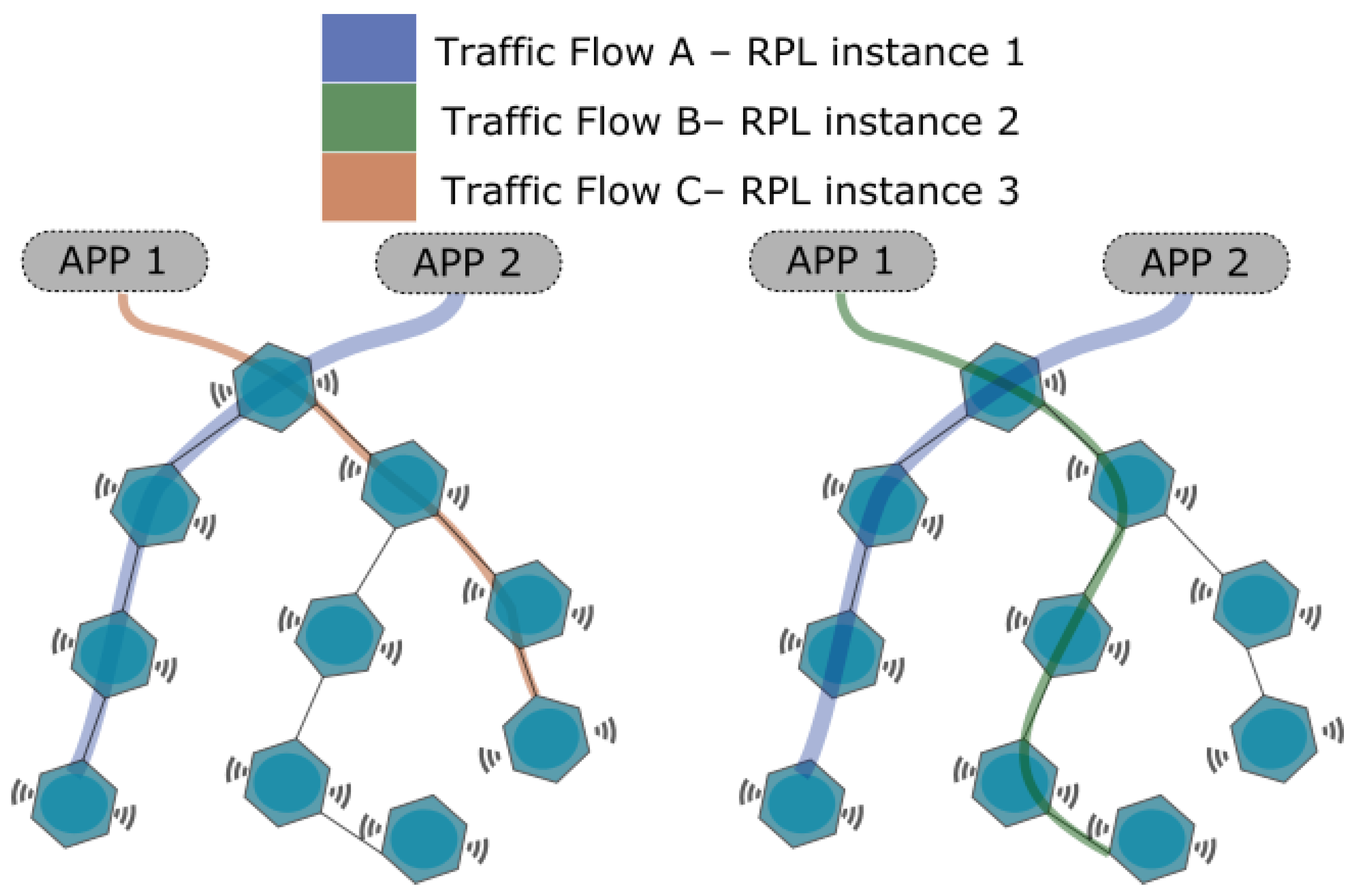
4. DYNAmic Multiple RPL Instances for Multiple IoT ApplicatIons (DYNASTI)
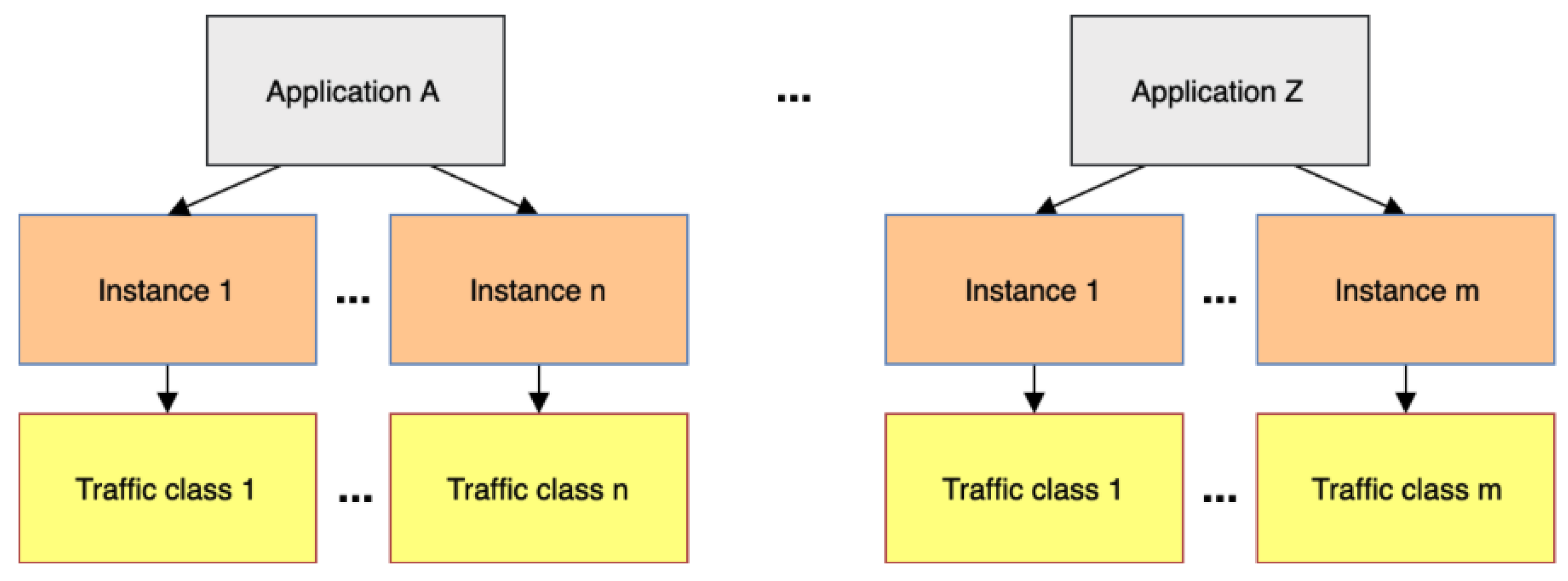
4.1. Concepts and Definitions: Applications, Traffic Classes, and RPL Instances
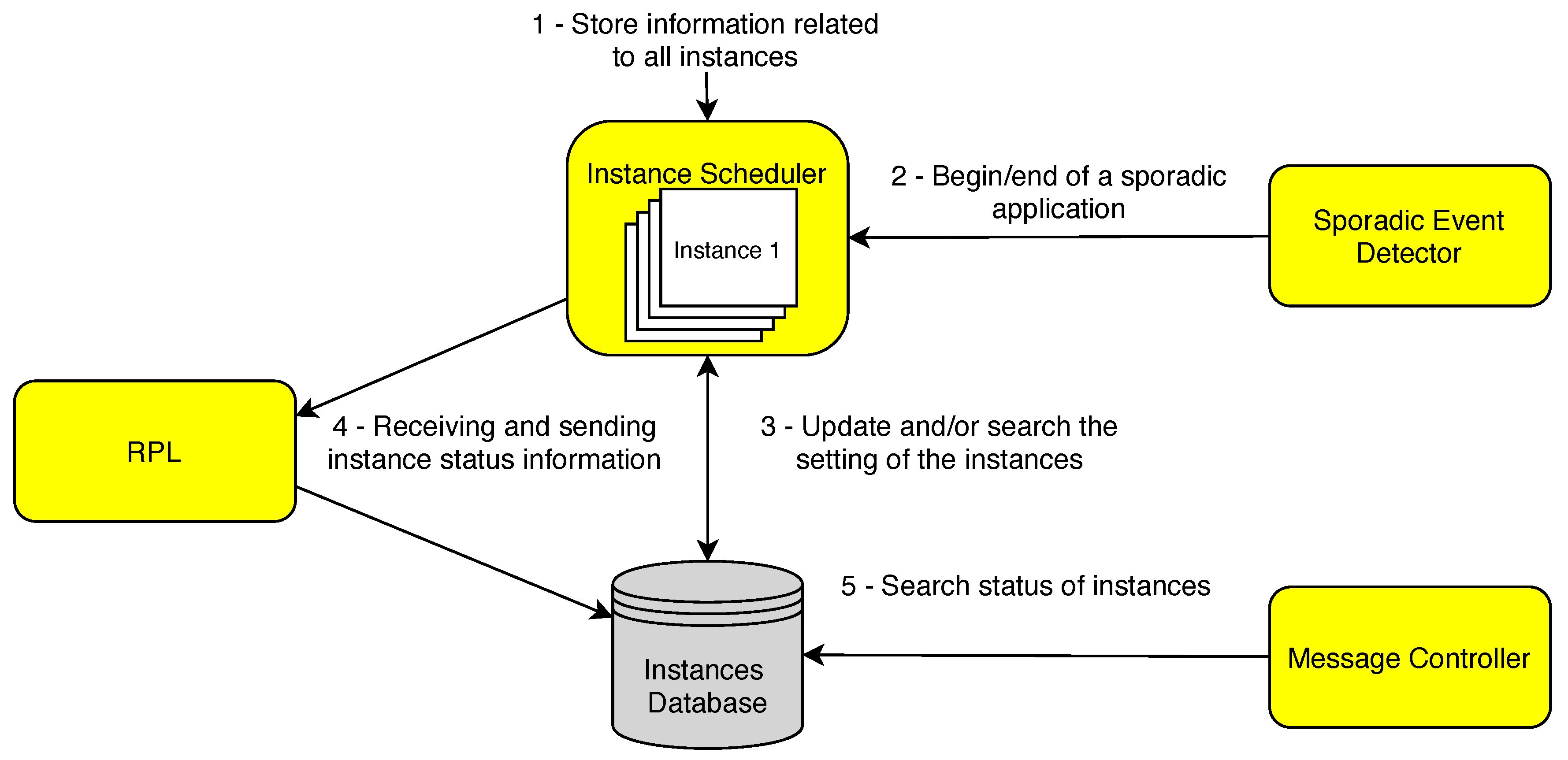
4.2. DYNASTI Architecture
- Instance Scheduler.
- Sporadic Event Detector.
- Instances Database.
- Message Controller.
- RPL.
4.3. Instance Scheduler
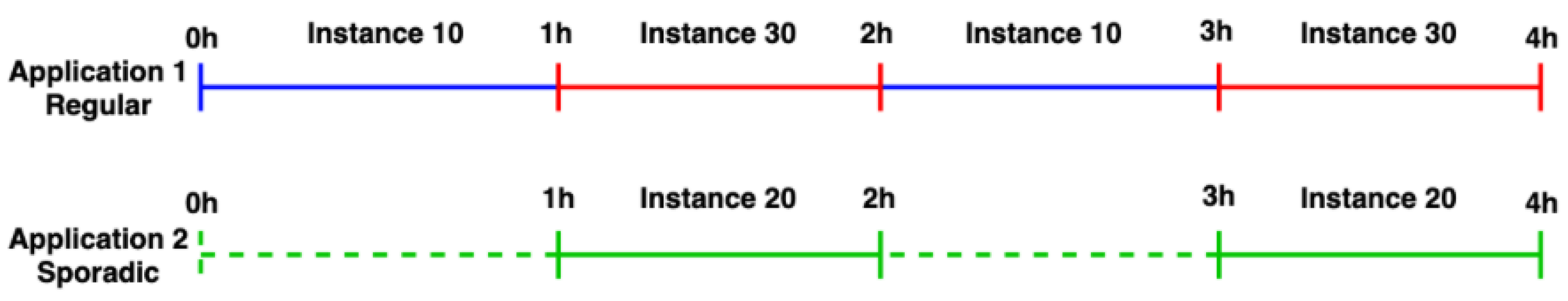
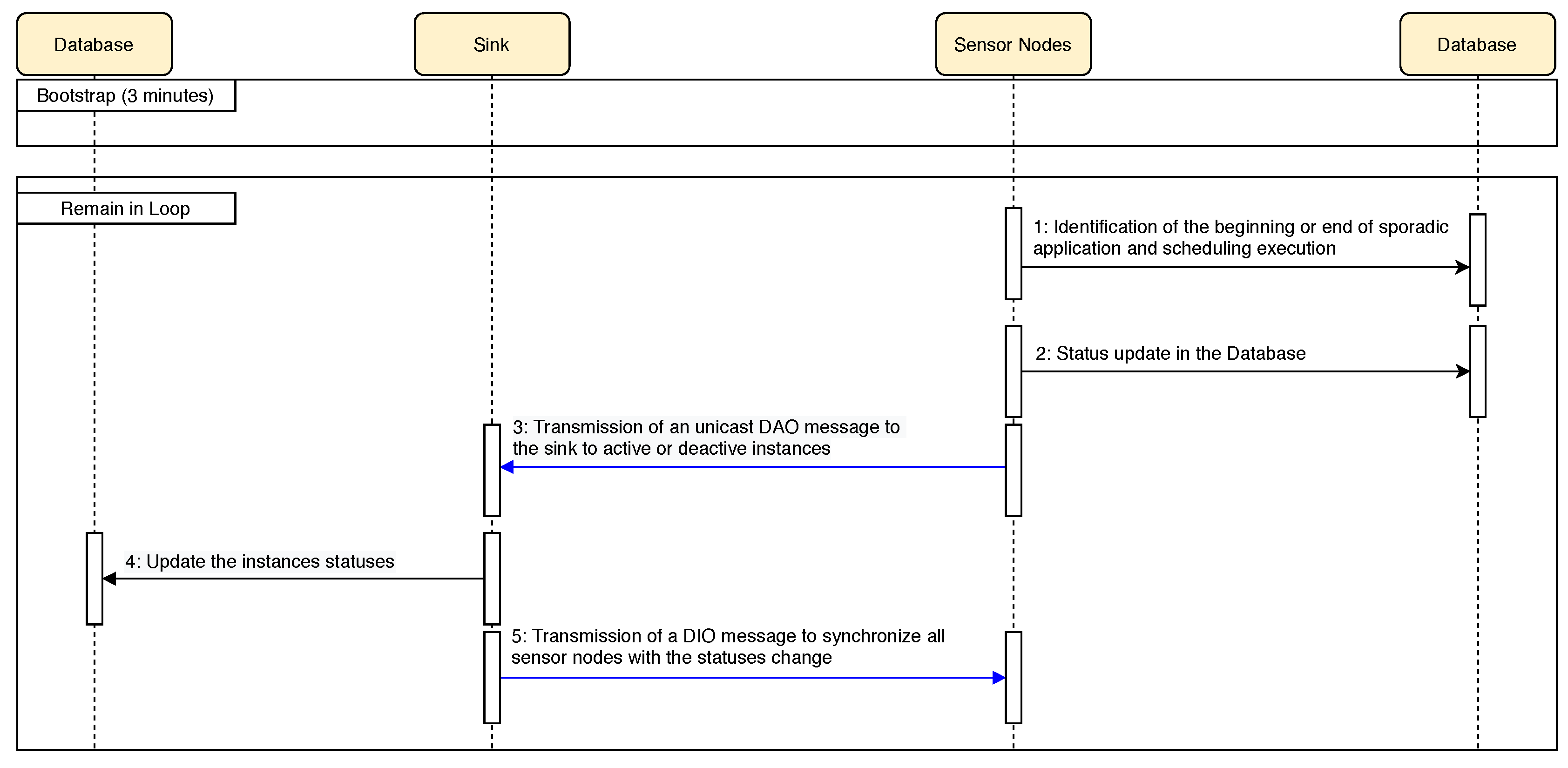
4.4. Dissemination and Storing Information of RPL Instance Scheduling
- Status 1: Instance communicates only control messages.
- Status 2: Instance communicates both control and application messages.
- Status 3: Instance is deactivated, it does not communicate control or application messages.
4.5. Implementation Notes
5. Performance Evaluation and Results
5.1. Network Configuration Environment
5.2. Performance Metrics
5.3. Application Scenario
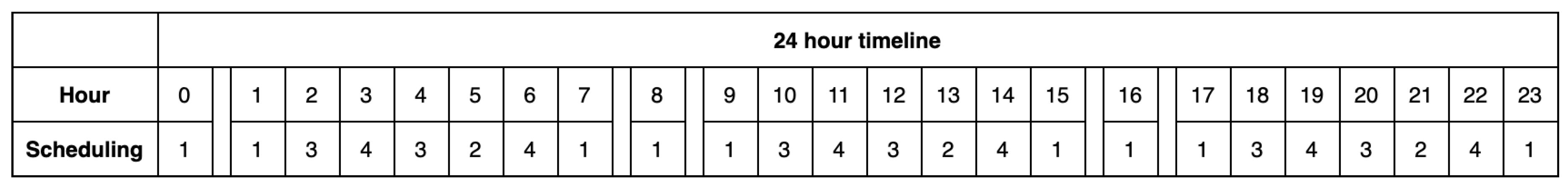
5.4. Selection of the Scheduling of Instances
5.5. Results
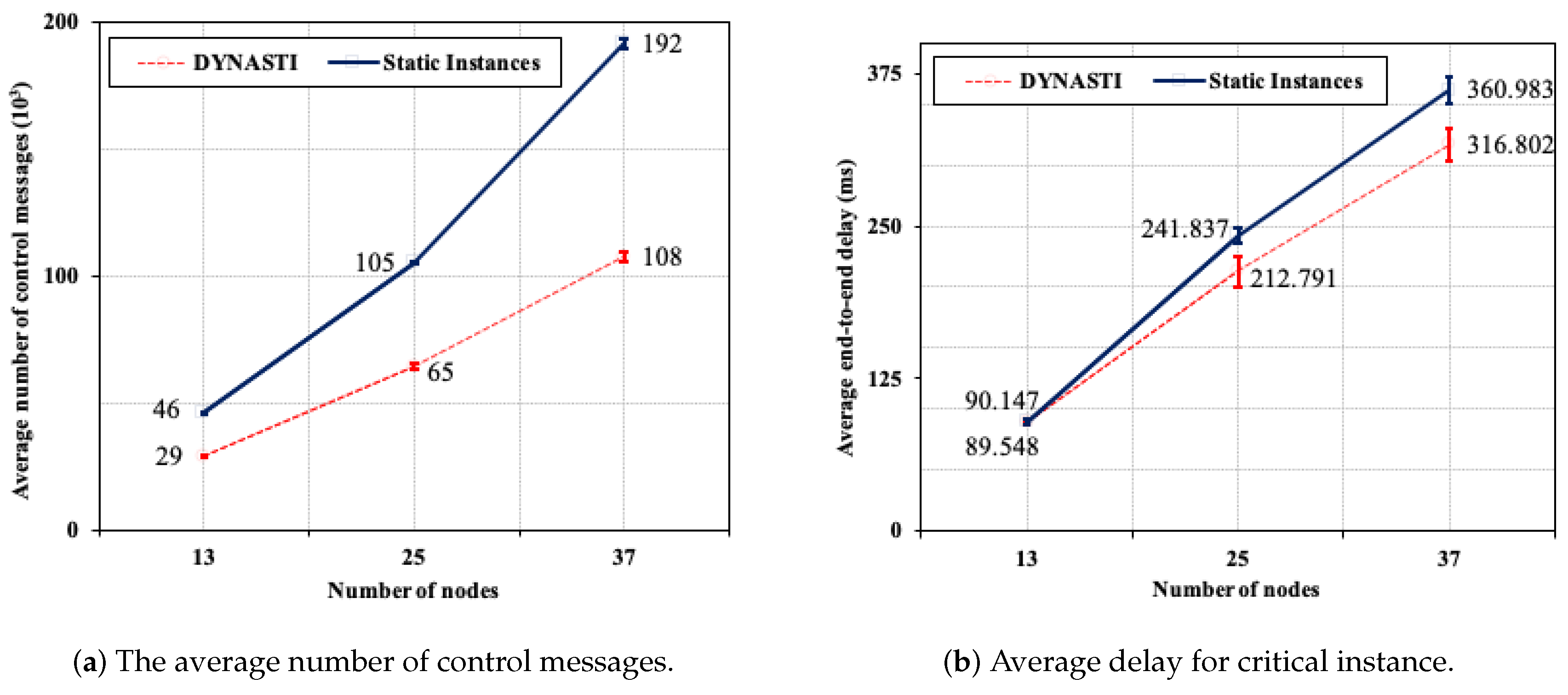
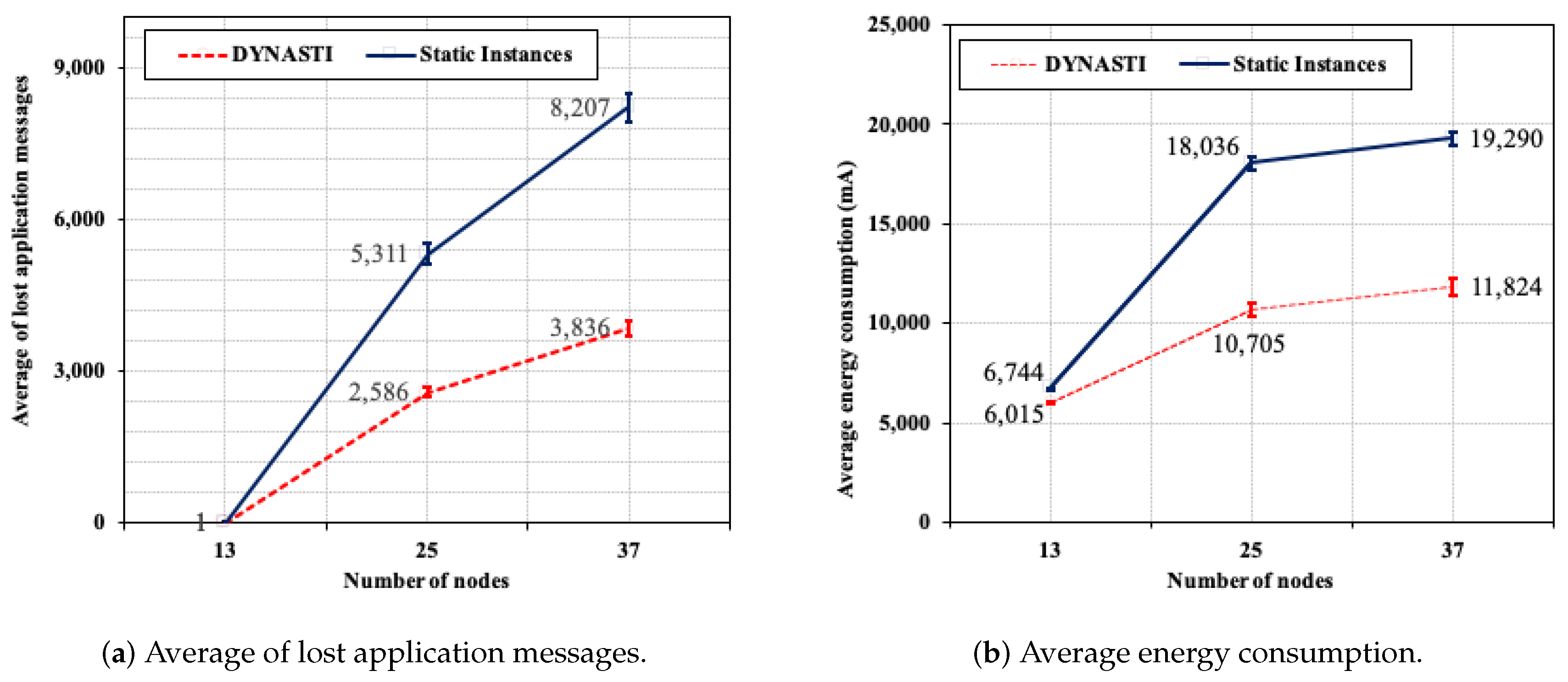
5.5.1. Varying the Number of Nodes
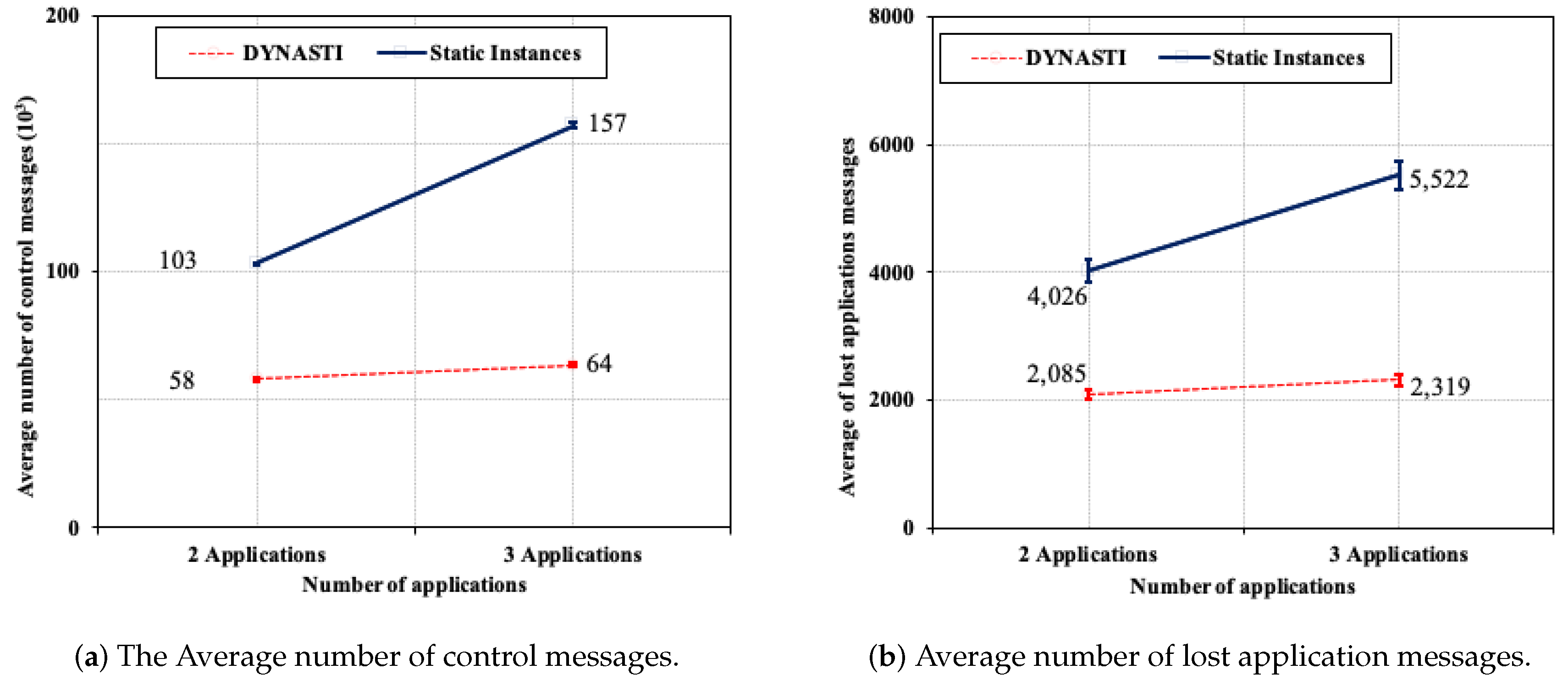
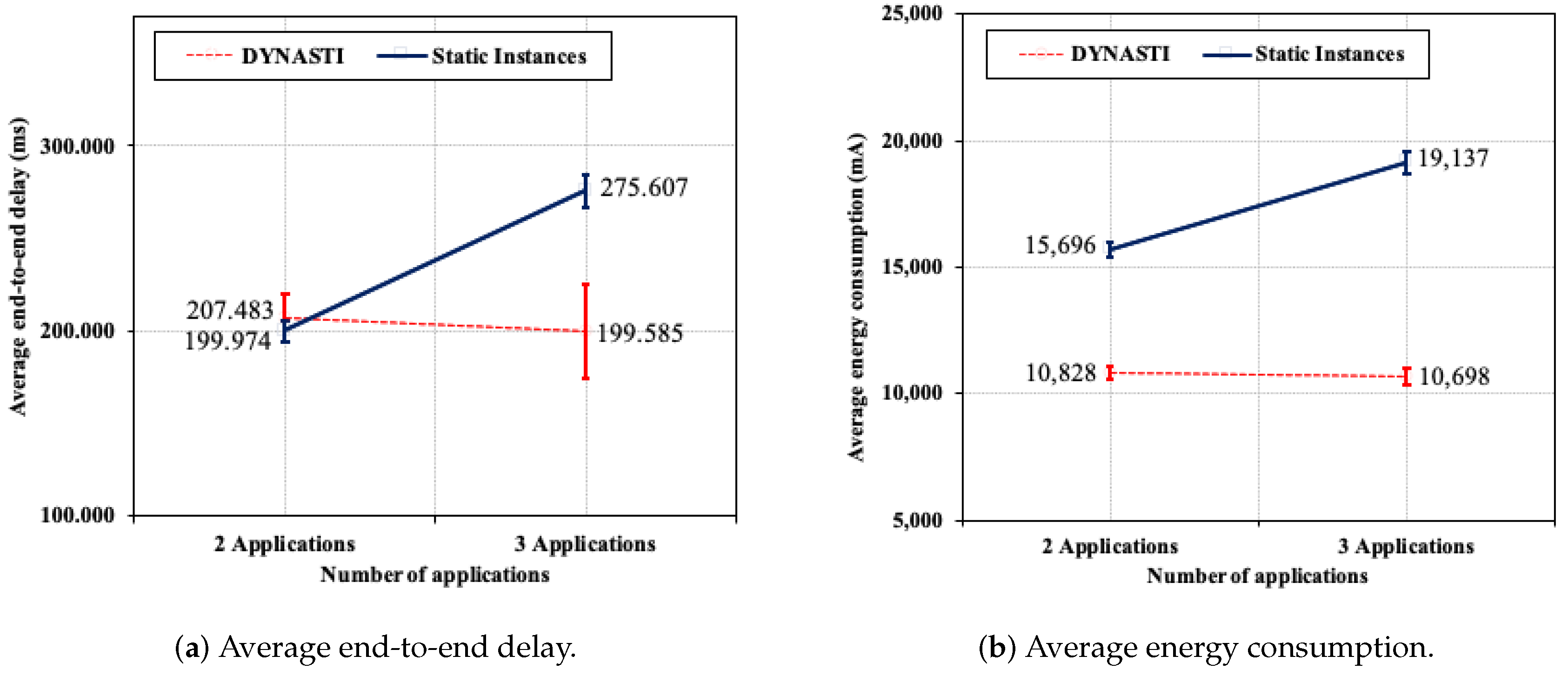
5.5.2. Varying the Number of Applications
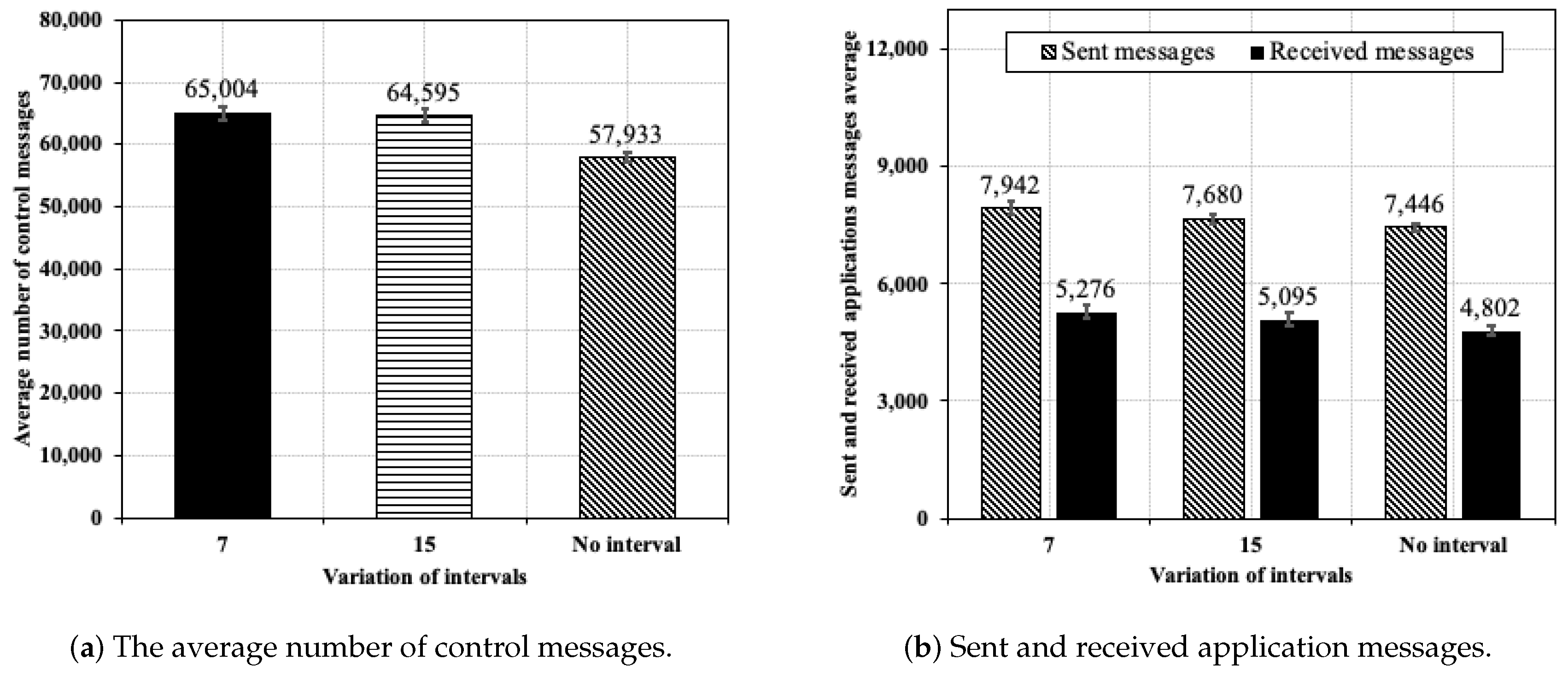
5.5.3. Varying the Application Message Send Intervals
5.5.4. Results Summary
6. Conclusions and Future Work
Author Contributions
Funding
Conflicts of Interest
References
- Hammi, B.; Khatoun, R.; Zeadally, S.; Fayad, A.; Khoukhi, L. IoT technologies for smart cities. IET Netw. 2018, 7, 1–13. [Google Scholar] [CrossRef]
- Alsaig, A.; Alagar, V.; Chammaa, Z.; Shiri, N. Characterization and Efficient Management of Big Data in IoT-Driven Smart City Development. Sensors 2019, 19, 2430. [Google Scholar] [CrossRef] [PubMed]
- Al-Fuqaha, A.; Guizani, M.; Mohammadi, M.; Aledhari, M.; Ayyash, M. Internet of Things: A Survey on Enabling Technologies, Protocols, and Applications. IEEE Commun. Surv. Tutor. 2015, 17, 2347–2376. [Google Scholar] [CrossRef]
- Amah, T.E.; Kamat, M.; Bakar, K.A.; Moreira, W.; Oliveira, A.; Batista, M.A. Preparing opportunistic networks for smart cities: Collecting sensed data with minimal knowledge. J. Parallel Distrib. Comput. 2020, 135, 21–55. [Google Scholar] [CrossRef]
- Vejlgaard, B.; Lauridsen, M.; Nguyen, H.; Kovacs, I.Z.; Mogensen, P.; Sorensen, M. Coverage and Capacity Analysis of Sigfox, LoRa, GPRS, and NB-IoT. In Proceedings of the 2017 IEEE 85th Vehicular Technology Conference (VTC Spring), Sydney, Australia, 4–7 June 2017; pp. 1–5. [Google Scholar]
- Ratasuk, R.; Vejlgaard, B.; Mangalvedhe, N.; Ghosh, A. NB-IoT system for M2M communication. In Proceedings of the 2016 IEEE Wireless Communications and Networking Conference, Doha, Qatar, 3–6 April 2016; pp. 1–5. [Google Scholar]
- Latre, S.; Leroux, P.; Coenen, T.; Braem, B.; Ballon, P.; Demeester, P. City of things: An integrated and multi-technology testbed for IoT smart city experiments. In Proceedings of the 2016 IEEE International Smart Cities Conference (ISC2), Trento, Italy, 12–15 September 2016; pp. 1–8. [Google Scholar]
- Pasetti, M.; Sisinni, E.; Ferrari, P.; Rinaldi, S.; Depari, A.; Bellagente, P.; Della Giustina, D.; Flammini, A. Evaluation of the Use of Class B LoRaWAN for the Coordination of Distributed Interface Protection Systems in Smart Grids. J. Sens. Actuator Netw. 2020, 9, 13. [Google Scholar] [CrossRef]
- Kuzlu, M.; Pipattanasomporn, M.; Rahman, S. Communication network requirements for major smart grid applications in HAN, NAN and WAN. Comput. Netw. 2014, 67, 74–88. [Google Scholar] [CrossRef]
- Cam-Winget, N.; Hui, J.; Popa, D. Applicability Statement for the Routing Protocol for Low-Power and Lossy Networks (RPL) in Advanced Metering Infrastructure (AMI) Networks; RFC 8036; Internet Engineering Task Force: Fremont, CA, USA, 2017. [Google Scholar] [CrossRef]
- Khanna, A.; Anand, R. IoT based smart parking system. In Proceedings of the 2016 International Conference on Internet of Things and Applications (IOTA), Pune, India, 22–24 January 2016. [Google Scholar] [CrossRef]
- Xu, S.; Qian, Y.; Hu, R.Q. On Reliability of Smart Grid Neighborhood Area Networks. IEEE Access 2015, 3, 2352–2365. [Google Scholar] [CrossRef]
- Oliveira-Jr, A.; Resende, C.; Gonçalves, J.; Soares, F.; Moreira, W. IoT Sensing Platform for e-Agriculture in Africa. In Proceedings of the 2020 IST-Africa Week Conference (IST-Africa), Kampala, Uganda, 1–8 May 2020. [Google Scholar]
- Davito, B.; Tai, H.; Uhlaner, R. The smart grid and the promise of demand-side management. Mckinsey Smart Grid 2010, 3, 8–44. [Google Scholar]
- Budka, K.C.; Deshpande, J.G.; Doumi, T.L.; Madden, M.; Mew, T. Communication network architecture and design principles for smart grids. Bell Labs Tech. J. 2010, 15, 205–227. [Google Scholar] [CrossRef]
- Taxonomy, B.S.G. A System View from a Grid Operator’s Perspective. 2015, Volume 84. Available online: http://www.bkw.ch/fileadmin/user_upload/3_Gemeinden_EVU/gem_smart_grid_systematik_en.pdf (accessed on 10 May 2020).
- Delphinanto, A.; Koonen, T.; den Hartog, F. End-to-end available bandwidth probing in heterogeneous IP home networks. In Proceedings of the 2011 IEEE Consumer Communications and Networking Conference (CCNC), Las Vegas, NV, USA, 9–12 January 2011. [Google Scholar] [CrossRef]
- Sobral, J.V.V.; Rodrigues, J.J.P.C.; Rabêlo, R.A.L.; Al-Muhtadi, J.; Korotaev, V. Routing Protocols for Low Power and Lossy Networks in Internet of Things Applications. Sensors 2019, 19, 2144. [Google Scholar] [CrossRef] [PubMed]
- Watteyne, T.; Winter, T.; Barthel, D.; Dohler, M. Routing Requirements for Urban Low-Power and Lossy Networks; RFC 5548; Internet Engineering Task Force: Fremont, CA, USA, 2009. [Google Scholar] [CrossRef]
- Alexander, R.; Brandt, A.; Vasseur, J.; Hui, J.; Pister, K.; Thubert, P.; Levis, P.; Struik, R.; Kelsey, R.; Winter, T. RPL: IPv6 Routing Protocol for Low-Power and Lossy Networks; RFC 6550; Internet Engineering Task Force: Fremont, CA, USA, 2012. [Google Scholar] [CrossRef]
- Nassar, J.; Gouvy, N.; Mitton, N. Towards Multi-instances QoS Efficient RPL for Smart Grids. In Proceedings of the 14th ACM Symposium on Performance Evaluation of Wireless Ad Hoc, Sensor, & Ubiquitous Networks—PE-WASUN ’17, Miami, FL, USA, 21–25 November 2017. [Google Scholar] [CrossRef]
- Nassar, J.; Berthomé, M.; Dubrulle, J.; Gouvy, N.; Mitton, N.; Quoitin, B. Multiple Instances QoS Routing in RPL: Application to Smart Grids. Sensors 2018, 18, 2472. [Google Scholar] [CrossRef] [PubMed]
- Long, N.T.; Uwase, M.P.; Tiberghien, J.; Steenhaut, K. QoS-aware cross-layer mechanism for multiple instances RPL. In Proceedings of the 2013 International Conference on Advanced Technologies for Communications (ATC 2013), Phoenix Park, PyeongChang, Korea, 27–30 January 2013. [Google Scholar] [CrossRef]
- Rajalingham, G.; Gao, Y.; Ho, Q.D.; Le-Ngoc, T. Quality of service differentiation for smart grid neighbor area networks through multiple RPL instances. In Proceedings of the 10th ACM Symposium on QoS and Security for Wireless and Mobile Networks—Q2SWinet’ 14, Montréal, QC, Canada, 21–22 September 2014. [Google Scholar] [CrossRef]
- Banh, M.; Mac, H.; Nguyen, N.; Phung, K.H.; Thanh, N.H.; Steenhaut, K. Performance evaluation of multiple RPL routing tree instances for Internet of Things applications. In Proceedings of the 2015 International Conference on Advanced Technologies for Communications (ATC), Ho Chi Minh City, Vietnam, 14–16 October 2015. [Google Scholar] [CrossRef]
- Barcelo, M.; Correa, A.; Vicario, J.L.; Morell, A. Cooperative interaction among multiple RPL instances in wireless sensor networks. Comput. Commun. 2016, 81, 61–71. [Google Scholar] [CrossRef]
- Sehgal, A. Using the Contiki Cooja Simulator; Technical Report; Jacobs University: Bremen, Germany, October 2013. [Google Scholar]
- Österlind, F. A Sensor Network Simulator for the Contiki OS; SICS Technical Report, T2006:05; Swedish Institute of Computer Science (SICS): Kista, Sweden, February 2006. [Google Scholar]
- Winter, T.; Thubert, A.B.P.; Clausen, T.; Hui, J.; Kelsey, R.; Levis, P.; Pister, K.; Struik, R.; Vasseur, J. RPL: IPv6 Routing Protocol for Low Power and Lossy Networks, (RFC 6550); IETF ROLL WG, Tech. Rep; Internet Engineering Task Force: Fremont, CA, USA, 2012. [Google Scholar]
- De Couto, D.S.; Aguayo, D.; Bicket, J.; Morris, R. A high-throughput path metric for multi-hop wireless routing. In Proceedings of the 9th Annual International Conference on Mobile Computing and Networking, San Diego, CA, USA, 14–19 September 2003; pp. 134–146. [Google Scholar]
- Thubert, P. Objective Function Zero for the Routing Protocol for Low-Power and Lossy Networks (RPL); RFC 6552; Internet Engineering Task Force: Fremont, CA, USA, 2012. [Google Scholar] [CrossRef]
- Junior, S.A. DYNASTI Implementation. Github. 2020. Available online: https://github.com/SidneiJuniorx/contiki-dynasti (accessed on 10 May 2020).
- Riker, A.; Curado, M.; Monteiro, E. Neutral Operation of the Minimum Energy Node in energy-harvesting environments. In Proceedings of the 2017 IEEE Symposium on Computers and Communications (ISCC), Heraklion, Greece, 3–6 July 2017. [Google Scholar] [CrossRef]
- Varghese, B.; John, N.E.; Sreelal, S.; Gopal, K. Design and development of an RF energy harvesting wireless sensor node (EH-WSN) for aerospace applications. Procedia Comput. Sci. 2016, 93, 230–237. [Google Scholar] [CrossRef]


| Approach | Metric | Number of Instances Per Application | Differentiation of Services for Applications | Traffic Pattern |
|---|---|---|---|---|
| Long et al. [23] | ETX | 1 | No | Regular |
| Rajalingham et al. [24] | ETX e HC | 1 | No | Regular |
| Banh et al. [25] | ETX e HC | 1 | No | Regular |
| Barcelo et al. [26] | ETX, PDR e HC | 1 | Yes | Regular |
| Nassar et al. [21,22] | mOFQS | 1 | Yes | Regular |
| DYNASTI | Multiple Metrics | multiple | Yes | Regular and Sporadic |
| Parameters | Values |
|---|---|
| Initial Residual Energy | 80.000 mA |
| Routing Metric | ETX |
| Control Messages Length (DIO e DAO) | 4 bytes |
| Application Message Payload | 40 bytes |
| Sensor Actuator | WiSMote |
| Simulation Time | 24 h |
| PHY layer | IEEE 802.15.4 |
| MAC layer | ContikiMac |
| Microcontroler | MSP430 |
| Transceiver | CC2520 |
| RAM memory | 768 bytes |
| Processor Clock | 1–16 MHz |
| Maximum transmission rate | 250 kbps |
| Application | Instance | Traffic Pattern | Traffic Type | Messages Interval | Scheduling |
|---|---|---|---|---|---|
| 1 | 10 | Regular | Normal | 5 min | 1 |
| 1 | 30 | Regular | Normal | 15 min | 2 |
| 2 | 20 | Sporadic | Critical | 3 min | 2 |
| Application | Instance | Traffic Pattern | Traffic Type | Messages Interval | Scheduling |
|---|---|---|---|---|---|
| 1 | 10 | Regular | Normal | 7 | 3,4,5,6 |
| 2 | 20 | Sporadic | Critical | 5 | 4,6 |
| 3 | 30 | Sporadic | Critical | 3 | 5,6 |
| Application | Instance | Traffic Pattern | Traffic Type | Messages Interval | Scheduling |
|---|---|---|---|---|---|
| 1 | 10 | Regular | Normal | 7 | 7,8 |
| 2 | 20 | Sporadic | Critical | 3 | 8 |
| Application | Instance | Traffic Pattern | Traffic Type | Messages Interval | Scheduling |
|---|---|---|---|---|---|
| 1 | 10 | Regular | Normal | 5 | 9 |
| 1 | 30 | Regular | Normal | 7 or 15 | 10 |
| 2 | 20 | Sporadic | Critical | 3 | 10 |
| Application | Instance | Traffic Pattern | Traffic Type | Messages Interval | Scheduling |
|---|---|---|---|---|---|
| 1 | 10 | Regular | Normal | 5 | 11, 12 |
| 2 | 20 | Sporadic | Critical | 3 | 12 |
© 2020 by the authors. Licensee MDPI, Basel, Switzerland. This article is an open access article distributed under the terms and conditions of the Creative Commons Attribution (CC BY) license (http://creativecommons.org/licenses/by/4.0/).
Share and Cite
Junior, S.; Riker, A.; Silvestre, B.; Moreira, W.; Oliveira-Jr, A.; Borges, V. DYNASTI—Dynamic Multiple RPL Instances for Multiple IoT Applications in Smart City. Sensors 2020, 20, 3130. https://doi.org/10.3390/s20113130
Junior S, Riker A, Silvestre B, Moreira W, Oliveira-Jr A, Borges V. DYNASTI—Dynamic Multiple RPL Instances for Multiple IoT Applications in Smart City. Sensors. 2020; 20(11):3130. https://doi.org/10.3390/s20113130
Chicago/Turabian StyleJunior, Sidnei, André Riker, Bruno Silvestre, Waldir Moreira, Antonio Oliveira-Jr, and Vinicius Borges. 2020. "DYNASTI—Dynamic Multiple RPL Instances for Multiple IoT Applications in Smart City" Sensors 20, no. 11: 3130. https://doi.org/10.3390/s20113130
APA StyleJunior, S., Riker, A., Silvestre, B., Moreira, W., Oliveira-Jr, A., & Borges, V. (2020). DYNASTI—Dynamic Multiple RPL Instances for Multiple IoT Applications in Smart City. Sensors, 20(11), 3130. https://doi.org/10.3390/s20113130







