Emulating and Evaluating Virtual Remote Laboratories for Cybersecurity †
Abstract
1. Introduction
2. State of the Art
3. Methodology
3.1. Instruments and Demography
3.2. Educational Contextualization
- Capacity for strategic planning, development, management, coordination, and technical and economic management in the fields of Computer Science Engineering, among others, with: systems, applications, services, networks, or computer facilities and software development centers or factories, respecting the adequate fulfillment of quality and environmental criteria and in multidisciplinary work environments.
- Ability to design, develop, manage and evaluate mechanisms for certification and guarantee of cybersecurity in the treatment and access to information in a local or distributed processing system.
- LR1. Understand advanced concepts of cybersecurity in the treatment and access of data.
- LR2. Know advanced mechanisms of certification and guarantee of cybersecurity.
- LR3. Understand challenges and cybersecurity solutions of within the context of the Internet.
- LR4. Design, development, and management of cybersecurity mechanisms.
- Advanced design of a cybersecurity program. In this unit, students are introduced to the cybersecurity programs within the Information Security Management Systems (ISMS). In particular, the fundamental concepts of ISO–27001 standard is introduced, which allow us to develop a successful safety program. This standard is also compared to other existing ones in the literature. The primary objective of any cybersecurity program is to mitigate the risks that may occur within the organization by implementing this program. The mitigation concept does not consist of eliminating them, but reducing them to an acceptable level, taking into account various economic, social, structural parameters, etc. To ensure that the cybersecurity elements deployed in an organization control the risks, it will be necessary to anticipate the incidents that may arise, through the various techniques of risk analysis.
- Advanced cybersecurity models in information systems. Modern cybersecurity products are designed to strike a balance between the needs of businesses on the Internet. Within this unit, we will offer an initial vision of the latest technologies that allow future cybersecurity professionals to take into account the most modern threats in the design of their cybersecurity programs.
- Management of cybersecurity operations. We will focus on the metrics and Key Performance Indicators (KPIs) that we can use to monitor compliance. These measures, being some qualitative and others quantitative, allow us to determine how close we are to fulfill a cybersecurity program in the organization in terms of time, costs, percentages, and so on. These metrics and KPIs refer to the performance of security policies (incidents, vulnerabilities, updating, configurations, changes …), which are not related to the psychological factors studied and analyzed in the paper.A cybersecurity program is not a static process, but will undergo several changes over time, offering improvements. We will also deal with change management and its documentation in this module. We also describe the creation of controls that verify when the cybersecurity program is fulfilled or not within our ISMS. Methodologies that allow us to verify compliance with the cybersecurity program as the guide that the ISO–27001 standard offers us through these controls are detailed.
- Monitoring, recovery, and response to vulnerabilities. Within this unit, we will concentrate on the monitoring of the cybersecurity of our systems, as well as its audit. This procedure should indicate to the administrators of the system that operates in an expected manner, where the faults are located, as well as the load supported by the system. It also allows to expose suspicious activities, audit trails of system use, as well as forensic evidence that is useful in the subsequent diagnosis of attacks. On the other hand, the unit focus on the practices necessary to provide the services offered by the organization reliability and recovery. It also address issues related to advanced backup schemes in a recovery scenario, as well as high availability of the services of the organization to ensure its continuity of operation.
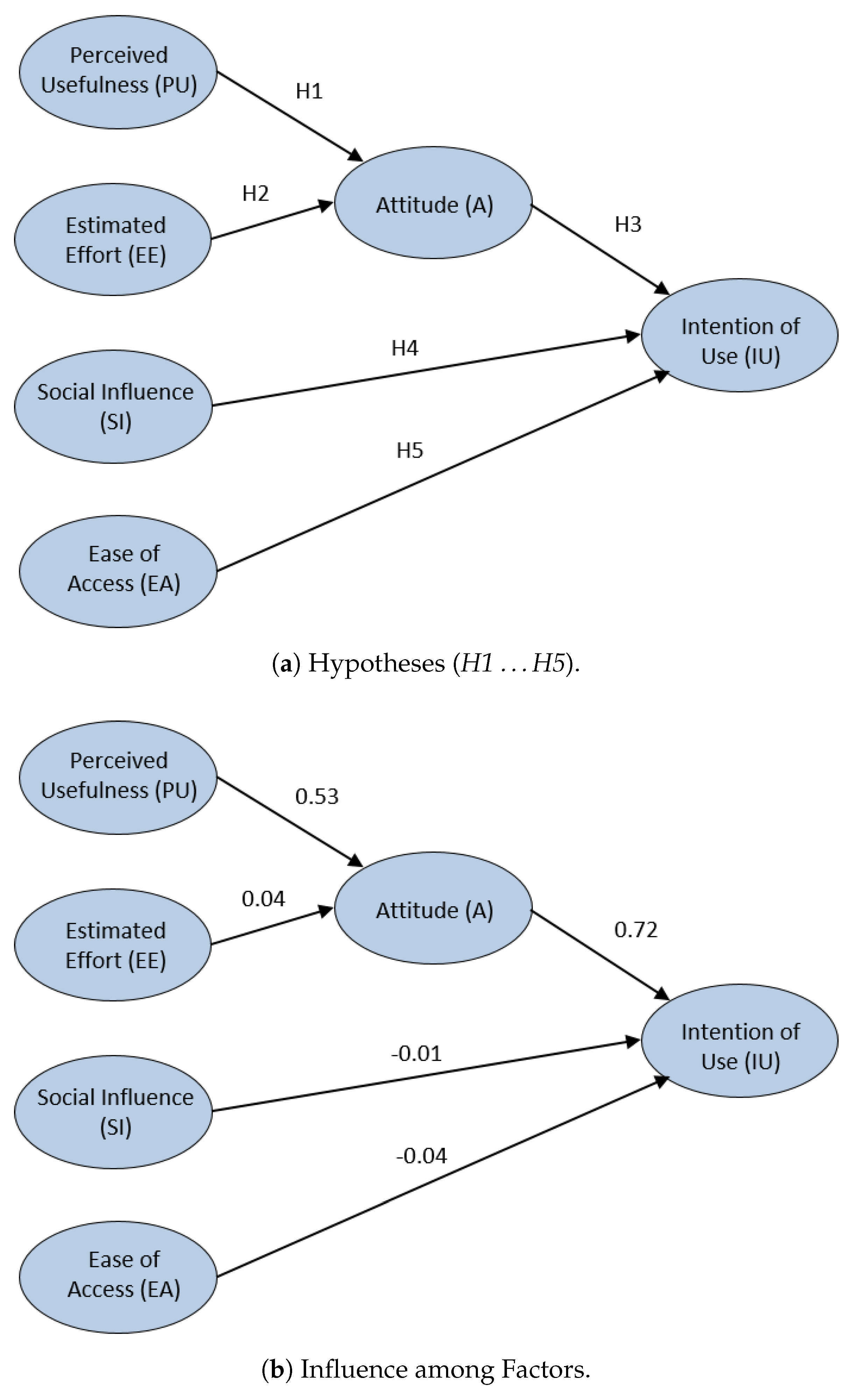
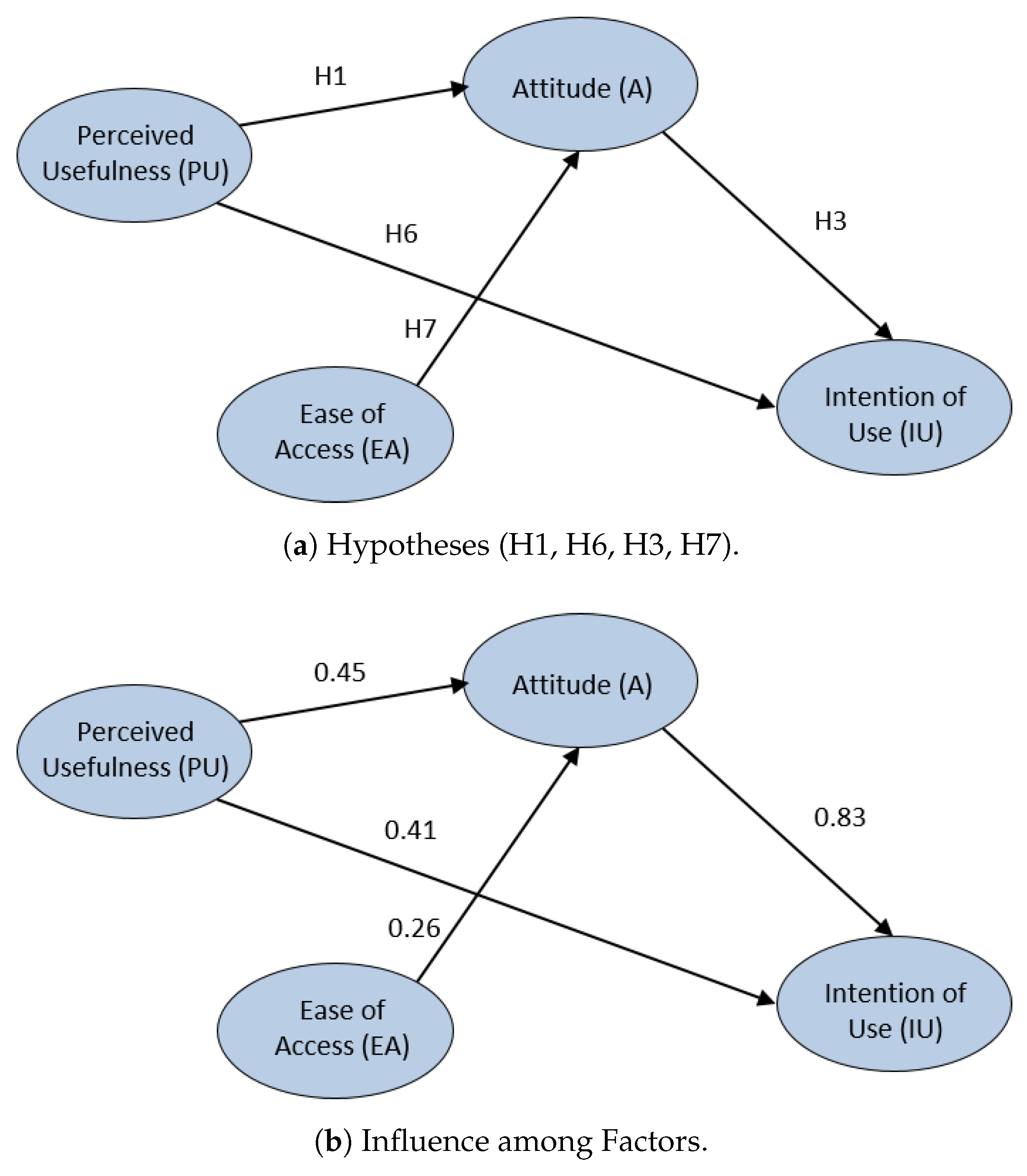
3.3. Initial Hypotheses
4. Emulating Virtual Remote Laboratories in the Cloud
4.1. Creation of the EVE-NG Virtual Environment
- Obtaining the virtualization software and remote connection tools. The virtualization software can be based on Virtual Box, VMware, Docker containers, or a similar virtualization technology. Additionally, remote connection tools will be useful to graphically access the virtualization resources located in the EVE-NG environment, such as Telnet, VNS, among others. These tools have to be installed into the network infrastructure where hosted the virtualized EVE-NG environment.
- Creation of the emulated virtual environment with EVE-NG. It is necessary to download and install the virtualized EVE-NG core within the network infrastructure as the principal virtual resource, which controls all resources. For instance, virtualization could be based on a VMWare ESXi server.
- Updating access and configuration permissions. All the access permissions to the network interfaces have to be specified according to the pre-established access policy. The same happens with the interface configuration files. These permissions can be updated later.
- Adding the required virtual resources to the EVE-NG environment. The desired images and VMs for emulating the different devices of the network scenarios have to be incorporated to the virtualization server. This fact depends on the concrete scenarios defined for the practical activities of the subjects. The set of available resources can dynamically be updated later.
- Starting the EVE-NG core and deploying an automatic setup script. Once the emulated EVE-NG environment is created, this platform has to be restarted with a concrete configuration, as well as a set of scripting lines to automatically re-init system correctly when it fails, turns off, etc. With this technology, real and emulated devices can be mixed at the same time.
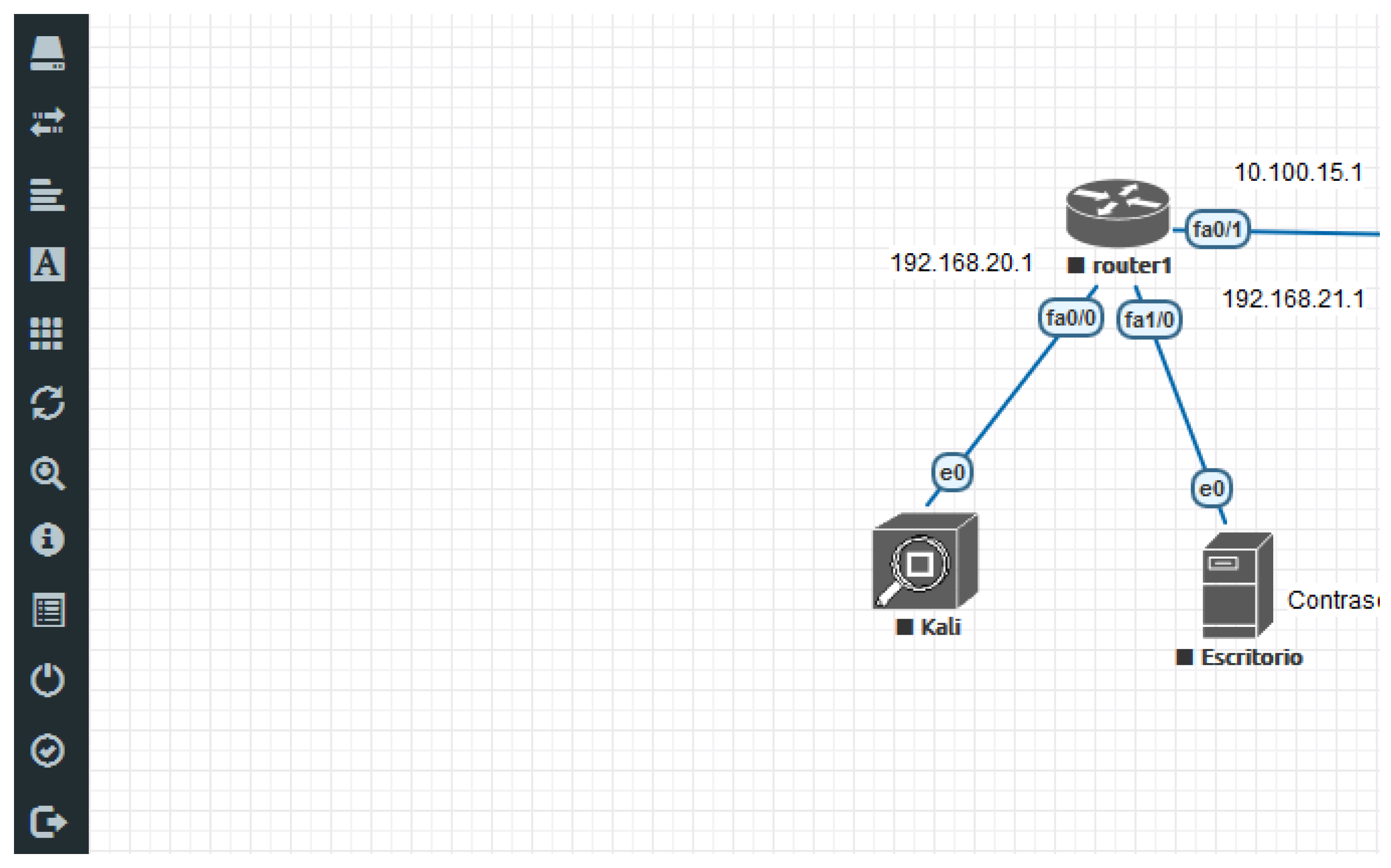
- Defining practical scenarios for the corresponding subjects. A set of sample scenarios have to be defined and tested prior to deployment for production purposes. As an example, Figure 1 represents a part of a virtual laboratory with a network facility defined in ViRe-Lab for audit purposes. In particular, there is an access point for the auditor, another machine with a set of audit tools (available in a Kali Linux distribution), and a local router connected to the access point and Kali. Prior to enter the laboratory, but not shown here, the user finds information about the own working laboratory and some guidelines about the practical activity.
4.2. The Purpose and Access of the Laboratory
| Algorithm 1 Access Control and Booking Algorithm for ViRe-Lab. |
| procedure Laboratory Access and Booking (UserData, booking) |
| Calendar ← Data structure with free and busy slots of time |
| if ((booking)&&(AvailableSlot(Calendar)) then |
| BookingSession(UserData, Calendar) |
| message(“Booked a selected and free session in the calendar.”) |
| return True |
| else |
| if (!BookedSlot(UserData, Calendar)) then |
| message(“There is not a booked slot session for the user at the moment. Yo can do it.”) |
| return False |
| else |
| Resources ← List of available virtual resources |
| if (!AvailableResources(Resources)) then |
| message(“There is not available resources at the moment. Try it later, please.”) |
| return False |
| else |
| UserResources ← List of booked virtual resources for this user |
| CheckingConfigurations(UserData, UserResources) |
| RunVirtualLab(UserData, UserResources) |
| message(“Setting up the laboratory for user access.”) |
| return True |
4.3. Practical Activity
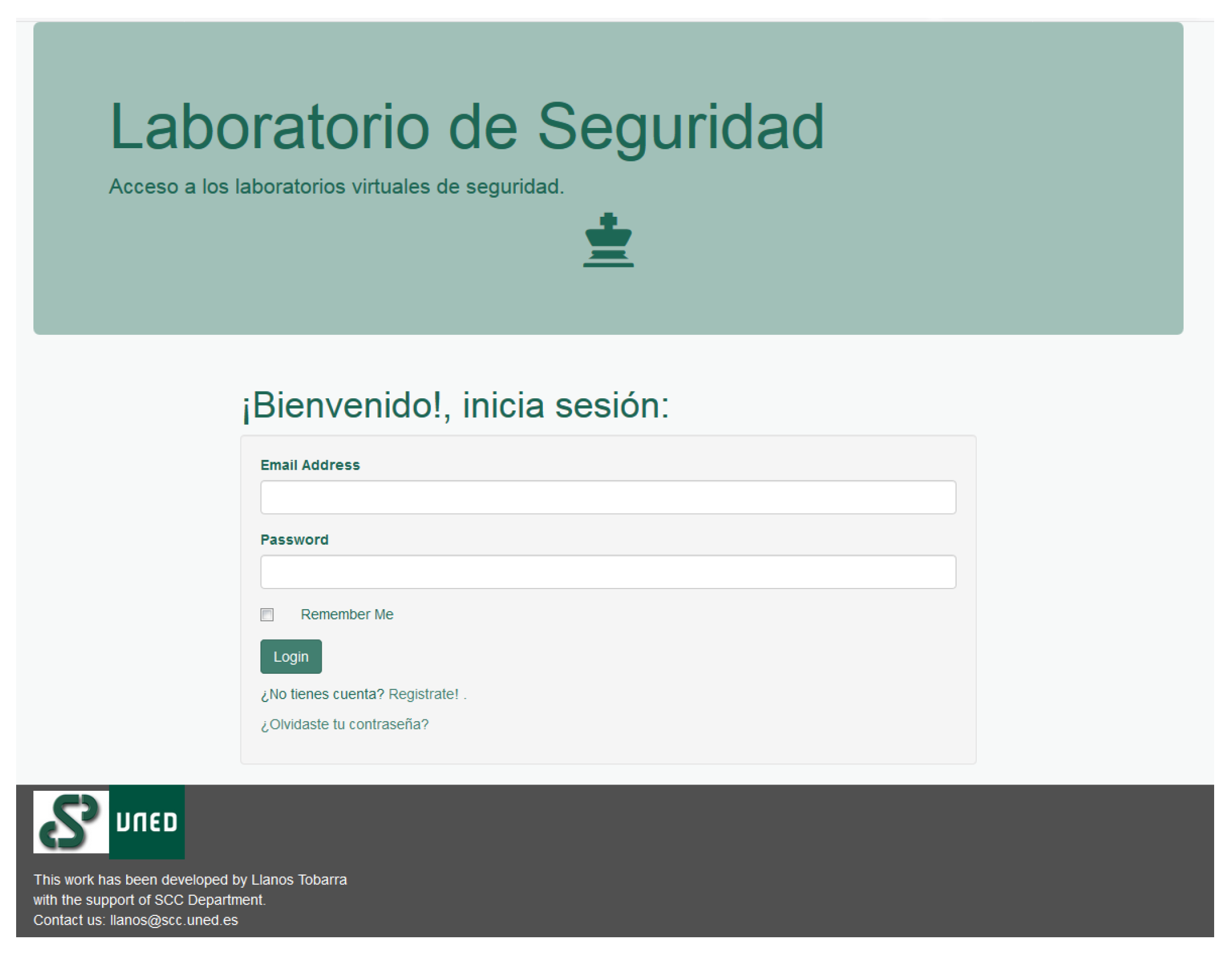
- Analyzing the context of the company in a non-intrusive way. The search for non-intrusive information focuses on obtaining as much information as possible from the company system with no knowledge of the organization’s internal structure. Students must avoid techniques that are considered intrusive (to be used in the following steps). Therefore, a student will be take the role of a penetration tester (pentester) recruited by a fictional company, named Disaster Corporation. As initial tasks, he/she can visit the company portal and obtain information about the network facility of the company The student can access the system through an unique access point in the cloud, as shown in Figure 3. He/she will not know any details about facility of the company.
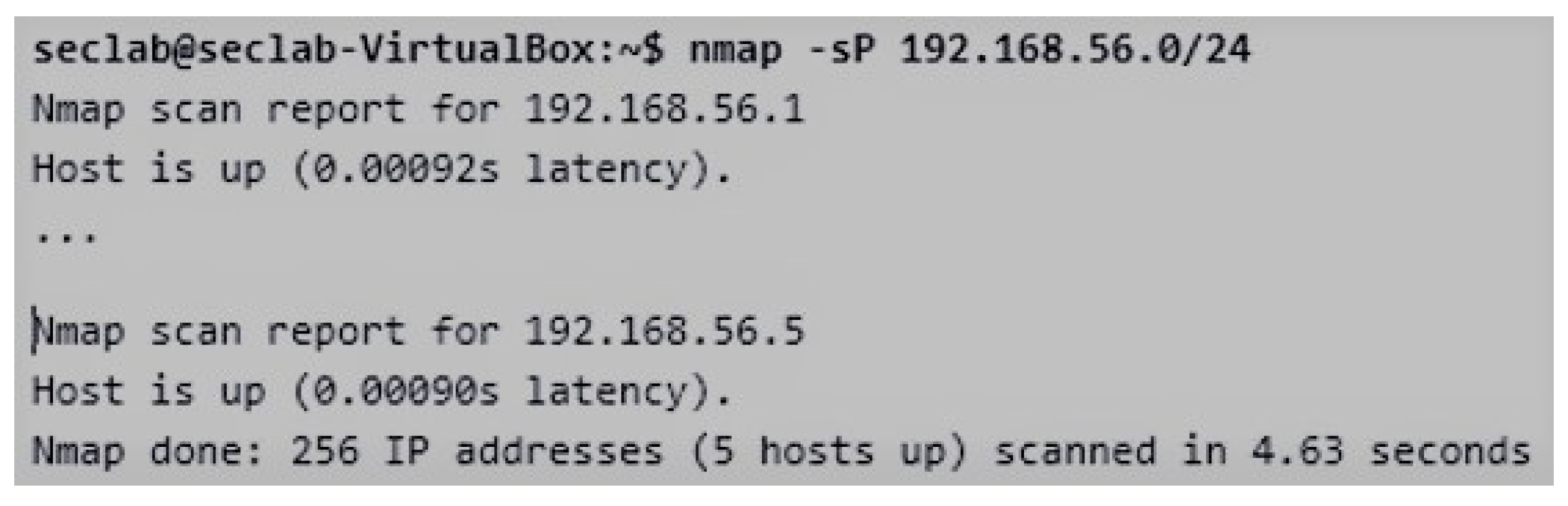
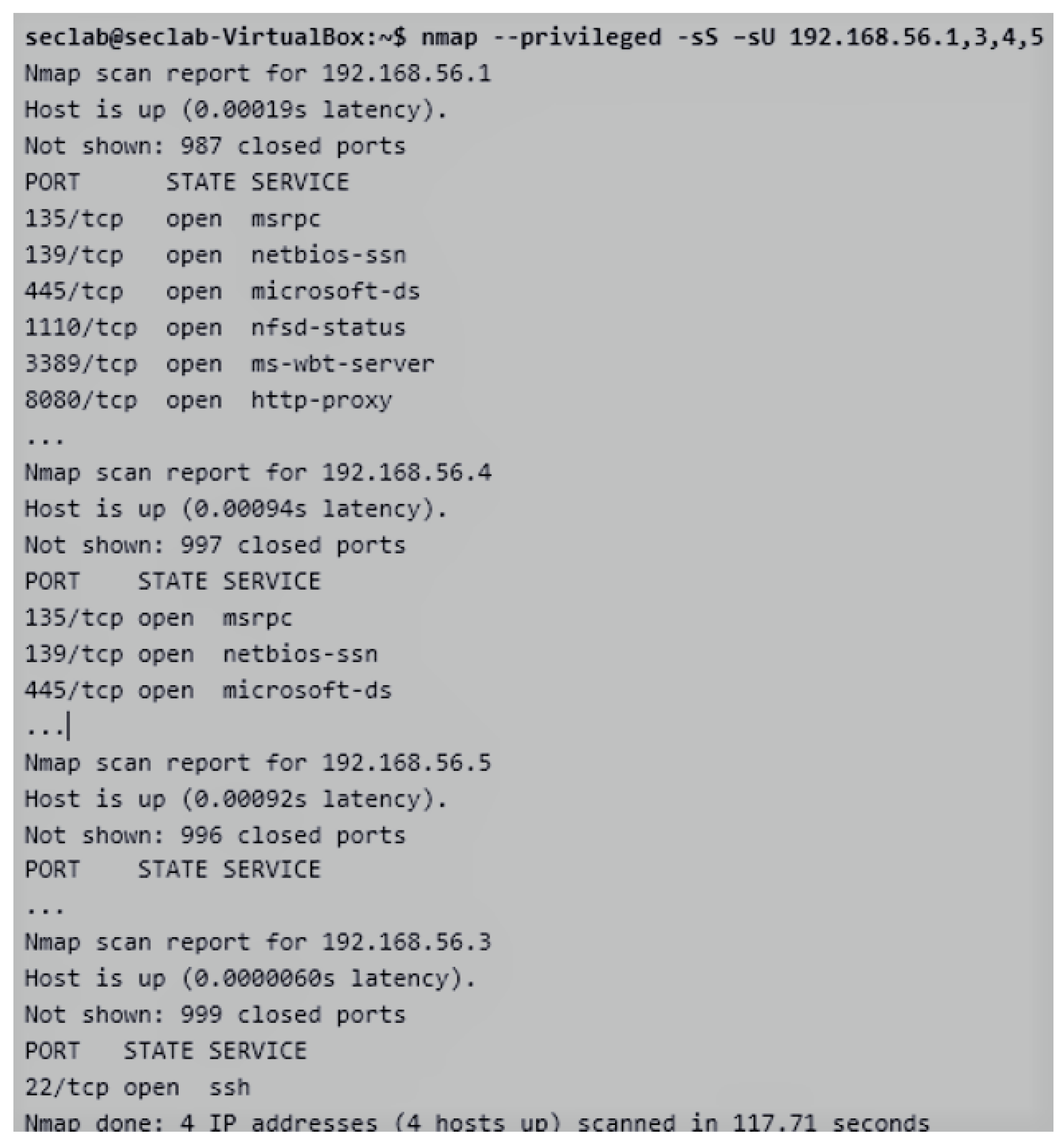
- Discovering the network structure of the company in both a non-intrusive and intrusive ways. Some initial tools can be employed by students to discover information about the network system: (1) the nslookup tool, in order to make queries to the DNS servers, so obtaining information about a possible target; and (2) the ping tool, in order to find out accessible and non-accessible IP addresses. It is worth mentioning the traceroute tool that allows detecting the route followed on the Internet to reach an IP address [44]. In addition to this. The first intrusive step will be to locate those computers that are turned on and connected to the network (devices, ports, and services) with the nmap tool [45]. We can find out which network we are connected to by using the ifconfig (Linux) or ipconfig (Windows) command. As observed in Figure 4, the company network of the practical activity is composed of five devices (from 192.168.56.1 to 192.168.56.5). The network IP (192.168.56.0) was found out with both the nslookup and ping tools.
- Finding out weak access points (open ports) in the network structure of the company. After knowing which devices are active into the network, it is interesting to find out possible access points to those computers. Therefore, the student must pay attention of the existing open ports. In the previous step, the devices of the network were discovered. It is now necessary to scan one-by-one with the nmap tool, instead of scanning the whole network, in order to discover the active ports of each of them. This will allow us to work faster, since our all information about our own devices is already in our own.
- Discovering active services using the detected the access points (or devices). The next step is to determine which services are running associated with each port. At this point, if we found a machine with all ports closed, we would ignore it, prior to do a more exhaustive scan. In particular, the open ports and associated services belonging to a set of network devices are shown in Figure 5. From this analysis, we obtain additional information to verify existing vulnerabilities into the network facility of the company.
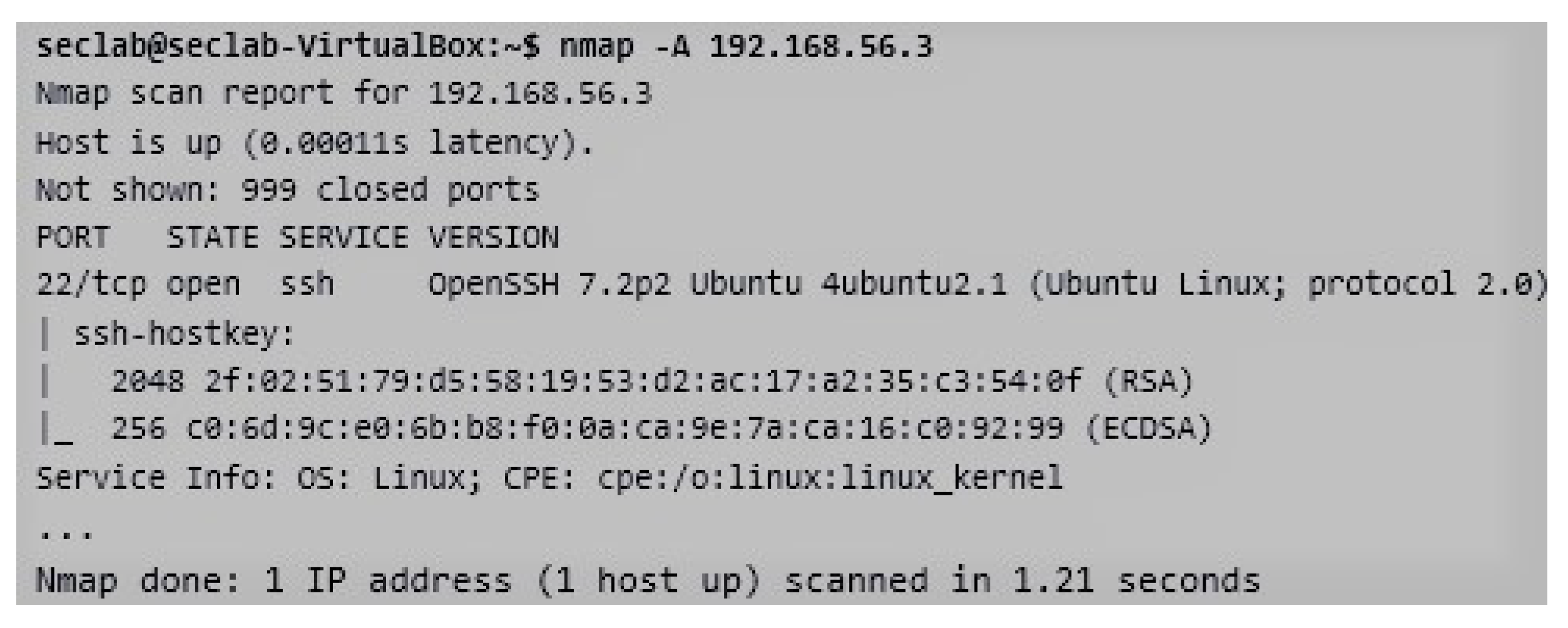
- Achieving all the possible information about possible targets. It is also needed to obtain more detailed information about each device of the company, which is a possible attack target, such as operating system, users, computer names and any information we may locate. It is also possible to perform this enumeration with the nmap tool. This command option usually takes time and generates large amounts of traffic. It also produces extensive output information. As an example, all information about the ssh service (open port 22), the operating system located in the host, keys, version of protocol, etc., is shown in Figure 6.
- Identifying and reporting vulnerabilities. From the previous findings, the student will have to identify the most relevant vulnerabilities found in the network system, and to make a report about these and how to solve them. Therefore, the cybersecurity policy of the company will be updated.
- Exploiting vulnerabilities. From the information collected in the report, the student must check the redefined cybersecurity policy with the role of a pentester. This will allow us to detect which system vulnerabilities can be exploited and to implement some known exploit to see if it is possible to find an attack in the system.
5. Results
5.1. Experiment Setup
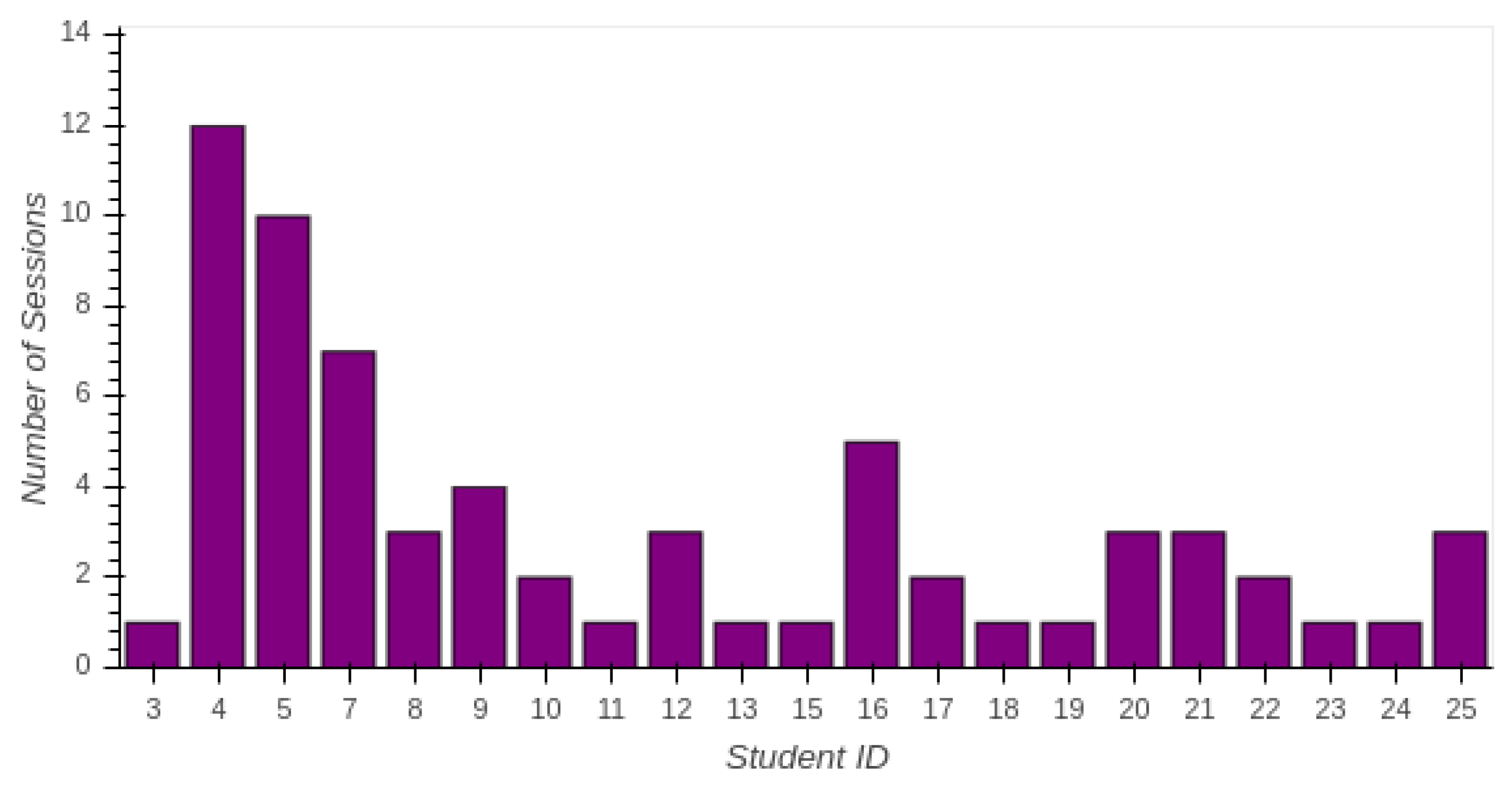
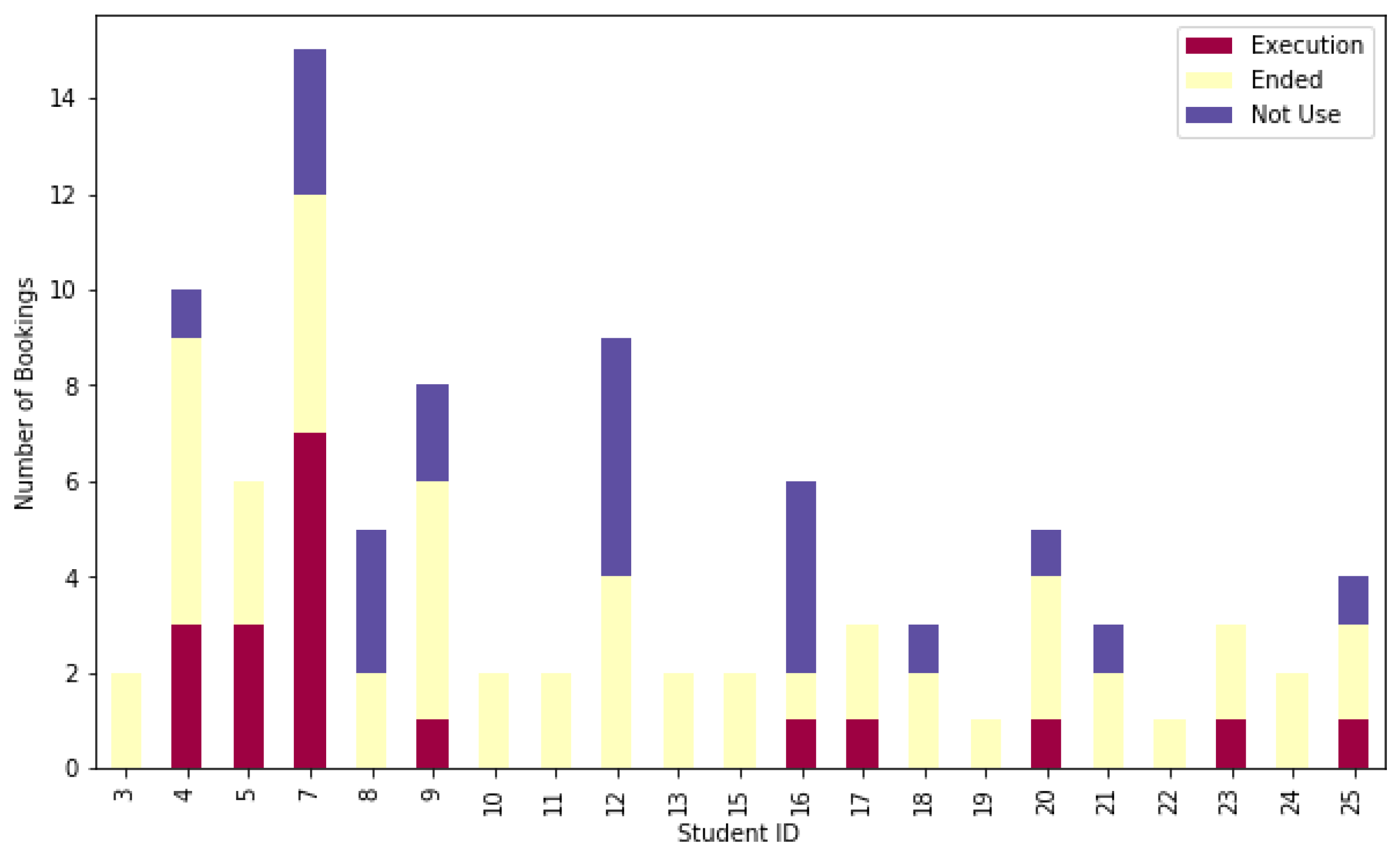
5.2. Students’ Interactions
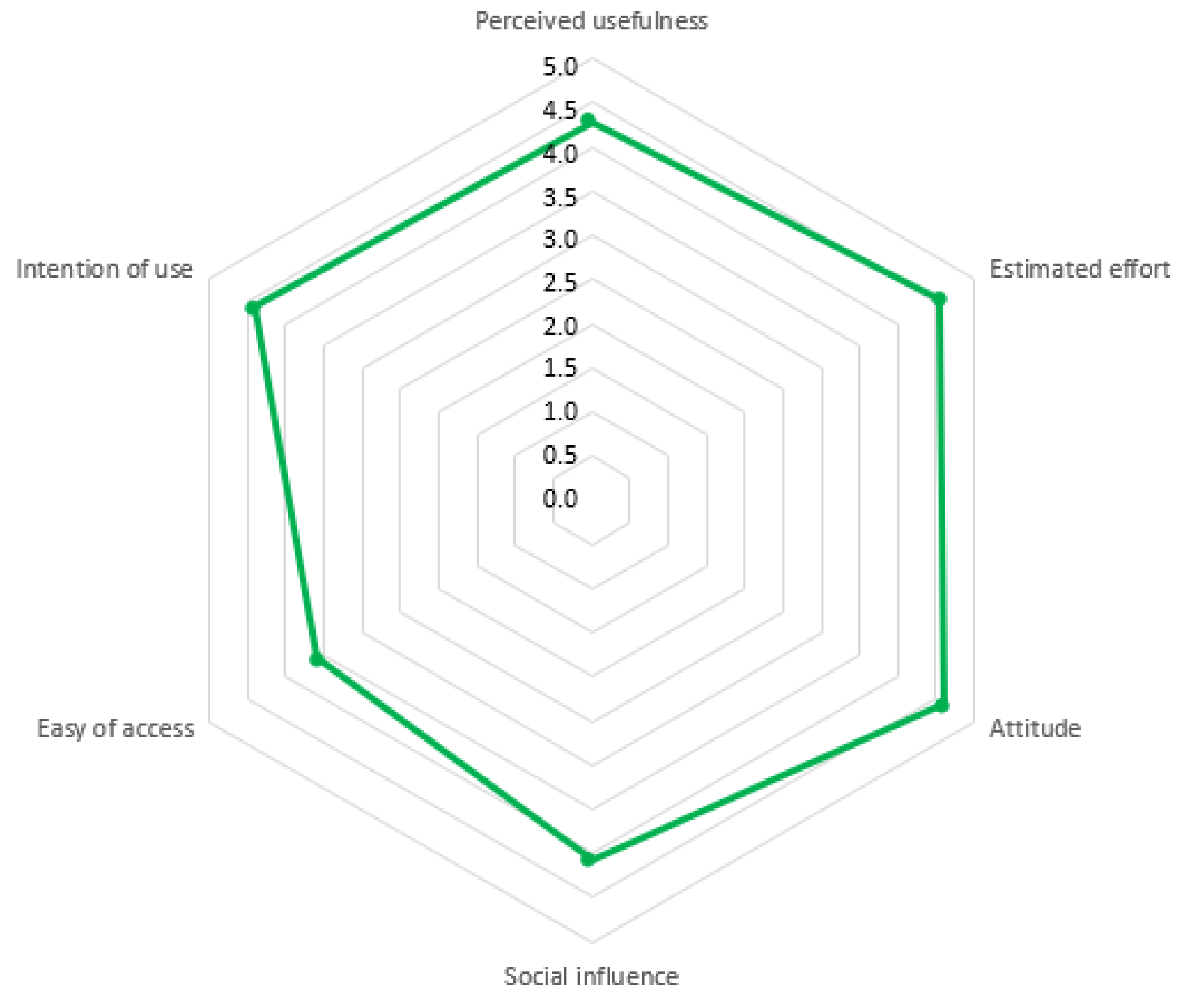
5.3. Students’ Satisfaction
5.4. Students’ Acceptance with SEM Models
6. Conclusions and Future Works
Author Contributions
Funding
Acknowledgments
Conflicts of Interest
References
- Duan, Y. Value Modeling and Calculation for Everything as a Service (XaaS) Based on Reuse. In Proceedings of the 13th International Conference on Software Engineering, Artificial Intelligence, Networking and Parallel/Distributed Computing (SNPD), Kyoto, Japan, 8–10 August 2012. [Google Scholar]
- Martini, N.; Farmer, K.; Patil, S.; Tan, G.; Wang, C.; Wong, L.; Webster, C.S. Designing and Evaluating a Virtual Patient Simulation—The Journey from Uniprofessional to Interprofessional Learning. Information 2019, 10, 28. [Google Scholar] [CrossRef]
- Juan, Y.K.; Chen, H.H.; Chi, H.Y. Developing and Evaluating a Virtual Reality-Based Navigation System for Pre-Sale Housing Sales. Appl. Sci. 2018, 8, 952. [Google Scholar] [CrossRef]
- Pastor, R.; Tobarra, L.; Robles-Gómez, A.; Cano, J.; Hammad, B.; Al-Zoubi, A.; Hernández, R.; Castro, M. Renewable energy remote online laboratories in Jordan universities: Tools for training students in Jordan. Renew. Energy 2020, 149, 749–759. [Google Scholar] [CrossRef]
- Tobarra, L.; Ros, S.; Hernández, R.; Marcos-Barreiro, A.; Robles-Gómez, A.; Caminero, A.C.; Pastor, R.; Castro, M. Creation of Customized Remote Laboratories Using Deconstruction. IEEE-RITA 2015, 10, 69–76. [Google Scholar] [CrossRef]
- Dasgupta, D.; Ferebee, D.M.; Michalewicz, Z. Applying Puzzle-Based Learning to Cyber-Security Education. In Proceedings of the 2013 on InfoSecCD ’13: Information Security Curriculum Development Conference, Kennesaw, GA, USA, 12–13 October 2013; pp. 20:20–20:26. [Google Scholar] [CrossRef]
- Martini, B.; Choo, K.K.R. Building the Next Generation of Cyber Security Professionals. In Proceedings of the 22nd European Conference on Information Systems (ECIS 2014), Tel Aviv, Israel, 9–11 June 2014. [Google Scholar]
- Willingham, D.T. Critical Thinking: Why Is It So Hard to Teach? Arts Educ. Policy Rev. 2008, 109, 21–32. [Google Scholar] [CrossRef]
- Hamari, J.; Koivisto, J.; Sarsa, H. Does Gamification Work?—A Literature Review of Empirical Studies on Gamification. In Proceedings of the 2014 47th Hawaii International Conference on System Sciences, Waikoloa, HI, USA, 6–9 January 2014; pp. 3025–3034. [Google Scholar] [CrossRef]
- Cano, J.; Hernández, R.; Ros, S. Bringing an engineering lab into social sciences: didactic approach and an experiential evaluation. IEEE Commun. Mag. 2014, 52, 101–107. [Google Scholar] [CrossRef]
- Cano, J.; Hernández, R.; Ros, S.; Tobarra, L. A distributed laboratory architecture for game based learning in cybersecurity and critical infrastructures. In Proceedings of the 2016 13th International Conference on Remote Engineering and Virtual Instrumentation (REV), Madrid, Spain, 24–26 February 2016; pp. 183–185. [Google Scholar] [CrossRef]
- EVE-ND, Emulated Virtual Environment–Next Generation. Available online: http://www.eve-ng.net/index.php/downloads/eve-ng (accessed on 30 April 2020).
- Tobarra, L.; Robles-Gómez, A.; Pastor, R.; Hernández, R.; Duque, A.; Cano, J. A Cybersecurity Experience with Cloud Virtual-Remote Laboratories. Proceedings 2019, 31, 1003. [Google Scholar] [CrossRef]
- Santos, O.C.; Boticario, J.G.; Raffenne, E.; Pastor, R. Why using dotLRN? UNED use cases. In Proceedings of the FLOSS (Free/Libre/Open Source Systems) International Conference, Jerez de la Frontera, Spain, 7–9 March 2007; pp. 195–212. [Google Scholar]
- Venkatesh, V.; Morris, M.G.; Davis, G.B.; Davis, F.D. User Acceptance of Information Technology: Toward a Unified View. MIS Q. 2003, 27, 425–478. [Google Scholar] [CrossRef]
- Holden, R.; Karsh, B.T. The Technology Acceptance Model: Its Past and Its Future in Health Care. J. Biomed. Inform. 2010, 43, 159–172. [Google Scholar] [CrossRef]
- Estriegana, R.; Medina-Merodio, J.A.; Barchino, R. Student acceptance of virtual laboratory and practical work: An extension of the technology acceptance model. Comput. Educ. 2019, 135, 1–14. [Google Scholar] [CrossRef]
- Konak, A.; Bartolacci, M.R.; Kulturel-Konak, S.; Nasereddin, M. Impact of collaborative learning on student perception of virtual computer laboratories. In Proceedings of the 2016 IEEE Frontiers in Education Conference (FIE), Erie, PA, USA, 12–15 October 2016; pp. 1–4. [Google Scholar]
- Kim, S.; Lee, K.H.; Hwang, H.; Yoo, S. Analysis of the factors influencing healthcare professionals’ adoption of mobile electronic medical record (EMR) using the unified theory of acceptance and use of technology (UTAUT) in a tertiary hospital. BMC Med Inform. Decis. Mak. 2016, 16, 12. [Google Scholar] [CrossRef] [PubMed]
- Badshah, A.; Ghani, A.; Shamshirband, S.; Chronopoulos, A.T. Optimising infrastructure as a service provider revenue through customer satisfaction and efficient resource provisioning in cloud computing. IET Commun. 2019, 13, 2913–2922. [Google Scholar] [CrossRef]
- Badshah, A.; Ghani, A.; Qureshi, M.A.; Shamshirb, S. Smart Security Framework for Educational Institutions Using Internet of Things (IoT). Comput. Mater. Contin. 2019, 61, 81–101. [Google Scholar] [CrossRef]
- Mansoor, K.; Ghani, A.; Chaudhry, S.A.; Shamshirband, S.; Ghayyur, S.A.K.; Mosavi, A. Securing IoT-Based RFID Systems: A Robust Authentication Protocol Using Symmetric Cryptography. Sensors 2019, 19, 4752. [Google Scholar] [CrossRef] [PubMed]
- Moreno, R.; Robles-Gómez, A.; Bermúdez, A.; Casado, R. SensGrid: modeling and simulation for wireless sensor grids. Simulation 2012, 88, 972–987. [Google Scholar] [CrossRef]
- Román-Ibáñez, V.; Pujol-López, F.A.; Mora-Mora, H.; Pertegal-Felices, M.L.; Jimeno-Morenilla, A. A Low-Cost Immersive Virtual Reality System for Teaching Robotic Manipulators Programming. Sustainability 2018, 10, 1102. [Google Scholar] [CrossRef]
- Tawfik, M.; Sancristobal, E.; Martin, S.; Diaz, G.; Castro, M. State-of-the-art remote laboratories for industrial electronics applications. In Proceedings of the Conference on Technologies Applied to Electronics Teaching (TAEE), Vigo, Spain, 13–15 June 2012; pp. 359–364. [Google Scholar] [CrossRef]
- Shankar, B.; Sarithlal, M.; Vijayan, V.; Freeman, J.; Achuthan, K. Remote Triggered Solar Thermal Energy Parabolic Trough laboratory: Effective implementation and future possibilities for Virtual Labs. In Proceedings of the 2013 IEEE International Conference on Control Applications (CCA), Hyderabad, India, 28–30 August 2013; pp. 472–476. [Google Scholar] [CrossRef]
- Rao, P.; Dinesh, P.; Ilango, G.; Nagamani, C. Laboratory course on solar photovoltaic systems based on low cost equipment. In Proceedings of the 2013 IEEE International Conference on MOOC Innovation and Technology in Education (MITE), Jaipur, India, 20–22 December 2013; pp. 146–151. [Google Scholar] [CrossRef]
- Tobarra, L.; Ros, S.; Hernández, R.; Pastor, R.; Robles-Gómez, A.; Caminero, A.C.; Castro, M. Low-Cost Remote Laboratories for Renewable Energy in Distance Education. In Proceedings of the 11th International Conference on Remote Engineering and Virtual Instrumentation (REV 2014), Porto, Portugal, 26–28 February 2014. [Google Scholar]
- Al-Zoubi, A.; Hammad, B.; Ros, S.; Tobarra, L.; Hernández, R.; Pastor, R.; Castro, M. Remote laboratories for renewable energy courses at Jordan universities. In Proceedings of the 2014 IEEE Frontiers in Education Conference (FIE) Proceedings, Madrid, Spain, 22–25 October 2014; pp. 1–4. [Google Scholar]
- Tobarra, L.; Ros, S.; Hernández, R.; Pastor, R.; Castro, M.; Al-Zoubi, A.Y.; Hammad, B.; Dmour, M.; Robles-Gómez, A.; Caminero, A.C. Analysis of integration of remote laboratories for renewable energy courses at Jordan universities. In Proceedings of the 2015 IEEE Frontiers in Education Conference (FIE), El Paso, TX, USA, 21–24 October 2015; pp. 1–5. [Google Scholar]
- Pastor, R.; Caminero, A.C.; Rama, D.S.; Hernández, R.; Ros, S.; Robles-Gómez, A.; Tobarra, L. Laboratories as a Service (LaaS): Using Cloud Technologies in the Field of Education. J. UCS 2013, 19, 2112–2126. [Google Scholar]
- Tobarra, L.; Robles-Gómez, A.; Pastor, R.; Hernández, R.; Cano, J.; López, D. Web of Things Platforms for Distance Learning Scenarios in Computer Science Disciplines: A Practical Approach. Technologies 2019, 7, 17. [Google Scholar] [CrossRef]
- Burgos, D. A Predictive System Informed by Students’ Similar Behaviour. Sustainability 2020, 12, 706. [Google Scholar] [CrossRef]
- Ros, S.; Robles-Gómez, A.; Hernández, R.; Caminero, A.C.; Pastor, R. Using Virtualization and Automatic Evaluation: Adapting Network Services Management Courses to the EHEA. IEEE Trans. Educ. 2012, 55, 196–202. [Google Scholar] [CrossRef]
- Bora, U.J.; Ahmed, M. E-learning using Cloud Computing. Int. J. Sci. Mod. Eng. (IJISME) 2013, 1, 9–13. [Google Scholar]
- IBM Corporation. Cloud Computing Saves Time, Money and Shortens Production Cycle. Available online: http://www-935.ibm.com/services/in/cio/pdf/dic03001usen.pdf (accessed on 30 April 2020).
- Selviandro, N.; Hasibuan, Z. Cloud-Based E-Learning: A Proposed Model and Benefits by Using E-Learning Based on Cloud Computing for Educational Institution. In Information and Communication Technology; Lecture Notes in Computer Science; Springer: Berlin/Heidelberg, Germany, 2013; Volume 7804. [Google Scholar]
- Caminero, A.C.; Ros, S.; Hernández, R.; Robles-Gómez, A.; Tobarra, L.; Granjo, P.J.T. VirTUal remoTe labORatories Management System (TUTORES): Using Cloud Computing to Acquire University Practical Skills. IEEE Trans. Learn. Technol. 2016, 9, 133–145. [Google Scholar] [CrossRef]
- Global Online Science Labs for Inquiry Learning at School (Go-Lab Project). Available online: http://www.go-lab-project.eu/ (accessed on 30 April 2020).
- Salmerón-Manzano, E.; Manzano-Agugliaro, F. The Higher Education Sustainability through Virtual Laboratories: The Spanish University as Case of Study. Sustainability 2018, 10, 4040. [Google Scholar] [CrossRef]
- Tobarra, L.; Robles-Gómez, A.; Pastor, R.; Hernández, R.; Duque, A.; Cano, J. Students’ Acceptance and Tracking of a New Container-Based Virtual Laboratory. Appl. Sci. 2020, 10, 1091. [Google Scholar] [CrossRef]
- Bielby, W.T.; Hauser, R.M. Structural Equation Models. Annu. Rev. Sociol. 1977, 3, 137–161. [Google Scholar] [CrossRef]
- Liu, I.F.; Chen, M.C.; Sun, Y.S.; Wible, D.; Kuo, C.H. Extending the TAM model to explore the factors that affect Intention to Use an Online Learning Community. Comput. Educ. 2010, 54, 600–610. [Google Scholar] [CrossRef]
- Luckie, M.; Hyun, Y.; Huffaker, B. Traceroute Probe Method and Forward IP Path Inference. In Proceedings of the 8th ACM SIGCOMM Conference on Internet Measurement (IMC ’08); Association for Computing Machinery: New York, NY, USA, 2008; pp. 311–324. [Google Scholar] [CrossRef]
- Shah, M.; Ahmed, S.; Saeed, K.; Junaid, M.; Khan, H.; Ata-ur-rehman. Penetration Testing Active Reconnaissance Phase–Optimized Port Scanning With Nmap Tool. In Proceedings of the 2019 2nd International Conference on Computing, Mathematics and Engineering Technologies (iCoMET), Sukkur, Pakistan, 30–31 January 2019; pp. 1–6. [Google Scholar]
- Ros, S.; Hernández, R.; Caminero, A.; Robles, A.; Barbero, I.; Maciá, A.; Holgado, F.P. On the use of extended TAM to assess students’ acceptance and intent to use third-generation learning management systems. Br. J. Educ. Technol. 2015, 46, 1250–1271. [Google Scholar] [CrossRef]
- León, J.A.M.; Cantisano, G.T.; Mangin, J.P.L. Leadership in Nonprofit Organizations of Nicaragua and El Salvador: A Study from the Social Identity Theory. Span. J. Psychol. 2009, 12, 667–676. [Google Scholar] [CrossRef]
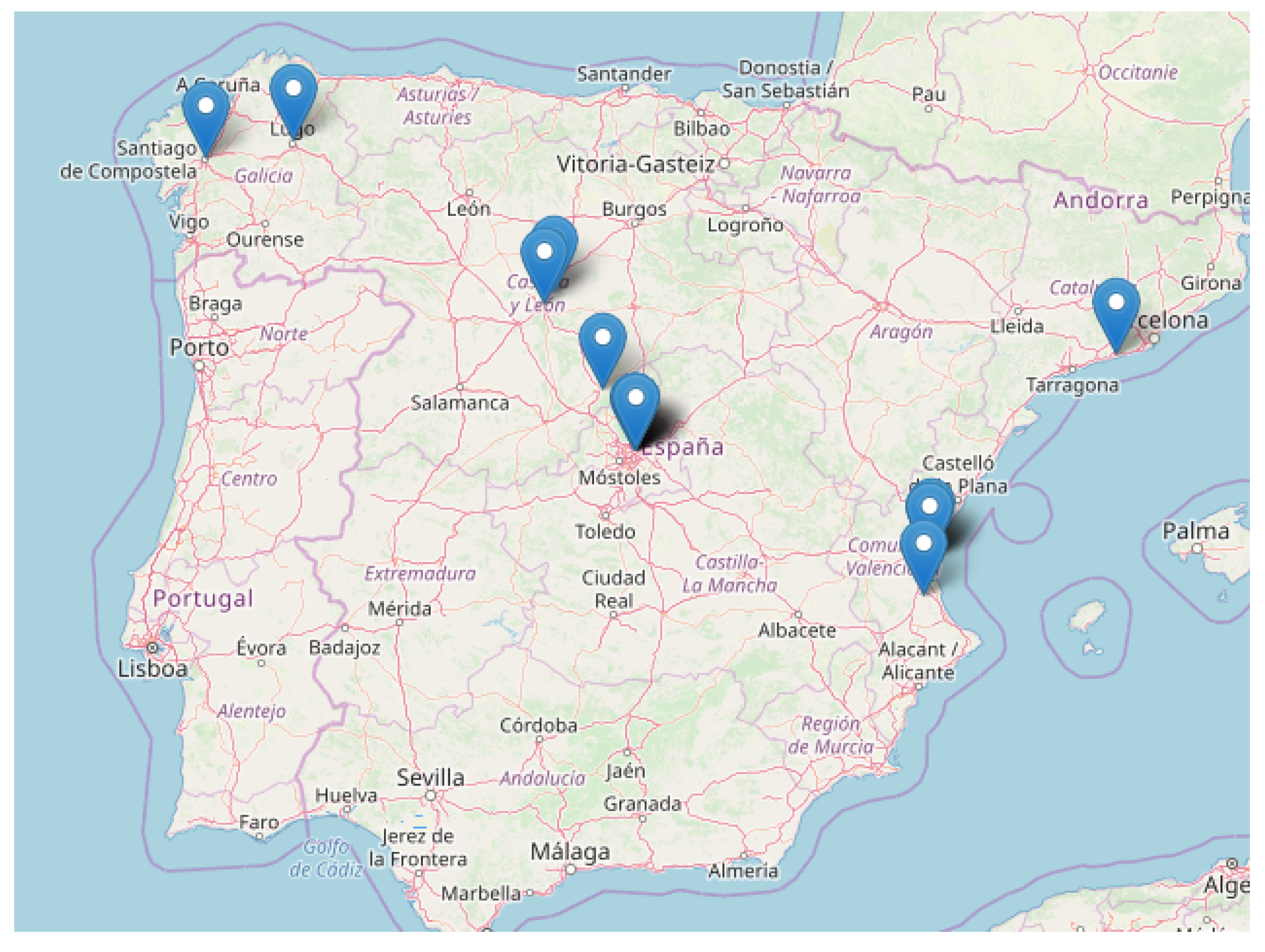
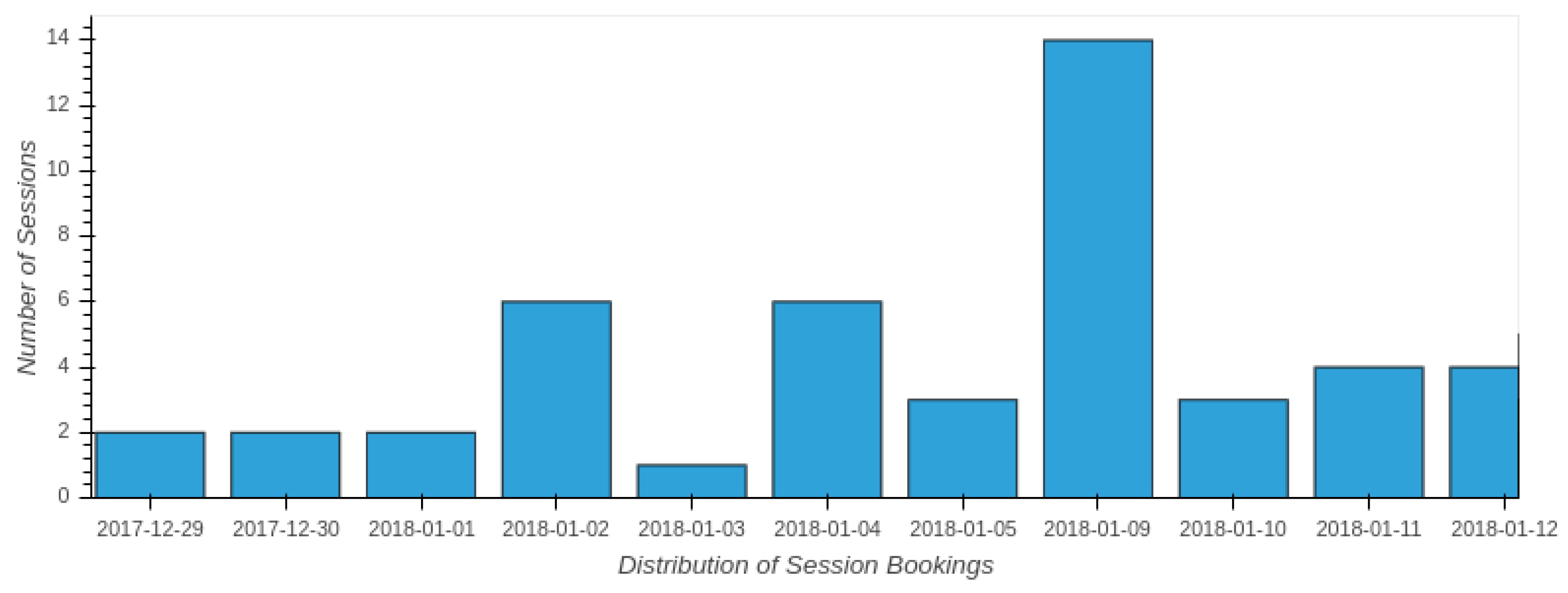
| Type | Option | Percentage (%) |
|---|---|---|
| Gender | Male | 85% |
| Female | 15% | |
| Age Group | ≤30 years | 40% |
| 30–39 years | 40% | |
| 40–50 years | 15% | |
| ≥50 years | 5% | |
| Occupation | Non-computer science related job position | 5% |
| Computer science related job position | 80% | |
| Other situation | 15% |
| Factor | M | SD |
|---|---|---|
| Perceived usefulness | 4.30 | 0.59 |
| Estimated effort | 4.55 | 0.42 |
| Attitude | 4.61 | 0.46 |
| Social influence | 4.07 | 0.80 |
| Ease of access | 3.58 | 0.65 |
| Intention of use | 4.40 | 0.71 |
| Factor | Strongly Agree | Agree | Neutral | Disagree | Strongly Disagree |
|---|---|---|---|---|---|
| Perceived usefulness | 45% | 50% | 5% | 0% | 0% |
| Estimated Effort (Ease to Use) | 55% | 45% | 0% | 0% | 0% |
| Attitude | 75% | 20% | 5% | 0% | 0% |
| Social influence | 30% | 40% | 30% | 0% | 0% |
| Ease of access | 10% | 55% | 35% | 0% | 0% |
| Intention of use | 55% | 35% | 10% | 0% | 0% |
© 2020 by the authors. Licensee MDPI, Basel, Switzerland. This article is an open access article distributed under the terms and conditions of the Creative Commons Attribution (CC BY) license (http://creativecommons.org/licenses/by/4.0/).
Share and Cite
Robles-Gómez, A.; Tobarra, L.; Pastor-Vargas, R.; Hernández, R.; Cano, J. Emulating and Evaluating Virtual Remote Laboratories for Cybersecurity. Sensors 2020, 20, 3011. https://doi.org/10.3390/s20113011
Robles-Gómez A, Tobarra L, Pastor-Vargas R, Hernández R, Cano J. Emulating and Evaluating Virtual Remote Laboratories for Cybersecurity. Sensors. 2020; 20(11):3011. https://doi.org/10.3390/s20113011
Chicago/Turabian StyleRobles-Gómez, Antonio, Llanos Tobarra, Rafael Pastor-Vargas, Roberto Hernández, and Jesús Cano. 2020. "Emulating and Evaluating Virtual Remote Laboratories for Cybersecurity" Sensors 20, no. 11: 3011. https://doi.org/10.3390/s20113011
APA StyleRobles-Gómez, A., Tobarra, L., Pastor-Vargas, R., Hernández, R., & Cano, J. (2020). Emulating and Evaluating Virtual Remote Laboratories for Cybersecurity. Sensors, 20(11), 3011. https://doi.org/10.3390/s20113011







