A Trust-Based Formal Model for Fault Detection in Wireless Sensor Networks
Abstract
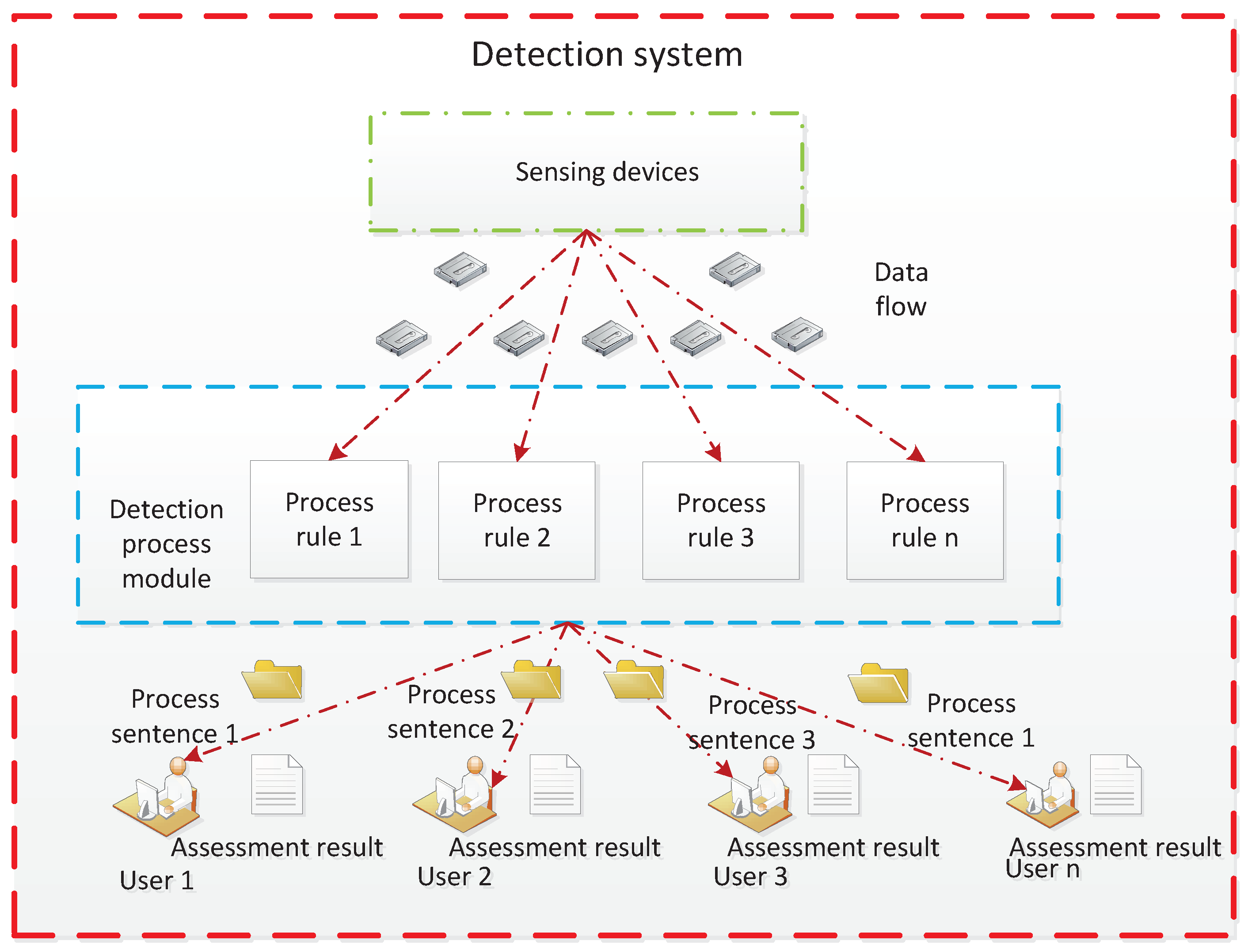
1. Introduction
2. Related Works
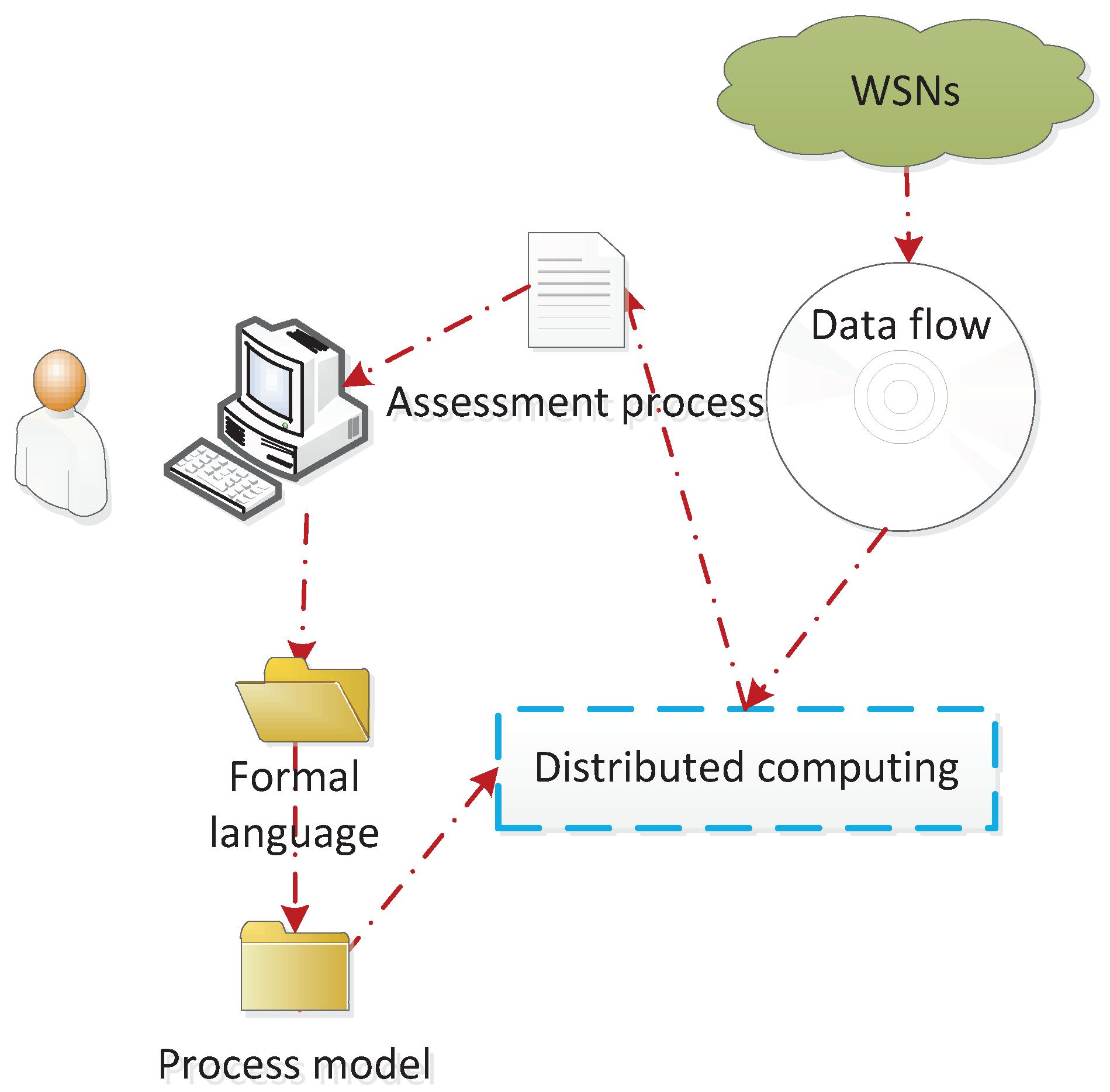
3. A Trust-Based Formal Model
- The time of data sensed
- The weight of each factor
- The threshold for decision
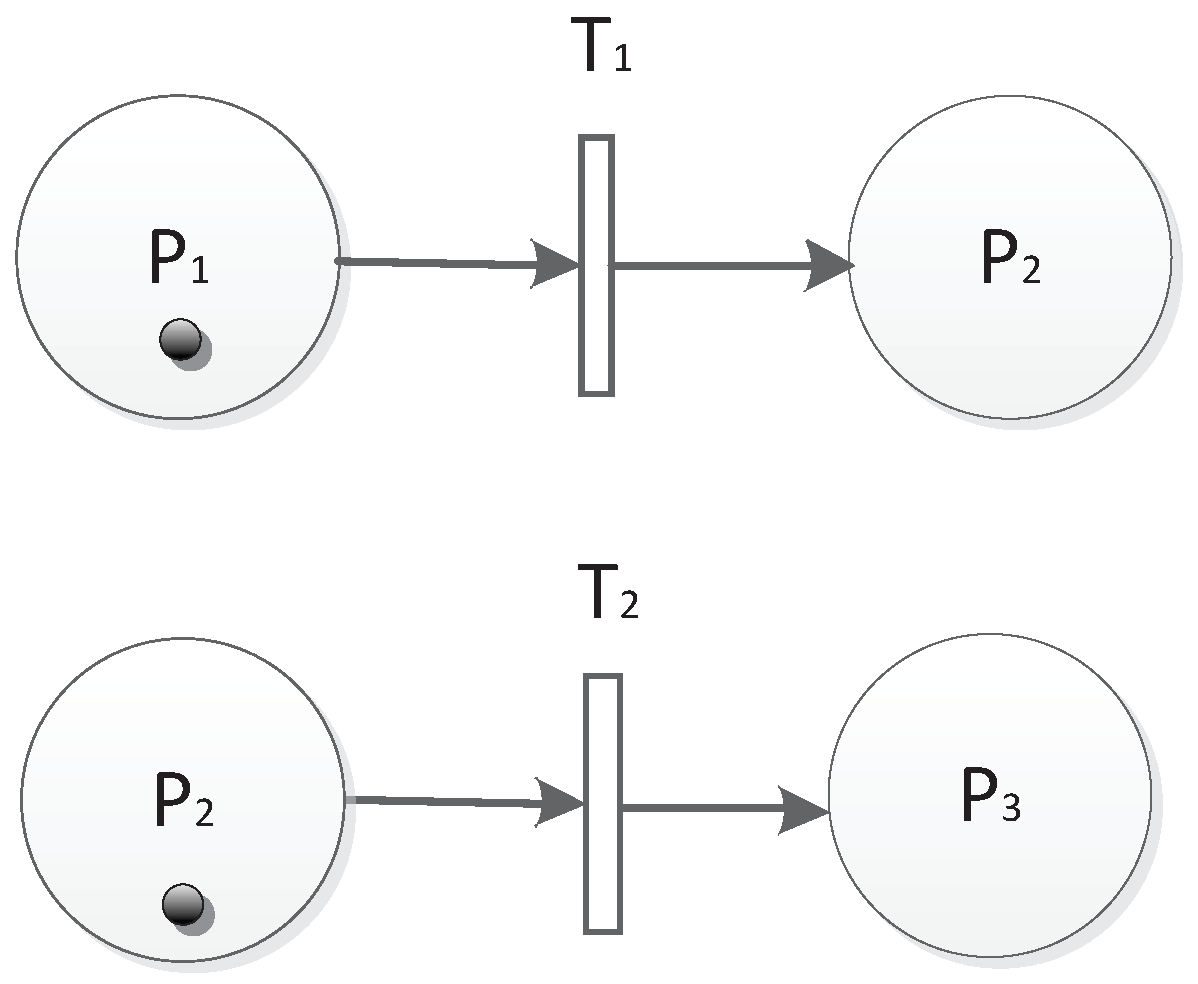
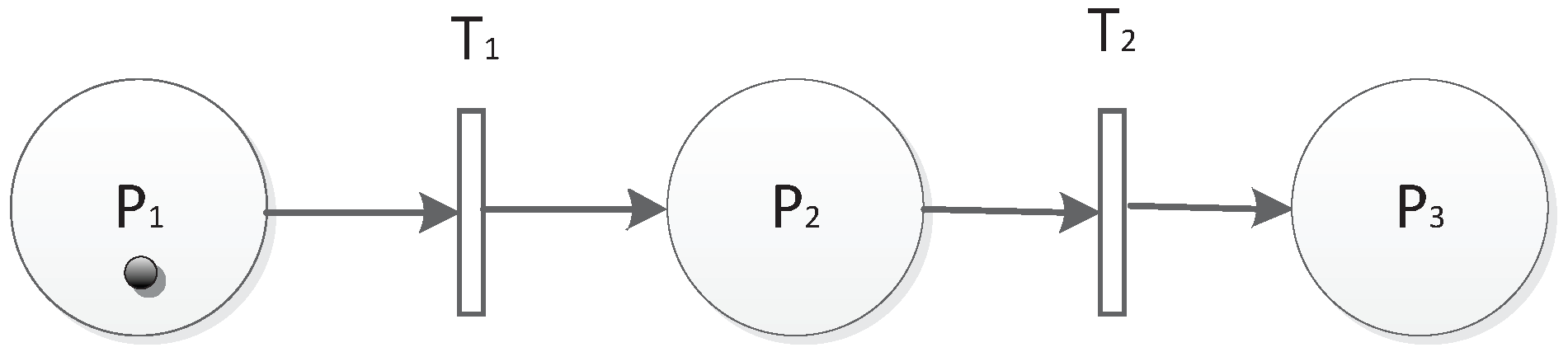
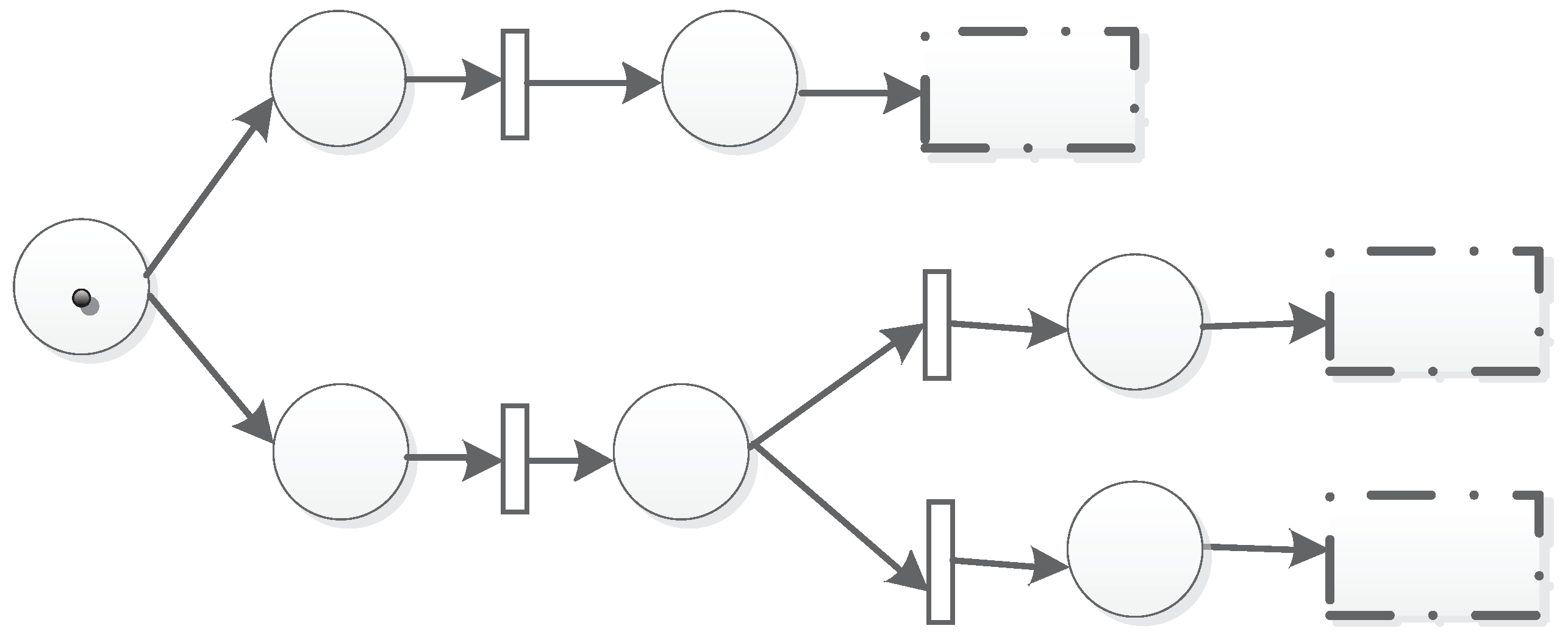
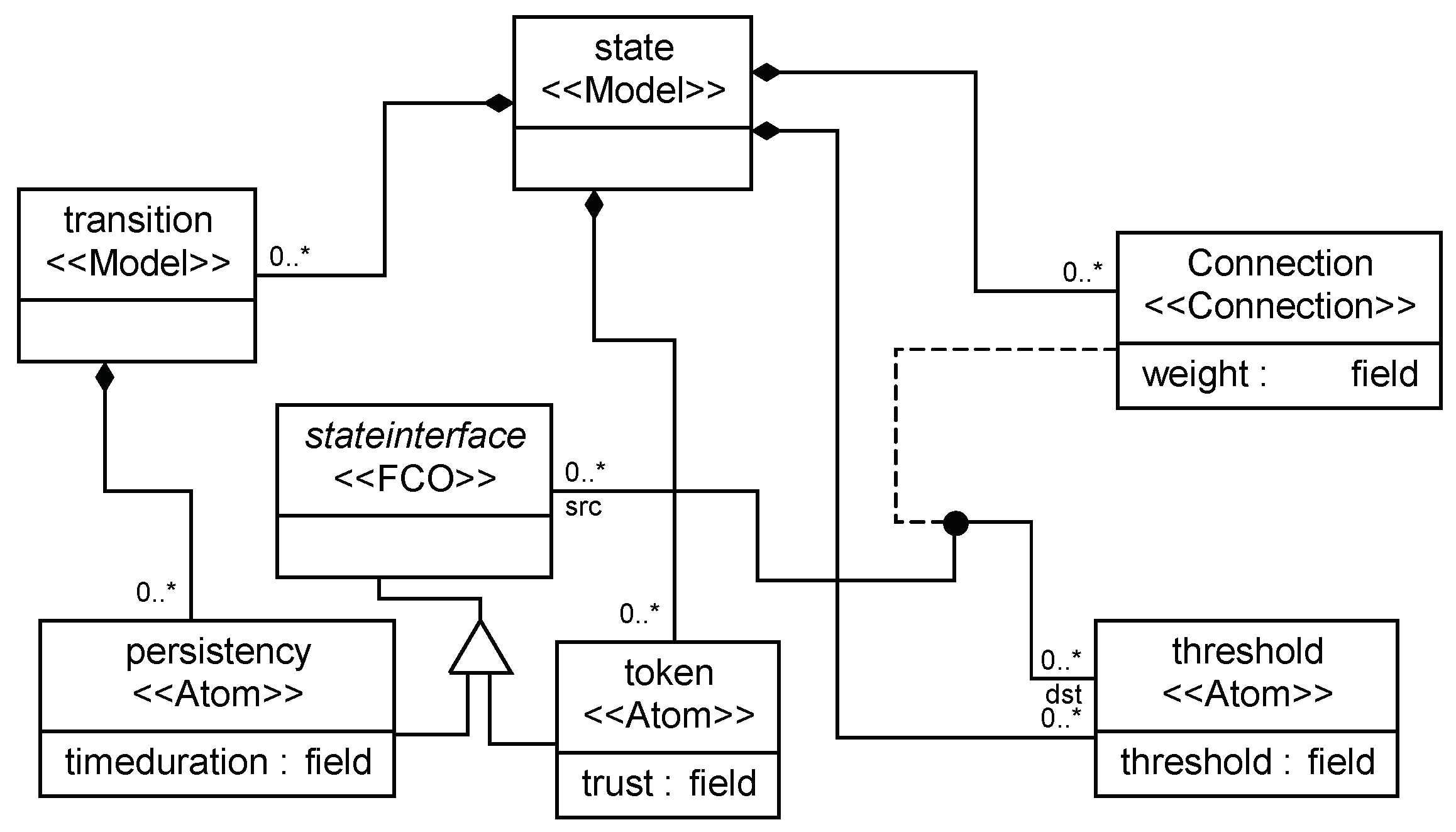
3.1. Definition of the TFM
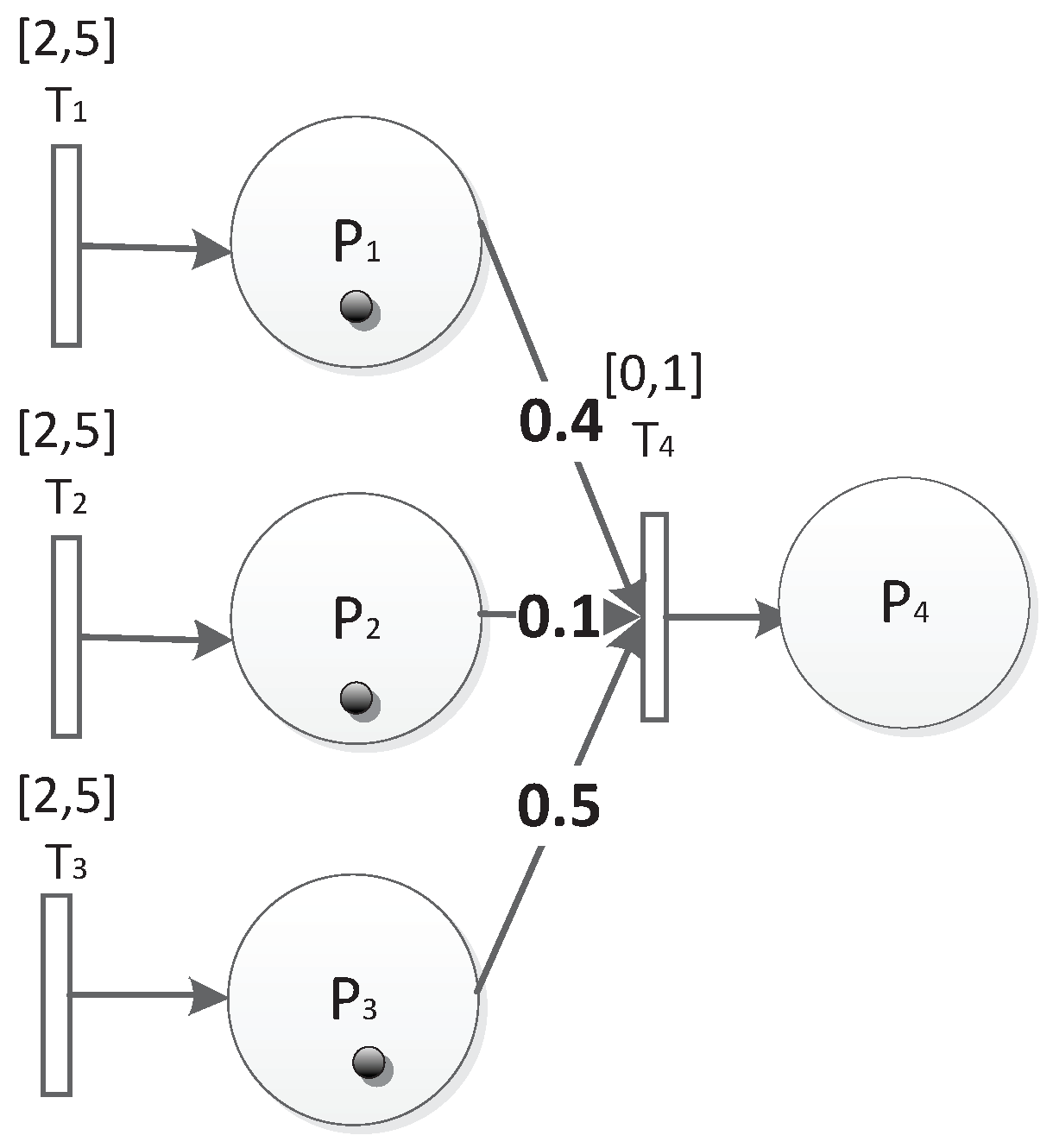
- is the weight on arcs, which represents the probability or importance of factors of a transition. and where n is the number of input arcs into a transition. For example, if there is an arc , means there is a probability of inducing the token entering t from p. If the token has a capacity c, the new capacity will be .
- is a time guard for T, : T, and . means transition T can only fire during and . Especially, if = , that means the transition can only happen during .
- is the threshold of token capacity in P, : , and R is a real type data. = , means when the capacity of the token in P is greater than or equal to , P can reach a new station.
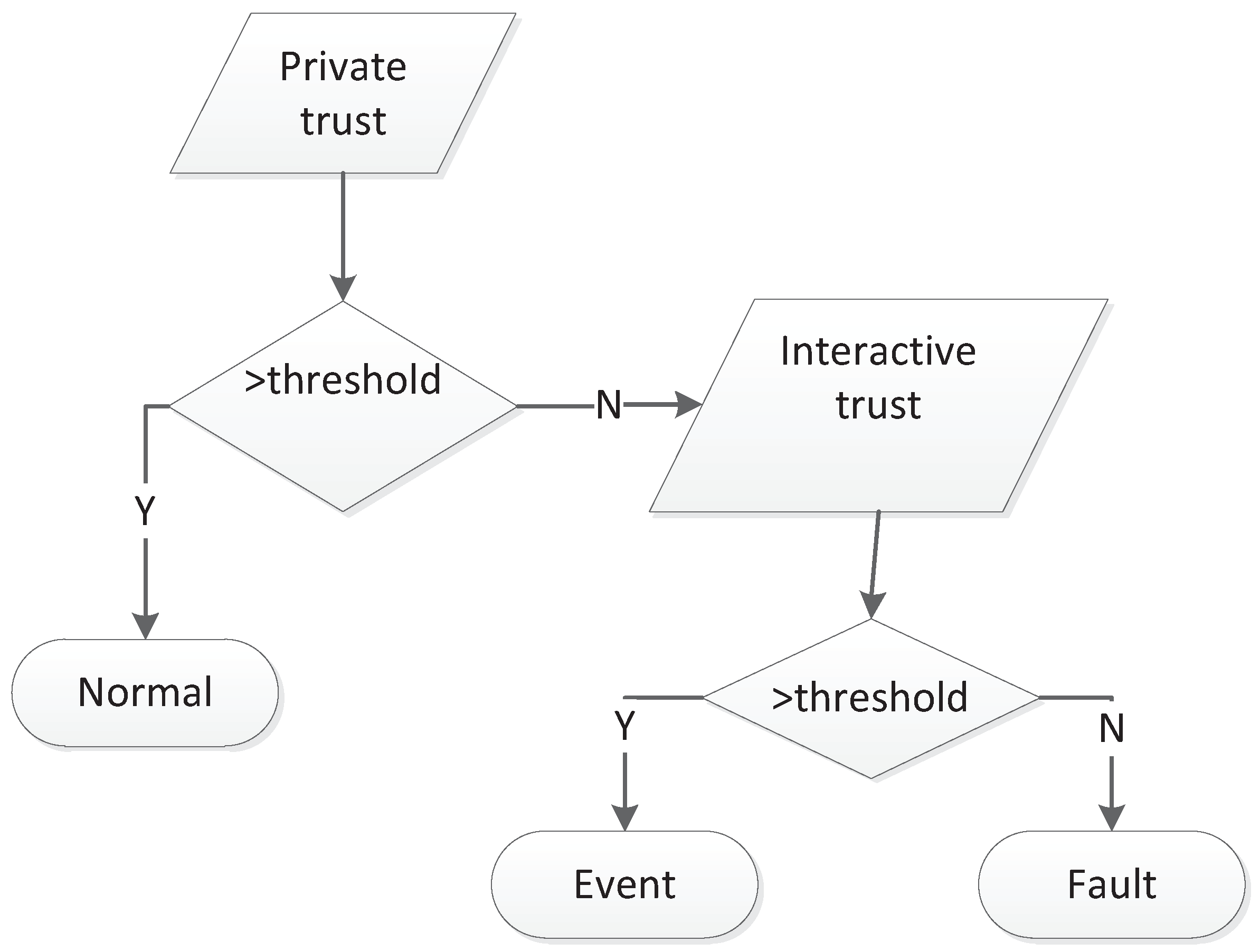
3.2. Trust Modeling
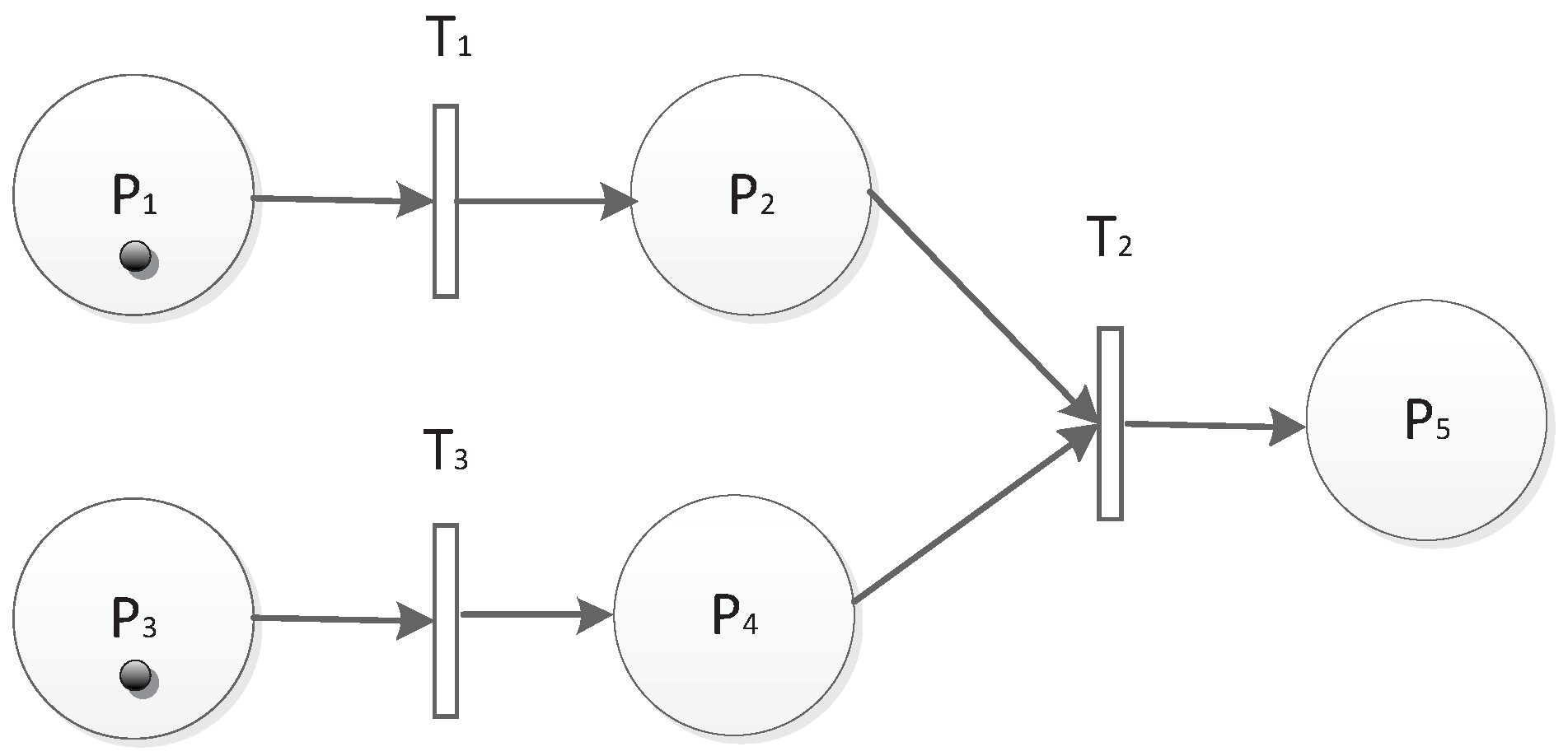
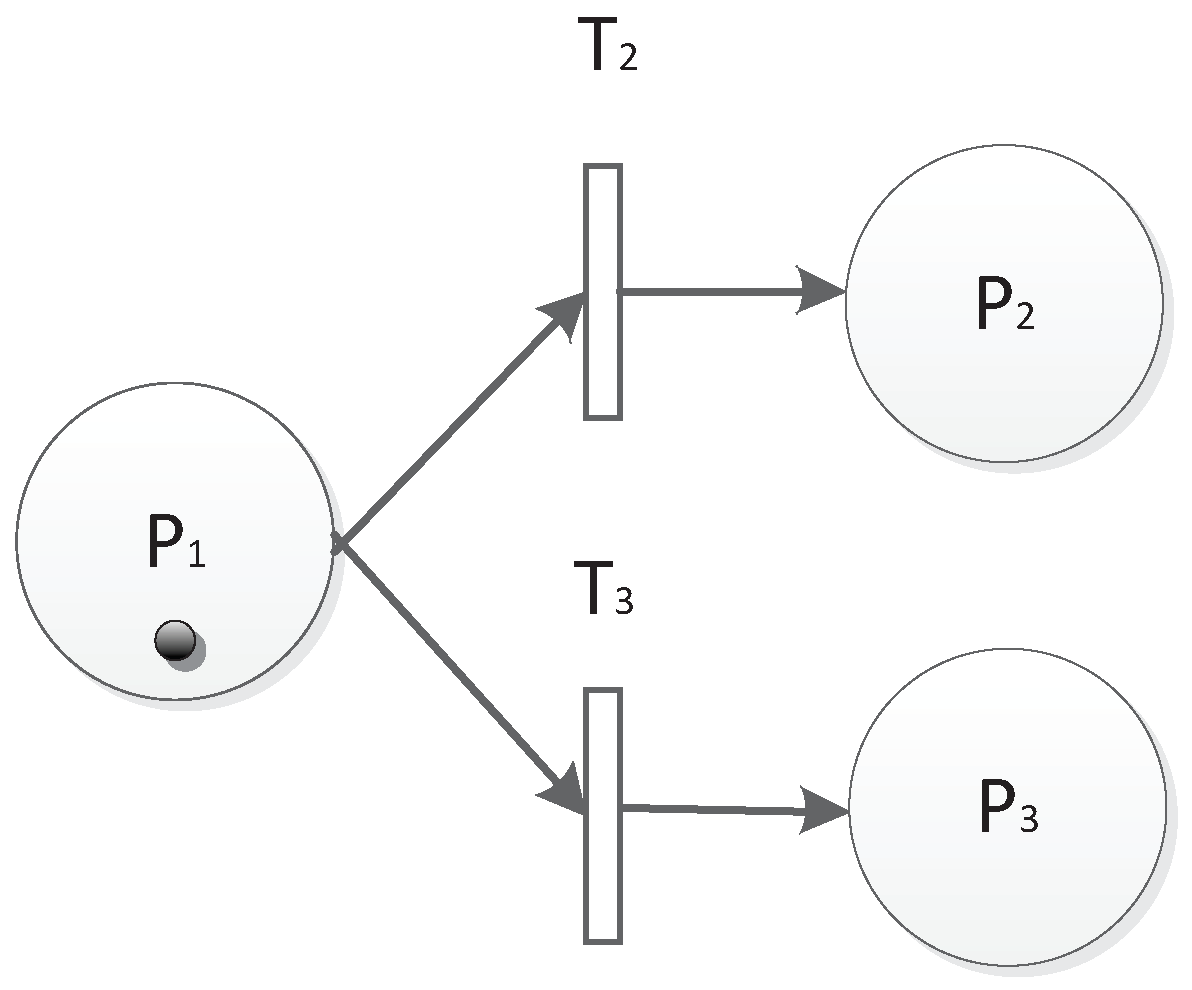
3.3. Rules in TFM
3.4. An Example
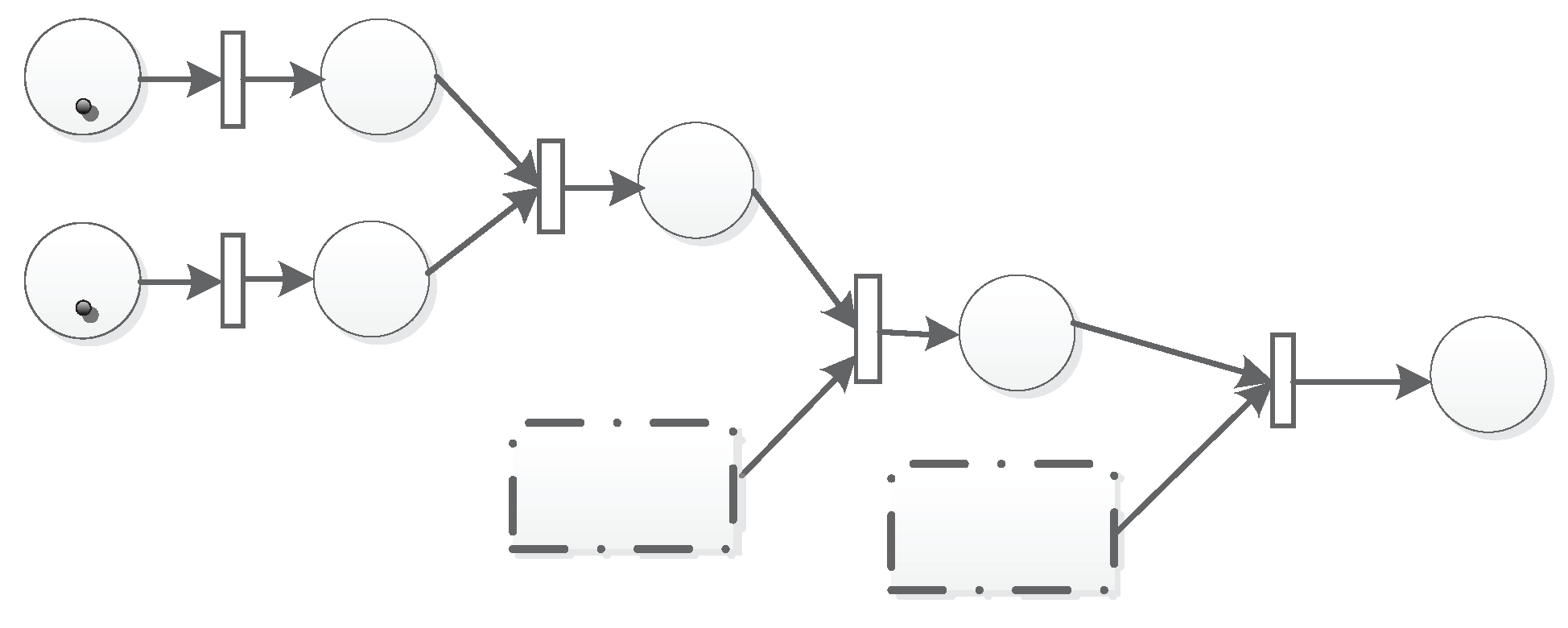
3.5. Structures of the TFM
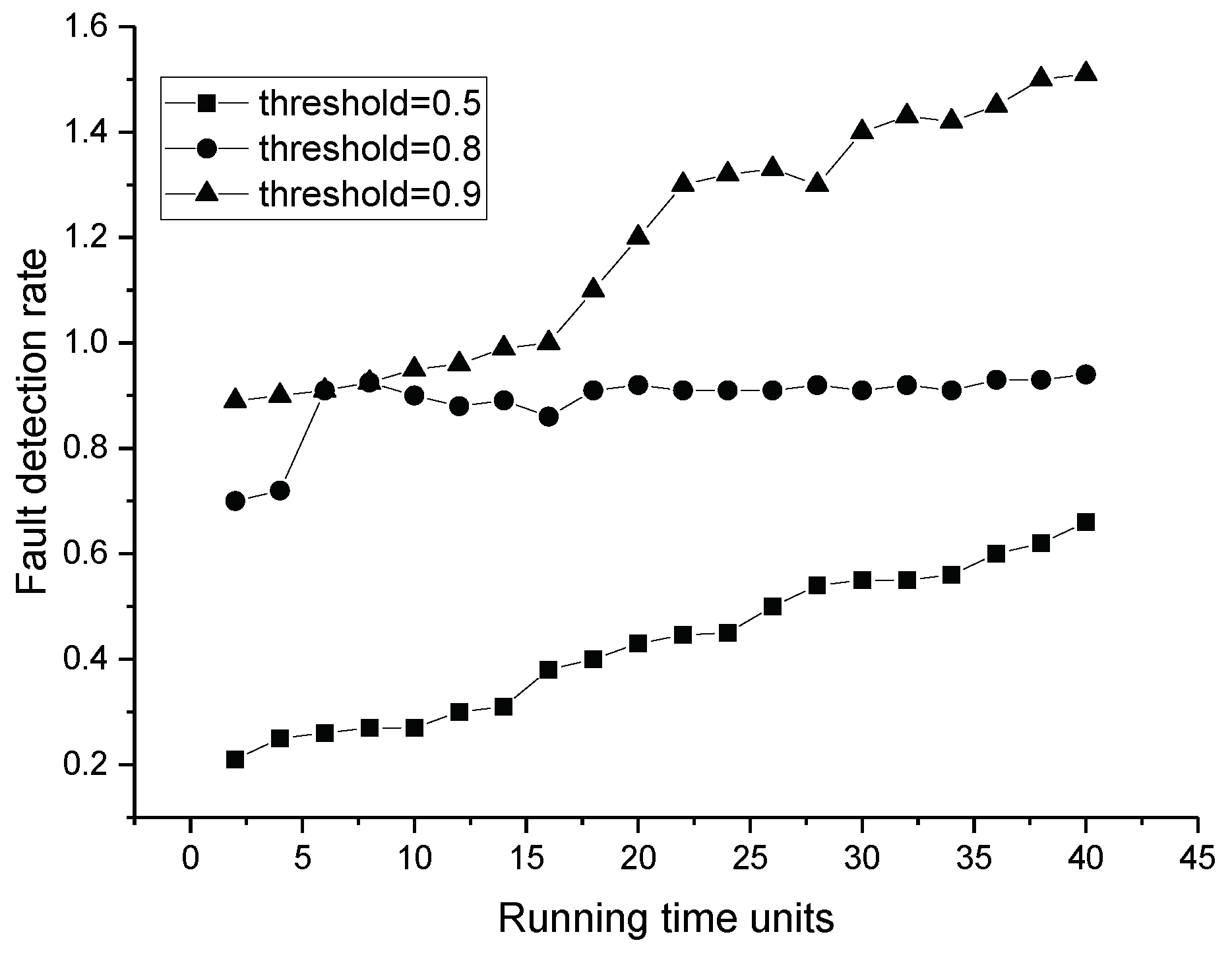
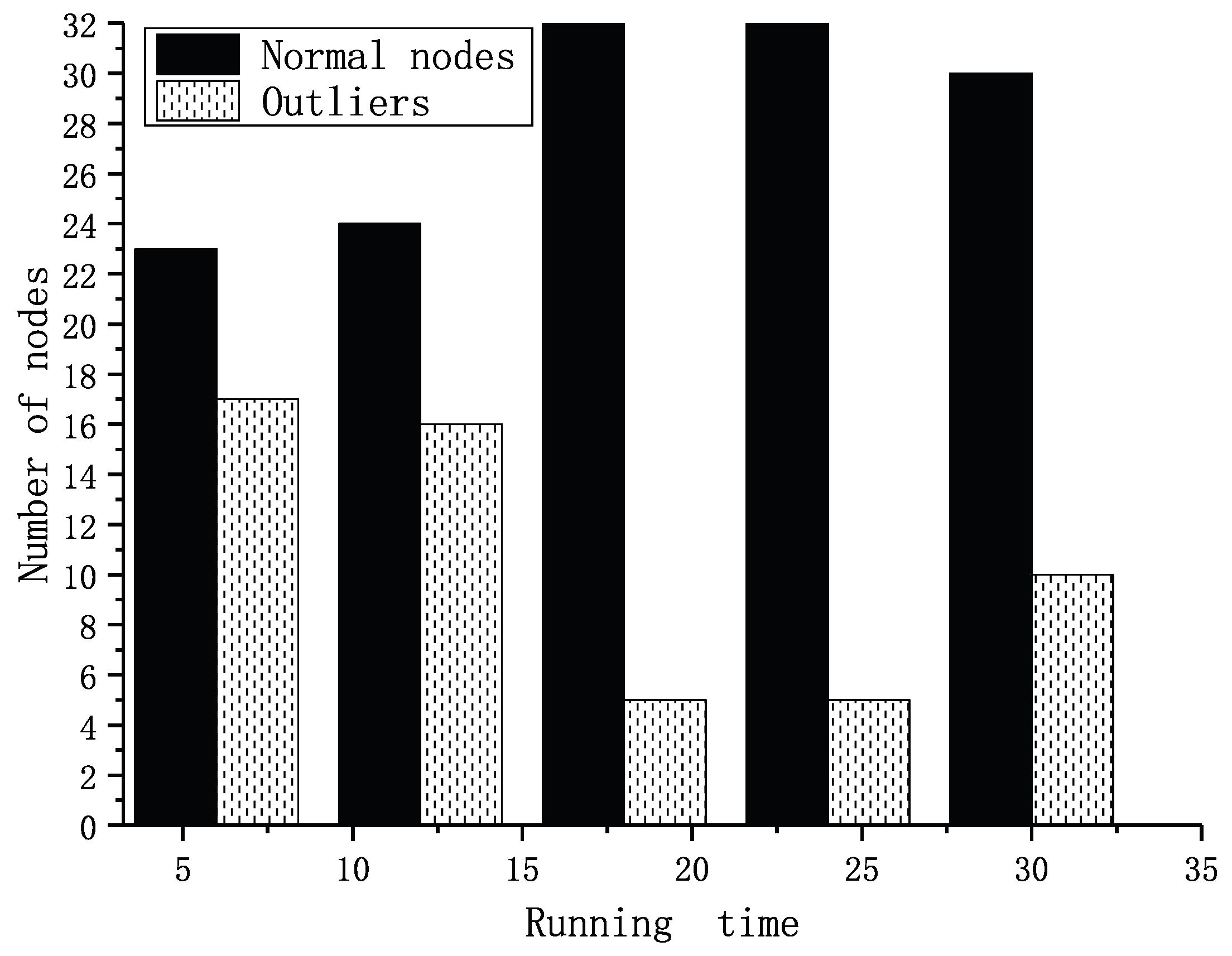
4. Analysis of the TFM
- (1)
- A node’s private trust in the last cycle.
- (2)
- The number of times it deviated from the aggregation value in the current cycle.
- (3)
- The number of times it sensed the same data consecutively.
4.1. Analysis
4.2. The TFM for the Trust Model Based on Multi-Factors
| Algorithm 1 TFM analysis algorithm. |
| Input: Input: Multi-factors; Thresholds; Weights; Lower time; Upper time; Output: Node status; j=0; while { for (i=0; i<n; i++) { if calculate using Equation (9); } calculate using Equation (8); if j++; } |
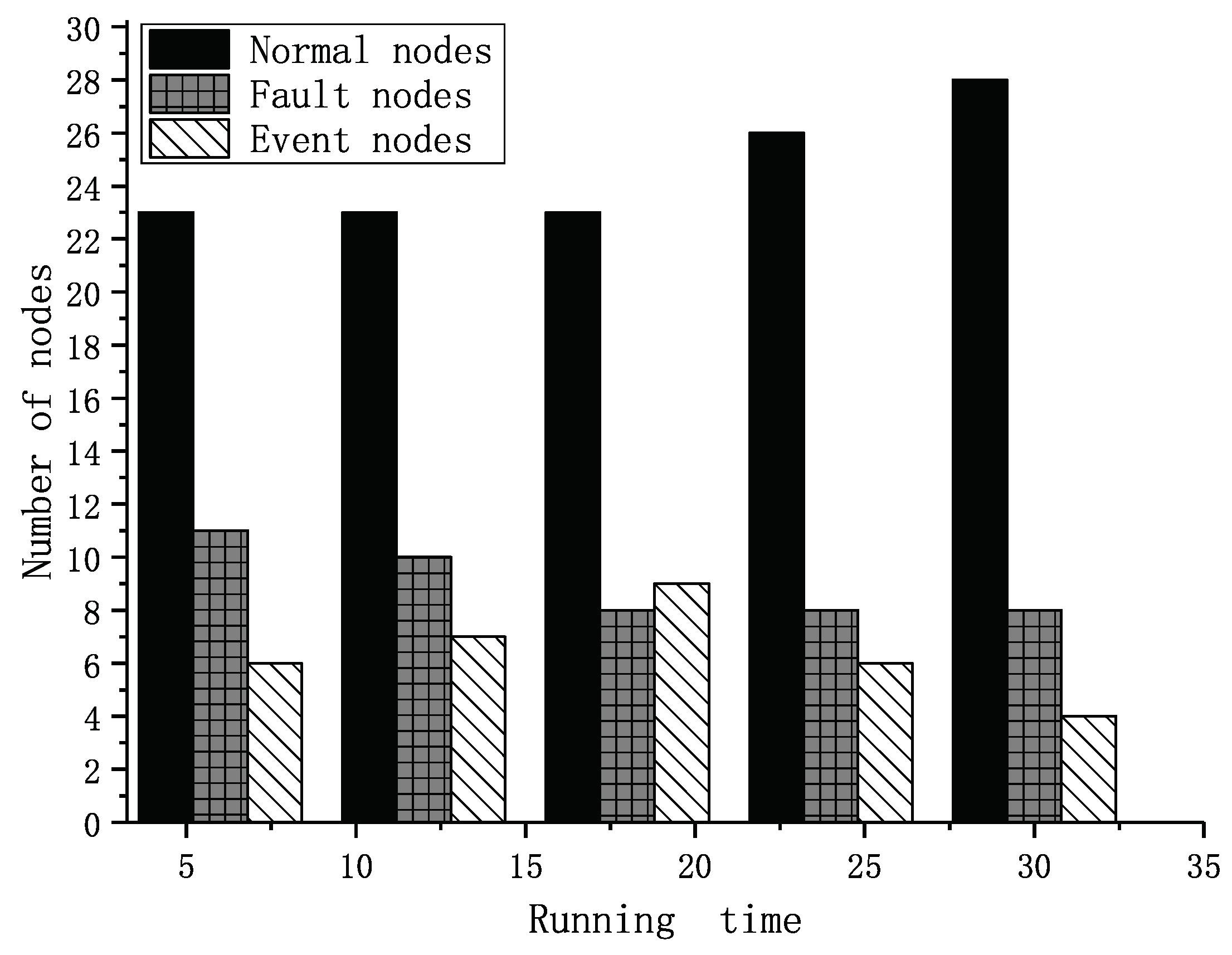
5. Implementation of the TFM
6. Conclusions and Future Work
Author Contributions
Funding
Conflicts of Interest
Abbreviations
| WSNs | Wireless Sensor Networks |
| TFM | Trust-based Formal Model |
| GME | Generic Modeling Environment |
| ROWN | Resource-Oriented Workflow Nets |
References
- Butun, I.; Morgera, S.D.; Sankar, R. A survey of intrusion detection systems in wireless sensor networks. IEEE Commun. Surv. Tutor. 2014, 16, 266–282. [Google Scholar] [CrossRef]
- Boubiche, S.; Boubiche, D.E.; Bilami, A.; Toral-Cruz, H. Big Data Challenges and Data Aggregation Strategies in Wireless Sensor Networks. IEEE Access 2018, 6, 20558–20571. [Google Scholar] [CrossRef]
- Munir, A.; Gordon-Ross, A.; Ranka, S. Modeling and Analysis of Fault Detection and Fault Tolerance in Embedded Wireless Sensor Networks. In Modeling and Optimization of Parallel and Distributed Embedded Systems; John Wiley & Sons, Ltd: Hoboken, NJ, USA, 2016. [Google Scholar] [CrossRef]
- Muhammed, T.; Shaikh, R.A. An analysis of fault detection strategies in wireless sensor networks. J. Netw. Comput. Appl. 2017, 78, 267–287. [Google Scholar] [CrossRef]
- Zidi, S.; Moulahi, T.; Alaya, B. Fault detection in wireless sensor networks through SVM classifier. IEEE Sens. J. 2018, 18, 340–347. [Google Scholar] [CrossRef]
- Chanak, P.; Banerjee, I. Fuzzy rule-based faulty node classification and management scheme for large scale wireless sensor networks. Expert Syst. Appl. 2016, 45, 307–321. [Google Scholar] [CrossRef]
- Jia, S.; Ma, L.; Qin, D. Fault Detection Modelling and Analysis in a Wireless Sensor Network. J. Sens. 2018, 2018, 7935802. [Google Scholar] [CrossRef]
- Sharma, K.P.; Sharma, T.P. rDFD: Reactive distributed fault detection in wireless sensor networks. Wirel. Netw. 2017, 23, 1145–1160. [Google Scholar] [CrossRef]
- Cheng, Y.; Liu, Q.; Wang, J.; Wan, S.; Umer, T. Distributed Fault Detection for Wireless Sensor Networks Based on Support Vector Regression. Wirel. Commun. Mob. Comput. 2018, 2018, 4349795. [Google Scholar] [CrossRef]
- Hidoussi, F.; Toral-Cruz, H.; Boubiche, D.E.; Lakhtaria, K.; Mihovska, A.; Voznak, M. Centralized IDS Based on Misuse Detection for Cluster-Based Wireless Sensors Networks. Wirel. Pers. Commun. 2015, 85, 207–224. [Google Scholar] [CrossRef]
- Rani, V.S. Review of Trust Models in Wireless Sensor Networks. Int. J. Comput. Inf. Eng. 2014, 8, 371–377. [Google Scholar]
- Wang, J.; Jiang, S.; Fapojuwo, A.O. A Protocol Layer Trust-Based Intrusion Detection Scheme for Wireless Sensor Networks. Sensors 2017, 17, 1227. [Google Scholar] [CrossRef]
- Chen, Z.; Tian, L.; Lin, C. Trust Model of Wireless Sensor Networks and Its Application in Data Fusion. Sensors 2017, 17, 703. [Google Scholar] [CrossRef] [PubMed]
- Gu, X.; Qiu, J.; Wang, J. Research on Trust Model of Sensor Nodes in WSNs. Procedia Eng. 2012, 29, 909–913. [Google Scholar]
- Yim, S.J.; Choi, Y.H. An Adaptive Fault-Tolerant Event Detection Scheme for Wireless Sensor Networks. Sensors 2010, 10, 2332–2347. [Google Scholar] [CrossRef]
- Wang, N.; Chen, Y. A Comprehensive Trust Model Based on Multi-factors for WSNs. Int. J. Comput. Commun. Control 2015, 10, 257–271. [Google Scholar] [CrossRef][Green Version]
- Wang, J. Petri Nets for Dynamic Event-Driven System Modeling. In Handbook of Dynamic System Modeling; Fishwick, P., Ed.; CRC Press: Boca Raton, FL, USA, 2007; Chapter 24. [Google Scholar]
- Wang, J. Timed Petri Nets: Theory and Application; Kluwer Academic Publishers: Boston, MA, USA, 1998. [Google Scholar]
- Qasim, M.; Hasan, O.; Elleuch, M.; Tahar, S. Formalization of Normal Random Variables in HOL. In Intelligent Computer Mathematics; Kohlhase, M., Johansson, M., Miller, B., de Moura, L., Tompa, F., Eds.; Springer International Publishing: Cham, Switzerland, 2016; pp. 44–59. [Google Scholar]
- Elleuch, M.; Hasan, O.; Tahar, S.; Abid, M. Formal probabilistic analysis of detection properties in wireless sensor networks. Formal Aspects Comput. 2015, 27, 79–102. [Google Scholar] [CrossRef]
- Riaz, S.; Afzaal, H.; Imran, M.; Zafar, N.A.; Aksoy, M.S. Formalizing Mobile Ad Hoc and Sensor Networks Using VDM-SL. Procedia Comput. Sci. 2015, 63, 148–153. [Google Scholar] [CrossRef][Green Version]
- Man, K.L.; Krilavičius, T.; Vallee, T.; Leung, H.L. TEPAWSN: A Formal Analysis Tool for Wireless Sensor Networks. Int. J. Res. Rev. Comput. Sci. 2009, 1, 24. [Google Scholar]
- Ölveczky, P.C.; Thorvaldsen, S. Formal Modeling and Analysis of the OGDC Wireless Sensor Network Algorithm in Real-Time Maude. In Formal Methods for Open Object-Based Distributed Systems; Bonsangue, M.M., Johnsen, E.B., Eds.; Springer: Berlin/Heidelberg, Germany, 2007; pp. 122–140. [Google Scholar]
- Ölveczky, P.C.; Meseguer, J. Specification and Analysis of Real-Time Systems Using Real-Time Maude. In Fundamental Approaches to Software Engineering; Wermelinger, M., Margaria-Steffen, T., Eds.; Springer: Berlin/Heidelberg, Germany, 2004; pp. 354–358. [Google Scholar]
- Agha, G.; Meseguer, J.; Sen, K. PMaude: Rewrite-based Specification Language for Probabilistic Object Systems. Electron. Notes Theor. Comput. Sci. 2006, 153, 213–239. [Google Scholar] [CrossRef]
- Zayani, H.; Barkaoui, K.; Ayed, R.B. Probabilistic verification and evaluation of Backoff procedure of the WSN ECo-MAC protocol. Int. J. Wirel. Mob. Netw. 2010, 2, 156–170. [Google Scholar] [CrossRef]
- Fischer, F.; Deutscher, J. Algebraic fault detection and isolation for parabolic distributed–parameter systems using modulation functions. IFAC-PapersOnLine 2016, 49, 162–167. [Google Scholar] [CrossRef]
- Silva, D.S.; Resner, D.; de Souza, R.L.; Martina, J.E. Formal Verification of a Cross-Layer, Trustful Space-Time Protocol for Wireless Sensor Networks. Lect. Notes Comput. Sci. 2016, 10063, 426–443. [Google Scholar]
- Testa, A.; Cinque, M.; Coronato, A.; De Pietro, G.; Augusto, J.C. Heuristic strategies for assessing wireless sensor network resiliency: An event-based formal approach. J. Heuristics 2015, 21, 145–175. [Google Scholar] [CrossRef]
- Babich, F.; Deotto, L. Formal methods for specification and analysis of communication protocols. IEEE Commun. Surv. Tutor. 2002, 4, 2–20. [Google Scholar] [CrossRef]
- Wang, J.; Li, D. Resource Oriented Workflow Nets and Workflow Resource Requirement Analysis. Int. J. Softw. Eng. Knowl. Eng. 2013, 23, 677–693. [Google Scholar] [CrossRef]
- Lefebvre, D.; Aguayo-Lara, E. A Discussion on Fault detection for a class of Hybrid Petri Nets. IFAC-PapersOnLine 2017, 50, 6837–6842. [Google Scholar] [CrossRef]
- Cho, J.H.; Chang, M.; Chen, I.R.; Swami, A. A Provenance-Based Trust Model for Delay Tolerant Networks. In Trust Management VI; Dimitrakos, T., Moona, R., Patel, D., McKnight, D.H., Eds.; Springer: Berlin/Heidelberg, Germany, 2012; pp. 52–67. [Google Scholar]
- Lory, P. A colored Petri net trust model. In Proceedings of the 14th International Workshop on Database and Expert Systems Applications, Prague, Czech Republic, 1–5 September 2003; pp. 415–419. [Google Scholar] [CrossRef]
- Kapitanova, K.; Son, S.H. MEDAL: A coMpact event description and analysis language for wireless sensor networks. In Proceedings of the 2009 Sixth International Conference on Networked Sensing Systems (INSS), Pittsburgh, PA, USA, 17–19 June 2009; pp. 1–4. [Google Scholar] [CrossRef]
- Wang, N.; Chen, X. A Formal Model for Temporal—Spatial Event in Internet of Vehicles. Lect. Notes Comput. Sci. 2018, 11280, 222–234. [Google Scholar]
- Hodge, V.J.; Austin, J. A Survey of Outlier Detection Methodologies. Artif. Intell. Rev. 2004, 22, 85–126. [Google Scholar] [CrossRef]
- Chandola, V.; Banerjee, A.; Kumar, V. Outlier Detection: A Survey; Technical Report 07-017; University of Minnesota: Minneapolis, MN, USA, 2007. [Google Scholar]
- Feng, R.; Che, S.; Wang, X.; Yu, N. Trust Management Scheme Based on D-S Evidence Theory for Wireless Sensor Networks. Int. J. Distrib. Sens. Netw. 2013, 2013, 130–142. [Google Scholar] [CrossRef]
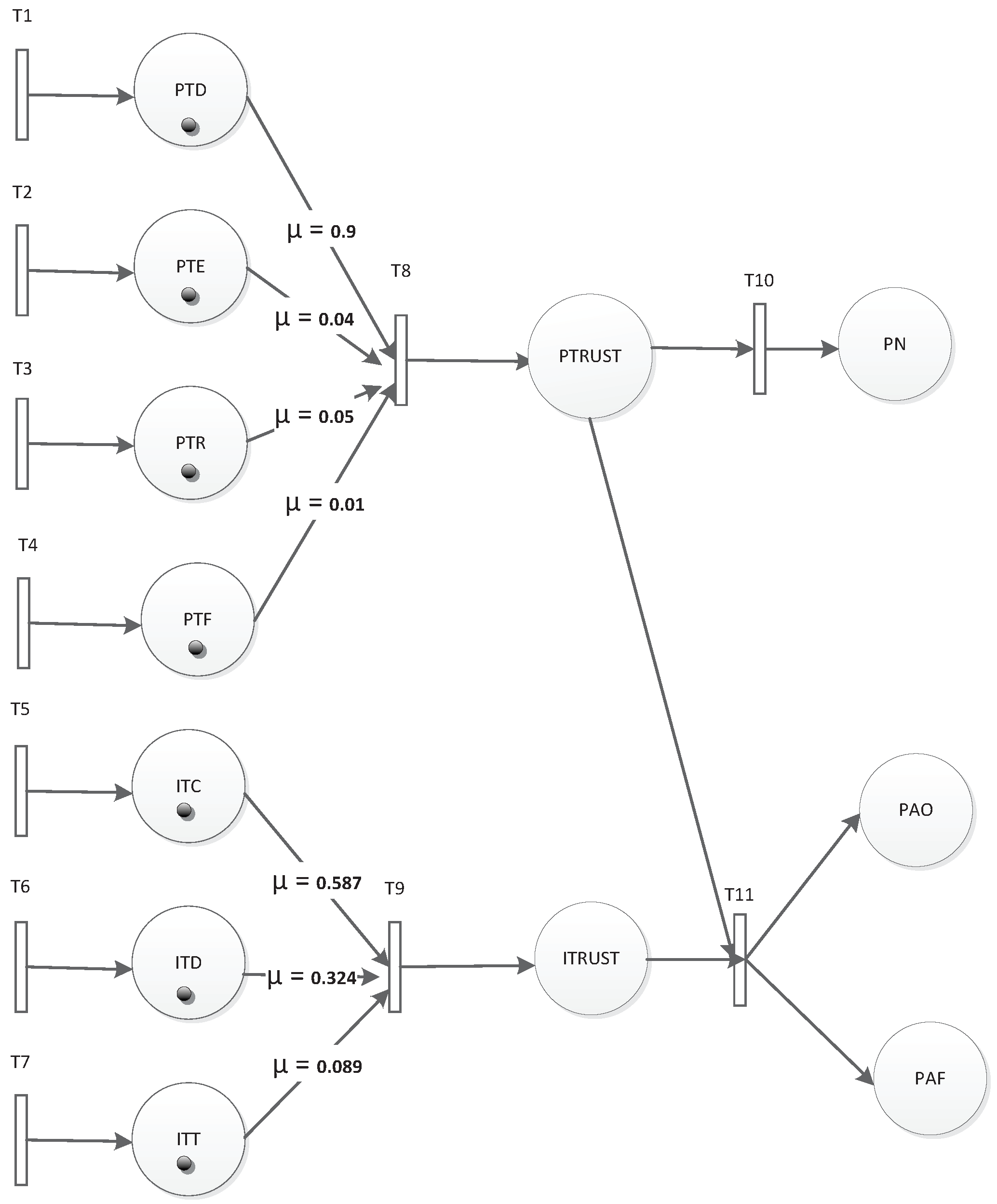
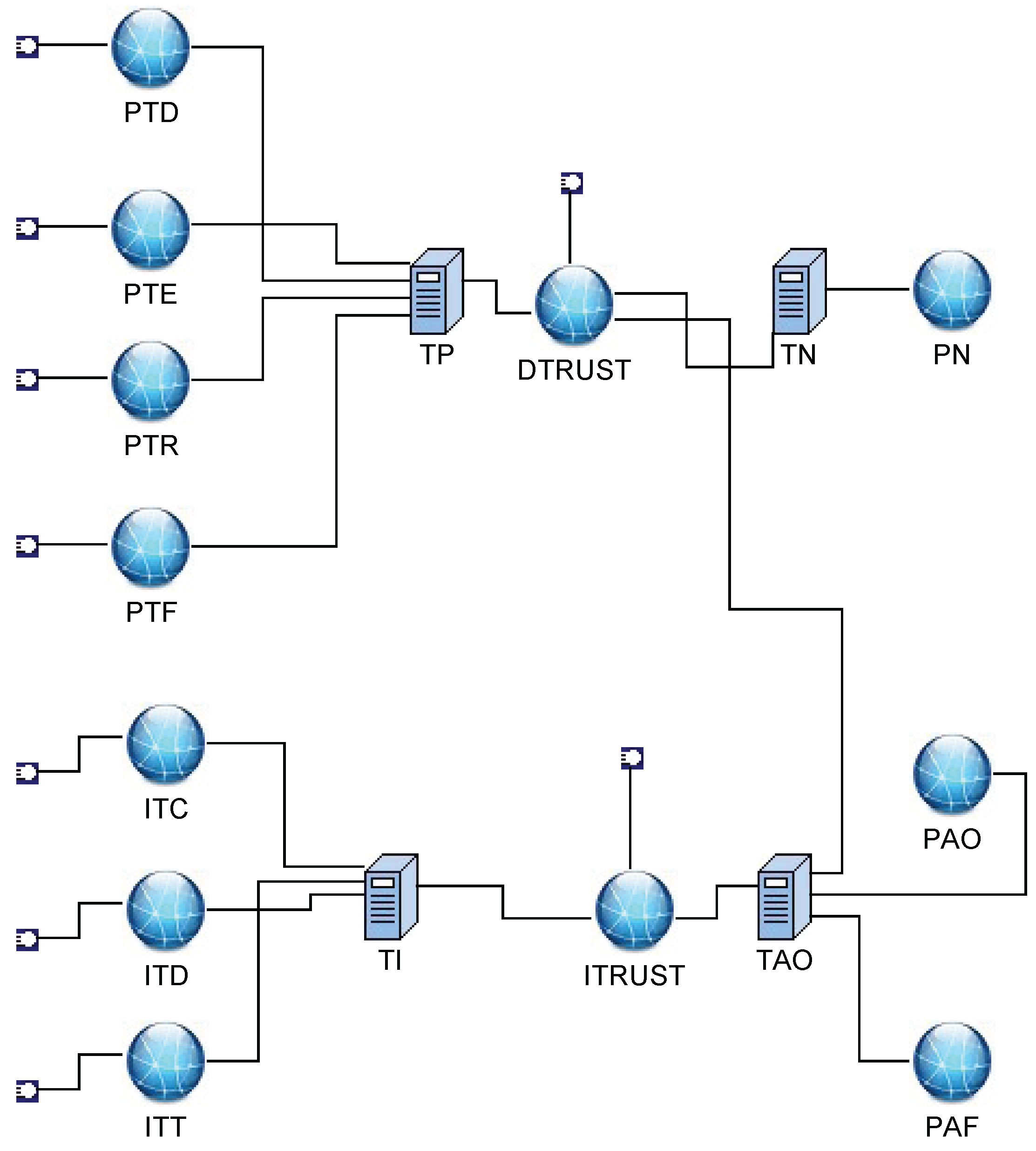

| ITC | ITD | ITT |
|---|---|---|
| valid communication | data similarity | clock synchronization |
| PTD | PTE | PTR | PTF |
|---|---|---|---|
| History data | Remaining energy | Penalty of misreading | Consecutive same sensing |
| Place | Value1 | Value2 | Value3 |
|---|---|---|---|
| PTD | 0.89 | 0.29 | 0.29 |
| PTE | 0.93 | 0.93 | 0.93 |
| PTR | 0.7 | 0.7 | 0.7 |
| PTF | 0.88 | 0.88 | 0.88 |
| ITC | 0.94 | 0.94 | 0.64 |
| ITD | 0.82 | 0.82 | 0.82 |
| ITT | 0.77 | 0.77 | 0.77 |
| ITC | ITT | ITD | PTD | PTE | PTR | PTF |
|---|---|---|---|---|---|---|
| 0.587 | 0.324 | 0.089 | 0.9 | 0.04 | 0.05 | 0.01 |
| Transition | Enabled Time | Firing Time | Firing Order | |
|---|---|---|---|---|
| T1 | [1, 5] | 1 | 1.5 | 1 |
| T2 | [2, 4] | 2 | 1 | 3 |
| T3 | [2, 5] | 1 | 0.5 | 2 |
| T4 | [3, 6] | 2 | 1 | 4 |
| T5 | [2, 3] | 2 | 1.5 | 2 |
| T6 | [1, 4] | 2 | 1 | 1 |
| T7 | [2, 4] | 1 | 0.5 | 3 |
| T8 | [1, 2] | 1 | 1 | 1 |
| T9 | [2, 4] | 2 | 2.5 | 1 |
| T10 | [2, 4] | 2 | 3 | 1 |
| PN | PAO | PAF | |
|---|---|---|---|
| D | { } | { } | { } |
| M | |||
| 0.882> 0.8 | 0.886 > 0.8 | 0.71 < 0.8 |
© 2019 by the authors. Licensee MDPI, Basel, Switzerland. This article is an open access article distributed under the terms and conditions of the Creative Commons Attribution (CC BY) license (http://creativecommons.org/licenses/by/4.0/).
Share and Cite
Wang, N.; Wang, J.; Chen, X. A Trust-Based Formal Model for Fault Detection in Wireless Sensor Networks. Sensors 2019, 19, 1916. https://doi.org/10.3390/s19081916
Wang N, Wang J, Chen X. A Trust-Based Formal Model for Fault Detection in Wireless Sensor Networks. Sensors. 2019; 19(8):1916. https://doi.org/10.3390/s19081916
Chicago/Turabian StyleWang, Na, Jiacun Wang, and Xuemin Chen. 2019. "A Trust-Based Formal Model for Fault Detection in Wireless Sensor Networks" Sensors 19, no. 8: 1916. https://doi.org/10.3390/s19081916
APA StyleWang, N., Wang, J., & Chen, X. (2019). A Trust-Based Formal Model for Fault Detection in Wireless Sensor Networks. Sensors, 19(8), 1916. https://doi.org/10.3390/s19081916





