1. Introduction
A wireless sensor network consists of sink nodes and sensor nodes [
1]. In the network, a sensor node gathers information in the vicinity and delivers it to a sink node. To carry out such a mission, a sensor node is typically equipped with a battery that powers the sensor node itself. A wireless sensor network is often deployed in a harsh environment, where batteries are hardly recharged or replaced. Consequently, issues on energy consumption have arisen in designing a wireless sensor network. Then, many efforts have been made to solve the energy problems in a wireless sensor network, most of which were focused on devising efficient communication schemes to reduce energy consumption and ultimately to extend the lifetime of the network [
2,
3,
4,
5].
Recently, radio frequency (RF) energy harvesting technologies provided us with a new paradigm for wireless sensor networks [
6,
7,
8]. These technologies are mainly divided into two categories: a category of technologies which enable sensor nodes to harvest energy by scavenging ambient RF waves and the other category of technologies which designate external RF sources to supply energy to sensor nodes by radiating RF waves. In [
9], the capacitor leakage problem was taken into account when sensor nodes harvest ambient RF energy. In [
10,
11], it was assumed that a sensor node is able to extract information and harvest energy as well from the signal transmitted by another node. In [
12], cooperation of licensed and unlicensed users was investigated in a cognitive network where unlicensed users harvest ambient energy to charge their batteries. In [
13], a cognitive network was considered in which a sensor node senses the spectrum and harvests energy in the spectral band used by access points. By harvesting RF energy, a wireless sensor network can overcome the battery constraint and is, at least theoretically, able to live eternally. However, harvested energy is not enough to directly power a sensor node but merely capable of charging an internal capacitor, especially, when a sensor node harvests energy by scavenging ambient RF waves. Moreover, it takes quite a long time to charge the capacitor compared to the time for which the sensor node actually participates in communicating with a sink node [
14,
15]. As a result, energy is still scarce in practice and a sensor node should repeat the transition between the long harvesting state and the short communicating state. For example, it was reported that the harvesting state has to last roughly 20 times longer than the communicating state in [
16].
A medium access control (MAC) scheme is needed for a sensor node to deliver information to a sink node, especially, in a wireless sensor network where several sensor nodes attempt to send their data to a common sink node. In an RF energy harvesting wireless sensor network, which suffers from a scarcity of energy, signaling is not easily provided between sink and sensor nodes. Furthermore, a sensor node is hardly able to exchange information with another sensor node. Thus, a sophisticated MAC scheme of scheduling-type is not suitable for supporting a sensor node to deliver data to a sink node. Structural simplicity has to be within the MAC scheme in an RF energy harvesting wireless sensor network. In the literature, a set of MAC schemes have been reported for energy harvesting wireless sensor networks [
17,
18,
19,
20,
21,
22,
23,
24,
25,
26,
27,
28,
29,
30,
31,
32]. In [
17], a polling-based MAC scheme was introduced in which the sink node gives a chance of transmitting data with a certain probability to a sensor node. Then, the proposed scheme was evaluated under the assumption that sensor nodes harvest solar or thermal energy. As MAC schemes for energy harvesting wireless sensor networks, time division multiple access (TDMA) and framed and slotted ALOHA were considered in [
18]. To maintain slotted time structure, such schemes were also complemented by periodic signaling of the sink node destined to sensor nodes. In [
19,
29], MAC schemes based on carrier sense multiple access with collision avoidance (CSMA/CA) were proposed. These schemes were designed to assign an external RF source to supply RF energy to a sensor node. In [
20], a MAC scheme based on CSMA/CA was addressed. To behave according to the scheme, a sensor node was assumed to continuously harvest energy from surrounding environments. In [
21,
26], TDMA and slotted CSMA/CA were respectively used for sensor nodes to send their data to the sink node, where the sink node was assumed to be able to receive data from sensor nodes and send RF energy to sensor nodes simultaneously. In [
22], a MAC scheme using two different polling methods was suggested for supporting two priority classes in a wireless body area network. In this work, sensor nodes were assumed to harvest energy in human body. Also, a simulation method was employed to evaluate the suggested MAC scheme. In [
23], relays were deployed at a wireless body area network. Then, a MAC scheme was proposed for cooperative communications. In this work, relays were assumed to harvest thermal or biochemical energy in human body. Also, the proposed MAC scheme was evaluated by use of a simulation method. In [
27], duty cycles were investigated in energy harvesting wireless sensor networks where sensor nodes harvest photovoltaic energy. In [
28], a MAC scheme which is compatible with IEEE 802.15.4 standard was proposed for RF energy harvesting wireless sensor networks. To use the scheme, the authors assumed that an external RF source supply energy to sensor nodes by radiating RF waves. In [
30], a MAC scheme based on distributed coordination function in IEEE 802.11 was proposed for sensor nodes to send data to an access point. In this MAC scheme, access points were assumed to supply RF energy to sensor nodes. In [
31], a MAC scheme was introduced to meet the quality-of-service (QoS) requirement per priority class. The scheme was then evaluated under the assumption that sensor nodes harvest solar energy. In [
32], a MAC scheme based on slotted ALOHA was reported for energy harvesting wireless sensor network, where the sink node was assumed to be able to receive data from sensor nodes and send RF energy to sensor nodes simultaneously. Considerable effort has been made to device MAC schemes for wireless sensor networks in which sensor nodes harvest solar energy or receive RF energy from external RF sources. On the other hand, a limited number of MAC schemes have been reported for wireless sensor networks where sensor nodes harvest RF energy only by scavenging ambient RF waves. Some of the MAC schemes were designed to let sensor nodes to often make a transit between transmitter and receiver modes. Unfortunately, such schemes may be rather complicated to follow in case sensor nodes can only harvest weak RF energy, e.g., −20 dBm [
15], from ambient RF waves so that sensor nodes are not able to operate with being directly powered by harvested energy but also need long time, e.g., 3 h [
15], to charge its capacitor. Some other MAC schemes were devised based on the technologies which enable a sink node to receive data from sensor nodes and send RF energy to sensor nodes simultaneously. These technologies have not yet fully matured to be hired in various wireless environments [
33,
34]. Also, they are not applicable to a wireless sensor network in which sensor nodes scavenge ambient RF waves to harvest energy. In previous studies, simulation methods were often used to evaluate proposed MAC schemes. Compared with deriving mathematical expressions for performance measures, simulation methods are advantageous in the sense that they are able to embrace complex practical models for energy harvesting wireless sensor networks. On the other hand, deriving exact, or alternatively approximate, expressions provides a handy tool for optimization, which typically requires vast simulation results. In wireless sensor networks where sensor nodes harvest energy by scavenging ambient RF waves; However, there have been reported few results about exact expressions of performance measures, e.g., throughput, for evaluating as well as optimizing a MAC scheme.
In this paper, we consider an RF energy harvesting wireless sensor network in which sensor nodes harvest RF energy by scavenging ambient RF waves. Upon perception of such difficulties in an RF energy harvesting wireless sensor network, our practical choice for the MAC scheme is a basic contending-type MAC scheme based on pure ALOHA [
35]. In the basic MAC scheme, a sensor node harvests energy from ambient RF waves, charges a capacitor, senses the environment, generates a packet, takes a back-off time, and transmits the packet. Then, the sensor node simply repeats the procedures above. (Please note that the basic MAC scheme is not identical to pure ALOHA but only employs some features of pure ALOHA including back-off times.) If two or more sensor nodes may simultaneously send their packets to a sink node, a collision of the packets takes place and the sink node may not able to identify any packet. However, the basic MAC scheme is not able to perfectly prevent such a collision of packets since it belongs to ALOHA clan. As a result, the throughput that the basic MAC scheme can attain is deteriorated by a collision of packets. Using the renewal theory, we thus derive an exact expression of the throughput that the basic MAC scheme can achieve. In various case studies, we then look for a way to enhance the throughput by use of the throughput formula. Specifically, we seek answers to the fundamental questions; what is an optimal distribution for the back-off time which maximizes the total throughput?”, “Is it possible to effectively increase the total throughput by taking back-off times?” and “how to shape the distribution for the back-off time as to improve the total throughput?” There have been classical studies on back-off methods. In [
36], several back-off methods, which adjust the back-off times as retransmissions go on, were considered in networks governed by slotted ALOHA. Then, these methods are evaluated comparatively. In [
37], an exponential back-off method was suggested for slotted ALOHA systems. Then, a simulation method was used to evaluate the proposed back-off method. In [
38], back-off methods, which dynamically control the back-off time according to the result of packet delivery, were investigated in slotted ALOHA networks. In [
39], a back-off method, which can be adopted at CSMA/CA was proposed for IEEE 802.15.4 networks. In [
40], an adaptive back-off method was explored to be used, in IEEE 802.11 wireless local area networks. In the basic MAC scheme, a sensor node is not acknowledged about its attempt to deliver a packet to the sink node. However, most of the previous studies have focused on adaptive back-off methods that rely on the result of packet delivery. The basic MAC scheme is based on pure ALOHA which works on a continuous time structure. On the other hand, many previous works have assumed MAC schemes operating on discrete time structures, e.g., slotted ALOHA. As far as we know, there has been no intensive study on back-off methods which will be employed in a contending-type MAC scheme, rooted in pure ALOHA, for RF energy harvesting wireless sensor networks.
In
Section 2, we describe a basic MAC scheme for supporting sensor nodes to deliver their data to a sink node in a wireless sensor network where sensor nodes harvest RF energy by scavenging ambient RF waves. In
Section 3, using the renewal theory, we derive an exact expression of the throughput that the basic MAC scheme is able to achieve. Also, we exactly present the throughput in a closed form when harvest times, back-off times and transmission times are exponentially distributed.
Section 4 is devoted to case studies for seeking strategies to improve the throughput by controlling back-off times. First, we find an optimal distribution for the back-off time when harvest times are deterministic. Secondly, we examine the impact of taking back-off times on the throughput when harvest times are random. Thirdly, we investigate the effect of variance of back-off time on the throughput when the sum of harvest and back-off times are governed by an Erlang distribution.
2. Basic MAC Scheme
Consider an RF energy harvesting wireless sensor network which consists of a single sink node and many sensor nodes. The sink node is laid at the center of the network and sensor nodes are scattered around the sink node. An exemplary configuration of the RF energy harvesting wireless sensor network is illustrated in
Figure 1. In the network, a sensor node harvests energy by scavenging ambient RF waves. By consuming the harvested energy, the sensor node gathers information in its vicinity and then sends the collected data to the sink node. For such delivery of data, we consider a contending-type MAC scheme, rooted in ALOHA, as follows:
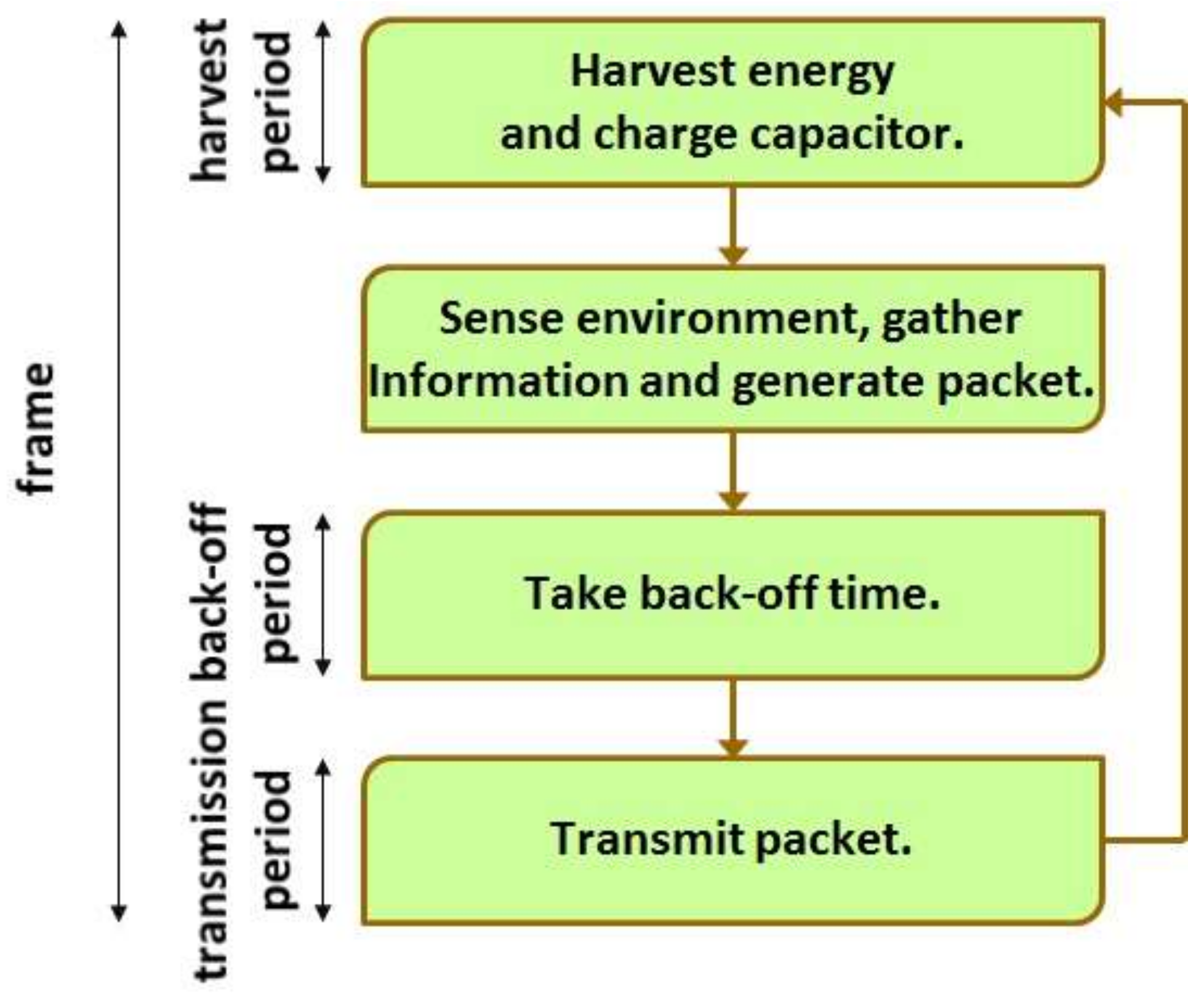
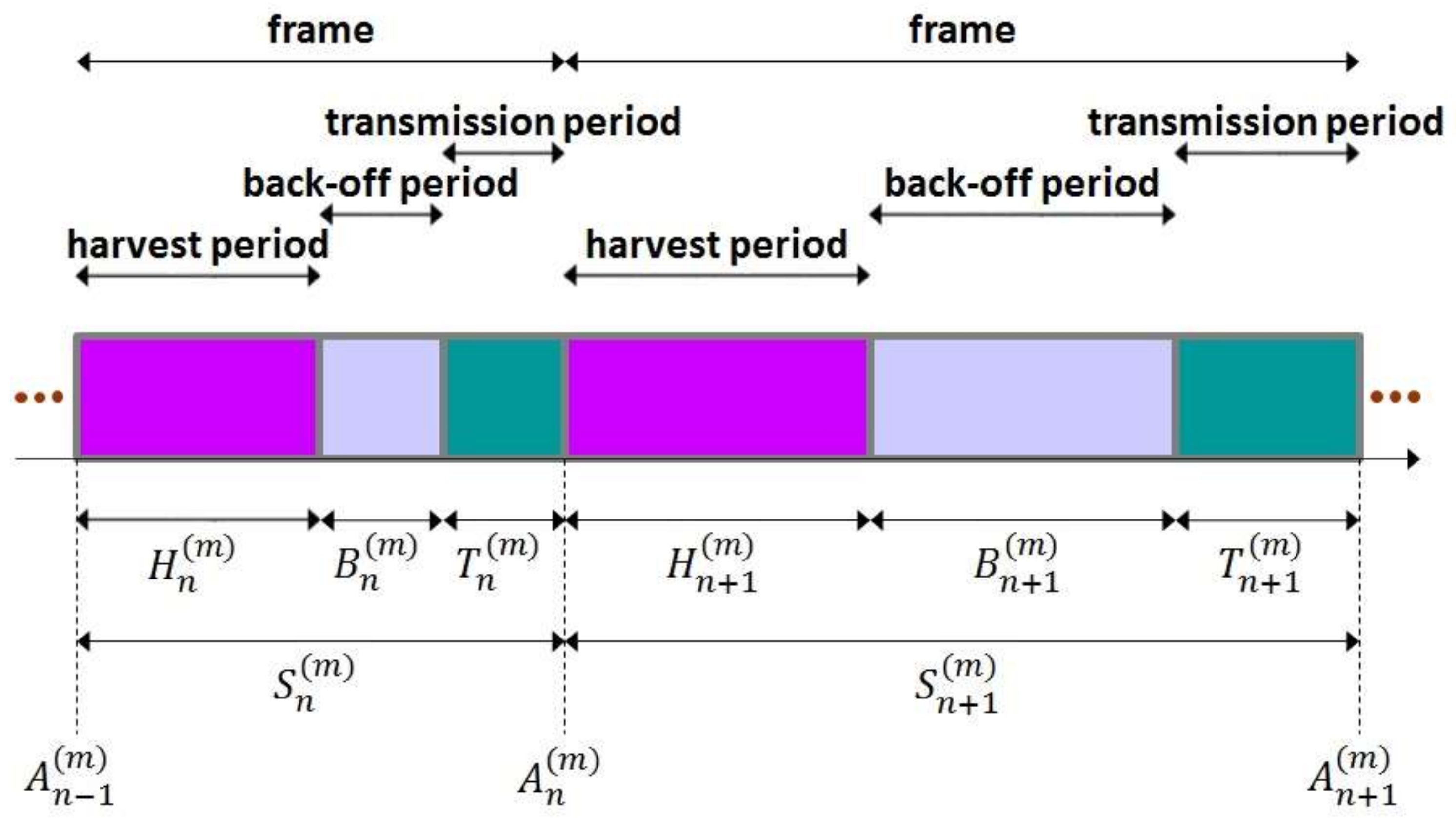
At each sensor node, time is divided into frames and a frame is partitioned into harvest period, back-off period and transmission period. (See
Figure 2.) When a frame starts at a sensor node, a harvest period of the sensor node also begins. During the harvest period, the sensor node harvests RF energy and charges the internal capacitor. Please note that the harvest period lasts until the sensor node accumulates as much energy as it can transmit a packet. As the harvest period ends, the sensor node senses the environment, collects information and encapsulates the information into a packet. Then, a back-off period of the sensor node starts. The sensor node intentionally waits for the back-off period in the expectation for reducing the possibility of packet collision. When the back-off period is over, a transmission period of the sensor node begins and the sensor node finally transmits the packet to the sink node. As the transmission period ends, the next frame starts.
Figure 3 summarizes the behavior of the basic MAC scheme considered in the paper.
According to the basic MAC scheme, two or more transmission periods of different sensor nodes may overlap. Then, the packets which are sent during these transmission periods collide and the sink node may not be able to identify any packet. Please note that the sink node returns no acknowledgement message even if it receives and identifies a packet. Thus, as a sensor node finishes transmitting a packet, the sensor node immediately discards the packet and never retransmits it. Consequently, a sensor node may lose a packet if the packet is involved in a collision.
4. Some Studies on Back-Off Time
The back-off time is a crucial factor in designing the basic MAC scheme. In this section, we consider three cases and then look for a way to improve the throughput by controlling the back-off times in each case. In the first case in which harvest times are deterministic, we find an optimal distribution for the back-off time which maximizes the total throughput. In the second case, where the harvest times are exponentially distributed, we confirm that taking proper back-off times is able to effectively enhance the total throughput. Finally, we show that shaping the distribution for the back-off time as to have high variance helps improve the total throughput.
4.1. Optimal Distribution for Back-Off Time
Suppose that harvest times and transmission times are deterministic. Then, once several packets collide, their collision will be definitely repeated forever unless the sensor nodes involved in the collision take back-off times. In this section, we focus on a case in which the harvest times and the transmission times are degenerated into some constants. Then, we obtain an optimal distribution for the back-off time which maximizes the total throughput.
Suppose that the harvest time
and the transmission time
are degenerated into positive numbers
and
respectively, i.e.,
almost surely for all
. In addition, assume that the back-off times
are strictly positive random variables which are governed by a same proper distribution with mean
. Let
denote a random variable such that
in distribution for all
and
represent the distribution function of
. Then, the probability
in (16) is expressed by
for
. From (17) and (35), we also have
as
for all
. Thus, the pairwise non-collision probability
, i.e., the probability that a packet of sensor node
does not collide with any packet of sensor node
at steady state is yielded by
for all
. Since the probability
is identical for all
, the non-collision probability
, which represents the probability that a packet of sensor node
does not collide with any other packet at steady state, is obtained by
Therefore, the nodal throughput that sensor node
can achieve
is expressed by
Moreover, the total throughput is obtained by
since nodal throughputs are identical.
First, consider the case that
. Please note that it is a practically feasible case since the harvest time is typically much longer than the transmission time in practice. By differentiating the total throughput
with respect to the expected back-off time
and then equating it to zero, we obtain a critical point, denoted by
as follows.
Please note that
is also a global maximum point. However, as far as
,
is the optimal expected back-off time since the expected back-off time
should be strictly positive. Otherwise, there exists no optimal expected back-off time. Please note that no specific distribution for the back-off time has been assumed until the optimal expected back-off time in (31) is derived. Thus, an optimal back-off time is proved not to be characterized by the distribution but only by the expected value. Suppose that
. Let
denote the maximum total throughput. Then, we have
when
. On the other hand,
as
when
.
Secondly, consider the case that
. Since
the total throughput
is bounded as follows.
In (45), the upper bound on the total throughput has a critical point, denoted by
, as follows.
Please note that
is also a global maximum point. Replacing
with
in the lower bound as well as
with
in the upper bound shown in (45), we obtain upper and lower bounds on the maximum total throughput, denoted by
, as follows.
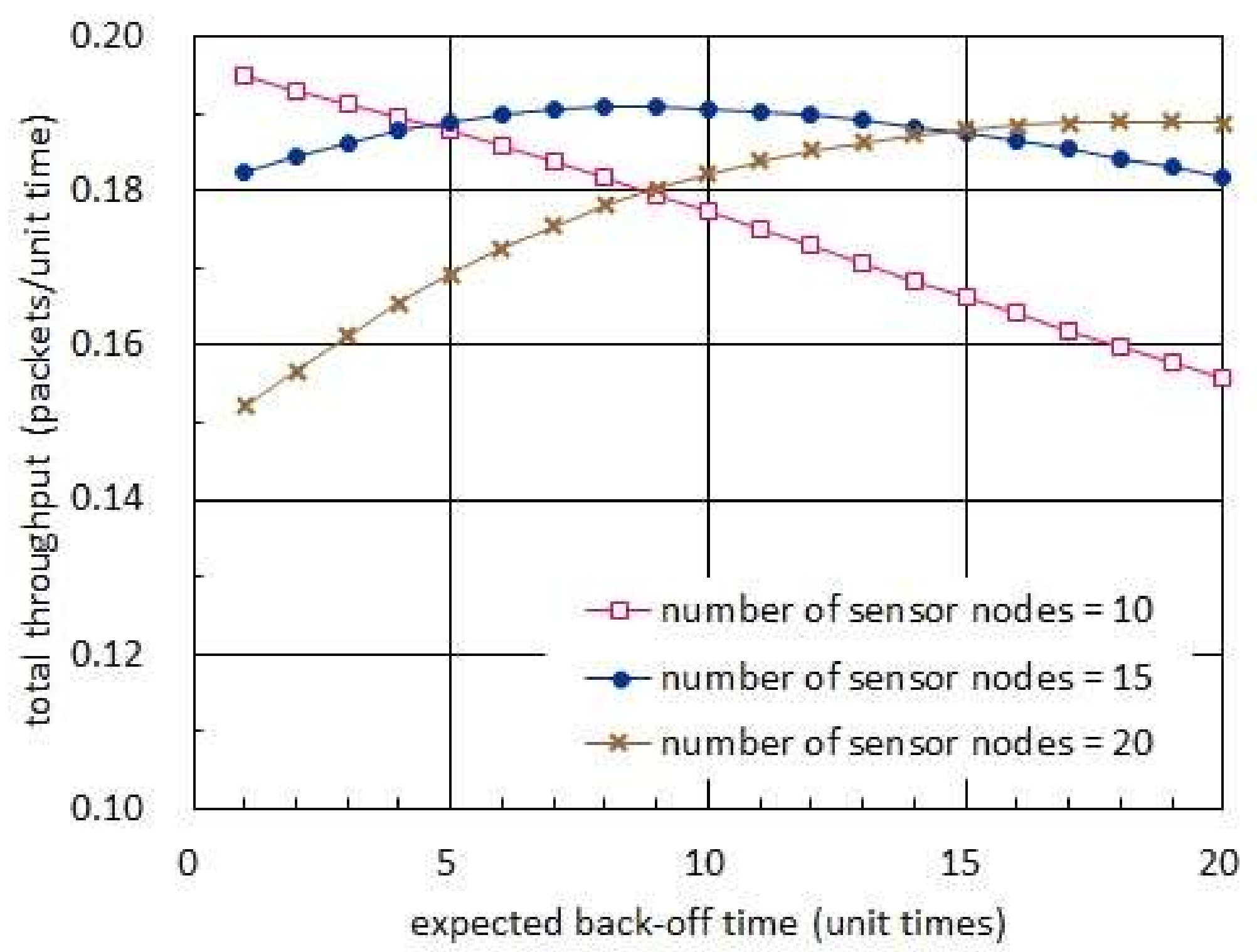
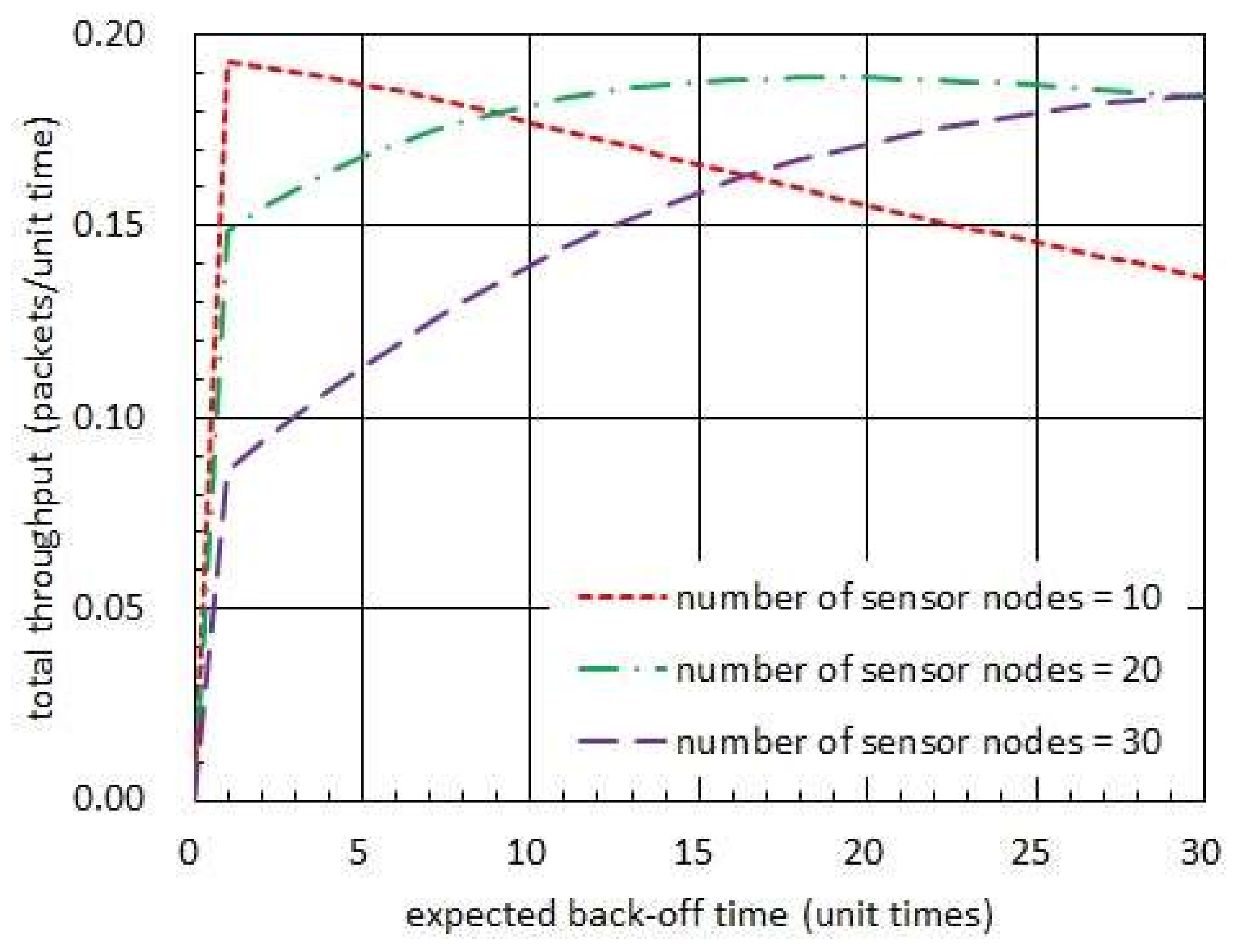
Figure 7 shows the total throughput with respect to the expected back-off time. In this figure, the harvest times are fixed to 20 unit times while the transmission times are set to be 1 unit time [
16]. In addition, the back-off times are set to have an exponential distribution. In
Figure 7, we observe that there exists an optimal expected back-off time, which maximizes the total throughput, when the number of sensor nodes is 20 or 30. On the other hand, there is no optimal value in case 10 sensor nodes reside in the network. Such a dichotomy of the expected values of back-off time corresponds to the one which results in (42) and (43), respectively. In addition, we notice that the optimal expected back-off time increases as the number of sensor nodes increases.
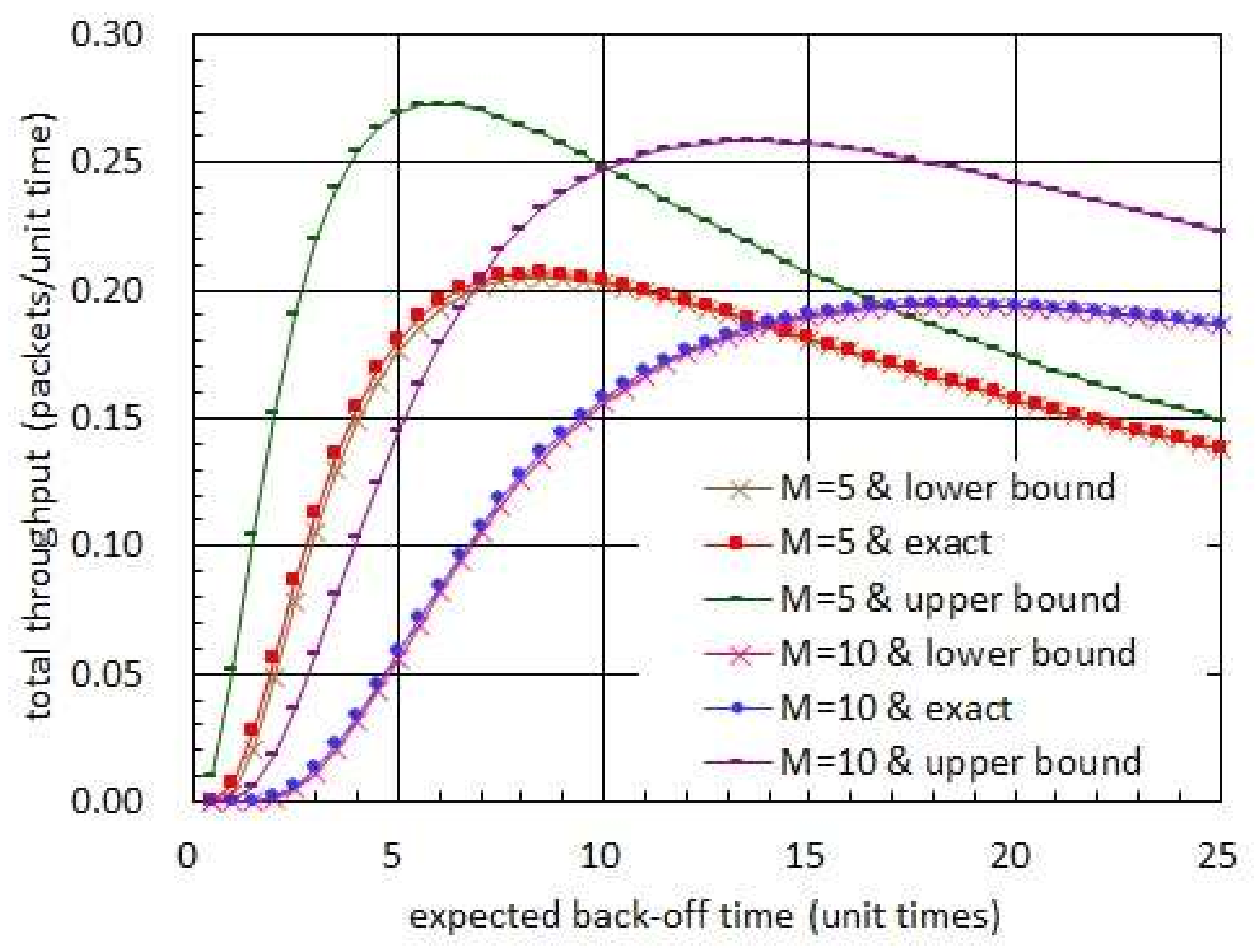
Figure 8 shows the total throughput with respect to the expected back-off time. In this figure, the harvest times are assumed to be fixed to 0.5 unit times while the transmission times are set to be 1 unit time. Also, the back-off times are set to have an exponential distribution. In figure 8, we observe that the total throughput is well bounded by the upper and lower bounds given in (45). In particular, we notice that the lower bound is highly tighter than the upper bound. Moreover, the optimal expected back-off time is fairly close to the value of expected back-off time which maximizes the lower bound.
4.2. Effectiveness of Taking Back-Off Time
Suppose that the harvest times are not deterministic. Then, due to the random fluctuations in harvest times, a collision of packets may be never repeated even if the sensor nodes, which are involved in the collision, take no back-off time at all. Furthermore, without taking back-off times, a sensor node is able to attempt to deliver packets more frequently. In this section, we consider two cases; sensor nodes take exponentially distributed back-off times in a case and sensor nodes take no back-off time in the other case. Then, we investigate whether taking positive back-off times can help enhance the throughput or not.
First, consider the case in which sensor nodes take positive back-off times. Suppose that the harvest times are governed by a same exponential distribution with mean . Let denote a random variable such that for all . The distribution function of , denoted by , is given in (17). In this case, the back-off times are set to identically have an exponential distribution with mean . Let denote a random variable such that in distribution for all . The distribution function of , denoted by , is given in (18). In addition, the transmission times are set to be degenerated into a positive number , i.e., almost surely for all .
In the case that sensor nodes take positive back-off times, the probability
in (16) is calculated by
for
. Thus, for sensor node
, the pairwise non-collision probability
in (22) is yielded by
for all
and the non-collision probability
in (23) is also yielded by
for all
. Therefore, the nodal throughput that sensor node
can attain is obtained by
for all
and the total throughput is also expressed by
Secondly, consider the case in which sensor nodes take no back-off times. Suppose that the harvest times are governed by a same exponential distribution with mean . In this case, the back-off times are set to be degenerated into , i.e., almost surely for all . Also, the transmission times are set to be degenerated into a positive number .
In the case that sensor nodes take no back-off time, the probability
given in (16) is calculated by
for
. Thus, for sensor node
, the pairwise non-collision probability
in (22) is yielded by
for all
and the non-collision probability
in (23) is also yielded by
for all
. Therefore, the nodal throughput that sensor node
can attain is obtained by
for all
and the total throughput is also obtained by
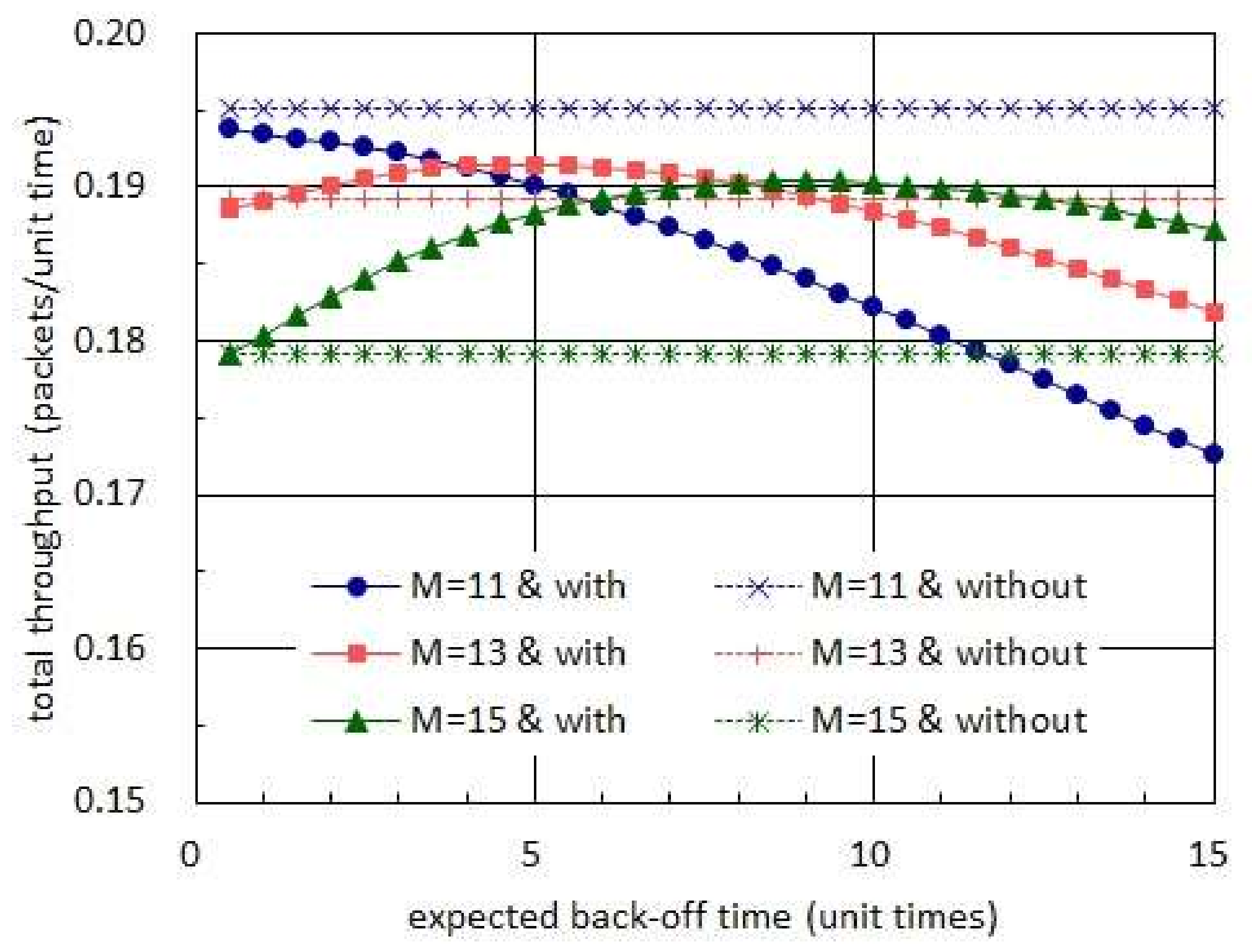
Figure 9 compares the total throughputs which are, respectively, achieved with and without taking back-off times. In this figure, the harvest times are assumed to have the exponential distribution with mean of 20 unit times while the transmission times are set to be almost surely equal to 1 unit time [
16]. In addition, the back-off times are set to be governed by an exponential distribution in case sensor nodes take positive back-off times. In this figure, we observe that taking no back-off time is always able to achieve higher total throughput than taking exponentially distributed back-off times when the number of sensor nodes is 11. However, in the network consisting of 13 or 15 sensor nodes, we notice that taking proper back-off times can effectively improve the total throughput.
4.3. Shaping Distribution for Back-Off Time
Apparently, the shape of the distribution for the back-off time affects the throughput that the basic MAC scheme is able to attain. Please note that the variance of a distribution is a key parameter which determines the shape of the distribution. In this section, we assume a situation in which the sum of harvest and back-off times is governed by an Erlang distribution. Then, we examine the dominant tendency that the total throughput shows as the variance of back-off time changes.
First, suppose that the harvest times
are identically distributed with mean
. Let
denote a random variable such that
in distribution for all
. Also, let
denote the distribution function of
and
be the Laplace-Stieltjes transform of
, i.e.,
for complex number
. Secondly, suppose that the back-off times
are governed by a same distribution with mean
. Let
denote a random variable such that
in distribution for all
and
be the distribution function of
. Then, the random variable
is set to have the Erlang distribution with shape parameter
and rate parameter
, i.e.,
for
. The Laplace-Stieltjes transform of
is calculated by
Please note that
is equal to the inverse Laplace-Stieltjes transform of
. Thirdly, suppose that the transmission times
are degenerated into a positive number
, i.e.,
almost surely for all
.
In case the sum of harvest and back-off times has an Erlang distribution, the probability
in (16) is obtained by
for
. Then,
as
. From (63), the pairwise non-collision probability
is yielded by
for all
and the non-collision probability
is also yielded by
for all
. From (65), the nodal throughput
is expressed by
for all
and the total throughput
is also obtained by
Figure 10 shows the total throughput with respect to the shape parameter of Erlang distribution. In this figure, a specific distribution is not assumed for the harvest times. Given distribution for the harvest times, however, the back-off times are set to have a certain distribution so that the sum of harvest and back-off times are governed by an Erlang distribution with mean of 30 unit times. In addition, the transmission times are set to be 1 unit time almost surely. In
Figure 10, we observe that the total throughput is reduced as the shape parameter is increased. First, note that the mean of the sum of harvest and back-off times is set to be unchanged with respect to the shape parameter. Thus, the mean of the back-off time is fixed in this figure. Secondly, note that the mean and variance of the Erlang distribution with shape parameter
and rate parameter
are equal to
and
, respectively. Thus, as the shape parameter increases, the variance of the sum of harvest and back-off times decreases and hence the variance of the back-off time decreases. (
Figure 10 illustrates the standard deviation which decreases as the shape parameter increases.) The two arguments above corroborate the conclusion that shaping the back-off time so that its variance is increased while its mean is not changed contributes to the throughput enhancement. Please note that all of the expected harvest time, expected back-off time and expected transmission time are fixed regardless of the shape parameter in
Figure 10. Thus, the phenomenon stated in the conclusion above takes place since the probability of packet collision decreases as the shape parameter increases while the fraction of time that no sensor node uses for transmitting a packet is unchanged.