Quantum Multi-User Broadcast Protocol for the “Platform as a Service” Model
Abstract
1. Introduction
2. Overview
2.1. Multicast Addresses
2.2. Phase-Covariant Quantum Cloning
3. Multi-User Broadcast Protocol Based on
3.1. Neighbor Quantum Node Discovery Process
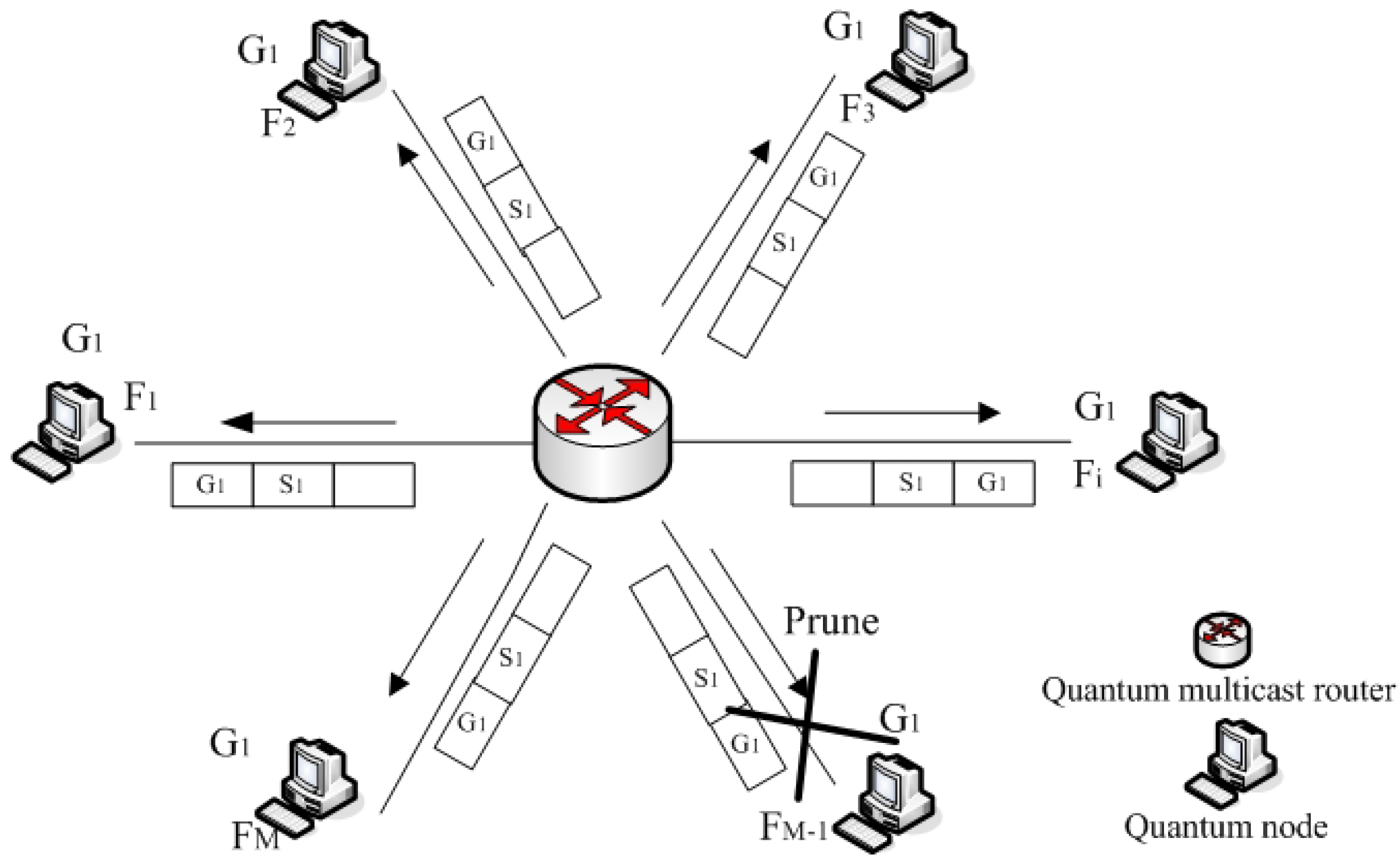
3.2. Neighbor Quantum Node Pruning Process
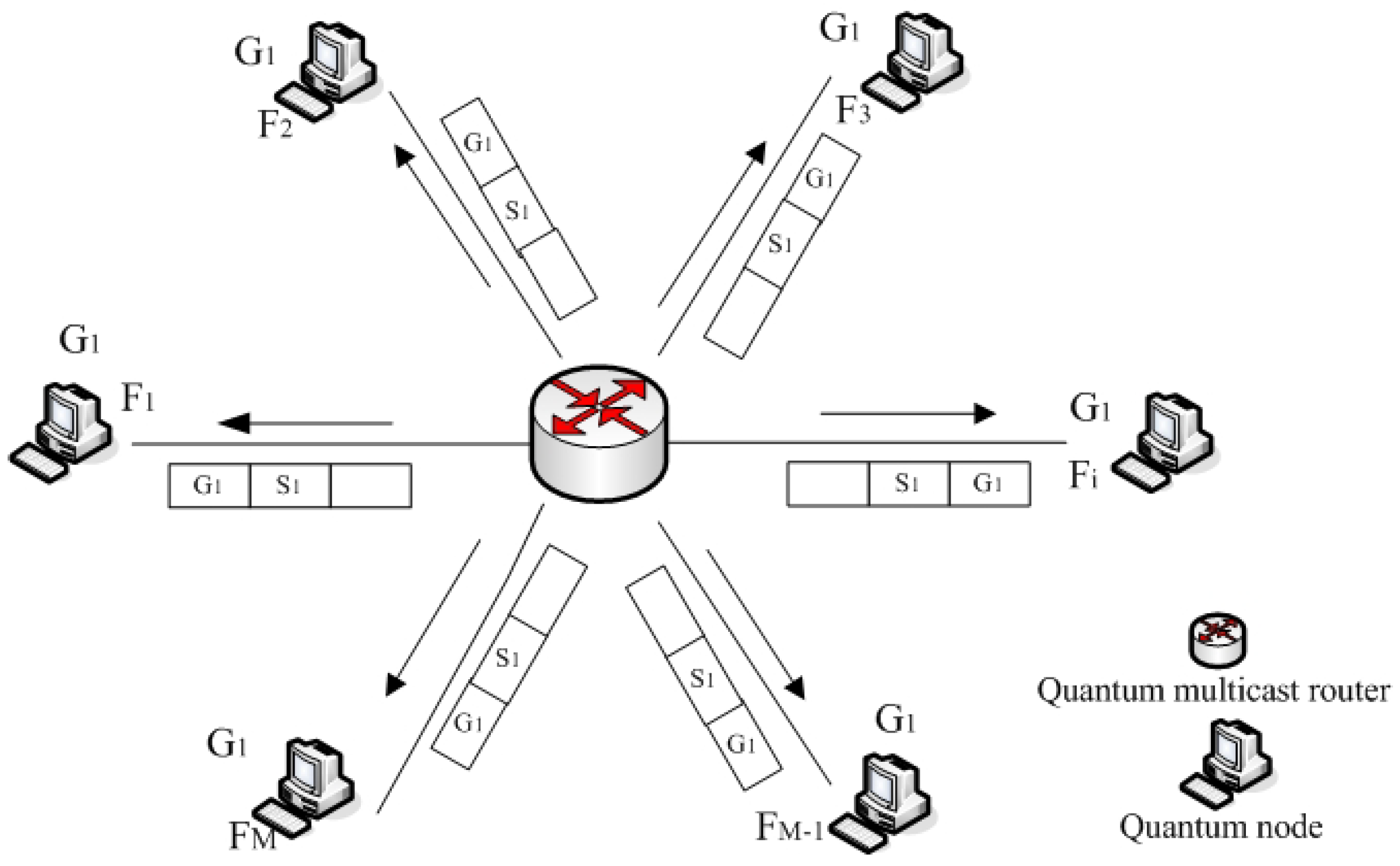
3.3. Group Routing Tables Building Process
3.4. Multicast Date Packet Communication on Quantum Cloning Process
3.5. Selective Repeating Process
4. Analysis
4.1. Analysis of Quantum Bit Error Rate and Secure Key Rate
4.2. Analysis of Optimal Fidelity
4.3. Analysis of Throughput Efficiency
4.4. Analysis of Security under Typical Attack
4.4.1. Attack via Direct Measurement
4.4.2. Attack via Ancilla Particle
5. Conclusions
Author Contributions
Funding
Conflicts of Interest
References
- Singh, H.; Sachdev, A. The Quantum way of Cloud Computing. In Proceedings of the 2014 International Conference on Reliability Optimization and Information Technology (ICROIT), Faridabad, India, 6–8 February 2014; pp. 397–400. [Google Scholar]
- Keller, E.; Rexford, J. The ”Platform as a Service” Model for Networking. In Proceedings of the 2010 Internet Network Management Workshop/Workshop on Research on Enterprise Networking (INM/WREN), San Jose, CA, USA, 27 April 2010; pp. 95–108. [Google Scholar]
- Bennett, C.H.; Brassard, G. WITHDRAWN: Quantum cryptography: Public key distribution and coin tossing. In Proceedings of the IEEE International Conference on Computers, Bangalore, India, 9–12 December 1984; p. 175. [Google Scholar]
- Loukopoulos, K.; Browne, D.E. Secure multiparty computation with a dishonest majority via quantum means. Phys. Rev. A 2010, 81, 062336. [Google Scholar] [CrossRef]
- Ma, H.; Chen, B.; Guo, Z.; Li, H. Development of quantum network based on multiparty quantum secret sharing. Can. J. Phys. 2008, 86, 1097–1101. [Google Scholar] [CrossRef]
- Zhou, N.R.; Cheng, H.L.; Gong, L.H.; Li, C.S. Three-Party Quantum Network Communication Protocols Based on Quantum Teleportation. Int. J. Theor. Phys. 2014, 53, 1387–1403. [Google Scholar] [CrossRef]
- Matsumoto, R. Multiparty quantum-key-distribution protocol without use of entanglement. Phys. Rev. A 2007, 76, 062316. [Google Scholar] [CrossRef]
- Yan, F.L.; Gao, T. Quantum secret sharing between multiparty and multiparty without entanglement. Phys. Rev. A 2005, 72, 012304. [Google Scholar] [CrossRef]
- Woodhead, E. Quantum cloning bound and application to quantum key distribution. Phys. Rev. A 2013, 88, 012331. [Google Scholar] [CrossRef]
- Iblisdir, S.; Acín, A.; Cerf, N.J.; Filip, R.; Fiurášek, J.; Gisin, N. Multipartite asymmetric quantum cloning. Phys. Rev. A 2005, 72, 042328. [Google Scholar] [CrossRef]
- Bužek, V.; Braunstein, S.L.; Hillery, M.; Bruß, D. Quantum copying: A network. Phys. Rev. A 1997, 56, 3446–3452. [Google Scholar] [CrossRef]
- Andersen, U.L.; Josse, V.; Leuchs, G. Unconditional Quantum Cloning of Coherent States with Linear Optics. Phys. Rev. Lett. 2005, 94, 240503. [Google Scholar] [CrossRef]
- Scarani, V.; Iblisdir, S.; Gisin, N.; Acín, A. Quantum cloning. Rev. Mod. Phys. 2005, 77, 1225–1256. [Google Scholar] [CrossRef]
- Fang, B.L.; Song, Q.M.; Ye, L. Realization of a universal and phase-covariant quantum cloning machine in separate cavities. Phys. Rev. A 2011, 83, 042309. [Google Scholar] [CrossRef]
- Wootters, W.K.; Zurek, W.H. A single quantum cannot be cloned. Nature 1982, 299, 802–803. [Google Scholar] [CrossRef]
- Fan, H.; Matsumoto, K.; Wang, X.B.; Wadati, M. Quantum cloning machines for equatorial qubits. Phys. Rev. A 2001, 65, 012304. [Google Scholar] [CrossRef]
- Bruß, D.; Cinchetti, M.; Mauro D’Ariano, G.; Macchiavello, C. Phase-covariant quantum cloning. Phys. Rev. A 2000, 62, 012302. [Google Scholar] [CrossRef]
- Fan, H.; Wang, Y.N.; Jing, L.; Yue, J.D.; Shi, H.D.; Zhang, Y.L.; Mu, L.Z. Quantum cloning machines and the applications. Phys. Rep. 2014, 544, 241–322. [Google Scholar] [CrossRef]
- Fan, H.; Imai, H.; Matsumoto, K.; Wang, X.B. Phase-covariant quantum cloning of qudits. Phys. Rev. A 2003, 67, 022317. [Google Scholar] [CrossRef]
- Gisin, N.; Massar, S. Optimal Quantum Cloning Machines. Phys. Rev. Lett. 1997, 79, 2153–2156. [Google Scholar] [CrossRef]
- Eleuch, H. Quantum Trajectories and Autocorrelation Function in Semiconductor Microcavity. Appl. Math. Inf. Sci. 2009, 3, 185–196. [Google Scholar]
- Mohamed, A.B.; Eleuch, H. Non-classical effects in cavity QED containing a nonlinear optical medium and a quantum well: Entanglement and non-Gaussanity. Eur. Phys. J. D 2015, 69, 191. [Google Scholar] [CrossRef]
- Berrada, K.; Abdel-Khalek, S.; Eleuch, H.; Hassouni, Y. Beam splitting and entanglement generation: Excited coherent states. Quantum Inf. Process. 2013, 12, 69–82. [Google Scholar] [CrossRef]
- Lütkenhaus, N.; Calsamiglia, J.; Suominen, K.A. Bell measurements for teleportation. Phys. Rev. A 1999, 59, 3295–3300. [Google Scholar] [CrossRef]
- Zeng, G.; Keitel, C.H. Arbitrated quantum-signature scheme. Phys. Rev. A 2002, 65, 042312. [Google Scholar] [CrossRef]
- Gisin, N.; Ribordy, G.; Tittel, W.; Zbinden, H. Quantum cryptography. Rev. Mod. Phys. 2002, 74, 145–195. [Google Scholar] [CrossRef]
- Cao, Z.W.; Zhao, G.; Zhang, S.H.; Feng, X.Y.; Peng, J.Y. Quantum secure direct communication protocol based on the mixture of Bell state particles and single photons. Acta Phys. Sin. 2016, 65, 230301. [Google Scholar]
- Nielsen, M.A.; Chuang, I.L. Quantum Computation and Quantum Information, 1st ed.; Cambridge University Press: Cambridge, UK, 2000. [Google Scholar]
- Eleuch, H.; Rotter, I. Resonances in open quantum systems. Phys. Rev. A 2017, 95, 022117. [Google Scholar] [CrossRef]
- Eleuch, H.; Rotter, I. Open quantum systems and Dicke superradiance. Eur. Phys. J. D 2014, 68, 74. [Google Scholar] [CrossRef]

© 2019 by the authors. Licensee MDPI, Basel, Switzerland. This article is an open access article distributed under the terms and conditions of the Creative Commons Attribution (CC BY) license (http://creativecommons.org/licenses/by/4.0/).
Share and Cite
Shi, P.; Li, N.; Wang, S.; Liu, Z.; Ren, M.; Ma, H. Quantum Multi-User Broadcast Protocol for the “Platform as a Service” Model. Sensors 2019, 19, 5257. https://doi.org/10.3390/s19235257
Shi P, Li N, Wang S, Liu Z, Ren M, Ma H. Quantum Multi-User Broadcast Protocol for the “Platform as a Service” Model. Sensors. 2019; 19(23):5257. https://doi.org/10.3390/s19235257
Chicago/Turabian StyleShi, Peng, Nachuan Li, Shumei Wang, Zhi Liu, Mengran Ren, and Hongyang Ma. 2019. "Quantum Multi-User Broadcast Protocol for the “Platform as a Service” Model" Sensors 19, no. 23: 5257. https://doi.org/10.3390/s19235257
APA StyleShi, P., Li, N., Wang, S., Liu, Z., Ren, M., & Ma, H. (2019). Quantum Multi-User Broadcast Protocol for the “Platform as a Service” Model. Sensors, 19(23), 5257. https://doi.org/10.3390/s19235257



