A Malicious Behavior Awareness and Defense Countermeasure Based on LoRaWAN Protocol
Abstract
:1. Introduction
- We propose a New One-Time-Password (OTP) method that can be used in LoRaWAN protocol. This method can effectively encrypt the plain text (join request data). Through theoretical analysis, we prove that this encryption algorithm is safe and reliable.
- Original join-request message has been redefined as New-join-request (Njr). Based on the characteristics of the original join request message, a new dynamic coding technique is proposed to generate Njr. If Njr is intercepted, it is almost impossible for the attacker to perform correct decoding.
- We used Ban Logic and Scyther for formal verification. The results of formal verification prove that the theory of the protocol is safe. We also validated our scheme by using the Omnet++ following the way in [10]. The simulation results show the feasibility and robustness of the SPT.
- Our countermeasure has been implemented on the SM1276 node. We design a testbed to verify the effectiveness and security of the method at the same time.
2. Background
2.1. The Security Mechanism of the OTAA
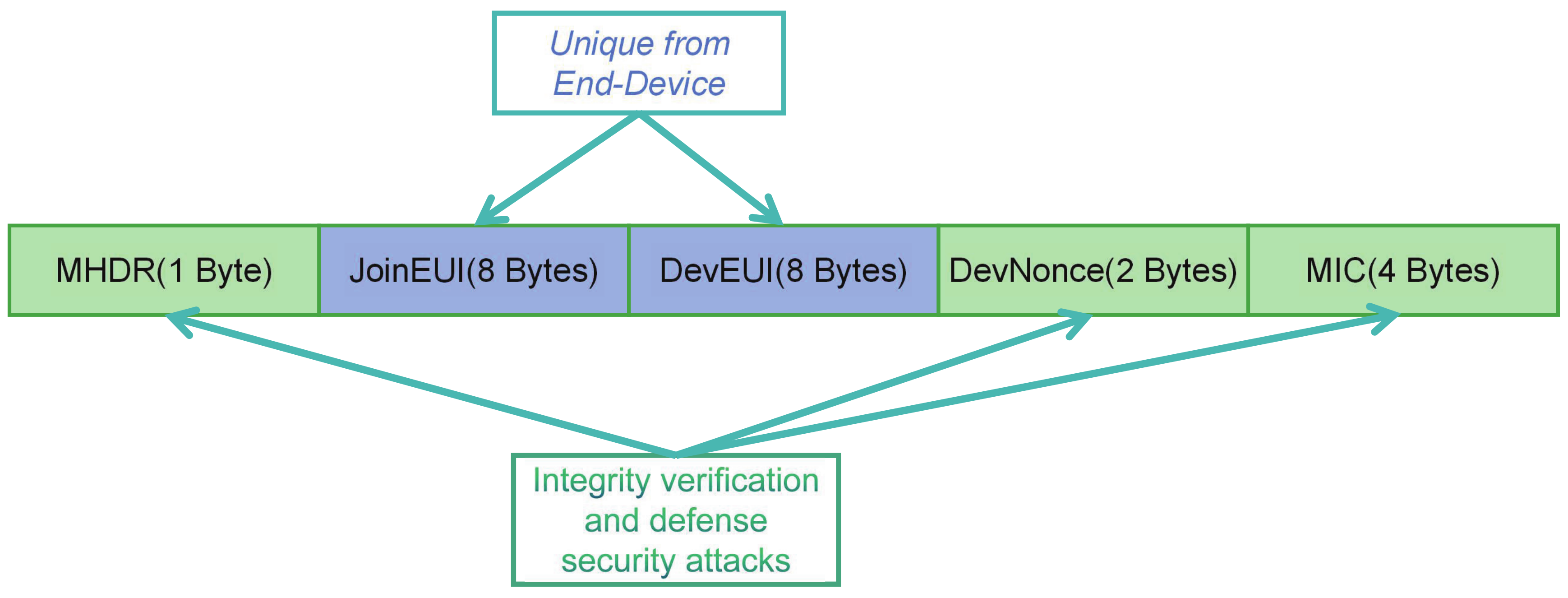
- In join-request, MHDR represents the data type;
- JoinEUI and DevEUI contain the basic information of a node, which is unique;
- DevNonce is used to record the number for joining time.Changing the DevNonce and MIC is the countermeasure of defending against replay attacks.
- The MIC is calculated by AES128 (NwkKey, MHDR|JoinEUI|DEVEUI|DevNonce). We can see the importance of the NwkKey (the root key) is irreplaceable from this Equation. Without the root key, any process that requires encryption cannot be completed. Therefore, if the root key cannot be properly kept, all security measures may fail.
2.2. One Time Password
2.3. ADR Algorithm
2.4. BAN Logic
- : Principal P believes a statement X, or P is entitled to believe X.
- : Formula X is fresh.
- : P has jurisdiction over a statement X.
- : P sees X, the principal P received the message containing X, and P is able to read or repeat X.
- : P once said X, the principal P sent a message containing X at some time.
- : The formula X or Y is one part of formula (X,Y).
- : The formula X is encrypted using the key K.
2.5. Abbreviation
3. System Model
3.1. The Original System Model of OTAA
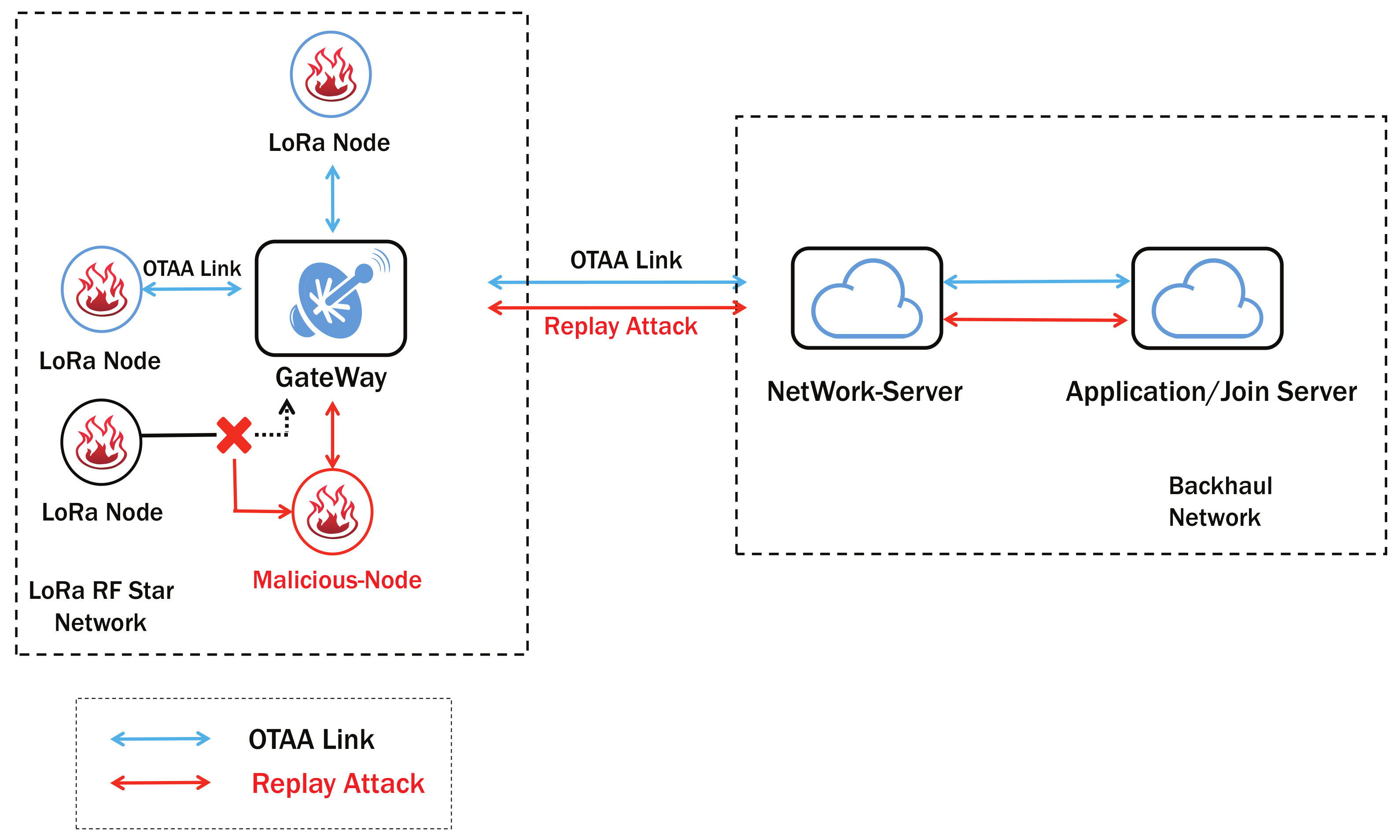
3.2. Attack Model in OTAA
3.3. Security Requirements
- A new authentication mechanism to ensure that the server can identify whether the data is from a malicious node.
- This mechanism is not only effective in this case, but can directly replace the original defense mechanism to protect LoRaWAN’s network security.
- The power consumption of each node using the new protection mechanism cannot be increased.
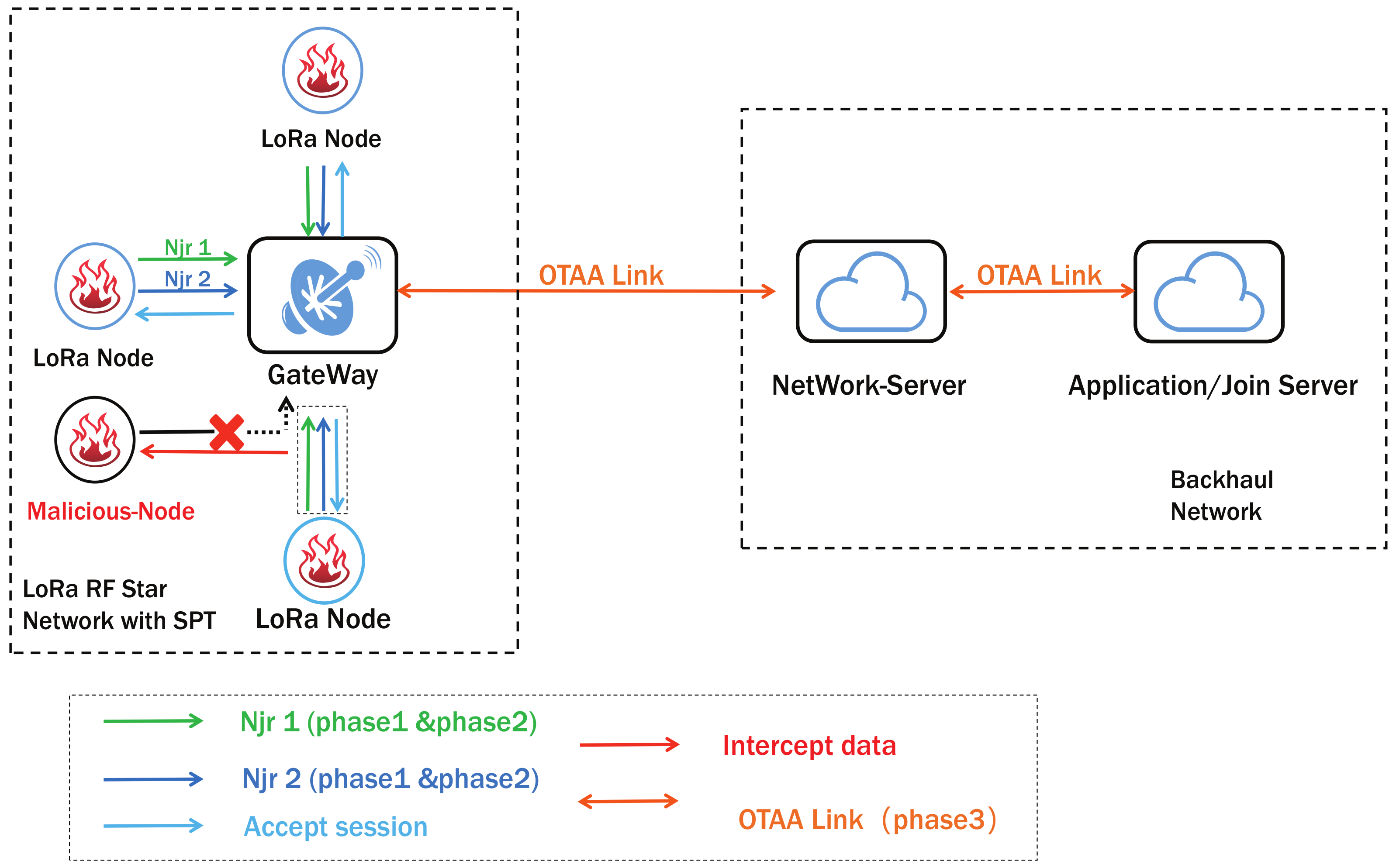
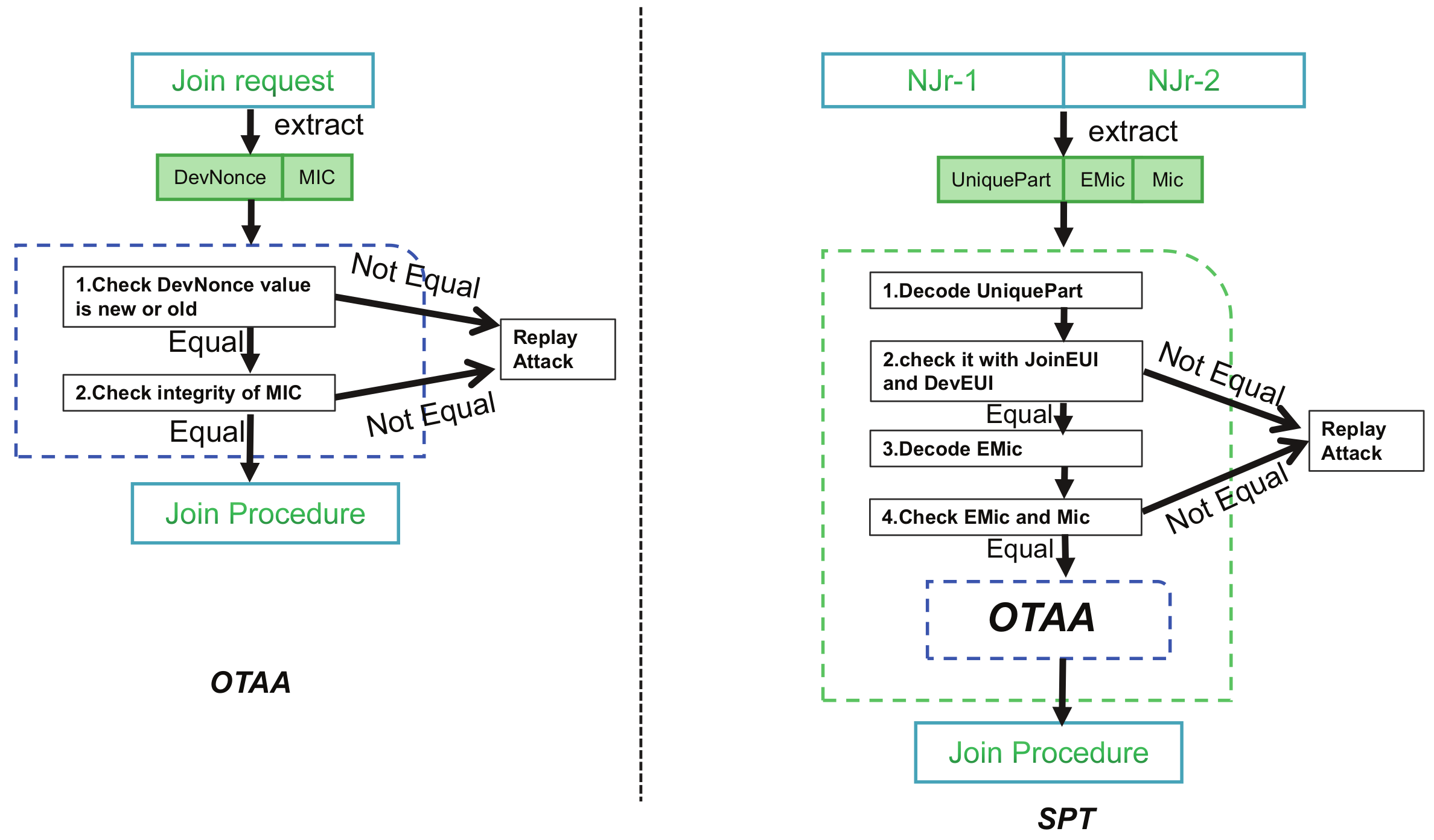
3.4. The Proposed System
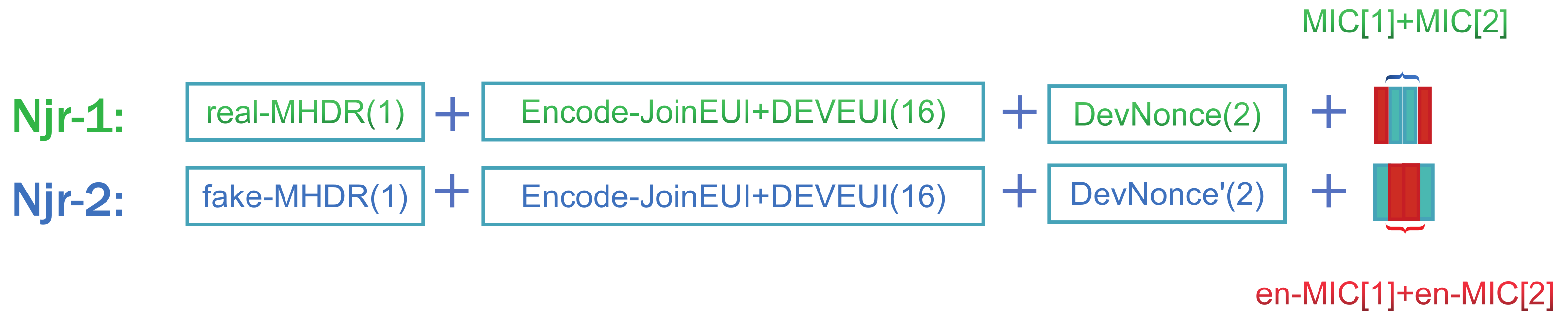
- Combine the first and fourth positions of the MIC and the second and third positions of the En-Mic together as MIC1. MIC2 is the remaining four bytes of data to combine.
- Generate Fake-MHDR by storing the pos value.
- According to the order in Figure 4 to assemble Njr1 and Njr2.
- Step 1.
- Check if the DevNnonce2 is equal to DevNonce1 plus one;
- Step 2.
- Restore JoinEUI and DevEUI by the value from fake-MHDR;
- Step 3.
- Verify the relationship between Encode-MIC and MIC. The join accept message can be generated by a network server only through all the above steps. After this part, all communication processes will be consistent with the original LoRaWAN. Otherwise NS will refuse to reply.
3.5. The Advantage for Encryption Strategy
- The attacker did not modify the unique part.
- The attacker cannot directly derive the specific meaning of En-Mic because it is a randomly inserted noise data. So the only thing for attacker can do is to modify the MIC part directly.
- The attacker did not use the correct number for the encoding operation.
3.6. Method for Reducing Power Consumption
3.7. How to Implement SPT
4. Security Analysis for SPT
- Logic Correctness proof by BAN Logic;
- Formal analysis the SPT by using Scyther.
4.1. Logic Correctness Proof Based on BAN Logic
4.2. Formal Analysis of SPT and LoRaWAN
5. Performance Evaluation
5.1. Delivery Ratio Evaluation
5.1.1. Parameter Setup
5.1.2. Delivery Ratio Result in Omnet
5.1.3. Delivery Ratio Result in Testbed
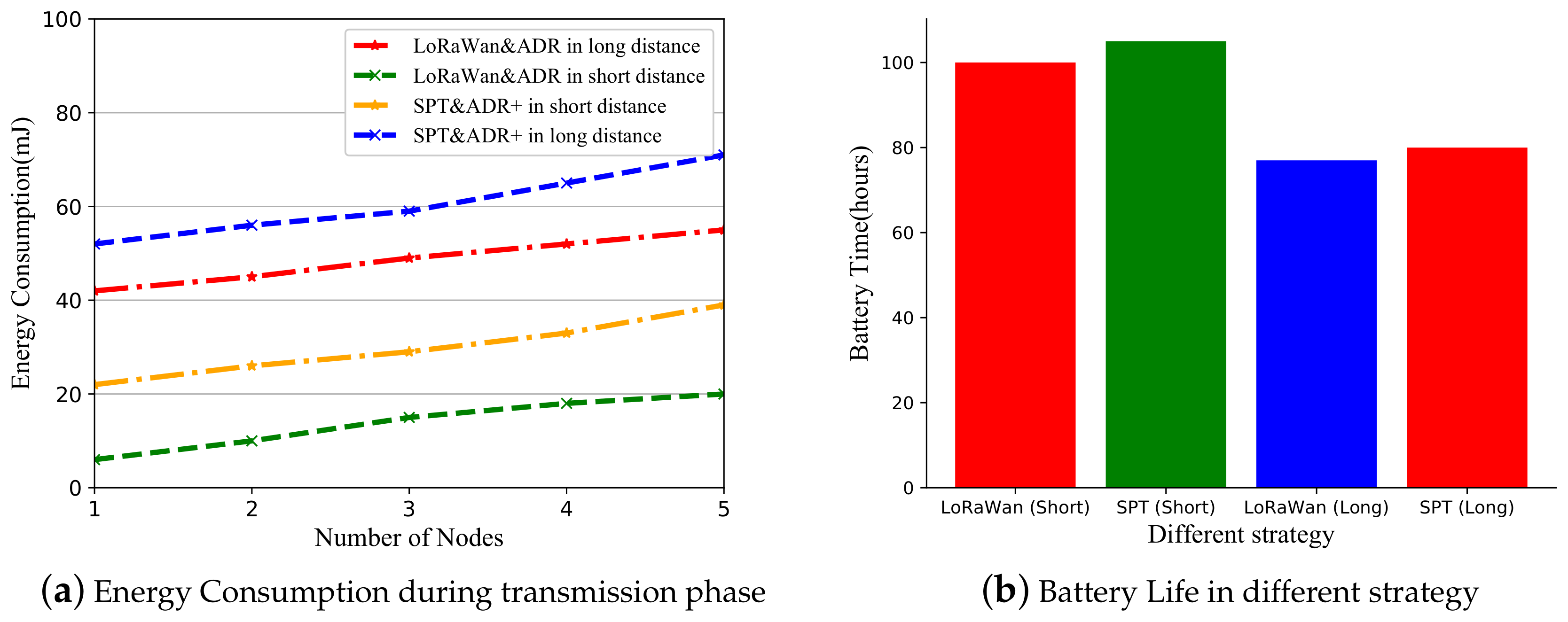
5.2. Power Consumption Experiment
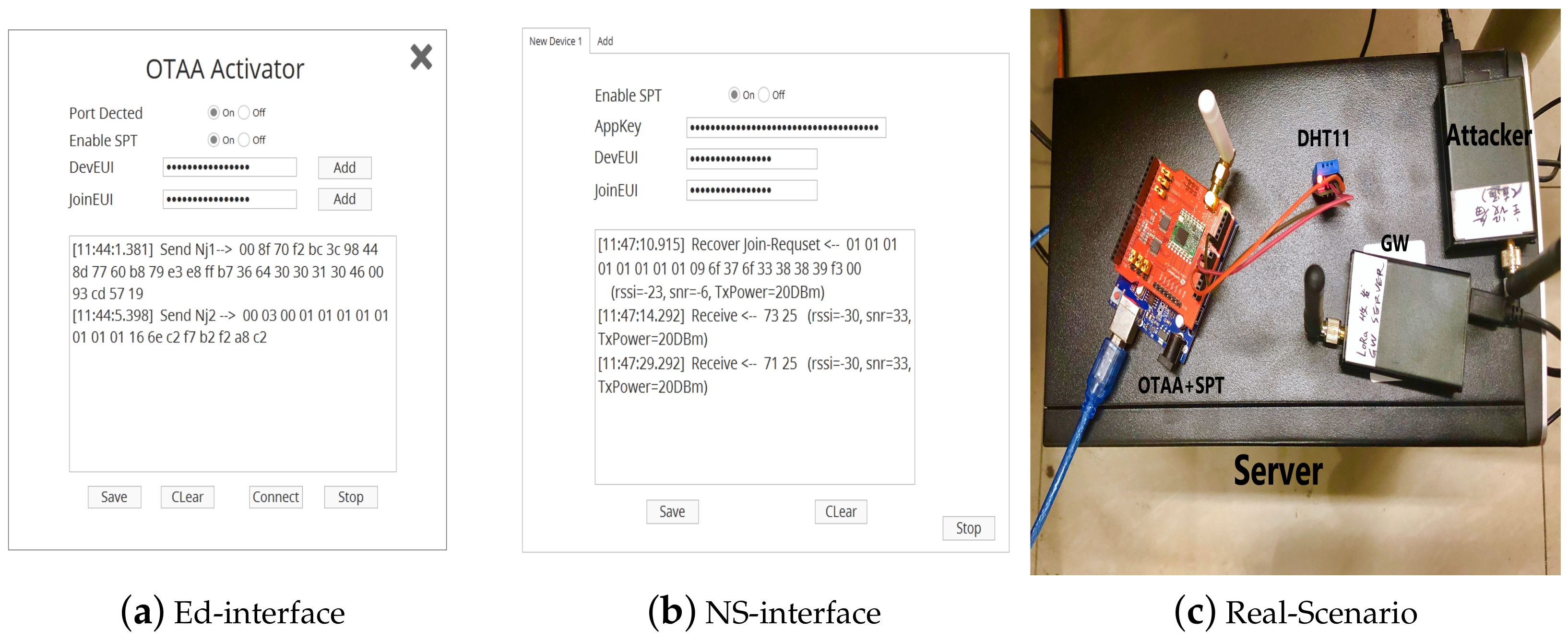
5.2.1. Testbed System Setup
5.2.2. Power Consumption Results in Testbed
5.3. Replay Attack Experiment
5.3.1. Preset Conditions
5.3.2. Attack Results in Testbed
6. Conclusions
7. Related Work
Author Contributions
Funding
Conflicts of Interest
References
- LoRa Alliance Technical Committee. LoRaWAN™ Specification Version 1.0.2; LoRa Alliance Technical Committee: Barcelona, Spain, 2016. [Google Scholar]
- Basford, P.J.; Johnston, S.J.; Apetroaie-Cristea, M.; Bulot, F.M.J.; Cox, S.J. LoRaWAN for City Scale IoT Deployments. In Proceedings of the 2019 Global IoT Summit (GIoTS), Aarhus, Denmark, 17–21 June 2019; pp. 1–6. [Google Scholar] [CrossRef]
- Geneiatakis, D.; Kounelis, I.; Neisse, R.; Nai-Fovino, I.; Steri, G.; Baldini, G. Security and Privacy Issues for an IoT Based Smart Home. In Proceedings of the 2017 40th International Convention on Information and Communication Technology, Electronics and Microelectronics (MIPRO), Opatija, Croatia, 22–26 May 2017; pp. 1297–1298. [Google Scholar] [CrossRef]
- Tomasin, S.; Zulian, S.; Vangelista, L. Security Analysis of LoRaWAN Join Procedure for Internet of Things Networks. In Proceedings of the IEEE Wireless Communications and Networking Conference Workshops, San Francisco, CA, USA, 19–22 March 2017; pp. 1–6. [Google Scholar]
- Tsai, K.L.; Huang, Y.L.; Leu, F.Y.; You, I.; Huang, Y.L.; Tsai, C.H. An AES-128 Based Secure Low Power Communication for LoRaWAN IoT Environments. IEEE Access 2018, 6, 45325–45334. [Google Scholar] [CrossRef]
- Miller, R. LoRa Security—Building a Secure LoRa Solution; MWR Labs: London, UK, 2016. [Google Scholar]
- Naoui, S.; Elhdhili, M.E.; Saidane, L.A. Enhancing the security of the IoT LoraWAN architecture. In Proceedings of the 2016 International Conference on Performance Evaluation and Modeling in Wired and Wireless Networks (PEMWN), Paris, France, 22–25 November 2016. [Google Scholar]
- Kim, J.; Song, J. A dual key-based activation scheme for secure LoRaWAN. Wirel. Commun. Mobile Comput. 2017, 2017, 6590713. [Google Scholar] [CrossRef]
- OWASP Serverless Top 10 Project. Available online: https://www.owasp.org/index.php (accessed on 10 October 2017).
- Slabicki, M.; Premsankar, G.; Di Francesco, M. Adaptive Configuration of Lora Networks for Dense IoT Deployments. In Proceedings of the 2018 IEEE/IFIP Network Operations and Management Symposium, NOMS, Taipei, Taiwan, 23–27 April 2018. [Google Scholar]
- Park, C.S. One-time password based on hash chain without shared secret and re-registration. Comput. Secur. 2018, 75, 138–146. [Google Scholar] [CrossRef]
- LoRa Alliance Technical Committee. LoRaWAN™ Specification Version 1.1; LoRa Alliance Technical Committee: Barcelona, Spain, 2017. [Google Scholar]
- Benkahla, N.; Tounsi, H.; Ye-Qiong, S.O.N.G.; Frikha, M. Enhanced ADR for LoRaWAN networks with mobility. In Proceedings of the 2019 15th International Wireless Communications Mobile Computing Conference (IWCMC), Tangier, Morocco, 24–28 June 2019; pp. 1–6. [Google Scholar] [CrossRef]
- The Scyther Tool Overview. Available online: https://people.cispa.io/cas.cremers/scyther/index.html (accessed on 25 August 2019).
- Scyther-Manual. Available online: https://people.cispa.io/cas.cremers/downloads/scyther/scyther-w32-v1.1.3.zip (accessed on 28 August 2019).
- Eldefrawy, M.; Butun, I.; Pereira, N.; Gidlund, M. Formal security analysis of LoRaWAN. Comput. Netw. 2019, 148, 328–339. [Google Scholar] [CrossRef]
- Semtech SX1276 Tools. Available online: https://www.semtech.com/products/wireless-rf/lora-transceivers/SX1276 (accessed on 28 August 2019).
- How to Set Up the DHT11 Humidity Sensor on an Arduino. Available online: http://www.circuitbasics.com/how-to-set-up-the-dht11-humidity-sensor-on-an-arduino (accessed on 8 October 2018).
- Qiu, T.; Liu, J.; Si, W.; Wu, D.O. Robustness optimization scheme with multi-population co-evolution for scale-free wireless sensor networks. IEEE/ACM Trans. Netw. 2019, 27, 1028–1042. [Google Scholar] [CrossRef]
- Jacobsson, A.; Boldt, M.; Carlsson, B. A risk analysis of a smart home automation system. Future Gener. Comput. Syst. 2016, 56, 719–733. [Google Scholar] [CrossRef]
- Jacobsson, A.; Davidsson, P. Towards a Model of Privacy and Security for Smart Homes. In In Proceedings of the 2015 IEEE 2nd World Forum on Internet of Things (WF-IoT), Milan, Italy, 14–16 December 2015; pp. 727–732. [Google Scholar]
- Aras, E.; Ramachandran, G.S.; Lawrence, P.; Hughes, D. Exploring the Security Vulnerabilities of LoRa. In Proceedings of the IEEE International Conference on Cybernet, Exeter, UK, 21–23 June 2017. [Google Scholar]
- Kim, J.; Song, J. A Simple and Efficient Replay Attack Prevention Scheme for LoRaWAN. In Proceedings of the 7th International Conference on Communication and Network Security, Tokyo, Japan, 24–26 November 2017; pp. 32–36. [Google Scholar]
- Na, S.; Hwang, D.; Shin, W.; Kim, K.H. Scenario and countermeasure for replay attack using join request messages in LoRaWAN. In Proceedings of the International Conference on Information Networking, Da Nang, Vietnam, 11–13 January 2017; pp. 718–720. [Google Scholar]
- Tashsin, C.; Ethiopia, N. Security of Join Procedure and its Delegation in LoRaWAN v1.1. Procedia Comput. Sci. 2018, 134, 204–211. [Google Scholar] [CrossRef]
- Yang, X.; Karampatzakis, E.; Doerr, C.; Kuipers, F. Security Vulnerabilities in LoRaWAN. In Proceedings of the IEEE/ACM Third International Conference on Internet-of-Things Design and Implementation(IoTDI), Orlando, FL, USA, 17–20 April 2018; pp. 129–140. [Google Scholar]
- Qiu, T.; Wang, X.; Chen, C.; Atiquzzaman, M.; Liu, L. TMED: A spider web-like transmission mechanism for emergency data in vehicular ad hoc networks. IEEE Trans. Veh. Technol. 2018, 67, 8682–8694. [Google Scholar] [CrossRef]
- Bouguera, T.; Diouris, J.F.; Chaillout, J.J.; Jaouadi, R. Energy Consumption Model for Sensor Nodes Based on LoRa and LoRaWAN. Sensors 2018, 18, 2104. [Google Scholar] [CrossRef] [PubMed]
- Sanchez-Iborra, R.; Sánchez-Gómez, J.; Pérez, S.; Fernández, P.; Santa, J.; Hernández-Ramos, J.; Skarmeta, A. Enhancing LoRaWAN Security through a Lightweight and Authenticated Key Management Approach. Sensors 2018, 18, 1833. [Google Scholar] [CrossRef] [PubMed] [Green Version]




| Notations | Description |
|---|---|
| ED | End Device same as node |
| GW | Gate Way between Node and Network Server |
| NS | NetWork Server |
| jr | Join request |
| Njr | New Join request |
| en- | encode some message |
| snr | signal-to-noise ratio |
| ae | aes128-encryption method |
| Protocol | LoRaWAN v1.1 | LoRaWAN+SPT | ||
|---|---|---|---|---|
| Claim | Status | Attack Patterns | Status | Attack Patterns |
| Role:Node | ||||
| Alive | Ok | No attack | Ok | No attack |
| Weakagree | Ok | No attack | Ok | No attack |
| Niagree | Ok | No attack | Ok | No attack |
| Nisynch | Fail | At least 1 attack | Ok | No attack |
| SKRAPPSKey | Ok | No attack | Ok | No attack |
| SKRNwkSKey | Ok | No attack | Ok | No attack |
| SKRSnwkSIntKey | Ok | No attack | Ok | No attack |
| SKRNwkSencKey | Ok | No attack | Ok | No attack |
| SKRJSEncKey | Ok | No attack | Ok | No attack |
| SKRJSIntKey | Ok | No attack | Ok | No attack |
| Role:Server | ||||
| Alive | Ok | No attack | Ok | No attack |
| Weakagree | Ok | No attack | Ok | No attack |
| SKRAPPSKey | Ok | No attack | Ok | No attack |
| SKRNwkSKey | Ok | No attack | Ok | No attack |
| SKRSnwkSIntKey | Ok | No attack | Ok | No attack |
| SKRNwkSencKey | Ok | No attack | Ok | No attack |
| SKRJSEncKey | Ok | No attack | Ok | No attack |
| SKRJSIntKey | Ok | No attack | Ok | No attack |
| Parameter | Value |
|---|---|
| Carrier Frequency | 433 MHz |
| Bandwidth | 125 kHz |
| Code Rate | 3/4 |
| Spreading Factor | 7 to 12 |
| Transmission Power | 2 dBm to 14 dBm |
| Scenario | Ideal | Moderate Variability | Typical Variability |
|---|---|---|---|
| Urbany | 0 | 1.78 | 3.55 |
| Sub-urban | 0 | 3.56 | 7.2 |
| Node | OTAA-u | OTAA-su | SPT-u | SPT-su |
|---|---|---|---|---|
| 100 | 99 | 85 | 99% | 83% |
| 200 | 95 | 82 | 97% | 82% |
| 300 | 92 | 87 | 96% | 87% |
| 400 | 93 | 83 | 95% | 80% |
| 500 | 98 | 84 | 91% | 85% |
| 600 | 92 | 82 | 90% | 83% |
| 700 | 90 | 81 | 92% | 82% |
| Nodes | Moderate Variability | Typical Variability | ||||||
|---|---|---|---|---|---|---|---|---|
| OTAA -Urban | OTAA -Suburban | SPT -Urban | SPT -Suburban | OTAA -Urban | OTAA -Suburban | SPT -Urban | SPT -Suburban | |
| 100 | 65 | 22 | 64% | 23% | 23 | 16 | 22% | 17% |
| 200 | 66 | 23 | 63% | 22% | 22 | 17 | 21% | 16% |
| 300 | 63 | 23 | 64% | 24% | 24 | 17 | 20% | 15% |
| 400 | 62 | 24 | 65% | 25% | 25 | 16 | 24% | 15% |
| 500 | 64 | 26 | 63% | 26% | 21 | 18 | 22% | 14% |
| 600 | 65 | 22 | 62% | 21% | 20 | 17 | 23% | 15% |
| 700 | 61 | 23 | 63% | 22% | 20 | 16 | 25% | 13% |
| Node | OTAA-Short | OTAA-Long | SPT-Short | SPT-Long |
|---|---|---|---|---|
| 1 | 98 | 82 | 97% | 83% |
| 2 | 95 | 84 | 96% | 84% |
| 3 | 92 | 85 | 95% | 85% |
| 4 | 95 | 86 | 94% | 85% |
| 5 | 96 | 86 | 93% | 86% |
| MHDR | Unique Part | DevNonce | MIC | Temperature | Distance | |
|---|---|---|---|---|---|---|
| A-1 | No | No | Yes | No | 22 C | 0.1 km/2 km |
| A-2 | Yes | No | Yes | Yes | 20 C | 0.1 km/2 km |
| A-3 | Yes | No | Yes | Yes | 20 C | 0.1 km/2 km |
© 2019 by the authors. Licensee MDPI, Basel, Switzerland. This article is an open access article distributed under the terms and conditions of the Creative Commons Attribution (CC BY) license (http://creativecommons.org/licenses/by/4.0/).
Share and Cite
Gao, S.-Y.; Li, X.-H.; Ma, M.-D. A Malicious Behavior Awareness and Defense Countermeasure Based on LoRaWAN Protocol. Sensors 2019, 19, 5122. https://doi.org/10.3390/s19235122
Gao S-Y, Li X-H, Ma M-D. A Malicious Behavior Awareness and Defense Countermeasure Based on LoRaWAN Protocol. Sensors. 2019; 19(23):5122. https://doi.org/10.3390/s19235122
Chicago/Turabian StyleGao, Shu-Yang, Xiao-Hong Li, and Mao-De Ma. 2019. "A Malicious Behavior Awareness and Defense Countermeasure Based on LoRaWAN Protocol" Sensors 19, no. 23: 5122. https://doi.org/10.3390/s19235122
APA StyleGao, S.-Y., Li, X.-H., & Ma, M.-D. (2019). A Malicious Behavior Awareness and Defense Countermeasure Based on LoRaWAN Protocol. Sensors, 19(23), 5122. https://doi.org/10.3390/s19235122





