Authentication Protocol for Cloud Databases Using Blockchain Mechanism
Abstract
1. Introduction
1.1. Motivation
1.2. Research Contribution
- The proposed mechanism is authenticating the insider as well as outsider attack on the system.
- The peer-to-peer authentication is provided to the cloud database user via Blockchain mechanism.
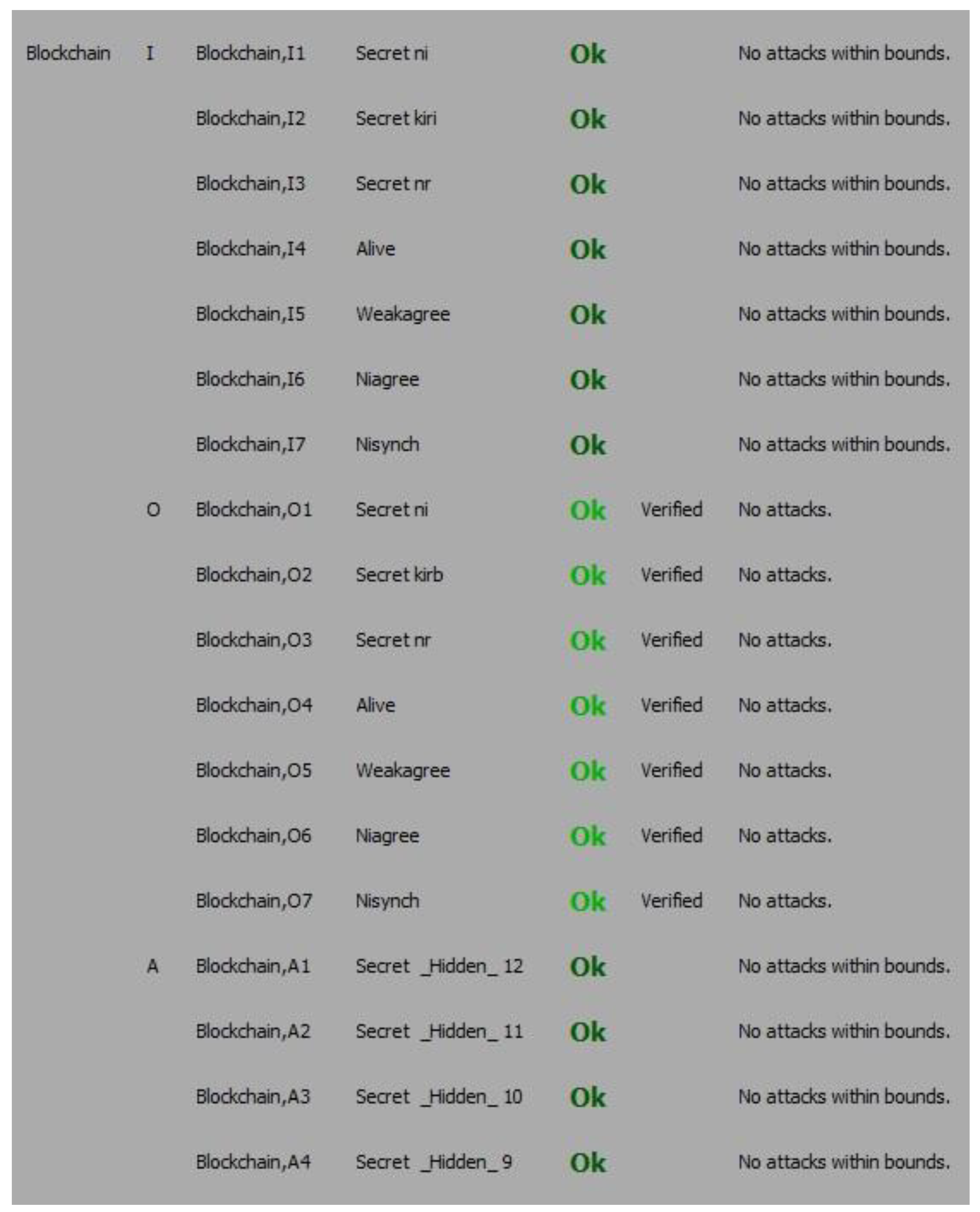
- The performance of the system is evaluated via formal system tool—Scyther and results demonstrate that the proposed mechanism is robust and secure.
2. Related Works
2.1. Insider Threat
2.2. Outsider Threat
3. Proposed Blockchain Authentication Mechanism (BAM)
3.1. Blockchain Mechanism
3.2. Overall Framework
Algorithm and Theorem
| Algorithm 1 User Authentication using Blockchain Mechanism. |
| Input: Request Q received at Blockchain Database Server/Cloudb, It checks for Q Request is from an insider (Bob) or an outsider. |
| Output: Access Granted or Rejected. |
| Step 1: If Request == Insider (Bob) Go to Step 2 else Go to step 5 |
| Step 2: If Login ID &User Signature== Valid then continue this step else Go to Step 3 |
| If current index value > Last stored index ˄Hash value ˄ Timestamp value˄ Nonce value == Valid then continue this step else Go to step 4. |
| Create New Blockchain node and Grant Authentication. |
| Step 3: If User ≠ ≠ Exist in Blockchain Database then for Retrying Go to Step 1 else continue this step |
| Add new user Node (Genesis Block) |
| Initialize Index value |
| Allocate current Time stamp value |
| Store Predefined value in Current Hash value |
| Store Data value |
| Allocate valid Nonce Value |
| Update user record in Blockchain Database |
| Step 4: Give error message and Exit |
| Step 5: If User== Outsider Go to Step 2 else go to Step 3 |
4. Experimentation Results
5. Conclusions
Author Contributions
Funding
Acknowledgments
Conflicts of Interest
References
- Wu, Z.; Xu, G.; Lu, C.; Chen, E.; Jiang, F.; Li, G. An effective approach for the protection of privacy text data in the CloudDB. World Wide Web 2018, 21, 915–938. [Google Scholar] [CrossRef]
- InfoSecurity Europe and PwC: 2015 Information Security Breaches Survey. Available online: https://www.pwc.co.uk/assets/pdf/2015-isbs-technical-report-blue-digital.pdf (accessed on 5 June 2019).
- Insider Threat 2018 Report. Available online: https://www.ca.com/content/dam/ca/us/files/ebook/insider-threat-report.pdf (accessed on 5 June 2019).
- Forrester Corporation: The Value of Corporate Secrets. 2016. Available online: https://www.nsi.org/pdf/reports/The%20Value%20of% 20Corporate%20Secrets.pdf (accessed on 12 October 2015).
- Bhatia, T.; Verma, A.K. Data security in mobile cloud computing paradigm: A survey, taxonomy and open research issues. J. Supercomput. 2017, 73, 2558–2631. [Google Scholar] [CrossRef]
- Ghafir, I.; Saleem, J.; Hammoudeh, M.; Faour, H.; Prenosil, V.; Jaf, S.; Baker, T. Security threats to critical infrastructure: The human factor. J. Supercomput. 2018, 74, 4986–5002. [Google Scholar] [CrossRef]
- Current State of Cybercrime. 2018. Available online: https://www.rsa.com/content/dam/premium/en/white-paper/2016-current-state-of-cybercrime.pdf (accessed on 8 March 2019).
- Moon, C.S.; Chung, S.; Endicott-Popovsky, B. A Cloud and In-Memory Based Two-Tier Architecture of a Database Protection System from Insider Attacks. In International Workshop on Information Security Applications; Springer: Cham, Switzerland, 2013; pp. 260–271. [Google Scholar]
- Yaseen, Q.; Panda, B. Predicting and preventing insider threat in relational database systems. In IFIP International Workshop on Information Security Theory and Practices; Springer: Berlin/Heidelberg, Germany, 2010; pp. 368–383. [Google Scholar]
- Yaseen, Q.; Panda, B. Insider threat mitigation: Preventing unauthorized knowledge acquisition. Int. J. Inf. Secur. 2012, 11, 269–280. [Google Scholar] [CrossRef]
- Yaseen, Q.; Jararweh, Y.; Panda, B.; Althebyan, Q. An insider threat aware of access control for cloud relational databases. Clust. Comput. 2017, 20, 2669–2685. [Google Scholar] [CrossRef]
- Dou, Z.; Khalil, I.; Khreishah, A.; Al-Fuqaha, A. Robust insider attacks countermeasure for Hadoop: Design and implementation. IEEE Syst. J. 2018, 12, 1874–1885. [Google Scholar] [CrossRef]
- Shaghaghi, A.; Kanhere, S.S.; Kaafar, M.A.; Bertino, E.; Jha, S. Gargoyle: A Network-based Insider Attack Resilient Framework for Organizations. arXiv 2018, arXiv:1807.02593. [Google Scholar]
- Chattopadhyay, P.; Wang, L.; Tan, Y.P. Scenario-based insider threat detection from cyber activities. IEEE Trans. Comput. Soc. Syst. 2018, 99, 1–16. [Google Scholar] [CrossRef]
- Baracaldo, N.; Palanisamy, B.; Joshi, J. G-sir: An insider attack resilient geo-social access control framework. IEEE Trans. Dependable Secur. Comput. 2017, 16, 84–98. [Google Scholar] [CrossRef]
- Tsai, J.L.; Lo, N.W. A privacy-aware authentication scheme for distributed mobile cloud computing services. IEEE Syst. J. 2015, 9, 805–815. [Google Scholar] [CrossRef]
- Yang, T.C.; Lo, N.W.; Liaw, H.T.; Wu, W.C. A secure smart card authentication and authorization framework using in multimedia cloud. Multimed. Tools Appl. 2017, 76, 11715–11737. [Google Scholar] [CrossRef]
- Kumari, S.; Karuppiah, M.; Das, A.K.; Li, X.; Wu, F.; Kumar, N. A secure authentication scheme based on elliptic curve cryptography for IoT and cloud servers. J. Supercomput. 2018, 74, 6428–6453. [Google Scholar] [CrossRef]
- Shajina, A.R.; Varalakshmi, P. A novel dual authentication protocol (DAP) for multi-owners in cloud computing. Clust. Comput. 2017, 20, 507–523. [Google Scholar] [CrossRef]
- Anakath, A.S.; Rajakumar, S.; Ambika, S. Privacy-preserving multi-factor authentication using trust management. Clust. Comput. 2017, 1–7. [Google Scholar] [CrossRef]
- Chaudhry, S.A.; Kim, I.L.; Rho, S.; Farash, M.S.; Shon, T. An improved anonymous authentication scheme for distributed mobile cloud computing services. Clust. Comput. 2017. [Google Scholar] [CrossRef]
- Kumar, S.; Singh, S.K.; Singh, A.K.; Tiwari, S.; Singh, R.S. Privacy-preserving security using biometrics in cloud computing. Multimed. Tools Appl. 2018, 77, 11017–11039. [Google Scholar] [CrossRef]
- Chatterjee, K. Biometric re-authentication: An approach towards achieving transparency in user authentication. Multimed. Tools Appl. 2019, 78, 6679–6700. [Google Scholar]
- Cresitello-Dittmar, B. Application of the Blockchain For Authentication and Verification of Identity. Independent Paper. 2016. [Google Scholar]
- Zheng, Z.; Xie, S.; Dai, H.; Chen, X.; Wang, H. An overview of Blockchain technology: Architecture, consensus, and future trends. In 2017 IEEE International Congress on Big Data (Big Data Congress); IEEE: Piscataway, NJ, USA, 2017; pp. 557–564. [Google Scholar]
- Minoli, D.; Occhiogrosso, B. Blockchain mechanisms for IoT security. Internet Things 2018, 1, 1–13. [Google Scholar] [CrossRef]
- Blockchain Demo. Available online: https://blockchaindemo.io/ (accessed on 5 June 2019).
- Niranjanamurthy, M.; Nithya, B.N.; Jagannatha, S. Analysis of Blockchain technology: Pros, cons, and SWOT. Clust. Comput. 2018, 1–15. [Google Scholar] [CrossRef]
- Zheng, B.K.; Zhu, L.H.; Shen, M.; Gao, F.; Zhang, C.; Li, Y.D.; Yang, J. Scalable and privacy-preserving data sharing based on Blockchain. J. Comput. Sci. Technol. 2018, 33, 557–567. [Google Scholar] [CrossRef]
- Tian, H.; He, J.; Ding, Y. Medical Data Management on Blockchain with Privacy. J. Med. Syst. 2019, 43, 26. [Google Scholar] [CrossRef] [PubMed]
- Ryu, J.H.; Sharma, P.K.; Jo, J.H.; Park, J.H. A Blockchain-based decentralized efficient investigation framework for IoT digital forensics. J. Supercomput. 2019, 1–16. [Google Scholar] [CrossRef]
- Knirsch, F.; Unterweger, A.; Engel, D. Privacy-preserving Blockchain-based electric vehicle charging with dynamic tariff decisions. Comput. Sci. Res. Dev. 2018, 33, 71–79. [Google Scholar] [CrossRef]
- Mengelkamp, E.; Notheisen, B.; Beer, C.; Dauer, D.; Weinhardt, C. A Blockchain-based smart grid: Towards sustainable local energy markets. Comput. Sci. Res. Dev. 2018, 33, 207–214. [Google Scholar] [CrossRef]
- Zegzhda, D.P.; Moskvin, D.A.; Myasnikov, A.V. Assurance of Cyber Resistance of the Distributed Data Storage Systems Using Blockchain Technology. Autom. Control Comput. Sci. 2018, 52, 1111–1116. [Google Scholar] [CrossRef]
- Dasgupta, D.; Shrein, J.M.; Gupta, K.D. A survey of Blockchain from the security perspective. J. Bank. Financ. Technol. 2019, 3, 1–17. [Google Scholar] [CrossRef]
- Huh, J.H.; Seo, K. Blockchain-based mobile fingerprint verification and automatic login platform for future computing. J. Supercomput. 2019, 75, 3123–3139. [Google Scholar] [CrossRef]
- Nagasubramanian, G.; Sakthivel, R.K.; Patan, R.; Gandomi, A.H.; Sankayya, M.; Balusamy, B. Securing e-health records using keyless signature infrastructure Blockchain technology in the cloud. Neural Comput. Appl. 2019, 1–9. [Google Scholar] [CrossRef]
- Xue, J.; Xu, C.; Zhao, J.; Ma, J. Identity-based public auditing for cloud storage systems against malicious auditors via Blockchain. Sci. China Inf. Sci. 2019, 62, 32104. [Google Scholar] [CrossRef]
- Lee, B.; Lee, J.H. Blockchain-based secure firmware update for embedded devices in an Internet of Things environment. J. Supercomput. 2017, 73, 1152–1167. [Google Scholar] [CrossRef]
- Yu, Q.; Meeuw, A.; Wortmann, F. Design and implementation of a Blockchain multi-energy system. Energy Inform. 2018, 1, 17. [Google Scholar] [CrossRef]
- Malomo, O.O.; Rawat, D.B.; Garuba, M. Next-generation cybersecurity through a Blockchain-enabled federated cloud framework. J. Supercomput. 2018, 74, 5099–5126. [Google Scholar] [CrossRef]
- Altulyan, M.; Yao, L.; Kanhere, S.S.; Wang, X.; Huang, C. A unified framework for data integrity protection in people-centric smart cities. Multimed. Tools Appl. 2019, 1–14. [Google Scholar] [CrossRef]
- Feng, L.; Zhang, H.; Tsai, W.T.; Sun, S. System architecture for high-performance permissioned Blockchains. Front. Comput. Sci. 2019, 1–15. [Google Scholar] [CrossRef]
- Brilliantova, V.; Thurner, T.W. Blockchain and the future of energy. Technol. Soc. 2019, 57, 38–45. [Google Scholar] [CrossRef]
- Reyna, A.; Martín, C.; Chen, J.; Soler, E.; Díaz, M. On Blockchain and its integration with IoT. Challenges and opportunities. Future Gener. Comput. Syst. 2018, 88, 173–190. [Google Scholar] [CrossRef]
- Chen, G.; Xu, B.; Lu, M.; Chen, N.S. Exploring blockchain technology and its potential applications for education. Smart Learn. Environ. 2018, 5, 1. [Google Scholar] [CrossRef]
- Amadio, R.M.; Charatonik, W. On name generation and set-based analysis in the Dolev-Yao model. In International Conference on Concurrency Theory; Springer: Berlin/Heidelberg, Germany, 2002. [Google Scholar]
- Cremers, C.J. The Scyther Tool: Verification, falsification, and analysis of security protocols. In International Conference on Computer–Aided Verification; Springer: Berlin/Heidelberg, Germany, 2008; pp. 414–418. [Google Scholar]
- Cremers, C. Scyther. Semantics and Verification of Security Protocols; University Press Eindhoven: Eindhoven, The Netherlands, 2006. [Google Scholar]
- Yang, H.; Oleshchuk, V.A.; Prinz, A. Verifying Group Authentication Protocols by Scyther. JoWUA 2016, 7, 3–19. [Google Scholar]
- Singh, S.P.; Nayyar, A.; Kumar, R.; Sharma, A. Fog computing: From architecture to edge computing and big data processing. J. Supercomput. 2018, 75, 1–36. [Google Scholar] [CrossRef]
- Pramanik, P.K.D.; Pareek, G.; Nayyar, A. Security and Privacy in Remote Healthcare: Issues, Solutions, and Standards. In Telemedicine Technologies; Academic Press: Cambridge, MA, USA, 2019; pp. 201–225. [Google Scholar]
- Nayyar, A.; Jain, R.; Mahapatra, B.; Singh, A.Q. Cyber Security Challenges for Smart Cities. In Driving the Development, Management, and Sustainability of Cognitive Cities; IGI Global: Hershey, PA, USA, 2019; pp. 27–54. [Google Scholar]
- Tandon, A.; Nayyar, A. A Comprehensive Survey on Ransomware Attack: A Growing Havoc Cyber threat. In Data Management, Analytics and Innovation; Springer: Singapore, 2019; pp. 403–420. [Google Scholar]


| Features Available | Wu et al. [1] | Moon et al. [8] | Yaseen et al. [9,10,11] | Dou et al. [12] | Shaghaghi et al. [13] | Chattopadhyay et al. [14] | Baracaldo et al. [15] |
|---|---|---|---|---|---|---|---|
| Insider behavior/Activity Analysis | No | Yes | Yes | Yes | Yes | Yes | Yes |
| Modification of Authorization rules based on Insider Activity Analysis | No | Yes | Yes | Yes | Yes | No | Yes |
| User-Machine integrity Dependency | No | No | No | Yes | No | No | No |
| Authentication of Insider | No | No | No | No | No | No | No |
| The encryption used on User Data before querying on cloud | Yes | No | No | No | No | No | No |
| Features Available | Tsai et al. [16] | Yang et al. [17] | Kumari et al. [18] | Shajina and Varalakshmi [19] | Anakath et al. [20] | Chaudhary et al. [21] | Kumar et al. [22] | Neha and Chatterjee [23] |
|---|---|---|---|---|---|---|---|---|
| Authentication Type | Three factor | Two Factor | Multi-Factor | Two Factor | Multi-Factor | Three factor | Biometric | Biometric |
| Single sign-on | Yes | Yes | No | Yes | No | Yes | No | No |
| Cryptography Algorithm used | Yes | Yes | Yes | Yes | Yes | Yes | Yes | No |
| Clustering Algorithm Used | No | No | No | No | No | No | No | Yes |
| Suitable for Resource constraint IOT | No | No | Yes | No | No | No | No | No |
| Mutual Authentication | Yes | No | Yes | Yes | No | Yes | Yes | Yes |
| Multi Owners Authentication | No | No | No | Yes | No | No | No | No |
| Distributed Ledger Based Authentication | No | No | No | No | No | No | No | No |
| Attacks | Proposed Blockchain Authentication Mechanism | Tsai et al. [16] | Yang et al. [17] | Shajina and Varalakshmi [19] | Anakath et al. [20] | Chaudhary et al. [21] |
|---|---|---|---|---|---|---|
| Resist of-line password Guessing attack | Yes | Yes | Yes | No | Yes | Yes |
| Prevent replay attack | Yes | Yes | Yes | Yes | Yes | Yes |
| Minimize DoS attack during the authentication process | Yes | Yes | Yes | Yes | Yes | Yes |
| Prevent insider attack | Yes | No | No | No | No | No |
| Prevent impersonation attack | Yes | No | Yes | Yes | Yes | Yes |
© 2019 by the authors. Licensee MDPI, Basel, Switzerland. This article is an open access article distributed under the terms and conditions of the Creative Commons Attribution (CC BY) license (http://creativecommons.org/licenses/by/4.0/).
Share and Cite
Deep, G.; Mohana, R.; Nayyar, A.; Sanjeevikumar, P.; Hossain, E. Authentication Protocol for Cloud Databases Using Blockchain Mechanism. Sensors 2019, 19, 4444. https://doi.org/10.3390/s19204444
Deep G, Mohana R, Nayyar A, Sanjeevikumar P, Hossain E. Authentication Protocol for Cloud Databases Using Blockchain Mechanism. Sensors. 2019; 19(20):4444. https://doi.org/10.3390/s19204444
Chicago/Turabian StyleDeep, Gaurav, Rajni Mohana, Anand Nayyar, P. Sanjeevikumar, and Eklas Hossain. 2019. "Authentication Protocol for Cloud Databases Using Blockchain Mechanism" Sensors 19, no. 20: 4444. https://doi.org/10.3390/s19204444
APA StyleDeep, G., Mohana, R., Nayyar, A., Sanjeevikumar, P., & Hossain, E. (2019). Authentication Protocol for Cloud Databases Using Blockchain Mechanism. Sensors, 19(20), 4444. https://doi.org/10.3390/s19204444








