Crowdsourced Traffic Event Detection and Source Reputation Assessment Using Smart Contracts
Abstract
1. Introduction
2. Related Work
3. Proposed Solution
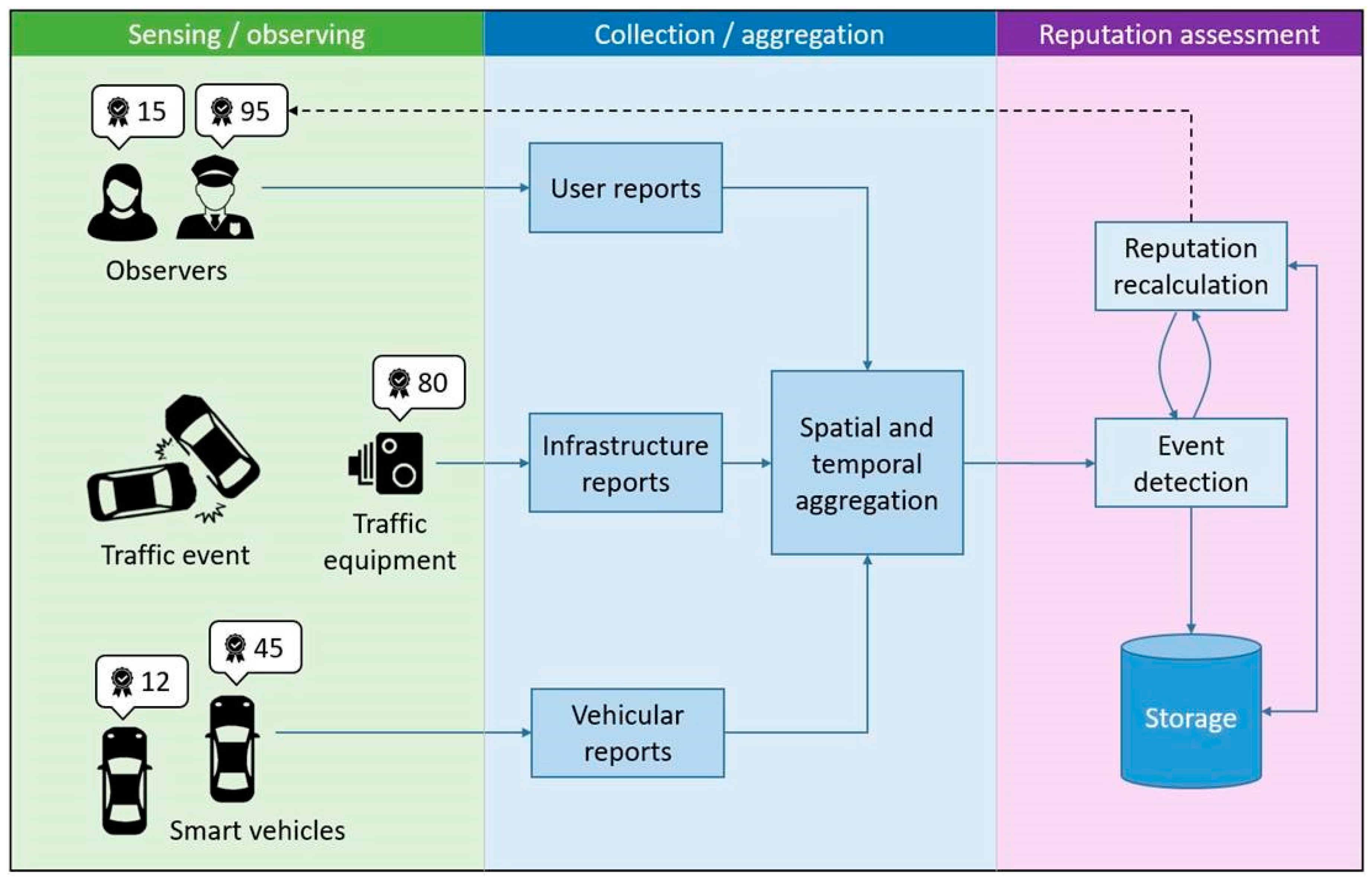
3.1. Assumptions and System Design
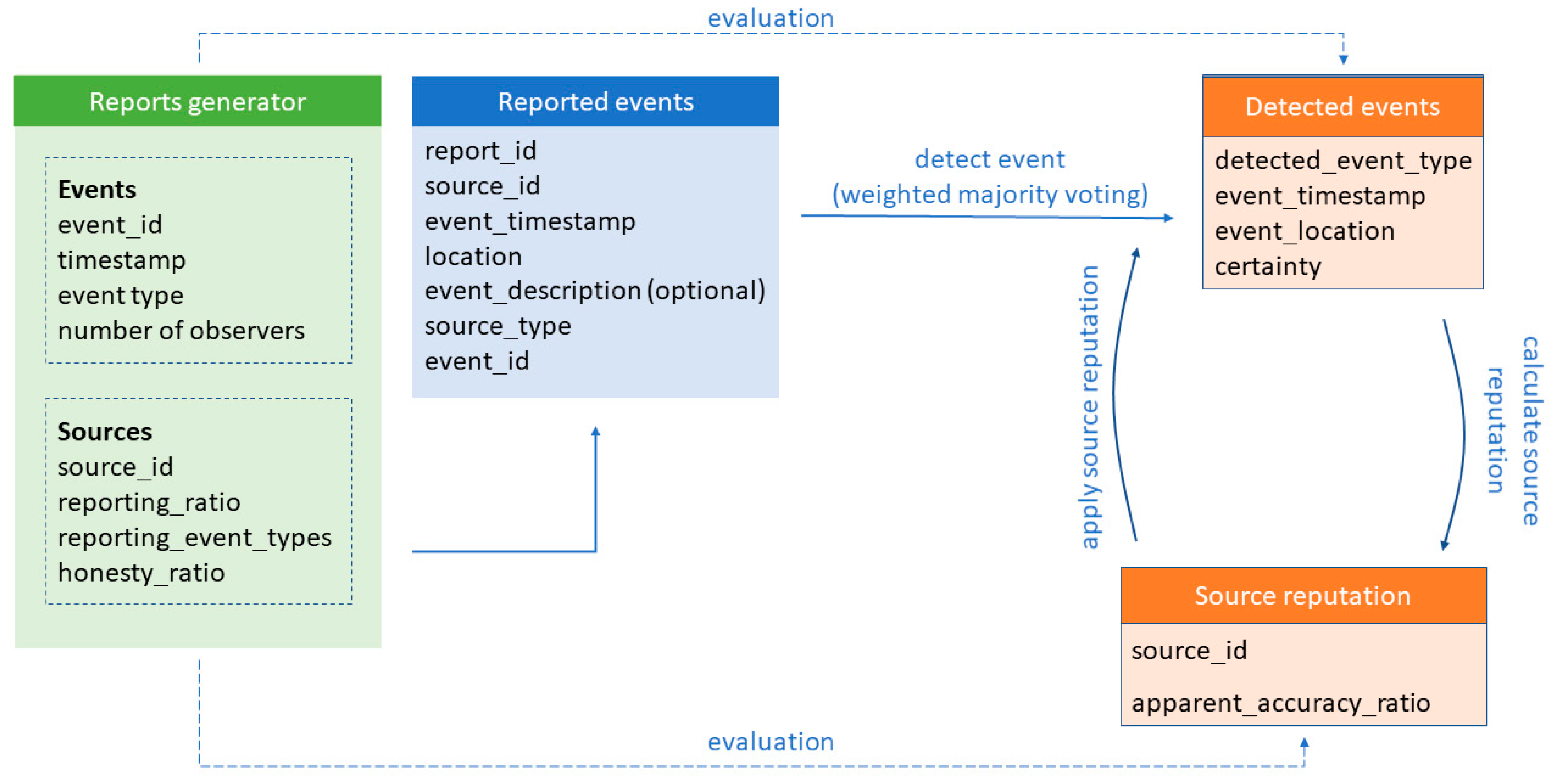
3.2. Data Model
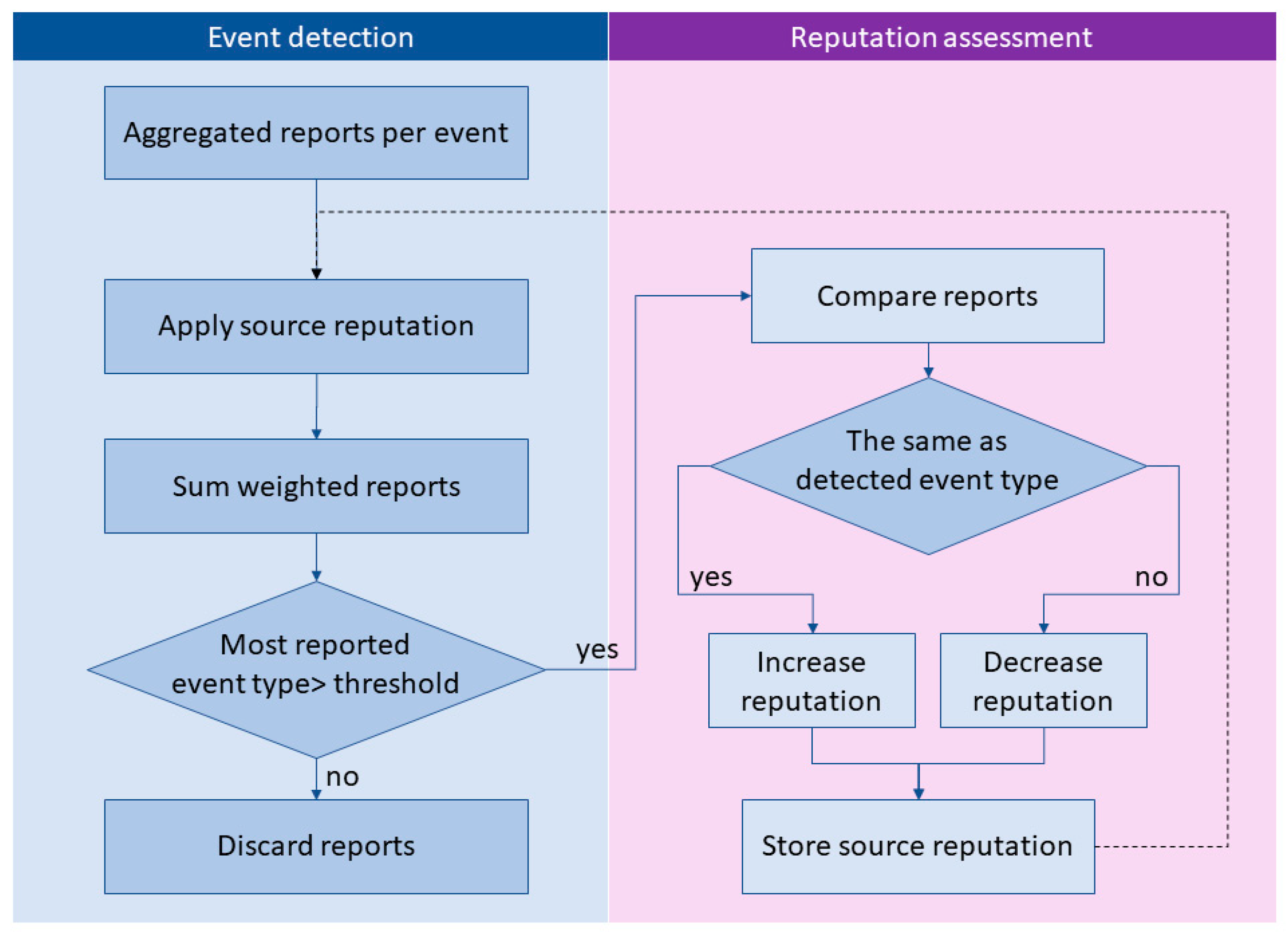
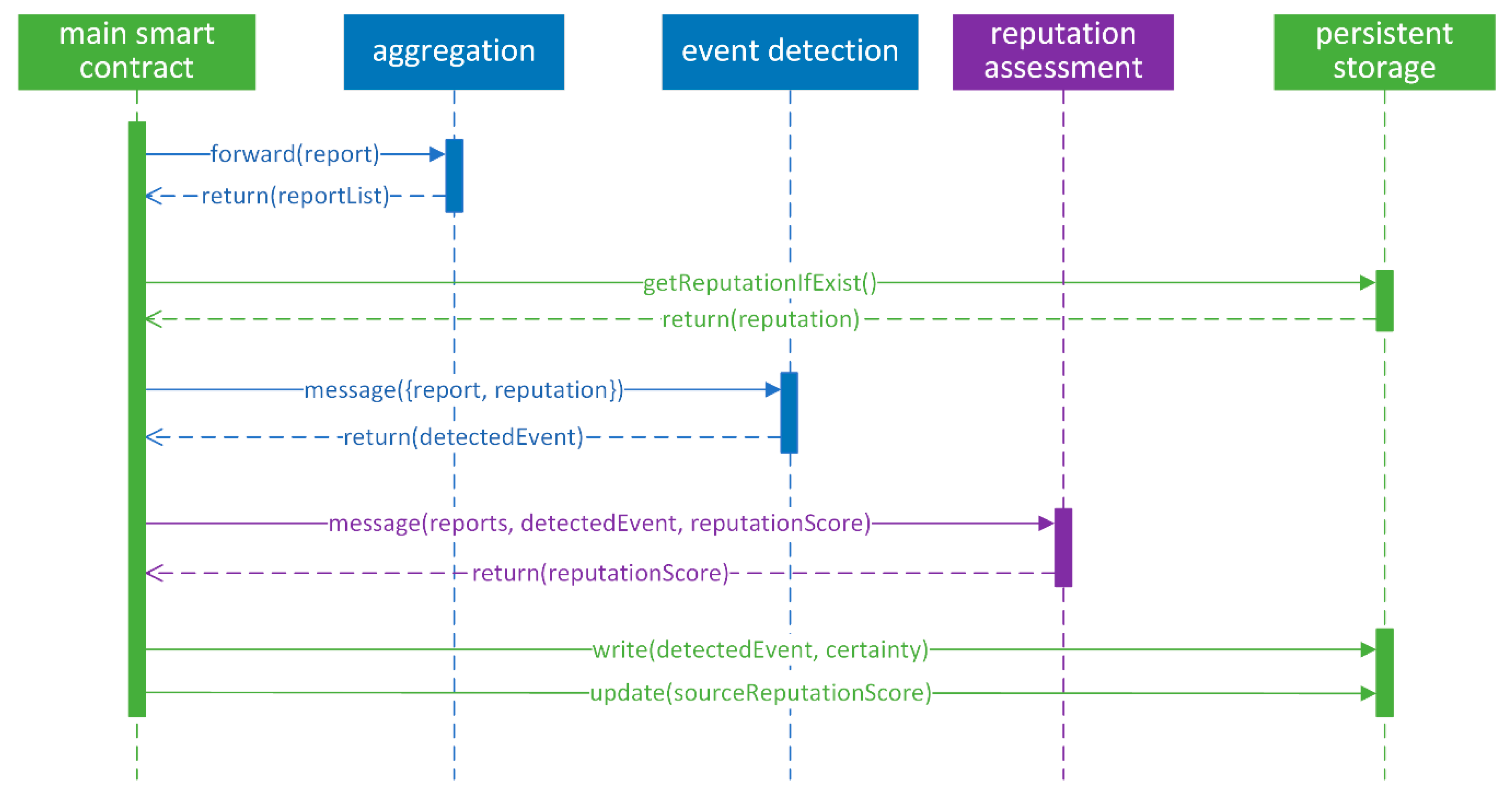
3.3. Event Detection and Source Reputation
4. Implementation and Verification
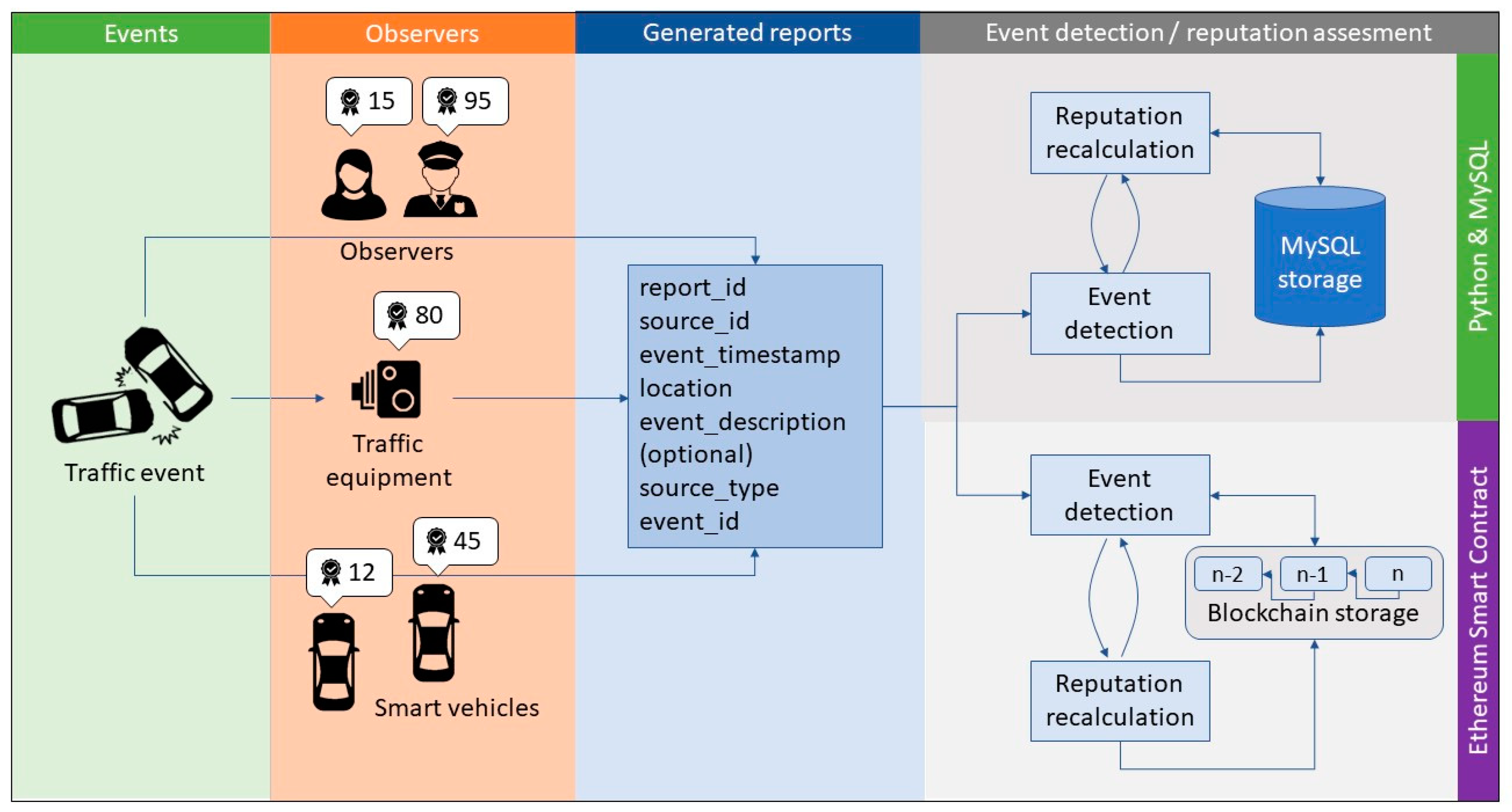
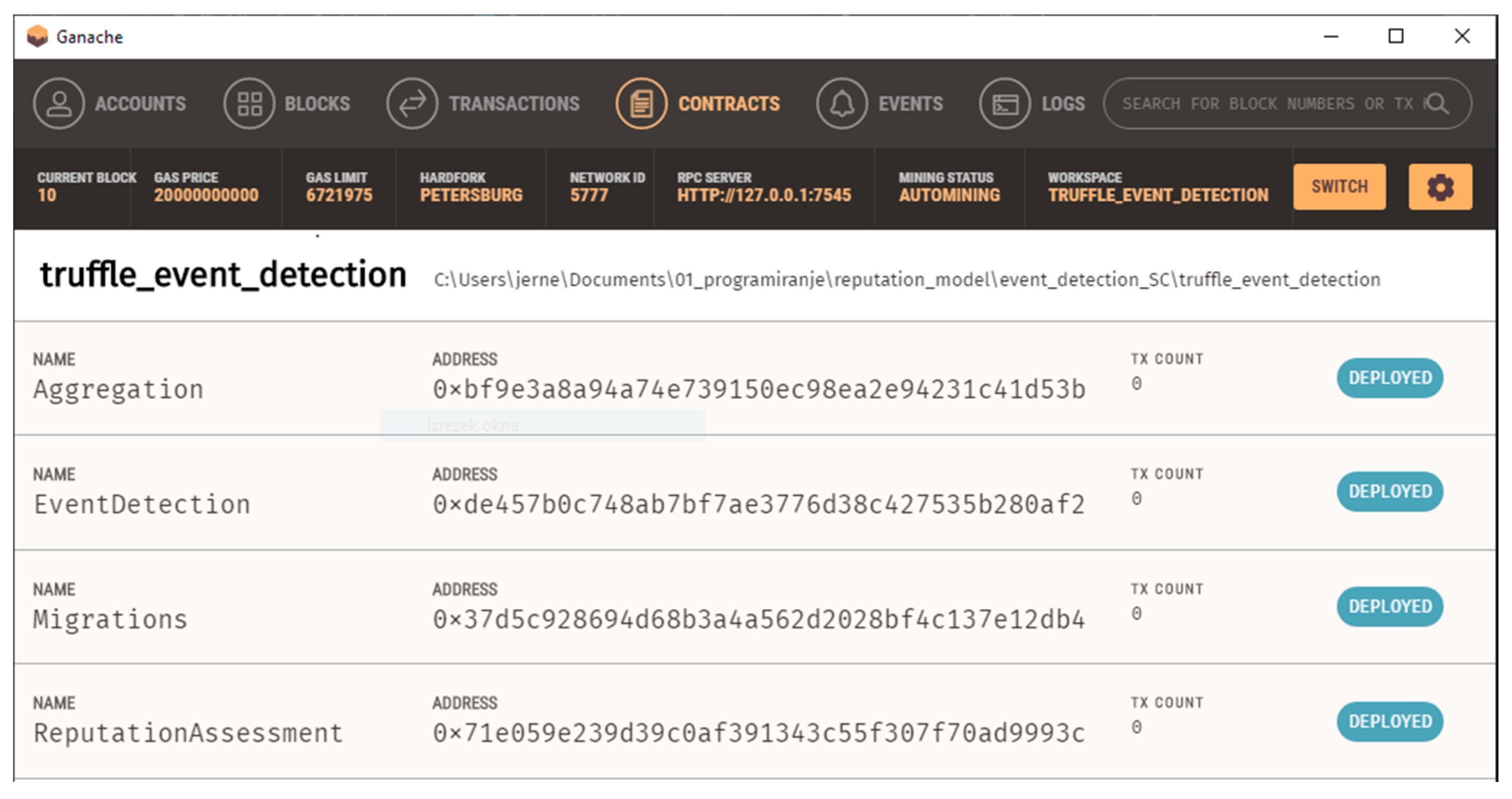
4.1. Blockchain Implementation
| Algorithm 1: Pseudocode of blockchain implementation |
| reports = [list of traffic reports made by users, vehicles and infrastructure] events = [dictionary of reports belonging to the same event] reputation_weights = [dictionary of reputation values for each data source] function aggregate_reports(reports): for each reporti in reports: for each eventj in events: if (reporti.time <= eventj.time + max_delta_t) and abs(reporti.location - eventj.location) <= max_distance): add reporti to eventj if no match: create new event and add reporti to it if count of reports for eventj == 5: detected_type = detect_event_type(eventj) if detected_type: store detected_type reputation_weight = assess_reputation(eventj, detected_type) store reputation_weight function detect_event_type(event): get reputation_weights for all reports in event based on reporting data source detected_event_types = [] for each reporti in event.reports: detected_event_types.push(reporti.event_type * reporti.source.reputation_weight) if max(detected_event_types) > threshold: return max(detected_event_types) function assess_reputation(event, detected_event_type): for each reporti in event.reports: if reporti.event_type == detected_event_type: increase reputation_weight else: decrease reputation_weight aggregate_reports(reports) |
4.2. Verification and Results
5. Conclusions and Future Work
Author Contributions
Funding
Acknowledgments
Conflicts of Interest
References
- Han, S.; Cao, D.; Li, L.; Li, L.; Li, S.E.; Zheng, N.N.; Wang, F.Y. From Software-Defined Vehicles to Self-Driving Vehicles: A Report on CPSS-Based Parallel Driving. IEEE Intell. Transp. Syst. Mag. 2019, 11, 6–14. [Google Scholar] [CrossRef]
- Restuccia, F.; Ghosh, N.; Bhattacharjee, S.; Das, S.K.; Melodia, U.T. Quality of Information in Mobile Crowdsensing: Survey and Research Challenges. ACM Trans. Sens. Netw. (TOSN) 2017, 13, 34. [Google Scholar] [CrossRef]
- Wan, J.; Liu, J.; Shao, Z.; Vasilakos, A.V.; Imran, M.; Zhou, K. Mobile crowd sensing for traffic prediction in internet of vehicles. Sensors 2016, 16, 88. [Google Scholar] [CrossRef] [PubMed]
- Wang, X.; Zhang, J.; Tian, X.; Gan, X.; Guan, Y.; Wang, X. Crowdsensing-Based Consensus Incident Report for Road Traffic Acquisition. IEEE Trans. Intell. Transp. Syst. 2017, 19, 2536–2547. [Google Scholar] [CrossRef]
- Shi, F.; Qin, Z.; Wu, D.; McCann, J.A. Effective truth discovery and fair reward distribution for mobile crowdsensing. Pervasive Mob. Comput. 2018, 51, 88–103. [Google Scholar] [CrossRef]
- Campbell, A.T.; Lane, N.D.; Miluzzo, E.; Peterson, R.A.; Eisenman, S.B. The Rise of People-Centric Sensing. IEEE Internet Comput. 2008, 12, 12–21. [Google Scholar] [CrossRef]
- Gubbi, J.; Buyya, R.; Marusic, S.; Palaniswami, M. Internet of Things (IoT): A vision, architectural elements, and future directions. Futur. Gener. Comput. Syst. 2013, 29, 1645–1660. [Google Scholar] [CrossRef]
- Ochoa, S.F.; Fortino, G.; di Fatta, G. Cyber-physical systems, internet of things and big data. Futur. Gener. Comput. Syst. 2017, 75, 82–84. [Google Scholar] [CrossRef]
- Fernandez-Carames, T.M.; Fraga-Lamas, P. A Review on the Use of Blockchain for the Internet of Things. IEEE Access 2018, 3536, 1. [Google Scholar] [CrossRef]
- Xiong, G.; Zhu, F.; Liu, X.; Dong, X.; Huang, W.; Chen, S.; Zhao, K. Cyber-physical-social system in intelligent transportation. IEEE/CAA J. Autom. Sin. 2015, 2, 320–333. [Google Scholar]
- Roman, R.; Lopez, J.; Mambo, M. Mobile edge computing, Fog et al.: A survey and analysis of security threats and challenges. Futur. Gener. Comput. Syst. 2018, 78, 680–698. [Google Scholar] [CrossRef]
- Hawlitschek, F.; Notheisen, B.; Teubner, T. The limits of trust-free systems: A literature review on blockchain technology and trust in the sharing economy. Electron. Commer. Res. Appl. 2018, 29, 50–63. [Google Scholar] [CrossRef]
- Tschorsch, F.; Scheuermann, B. Bitcoin and beyond: A technical survey on decentralized digital currencies. IEEE Commun. Surv. Tutor. 2016, 18, 2084–2123. [Google Scholar] [CrossRef]
- Panarello, A.; Tapas, N.; Merlino, G.; Longo, F.; Puliafito, A. Blockchain and iot integration: A systematic survey. Sensors 2018, 18, 2575. [Google Scholar] [CrossRef] [PubMed]
- Lu, Z.; Qu, G.; Liu, Z. A Survey on Recent Advances in Vehicular Network Security, Trust, and Privacy. IEEE Trans. Intell. Transp. Syst. 2019, 20, 760–776. [Google Scholar] [CrossRef]
- Reddy, A.G.; Suresh, D.; Phaneendra, K.; Shin, J.S.; Odelu, V. Provably secure pseudo-identity based device authentication for smart cities environment. Sustain. Cities Soc. 2018, 41, 878–885. [Google Scholar] [CrossRef]
- Hammi, M.T.; Hammi, B.; Bellot, P.; Serhrouchni, A. Bubbles of Trust: A decentralized blockchain-based authentication system for IoT. Comput. Secur. 2018, 78, 126–142. [Google Scholar] [CrossRef]
- Conti, M.; Passarella, A.; Das, S.K. The Internet of People (IoP): A new wave in pervasive mobile computing. Pervasive Mob. Comput. 2017, 41, 1–27. [Google Scholar] [CrossRef]
- Boavida, F.; Kliem, A.; Renner, T.; Riekki, J.; Jouvray, C.; Jacovi, M.; Triviño, A. People-Centric Internet of Things—Challenges, Approach, and Enabling Technologies. In Intelligent Distributed Computing IX; Novais, P., Camacho, D., Analide, C., El Seghrouchni, A.F., Badica, C., Eds.; Springer International Publishing: Cham, Switzerland, 2016; pp. 463–474. [Google Scholar]
- Draft Report on European Security Mechanism. Available online: https://www.c-roads.eu/fileadmin/user_upload/media/Dokumente/20190125_TF1_Security_report_v1.4_final.pdf (accessed on 26 February 2019).
- Zhang, Y.; Kasahara, S.; Shen, Y.; Jiang, X.; Wan, J. Smart Contract-Based Access Control for the Internet of Things. IEEE Internet Things J. 2018, 6, 1594–1605. [Google Scholar] [CrossRef]
- Wright, C.; Serguieva, A. Sustainable Blockchain-Enabled Services: Smart Contracts. In Proceedings of the IEEE International Conference on Big Data (Big Data), Boston, MA, USA, 11–14 December 2017; pp. 4255–4264. [Google Scholar]
- Christidis, K.; Devetsikiotis, M. Blockchains and Smart Contracts for the Internet of Things. IEEE Access 2016, 4, 2292–2303. [Google Scholar] [CrossRef]
- Alsheikh, M.A.; Jiao, Y.; Niyato, D.; Wang, P.; Leong, D.; Han, Z. The Accuracy-Privacy Trade-off of Mobile Crowdsensing. IEEE Commun. Mag. 2017, 55, 132–139. [Google Scholar] [CrossRef]
- Lu, Z.; Liu, W.; Wang, Q.; Qu, G.; Liu, Z. A Privacy-Preserving Trust Model Based on Blockchain for VANETs. IEEE Access 2018, 6, 45655–45664. [Google Scholar] [CrossRef]
- Wang, J.; Li, M.; He, Y.; Li, H.; Xiao, K.; Wang, C. A Blockchain Based Privacy-Preserving Incentive Mechanism in Crowdsensing Applications. IEEE Access 2018, 6, 17545–17556. [Google Scholar] [CrossRef]
- Li, M.; Weng, J.; Yang, A.; Lu, W.; Zhang, Y.; Hou, L.; Deng, H.R. CrowdBC: A Blockchain-based Decentralized Framework for Crowdsourcing. IEEE Trans. Parallel Distrib. Syst. 2018, 30, 1251–1266. [Google Scholar] [CrossRef]
- Lopez, J.; Rios, R.; Bao, F.; Wang, G. Evolving privacy: From sensors to the Internet of Things. Futur. Gener. Comput. Syst. 2017, 75, 46–57. [Google Scholar] [CrossRef]
- Jia, B.; Zhou, T.; Li, W.; Liu, Z.; Zhang, J. A Blockchain-Based Location Privacy Protection Incentive Mechanism in Crowd Sensing Networks. Sensors 2018, 18, 3894. [Google Scholar] [CrossRef] [PubMed]
- Khan, M.A.; Salah, K. IoT security: Review, blockchain solutions, and open challenges. Futur. Gener. Comput. Syst. 2018, 82, 395–411. [Google Scholar] [CrossRef]
- Nitti, M.; Girau, R.; Atzori, L.; Iera, A.; Morabito, G. A Subjective Model for Trustworthiness Evaluation in the Social Internet of Things. In Proceedings of the 23rd International Symposium on Personal, Indoor and Mobile Radio Communications (PIMRC), Sydney, Australia, 9–12 September 2012; pp. 18–23. [Google Scholar]
- Nitti, M.; Girau, R.; Atzori, L. Trustworthiness Management in the Social Internet of Things. IEEE Trans. Knowl. Data Eng. 2014, 26, 1253–1266. [Google Scholar] [CrossRef]
- Mousa, H.; Mokhtar, S.B.; Hasan, O.; Younes, O.; Hadhoud, M.; Brunie, L. Trust management and reputation systems in mobile participatory sensing applications: A survey. Comput. Netw. 2015, 90, 49–73. [Google Scholar] [CrossRef]
- Truffle Suite—Your Ethereum Swiss Army Knife. Available online: http://truffleframework.com (accessed on 10 May 2018).
- Available online: http://truffleframework.com/ganache (accessed on 10 May 2018).

| ID | Source Type | Reporting Ratio | Apparent Accuracy Aatio | Notes |
|---|---|---|---|---|
| 34 | Vehicle | 0.8 | 1 | |
| 140 | User | 0.8 | 1 | Reporting near school |
| 156 | User | 0.5 | 0.8 | Reporting dangerous situations |
| 446 | Vehicle | 0.5 | 1 | |
| 461 | Government | 1 | 1 | Police |
| 510 | User | 0.7 | 0.8 | Sometimes wrong reports |
| 527 | User | 0.6 | 0.0 | Misreporter |
| Event | Timestamp | Event Type | Location | |
| 4.09.2018 22:42 | Careless Driving | 46.0645718, 14.5066889 | ||
| Reports | Timestamp | Reported event type | Location | Source type |
| 4.09.2018 22:42 | careless driving | 46.0678532, 14.5088111 | user | |
| 4.09.2018 22:43 | careless driving | 46.0679797, 14.5086931 | user | |
| 4.09.2018 22:44 | careless driving | 46.0677266, 14.508618 | user | |
| 4.09.2018 22:42 | red light | 46.0673842, 14.5086394 | user | |
| 4.09.2018 22:42 | speeding | 46.0665059, 14.5077382 | vehicle | |
| Detected event | Timestamp | Event type | Location | Certainty |
| 4.09.2018 22:42 | careless driving | 46.067490, 14.508500 | 0.6 |
| Data Source | Infrastructure | Users | Vehicles | ||
|---|---|---|---|---|---|
| Misreporting | Accurate | In-between | |||
| Number of sources | 100 | 20 | 50 | 30 | 100 |
| Initial accuracy ratio | 1 | 0 | 1 | 0.8 | 0.8 |
| Assessed reputation correctness | Not assessed | 100% | >90% of sources in range [0.7,0.9] | ||
© 2019 by the authors. Licensee MDPI, Basel, Switzerland. This article is an open access article distributed under the terms and conditions of the Creative Commons Attribution (CC BY) license (http://creativecommons.org/licenses/by/4.0/).
Share and Cite
Mihelj, J.; Zhang, Y.; Kos, A.; Sedlar, U. Crowdsourced Traffic Event Detection and Source Reputation Assessment Using Smart Contracts. Sensors 2019, 19, 3267. https://doi.org/10.3390/s19153267
Mihelj J, Zhang Y, Kos A, Sedlar U. Crowdsourced Traffic Event Detection and Source Reputation Assessment Using Smart Contracts. Sensors. 2019; 19(15):3267. https://doi.org/10.3390/s19153267
Chicago/Turabian StyleMihelj, Jernej, Yuan Zhang, Andrej Kos, and Urban Sedlar. 2019. "Crowdsourced Traffic Event Detection and Source Reputation Assessment Using Smart Contracts" Sensors 19, no. 15: 3267. https://doi.org/10.3390/s19153267
APA StyleMihelj, J., Zhang, Y., Kos, A., & Sedlar, U. (2019). Crowdsourced Traffic Event Detection and Source Reputation Assessment Using Smart Contracts. Sensors, 19(15), 3267. https://doi.org/10.3390/s19153267






