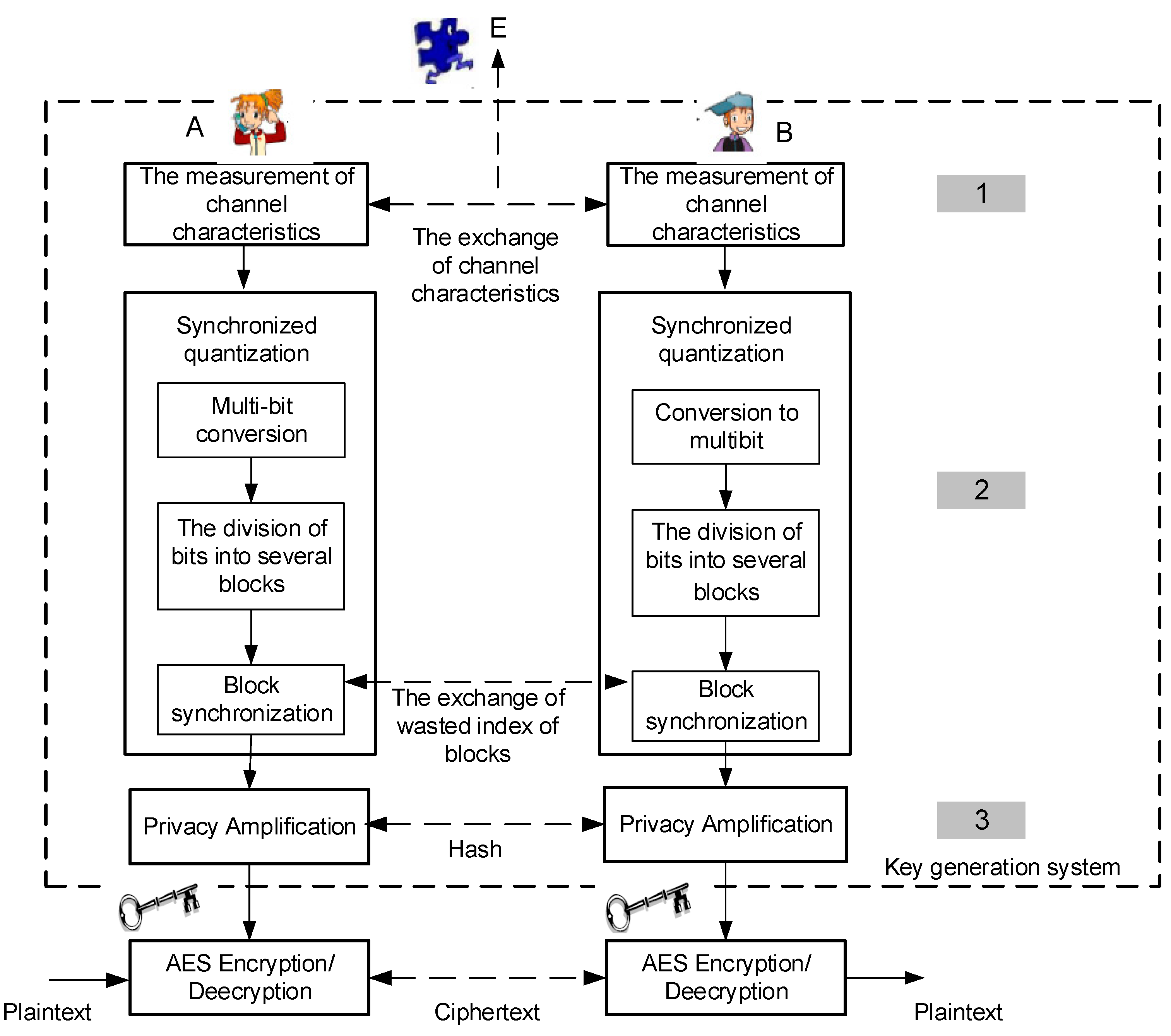
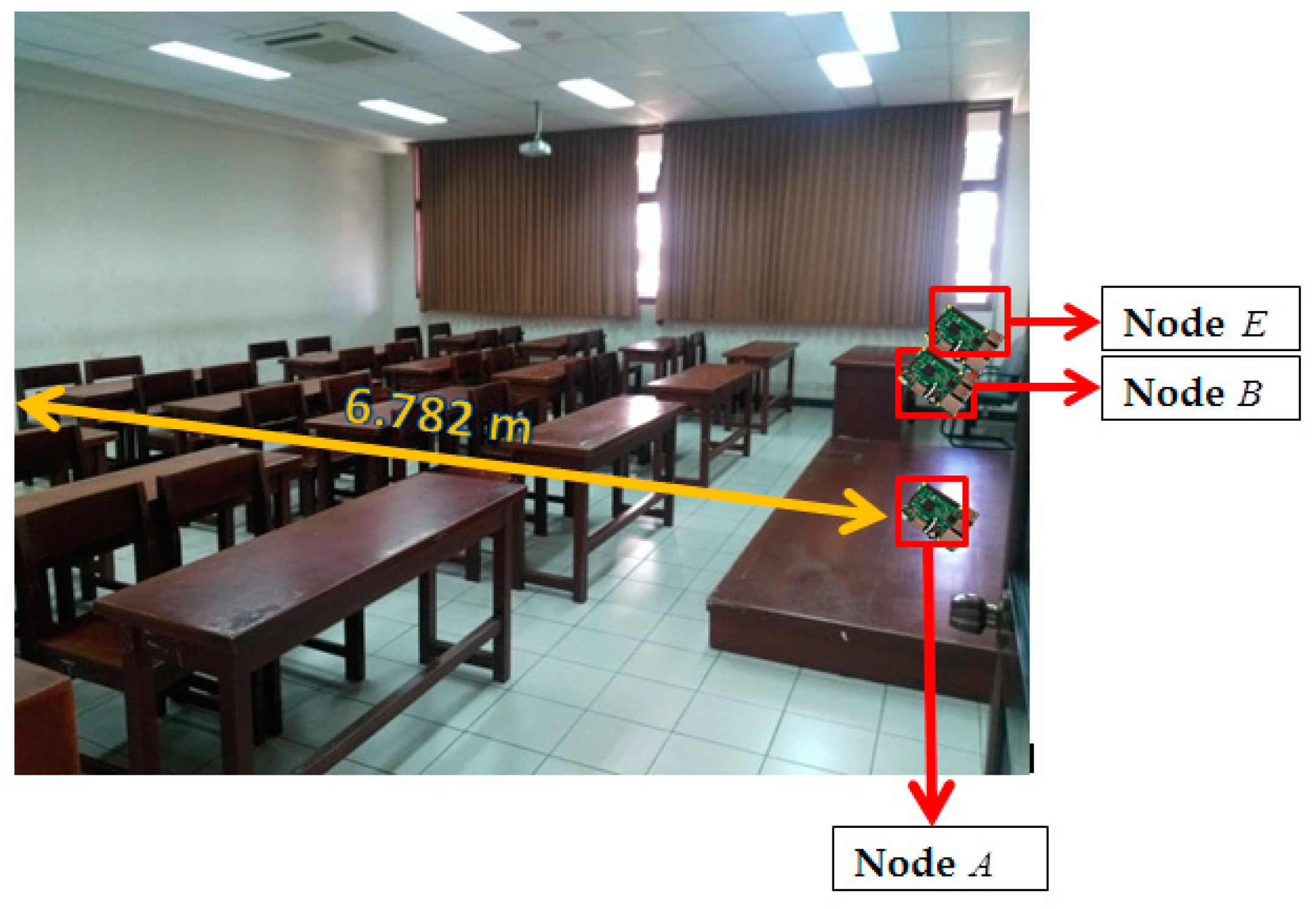
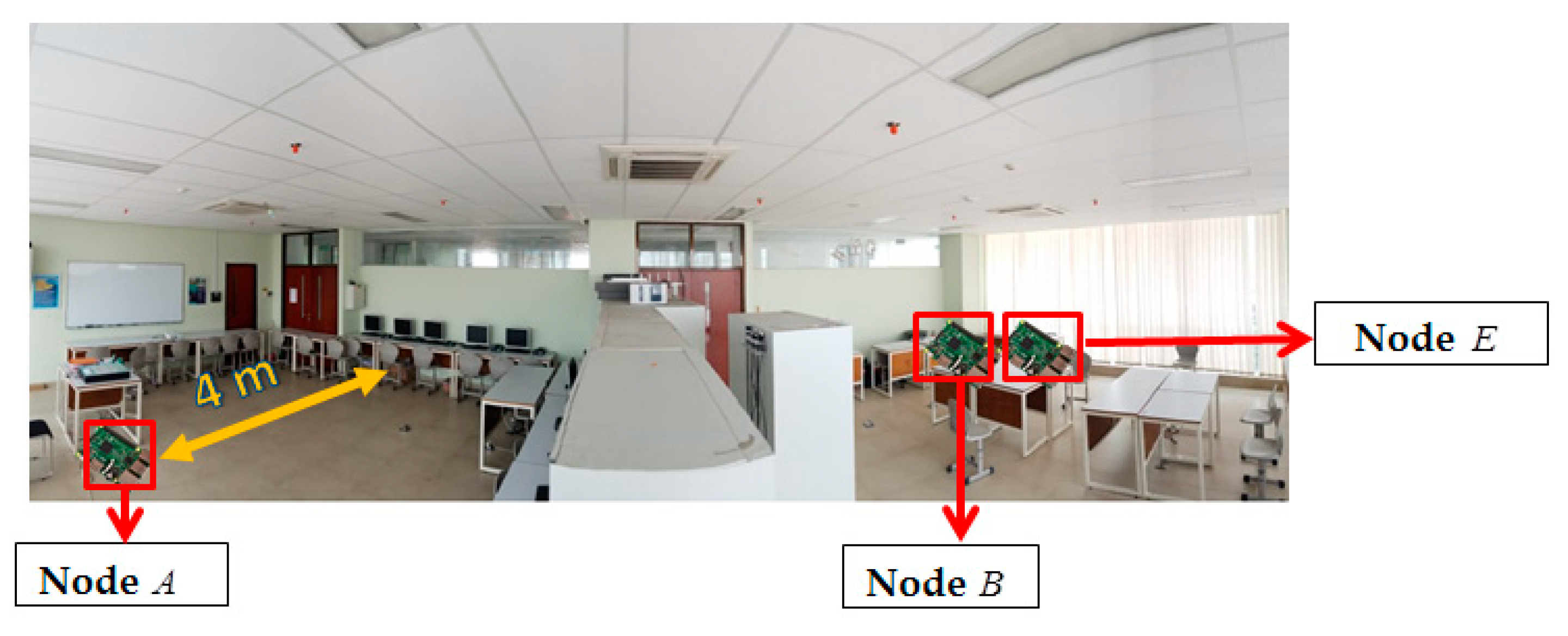
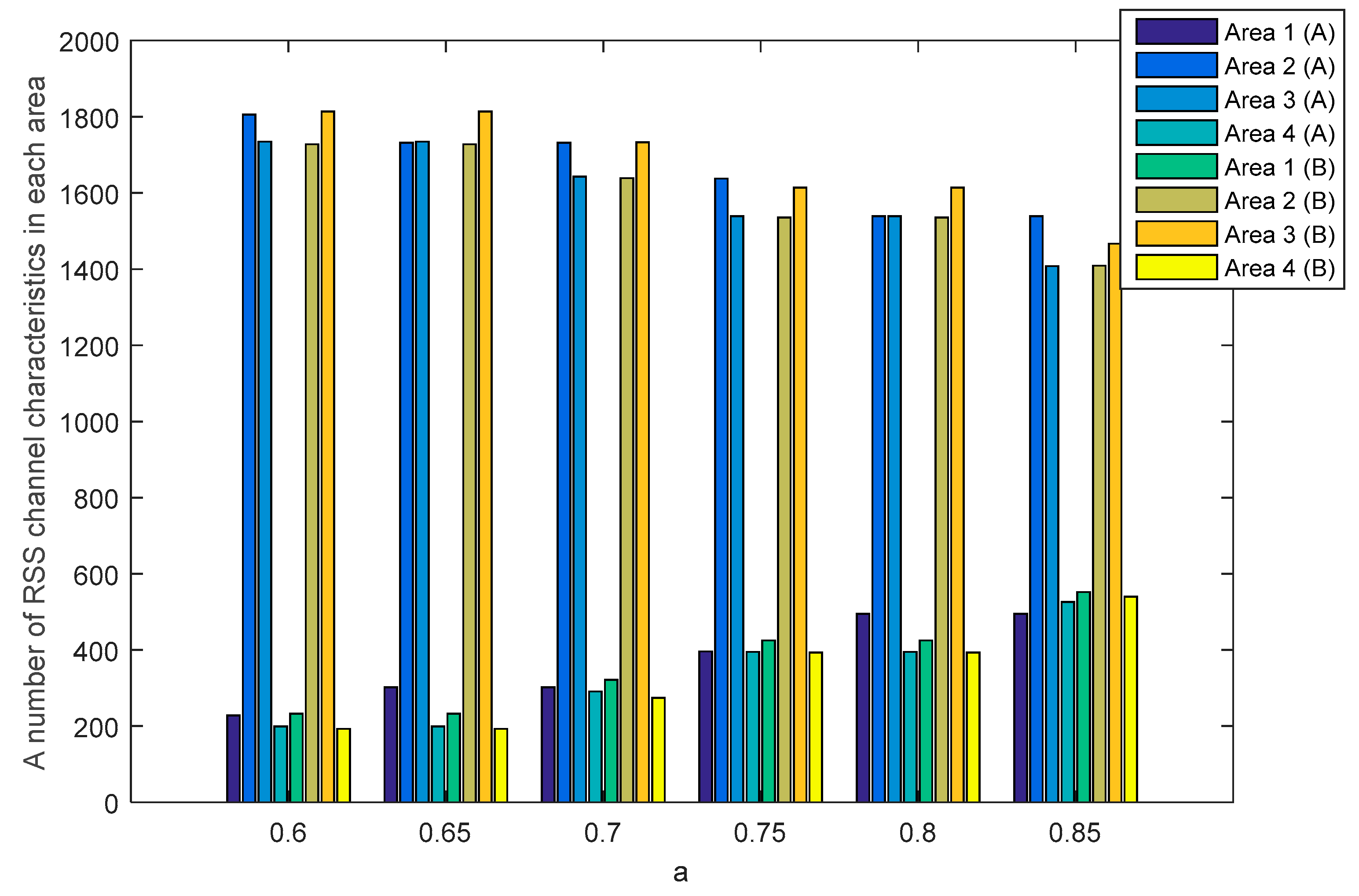This section discusses in detail the performance parameters and the performance analysis of test results. The used performance parameters are aimed at determining the success rate of the SSE key generation system. Performance analysis discusses in detail the measurement results performed in two types of scenarios and the advantages of the SSE system compared with previous key generation systems.
5.2.2. Performance Analysis of the SSE System
Figure 8 and
Figure 9 show box plots of the correlation coefficients measurement results between nodes in the unobstructed and obstacles scenarios. In this paper, the box plots were obtained from the calculation of data block correlation coefficients with Equation (1), each of which contained 128 RSS channel characteristics. The smaller the value of the correlation coefficient, the more different RSS channel characteristic values are obtained from the measurement results, so it is difficult to get the same keys. The correlation coefficients value range from 1 to −1. There are three pieces of information that will be retrieved from the box plots i.e., the median, the lower and upper quartile of the correlation coefficient. The correlation coefficient results between nodes
in the unobstructed scenario obtained a median value of 0.7547, lower quartile of 0.7303, and the upper quartile of 0.7809. The correlation coefficient results between nodes
show a median value of 0.0007, lower quartile of −0.0462 and upper quartile of 0.0825. Meanwhile, the correlation coefficient obtained between nodes
indicates similar results with correlation coefficient obtained from the node
with the median value of 0.0323, the lower quartile and the upper quartile of −0.0575 at 0.0718. The results of testing in an unobstructed scenario indicate the difficulty of the unauthorized node to get the same key because of the significant difference of the correlation coefficient between the authorized nodes (
) and the unauthorized node (
and
). The correlation coefficient results between nodes
in the obstacles scenario obtained a median value of 0.7021, lower quartile of 0.6645, and the upper quartile of 0.7326. The correlation coefficient results between nodes
show a median value of 0.0143, lower quartile of −0.0687 and the upper quartile of 0.0631. Whereas the correlation coefficient obtained between nodes
indicate similar results with correlation coefficient obtained from the node
with the median value of 0.0430, lower quartile of −0.0220 and upper quartile of 0.0772. Generally, it can be seen that the correlation coefficient value of authorized nodes in the obstacles scenario is lower than the unobstructed scenario. There is a barrier between authorized nodes so that the RSS channel characteristics obtained is also worse and decreases the correlation coefficient of the measurement results. Similar to the testing conducted in an unobstructed scenario, the correlation coefficients obtained also indicate the difficulty of the unauthorized node to get the same key because of the significant difference of the correlation coefficient between the authorized nodes (
) and the unauthorized node (
and
).
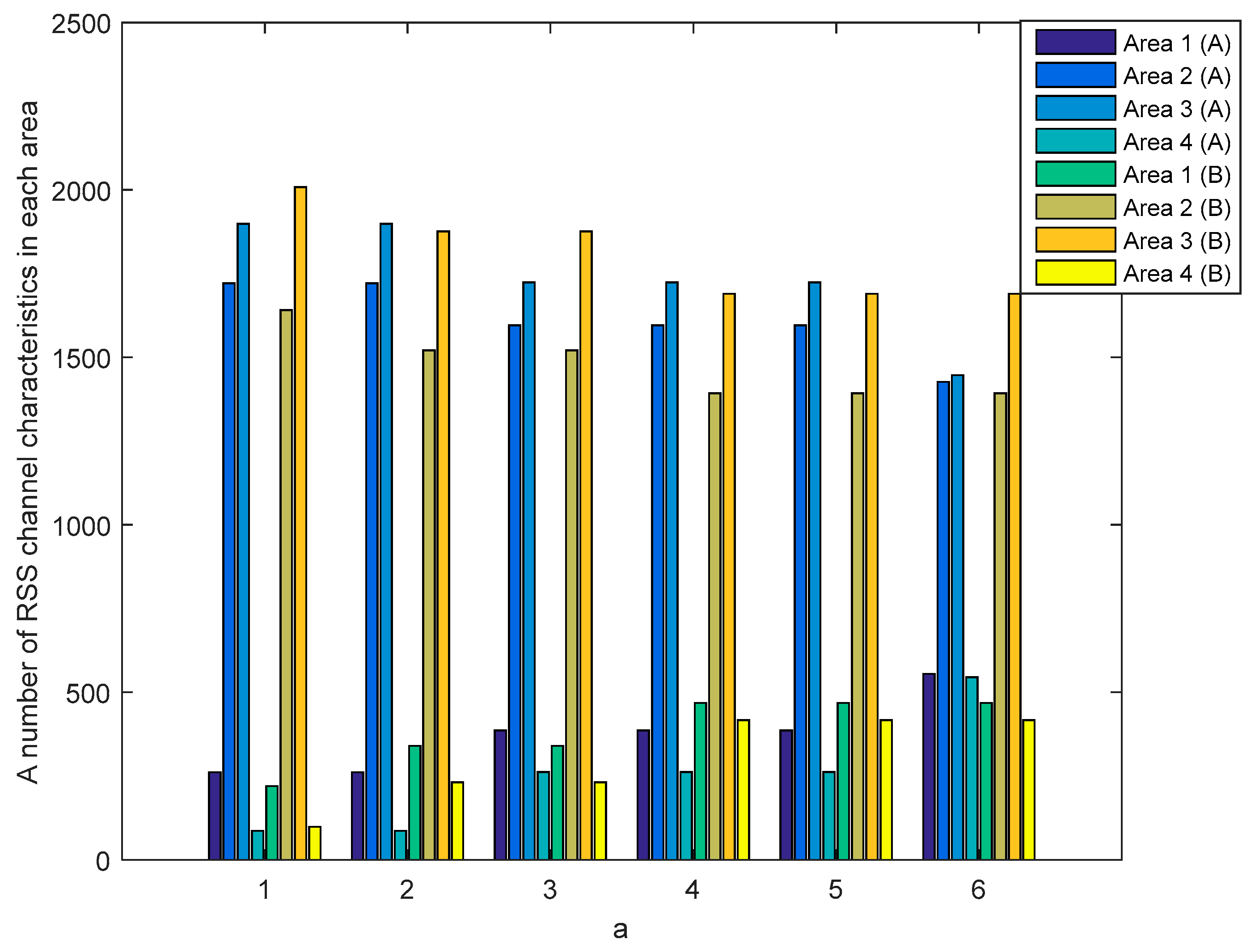
The SQ method performs the multi-bit conversion by dividing the RSS channel characteristics into several areas. The number of RSS channel characteristics in each area is strongly influenced by the selection of
as a standard deviation dividing parameter.
Figure 10 and
Figure 11 show the number of RSS channel characteristics from the node
and
in each area on the unobstructed and obstacles scenarios. The performed tests indicate that in all of the value of
the highest amount of RSS is in area 2 and 3. These conditions resulted in increasing the probability of getting three sequential bits i.e., 111 and convert it to 1. The resulting key bit will be dominated by 1. The higher the
value, the higher the possibility to get variations 1 and 0 of the produced keys is. This happens because of the growing number of RSS channel characteristics that are in area 1 and 4 thus increasing the probability of getting three sequential bits i.e., 000 and converting them to 0. The higher variations 1 and 0 in the resulting key, the higher the likelihood of different key bits being produced between the two nodes.
Table 2 shows the number of equal keys with lengths of 128, 192 and 256 that were successfully produced from two scenarios. Equal keys are obtained if the resulting KDIR between authorized nodes is 0. The test results in unobstructed scenario show that the higher the value of
the less equal key is successfully produced. This happens because of the higher variations of the 1 and 0 thus reducing the possibility of getting an equal key. The highest number of equal keys is obtained when
and
. In these parameters, most RSS channel characteristics are in areas 2 and 3 so that the resulting key bits are dominated by 1. The low variation in the resulting bits increases the possibility to get an equal key. The test results in obstacles scenario show that the equal key is only obtained when
and
. The high difference in the amount of RSS channel characteristics in each area and also the higher variations of 1 and 0 triggering more difficulties to get the equal key. The encryption method used to randomize the messages is Advanced Encryption Standard (AES) with key lengths of 128, 192, and 256. In this study, we focus on 128-bit keys because our proposed key generation system produces more keys at the key length of 128. The more keys produced, the higher the KSR value is generated so it can improve the performance of the built key generation system.
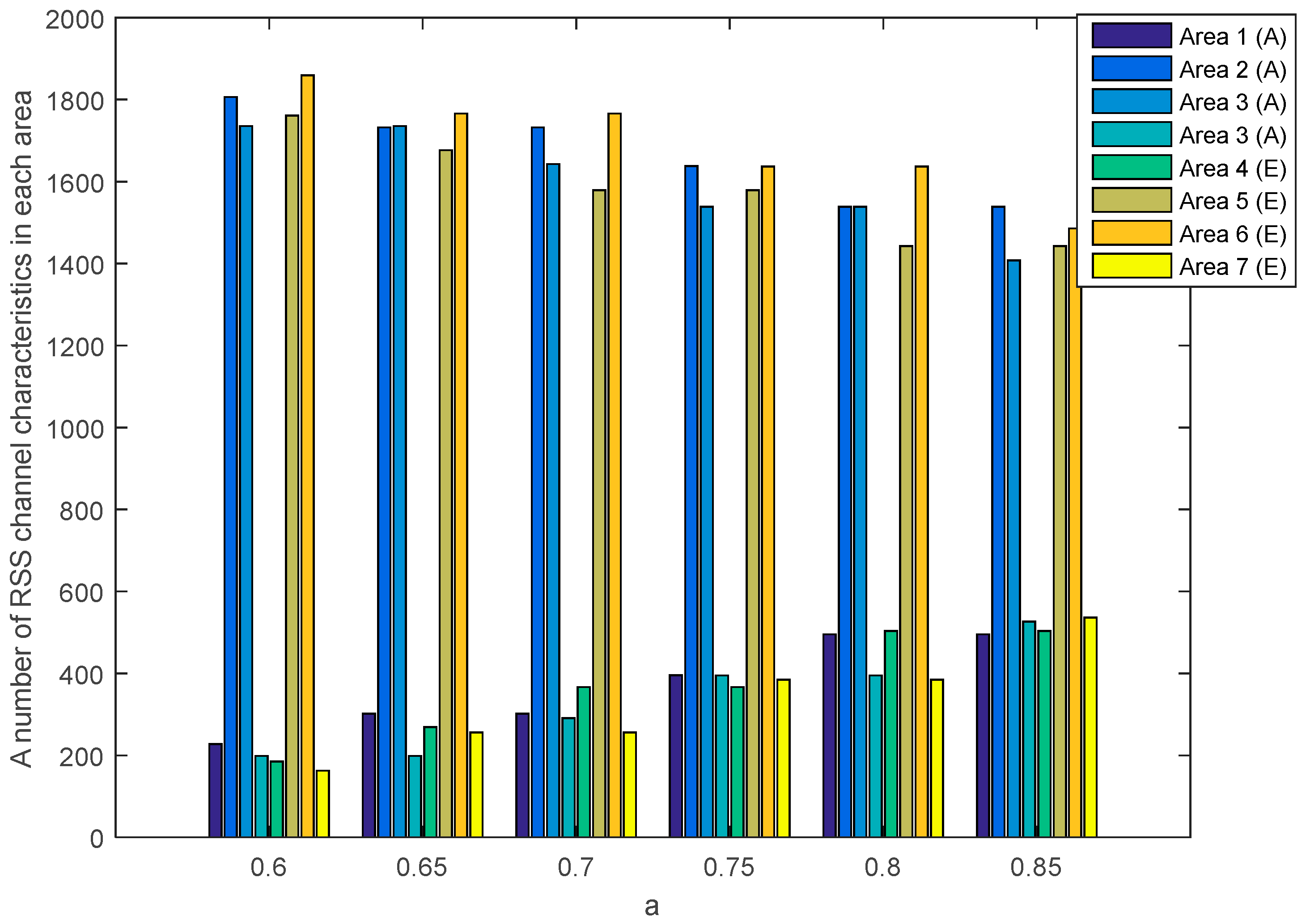
Figure 12 and
Figure 13 show the number of RSS channel characteristics from nodes
and
(node
) and nodes
and
(node
) in each area in the unobstructed scenario. Meanwhile,
Figure 14 and
Figure 15 show the number of RSS channel characteristics from nodes
and
(node
) and nodes
and
(node
) in each area in the obstacles scenario. At the node
, RSS channel characteristics that are processed by the node
is RSS channel characteristics received from the node
. At the node
, RSS channel characteristics that are processed by the node
is RSS received from the node
. From all scenarios, it can be seen that the number of RSS channel characteristics from a node
is mostly in areas 2 and 3 for all values of
. These conditions result in the higher probability of getting three sequential bits i.e., 111 and convert it to 1. However, testing in obstacles scenario results in the possibility of obtaining three sequential bits, i.e., 111 which are higher when compared to unobstructed scenarios because there are more numbers of RSS channel characteristics in areas 2 and 3. These results in the higher keys are produced. The number of RSS channel characteristics from a node
is also mostly in areas 2 and 3 for all values
, but there are significant differences in the number of RSS channel characteristics from area 2 and 3. These results in the lower probability of getting three sequential bits i.e., 111 so fewer keys are produced.
The number of produced 128-bit keys by the unauthorized node and key discrepancy rate (KDIR) between the unauthorized and authorized nodes is shown in
Table 3,
Table 4,
Table 5,
Table 6 and
Table 7. The produced 128-bit keys by the authorized nodes are expressed as Ka (node
) while the produced 128-bit keys by the unauthorized node are expressed as Ke (node
) and Kb (node
). The KDIR value was obtained from the number of discrepancy bits between Ka and Ke with Ka and Kb. To meet security requirements, it is expected that there is no equal 128-bit key obtained by the unauthorized node indicated by the KDIR value above 0. The performed test results in both scenarios indicate less number of produced 128-bit keys by node
compared to the node
. This happens because of the low probability of getting three sequential bits i.e., 111 because of the significant difference in the number of RSS in areas 2 and 3. The fewer three sequential bits produced, the fewer 128-bit keys that can be produced. The test results in unobstructed scenarios also indicate that the higher the value of
, the higher KDIR value between unauthorized and authorized nodes. The high KDIR is caused by the higher variations of the 1 and 0 so as to increase the difference in the produced bits. From the results of testing in the obstacles scenario, there is no significant difference in the KDIR value between the values of
and
. This happens because the number of RSS is almost the same in each area for both
values. Overall, it can be said that the built SSE system has met the security requirements because all KDIR values have exceeded 0. There are no equal keys that were successfully produced by the unauthorized node.
The computation of time testing is conducted by calculating the time needed in the SQ and privacy amplification phase. In the SQ phase, there are two calculated times, i.e., computing time (CT) of multi-bit conversion and the division of bits into several blocks, as well as communication/synchronization time (C/ST) of exchanges of wasted index of blocks to ensure the produced key is absolutely the same as it can eliminate the error-correcting phase. In the privacy amplification phase, there are also two calculated times, i.e., computing time (CT) of increased randomness and the verification mechanism, as well as communication/synchronization time (C/ST) of hash exchanges between the two authorized nodes. Communication overhead testing is conducted by calculating the size of the files sent for synchronization between 2 authorized nodes. Synchronization is conducted after the SQ and the privacy amplification phase.
Table 8 and
Table 9 show the computing time testing to get equal 128-bit keys for each
value in two scenarios while communication overhead testing is shown in
Table 10 and
Table 11. The results of the tests showed no significant computing time differences for each
value in both scenarios, even in the SQ or privacy amplification phases. Computing time differences actually occur between SQ and privacy amplification phases. This happens because the processed data in the SQ phase for each
value is the same channel characteristics measurement data. The processed data in the privacy amplification phase is the remaining of the SQ phase data. Communication/synchronization time testing also showed no significant time difference for each
value in both the SQ and privacy amplification phases. This happens because there is no significant difference between the produced communication overhead.
In this paper, the KSR parameter is obtained by calculating the number of equal key bits during the duration of the SSE system communication. The duration of this system communication includes the measurement of channel characteristics, computing and communication/synchronization time at the synchronized quantization (SQ) phase, as well as computing and communication/synchronization time at the privacy amplification phase. This study carried out testing by varying the parameter of
within 0.6 to 0.85. The varied selection of the value of
is based on the attempt to get the equal 128-bit keys between authorized nodes and ensuring that there are no equal 128-bit keys of the unauthorized node.
Figure 16 shows that the higher the value of
, the lower the generated KSR as there are fewer number of equal 128-bit keys. This happens because there is an increase of 1 and 0 of the produced key bits, thus minimizing the possibility of obtaining an equal key. The results of the performed tests in unobstructed scenarios showed that the highest KSR was obtained at
and
, i.e., 1.05 bps, while the lowest KSR was obtained at
i.e., 0.26 bps. The obtained values indicate that the computing time to get 128-bit keys ranges from 2.03 min to 8.21 min. Meanwhile, the results of the testing carried out in unobstructed scenarios showed that the highest KSR was obtained at
, i.e., 1.05 bps, while the lowest KSR was obtained at
, i.e., 0.26 bps. The obtained values indicate that the computing time to get 128-bit keys ranges from 2.03 min to 8.21 min. Overall, it can be said that the SSE system is able to produce keys below 1 hour to meet the requirements of the update key maximum time proposed by [
44].
Irregularity testing was carried out to ensure that the 128-bit keys of universal hash results met the randomness requirements. In this paper, the authors used the 128-bit keys produced by
. This value is selected because of the higher number of the produced 128-bit keys than the other value in both scenarios. In addition, the security requirements have also been met because there are no equal 128-bit keys produced by the unauthorized nodes. There were 6 randomization tests performed, i.e., frequency test (F), frequency block test (BF), runs test (R), a long run of ones in the block (LROB), approximate entropy test (AP), and cumulative sums test (CS). Each test result will produce a
value which is the randomness probability value of 128-bit keys (0
value
). The closer to 1, the more random the 128-bit keys are produced. In order to fulfill the randomization requirements, the minimum
value of the 128-bit keys is 0.01. The details of the usability of each test are explained as follows. The F test is used to determine the ratio of 0 and 1 of 128 key bits. The BF test aims to discover the ratio of 1 of each block in the 128-bit keys. The determination of whether fluctuations 0 or 1 in a 128-bit key is too fast or slow can be known by R tests, while the determination of whether fluctuations of 0 or 1 of each block in a 128-bit key is too fast or slow can be known with the LROB test. The AP test is used to determine the frequency of all possible intersection bits of each block in the 128-bit keys. Meanwhile, the CS test is used to specify that the accumulative number of the 128 key bits tested is too large or too small for the accumulative sum of the random sequence.
Table 12 shows the results of the NIST test in the unobstructed and obstacles scenario. In both scenarios, it appears that all the produced keys have met the randomness requirements for 6 tests because the resulting
value has exceeded the specified standard, i.e., 0.01. The ranking of keys to be selected on the SSE system is Ka-4, Ka-1, Ka-2, and Ka-3. The selection of this ranking is based on the results of the AP test. If Ka-4 fails to be used as a key in the verification phase, then Ka-1 will be used as such a key. The highest
value of the AP tests is 0.9484 (unobstructed scenarios) and 0.9403 (obstacles scenario). This shows that K-4 obtained during the obstacles scenario has a higher persistence bit compared to K-4 obtained when in the unobstructed scenario.
5.2.3. Comparison of Performance between SSE Systems and Existing Key Generation Systems
There are two performance parameters, i.e., computing time and the communication overhead, that are used to compare SSE systems with previous key generation systems that are also implemented on IoT devices with limited power and computing. The selection of these parameters is based on the consideration of obtaining an efficient key generation system in terms of computing time and the communication overhead. The lower the computing time and the communication overhead required, the more efficient the built key generation system. There are 4 existing key generation systems that will be used for comparison, i.e., system [
9,
31,
33,
46,
48]. The system [
9] uses four phases where the RSS channel characteristics will be quantized using the cumulative distribution function (CDF) method. The system [
31] uses five phases where the RSS channel characteristics will be divided into several blocks, each containing 50 data. Each block will be pre-processed using the Kalman method and the results will be converted into multi-bits with the quantization method proposed by [
24]. The system [
33] uses five phases in building a key generation system. The RSS channel characteristics will be pre-processed using a third order polynomial regression. The results of the signal pre-process phase will be divided into several blocks, each containing 250 bits. Each block will be converted into multi-bit with the quantization method proposed by [
24]. The system [
47] works by signal pre-processing the RSS channel characteristics using the discrete cosine transform (DCT) method. The results of the pre-process will be quantized using several parameters which include the mean and standard deviation. The system [
48] works using 4 phases where the RSS channel characteristics will be divided into several blocks, each containing 128 bits. Each block will be converted into multi-bit with the quantization method proposed by [
38]. All of the existing key generation systems still require an error-correcting phase to correct the different bits produced by the authorized nodes. In this paper, the error-correcting method used is BCH (255, 87), while privacy amplification uses the Universal Hash and SHA-1 methods.
Computing time system testing in both scenarios is divided into two parts, i.e., parts A and B. In the SSE system, part A consists of the SQ phase while part B consists of the privacy amplification phase. In the existing key generation system, part A consists of a signal pre-processing phase to the error-correcting phase, while part B consists of privacy amplification. Each part will be divided into two, i.e., computing time (CT) and communication/synchronization time (C/ST).
Table 13 shows a comparison of computing time between the SSE and the existing system. The results of the performed tests indicate that the SSE system is able to reduce computing time (CT) of part A to 25.77 times (unobstructed scenarios) and 26.08 times (obstacles scenario) compared to existing systems. The decrease in communication/synchronization time (C/ST) reaches 1.55 times (unobstructed scenarios) and 1.52 times (obstacles scenario). The test results of part B also show that SSE systems are able to reduce computing time (CT) to 2.60 times (unobstructed scenario) and 2.47 times (obstacles scenario) compared to existing systems. There is no significant communication/synchronization (C/ST) time difference of part B between SSE and the existing systems because the produced communication overhead is almost the same. Overall, it can be seen that the computing time (CT) and communication/synchronization (C/ST) time of the SSE system are lower than the existing system. This happens because, in part A, the multi-bit conversion of the SSE system is conducted directly from the RSS channel characteristics without going through the signal pre-processing phase. Further, there is no blocking division in processing RSS channel characteristics so it speeds up computing time compared to existing systems. The high computing time of existing systems is due to the error-correcting phase. The more data proceeded at this phase, the higher the computing time, communication/synchronization time and communication overhead required.
Table 14 shows a comparison of the communication overhead between the SSE system and existing systems. The communication overhead is calculated from the size of the file sent for synchronizing the authorized nodes. In the SSE system, the data synchronization occurs after the SQ and privacy amplification phase, whereas in existing systems, the data synchronization occurs after the error-correcting and privacy amplification phase. The results of the performed tests indicate that the SSE systems can reduce the communication overhead from part A to 2.75 times (unobstructed scenario) and 2.92 times (obstacles scenario) compared to existing systems. There is no significant communication overhead difference of part B between SSE and the existing systems because of produced the communication overhead is almost the same. This happens because synchronization after the SQ phase is only conducted on the index of the wasted data block, while synchronization after the error-correcting phase is carried out on the parity bit to increase the size of the communication overhead. Overall, the results of the tests conducted indicate that SSE systems are able to reduce computing time, communication/synchronization time and the communication overhead compared to existing systems. Therefore, it can be said that the SSE system is more efficient for implementation of IoT devices with limited resources compared to existing systems.