A Plug-and-Play Human-Centered Virtual TEDS Architecture for the Web of Things
Abstract
1. Introduction
- There is a lack of spread of solutions that provide plug-and-play mechanisms at the sensor node layer.
- There is a need for standards to enable the interoperability between sensors of different manufacturers or that make use of diverse communication technologies.
- There is a need for human-centered tools to configure motes dynamically in order to reduce the development time, even allowing the DIY community to implement IoT applications with little or no knowledge about electronics or programming.
- There is a need for lightweight protocols that enable mechanisms of detection and self-registration for the communications performed between a mote and a gateway, between a gateway and a cloud, and between a mote and a cloud.
- An architecture based on the IEEE 21451 standard that proposes different modifications related to the concept of Virtual Transducer Electronic Data Sheets (VTEDS) is presented. The proposed system allows for providing plug-and-play mechanisms at the sensor layer of an IoT ecosystem.
- A web application with an intuitive graphic interface that allows for monitoring, controlling, and managing all the sensors and the communications architecture is also presented.
- The proposed system is evaluated empirically in diverse real scenarios. The performed experiments make use of different sensor nodes in order to show that the designed architecture is very fast when deploying sensors and exchanging data.
2. Related Work
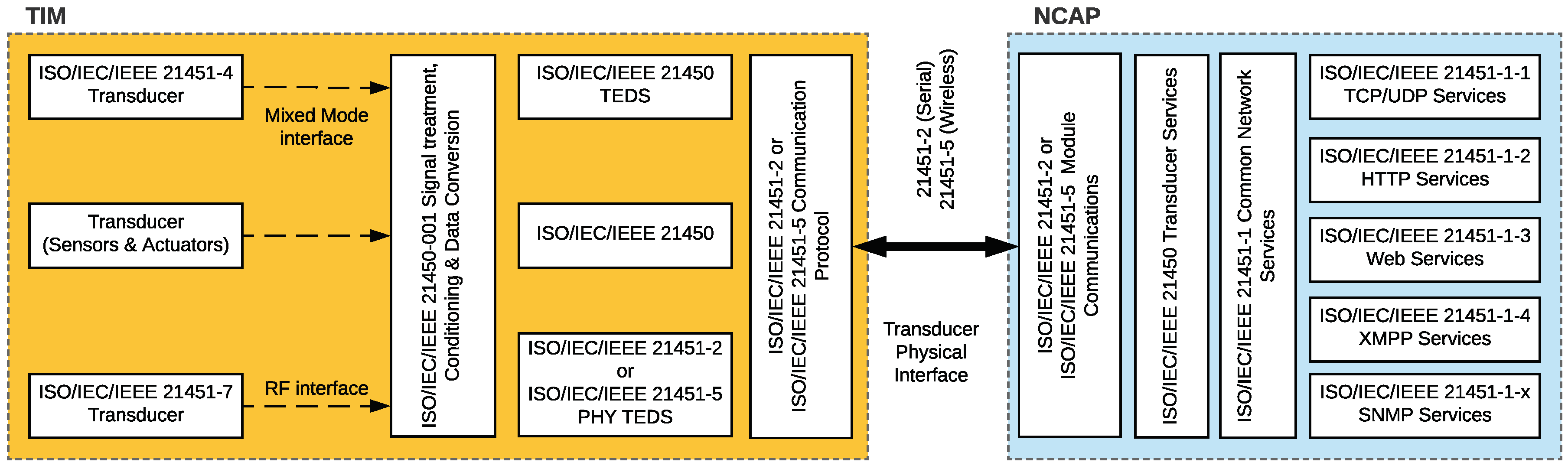
2.1. About ISO/IEC/IEEE 21451
- There should be standard physical and electrical connections between an NCAP and its transducers.
- The NCAP should be able to diagnose the state of a transducer.
- It should be possible for the NCAP to detect and identify a new transducer.
2.1.1. Previous IEEE 21451 Implementations
2.2. OGC Standards
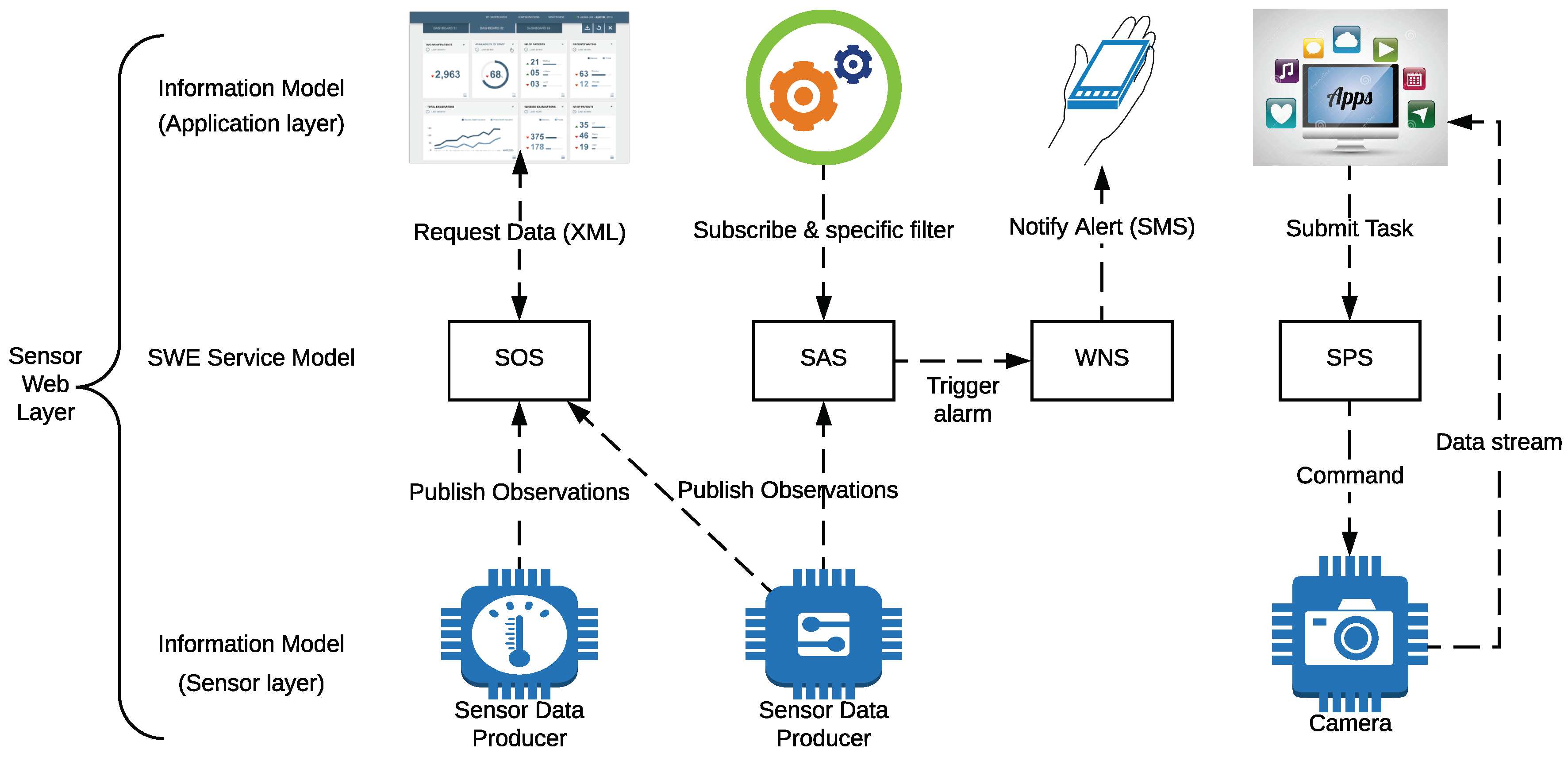
2.2.1. OGC-Sensor Web Enablement Framework
- Observations & Measurements Schema (O&M): it defines a scheme for encoding sensor data.
- Sensor Model Language (SensorML) and Transducer Markup Language (Transducer ML or TML): they allow for describing sensors.
- Sensor Observations Service (SOS) and Sensor Planning Service (SPS): they provide the link between the user and the measurements of the sensors.
- Sensor Alert Service (SAS): it defines the publish and subscribe scheme to send sensor alerts.
- Web Notification Services (WNS): it allows for delivering messages or alerts from SAS and SPS to users.
2.2.2. OGC-SensorML
2.2.3. OGC-PUCK Protocol
2.2.4. OGC-Plug-and-Work Mechanism
2.3. Other Initiatives for Providing Plug-and-Play and Interoperability
2.4. Analysis of the Related Work
3. Plug-and-Play Architecture Based on Virtual TEDS
3.1. Global Overview
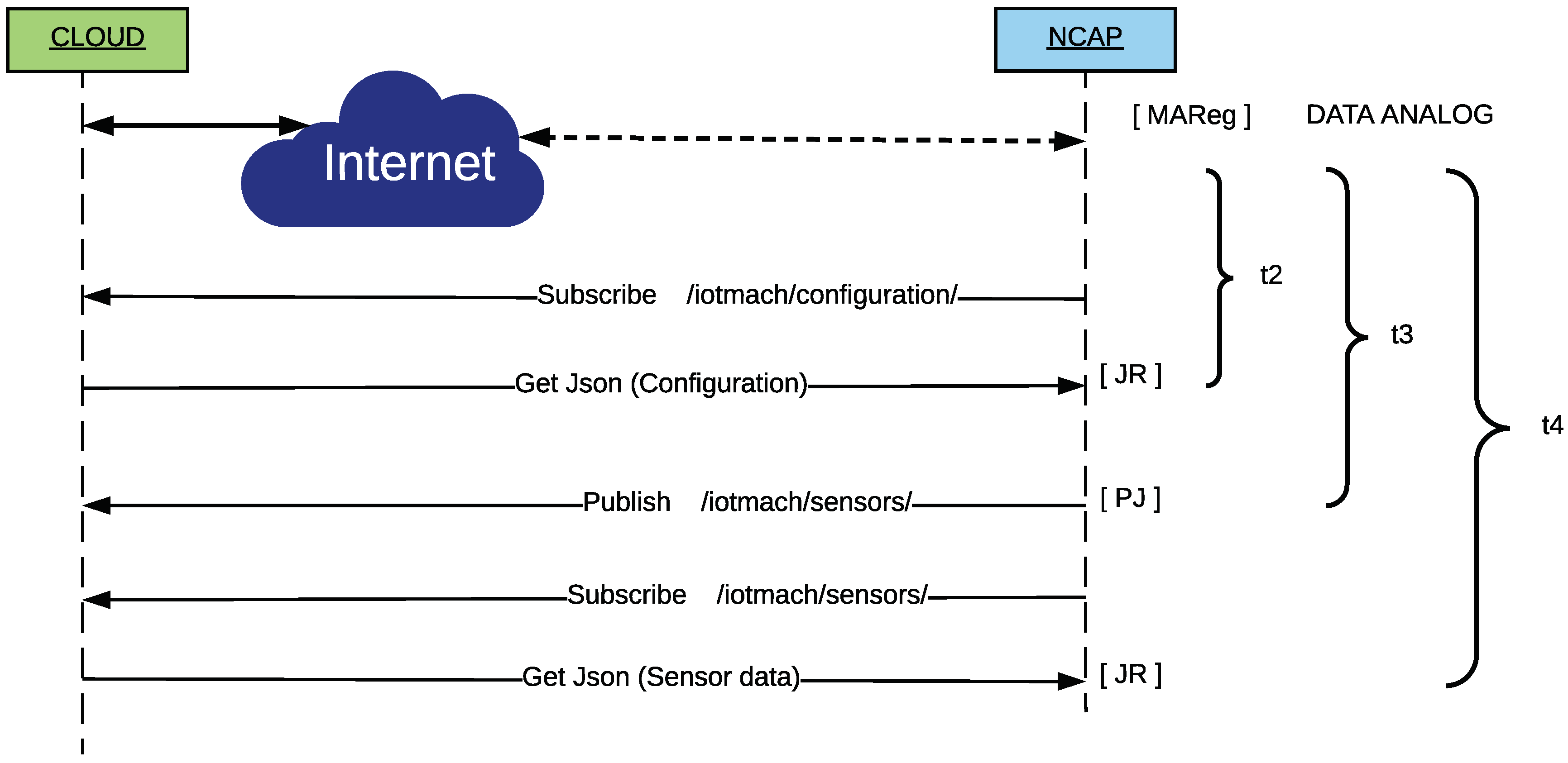
3.2. Messaging System and Communication Protocols
- They can be embedded into Bluetooth Low Energy (BLE) beacons.
- They can send data collected from beacon sensors and receive commands for actuators.
- The LP4S family of protocols requires little memory and CPU usage, which allows it to be implemented in low-resource devices. The protocols also reduce communication time, thus decreasing power consumption. For instance, the LP4S protocols were tested with Generic Attribute Profile (GATT)-based beacons, yielding a power consumption of only 35 A in standby mode (before connecting to other devices) and an average of 575 A when one or more users connected occasionally to the mote. In the case of the LP4S-6 protocol, it was tested on an Eddystone beacon with 100 ms to 5 s beaconing intervals, obtaining power consumptions between 125 and 865 A, which suggests that such a protocol may be used in scenarios where low-energy consumption is essential.
3.3. Plug-and-Play Mechanism
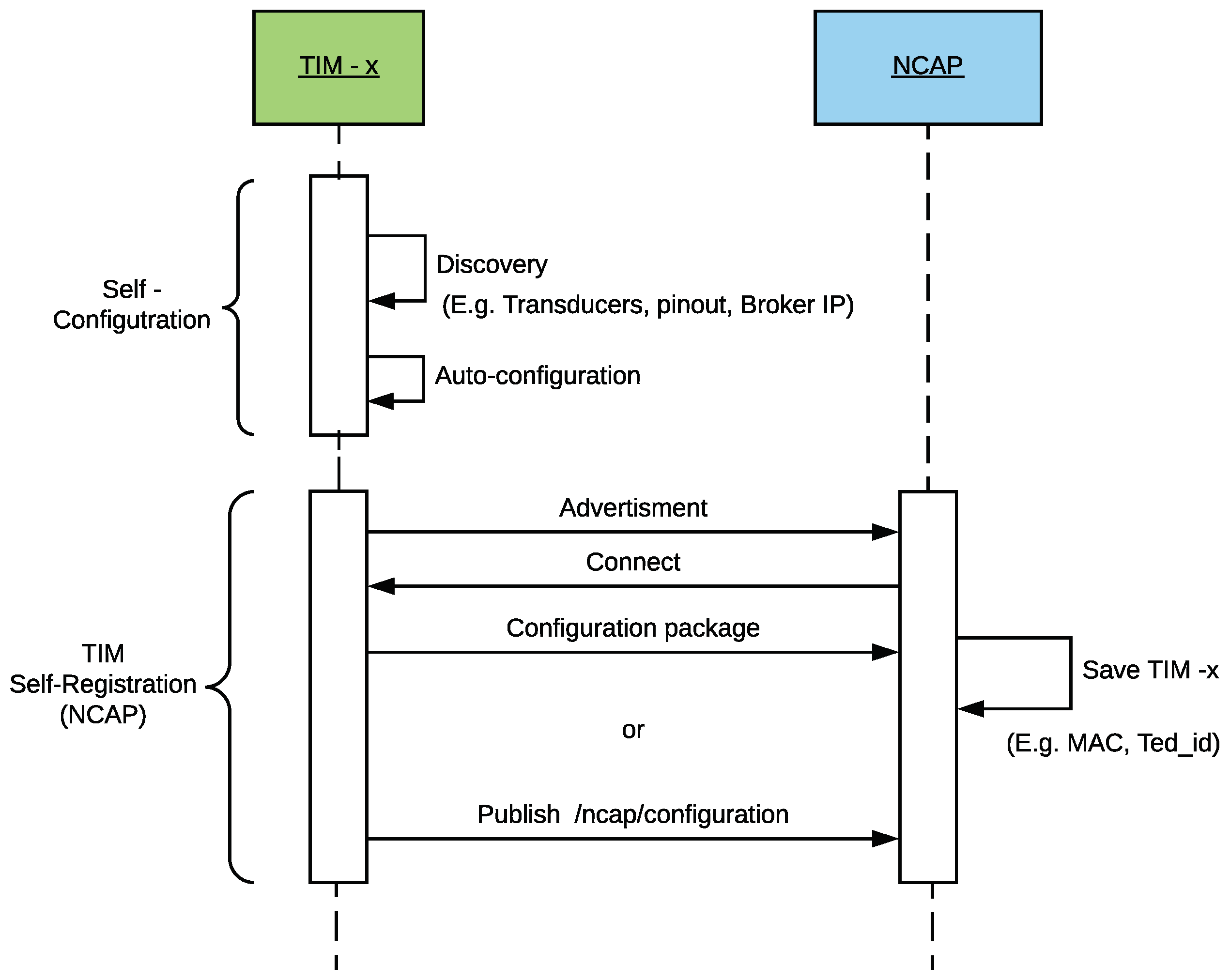
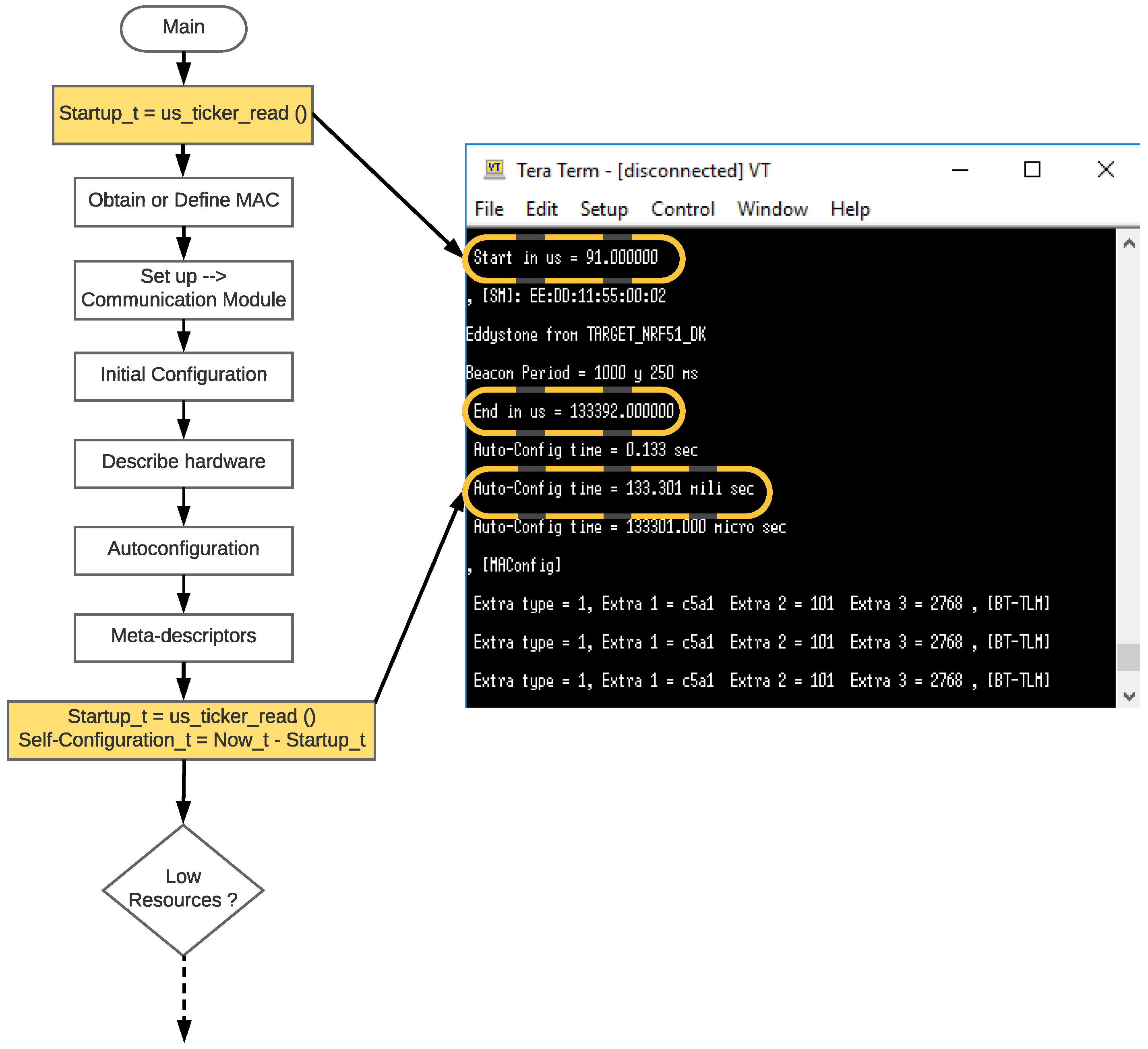
3.3.1. Auto-Configuration and Self-Registration at the NCAP and TIM Layers
3.3.2. Self-Registration and Auto-Calibration at the Cloud Layer
3.4. Metadata of a Sensor Node
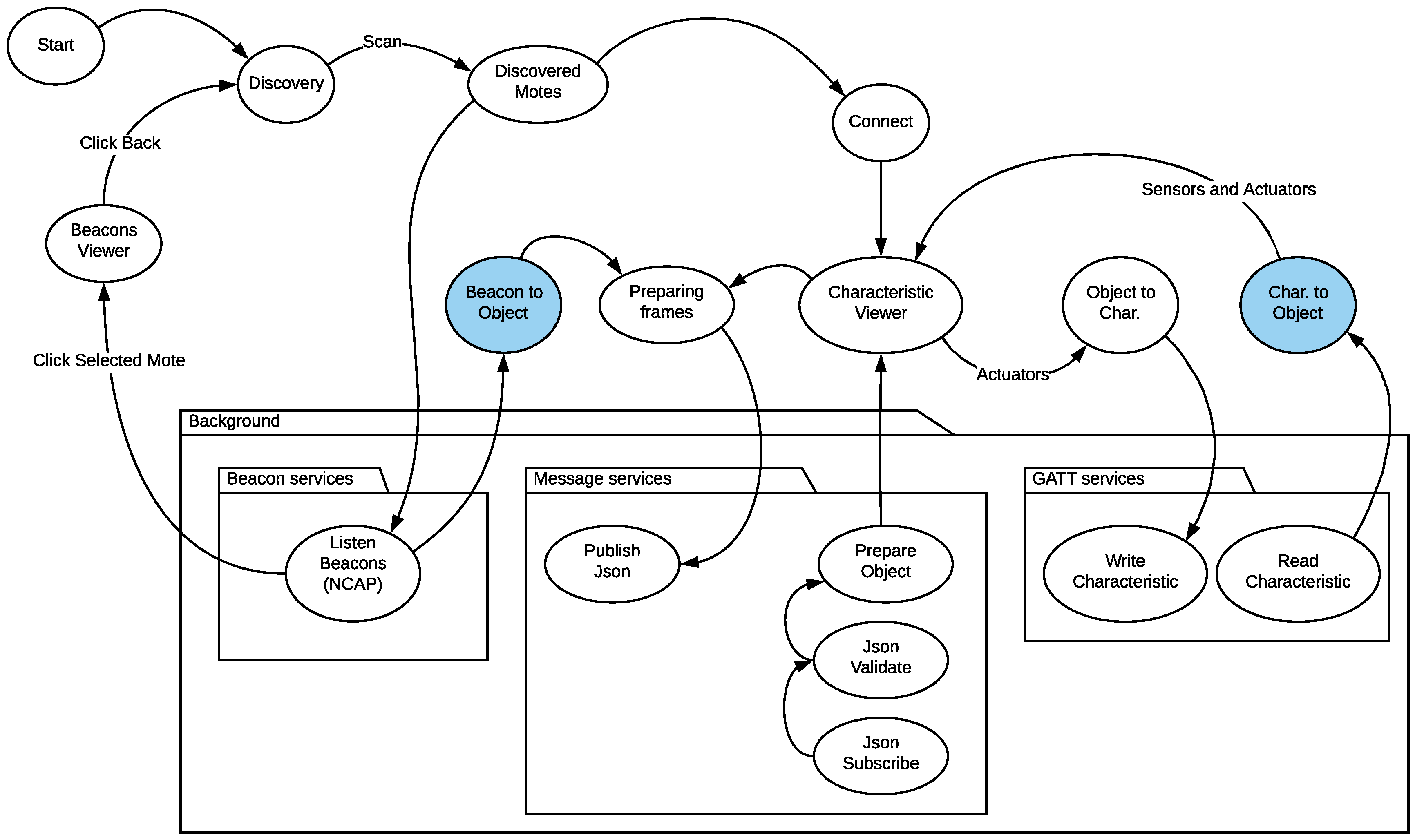
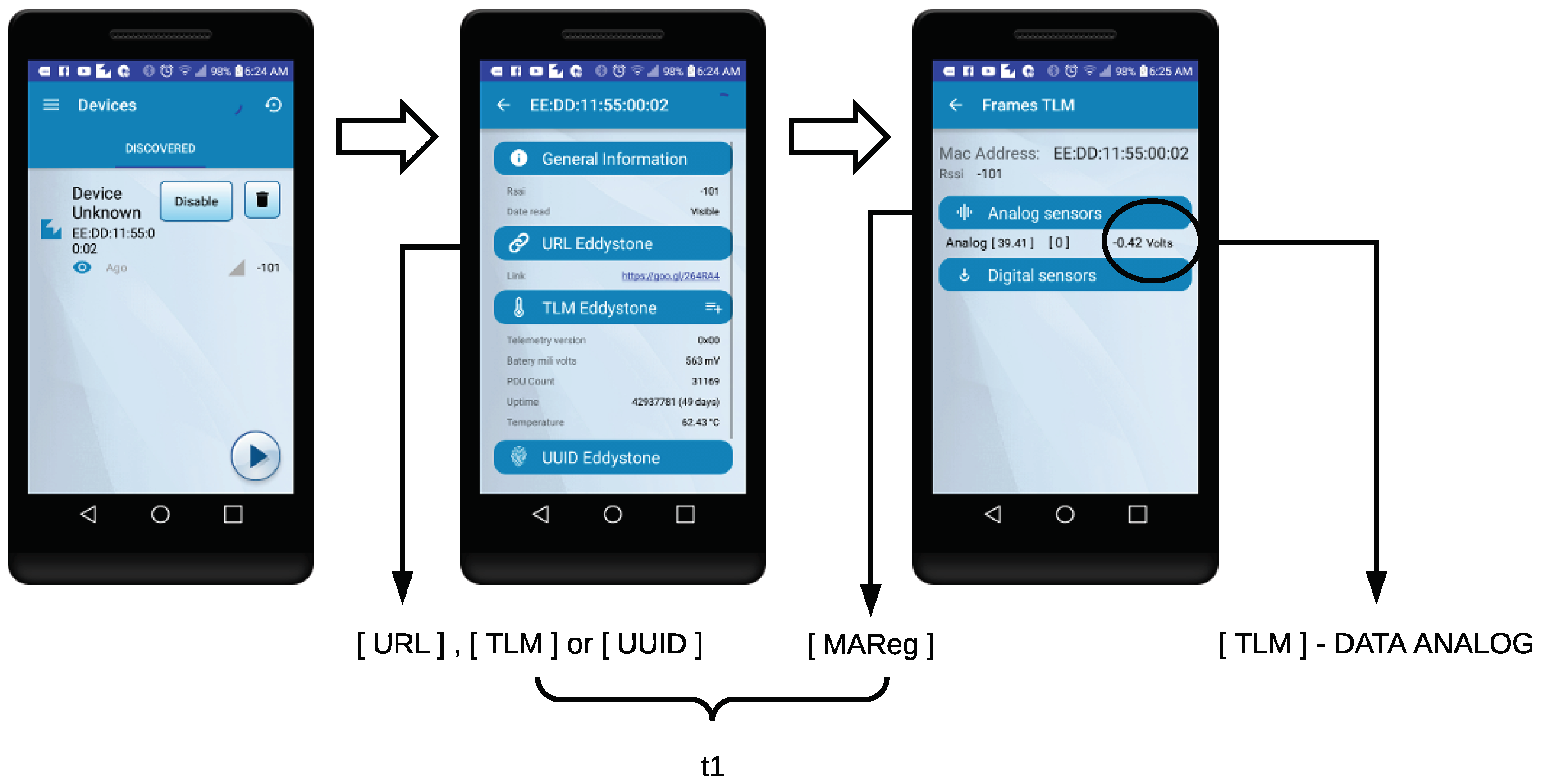
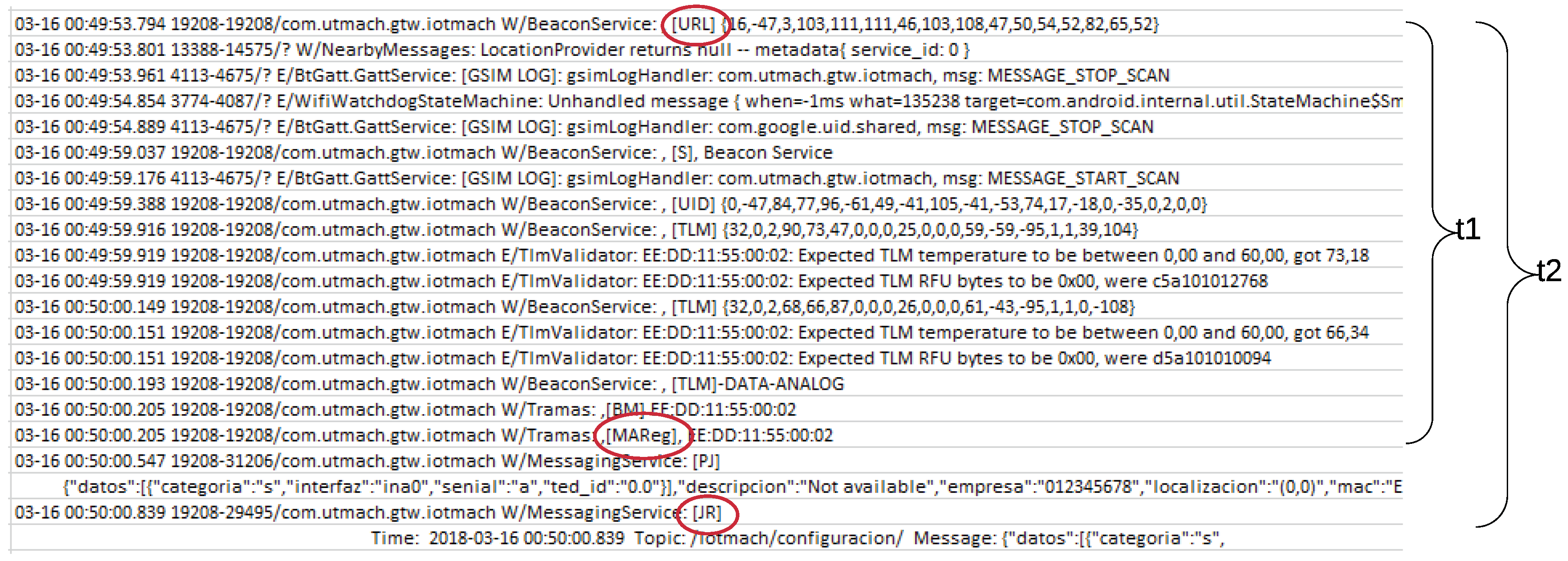
3.5. Sensor and Actuator Data Flow
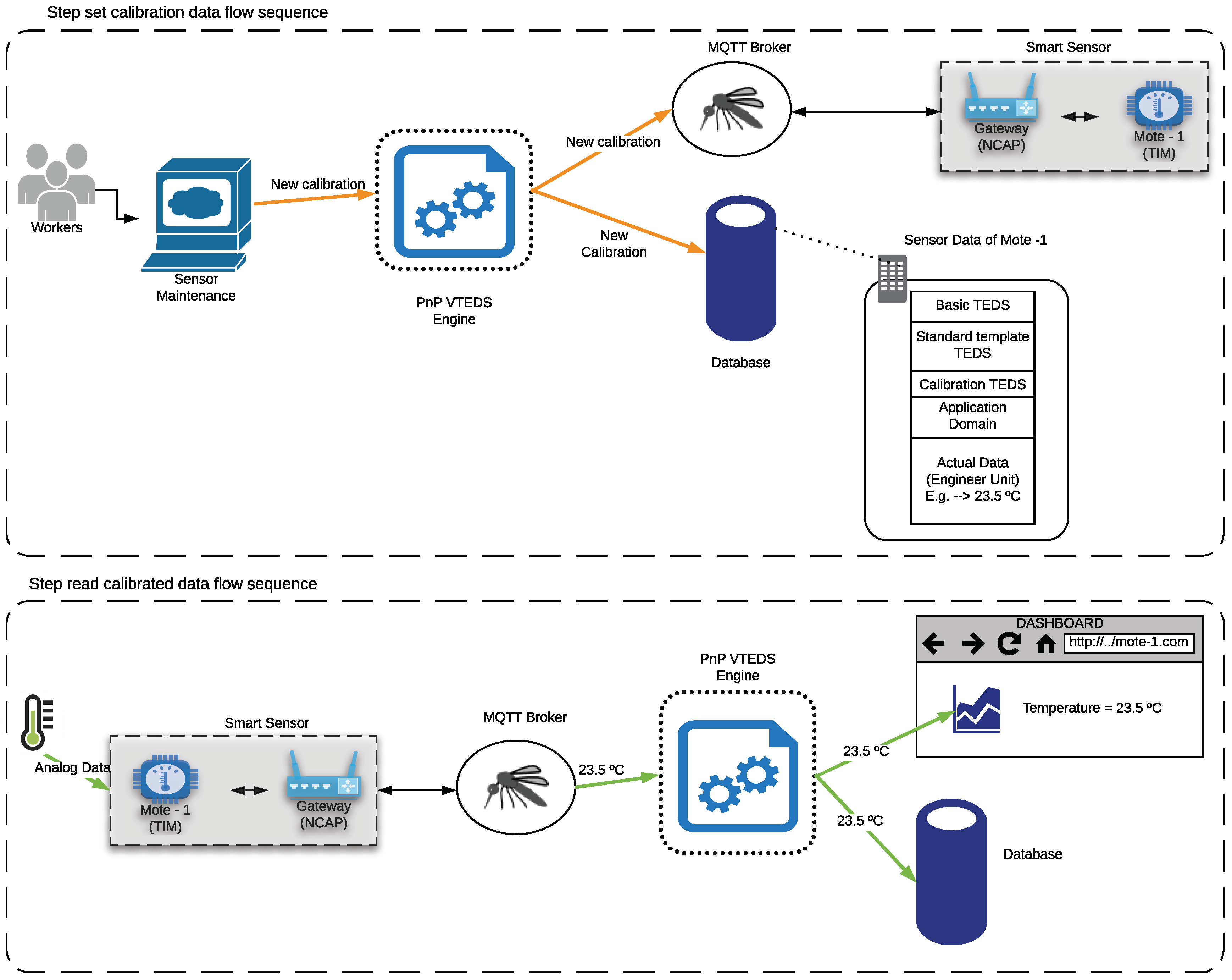
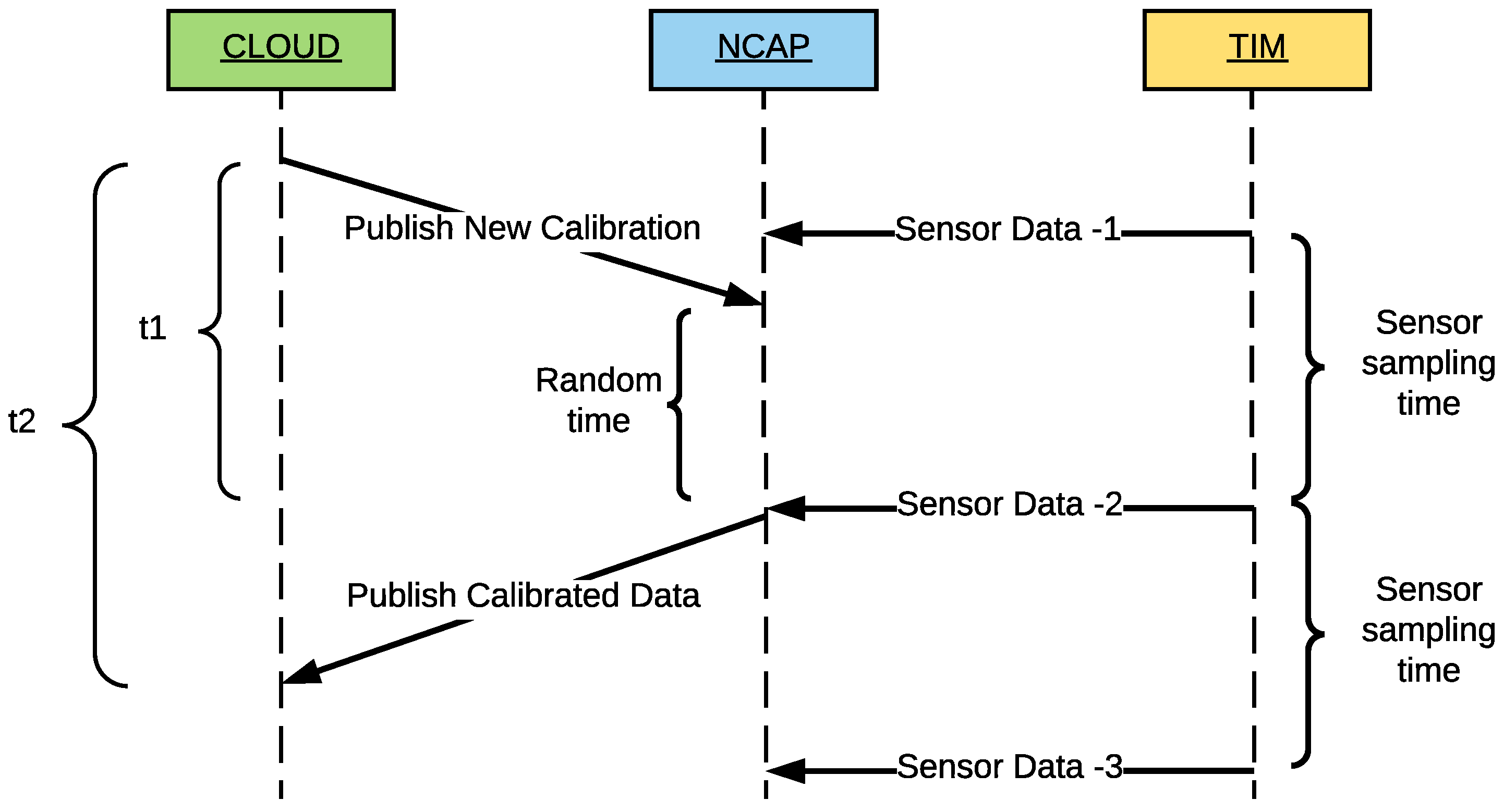
3.6. Calibration Data Flow
4. Implementation of the Architecture
4.1. The TIM Layer
4.2. The NCAP Layer
4.3. The Cloud Layer
4.3.1. TED Management
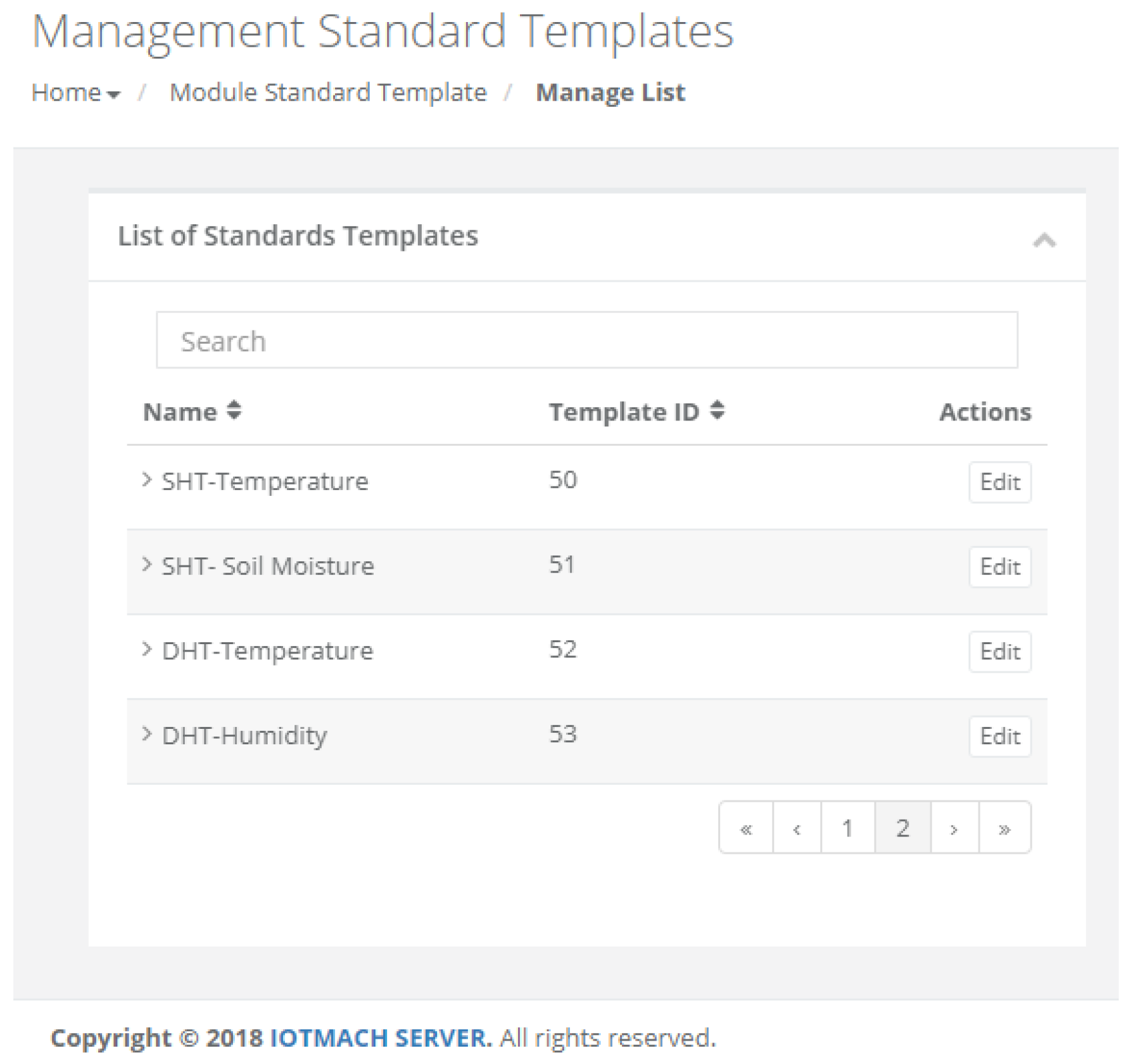
- Standard template. Figure 16 shows the interface that is used to manage the IEEE 21451 standard templates. Such an interface allows the user to add new templates depending on his/her needs.
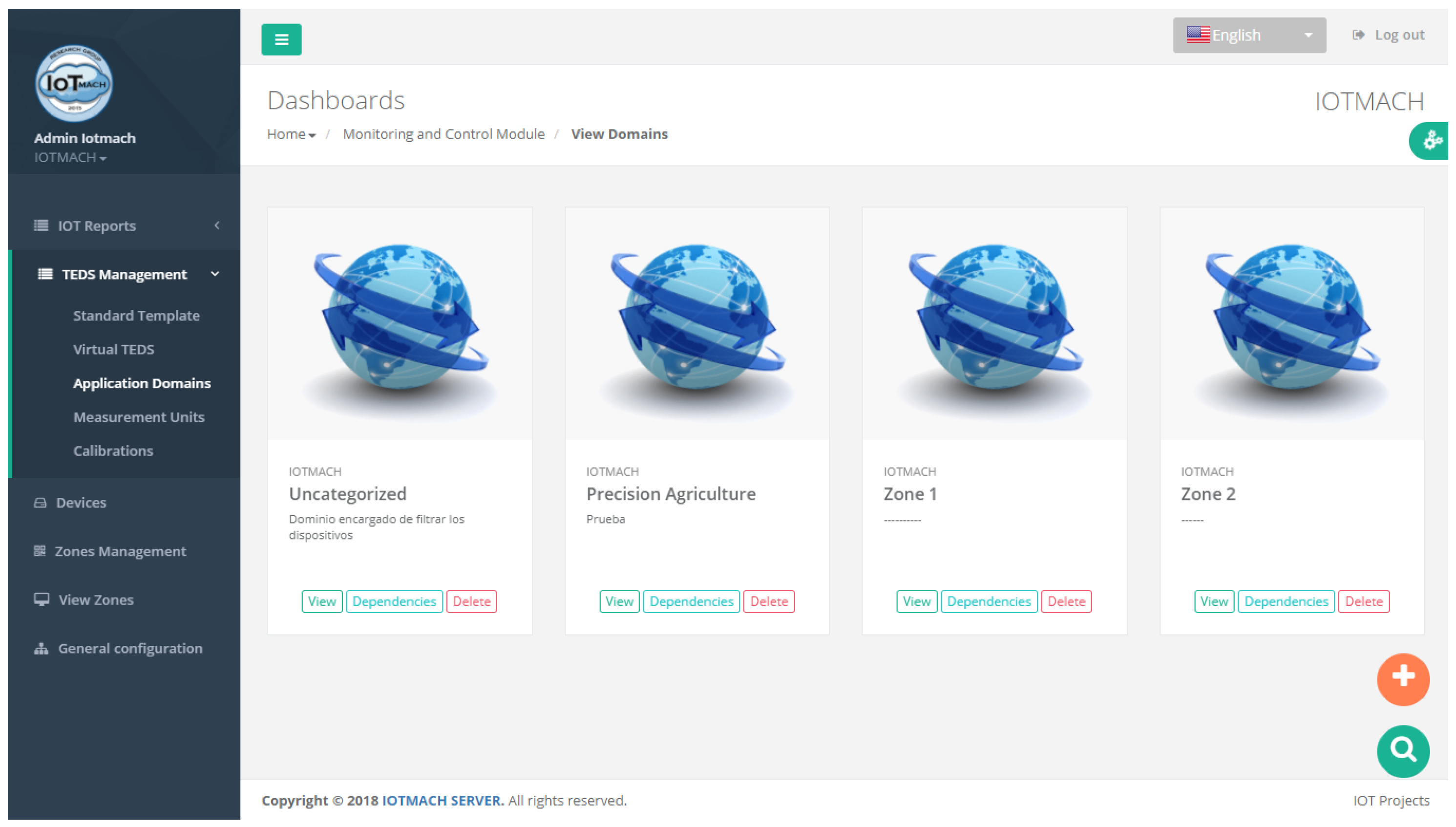
- Application domains. Figure 18 shows the web menu available to create the different application domains manually. The menu also shows the application domains discovered through the TIM configuration frames during the process of self-registration in the cloud.
- Units of measure. Figure 19 shows the menu to manage all types of units of measurement that are necessary for the sensors and actuators available.
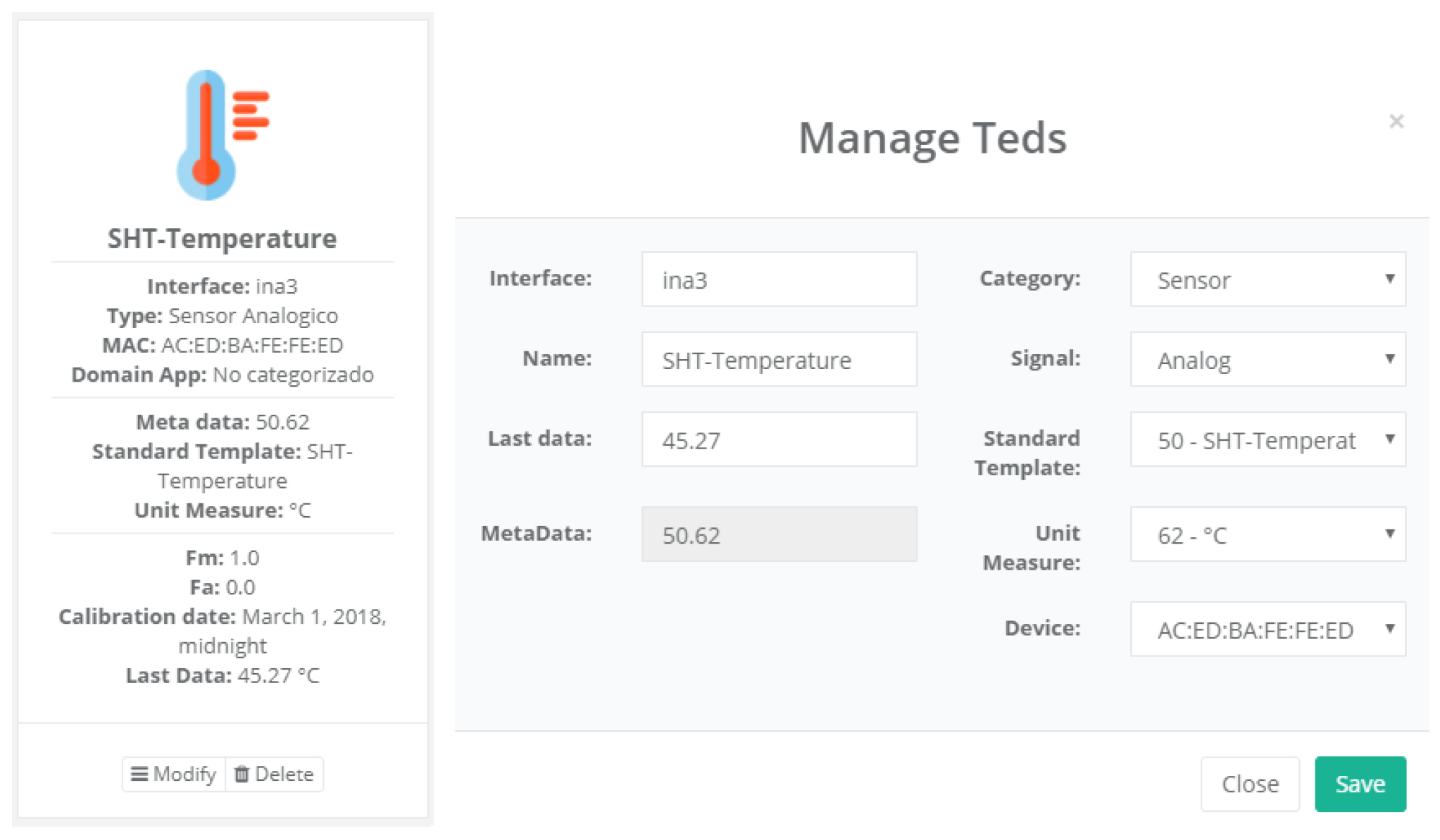
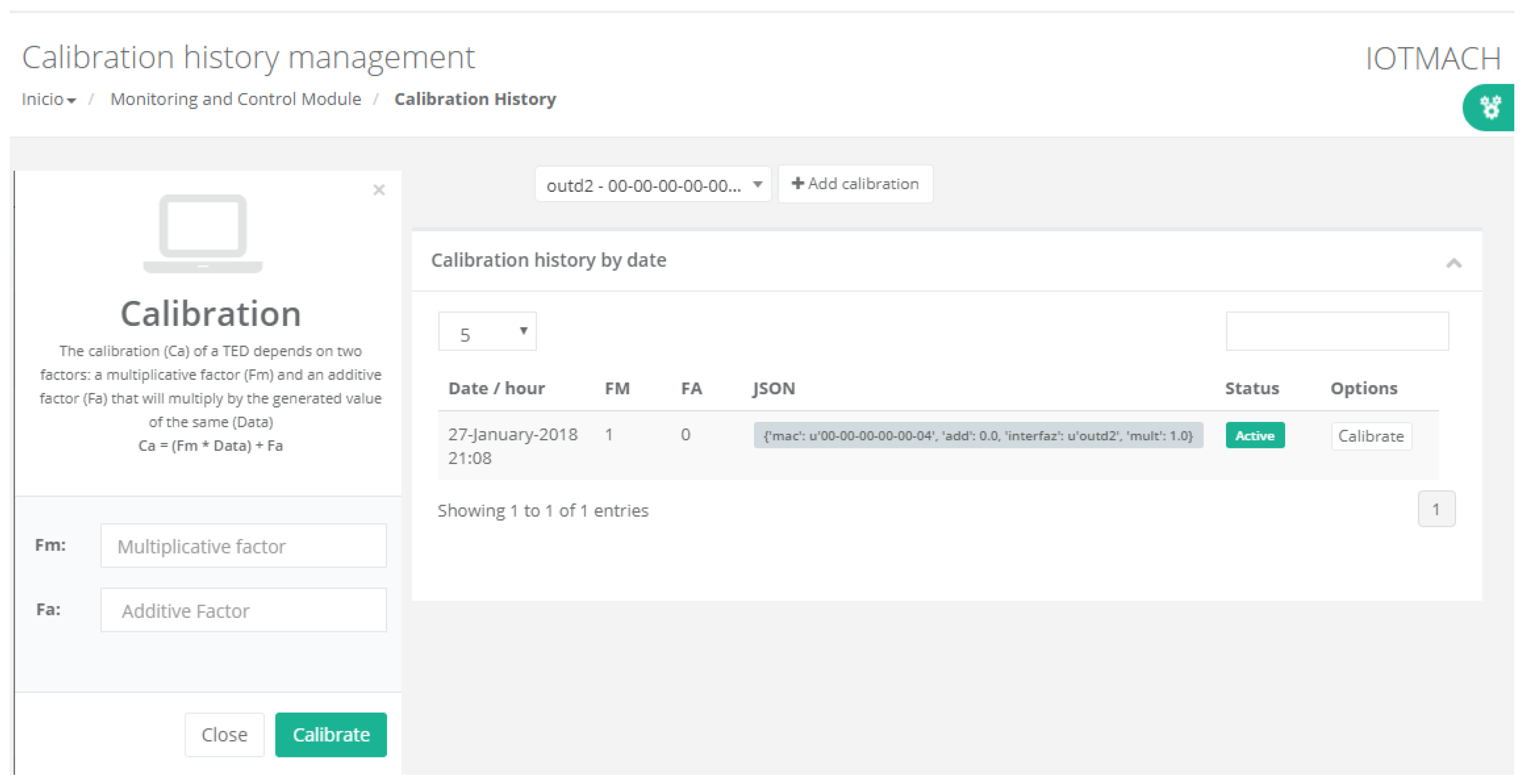
- Calibration. The calibration of the sensors and actuators in the architecture occurs dynamically, as explained in Section 3.3.2. Figure 20 shows the interface through which a maintenance technician can add new configuration parameters of one of the discovered sensors. Once the calibration button is clicked, the system sends an MQTT message with the necessary information, which is consumed by the corresponding NCAP. In addition, from this interface, the user can access historical calibrations and send again such previous parameters to a sensor.
- Device management. All the sensor nodes discovered by the cloud, from the moment they perform the auto-registration process, are listed in the menu shown in Figure 21. Once they are detected by the cloud, they can be edited manually.
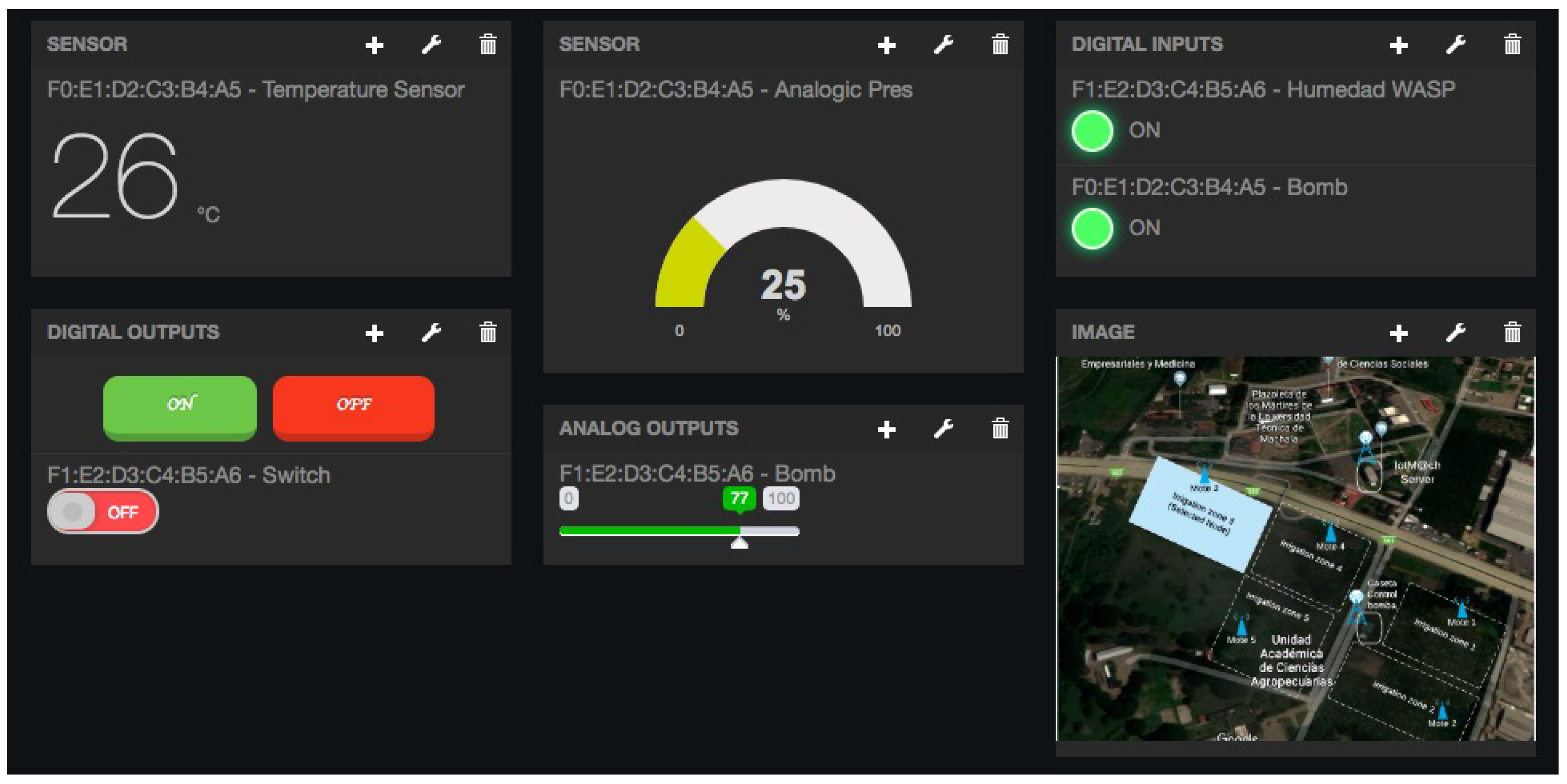
- Dashboard management. The implemented system is able to generate dashboards dynamically. Thus, the web application allows the user to customize the information to be displayed on the screen, which makes it possible to show together all the available information of different sensors, even the ones of different TIMs. This is performed through the interface shown in Figure 22, which can manage different display areas and choose the sensors and actuators listed in the device management menu. Figure 23 shows an example of a dashboard generated dynamically with real-time information.
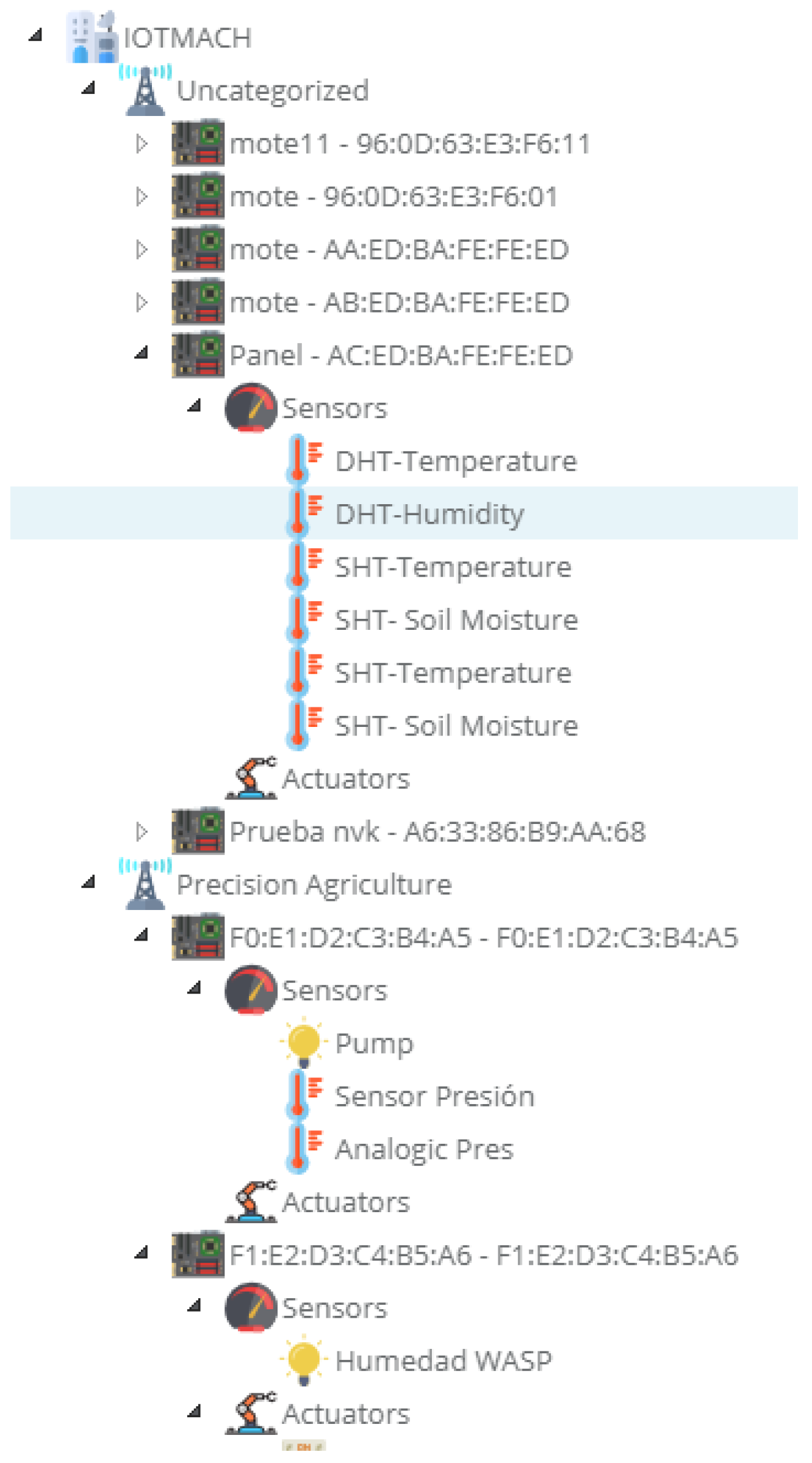
- General view. For a better visualization and management of all the elements discovered dynamically in the cloud, there is a structure in the form of drop-down tree (in Figure 24) that allows immediate access to the required information.
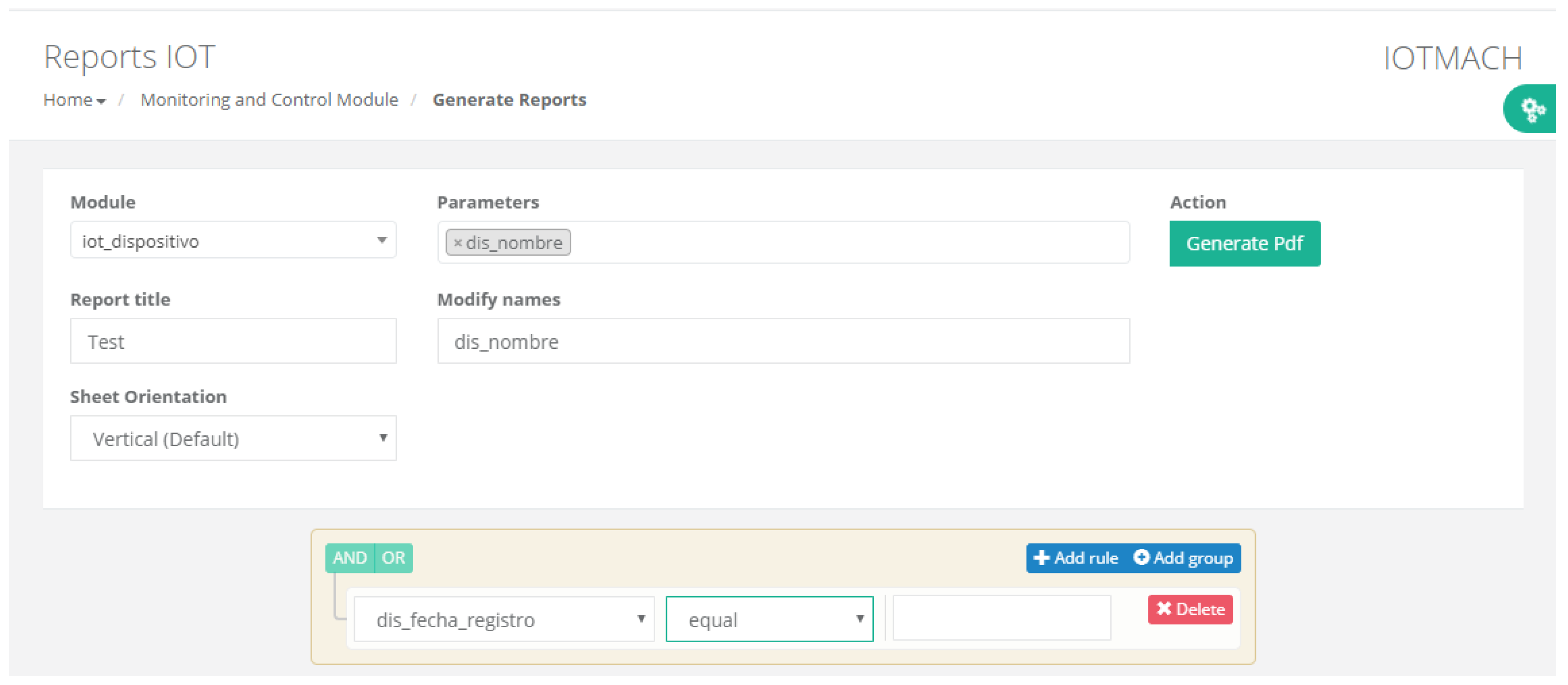
- Report management. The system also provides an interface to generate reports from the information stored in the database. Figure 25 shows the interface that allows the user to customize the desired information for the report to be generated.
5. Experiments
5.1. Experimental Setup
5.2. Self-Configuration Latency
- The TIMs use different hardware. Both TIMs use RISC processors that operate at 16 MHz, but the TIM nrf51422 [89] has slightly more resources than the Arduino Mega, since it is based on the ARM Cortex M0 [90] (32-bit CPU and 16 kB RAM), while the ATmega2560 [91] is based on an 8-bit AVR microcontroller with 8 kB SRAM.
- Each TIM makes use of a different development platform. On the one hand, in the case of the BLE TIMs, they were both programmed with Mbed, which is a platform for managing ARM-based IoT nodes that optimizes the firmware for devices with constraint hardware resources. On the other hand, Arduino is a development platform that includes an abstraction layer that allows for simpler and more intuitive programming, even for those who have no experience in IoT, but at the cost of optimizing the managed resources, which impacts configuration latencies and the amount of used program memory.
- The use of the Ethernet shield requires a serial connection with the CPU, which slows the discovery of the Ethernet module.
5.3. Self-Registration and Telemetry Latencies
5.4. Auto-Calibration with the Ethernet TIM
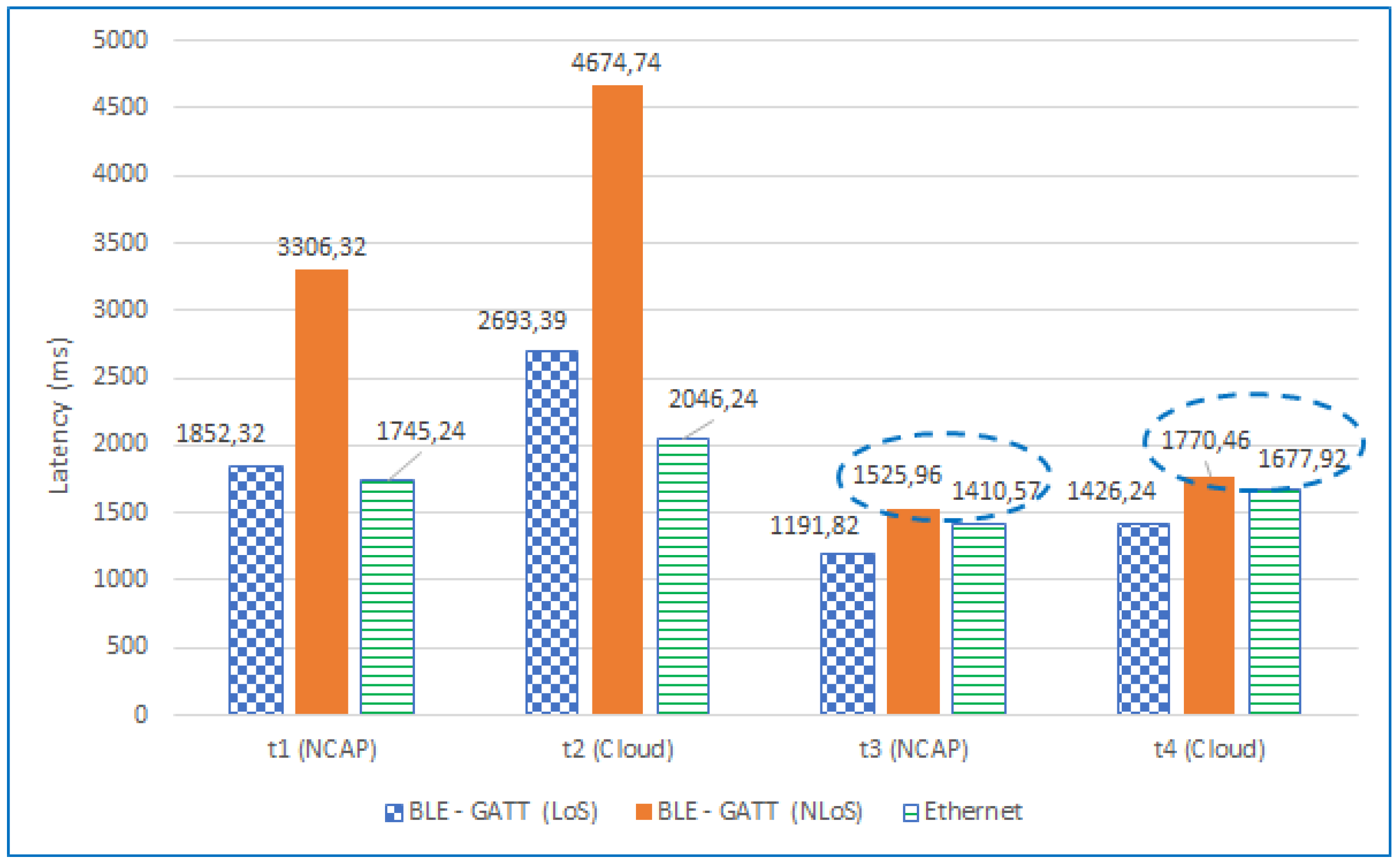
5.5. Self-Registration and Telemetry Latencies Without Line-of-Sight
5.6. Analysis of the Results
6. Conclusions
Author Contributions
Funding
Conflicts of Interest
Abbreviations
| AMQP | Advanced Message Queuing Protocol |
| API | Application Programming Interface |
| BLE | Bluetooth Low Energy |
| DIY | Do It Yourself |
| EEPROM | Electrically Erasable Programmable Read-Only Memory |
| GATT | Generic Attribute Profile |
| HAS | Home Automation System |
| IDE | Integrated Development Environment |
| IoT | Internet of Things |
| ISR | Interrupt Service Routine |
| JMS | Java Messaging Service |
| LP4S | Lightweight Protocol for Sensors |
| MQTT | Message Queuing Telemetry Transport |
| NCAP | Network Capable Application Processor |
| OGC | Open Geospatial Consortium |
| QoS | Quality of Service |
| REST | REpresentational State Transfer |
| RPC | Remote Procedure Call |
| SBC | Single-Board Computer |
| SoC | System-on-a-Chip |
| SWE | Sensor Web Enablement |
| TIM | Transducer Interface Module |
| TED | Transducer Electronic Data Sheet |
| VTEDS | Virtual TEDS |
| WoT | Web of Things |
| WSN | Wireless Sensor Network |
| XMPP | eXtensible Messaging and Presence Protocol |
References
- Leading the IoT. Gartner Insights on How to Lead in a Connected World (2017). Available online: https://www.gartner.com/imagesrv/books/iot/iotEbook_digital.pdf (accessed on 25 May 2018).
- Suárez-Albela, M.; Fernández-Caramés, T.M.; Fraga-Lamas, P.; Castedo, L. A Practical Evaluation of a High-Security Energy-Efficient Gateway for IoT Fog Computing Applications. Sensors 2017, 17, 1978. [Google Scholar] [CrossRef] [PubMed]
- Robert, J.; Kubler, S.; Kolbe, N.; Cerioni, A.; Gastaud, E.; Främling, K. Open IoT Ecosystem for Enhanced Interoperability in Smart Cities—Example of Métropole De Lyon. Sensors 2017, 17, 2829. [Google Scholar] [CrossRef] [PubMed]
- Fernández-Caramés, T. An Intelligent Power Outlet System for the Smart Home of the Internet of Things. Int. J. Distrib. Sens. Netw. 2015, 11, 214805. [Google Scholar] [CrossRef] [PubMed]
- Blanco-Novoa, O.; Fernández-Caramés, T.M.; Fraga-Lamas, P.; Castedo, L. An Electricity-Price Aware Open-Source Smart Socket for the Internet of Energy. Sensors 2017, 17, 643. [Google Scholar] [CrossRef] [PubMed]
- Rodrigues, J.J.P.C.; De Rezende Segundo, D.B.; Arantes Junqueira, H.; Sabino, M.H.; Prince, R.; Al-Muhtadi, J.; De Albuquerque, V.H.C. Enabling Technologies for the Internet of Health Things. IEEE Access 2018, 6, 13129–13141. [Google Scholar] [CrossRef]
- Fraga-Lamas, P.; Fernández-Caramés, T.M.; Castedo, L. Towards the Internet of Smart Trains: A Review on Industrial IoT-Connected Railways. Sensors 2017, 17, 1457. [Google Scholar] [CrossRef] [PubMed]
- Fraga-Lamas, P.; Fernández-Caramés, T.M. Reverse Engineering the Communications Protocol of an RFID Public Transportation Card. In Proceedings of the 2017 IEEE International Conference on RFID (RFID), Phoenix, AZ, USA, 9–11 May 2017; pp. 30–35. [Google Scholar] [CrossRef]
- Fernández-Caramés, T.M.; Fraga-Lamas, P.; Suárez-Albela, M.; Castedo, L. Reverse Engineering and Security Evaluation of Commercial Tags for RFID-Based IoT Applications. Sensors 2017, 17, 28. [Google Scholar] [CrossRef] [PubMed]
- Fraga-Lamas, P.; Fernández-Caramés, T.M.; Suárez-Albela, M.; Castedo, L.; González-López, M. A Review on Internet of Things for Defense and Public Safety. Sensors 2016, 16, 1644. [Google Scholar] [CrossRef] [PubMed]
- Pérez-Expósito, J.P.; Fernández-Caramés, T.M.; Fraga-Lamas, P.; Castedo, L. VineSens: An Eco-Smart Decision Support Viticulture System. Sensors 2017, 17, 465. [Google Scholar] [CrossRef] [PubMed]
- Fraga-Lamas, P.; Fernández-Caramés, T.M.; Noceda-Davila, D.; Vilar-Montesinos, M. RSS stabilization techniques for a real-time passive UHF RFID pipe monitoring system for smart shipyards. In Proceedings of the 2017 IEEE International Conference on RFID (RFID), Phoenix, AZ, USA, 9–11 May 2017; pp. 161–166. [Google Scholar] [CrossRef]
- Fraga-Lamas, P.; Fernández-Caramés, T.M.; Noceda-Davila, D.; Díaz-Bouza, M.A.; Vilar-Montesinos, M.; Pena-Agras, J.D.; Castedo, L. Enabling automatic event detection for the pipe workshop of the shipyard 4.0. In Proceedings of the 2017 56th FITCE Congress, Madrid, Spain, 14–15 September 2017; pp. 20–27. [Google Scholar] [CrossRef]
- Fraga-Lamas, P.; Noceda-Davila, D.; Fernández-Caramés, T.; Díaz-Bouza, M.; Vilar-Montesinos, M. Smart Pipe System for a Shipyard 4.0. Sensors 2016, 16, 2186. [Google Scholar] [CrossRef] [PubMed]
- Blanco-Novoa, O.; Fernández-Caramés, T.M.; Fraga-Lamas, P.; Vilar-Montesinos, M.A. A Practical Evaluation of Commercial Industrial Augmented Reality Systems in an Industry 4.0 Shipyard. IEEE Access 2018, 6, 8201–8218. [Google Scholar] [CrossRef]
- Fernández-Caramés, T.M.; Fraga-Lamas, P.; Suárez-Albela, M.; Vilar-Montesinos, M. A Fog Computing and Cloudlet Based Augmented Reality System for the Industry 4.0 Shipyard. Sensors 2018, 18, 1798. [Google Scholar] [CrossRef] [PubMed]
- Fernández-Caramés, T.M.; Fraga-Lamas, P.; Suárez-Albela, M.; Díaz-Bouza, M.A. A Fog Computing Based Cyber-Physical System for the Automation of Pipe-Related Tasks in the Industry 4.0 Shipyard. Sensors 2018, 18, 1961. [Google Scholar] [CrossRef] [PubMed]
- Fraga-Lamas, P.; Fernández-Caramés, T.M.; Blanco-Novoa, O.; Vilar-Montesinos, M.A. A Review on Industrial Augmented Reality Systems for the Industry 4.0 Shipyard. IEEE Access 2018, 6, 13358–13375. [Google Scholar] [CrossRef]
- Fraga-Lamas, P. Enabling Technologies and Cyber-Physical Systems for Mission-Critical Scenarios. Ph.D. Thesis, Universidade da Coruña, Galicia, Spain, May 2017. [Google Scholar]
- Fernández-Caramés, T.M.; Fraga-Lamas, P. A Review on the Use of Blockchain for the Internet of Things. IEEE Access 2018. [Google Scholar] [CrossRef]
- Fernández-Caramés, T.M.; Fraga-Lamas, P. A Review on Human-Centered IoT-Connected Smart Labels for the Industry 4.0. IEEE Access 2018, 6, 25939–25957. [Google Scholar] [CrossRef]
- Patel, S.N.; Smith, J.R. Powering Pervasive Computing Systems. IEEE Pervasive Comput. 2017, 16, 32–38. [Google Scholar] [CrossRef]
- Polianytsia, A.; Starkova, O.; Herasymenko, K. Survey of hardware IoT platforms. In Proceedings of the 2016 Third International Scientific-Practical Conference Problems of Infocommunications Science and Technology, Kharkiv, Ukraine, 4–6 October 2016; pp. 152–153. [Google Scholar]
- Kajimoto, K.; Kovatsch, M.; Davuluru, U. W3C Web of Things. Available online: https://w3c.github.io/wot-architecture/ (accessed on 25 May 2018).
- Khan, M.; Silva, B.N.; Han, K. A Web of Things-Based Emerging Sensor Network Architecture for Smart Control Systems. Sensors 2017, 17, 332. [Google Scholar] [CrossRef] [PubMed]
- Guinard, D.; Trifa, V. Using the Web to Build the IoT; Manning Publications: Shelter Island, NY, USA, 2016. [Google Scholar]
- Lee, K. IEEE 1451 and IEEE 1588 Standards, 208. Available online: https://www.nist.gov/sites/default/files/documents/el/isd/ieee/Information-on-1451_1588-V36.pdf (accessed on 25 May 2018).
- Mikhaylov, K.; Jämsä, J.; Luimula, M.; Tervonen, J. Intelligent sensor interface and data format. In Intelligent Sensor Networks: The Integration of Sensor Networks, Signal Processing and Machine Learning; CRC Press: Boca Raton, FL, USA, 2012; pp. 55–76. [Google Scholar]
- Celicourt, P.; Piasecki, M. An IEEE 1451.0-based Platform-Independent TEDS Creator using Open Source Software Components. Int. J. Sens. Sens. Netw. 2015, 3, 1–11. [Google Scholar]
- Song, E.; Lee, K. Smart Transducer Web Services Based on the IEEE 1451.0 Standard. In Proceedings of the 2007 IEEE Instrumentation Measurement Technology Conference IMTC 2007, Warsaw, Poland, 1–3 May 2007; pp. 1–6. [Google Scholar]
- Licht, T. The IEEE 1451.4 proposed standard. IEEE Instrum. Meas. Mag. 2001, 4, 12–18. [Google Scholar] [CrossRef]
- Jevtic, N.; Drndarevic, V. Design and Implementation of Plug-And-Play Analog Resistance Temperature Sensor. Metrol. Meas. Syst. 2013, 20, 565–580. [Google Scholar] [CrossRef]
- Higuera, J.; Hertog, W.; Perálvarez, M.; Polo, J.; Carreras, J. Smart Lighting System ISO/IEC/IEEE 21451 Compatible. IEEE Sens. J. 2015, 15, 2595–2602. [Google Scholar] [CrossRef]
- Kumar, A.; Srivastava, V.; Singh, M.K.; Hancke, G.P. Current Status of the IEEE 1451 Standard-Based Sensor Applications. IEEE Sens. J. 2015, 15, 2505–2513. [Google Scholar] [CrossRef]
- Corotinschi, G.; Guäitan, V.G. The development of IoT applications using old hardware equipment and virtual TEDS. In Proceedings of the 2016 International Conference on Development and Application Systems (DAS), Suceava, Romania, 19–21 May 2016; pp. 264–268. [Google Scholar]
- Liu, Z.; Monte, G.; Huang, V. ISO/IEC/IEEE P21451-001 standard for signal treatment of sensory data. In Proceedings of the 2016 IEEE 25th International Symposium on Industrial Electronics (ISIE), Santa Clara, CA, USA, 8–10 June 2016; pp. 766–771. [Google Scholar]
- Phala, K.S.E.; Kumar, A.; Hancke, G.P. Air Quality Monitoring System Based on ISO/IEC/IEEE 21451 Standards. IEEE Sens. J. 2016, 16, 5037–5045. [Google Scholar] [CrossRef]
- Arduino Official Website. Available online: http://www.arduino.cc (accessed on 25 May 2018).
- Raspberry Pi Official Website. Available online: http://raspberrypi.org (accessed on 25 May 2018).
- Ajigboye, O.S.; Danas, K. Towards semantics in wearable sensors: The role of transducers electronic data sheets (TEDS) ontology in sensor networks. In Proceedings of the 2016 IEEE 18th International Conference on e-Health Networking, Applications and Services (Healthcom), Munich, Germany, 14–16 September 2016; pp. 1–6. [Google Scholar]
- Pu, F.; Wang, Z.; Du, C.; Zhang, W.; Chen, N. Semantic integration of wireless sensor networks into open geospatial consortium sensor observation service to access and share environmental monitoring systems. IET Softw. 2016, 10, 45–53. [Google Scholar] [CrossRef]
- Suárez-Albela, M.; Fraga-Lamas, P.; Fernández-Caramés, T.; Dapena, A.; González-López, M. Home Automation System Based on Intelligent Transducer Enablers. Sensors 2016, 16, 1595. [Google Scholar] [CrossRef] [PubMed]
- OGC—Sensor Web Enablement (SWE). Available online: http://www.opengeospatial.org/ogc/markets-technologies/swe (accessed on 25 May 2018).
- Grothe, M.; Kooijman, J.; voor Geodesie, N.C. Sensor Web Enablement; NCG Nederlandse Commissie voor Geodesie: Amersfoort, The Netherlands, 2008; Volume 45. [Google Scholar]
- Botts, M.; Percivall, G.; Reed, C.; Davidson, J. OGC® sensor web enablement: Overview and high level architecture. In GeoSensor Networks; Springer: Berlin, Germany, 2008; pp. 175–190. [Google Scholar]
- Jirka, S.; Nust, D.; Schulte, J.; Houbie, F. Integrating the OGC sensor web enablement framework into the OGC catalogue. In Proceedings of the 1st International Workshop on Pervasive Web Mapping, Geoprocessing and Services, Como, Italy, 26–27 August 2010; pp. 26–27. [Google Scholar]
- Díaz Pardo de Vera, D.; Sigüenza Izquierdo, Á.; Bernat Vercher, J.; Hernández Gómez, L.A. A Ubiquitous sensor network platform for integrating smart devices into the semantic sensor web. Sensors 2014, 14, 10725–10752. [Google Scholar] [CrossRef] [PubMed]
- Veintimilla-Reyes, J.; Guillermo, J.; Vanegas, P.; Estrella, R. SWE Sensor Integration for Controlling Remote Sensors Applied to Hidrometeorological Sensing. In Proceedings of the 2017 International Conference on Information Systems and Computer Science (INCISCOS), Quito, Ecuador, 23–25 November 2017; pp. 212–216. [Google Scholar]
- Huang, C.Y.; Liang, S.H. Ahs model: Efficient topological operators for a sensor web publish/subscribe system. ISPRS Int. J. Geo-Inf. 2017, 6, 54. [Google Scholar] [CrossRef]
- Botts, M. Sensor Model Language (SensorML) | OGC. 2007. Available online: http://www.opengeospatial.org/standards/sensorml (accessed on 25 May 2018).
- O’Reilly, T. OGC® PUCK Protocol Standard | OGC. 2012. Available online: http://www.opengeospatial.org/standards/puck (accessed on 25 June 2018).
- OGC PUCK Standard Enables ‘Plug and Work’ Sensor Networks | OGC. 2012. Available online: http://www.opengeospatial.org/pressroom/pressreleases/1542 (accessed on 25 June 2018).
- Toma, D.M.; O’Reilly, T.C.; Bröring, A.; Dana, D.R.; Bache, F.; Headley, K.L.; Mànuel-Làzaro, A.; Edgington, D.R.; Río, J.D. Standards-based plug & work for instruments in ocean observing systems. IEEE J. Ocean. Eng. 2014, 39, 430–443. [Google Scholar]
- Mikhaylov, K.; Petäjäjärvi, J.; Mäkeläinen, M.; Paatelma, A.; Hänninen, T. Extensible modular wireless sensor and actuator network and IoT platform with Plug & Play module connection. In Proceedings of the 14th International Conference on Information Processing in Sensor Networks, Seattle, WA, USA, 13–16 April 2015; pp. 386–387. [Google Scholar]
- Matthys, N.; Yang, F.; Daniels, W.; Michiels, T.W.S.; Joosen, W.; Hughes, D. μPnP-Mesh: The Plug-and-Play Mesh Network for the Internet of Things. In Proceedings of the IEEE World Forum on Internet of Things, Milan, Italy, 14–16 December 2015; pp. 311–315. [Google Scholar]
- Contiki OS Official Website. Available online: http://www.contiki-os.org (accessed on 25 May 2018).
- Jabbar, S.; Ullah, F.; Khalid, S.; Khan, M.; Han, K. Semantic Interoperability in Heterogeneous IoT Infrastructure for Healthcare. Wirel. Commun. Mob. Comput. 2017, 2017. [Google Scholar] [CrossRef]
- RDF 1.1 Primer. Available online: https://www.w3.org/TR/rdf11-primer/ (accessed on 25 May 2018).
- Bröring, A.; Schmid, S.; Schindhelm, C.K.; Khelil, A.; Kaebisch, S.; Kramer, D.; Le Phuoc, D.; Mitic, J.; Anicic, D.; Teniente, E.; et al. Enabling IoT Ecosystems through Platform Interoperability. IEEE Softw. 2017, 34, 54–61. [Google Scholar] [CrossRef]
- BIG IoT EU H2020 Project-Bridging the Interoperability Gap of the Internet of Things. Available online: http://big-iot.eu/ (accessed on 25 May 2018).
- Gyrard, A.; Serrano, M.; Patel, P. Building Interoperable and Cross-Domain Semantic Web of Things Applications. arXiv, 2017; arXiv:cs.SE/1703.01426. [Google Scholar]
- Patel, P.; Gyrard, A.; Thakker, D.; Sheth, A.; Serrano, M. SWoTSuite: A Development Framework for Prototyping Cross-domain Semantic Web of Things Applications. arXiv, 2016; arXiv:1609.09014. [Google Scholar]
- H2020-ICT-2014-1 European Project FIESTA: Federated Interoperable Semantic IoT Testbeds and Applications. Available online: https://cordis.europa.eu/project/rcn/194117_es.html (accessed on 25 May 2018).
- OpenIoT—Open Source Cloud Solution for the Internet of Things. Available online: http://www.openiot.eu/ (accessed on 25 May 2018).
- Bröring, A.; Bache, F.; Bartoschek, T.; van Elzakker, C.P. The sid creator: A visual approach for integrating sensors with the sensor web. In Advancing Geoinformation Science for a Changing World; Springer: Berlin, Germany, 2011; pp. 143–162. [Google Scholar]
- Toma, D.M. Technology Transfer of Observatory Software. 2010. Available online: https://www3.mbari.org/pw/2010-TTOSInternProject-v1.pdf (accessed on 25 June 2018).
- Hernández-Rojas, D.L.; Fernández-Caramés, T.M.; Fraga-Lamas, P.; Escudero, C.J. Design and Practical Evaluation of a Family of Lightweight Protocols for Heterogeneous Sensing through BLE Beacons in IoT Telemetry Applications. Sensors 2018, 18, 57. [Google Scholar] [CrossRef] [PubMed]
- MQTT Official Website. Available online: http://www.mqtt.org (accessed on 25 May 2018).
- Al-Soh, M.; Zualkernan, I. An MQTT-Based Context-Aware Wearable Assessment Platform for Smart Watches. In Proceedings of the IEEE 17th International Conference on Advanced Learning Technologies (ICALT), Timisoara, Romania, 3–7 July 2017; pp. 98–100. [Google Scholar]
- Ahmed, S.; Topalov, A.; Shakev, N. A robotized wireless sensor network based on MQTT cloud computing. In Proceedings of the 2017 IEEE International Workshop of Electronics, Control, Measurement, Signals and Their Application to Mechatronics (ECMSM), Donostia-San Sebastian, Spain, 24–26 May 2017; pp. 1–6. [Google Scholar]
- Sinha, A.; Sharma, S.; Goswami, P.; Verma, V.K.; Manas, M. Design of an energy efficient Iot enabled smart system based on DALI network over MQTT protocol. In Proceedings of the 3rd International Conference on Computational Intelligence and Communication Technology (CICT), Ghaziabad, India, 9–10 February 2017; pp. 1–5. [Google Scholar]
- Oryema, B.; Kim, H.S.; Li, W.; Park, J.T. Design and implementation of an interoperable messaging system for IoT healthcare services. In Proceedings of the 14th IEEE Annual Consumer Communications and Networking Conference (CCNC), Las Vegas, NV, USA, 8–11 January 2017; pp. 45–52. [Google Scholar]
- Earl, B. Calibrating-Sensors. 2016. Available online: https://cdn-learn.adafruit.com/downloads/pdf/calibrating-sensors.pdf (accessed on 25 June 2018).
- RedBearLab BLE Nano Kit v2—nRF52832. Available online: https://www.sparkfun.com/products/14154 (accessed on 25 May 2018).
- BeagleBone Official Website. Available online: http://beagleboard.org/bone (accessed on 25 May 2018).
- Orange Pi PC Official Website. Available online: http://orangepi.org (accessed on 25 May 2018).
- Hernandez-Rojas, D.; Mazon-Olivo, B.; Novillo-Vicuña, J.; Escudero-Cascon, C.; Pan-Bermudez, A.; Belduma-Vacacela, G. IoT Android Gateway for Monitoring and Control a WSN. In Proceedings of the International Conference on Technology Trends, Babahoyo, Ecuador, 8–10 November 2017; pp. 18–32. [Google Scholar]
- Amazon AWS Official Website. Available online: https://aws.amazon.com (accessed on 25 May 2018).
- Microsoft Azure Official Website. Available online: https://azure.microsoft.com (accessed on 25 May 2018).
- Google Cloud Official Website. Available online: https://cloud.google.com (accessed on 25 May 2018).
- IOTM@CH—Cloud. Available online: http://iotmach.utmachala.edu.ec:8082/iot/conf_Iot (accessed on 25 May 2018).
- Google Cloud Platform Pricing Calculator | Google Cloud Platform | Google Cloud. Available online: https://cloud.google.com/products/calculator/?hl=es#id=8bcb41f2-8eb1-4baf-8b86-d003aef848a4 (accessed on 25 June 2018).
- Google Beacon Platform: Eddystone Format. Available online: https://developers.google.com/beacons/eddystone (accessed on 25 May 2018).
- Davidson, R.; Townsend, K.; Wang, C.; Cufí, C. Getting Started with Bluetooth Low Energy—Tools and Techniques for Low-Power Networking; O’Reilly Media: Sevan Fort, CA, USA, 2014. [Google Scholar]
- Android Studio and SDK Tools | Android Developers. Available online: https://developer.android.com/studio/?hl=es-419 (accessed on 25 May 2018).
- Serial Port Monitor—RS232 Port Sniffer & Analyzer—Serial Monitor. Available online: https://www.eltima.com/products/serial-port-monitor/ (accessed on 25 May 2018).
- Products | Navicat. Available online: https://www.navicat.com/en/products (accessed on 25 May 2018).
- Tera Term Official Website. Available online: https://ttssh2.osdn.jp/index.html.en (accessed on 25 May 2018).
- nRF51422 Official Website. Available online: https://www.nordicsemi.com/eng/Products/ANT/nRF51422 (accessed on 25 May 2018).
- Cortex-M0 Official ARM Website. Available online: https://developer.arm.com/products/processors/cortex-m/cortex-m0 (accessed on 25 May 2018).
- ATmega2560 Official Microship’s Website. Available online: http://www.microchip.com/wwwproducts/en/ATmega2560 (accessed on 25 May 2018).


















| Typology | Name | Value/ID |
|---|---|---|
| Basic TEDs [30] | Manufacturer ID | 43 (Acme Accelerometer Company) |
| Model number | 7115 | |
| Version letter | B | |
| Version number | 1 | |
| Serial number | X0 1891 | |
| Standard templates [29] | Accelerometer & Force | 25 |
| Charge Amplifier (w/attached accelerometer) | 26 | |
| Charge Amplifier (w/attached force transducer) | 43 | |
| Microphone with built-in pre amplifier | 27 | |
| Microphone pre amplifier (w/attached microphone) | 28 | |
| Microphones (capacitive) | 29 | |
| High-Level Voltage output Sensors | 30 | |
| Current Loop Output Sensors | 31 | |
| Resistance Sensors | 32 | |
| Bridge Sensors | 33 | |
| AC Linear/Rotary Variable Differential Transformer (LVDT/RVDT) Sensors | 34 | |
| Strain Gauge | 35 | |
| Thermocouple | 36 | |
| Resistance Temperature Detectors (RTDs) | 37 | |
| Thermistor | 38 | |
| Potentiometric Voltage Divider | 39 | |
| Calibration template | Calibration table | 40 |
| Calibration Curve (polynomial) | 41 | |
| Frequency Response Table | 42 | |
| User Data | User name | John Smith |
| User ID | 123456 | |
| Location | Machala | |
| Other information | Project 1.2 |
| Components | Main Characteristics |
|---|---|
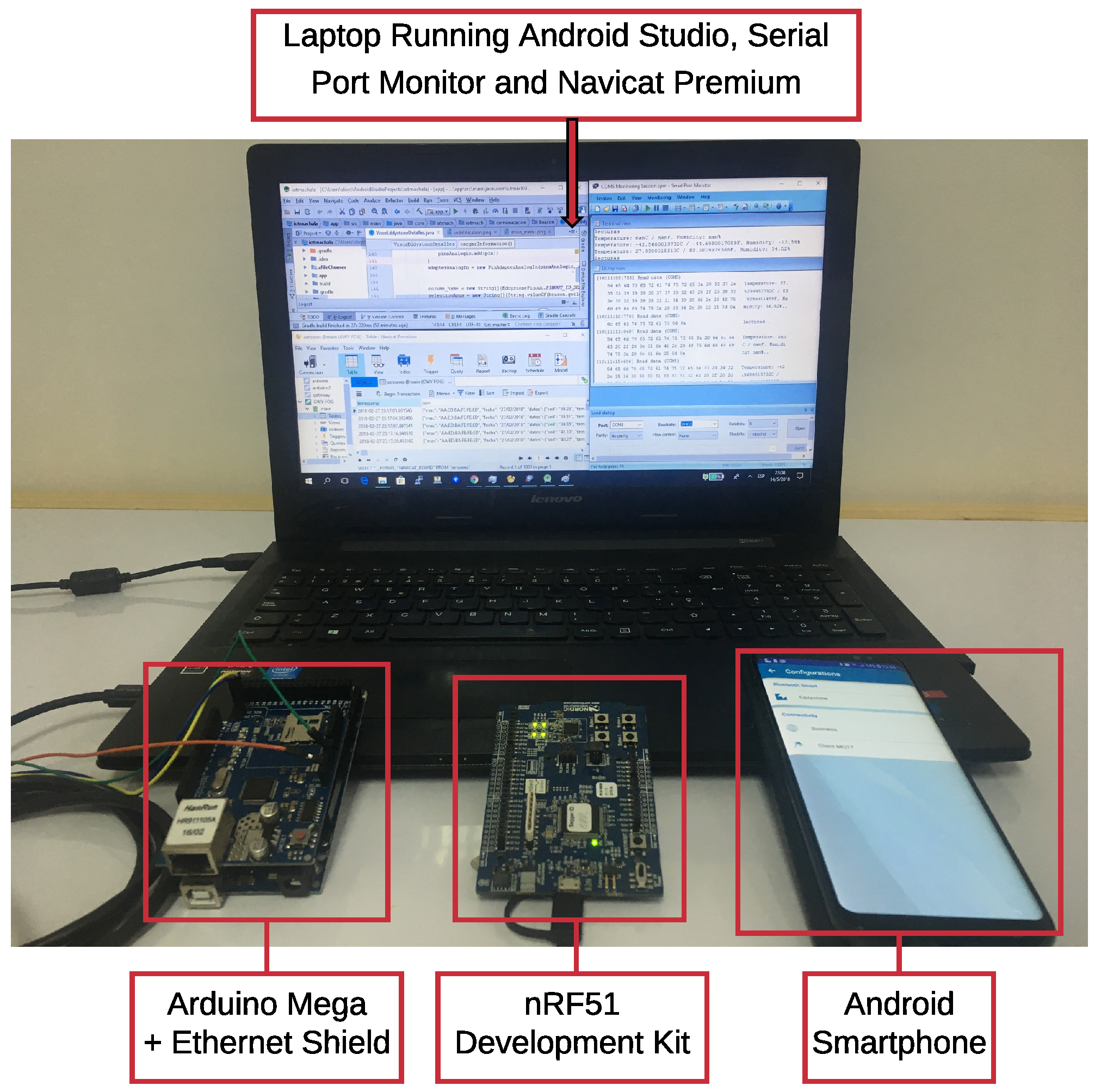
| Laptop | Lenovo 80E502A5SP G50-80: 15.6, 16 GB RAM, 1 TB HDD |
| Intel® Core™i7-5500U CPU @ 2.40 GHz | |
| OS version: Windows 10-Pro x 64 bits | |
| Android Studio 3.0.1 | AI-171.4443003, built on 9 November 2017 |
| JRE: 1.8.0.152-release-915 amd64 | |
| JVM: OpenJDK 64-Bit Server VM by JetBrains s.r.o | |
| Nordic nRF51-DK | SoC: nRF51822, 2.4 GHz multi-protocol device, 32-bit ARM® |
| Cortex™M0 CPU with 256 kB/128 kB flash + 32 kB/16 kB RAM | |
| Smartphone | Samsung Galaxy S-8, 4 GB RAM, 64 GB (UFS 2.1) ROM |
| Model: SM-G950F | |
| Android version: 7.0 (Nougat) | |
| Processor: Exynos 8895, 2.3 GHz Quad + 1.7 GHz Quad, 8 Cores (Octa-Core) | |
| Arduino Mega | SoC: ATmega2560, 8 bits, 16 Mhz |
| Digital I/O Pins: 54, Analog Input Pins: 6 | |
| 256 kB flash, 8 kB SRAM and 4 kB EEPROM | |
| Ethernet Shield | Ethernet Controller: W5500 with internal 32 K buffer, 10/100 Mb |
| connection with Arduino on SPI port. | |
| Operating voltage 5 V (supplied from the Arduino Board) | |
| Serial Port Monitor | Version 6.0, Build 6.0.235 Eltima Software |
| It analyzes serial port activity and monitors several ports within one session. | |
| Navicat Premium | Version 11.0.8, Seamless Data Migration, Diversified Manipulation Tool |
| Easy SQL Editing, Intelligent Database Designer, Advanced Secure Connection | |
| Connect to MySQL, MariaDB, SQL Server, Oracle, PostgreSQL, and SQLite |
| TIMs | Self-Registration Latency (ms) | Telemetry Latency (ms) | ||
|---|---|---|---|---|
| t1 (NCAP) | t2 (Cloud) | t3 (NCAP) | t4 (Cloud) | |
| BLE Beacon | 5655.21 | 6557.71 | 1156.23 | 1808.62 |
| BLE GATT | 1700.79 | 2541.86 | 1040.29 | 1274.71 |
| Ethernet | 739.46 | 1040.46 | 404.79 | 672.14 |
| Experiments | Self-Registration Latency (ms) | Telemetry Latency (ms) | ||
|---|---|---|---|---|
| t1 (NCAP) | t2 (Cloud) | t3 (NCAP) | t4 (Cloud) | |
| BLE-GATT (LoS) | 1700.79 | 2541.86 | 1040.29 | 1274.71 |
| BLE-GATT (NLoS) | 3154.79 | 4523.21 | 1374.43 | 1618.93 |
© 2018 by the authors. Licensee MDPI, Basel, Switzerland. This article is an open access article distributed under the terms and conditions of the Creative Commons Attribution (CC BY) license (http://creativecommons.org/licenses/by/4.0/).
Share and Cite
Hernández-Rojas, D.L.; Fernández-Caramés, T.M.; Fraga-Lamas, P.; Escudero, C.J. A Plug-and-Play Human-Centered Virtual TEDS Architecture for the Web of Things. Sensors 2018, 18, 2052. https://doi.org/10.3390/s18072052
Hernández-Rojas DL, Fernández-Caramés TM, Fraga-Lamas P, Escudero CJ. A Plug-and-Play Human-Centered Virtual TEDS Architecture for the Web of Things. Sensors. 2018; 18(7):2052. https://doi.org/10.3390/s18072052
Chicago/Turabian StyleHernández-Rojas, Dixys L., Tiago M. Fernández-Caramés, Paula Fraga-Lamas, and Carlos J. Escudero. 2018. "A Plug-and-Play Human-Centered Virtual TEDS Architecture for the Web of Things" Sensors 18, no. 7: 2052. https://doi.org/10.3390/s18072052
APA StyleHernández-Rojas, D. L., Fernández-Caramés, T. M., Fraga-Lamas, P., & Escudero, C. J. (2018). A Plug-and-Play Human-Centered Virtual TEDS Architecture for the Web of Things. Sensors, 18(7), 2052. https://doi.org/10.3390/s18072052







