Abstract
Energy harvester-integrated wireless devices are attractive for generating semi-permanent power from wasted energy in industrial environments. The energy-harvesting wireless devices may have difficulty in their communication with access points due to insufficient power supply for beacon recognition during network initialization. In this manuscript, we propose a novel method of beacon recognition based on wake-up control to reduce instantaneous power consumption in the initialization procedure. The proposed method applies a moving window for the periodic wake-up of the wireless devices. For unsynchronized wireless devices, beacons are always located in the same positions within each beacon interval even though the starting offsets are unknown. Using these characteristics, the moving window checks the existence of the beacon associated withspecified resources in a beacon interval, checks again for neighboring resources at the next beacon interval, and so on. This method can reduce instantaneous power and generates a surplus of charging time. Thus, the proposed method alleviates the problems of power insufficiency in the network initialization. The feasibility of the proposed method is evaluated using computer simulations of power shortage in various energy-harvesting conditions.
1. Introduction
Recently, wireless devices have been utilized for autonomous monitoring in industrial environments. The wireless devices monitor vibration, sound and temperature data to check the conditions of machinery. These wireless devices communicate with their access points to transmit the sensor data collected. The wireless devices could monitor mobile machines such as vehicles and robots, and their access points may change frequently if the devices are located on vehicular machines. In this case, the initialization procedure for connecting the device to a new access point will increase the power consumption of the wireless devices. The life-time of the wireless devices decreases when the devices are repeatedly attempting a connection. Therefore, power-efficient initialization is an important issue in these environments.
Traditionally, the batteries have been regarded as the primary source of power of the the wireless devices. The researchers in [1,2] considered power conservation approaches. In [1], wireless devices control their sleep time using a fuzzy logic controller. The ratio of throughput to workload and battery level is used as an input of the controller. An inference engine in this controller decides the sleep time of the devices with fuzzy rules. This method enables dynamic adjustment of the power consumption. However, power efficiency in the initial state might be inefficient due to the lack of a priori information such as throughput. In [2], wireless devices control their transmission power on the basis of each location. Beacon nodes transmit a signal with the power level increased step by step until the power reaches the maximum level. Each node calculates the propagation distance, then it selects the appropriate power level. This method leads to initialization delay since it requires time to figure out the optimal power allocation for each device.
These power conservation approaches help to extend the life-time of batteries. However, the batteries still need periodic replacement, requiring man power. The wireless devices are difficult to manage if they are installed in places that are not easy to access. To avoid human intervention, energy harvesters (EHs) are applied as the power source of the wireless devices [3,4]. The EHs generate electrical power as long as their sources of energy are available. Most machines incidentally produce vibrational and thermal energy. In [5], EHs are based on piezoelectric, electrostatic and electromagnetic power generation using mechanical vibration. In [6], thermoelectric EHs generate power using thermal differences. The EHs generate power continuously until the machines halt. However, the amount of generated power is usually at the microwatt level, and this power may be insufficient to operate wireless devices [7,8]. For this reason, the wireless devices should be implemented with low-power consumption.
After rectifying the generated power, super-capacitors store up the direct current (DC)-converted power [9]. In the case of exceeding a circuit-defined threshold, wireless devices are provided with the stored power in the super-capacitors [10]. The wireless devices should communicate with the access points using the stored power only. Since the quantity of industrial data is large, the wireless devices should utilize network bandwidth efficiently [11]. Furthermore, the wireless devices should maintain reliability to protect important data from collisions [12] or in-band interferences [13]. Thus, time-division communication methods are suitable for wireless devices [14]. Upon powering up of the wireless devices, the time-division networks are initialized. Once the wireless devices detect beacons, they start association procedures to allocate guaranteed network resources. However, the wireless devices have no information about the beacon arrival time, and the wireless devices should detect the beacons before power depletion.
In this manuscript, we propose a beacon recognition method based on periodic wake-up for industrial EH wireless devices. For all devices, beacons are located in the same positions in all beacon intervals. For access points, beacons always exist as the head of the beacon interval, and the location of the beacons does not change. For wireless devices, beacons exist at an unknown location in the beacon interval; however, the relative positions of the beacons are the same across all beacon intervals. In order to find the correct beacon location, the proposed method checks for the existence of the beacon using a moving window. The moving window controls the activation time of the receiving mode for the wireless devices. To reduce power consumption, the wireless devices change to the sleep state at the end of the moving window. The moving window shifts its position sequentially in each beacon interval to examine the resources until beacon recognition is finished. For example, the window position for any i-th beacon interval is located at the i-th resources to check the beacon arrival. Once the beacon is identified, the wireless devices synchronize on the basis of the beacon reception time.
EH wireless devices have to solve the problem of a finite life-time. However, low-power consumption methods should be applied to those kinds of wireless devices due to the insufficient power supply. Until now, many low-power techniques for wireless devices have been proposed; however, these techniques do not consider initialization. The proposed method is one of the low-power consumption techniques related to beacon recognition, and it is effective for network initialization under those power constraint conditions. This proposed method can charge power faster since the required power is less. Beacons are recognized faster, so our proposed method has the merit of fast initialization. Moreover, the proposed method can extend the life-time of battery-supplied wireless devices.
This manuscript provides two contributions. The first is the introduction of the reduction ratio to anticipate the energy efficiency. Engineers could utilize this ratio to design a power supply circuit or control the power consumption of the device. The second is the consideration of the problem of real-world clock drift. This analysis reflects physical layer parameters and provides an example of the applicable beacon interval (BI) range based on the tolerance of the 2.4-GHz specification of the IEEE 802.15.4 standard.
2. Related Work
2.1. IEEE 802.15.4 Beacon-Enabled Networks
Industrial wireless devices are applicable for monitoring various modules in industrial plant environments [11,12,13,14]. The wireless devices are installed in a wide-ranging area, so they should be managed with low cost and low maintenance. Furthermore, the wireless devices should ensure the reliability of data to figure out the states of machines correctly. The specifications of the IEEE 802.15.4 standard meet the requirements of low power consumption [15]. IEEE 802.15.4 devices can be implemented at a low cost because the physical components for signal processing use a small amount of hardware resources. Even if it is difficult to communicate in target environments such as those surrounded by metallic machinery, IEEE 802.15.4 devices have good reception performance. The signal of the standard is robust to low signal-to-noise conditions because it applies the sequence spread spectrum directly. The radio frequency (RF) sensitivity of the signal is lower than −85 dBm, so receivers secure a sufficient fade margin via a wide dynamic range [16]. Moreover, the IEEE 802.15.4 standard supports a beacon-enabled network, so wireless devices avoid collisions by allocating guaranteed resources. Thus, IEEE 802.15.4 devices are reliable enough, and they are applicable to the target environments.
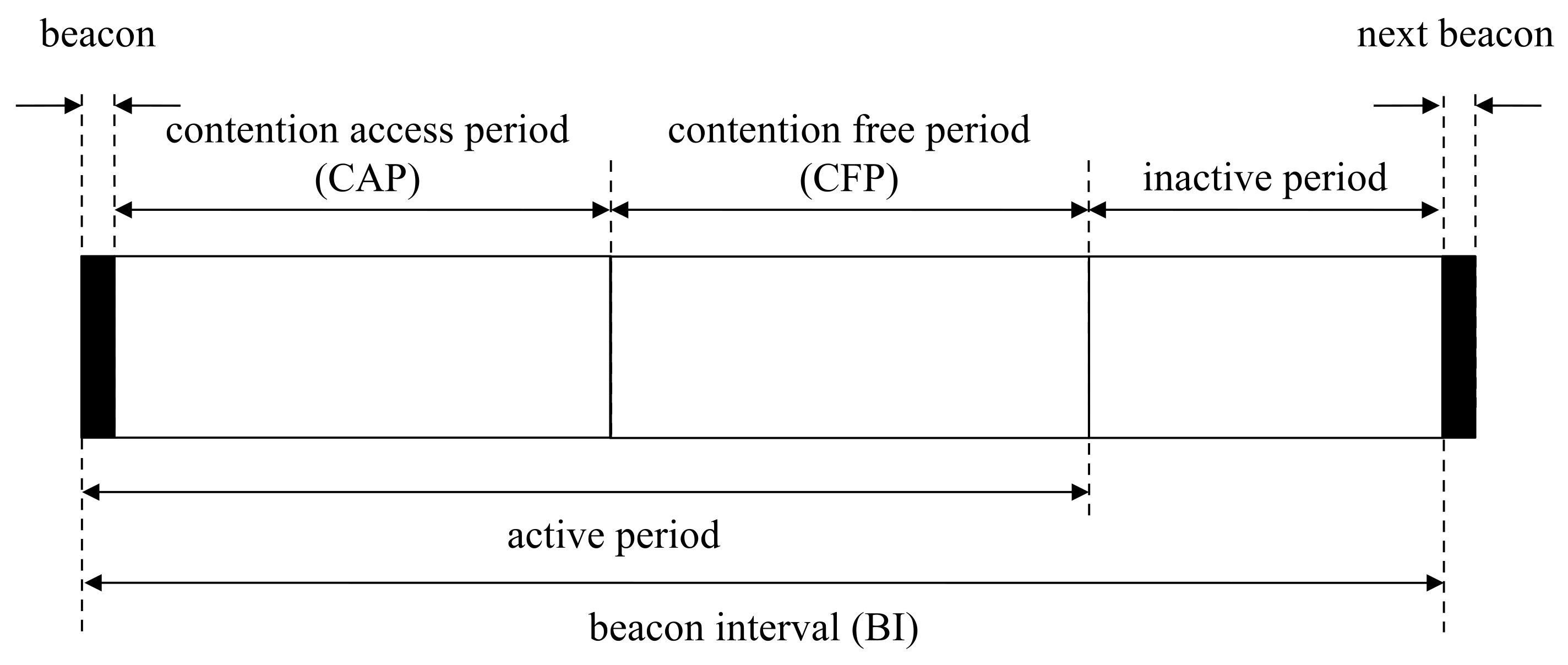
Access points communicate with wireless devices based on the superframe structure in beacon-enabled networks [17]. Access points in beacon-enabled networks manage slots defined by partitioned time logically. The beacon interval in this network is defined by the summation of the active and inactive period, as shown in Figure 1. In the inactive period, all devices belonging to the same network are powered down to save power. The active period is composed of the beacon, the contention-access period (CAP) and the contention-free period (CFP). Beacons transmit by access points to report network information and synchronize devices. In the CAP, devices attempt to connect to access points by random access. In the CFP, devices connect to access points with guaranteed resources by the time-division access in the clear channel. The devices try to associate with access points for addressing. After finalizing the association procedure, the devices are eligible to communicate with access points. Sleep mode is easy to configure for CFP, since the devices only need to continue to receive the mode during the allocated period from the access points [18].
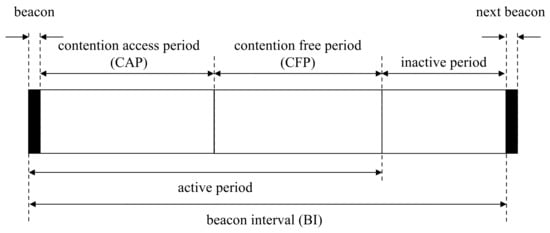
Figure 1.
Superframe structure in beacon-enabled networks.
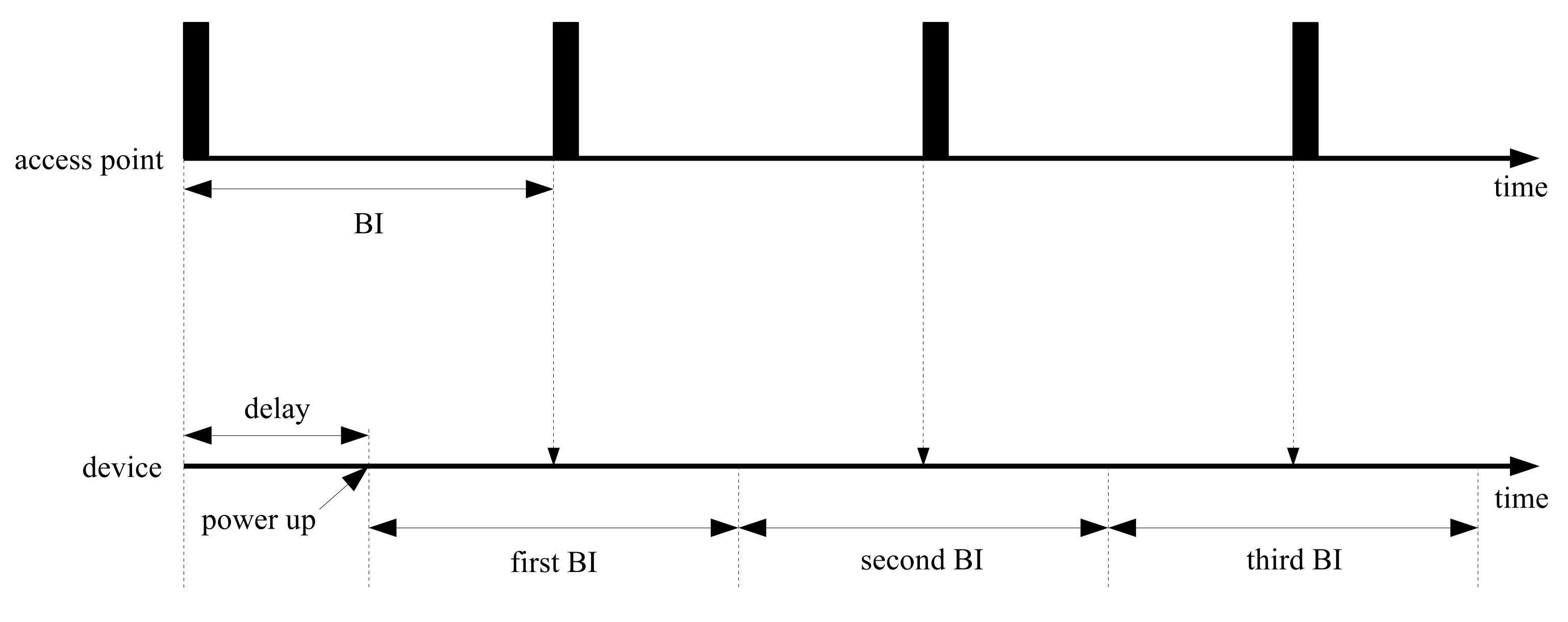
In Figure 2, the operation flows for access points and devices are represented along the time axis. Access points transmit beacons at a constant rate at the beginning of beacon-enabled networks. Devices start connecting to the access points randomly; however, the devices should control wireless functions to be able to catch incoming beacons. When power supply is sufficient, devices can retain the receive states of successful beacon recognition without termination. However, in the case of a lack of stored power, devices are turned on and off randomly. In the worst case, the devices are powered down repeatedly before beacon arrivals. Power insufficiency may occur by modifying beacon periods; however, the capacity of the power supply circuit is impossible to modify even by changing the network properties.
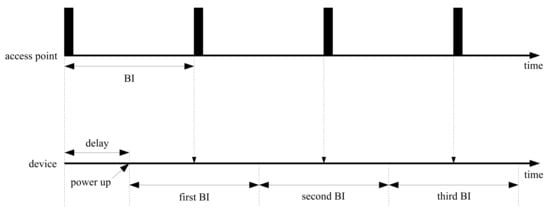
Figure 2.
Periodic beacon arrival with random delay.
2.2. Medium Access Control Protocols for Low-Power Consumption
Some medium access control (MAC) protocols were proposed related to periodic wake-up schemes for EHs. In [19], on-demand MAC (ODMAC) is a representative energy-efficient protocol. A device using this protocol broadcasts status information via small-length packets to neighboring devices. This method introduces an opportunistic forwarding scheme to avoid energy waste. To determine the duty cycle, this method monitors the amount of generated power using the battery level and a threshold. In [20], an energy-harvested receiver-initiated MAC (ERI-MAC) concatenates small packets without packet headers, and it eliminates overhead information. Furthermore, this method regards acknowledgment packets as the beacon packets. These two key ideas contribute to enhancing the energy efficiency; however, they make assumptions to be able to know the harvesting rate. In [21], RF-MAC supports both communication and wireless charge in the same frequency. This method perfectly overcomes the limitations of battery-powered systems. In this environment, devices are not able to communicate during the charging period; therefore, throughput is not optimized. Furthermore, in this approach, the distance of each device from an access point affects the charging performance. Devices located in the outer boundary may lose the communication opportunity due to the lack of power.
Receiver-initiated protocols begin network initialization by transmitting beacons from one of the devices. These protocols require additional procedures to synchronize neighboring devices [22,23]. In beacon-enabled networks, however, all devices should synchronize with the access points. The access points control the network resources. Each device should first figure out the properties of the resources from beacons and make an attempt to access them. This initialization procedure should support the low power consumption specification. In order to find beacons transmitting from access points, a modified duty-cycle approach is needed.
3. Periodic Wake-Up for Beacon Recognition
In this manuscript, a periodic wake-up method is considered to reduce wasted power. This proposed method uses the characteristics of periodic beacon transmission, and a moving window controls devices to carry out receive and sleep mode interchangeably. The moving window is designed to cover beacon arrivals by sliding as much as a BI until the correct beacon is detected. The proposed method is focused on beacon recognition without the synchronization of neighboring devices. We define some variables to design the moving window for beacon inspection. We assume that is the number of BIs for observation, is the time for BI, is the i-th BI, i is an integer in the range of zero to and is the offsets between the initial and actual BI from the perspective of the devices.
3.1. Moving Window Design
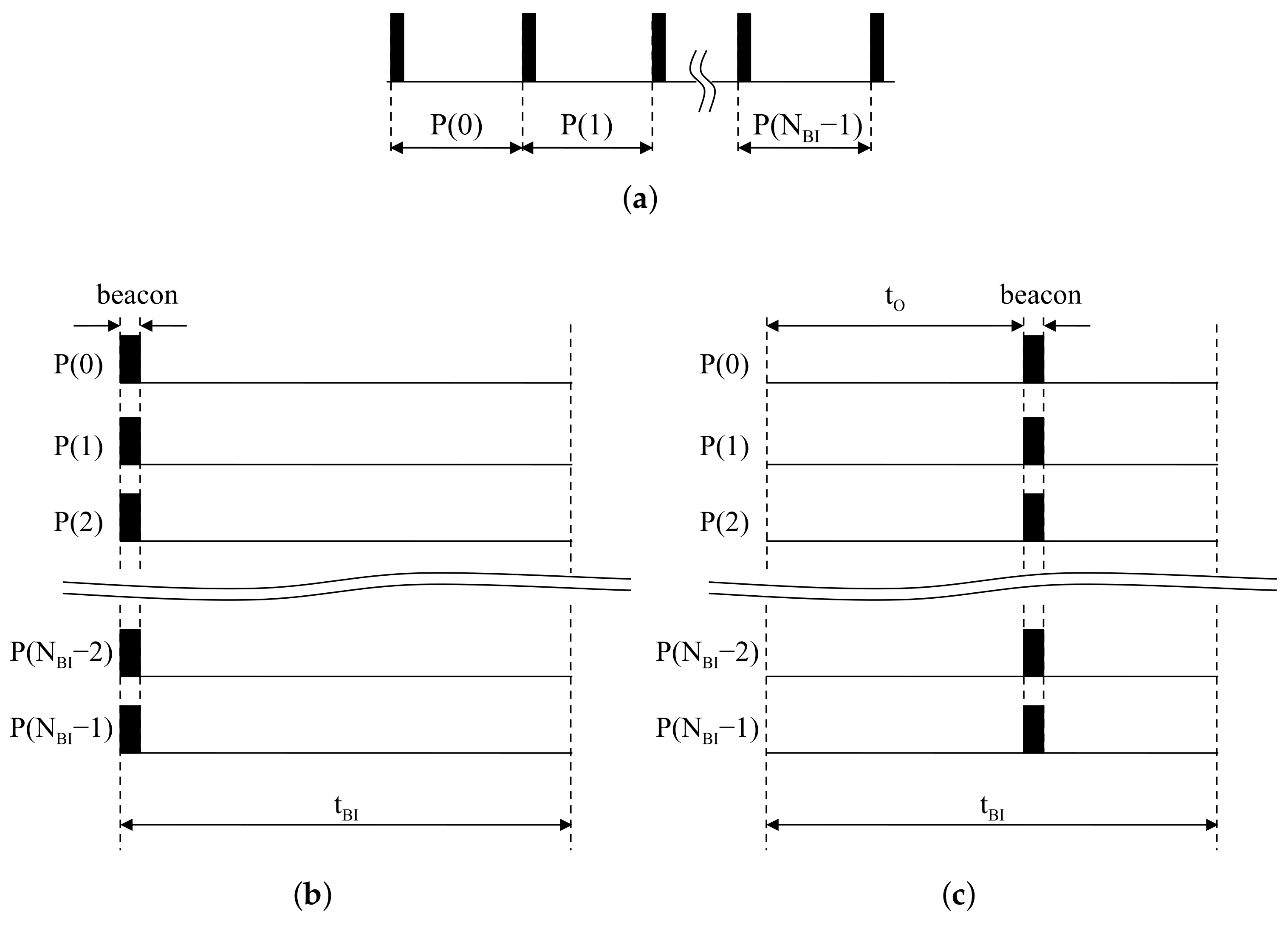
Once network configuration by access points is finished, BIs are rarely changed since the transmission rate of beacons is constant. In terms of access points, beacons always exist at the first slot in all BIs. Continuous BIs with respect to access points are represented in Figure 3a. Piling the sliced BIs, beacons are always located at the front of all BIs, as shown in Figure 3b. In the same situation, a device starting after is assumed to listen to the the wireless channel to catch signals from access points. The offset is regarded as the time difference between the beginning of the device and the first beacon reception. The partitioning result of the listening time into is represented in Figure 3c. The device is started with delay as at the first BI. The time difference between the beginning of the second BI and the second incoming beacon also corresponds with . Piling the partitioned results, beacons in the device appear at the same location inside BIs.
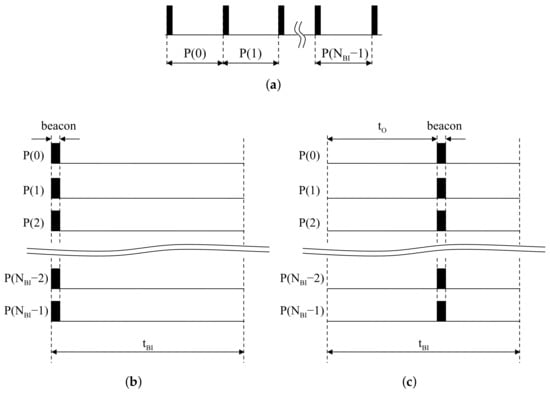
Figure 3.
Beacon alignment: (a) Periodic beacons at an access point; (b) Piled beacons at an access point; (c) Piled beacons at a device.
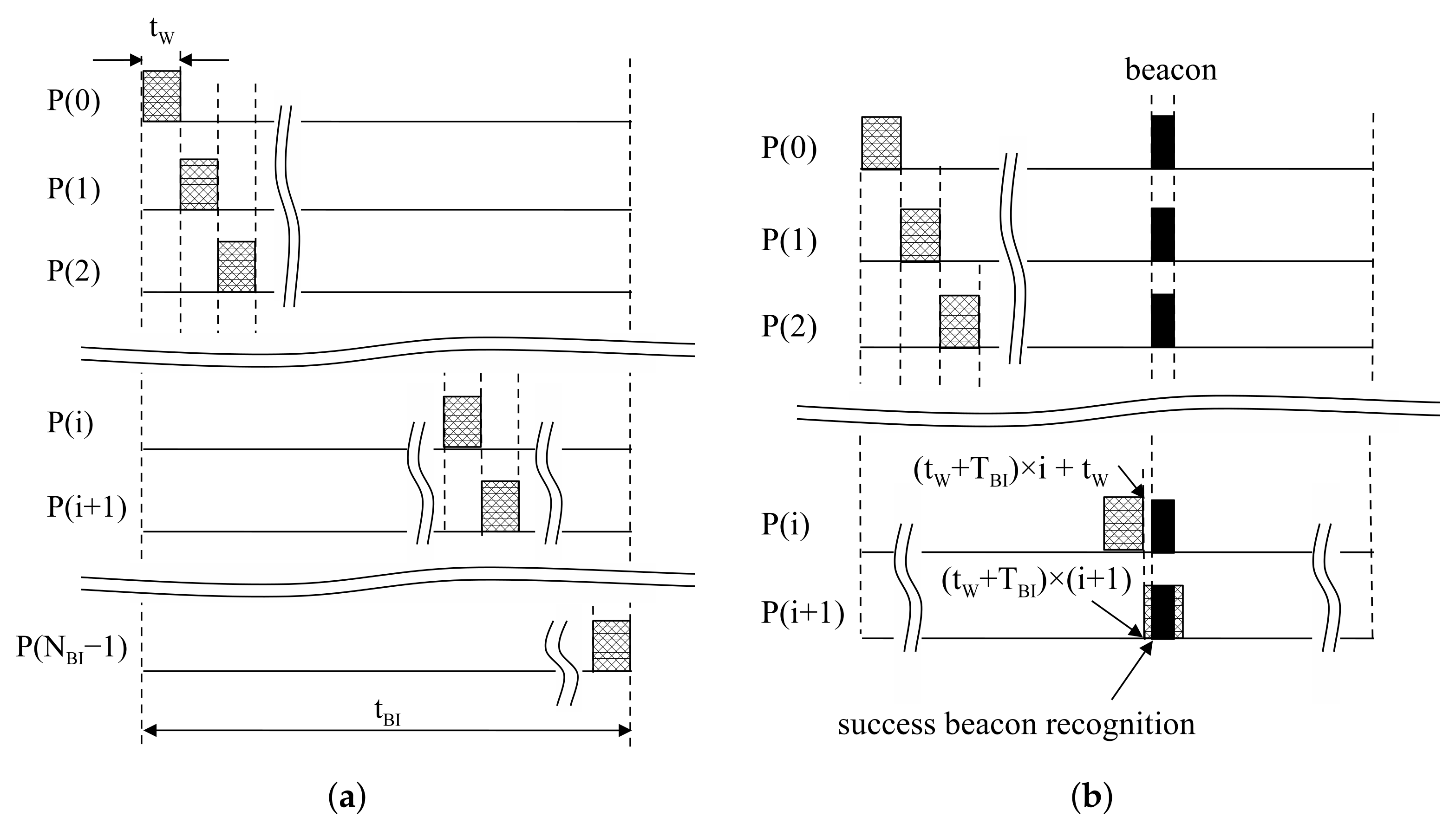
The proposed moving window detects aligned beacons at the same position in each BI. The moving window is designed to check the reception of a beacon for resources at each BI. In this method, the receive mode is activated during in . At the next , the remaining resources are checked in the same way. This process runs repeatedly until beacon reception is successfully finished, as shown in Figure 4b. Beacon recognition is able to finish within by the proposed moving window.
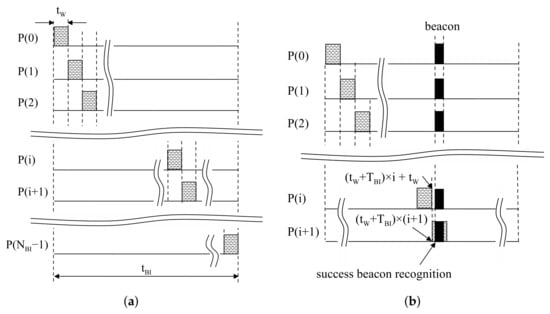
Figure 4.
Operation of a proposed moving window: (a) Design of the proposed moving window; (b) An example of success in beacon recognition.
The size of the moving window is defined as to recognize beacons within trials. Then, devices stay in sleep mode, except the activated time for the moving window. At in Figure 4a, the moving window is located at . Similarly, at in Figure 4a, the moving window is located at . The tail of the i-th moving window is , and the head of the -th moving window is ; then, . Thus, the proposed moving window can be realized by staying in sleep mode during after receiving during . A period of the moving window is , so the duty cycle is calculated with . From those results, the switching interval of the device can be generalized as:
where is the starting time of receive mode in and is the starting time of sleep mode in .
3.2. Calculation of Power Consumption
In this subsection, the power consumption of the proposed method is calculated. In Table 1, the parameters related to this calculation are described. The amount of the normalized power consumption is calculated by the total power consumption divided by the summation of the receiving delay.

Table 1.
Description of variables related to beacon detection procedure.
As shown in Figure 3b, for a device, the time offset is not changed in BI. We assume to represent in terms of , and . The is the verified time for the absence of a beacon by moving windows, so it is a multiple of . The is the time for the moving window at beacon reception. It is the remainder of divided by , so it is always less than . If the beacon is detected at the -th BI, the index of BIs i can be written as:
and are:
Then, can be written as:
Therefore, the total power consumption can be written as:
For , the instantaneous power in a single BI is the same as the total power consumption, so . In the case of , the instantaneous power in the same period can be written as . Then, a reduction ratio for the power consumption can be calculated by:
In the case of , . Usually , so the reduction ratio is definitely smaller than one. This result shows that the instantaneous power can be reduced by the proposed method.
Next, let us consider devices’ operation. The devices are operable when the generated power is greater than the power consumption. From this fact, the conditions are derived as follows.
Beacon detection for needs time for power generation above at least . At the initial state, devices based on the conventional method may be operated along with a delayed start. Devices should wait for the power to be sufficiently charged. In the case of , the generated power will be greater than since . This means that devices initialized by the proposed method may reach operable power faster than the conventional method. Therefore, the delay of the proposed method can be shorter than the conventional method.
3.3. Consideration of Clock Drift
In the standard of the IEEE 802.15.4 [15], the tolerance is specified as ±40 ppm. Therefore, one second of the devices could be perceived in the range of 0.99996–1.00004 s. Considering the transmitter and receiver, the maximum clock drift could be up to 80 ppm. We assume a beacon is supposed to arrive at the i-th window in the case of no clock drift and perfect link-layer communication conditions. Then, we consider two difficult situations by the real-world clock drift with respect to the devices.
The first situation assumes that a device runs fast with the maximum clock drift. Beacons in the device are moving in the direction toward the tail of beacon intervals gradually. Suppose that an -th beacon is located at the tail of an i-th window. At the next step, the beacon might deviate from the i-th window as 0.008% of a beacon interval. In this case, the i-th window should be extended as much as 0.008% at the last step of the beacon recognition. This extension probably will not affect most of situations due to the lack of sufficient power supply. This could be simply realized by turning off the radio after finishing the beacon recognition procedure.
The second situation assumes that a device runs slow with the maximum clock drift. Beacons in the device are moving in the direction toward the head of beacon intervals gradually. Suppose that an -th beacon is located at the head of an i-th window. This is a similar situation as shown above; however, a part of the beacon packet cannot be used for reception. This situation could lead to serious performance degradation due to packet loss. An actual packet is composed of a PHY (physical) header and a PHY payload. Here, a preamble is located at the beginning of the PHY header. In the preamble, eight identical symbols are allocated, and they utilize a coarse timing synchronization. This synchronization is the first step to detect packets with symbol level accuracy. Usually, the coarse timing can be calculated by autocorrelation based on the moving average with two identical symbols. This means that the remaining six symbols are redundant parts of the packet. For example, the symbol time is 16 s at a 2.4-GHz O-QPSK specification. Therefore, the packet has a 96 s margin. The beacon interval can be calculated by Equation (12). At BO = 7, the beacon interval is 0.98304 s, and the maximum clock drift is around 78.6 s. Based on this analysis, our method can be used under the condition BO < 8 without any modification.
In the reference standard, 15 slots are available at the same superframe since the first slot is only available for beacon packets. This means only 15 devices can communicate simultaneously. Furthermore, the maximal packet length is 133 bytes including PHY overheads. A signal of one byte is represented during 32 s. Therefore, the maximal packet time is 4.256 ms. If BO = 7, the maximum slot duration is 7.68 ms. If reliability is important, the packet length should be shorter since long packets increase the probability of errors occurring. In this standard, link-layer performance is guaranteed to be lower than 1% packet error probability at −85 dBm RF sensitivity with a 20-byte packet. Considering bandwidth efficiency and reliability, the beacon interval and packet length should not be too long in an industrial wireless network. For this reason, the condition of BO < 8 is sufficient for the practical target environment.
4. Evaluation of the Proposed Method
In this section, we prove the outstanding performances of the proposed method in terms of power consumption and recognition time by computer simulations. For the simulation scenario, each wireless device is directly connected to an access point. The performance results are represented in terms of power and delay with various simulation parameters. In this simulation, the proposed method is compared to a straightforward method. We assume that the straightforward method holds the receive mode until a device detects a beacon. The power supply in the straightforward method should secure power in order for the receive mode to be operable for at least one BI before starting the device. The results for show the performance of the straightforward approach since a BI is not partitioned; whereas, the results for the other conditions show the performance of the proposed method.
4.1. Simulation Setup
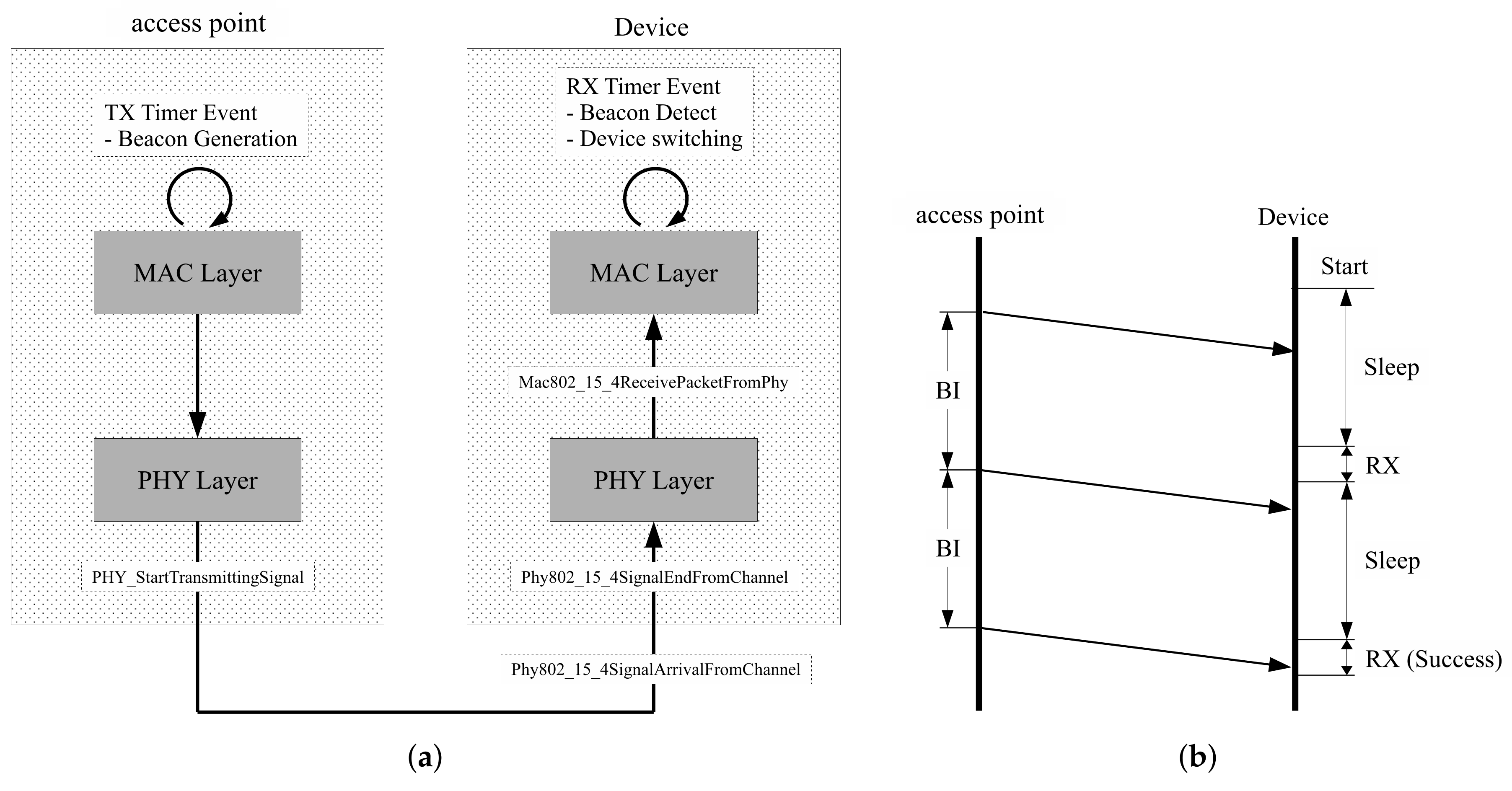
QualNet [24] is an event-driven communication system simulation software. This software supports fundamental functions for the IEEE 802.15.4 standard [25]. Using this library, the proposed method is implemented by modifying a part of the physical and MAC layer. In the physical layer, wireless signals are automatically calculated by reflecting radio propagation. At the transmitter, the radio properties are configured in relation to the transmission power. In wireless channels, path losses are calculated using the distance between wireless devices. At the receiver, incoming packets are verified as to whether error has occurred based on RF sensitivity and the signal-to-noise ratio. In the MAC layer, some commands are exchanged for device control. MAC functions exchange request and response messages to control remote devices. Some MAC messages should handle related events before the timer has expired.
Simulations are focused on the implementation of the beacon life-cycle, as shown in Figure 5a. Access points generate periodic beacons using the timer function. Beacon packets are transmitted when the timer has expired. In the physical layer, beacon packets are moved to a software kernel through the PHY StartTransmittingSignal function. The kernel handles the propagation delay, then transfers beacon signals to devices. The physical layer of the devices handles received signals with interface functions such as Phy802 15 4SignalArrivalFromChannel and Phy802 15 4SignalEndFromChannel. These functions decide whether the received signals are available by calculating the packet error probability based on the path loss information. Then, successful signals move to the next step through Mac802 15 4ReceivePacketFromPhy. In this procedure, the devices check the remaining energy. Packets move to the next step if the accumulated energy is sufficient to receive. The proposed method is implemented using MAC layer interfaces since the MAC layer is able to control device conditions. The proposed moving window is realized using timers that change the receive and sleep state by turning onwhen the device timers have expired.
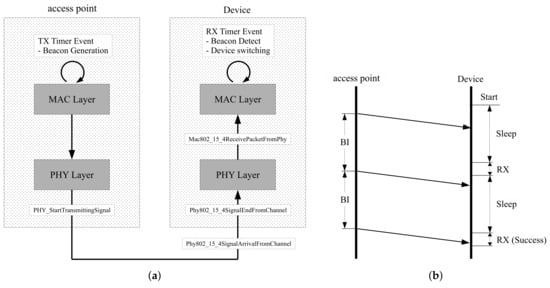
Figure 5.
Configuration of simulation software: (a) Beacon handling process; (b) Example of operation flow.
In this simulation, the propose method is evaluated using the MICAz model [26]. The MICAz model is one of the IEEE 802.15.4 device models that is provided by the simulation software. MICAz is powered by two AA batteries, and its radio is equipped with a CC2420 transceiver [27]. This model consumes a current of 18.8 mA in receive mode. while 0.02 mA in sleep mode. The AA batteries output 1.5 V per piece, so the input voltage of the radio is 3 V. Power is a result of multiplying the voltage and current; therefore, the power is calculated as 56.4 mW in receive mode and 0.06 mW in sleep mode, respectively. To monitor the power consumption in devices, we observe the change of energy stored in the super-capacitor. We assume that a power supplier has perfect energy efficiency. Then, the super-capacitor stores up the difference between generated and consumed energy. When the device is in sleep mode during and in receive mode during , the energy stored in the super-capacitor during is calculated as . Once the beacon has been received, the device will restart randomly within a BI.
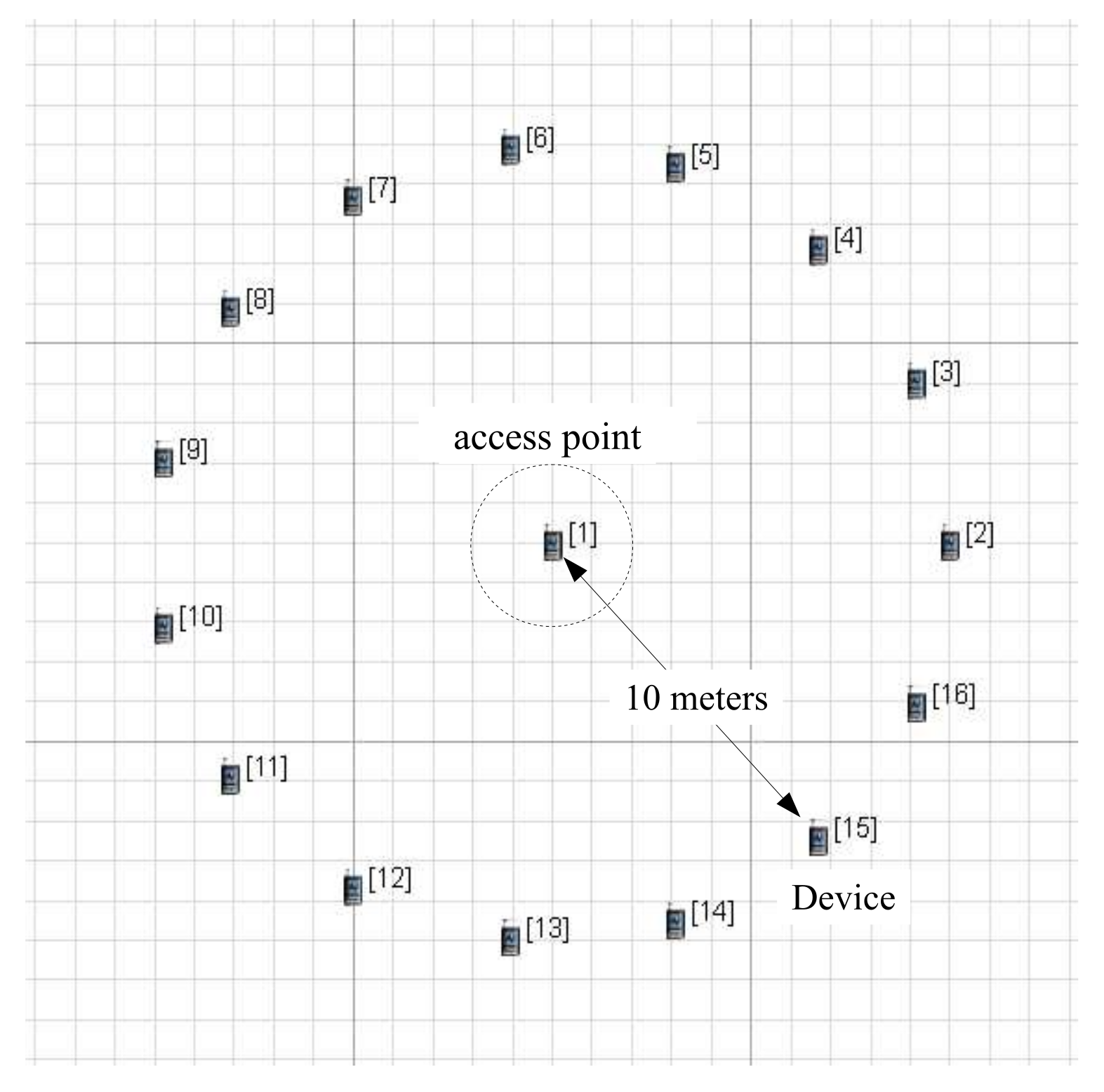
As shown in Figure 6, each device is 10 meters away from an access point in the scenario. This configuration does not cause link-layer errors, so the performance results depend on the simulation conditions alone. The beacon order (BO) decides the length of a BI, and it is configured as 3. The BI is related to the BO as follows:
where is the symbol time for a superframe, defined in the IEEE 802.15.4 standard, and set to a constant number: 960. The rest of the simulation parameters are described in Table 2.
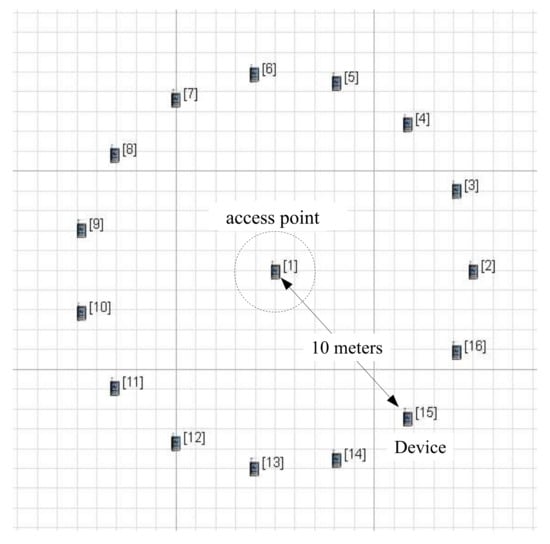
Figure 6.
Deployment of an access point and devices in scenario plane.

Table 2.
Configuration of simulation parameters.
4.2. Simulation Results
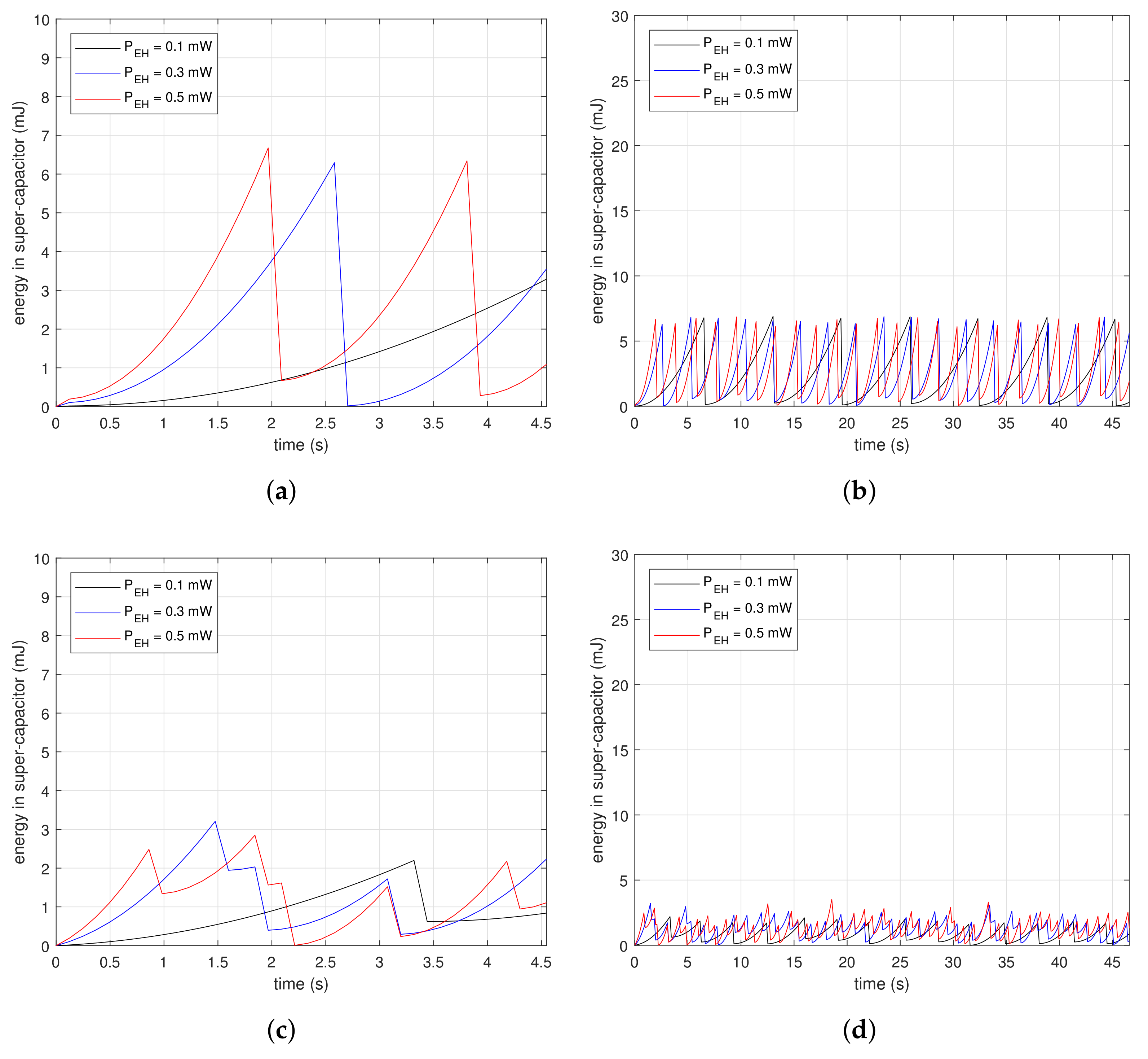
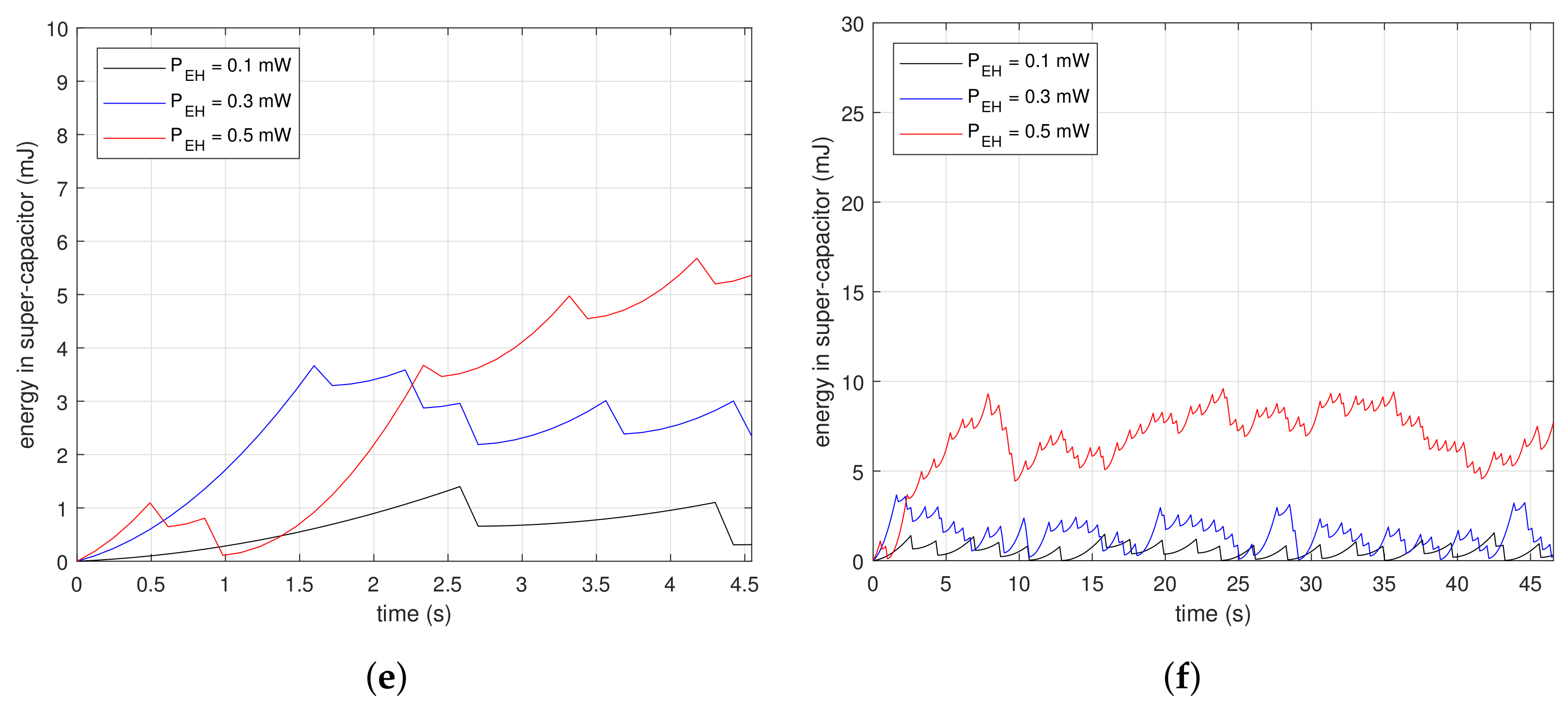
Figure 7 shows measurements of the energy changes in a super-capacitor at the beginning of beacon recognition. The subfigures are the results of drawing the energy variation along time in the condition of , and . Figure 7a,c,e are the magnified results of Figure 7b,d,f, respectively. The saw-shape graphs imply the energy property, which is either charging or consumption. Devices accumulate energy in the super-capacitor when the slopes are ascending, while they drain the energy out of the super-capacitor when the slopes are descending dramatically. Figure 7a,b are the results for . In Figure 7a, vertical slopes appear periodically at each . At the inflection points, devices consume energy instantaneously, as much as the descending depth. The first inflection points for mW and mW are 4.2 and 1.9 s, respectively. The reception delays are inversely proportional to since the higher finishes charging faster. In Figure 7b, the charge–discharge process appears repeatedly. Figure 7c,d are the results for . In Figure 7c, the first inflection point is reached faster than as shown in Figure 7a. Devices with the proposed method only need to charge as much as the time of the moving windows; therefore, they finish collecting the necessary energy faster than the case where . Furthermore, the descending depth of the slopes is less than in the case where . This means the proposed method consumes less energy for beacon recognition. The graphs in Figure 7d are at a lower position than in Figure 7b. These results show that the proposed method is suitable for low power devices. Figure 7e,f are the results for . In Figure 7e, the first inflection point is reached faster than shown in Figure 7c, and also the descending depth is less. Moreover, the stored power can grow as shown in Figure 7f due to the low power property of the proposed method.
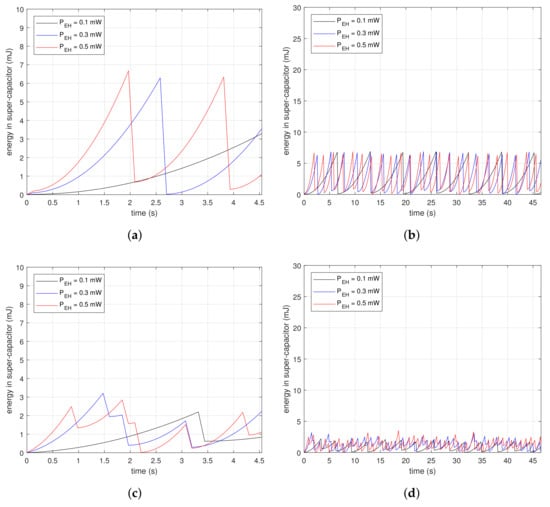
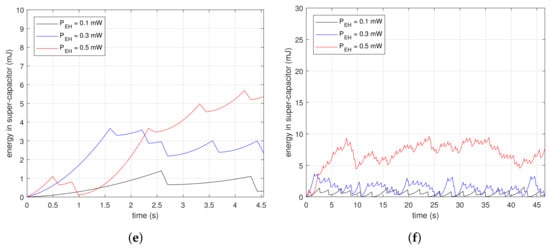
Figure 7.
Initial amount of stored energy in a super-capacitor in conditions of , , and : (a) From 0 to 4.5 s for ; (b) From 0 to 47 s for ; (c) From 0 to 4.5 s for ; (d) From 0 to 47 s for ; (e) From 0 to 4.5 s for ; (f) From 0 to 47 s for .
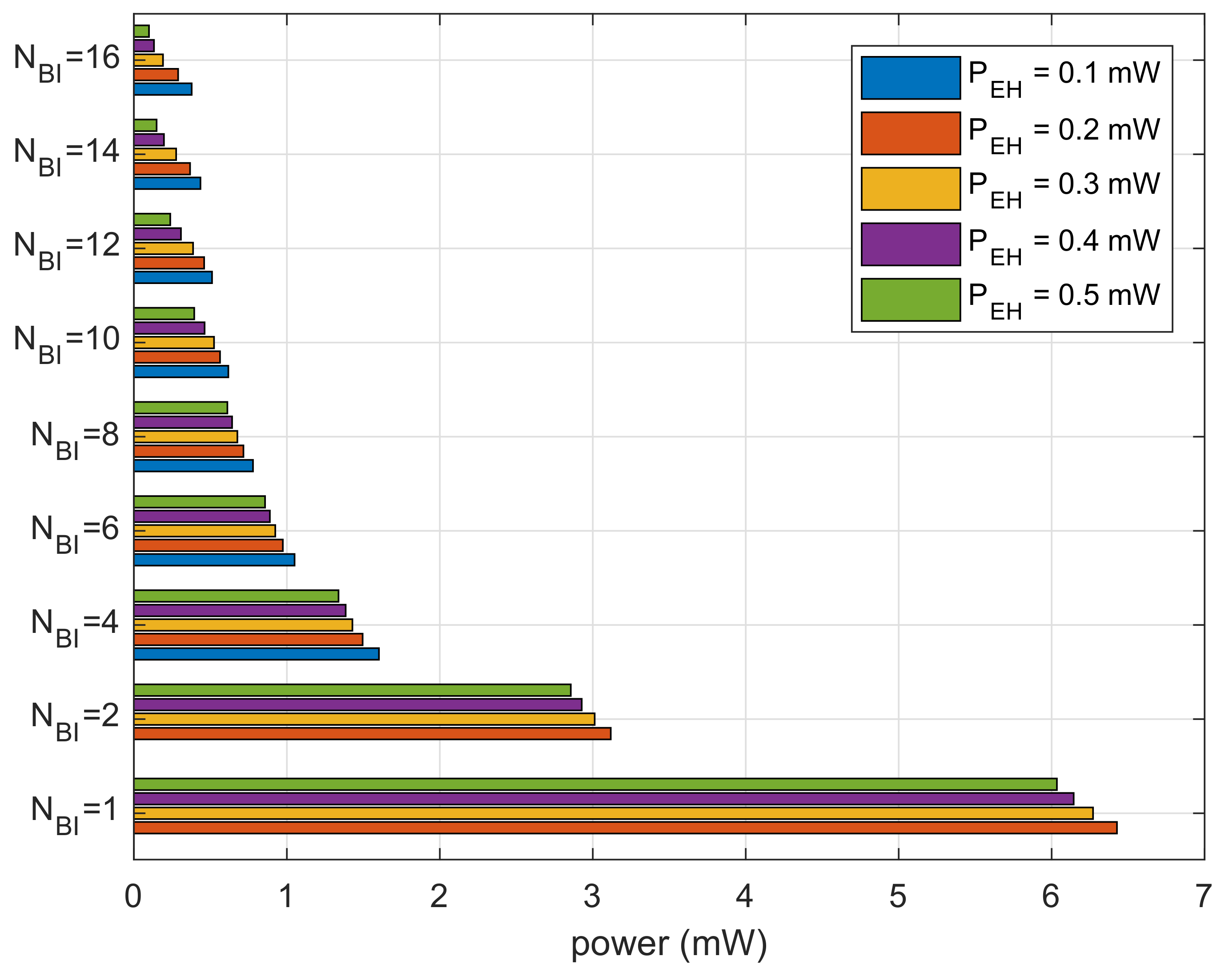
Figure 8 shows the results for cumulative power spent divided by the number of recognized beacons. The results show the average power consumption for receiving a beacon. We can observe that the bar graphs are decaying inversely proportional to because devices with a smaller size of the moving window expend less power. For the same , the lower expends more power. At a lower , the devices expend power in sleep mode during necessary power charging.
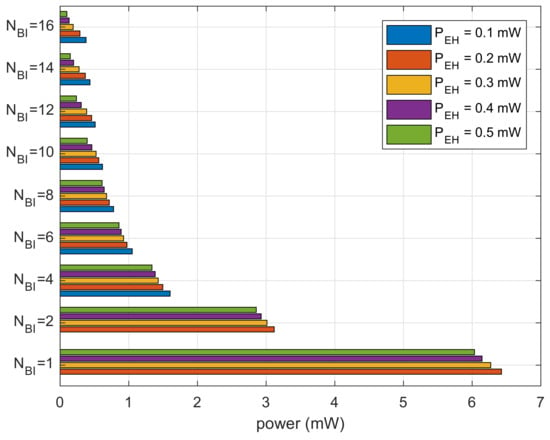
Figure 8.
Average power consumption to recognize one beacon.
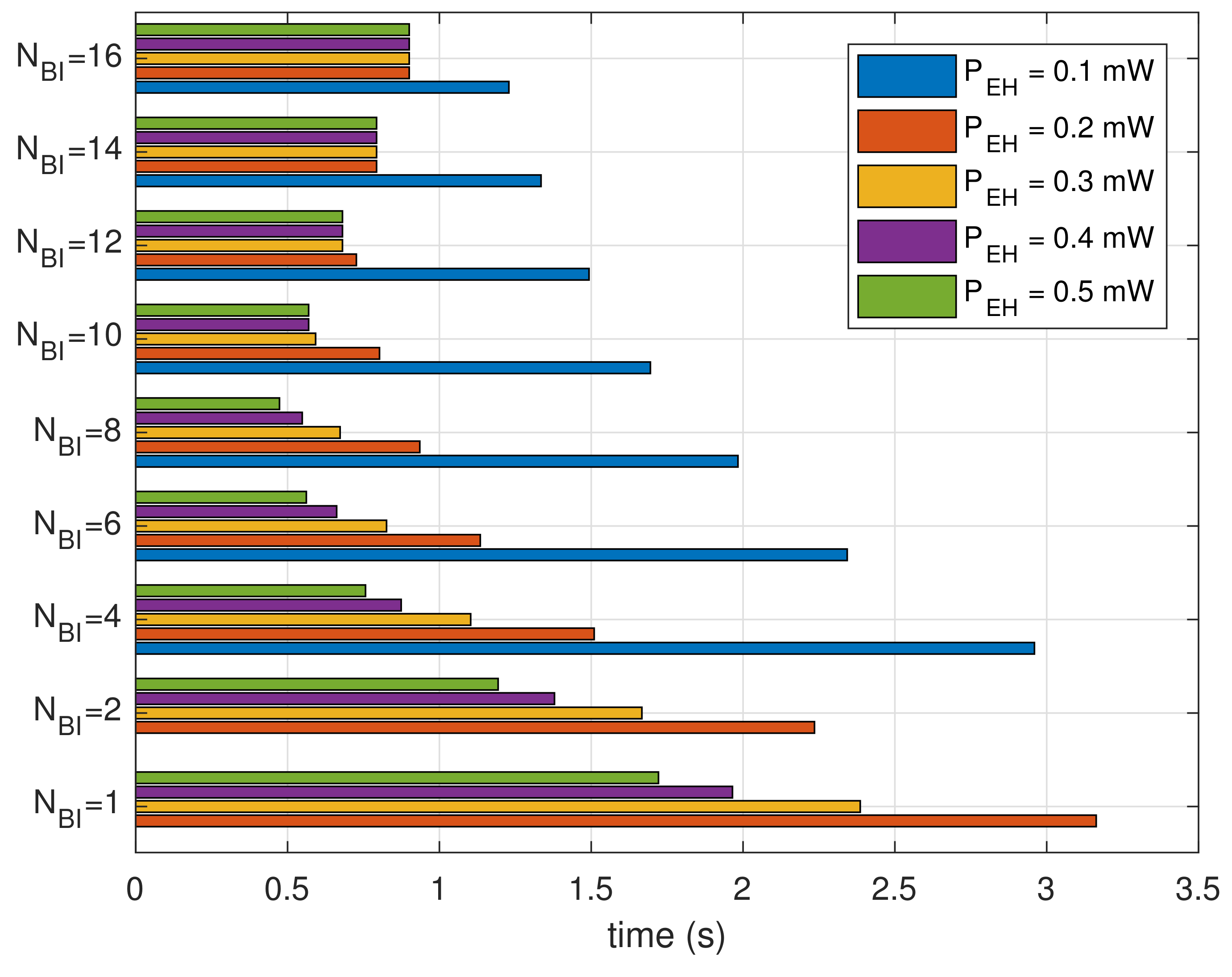
Figure 9 shows the results of dividing the cumulative reception delay by the number of recognized beacons. The results show the average time spent for receiving a beacon. For each generation amount, the bar graphs show a concave shape along the given . The beacon recognition delay is minimized at for mW. For , the beacon recognition delay decreases by reducing the power consumption due to shortening of the moving window. For , on the other hand, the results of beacon recognition delay increase because the moving window spends more time traveling to search for the beacons.
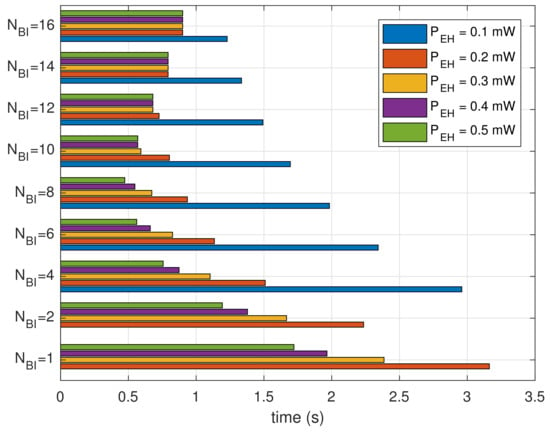
Figure 9.
Average time spent to recognize one beacon.
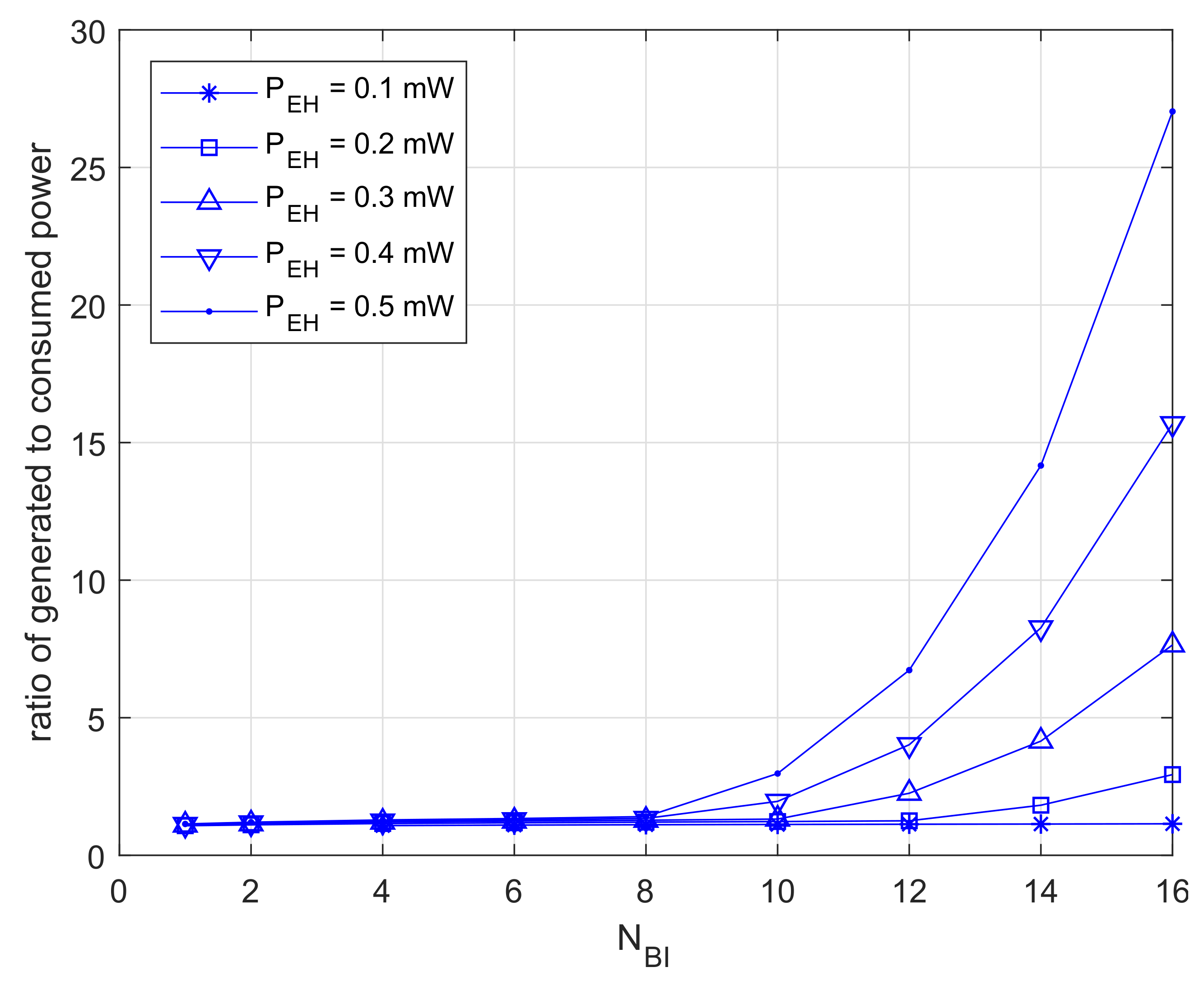
Figure 10 shows the results for dividing the generation quantity by the power usage. The results are close to one at , and this means that the devices consume most of the power stored. Furthermore, those results are increasing exponentially at . In this case, devices are able to retain excess power.
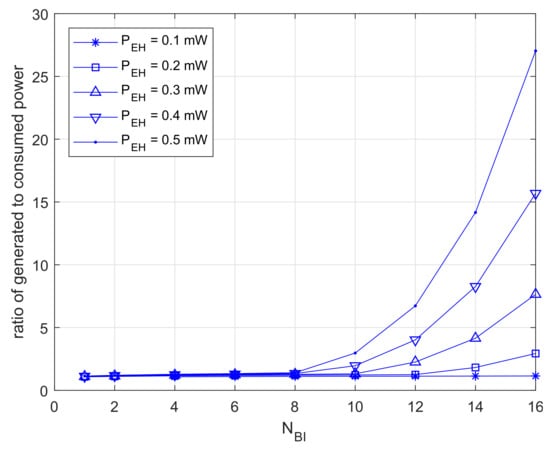
Figure 10.
Ratio of excessive power.
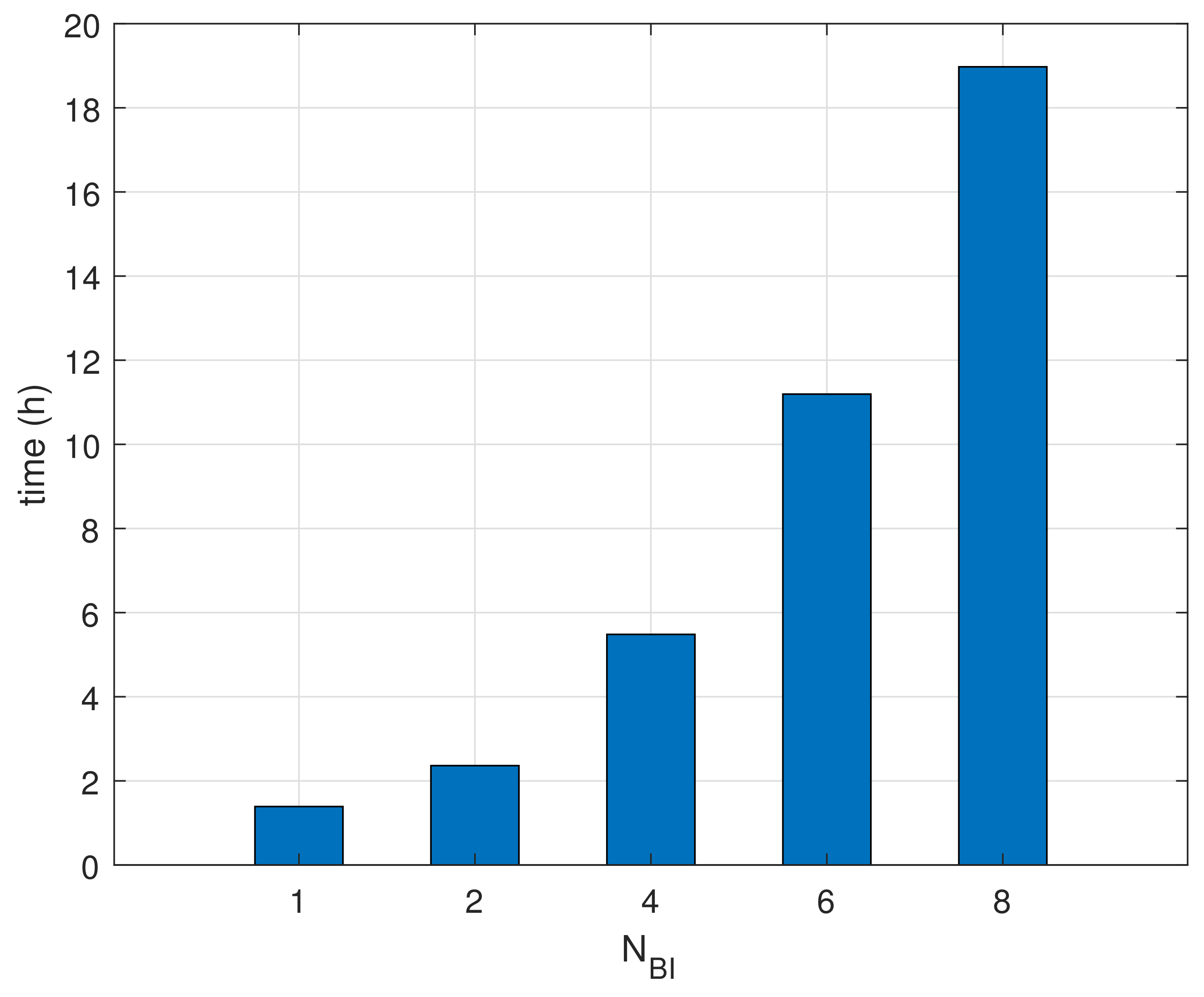
Finally, Figure 11 shows the measurements of the life-time in the condition of devices using batteries. The life-time for is reached at the very beginning since the devices consume power continuously until finishing beacon recognition. The life-time patterns are growing proportional to . These results show that the proposed method helps extend the life-time of battery-based wireless devices.
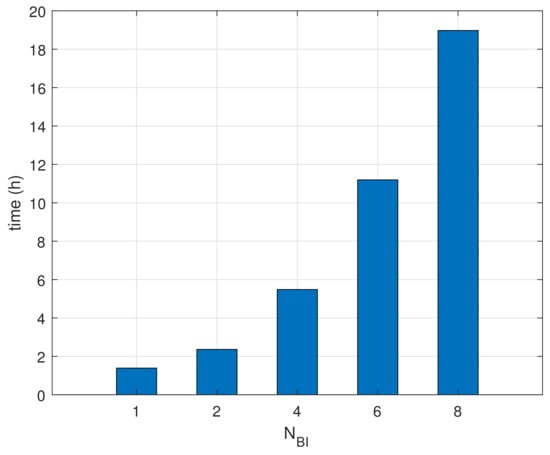
Figure 11.
Comparisons of life-time.
5. Discussion and Conclusions
This manuscript proposed a power-efficient beacon recognition method based on periodic wake-up in network initialization for wireless devices. In beacon-enabled communication between access points and devices, the proposed method reduced the power consumption for beacon detection. A moving window approach was introduced that was designed for wake-up scheduling, and it made it possible to find unknown beacon arrival times. The moving window examined the existence of beacons at partial resources in each BI. After changing the position of the moving window shifted to the next resource, the proposed method checked for the beacons’ existence again. Wireless devices went to sleep mode to save power, except when the moving window was in process. Therefore, our method provided power stability for wireless devices by consuming low power and securing the charging time.
The proposed method enables the reduction of instantaneous power consumption by spreading out the required energy in the time domain. This method reduces the charging time to reach the necessary energy level, so it could finalize beacon recognition procedure faster compared to the straightforward method. Additionally, this approach utilizes generated power efficiently by putting the right power at the right time; whereas, the proposed method leads to unnecessary delay in the condition of holding sufficient energy. Some networks using a long beacon period could result in packet loss due to clock drift. Thus, the proposed method should be applied carefully to low-speed communication systems or massive networks.
The proposed method is suitable for frequently-initialized and power-constrained wireless devices. Furthermore, this method is applicable to wireless devices because it facilitates recollecting wasted energy in industrial plants. Consequently, our method contributes to reducing the maintenance cost of industrial wireless devices based on a beacon-enabled network. Industrial wireless devices for plant monitoring relied on the previously-mentioned communication conditions. The wireless devices on relocatable machinery change access points frequently in these environments. The initialization of beacon-enabled networks can succeed under insufficient power supply since our method provides power-efficient beacon recognition. With the help of computer simulations, our results proved effective in the target environments.
Acknowledgments
This work was supported by the Electronics and Telecommunications Research Institute (ETRI) grant funded by the Korean government (18ZH1120, Distributed Intelligence Core Technology of Hyper-Connected Space). Furthermore, this manuscript is an extended version of the authors’ conference paper entitled “Low-Power Consumption Beacon Recognition Method to Access Wireless Sensor Networks”, which was addressed in proceedings of the 2017 International Conference on Information and Communication Technology Convergence (ICTC 2017).
Author Contributions
S.S. designed, implemented and evaluated the proposed method. D.L. advised on editing this article. I.J. and J.C. advised on research directions. Y.S. supervised this work.
Conflicts of Interest
The authors declare no conflict of interest.
Abbreviations
| BI | Beacon interval |
| BO | Beacon order |
| CAP | Contention access period |
| CFP | Contention free period |
| DC | Direct current |
| dBm | Decibel-milliwatts |
| EH | Energy harvester |
| GHz | Gigahertz |
| MAC | Medium access control |
| mA | Milli-Ampere |
| mW | Milli-Watt |
| O-QPSK | offset quadrature phase shift keying |
| PHY | Physical |
| ppm | Parts-per million |
| RF | Radio-frequency |
| SFD | Start-of-frame delimiter |
References
- Collotta, M.; Pau, G.; Maniscalco, V. A fuzzy logic approach by using particle swarm optimization for effective energy management in IWSNs. IEEE Trans. Ind. Electron. 2017, 64, 9496–9506. [Google Scholar] [CrossRef]
- Farooq-I-Azam, M.; Ni, Q.; Ansari, E.A. Intelligent energy efficient localization using variable range beacons in industrial wireless sensor networks. IEEE Trans. Ind. Inform. 2016, 12, 2206–2216. [Google Scholar] [CrossRef]
- Niyato, D.; Hossain, E.; Rashid, M.M.; Bhargava, V.K. Wireless sensor networks with energy harvesting technologies: A game-theoretic approach to optimal energy management. IEEE Wirel. Commun. 2007, 14. [Google Scholar] [CrossRef]
- Das, K.; Zand, P.; Havinga, P. Industrial wireless monitoring with energy-harvesting devices. IEEE Internet Comput. 2017, 21, 12–20. [Google Scholar] [CrossRef]
- Gilbert, J.M.; Balouchi, F. Comparison of energy harvesting systems for wireless sensor networks. Int. J. Autom. Comput. 2008, 5, 334–347. [Google Scholar] [CrossRef]
- Lopera, J.M.; del Arco Rodríguez, H.; Pereira, J.M.P.; de Castro, A.R.; Vigil, J.L.R. Wireless sensors supplied by energy harvesting thermoelectric generators. In Proceedings of the 2016 IEEE Industry Applications Society Annual Meeting, Portland, OR, USA, 2–6 October 2016; pp. 1–8. [Google Scholar]
- Chalasani, S.; Conrad, J.M. A survey of energy harvesting sources for embedded systems. In Proceedings of the 2008 IEEE Southeastcon, Huntsville, AL, USA, 3–6 April 2008; pp. 442–447. [Google Scholar]
- Sudevalayam, S.; Kulkarni, P. Energy harvesting sensor nodes: Survey and implications. IEEE Commun. Surv. Tutor. 2011, 13, 443–461. [Google Scholar] [CrossRef]
- Pizzotti, M.; Perilli, L.; del Prete, M.; Fabbri, D.; Canegallo, R.; Dini, M.; Masotti, D.; Costanzo, A.; Franchi Scarselli, E.; Romani, A. A Long-Distance RF-Powered Sensor Node with Adaptive Power Management for IoT Applications. Sensors 2017, 17, 1732. [Google Scholar] [CrossRef] [PubMed]
- Harb, A. Energy harvesting: State-of-the-art. Renew. Energy 2011, 36, 2641–2654. [Google Scholar] [CrossRef]
- Gungor, V.C.; Hancke, G.P. Industrial wireless sensor networks: Challenges, design principles, and technical approaches. IEEE Trans. Ind. Electron. 2009, 56, 4258–4265. [Google Scholar] [CrossRef]
- Zhao, G. Wireless sensor networks for industrial process monitoring and control: A survey. Netw. Protoc. Algorithms 2011, 3, 46–63. [Google Scholar] [CrossRef]
- Li, L.; Chen, C.; Wang, Y.; He, T.; Guan, X. Adaptive Beacon Transmission in Cognitive-OFDM-Based Industrial Wireless Networks. IEEE Commun. Lett. 2017, 21, 152–155. [Google Scholar] [CrossRef]
- Yoo, S.E.; Chong, P.K.; Kim, D.; Doh, Y.; Pham, M.L.; Choi, E.; Huh, J. Guaranteeing real-time services for industrial wireless sensor networks with IEEE 802.15. 4. IEEE Trans. Ind. Electron. 2010, 57, 3868–3876. [Google Scholar] [CrossRef]
- LAN/MAN Standards Committee. Part 15.4: Wireless Medium Access Control (MAC) and Physical Layer (PHY) Specifications for Low-Rate Wireless Personal Area Networks (LR-WPANs); IEEE Computer Society: Washington, DC, USA, 2003. [Google Scholar]
- Abbasi, A.Z.; Islam, N.; Shaikh, Z.A.; Aqeel-ur-Rehman. A review of wireless sensors and networks’ applications in agriculture. Comput. Stand. Interfaces 2014, 36, 263–270. [Google Scholar]
- Misic, J.; Shafi, S.; Misic, V.B. Performance of a beacon enabled IEEE 802.15. 4 cluster with downlink and uplink traffic. IEEE Trans. Parallel Distrib. Syst. 2006, 17, 361–376. [Google Scholar] [CrossRef]
- Moriyama, T.; Nakayama, T.; Fujii, T. Receiver beacon transmission interval design for multi-stage wireless sensor networks. In Proceedings of the 2016 Eighth International Conference on Ubiquitous and Future Networks (ICUFN), Vienna, Austria, 5–8 July 2016; pp. 192–197. [Google Scholar]
- Fafoutis, X.; Dragoni, N. ODMAC: An on-demand MAC protocol for energy harvesting-wireless sensor networks. In Proceedings of the 8th ACM Symposium on Performance Evaluation of Wireless Ad Hoc, Sensor, and Ubiquitous Networks, Miami Beach, FL, USA, 31 October–4 November 2011; ACM: New York, NY, USA, 2011; pp. 49–56. [Google Scholar]
- Nguyen, K.; Nguyen, V.H.; Le, D.D.; Ji, Y.; Duong, D.A.; Yamada, S. ERI-MAC: An energy-harvested receiver-initiated MAC protocol for wireless sensor networks. Int. J. Distrib. Sens. Netw. 2014, 10, 514169. [Google Scholar] [CrossRef]
- Naderi, M.Y.; Nintanavongsa, P.; Chowdhury, K.R. RF-MAC: A medium access control protocol for re-chargeable sensor networks powered by wireless energy harvesting. IEEE Trans. Wirel. Commun. 2014, 13, 3926–3937. [Google Scholar] [CrossRef]
- Rault, T.; Bouabdallah, A.; Challal, Y. Energy efficiency in wireless sensor networks: A top-down survey. Comput. Netw. 2014, 67, 104–122. [Google Scholar] [CrossRef]
- Kosunalp, S. MAC protocols for energy harvesting wireless sensor networks: Survey. ETRI J. 2015, 37, 804–812. [Google Scholar] [CrossRef]
- QualNet Simulator. 5.0, Qualnet 5 Users Guide Scalable Network Technologies; SCALABLE Network Technologies, Inc.: Culver City, CA, USA, 2010. [Google Scholar]
- Ullo, S.; Vaccaro, A.; Velotto, G. Performance analysis of IEEE 802.15. 4 based sensor networks for smart grids communications. J. Electr. Eng. Theory Appl. 2010, 1, 129–134. [Google Scholar]
- Datasheet. MICAz Wireless Measurement System; Crossbow Technology, Inc.: San Jose, CA, USA, 2006. [Google Scholar]
- Schmidt, D.; Krämer, M.; Kuhn, T.; Wehn, N. Energy modelling in sensor networks. Adv. Radio Sci. 2007, 5, 347–351. [Google Scholar] [CrossRef]
© 2018 by the authors. Licensee MDPI, Basel, Switzerland. This article is an open access article distributed under the terms and conditions of the Creative Commons Attribution (CC BY) license (http://creativecommons.org/licenses/by/4.0/).