A Passive Tracking System Based on Geometric Constraints in Adaptive Wireless Sensor Networks †
Abstract
:1. Introduction
- (1)
- Using the foundation of the passive tracking schemes based on geometric constraint methodology, we demonstrate the feasibility of identifying RFT phenomenon by utilizing the spatial diversity receiving technique;
- (2)
- To extend the application of the passive tracking schemes based on the geometric constraint method, a method for multiple device-free targets tracking is presented;
- (3)
- We first build a quantifiable power consumption model for RSS-based passive tracking WSNs, and an adaptive networking scheme is proposed with the mechanism of the tracking performance adjustment, as well as energy conservation.
2. Related Works
3. The RFT Identification
- (1)
- (2)
- (3)
- Moreover, the propagation time can also be adopted for detecting the RFT on the LOSL, since the time delay will be increased with the multi-path signal caused by the shadowing of the obstacle, which of course has a harsh requirement on the synchronization accuracy.
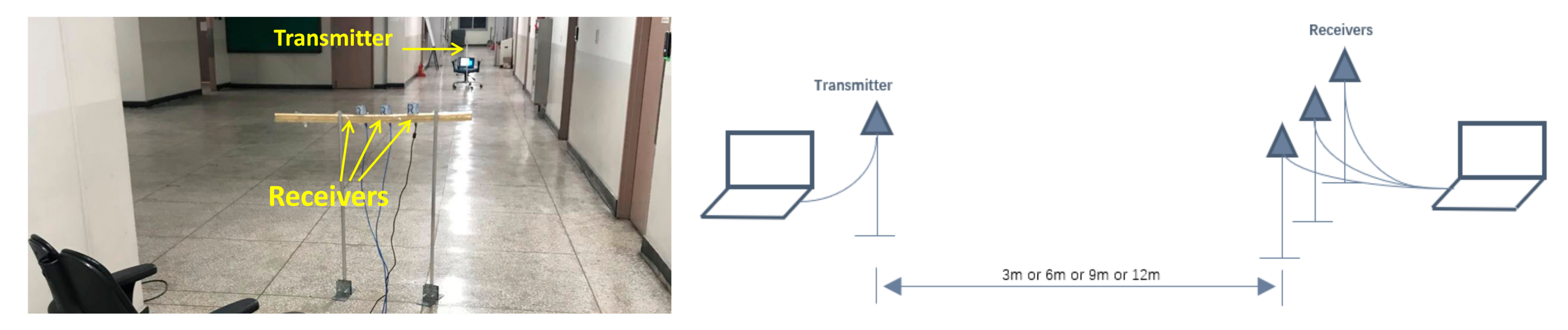
3.1. Experiment Environments
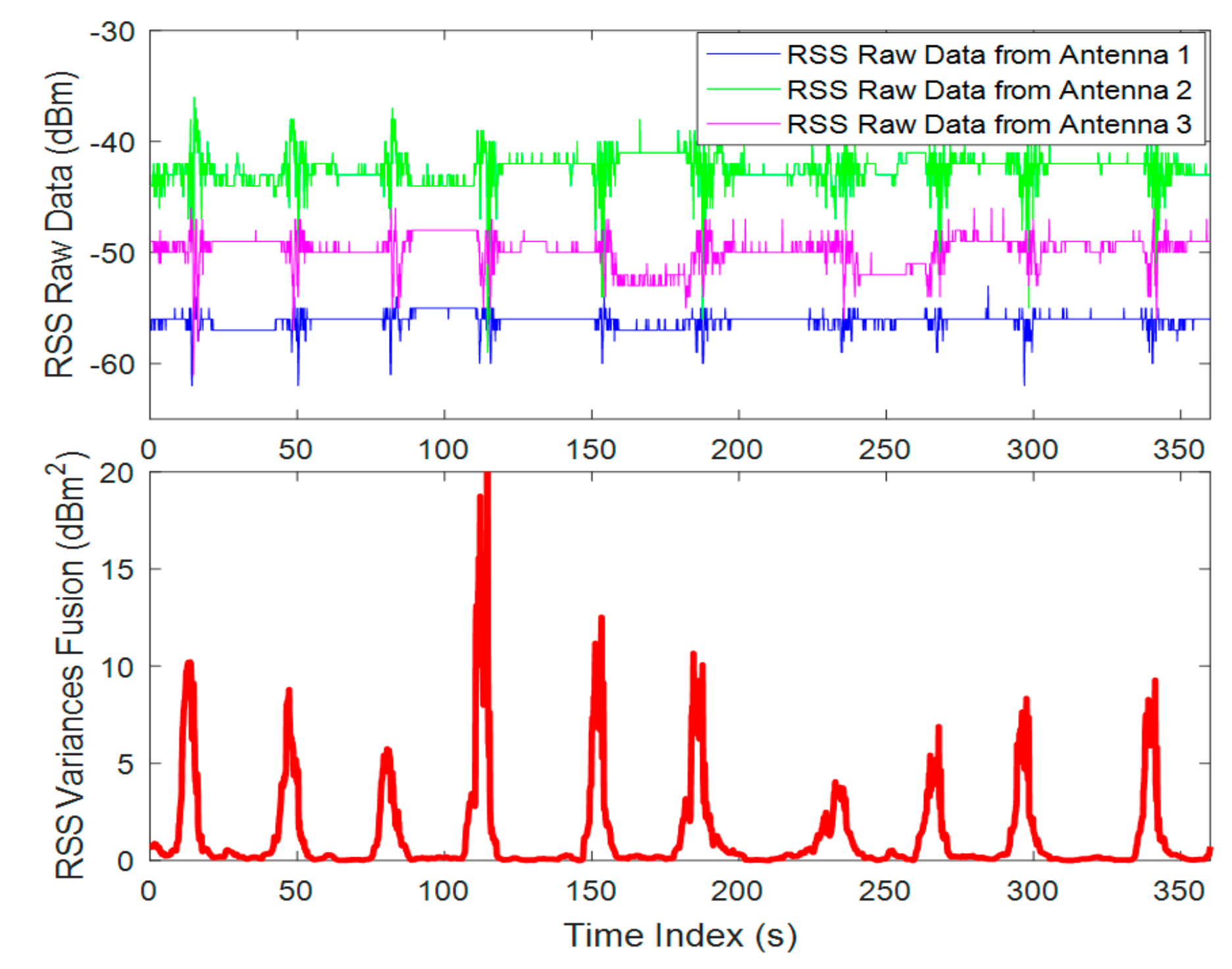
3.2. RSS Fusion under Spatial Diversity Receiving
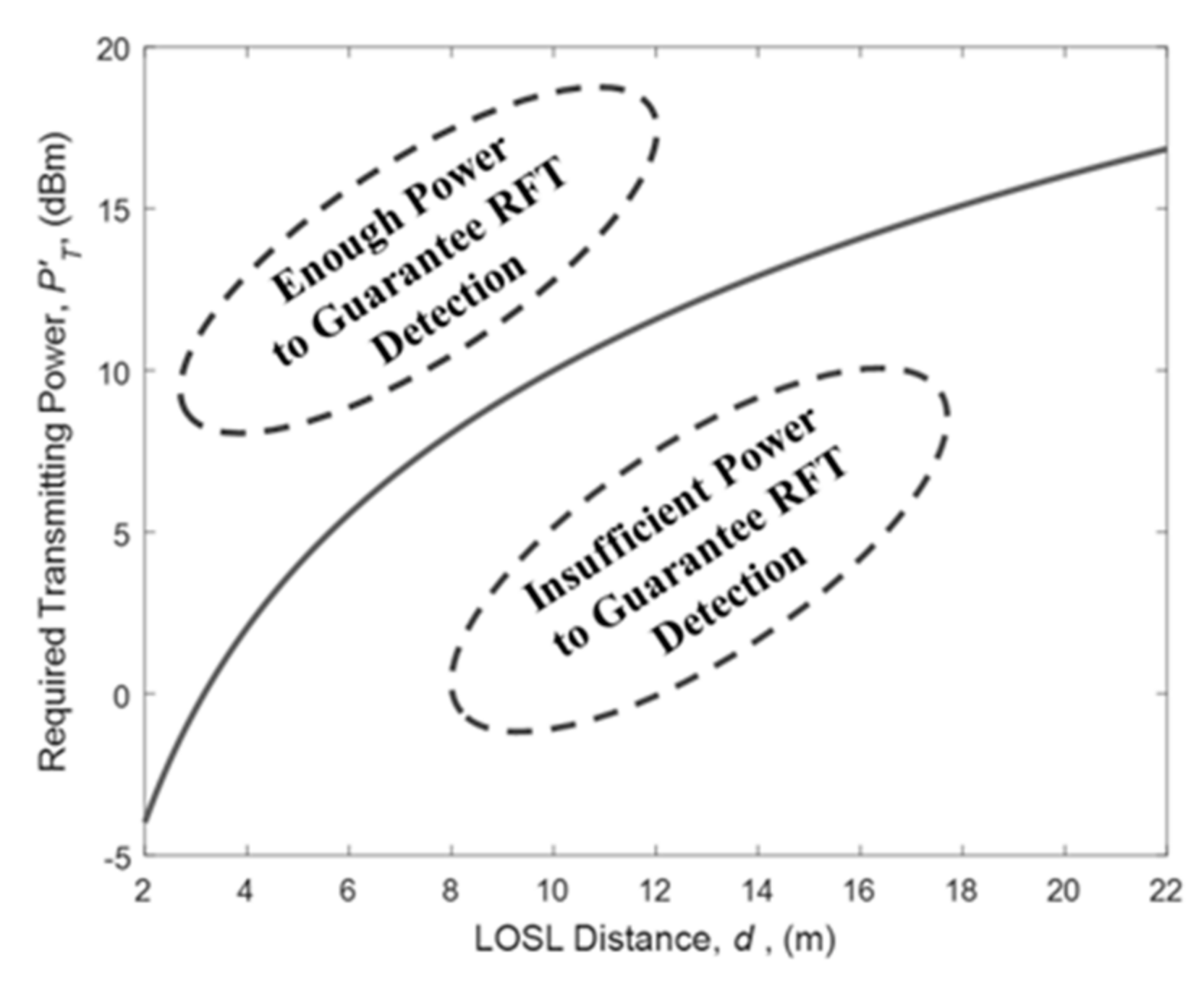
3.3. The Influencing Factors of RFT Detection
4. Passive Tracking System Description
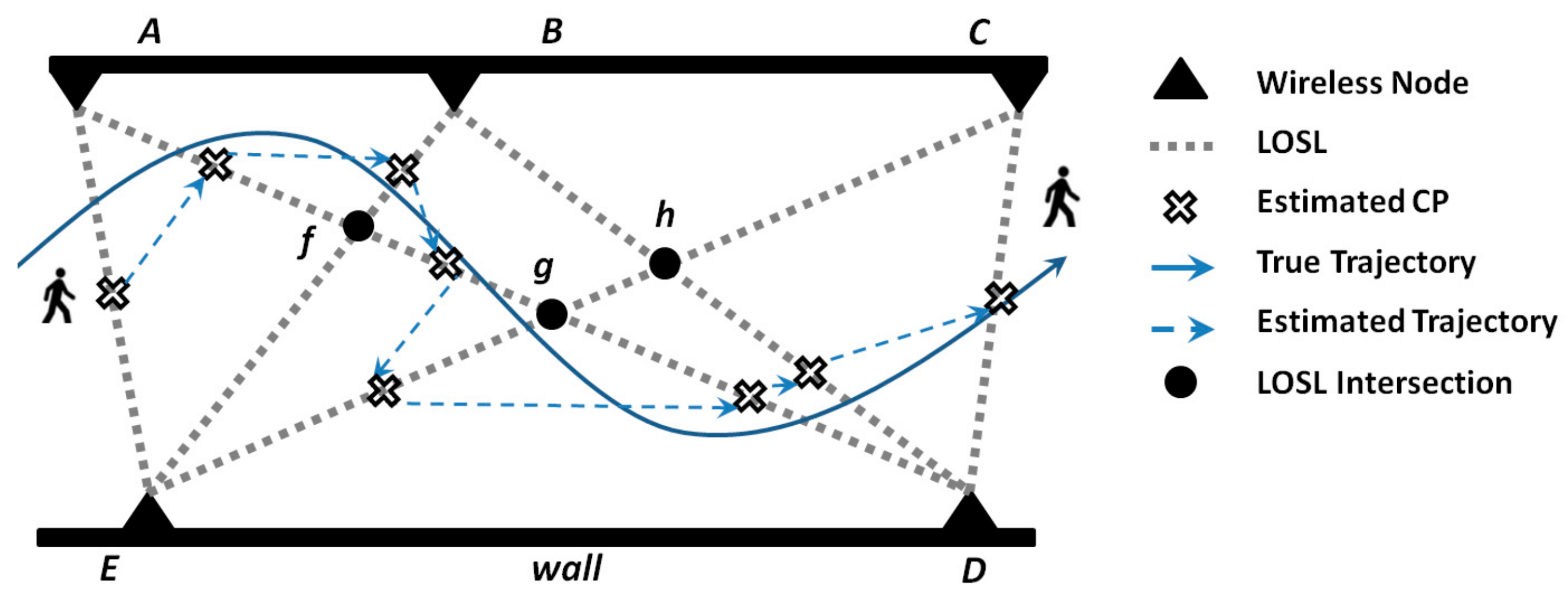
4.1. The CP Estimation for a Single Target Adopting the Geometric Constraint Method
| Algorithm 1. The CP Determination for Tracking a Single Target |
| Initialization: Get information of the WSN topology, including the node positions, LOSL formulas Step 1: get the first CP as the middle point of the edge LOSL , and decide . Step 2: Once is triggered Select the highest probability segment on , which is nearest to . Estimate CP as the middle point of and decide that is the opposite region of . Step 3: Go back to Step 2, until the target walks out of the monitoring area. |
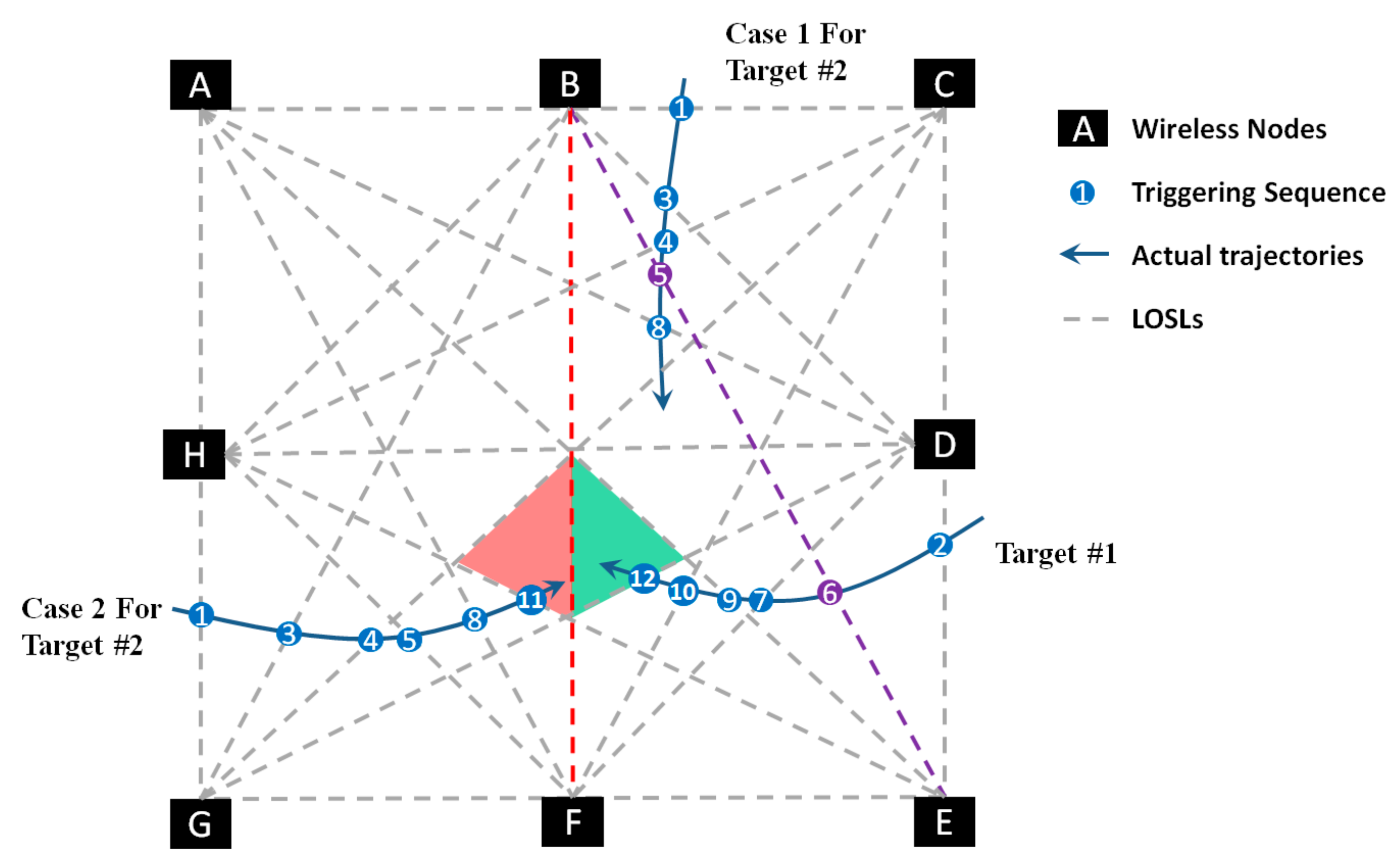
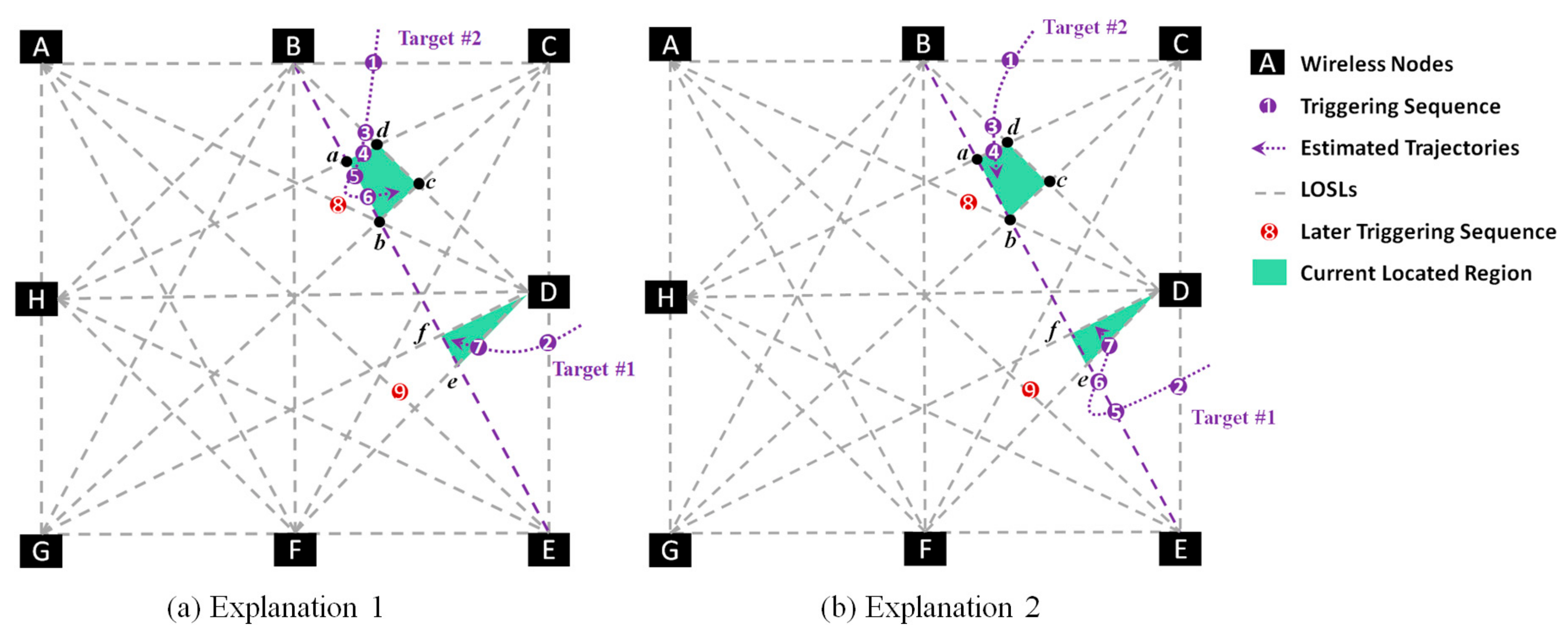
4.2. The Approach for Multiple Targets Tracking
- Explanation 1: is triggered by only Target #2 twice;
- Explanation 2: is triggered by only Target #1 twice;
- Explanation 3: is triggered by Target #2 as and by Target #1 as ;
- Explanation 4: is triggered by Target #1 as and by Target #2 as .
| Algorithm 2. The CP Determination for Tracking Multiple Targets. |
| Initialization: Get the coordinates of all wireless sensor nodes, as well as topology information of all LOSLs. Step 1. Decide the number of targets by triggering LOSL in separated zones if the targets do not meet at the neighbor regions.
Give warning sign and increase the LOSL density to solve the meeting event. end |
5. The Power Consumption Model
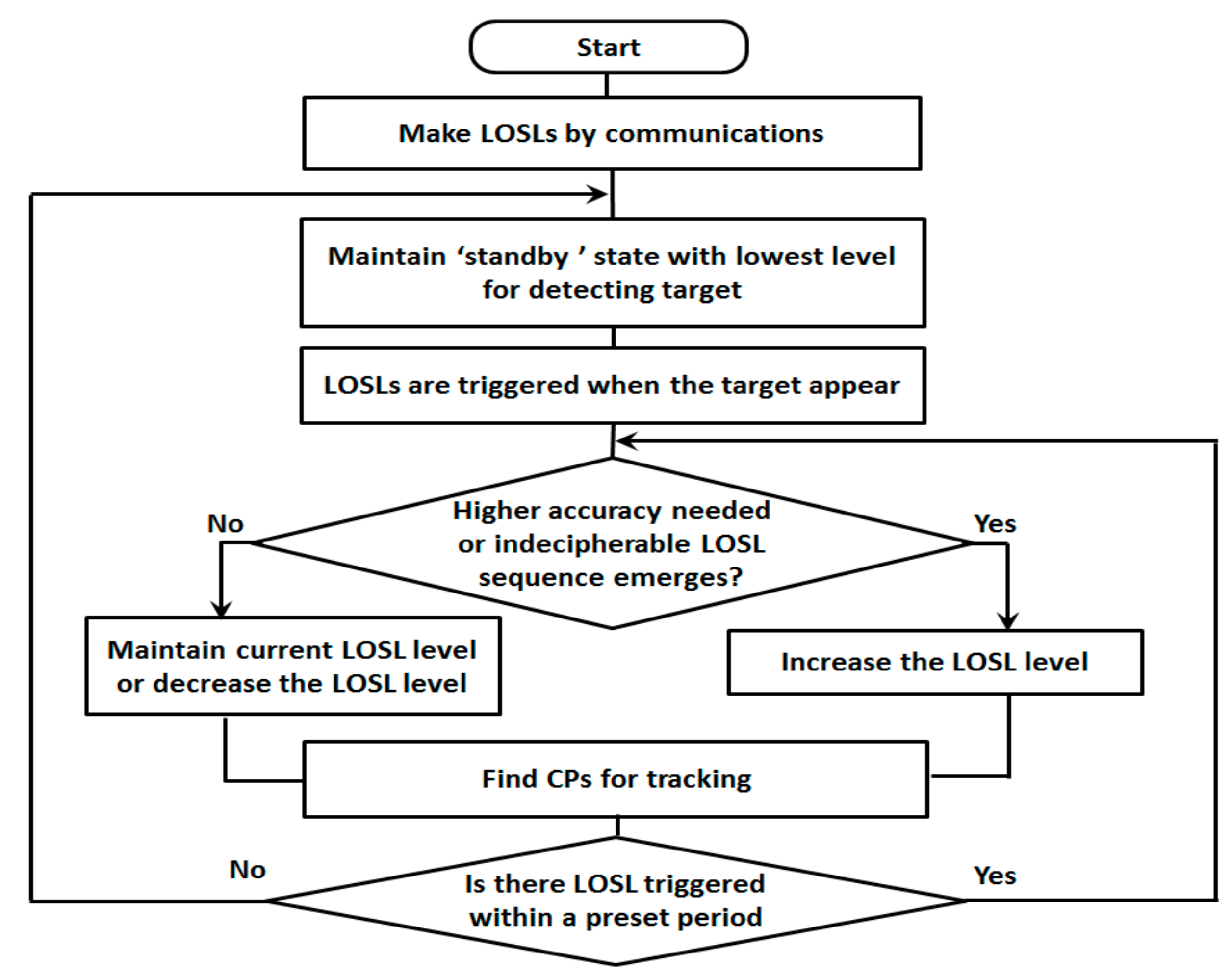
6. The Adaptive Solution for Energy Conservation
7. Performance Evaluation
7.1. The Tracking Performance Evaluation of the Proposed Passive Tracking Method
7.2. The Performance Evaluation of Multi-Target Tracking and Energy Conservation
8. Conclusions and Future Works
Author Contributions
Funding
Conflicts of Interest
References
- Deak, G.; Curran, K.; Condell, J. A survey of active and passive indoor localisation systems. Comput. Commun. 2012, 35, 1939–1954. [Google Scholar] [CrossRef]
- Youssef, M.; Mah, M.; Agrawala, A. Challenges: Device-free Passive Localization for Wireless Environments. In Proceedings of the 13th Annual International Conference on Mobile Computing and Networking, MOBICOM 2007, Montréal, QC, Canada, 9–14 September 2007; pp. 222–229. [Google Scholar]
- Chen, L.; Li, B.; Zhao, K.; Rizos, C.; Zheng, Z. An improved algorithm to generate a Wi-Fi fingerprint database for indoor positioning. Sensors 2013, 13, 11085–11096. [Google Scholar] [CrossRef] [PubMed]
- Nannuru, S.; Li, Y.; Zeng, Y.; Coates, M.; Yang, B. Radio-frequency tomography for passive indoor multitarget tracking. IEEE Trans. Mob. Comput. 2013, 12, 2322–2333. [Google Scholar] [CrossRef]
- Zhou, B.; Kim, N.; Kim, Y. A passive indoor tracking scheme with geometrical formulation. IEEE Antennas Wirel. Propag. Lett. 2016, 15, 1815–1818. [Google Scholar] [CrossRef]
- Zhou, B.; Sun, C.; Ahn, D.; Kim, Y. A novel passive tracking scheme exploiting geometric and intercept theorems. Sensors 2018, 18, 895. [Google Scholar] [CrossRef] [PubMed]
- Zheng, X.; Yang, J.; Chen, Y.; Xiong, H. An adaptive framework coping with dynamic target speed for device-free passive localization. IEEE Trans. Mob. Comput. 2015, 14, 1138–1150. [Google Scholar]
- Wilson, J.; Patwari, N. Radio tomographic imaging with wireless networks. IEEE Trans. Mob. Comput. 2010, 9, 621–632. [Google Scholar] [CrossRef]
- Zhou, B.; Ahn, D.; Lee, J.; Sun, C.; Ahmed, S.; Kim, Y. An Energy Conservation Tracking System for the Device-Free Target in Wireless Sensor Networks. In Proceedings of the IEEE International Conference on Knowledge Innovation and Invention, Jeju Island, Korea, 23–27 July 2018. [Google Scholar]
- Lei, Q.; Zhang, H.J.; Sun, H.; Tang, L.L. A New Elliptical Model for Device-Free Localization. Sensors 2016, 16, 577. [Google Scholar] [CrossRef] [PubMed]
- Wilson, J.; Patwari, N. See through walls: Motion tracking using variance-based radio tomography networks. IEEE Trans. Mob. Comput. 2011, 10, 612–621. [Google Scholar] [CrossRef]
- Edelstein, A.; Rabbat, M. Background subtraction for online calibration of baseline RSS in RF sensing networks. IEEE Trans. Mob. Comput. 2013, 12, 2386–2398. [Google Scholar] [CrossRef]
- Wilson, J.; Patwari, N. A fade level skew-laplace signal strength model for device-free localization with wireless networks. IEEE Trans. Mob. Comput. 2012, 11, 947–958. [Google Scholar] [CrossRef]
- Viani, F.; Rocca, P.; Oliveri, G.; Trinchero, D.; Massa, A. Localization, tracking, and imaging of targets in wireless sensor networks: An invited review. Radio Sci. 2011, 46, 1–12. [Google Scholar] [CrossRef]
- Talampas, M.; Low, K.S. An enhanced geometric filter algorithm with channel diversity for device-free localization. Trans. Instrum. Meas. 2016, 65, 378–387. [Google Scholar] [CrossRef]
- Wang, J.; Gao, Q.; Cheng, P.; Yu, Y.; Xin, K.; Wang, H. Lightweight robust device-free localization in wireless networks. IEEE Trans. Ind. Electron. 2014, 61, 5681–5689. [Google Scholar] [CrossRef]
- Xiao, W.; Song, B.; Yu, X.; Chen, P. Nonlinear optimization-based device-free localization with outlier link rejection. Sensors 2015, 15, 8072–8087. [Google Scholar] [CrossRef] [PubMed]
- Mao, X.; Tang, S.; Wang, J.; Li, X.Y. iLight: Device-free passive tracking using wireless sensor networks. IEEE Sens. J. 2013, 13, 3785–3792. [Google Scholar] [CrossRef]
- Ramachandran, A.; Jagannathan, S. Spatial Diversity in Signal Strength Based WLAN Location Determination Systems. In Proceedings of the 32nd IEEE Conference on Local Computer Networks (LCN 2007), Dublin, Ireland, 15–18 October 2007; pp. 10–17. [Google Scholar]
- Sen, A.; Gümüsay, M.U.; Kavas, A.; Bulucu, U. Programming an artificial neural network tool for spatial interpolation in GIS—A case study for indoor radio wave propagation of WLAN. Sensors 2008, 8, 5996–6014. [Google Scholar] [CrossRef] [PubMed]
- Han, L.; Peng, Y.; Wang, P.; Li, Y. An Off-Grid turbo channel estimation algorithm for millimeter wave communications. Sensors 2016, 16, 1562. [Google Scholar] [CrossRef] [PubMed]
- Jing, C.; Zhou, B.; Kim, N.; Kim, Y. Performance evaluation of an indoor positioning scheme using infrared motion sensors. Information 2014, 5, 548–557. [Google Scholar] [CrossRef]
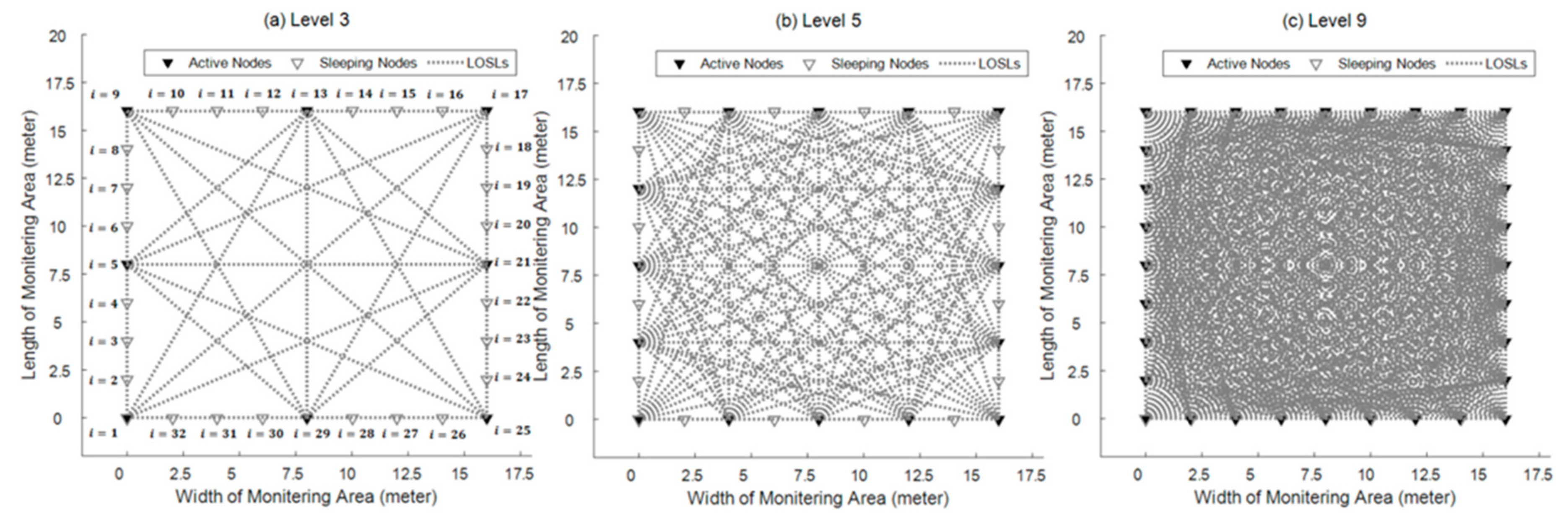
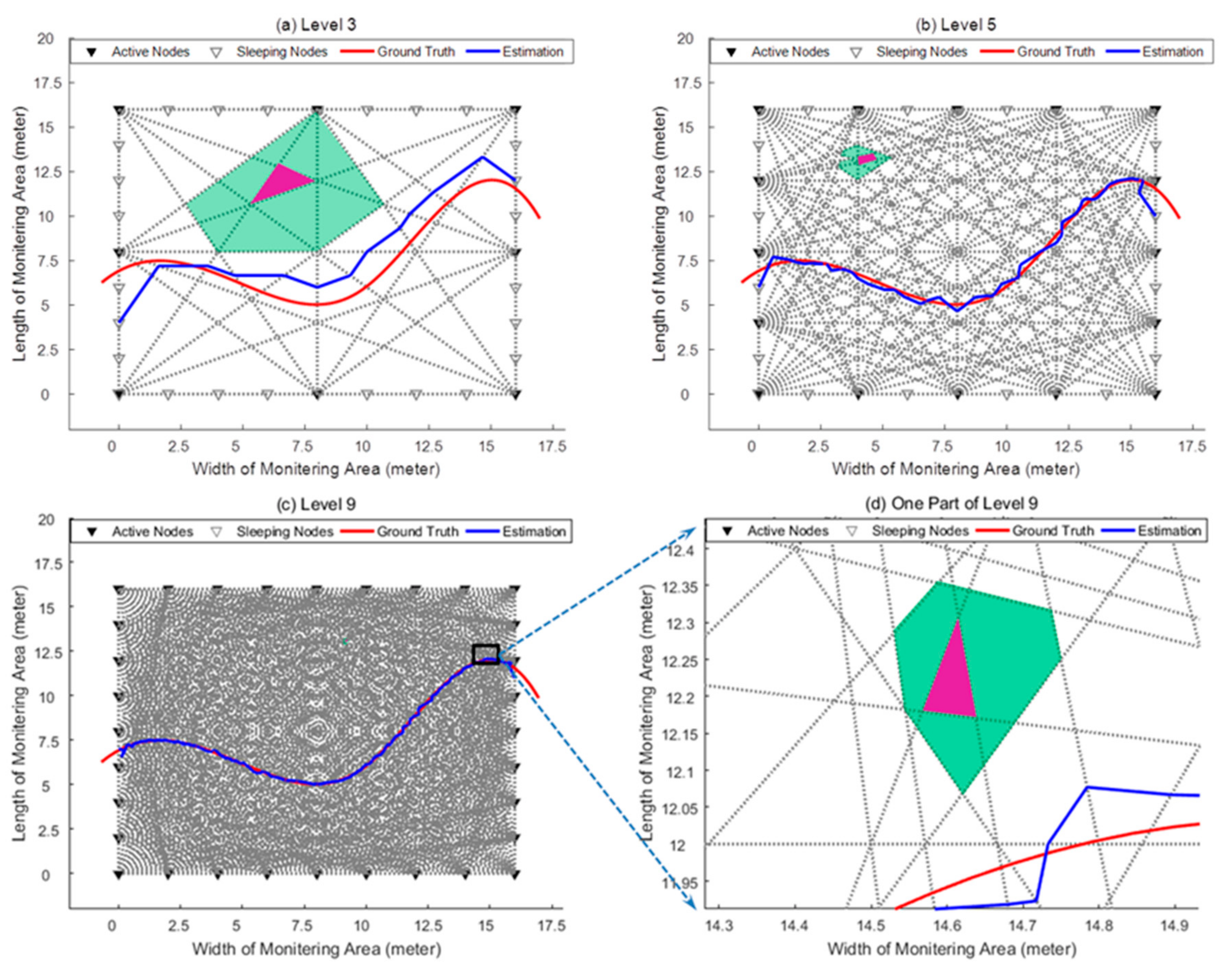
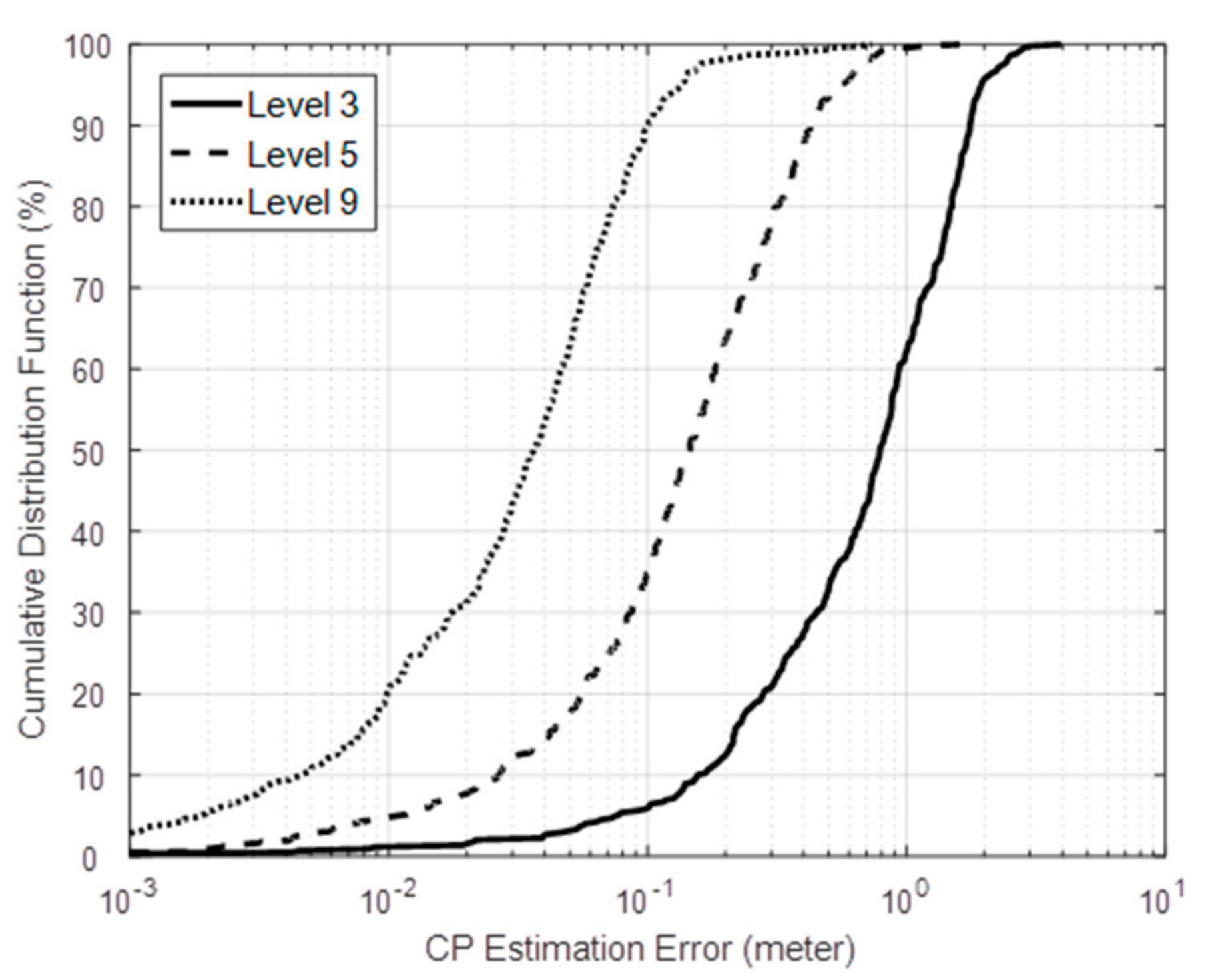
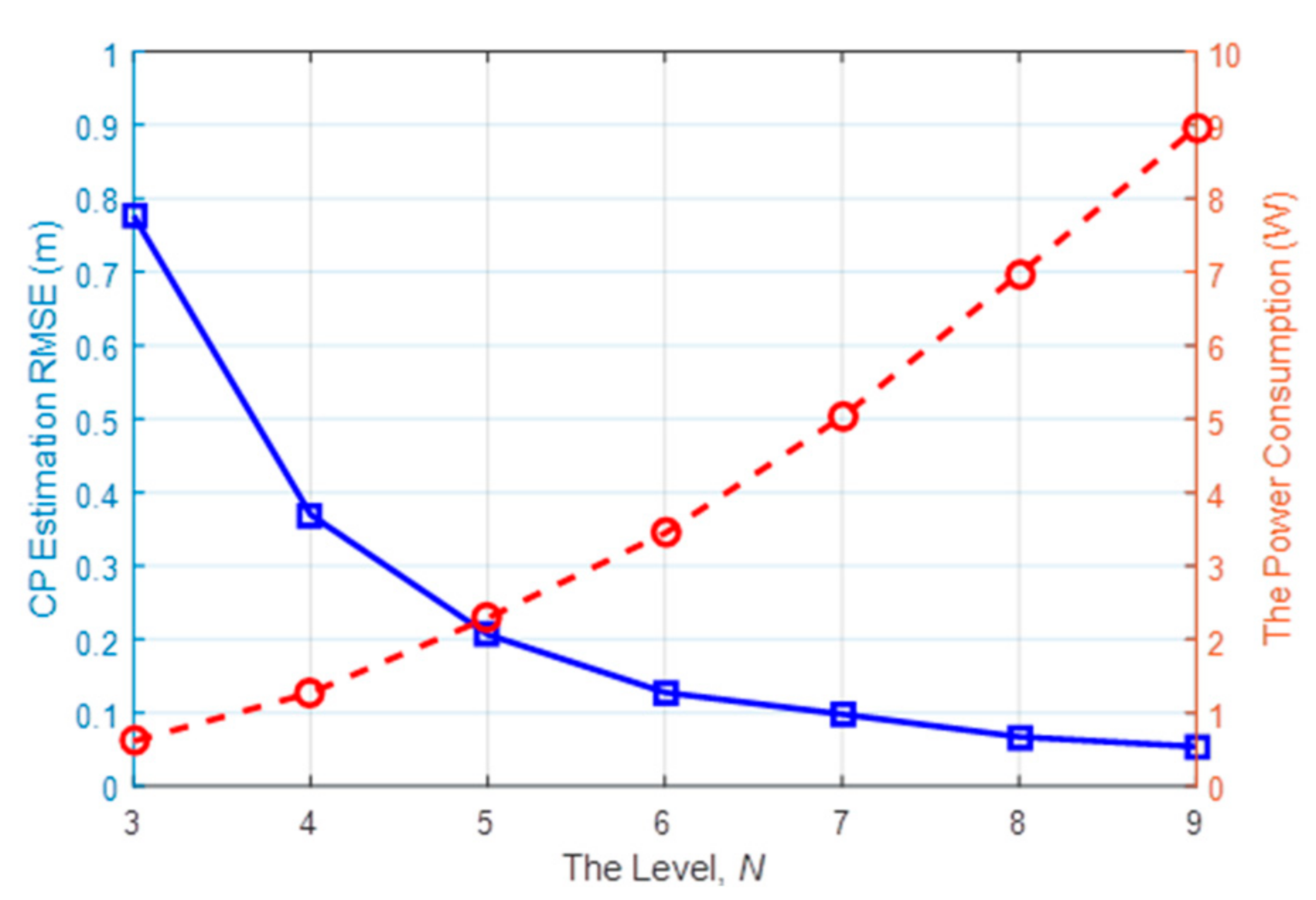
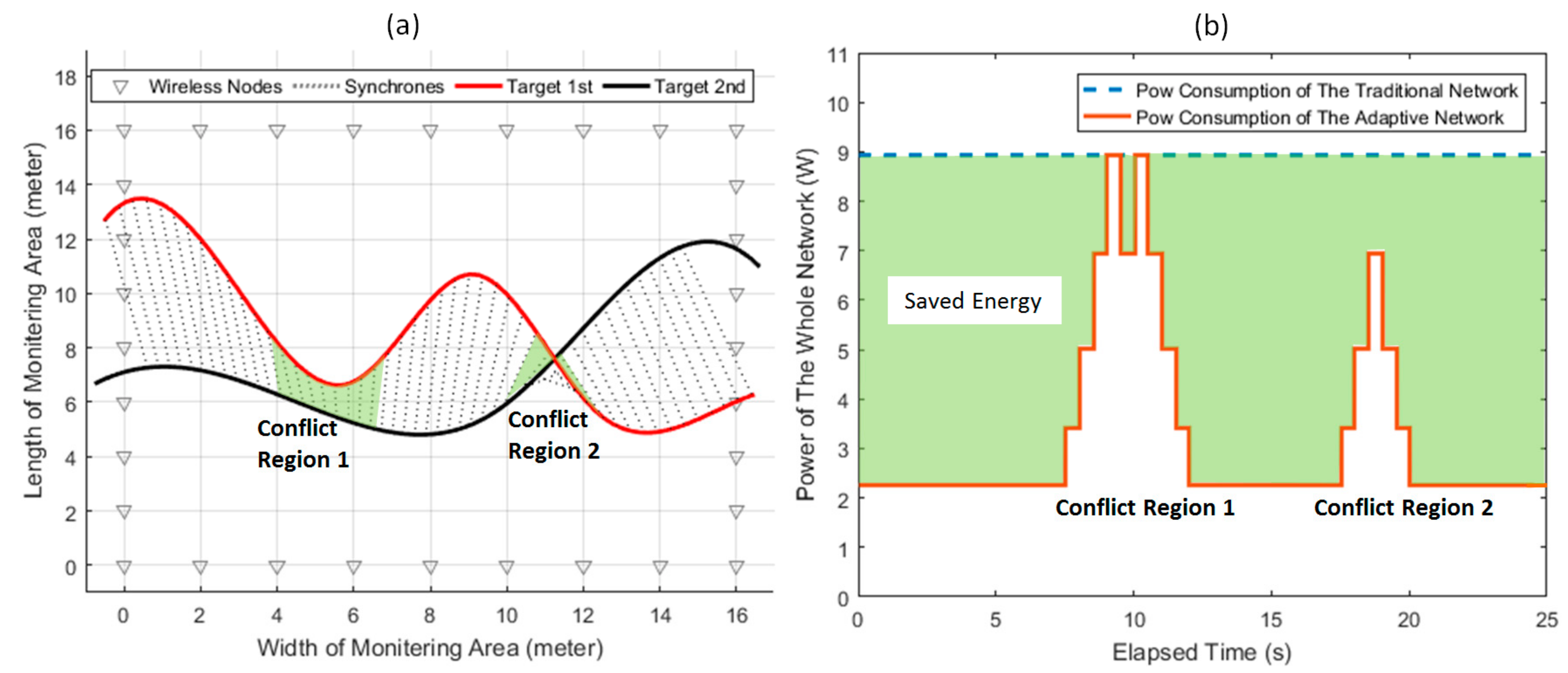
| Level N | Number of Active Nodes | Nodes Set |
|---|---|---|
| 3 | 8 | |
| 4 | 12 | |
| 5 | 16 | |
| 6 | 20 | |
| 7 | 24 | |
| 8 | 28 | |
| 9 | 32 |
| Tracking Scheme | Hardware Cost ① | Variance | Mean Error |
|---|---|---|---|
| Proposed Method (Level 5) | 0.0625 nodes/m2 | 0.035 m2 | 0.199 m |
| NOOLR Method | 0.0726 nodes/m2 | 0.037 m2 | 0.214 m |
| RTI Method | 0.0726 nodes/m2 | 0.130 m2 | 0.251 m |
© 2018 by the authors. Licensee MDPI, Basel, Switzerland. This article is an open access article distributed under the terms and conditions of the Creative Commons Attribution (CC BY) license (http://creativecommons.org/licenses/by/4.0/).
Share and Cite
Zhou, B.; Ahn, D.; Lee, J.; Sun, C.; Ahmed, S.; Kim, Y. A Passive Tracking System Based on Geometric Constraints in Adaptive Wireless Sensor Networks. Sensors 2018, 18, 3276. https://doi.org/10.3390/s18103276
Zhou B, Ahn D, Lee J, Sun C, Ahmed S, Kim Y. A Passive Tracking System Based on Geometric Constraints in Adaptive Wireless Sensor Networks. Sensors. 2018; 18(10):3276. https://doi.org/10.3390/s18103276
Chicago/Turabian StyleZhou, Biao, Deockhyeon Ahn, Jungpyo Lee, Chao Sun, Sabbir Ahmed, and Youngok Kim. 2018. "A Passive Tracking System Based on Geometric Constraints in Adaptive Wireless Sensor Networks" Sensors 18, no. 10: 3276. https://doi.org/10.3390/s18103276
APA StyleZhou, B., Ahn, D., Lee, J., Sun, C., Ahmed, S., & Kim, Y. (2018). A Passive Tracking System Based on Geometric Constraints in Adaptive Wireless Sensor Networks. Sensors, 18(10), 3276. https://doi.org/10.3390/s18103276





