Implementation of a Cross-Layer Sensing Medium-Access Control Scheme
Abstract
:1. Introduction
2. Compressed Sensing
3. Cross-Layer CS-MAC Design
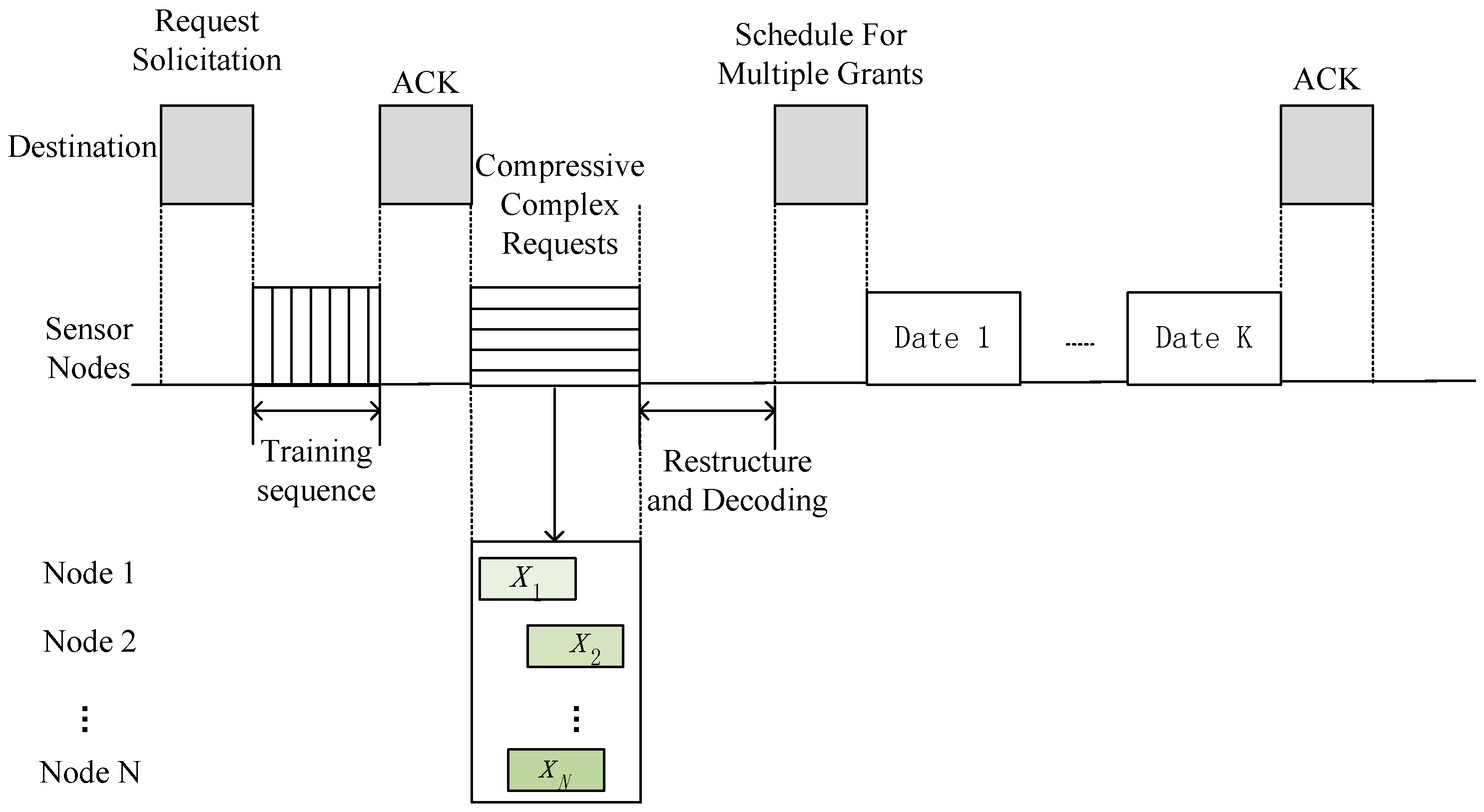
3.1. The Cross-Layer CS-MAC Scheme
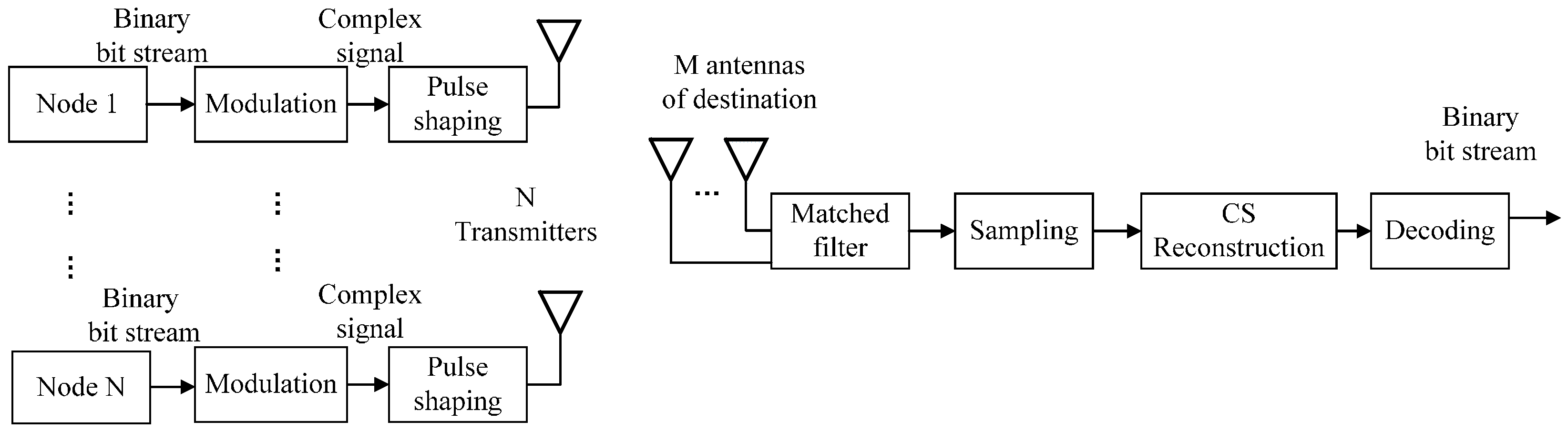
3.2. Compressive Complex Requests during Wireless Transmission
4. The Experimental Results
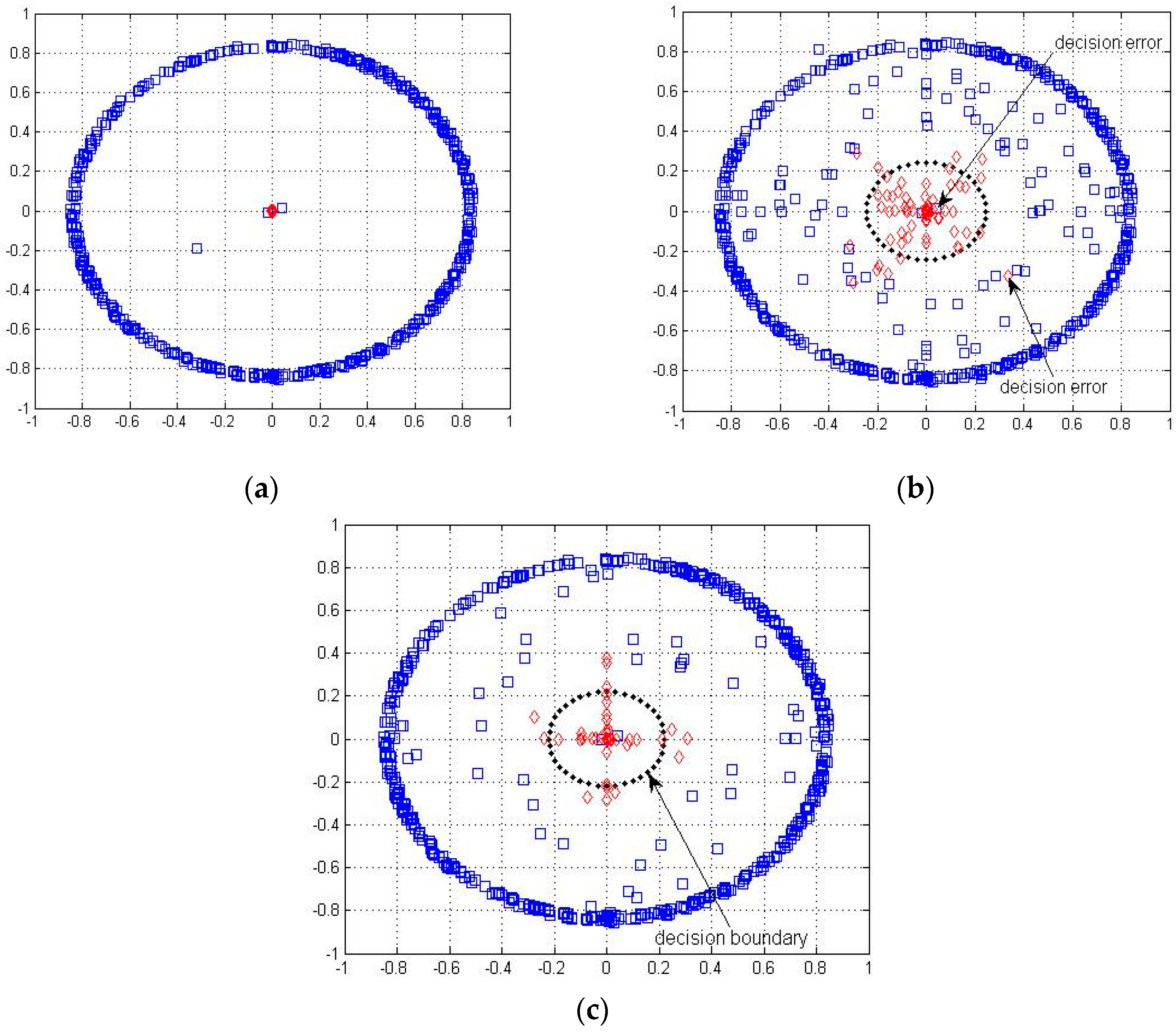
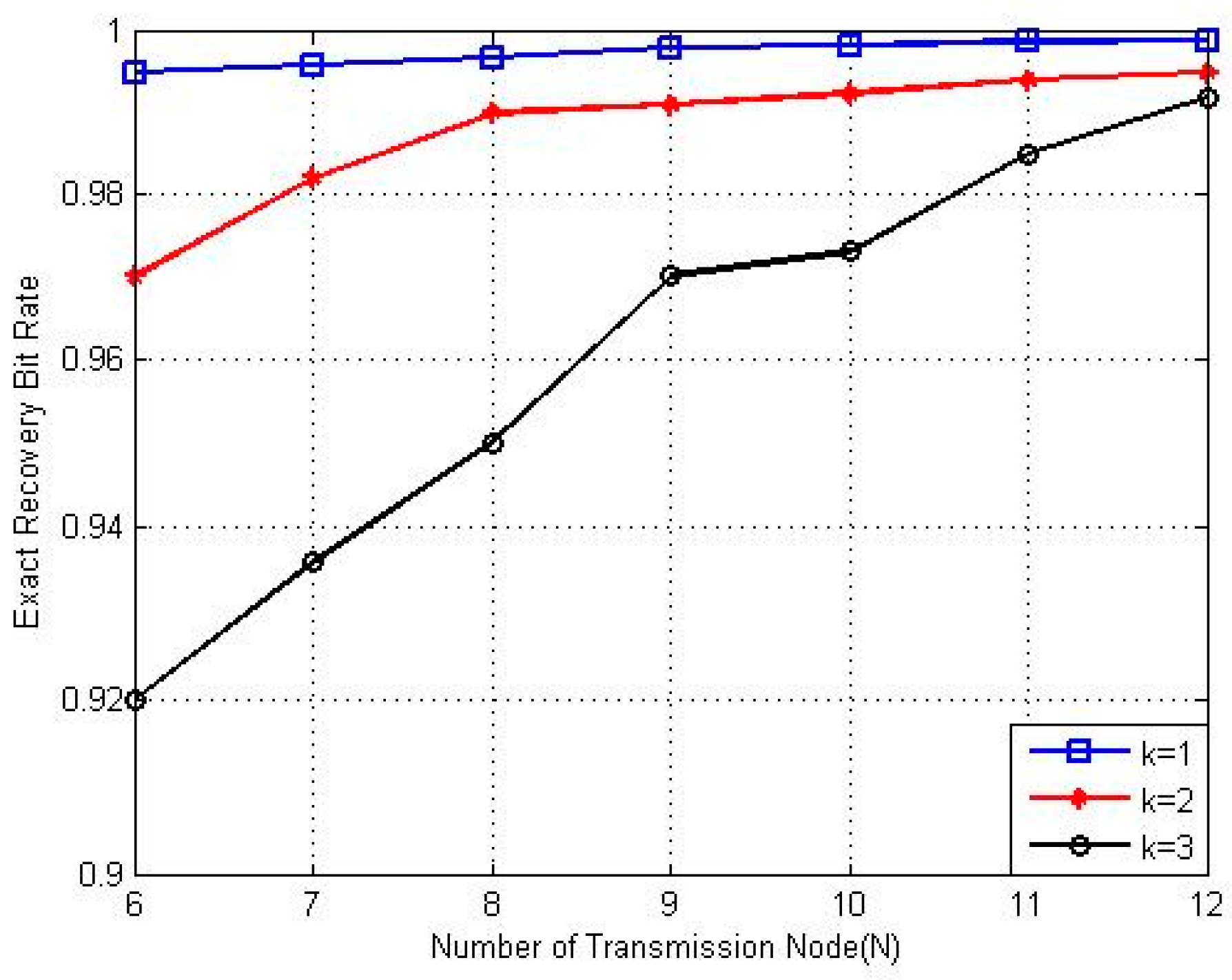
4.1. Determination of Active Nodes
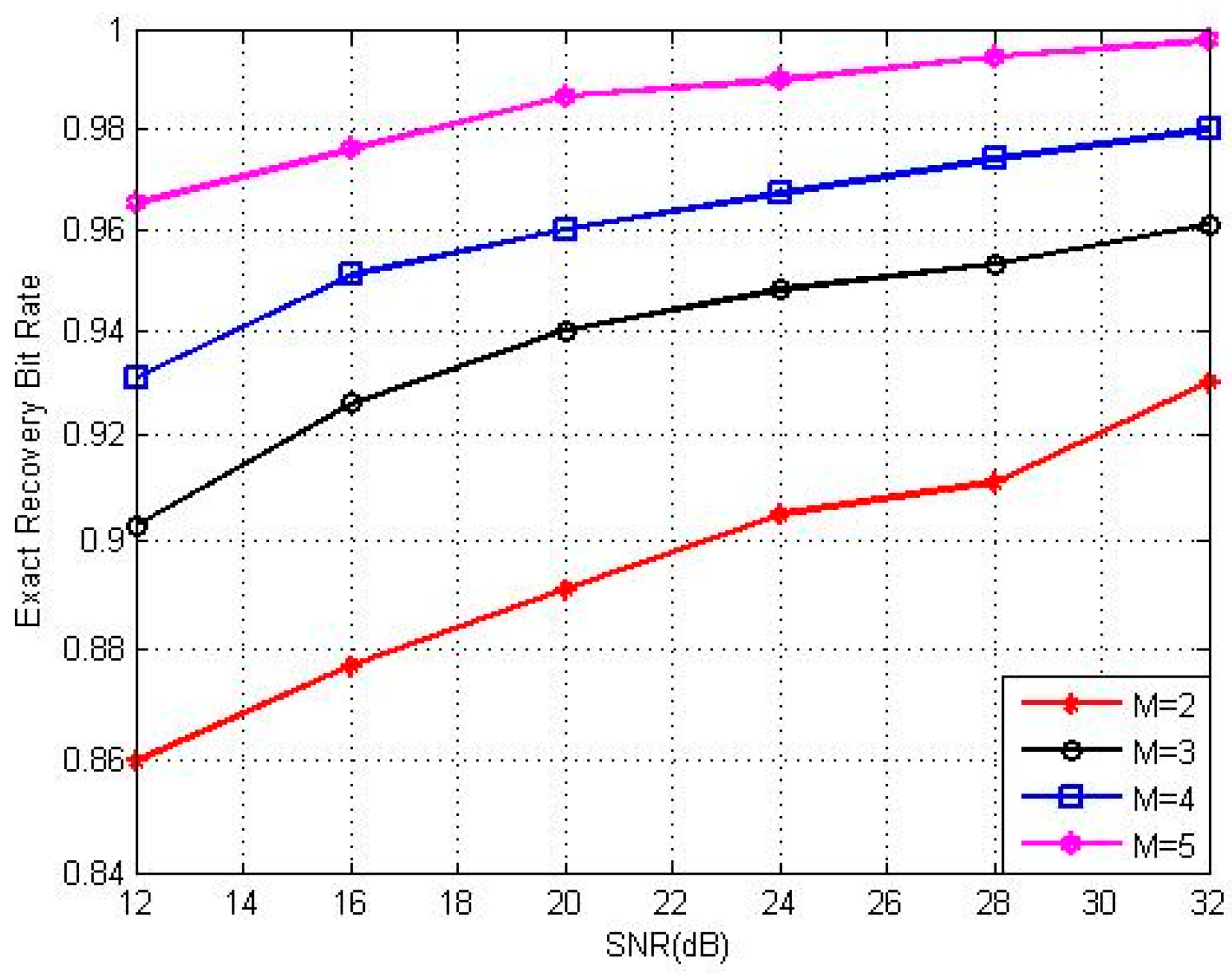
4.2. Identification of Active Nodes
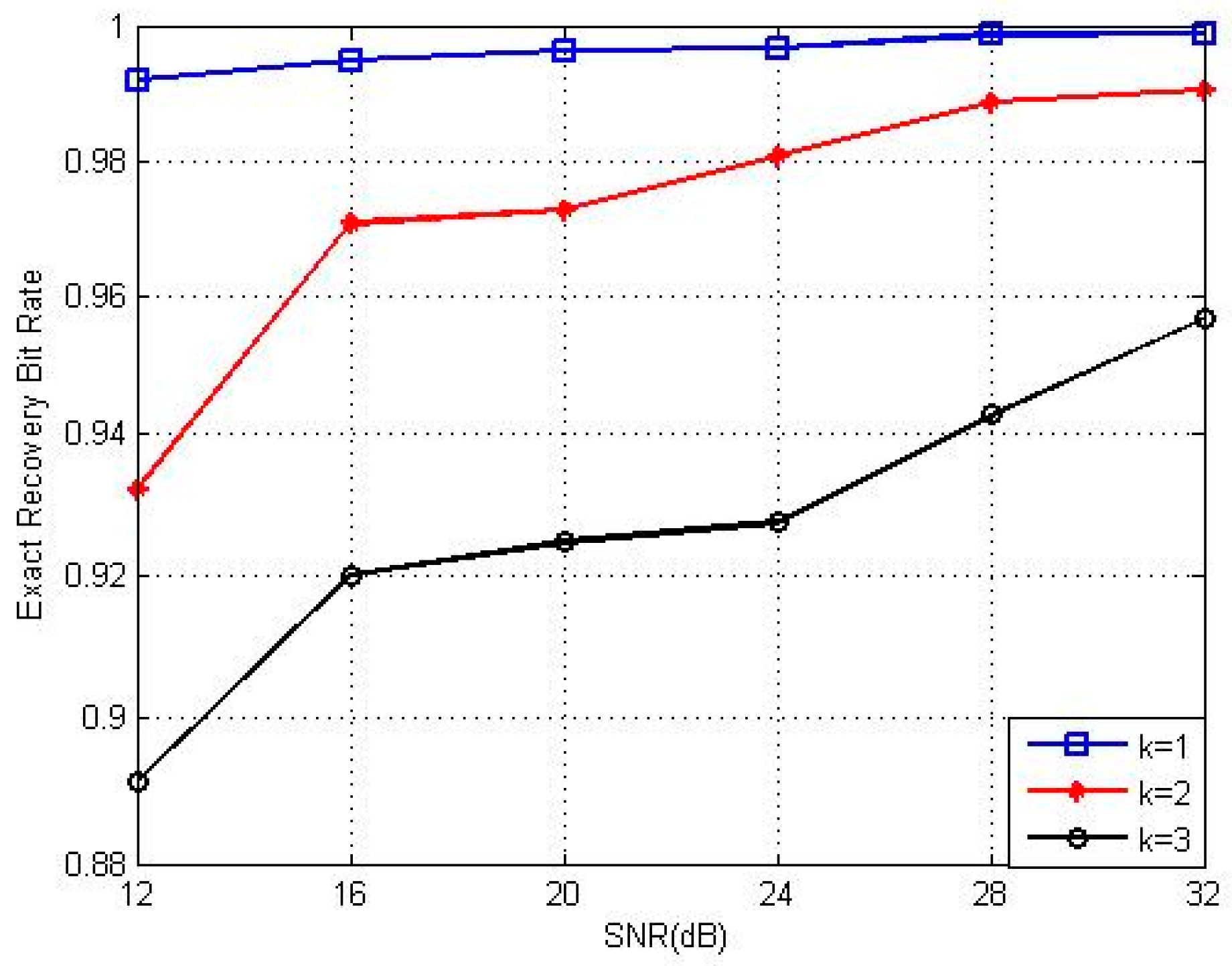
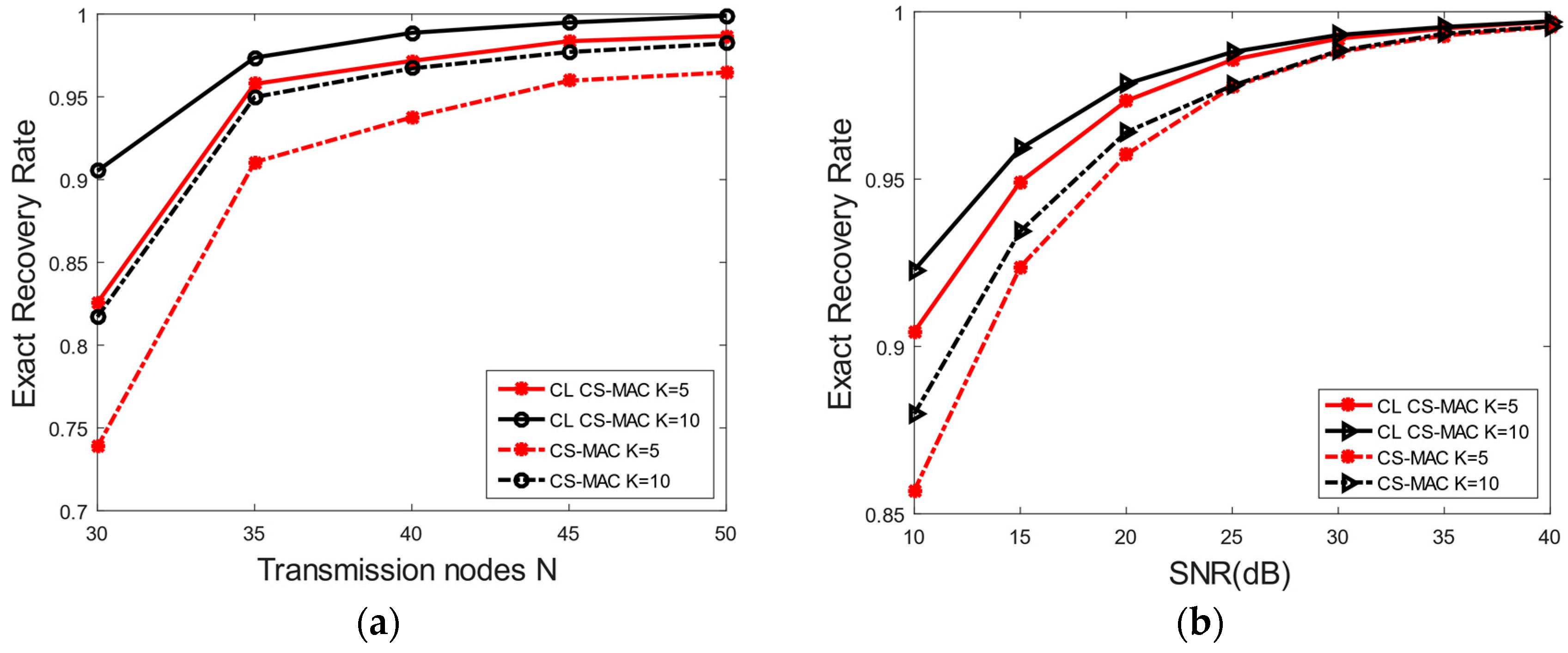
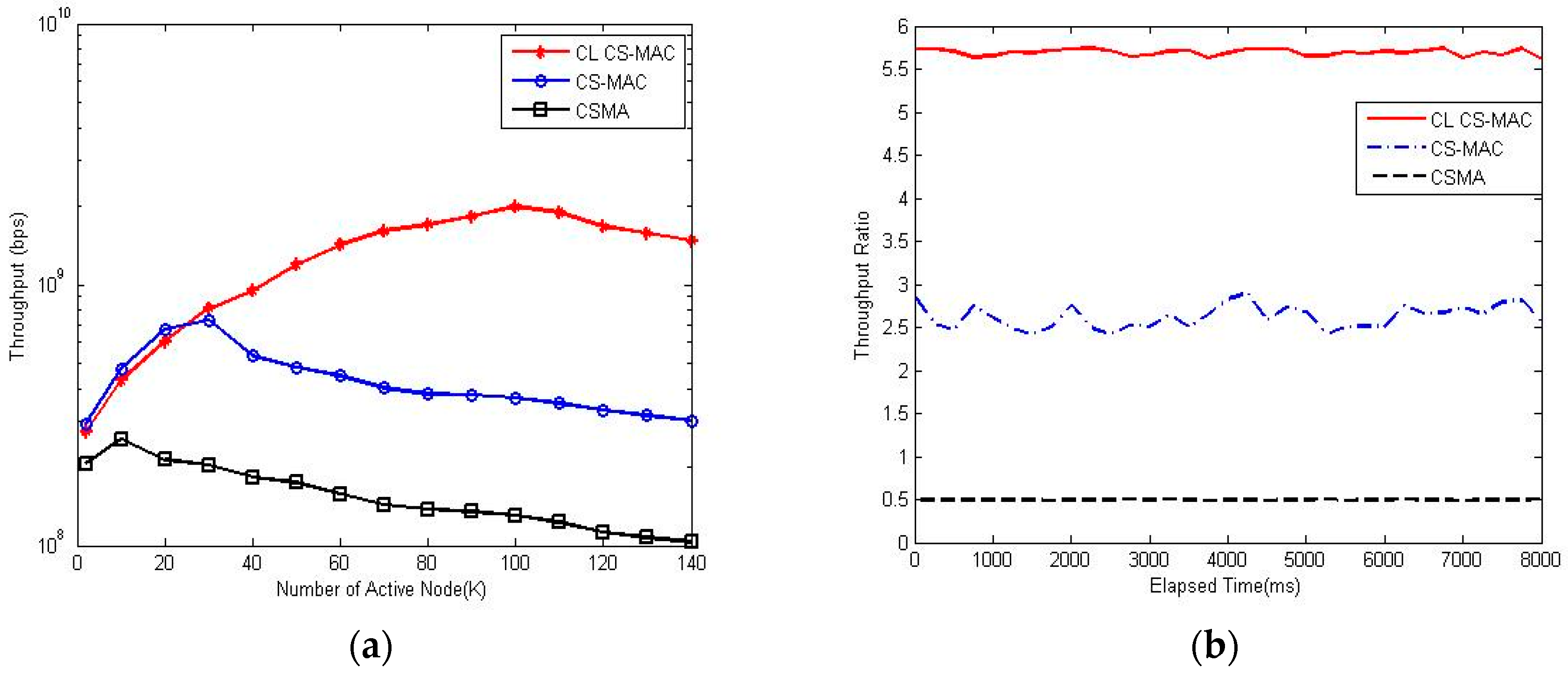
5. Simulation Performance of Cross-Layer CS-MAC Scheme
6. Conclusions
Acknowledgments
Author Contributions
Conflicts of Interest
References
- Needell, D.; Tropp, J.A. Cosamp: Iterative signal recovery from incomplete and inaccurate samples. Commun. ACM 2010, 53, 93–100. [Google Scholar] [CrossRef]
- Bakshi, M.; Jaumard, B.; Kaddour, M.; Narayanan, L. On TDMA scheduling in wireless sensor networks. In Proceedings of the 2016 IEEE Canadian Conference on Electrical and Computer Engineering (CCECE), Vancouver, BC, Canada, 15–18 May 2016; IEEE: New York, NY, USA; pp. 1–6. [Google Scholar]
- Candès, E.J.; Romberg, J.; Tao, T. Robust uncertainty principles: Exact signal reconstruction from highly incomplete frequency information. IEEE Trans. Inf. Theory 2006, 52, 489–509. [Google Scholar] [CrossRef]
- Donoho, D.L. Compressed sensing. IEEE Trans. Inf. Theory 2006, 52, 1289–1306. [Google Scholar] [CrossRef]
- Donoho, D.L. For most large underdetermined systems of linear equations the minimal 𝓁1-norm solution is also the sparsest solution. Commun. Pure Appl. Math. 2006, 59, 797–829. [Google Scholar] [CrossRef]
- Tropp, J.A.; Laska, J.N.; Duarte, M.F.; Romberg, J.K.; Baraniuk, R.G. Beyond Nyquist: Efficient sampling of sparse bandlimited signals. IEEE Trans. Inf. Theory 2010, 56, 520–544. [Google Scholar] [CrossRef]
- Chen, F.; Chandrakasan, A.P.; Stojanovic, V.M. Design and analysis of a hardware-efficient compressed sensing architecture for data compression in wireless sensors. IEEE J. Solid-State Circuits 2012, 47, 744–756. [Google Scholar] [CrossRef]
- Wang, X.; Zhao, Z.; Xia, Y.; Zhang, H. Compressed sensing for efficient random routing in multi-hop wireless sensor networks. Int. J. Commun. Netw. Distrib. Syst. 2011, 7, 275–292. [Google Scholar] [CrossRef]
- Xue, T.; Dong, X.; Shi, Y. A multiple access scheme based on multi-dimensional compressed sensing. In Proceedings of the 2012 IEEE International Conference on Communications (ICC), Ottawa, ON, Canada, 10–15 June 2012; IEEE: New York, NY, USA; pp. 3774–3778. [Google Scholar]
- Qaseem, S.T.; Al-Naffouri, T.Y.; Al-Murad, T.M. Compressive sensing based opportunistic protocol for exploiting multiuser diversity in wireless networks. In Proceedings of the 2009 IEEE 20th International Symposium on Personal, Indoor and Mobile Radio Communications, Toyko, Japan, 13–16 September 2009; IEEE: New York, NY, USA; pp. 1447–1451. [Google Scholar]
- Tan, L.T.; Le, L.B. Compressed sensing based data processing and MAC protocol design for smartgrids. In Proceedings of the 2015 IEEE Wireless Communications and Networking Conference (WCNC), New Orleans, LA, USA, 9–12 March 2015; pp. 2138–2143. [Google Scholar]
- Mao, R.; Li, H. A novel multiple access scheme via compressed sensing with random data traffic. J. Commun. Netw. 2010, 12, 308–316. [Google Scholar] [CrossRef]
- Kaneko, M.; Al Agha, K. Compressed sensing based protocol for interfering data recovery in multi-hop sensor networks. IEEE Commun. Lett. 2014, 18, 42–45. [Google Scholar] [CrossRef]
- Hong, J.P.; Choi, W.; Rao, B.D. Sparsity controlled random multiple access with compressed sensing. IEEE Trans. Wirel. Commun. 2015, 14, 998–1010. [Google Scholar] [CrossRef]
- Xue, T.; Dong, X.; Shi, Y. Multiple access and data reconstruction in wireless sensor networks based on compressed sensing. IEEE Trans. Wirel. Commun. 2013, 12, 3399–3411. [Google Scholar] [CrossRef]
- Lin, T.H.; Kung, H.T. Compressive sensing medium access control for wireless LANs. In Proceedings of the 2012 IEEE Global Communications Conference (GLOBECOM), Anaheim, CA, USA, 3–7 December 2012; IEEE: New York, NY, USA; pp. 5470–5475. [Google Scholar]
- Baraniuk, R.; Davenport, M.; DeVore, R.; Wakin, M. A simple proof of the restricted isometry property for random matrices. Constr. Approx. 2008, 28, 253–263. [Google Scholar] [CrossRef]
- Mitola, J. The software radio architecture. IEEE Commun. Mag. 1995, 33, 26–38. [Google Scholar] [CrossRef]
© 2017 by the authors. Licensee MDPI, Basel, Switzerland. This article is an open access article distributed under the terms and conditions of the Creative Commons Attribution (CC BY) license (http://creativecommons.org/licenses/by/4.0/).
Share and Cite
Su, Y.; Fu, X.; Han, G.; Xu, N.; Jin, Z. Implementation of a Cross-Layer Sensing Medium-Access Control Scheme. Sensors 2017, 17, 816. https://doi.org/10.3390/s17040816
Su Y, Fu X, Han G, Xu N, Jin Z. Implementation of a Cross-Layer Sensing Medium-Access Control Scheme. Sensors. 2017; 17(4):816. https://doi.org/10.3390/s17040816
Chicago/Turabian StyleSu, Yishan, Xiaomei Fu, Guangyao Han, Naishen Xu, and Zhigang Jin. 2017. "Implementation of a Cross-Layer Sensing Medium-Access Control Scheme" Sensors 17, no. 4: 816. https://doi.org/10.3390/s17040816
APA StyleSu, Y., Fu, X., Han, G., Xu, N., & Jin, Z. (2017). Implementation of a Cross-Layer Sensing Medium-Access Control Scheme. Sensors, 17(4), 816. https://doi.org/10.3390/s17040816






